Contents
Complete Guide to Atlassian Cloud SSO (Single Sign-On) Using Okta as OAuth Provider
With Jira OAuth Single Sign-On (SSO) for Atlassian Cloud, you can securely log in to Jira Cloud using your Okta credentials. This app allows you to perform seamless Single Sign-On (SSO) into your Atlassian Access or Jira/Confluence Cloud accounts using your existing OAuth Provider credentials.
Pre-requisites
1. Atlassian Guard (Atlassian Access) Subscription:
Atlassian Guard is an additional subscription applied across the Atlassian Cloud products like Jira Software, Jira Service Management, Jira Work Management, Confluence, and Bitbucket. It is needed for Single Sign-On (SSO) or any Cloud Service that comes under Atlassian Guard.
2. Domain Verification:
The first step of Atlassian Guard starts with the Domain Verification process to enforce SSO on the managed user accounts. This process verifies that you own a valid domain for managing the user accounts and use the same domain name for the email addresses.
Download And Installation
- Log into your Jira instance as an admin.
- Navigate to Apps → Explore more apps from the header menu.
- Next, search for the miniOrange OAuth/OpenID SSO app.
- Click on Try it free to begin a new trial of the app.
- On the menu bar click on Apps and locate the OAuth/OpenID SSO app and click .
In this guide, we will demonstrate the setup in three parts:
1: Configure OAuth SSO connection between miniOrange App (as OAuth Client) and Okta (as OAuth Provider).
2: Configure SAML SSO connection between Atlassian Guard (as SP) and miniOrange App (as IDP).
3: Add users to the SSO Authentication policy, and enforce the SSO.
Step 1: Configure Okta as a OAuth Provider
- Once the plugin is installed select the Apps dropdown from the top menu and click on mO Jira OAuth/OIDC SSO option.
- Next, you will be prompted with a welcome pop-up window. Click Start Configuration.
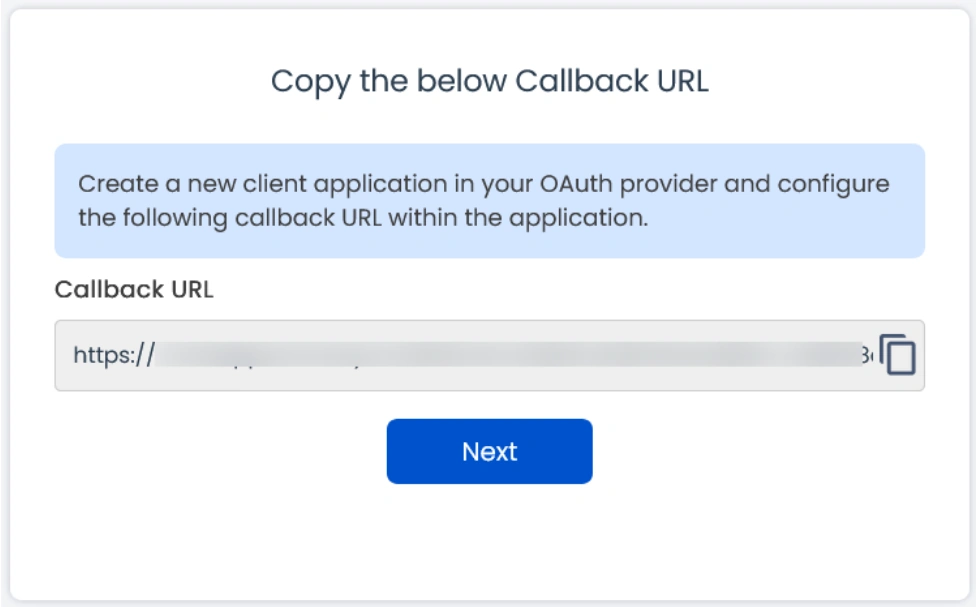
- Copy the Callback URL and keep it handy as it will be required while setting up the OAuth application in Okta.
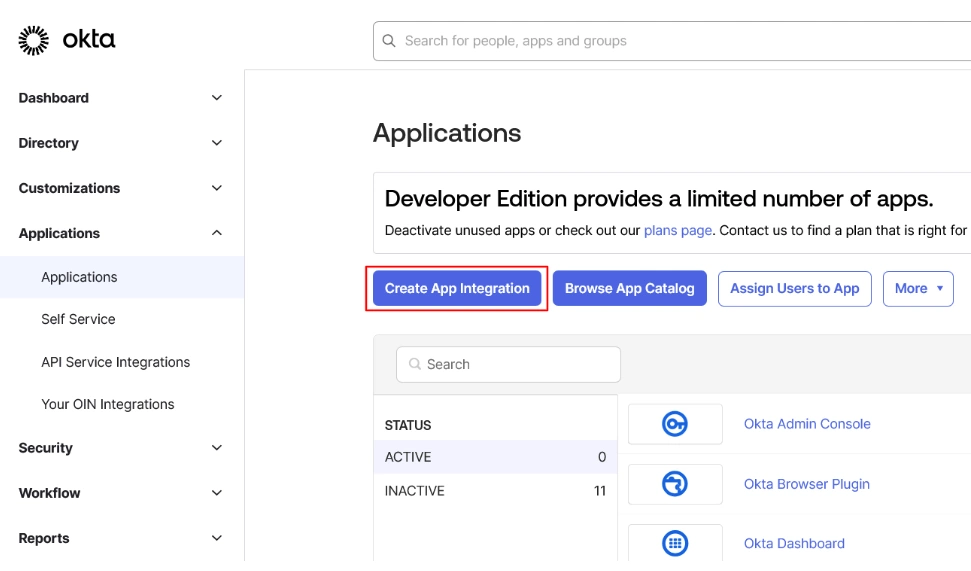
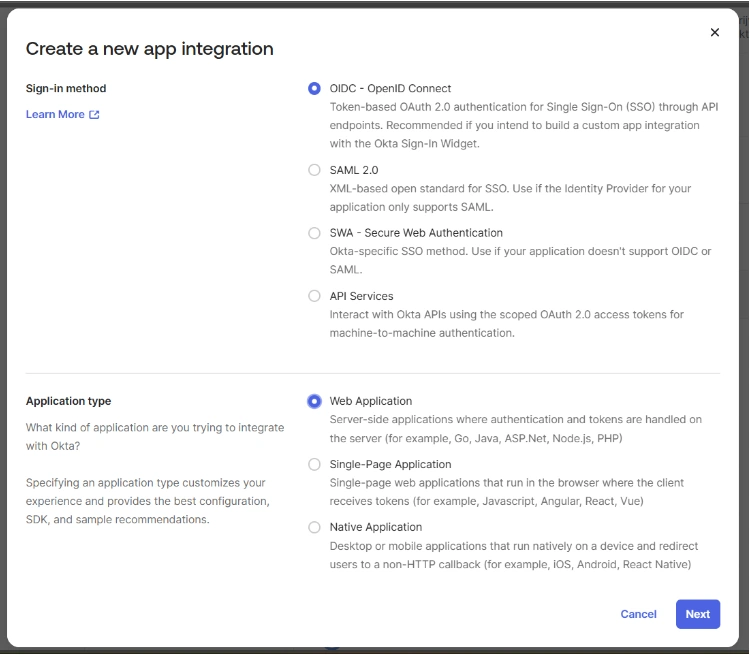
- After copying the callback URL, navigate to the Okta admin dashboard and click on Applications → Create App Integration.
- Here, choose OIDC - OpenID Connect as a Sign-in method, select Web Application as the Application type, and click Next.
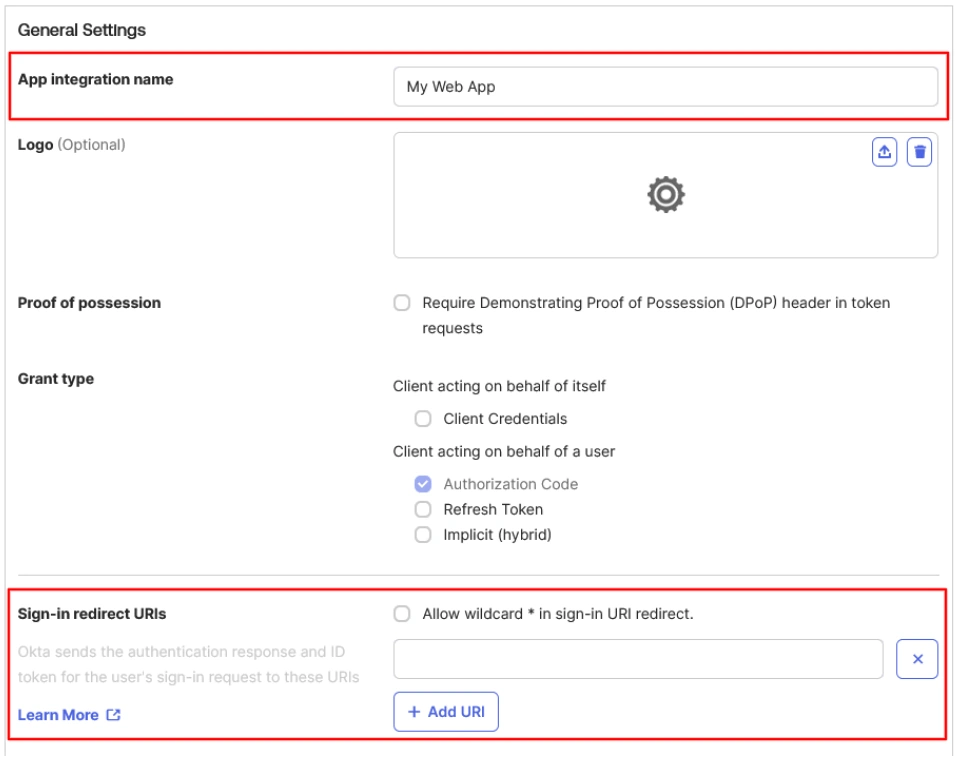
- Now, enter the App Integration Name and Callback URL in the Sign-in redirect URIs, and proceed with the OAuth app configuration.
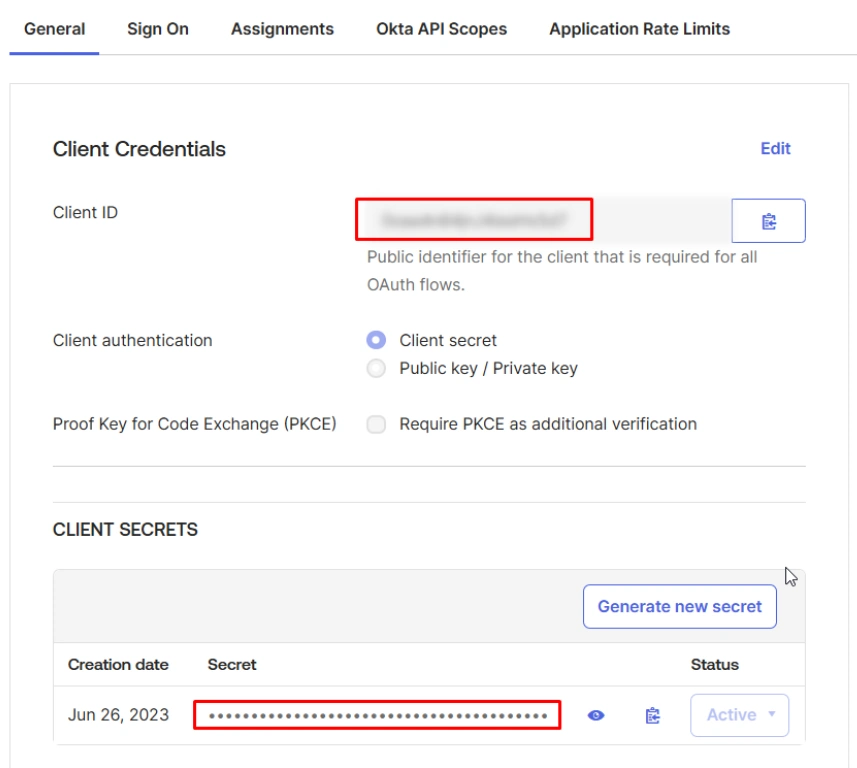
- Copy the Client ID and Client Secret.
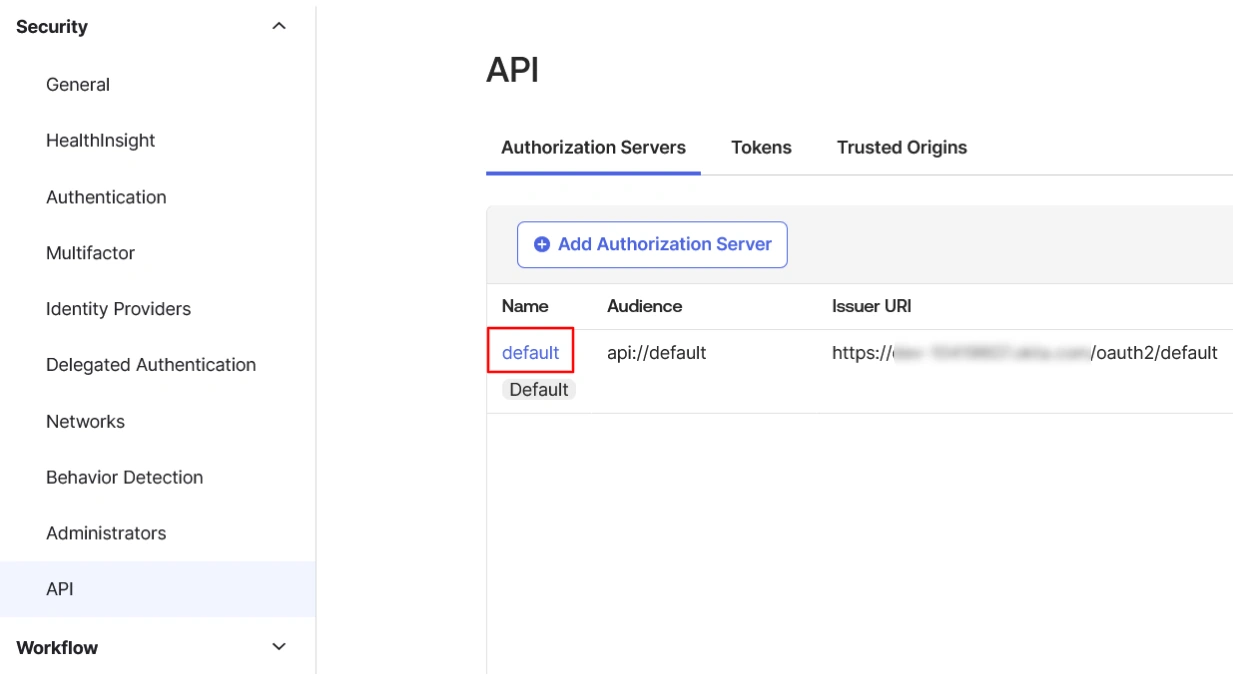
- Then go to the Security → API page from the Okta dashboard.
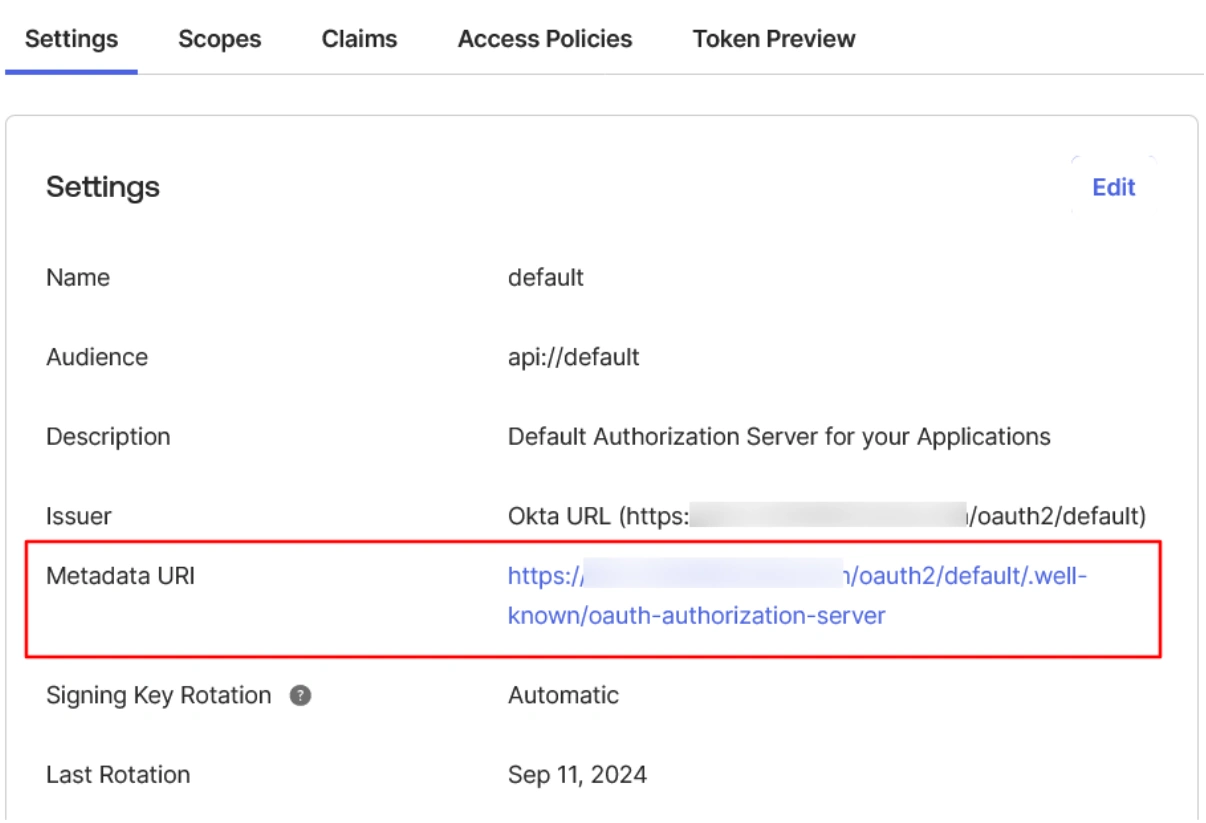
- Under the Authorization Servers tab select the default server.
- Then click on the link given in the Metadata URI field.
- Copy the Authorization endpoint, Token endpoint, etc., and keep it handy.
- Now, return to the miniOrange App configuration page and click Next from the Callback URL screen.
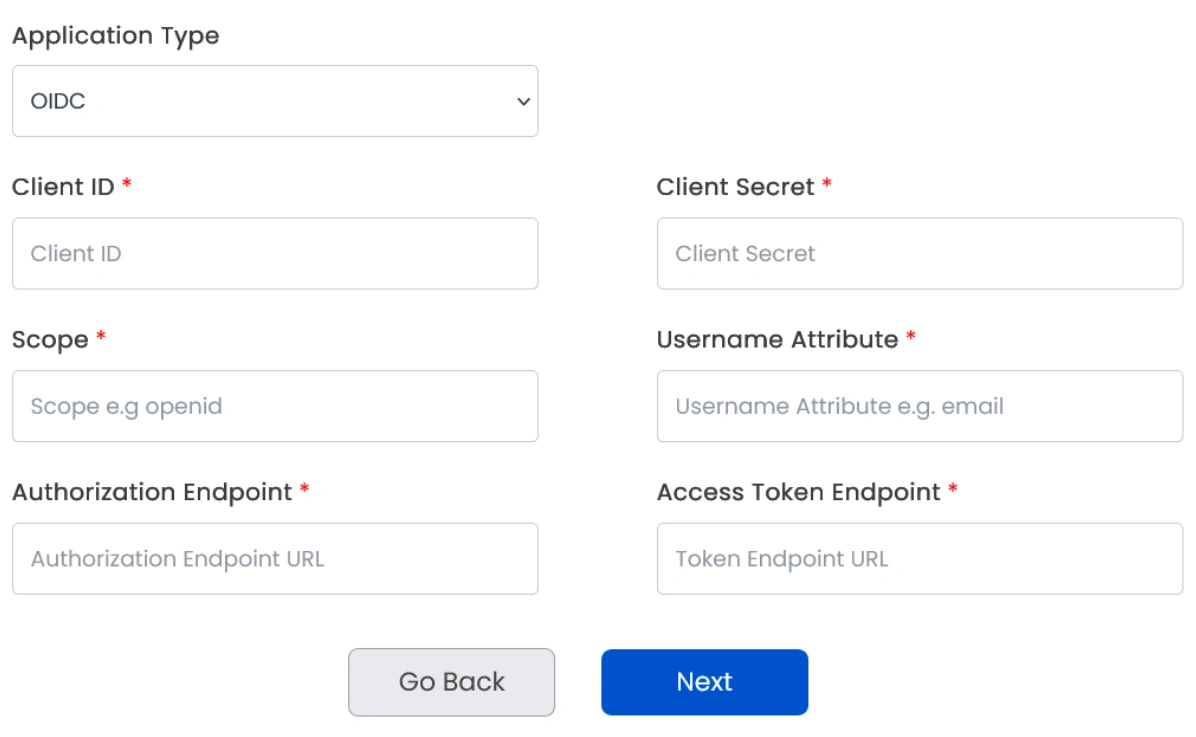
- Select Application Type as OIDC. Enter Client ID, Client Secret, Scopes (such as email, openid, etc), and other required endpoints copied in the previous step. Then click Next.
Step 2: Set up SSO between Atlassian Guard and miniOrange
- In the next window, you’ll find the Plugin Metadata details.
- Copy IDP Entity ID, IDP SSO URL, and IDP Public X.509 Certificate and keep it handy. You’ll need these to configure the Identity Provider in the Atlassian Guard.
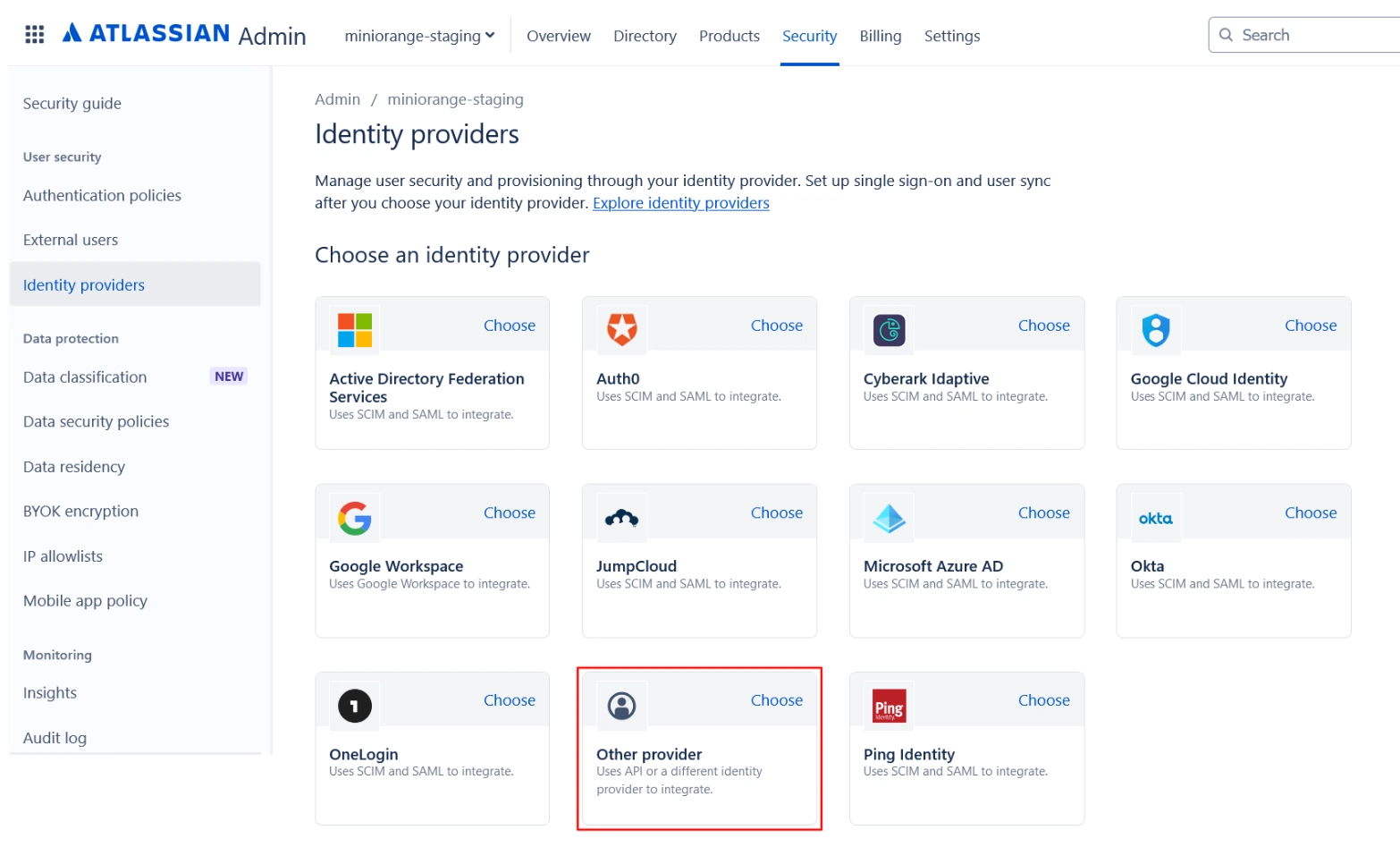
- Open the Atlassian Admin Console and go to the Security tab.
- Click on Identity providers and select Other provider.
- Provide an appropriate name, select Set up SAML Single Sign-On, and click Next.
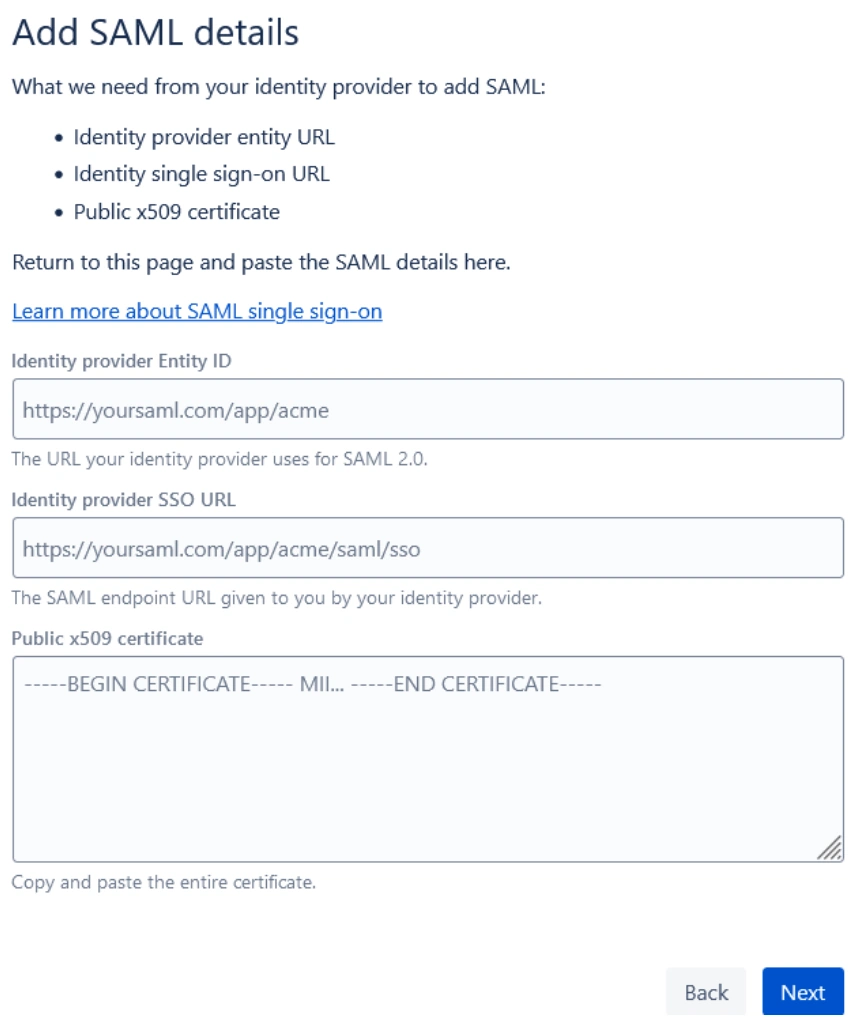
- Now, paste the IDP Entity ID, IDP SSO URL, and Public X.509 Certificate that you copied from the plugin configuration.
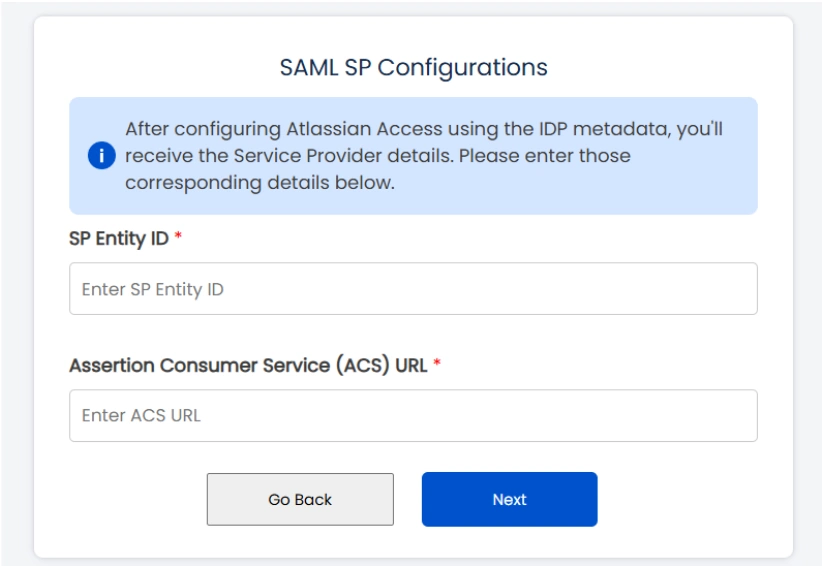
- Click Next and copy the Service Provider Entity ID and Service Provider Assertion Consumer Service URL. Keep these handy as they’re required to complete the plugin configuration.
- Complete the rest of the Atlassian Guard configuration
- Once you’re done, return to the plugin configuration page, go to the SAML IDP Metadata tab, and click Next.
- Enter the SP Entity ID and Assertion Consumer Service (ACS) URL that you copied, and click Next.
Note: In case you manage multiple organizations, you’ll have to select the intended one after accessing the admin console.
Step 3: Configure SSO Authentication Policy
Once all the SSO Configurations are done, you need to add users to the Authentication Policy and enforce Single Sign-On.
Follow these steps:
- Log in to Atlassian Cloud Admin Console, and go to the Security tab.
- Under the Authentication Policies section, find the respective SSO policy and click Edit.
- Select the checkbox for Enforce single sign-on option, then go to the Members section and add the new users to the policy.

