Confluence Using SCIM User And Group Provisioning For Okta
User Sync & Group Sync app provisions user and group information from Okta to Confluence. Users, groups and directory details can by provisioned using SCIM. SCIM provisioning works based on events performed on IDP. This way the administrator only needs to manage user accounts in Okta.
This reduces the administration time required to create users and groups in Confluence modules such as Confluence.
Video Setup Guide
Download and Installation
- Log into your atlassian instance as admin.
- Navigate to the settings menu and Click Manage Apps.
- Click on Find new apps .
- Locate miniOrange User and Group Sync app.
- Click Try free to begin a new trial or Buy now to purchase a license.
- Enter your information and click Generate license when redirected to MyAtlassian.
- Click Apply license.
Step 1: Get SCIM Client Details
- In the Configuration tab, please select OKTA provider.
- In the popup, please select SCIM method to perform user and group synchronization.
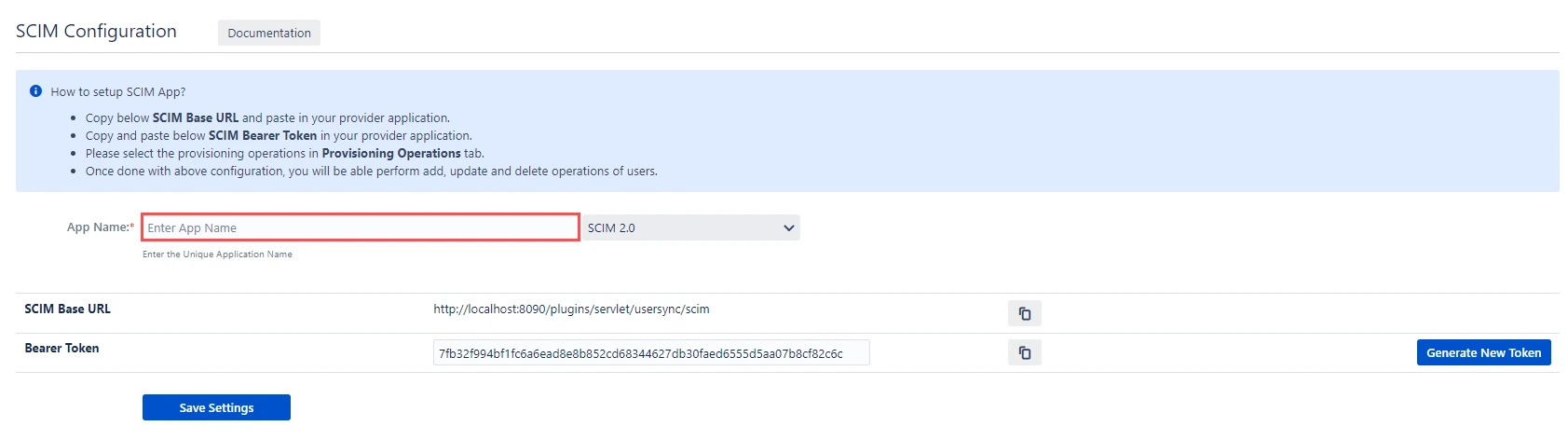
- In SCIM configuration, please enter App Name and click on Save Settings button. Copy the SCIM Base URL and SCIM Bearer Token, these will be used later to configure SCIM application on OKTA. Additionally, you can choose from SCIM 1.1 or SCIM 2.0.

Step 2: Setup Okta SCIM Configurations
- Login to your Okta organisation as a user with administrator privileges.
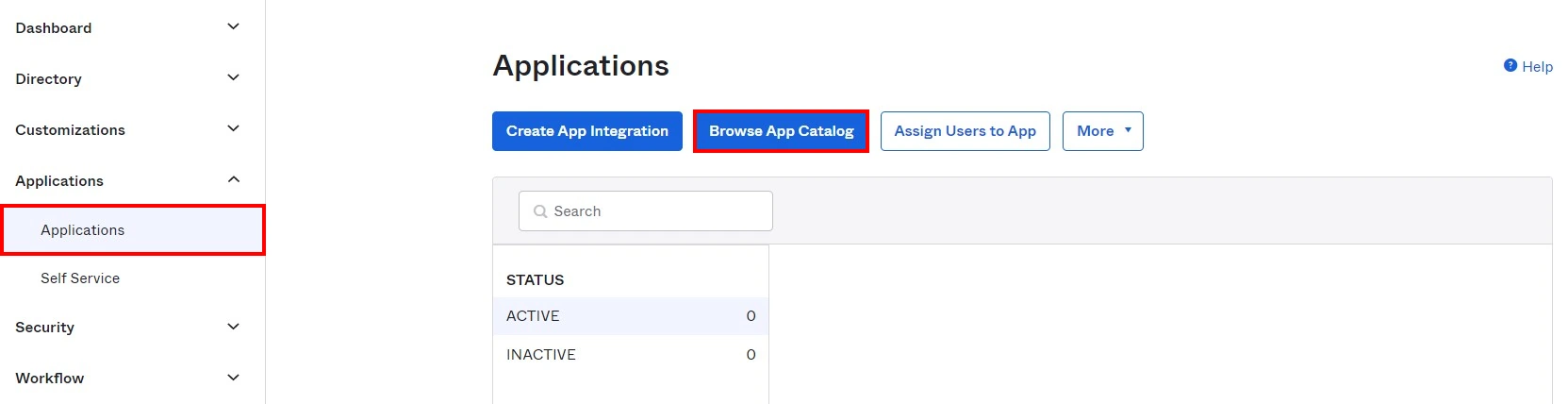
- Navigate to Admin Portal > Applications. Click on Browse App Catalog.
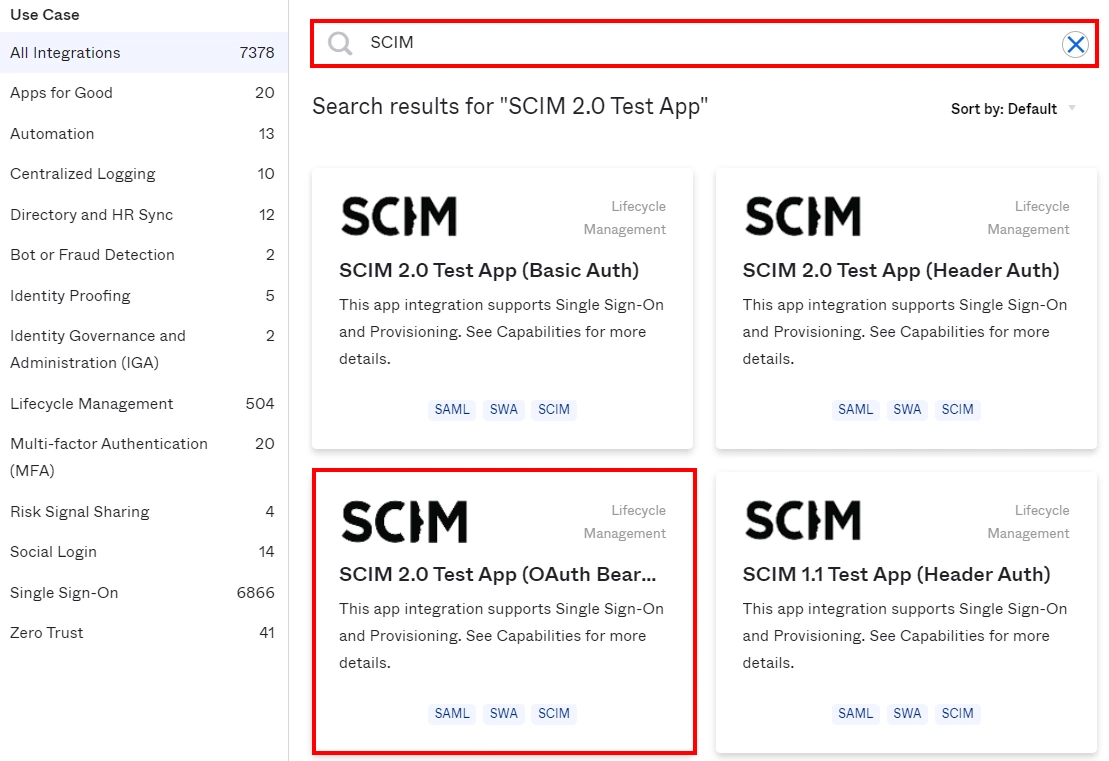
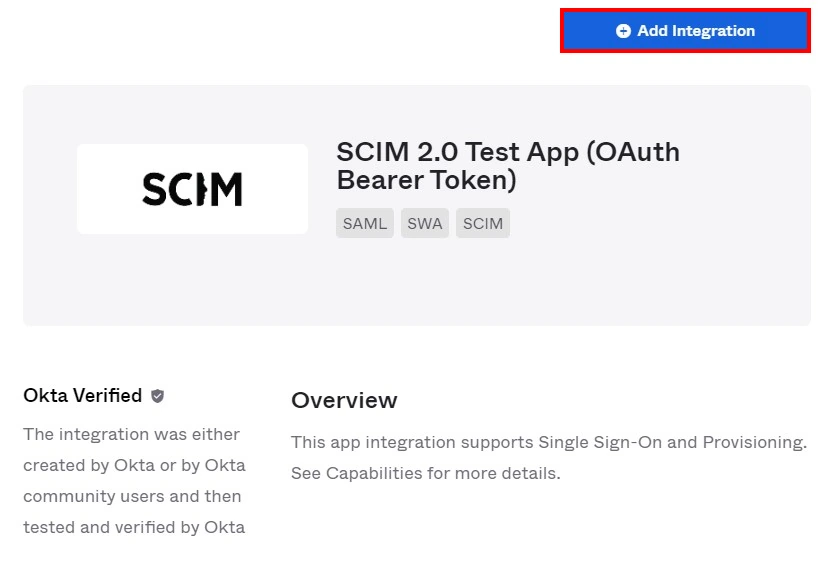
- Now search for the SCIM. Add the SCIM 2.0 Test App (Bearer Token) application. If you had selected SCIM 1.1 earlier, then you would need to select SCIM 1.1 Test App(Bearer Token).
- Click on the Add Integration button.
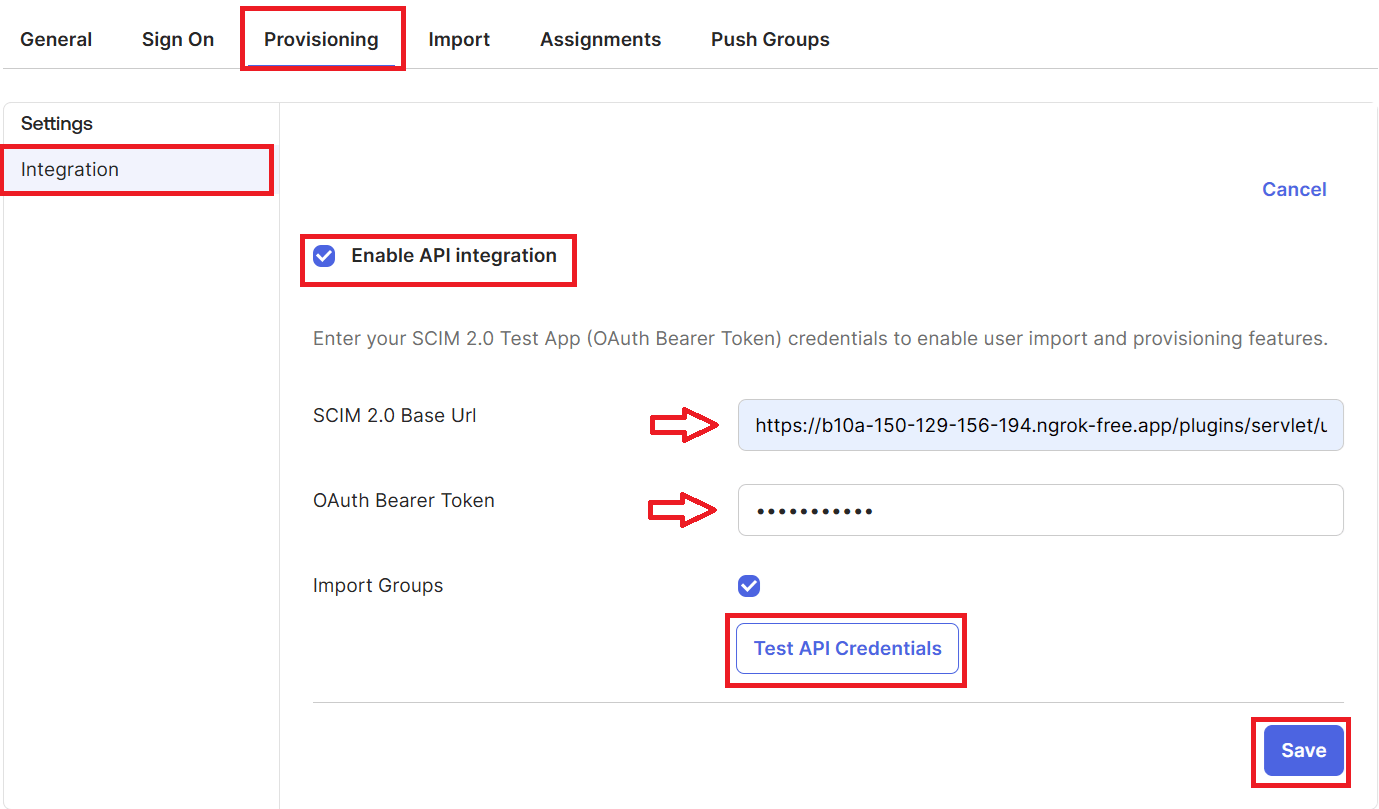
- Once the app is created, go to the Provisioning menu of the application and Click on the Configure API Integration button.
- Now click on the Enable API Integration and enter the SCIM Base URL (as SCIM connector base URL) and SCIM Bearer Token (as Authorization) from the SCIM Configuration tab of the plugin.
- Click on Test API Credentials. If the connection is established, it will show a success message.
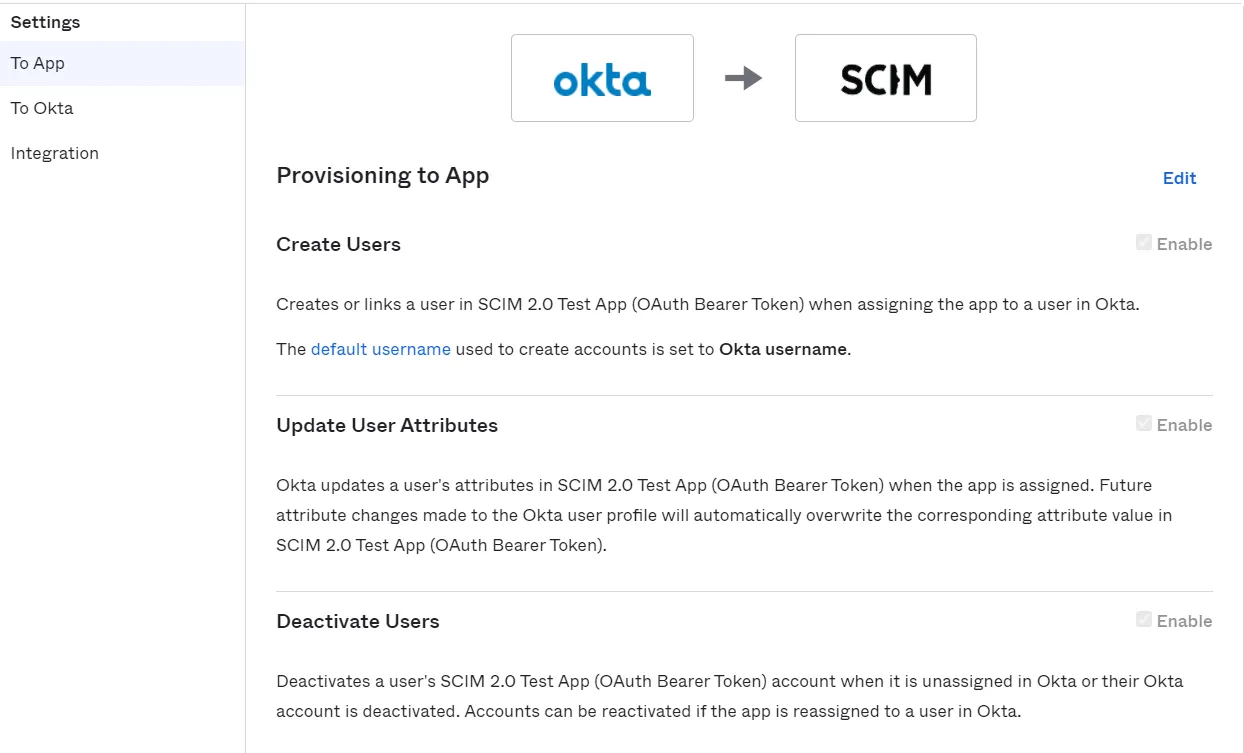
- Click on the Save button. After that Click on To App under the Settings option on the left side.
- Click on Edit button and check the Create Users, Update User Attributes and Deactivate Users checkbox and click on the Save button.
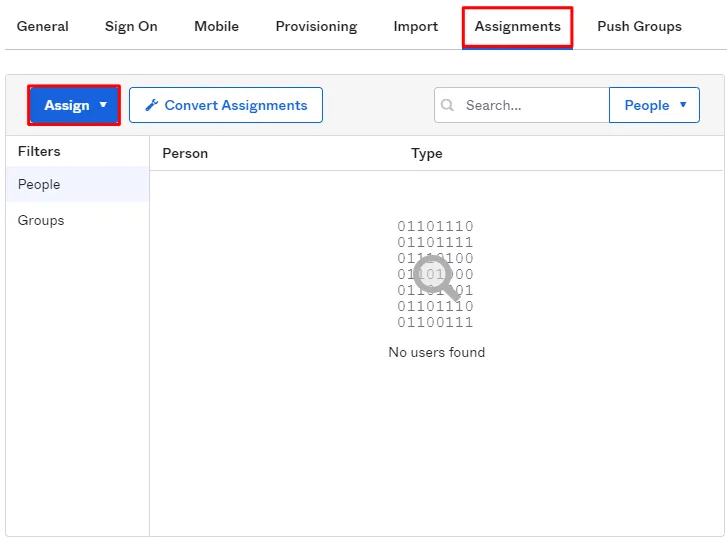
- Then go to Assignments menu and add Users that you want to provision into your application. You can also assign groups. Members of the assigned groups will be provisioned to Atlassian module.
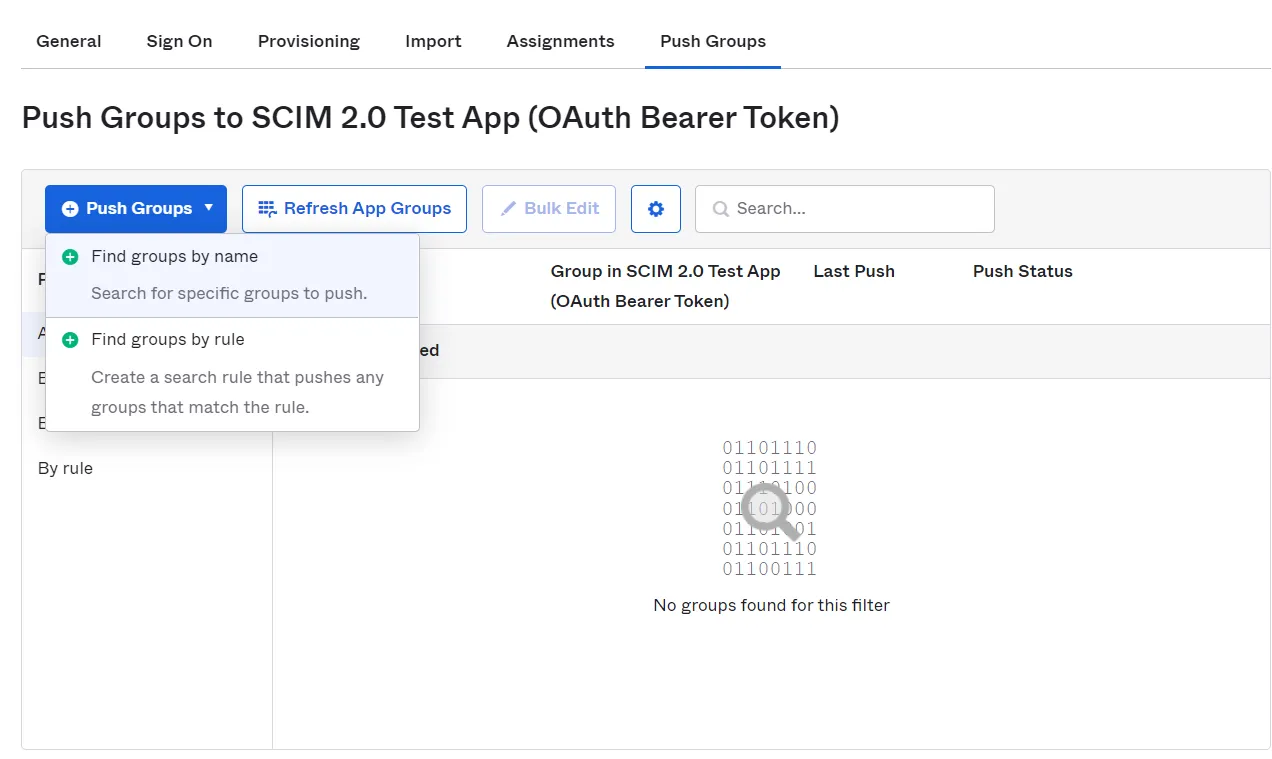
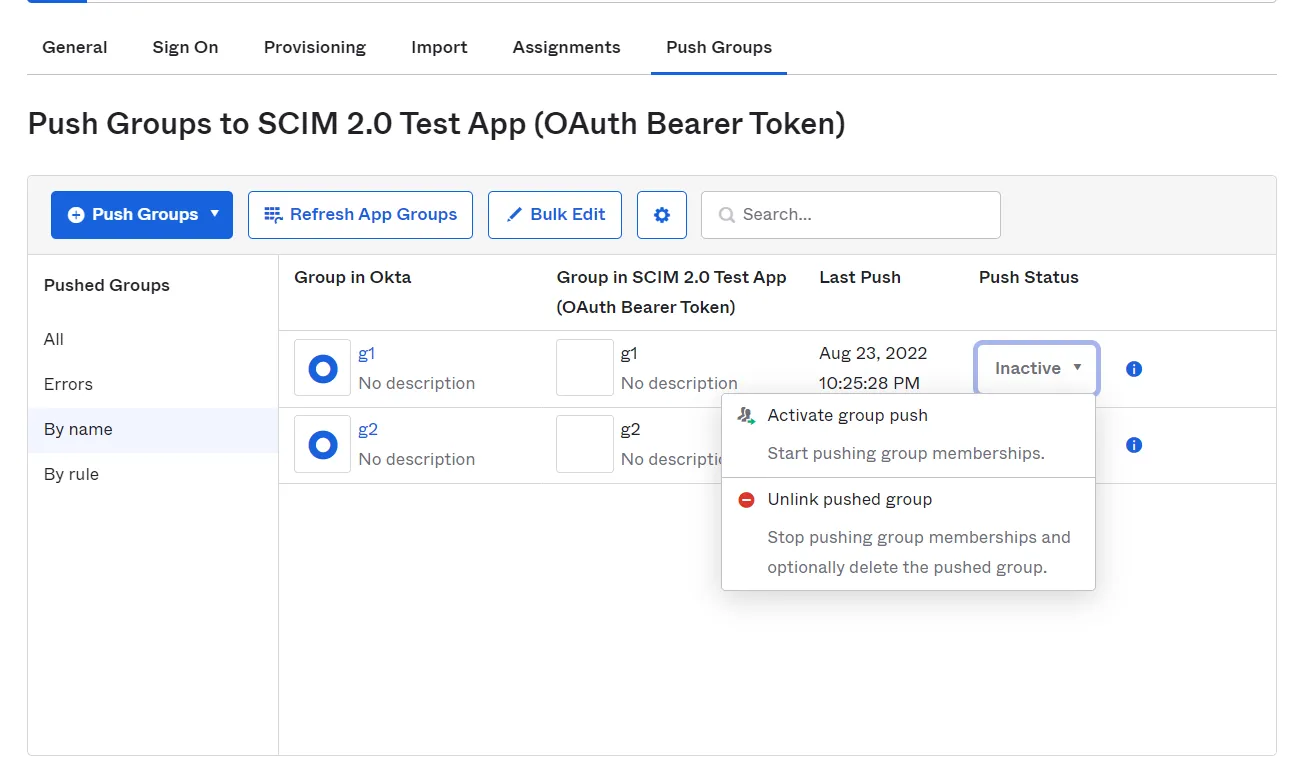
- To enable group mapping for a group you will need to add it in the push group section. Go to Push Groups tab and click on Push Groups button. Then click on find the group by name or you can also find it by the group rule. Then you can search and select the group.
- After finding the group you will need to Activate Group Push to start group sync.
Step 3: LDAP Sync Settings
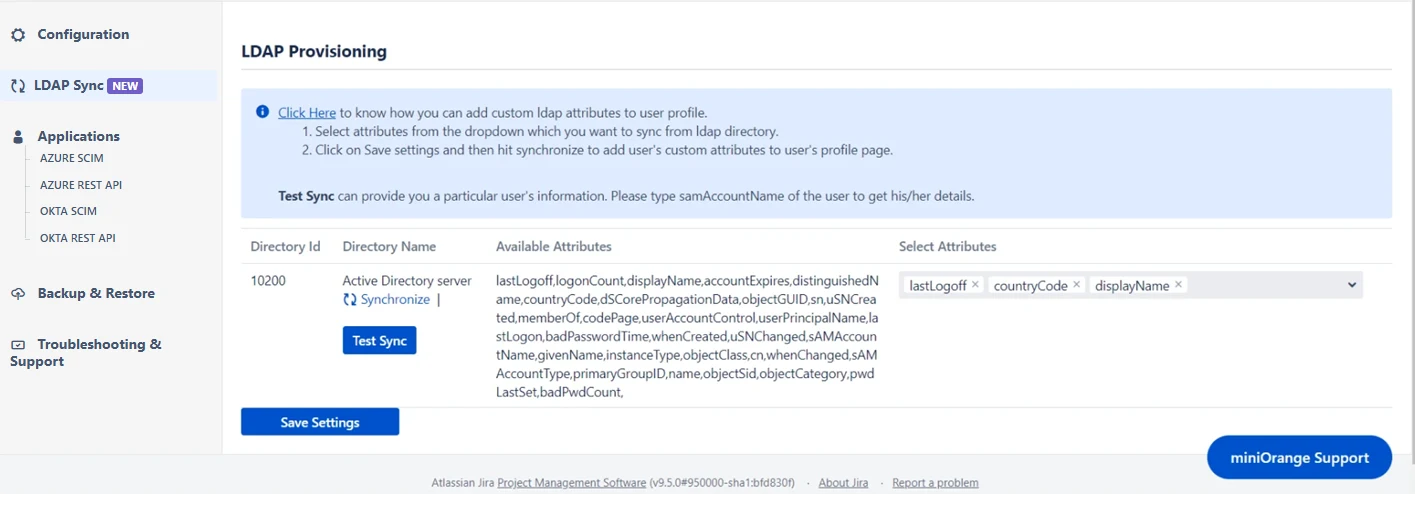
- The miniOrange user sync app now provides support for LDAP Sync. Follow the instructions to configure the LDAP directory. By configuring the LDAP directory, you can synchronize all attributes from your LDAP directory and choose the attributes you wish to include in Confluence.
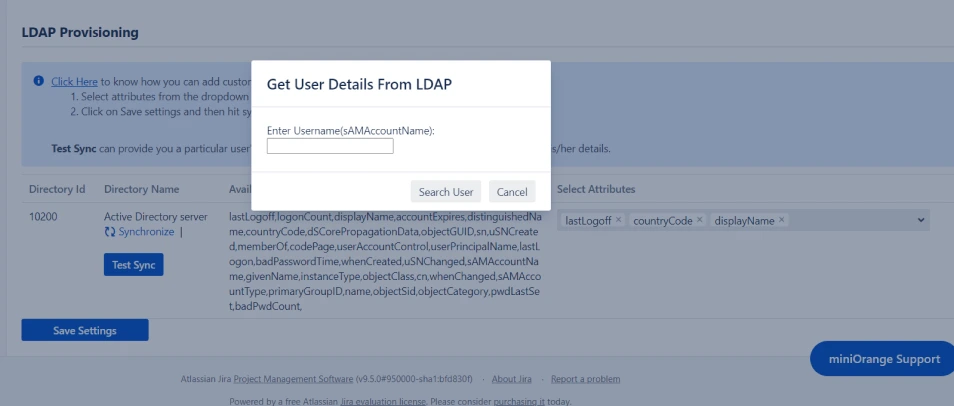
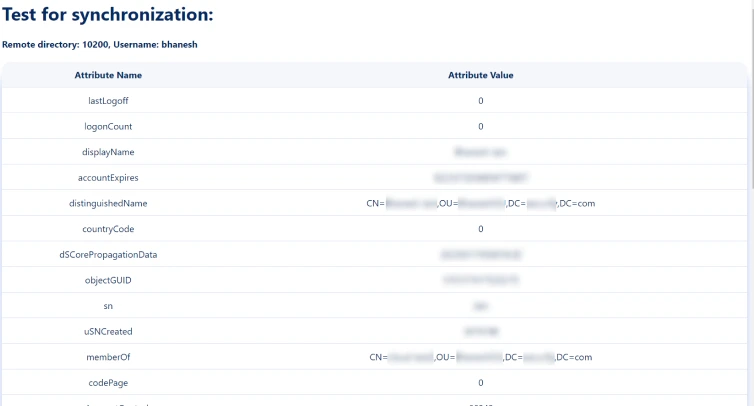
- Once you have successfully configured the LDAP directory in Confluence, you can test the specific user’s attributes by using the Test Sync button.
- To test your configuration, enter an username(sAMAccountName) from your directory's user data and click on the Search User button. You will then be able to view the details of the searched user.
Step 4: User Sync Settings
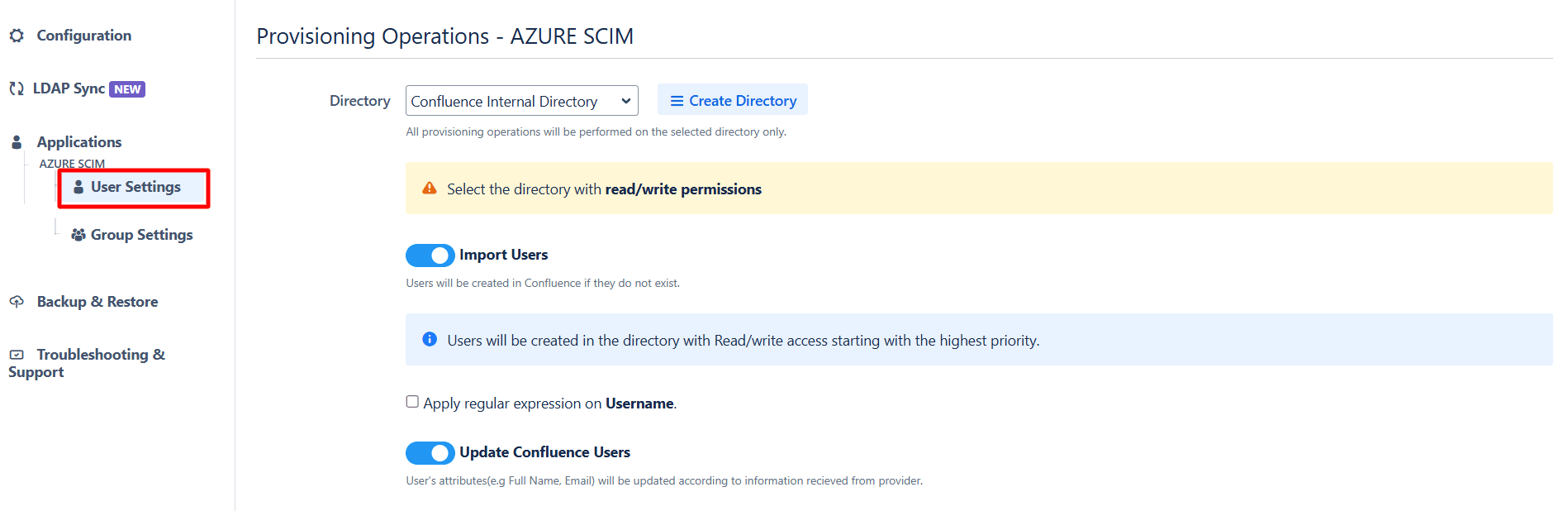
- Select the User Sync Settings tab from the left sidebar. Here you can configure different settings about user creation and updation.
- You can select the directory, enable or disable user import, update process.
- The user can be automatically enabled or disabled here based on IDP configuration.
- You also have an option to set Default Project Lead and Default Component Lead.
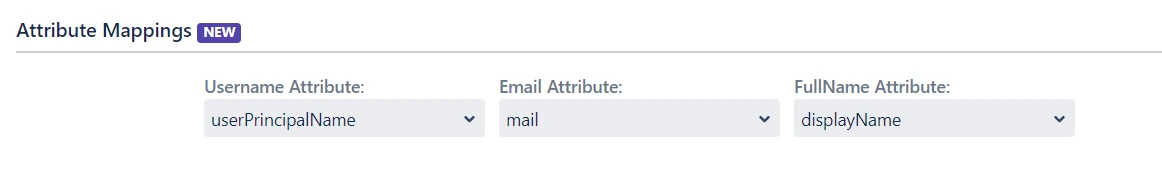
- Attribute mapping enables you to map your attributes sourced from the IDP to Confluence attributes. Through this section you can map your Confluence attributes to the attributes coming from IDP. By default, username attribute corresponds to the username/userPrincipalName attribute, email corresponds to the email/mail attribute, and displayName corresponds to the full name attribute. However, if you want to map these Confluence attributes with other attributes coming from IDP, you can use this feature to change the attribute mapping configurations.
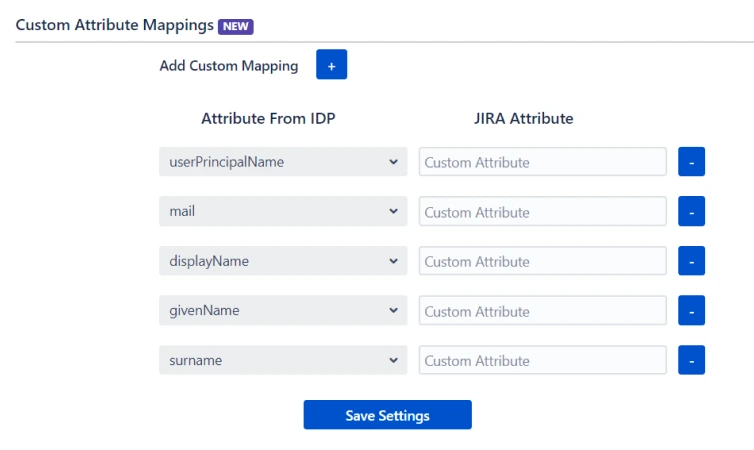
- User sync also supports mapping of custom attributes. Here, you can create custom attributes and automatically assign values to them from the IDP (Identity Provider). Select the desired attributes from the IDP that you want to display in Confluence and provide a name for the custom attributes to be shown in Confluence.
- Custom fields will be displayed in the user profile section as shown below
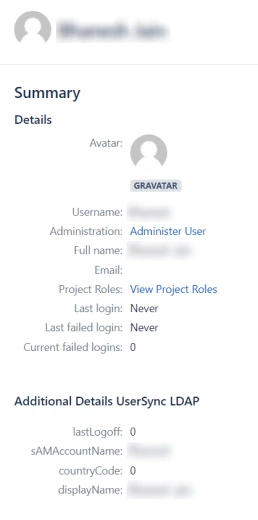
Step 5: Group Sync Settings
- Select the Group Sync Settings tab from the left sidebar. Here you can configure different settings about group creation and group mapping.
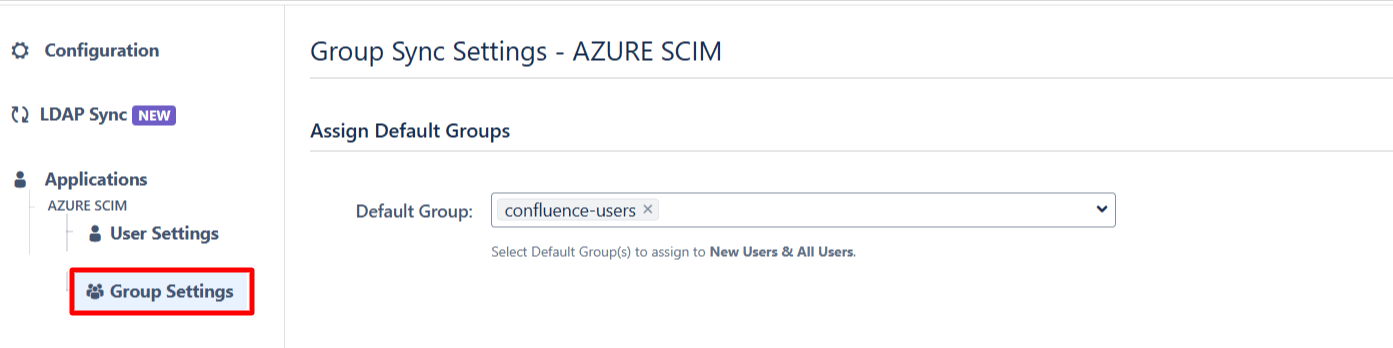
- Here you can configure Default groups for new and all users.
- You can set Manual Group Mapping or On-The Fly Group Mapping.
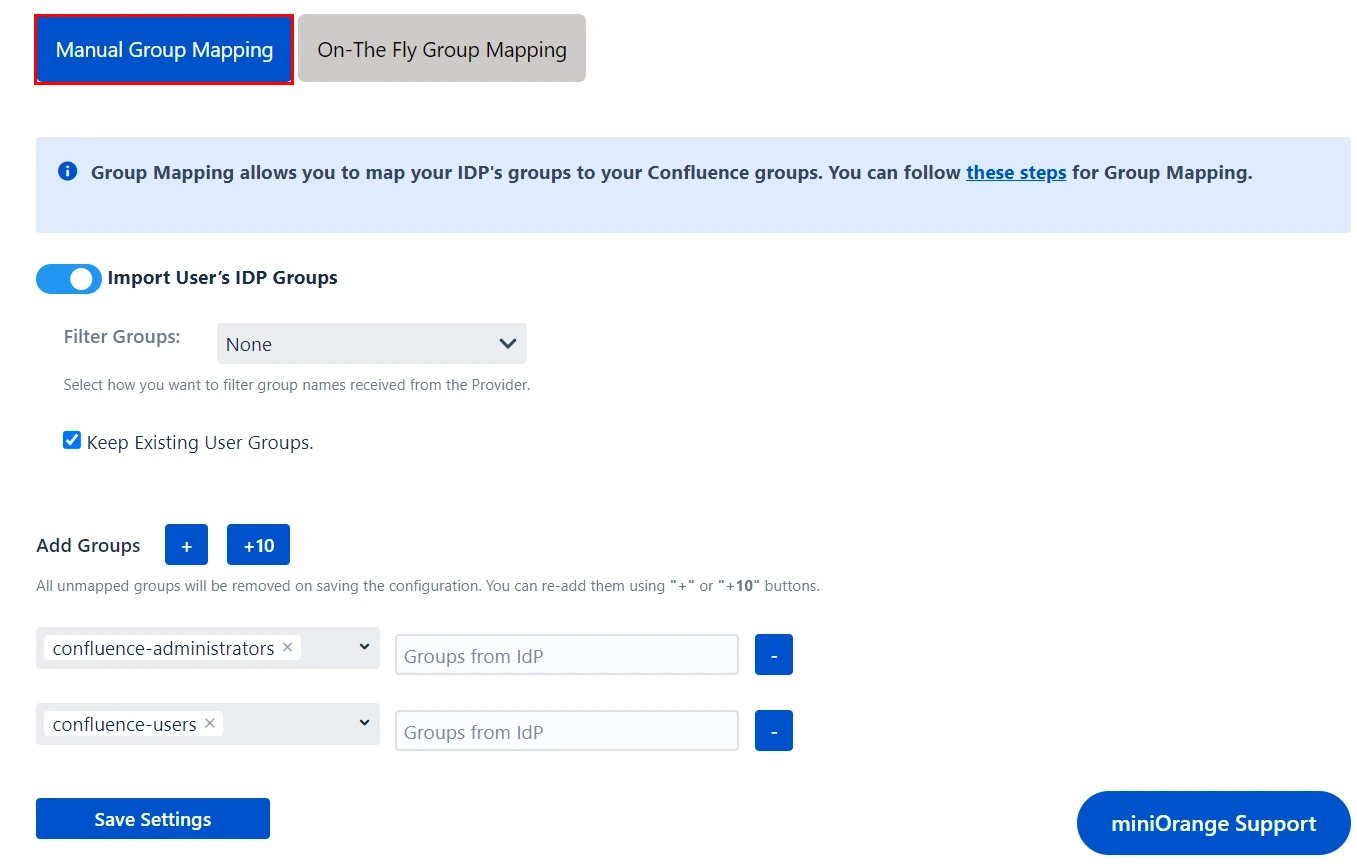
- Here you can manually map Confluence groups with the groups from IDP.
- You can also configure to import IDP groups, filter groups and whether to keep existing users or not.
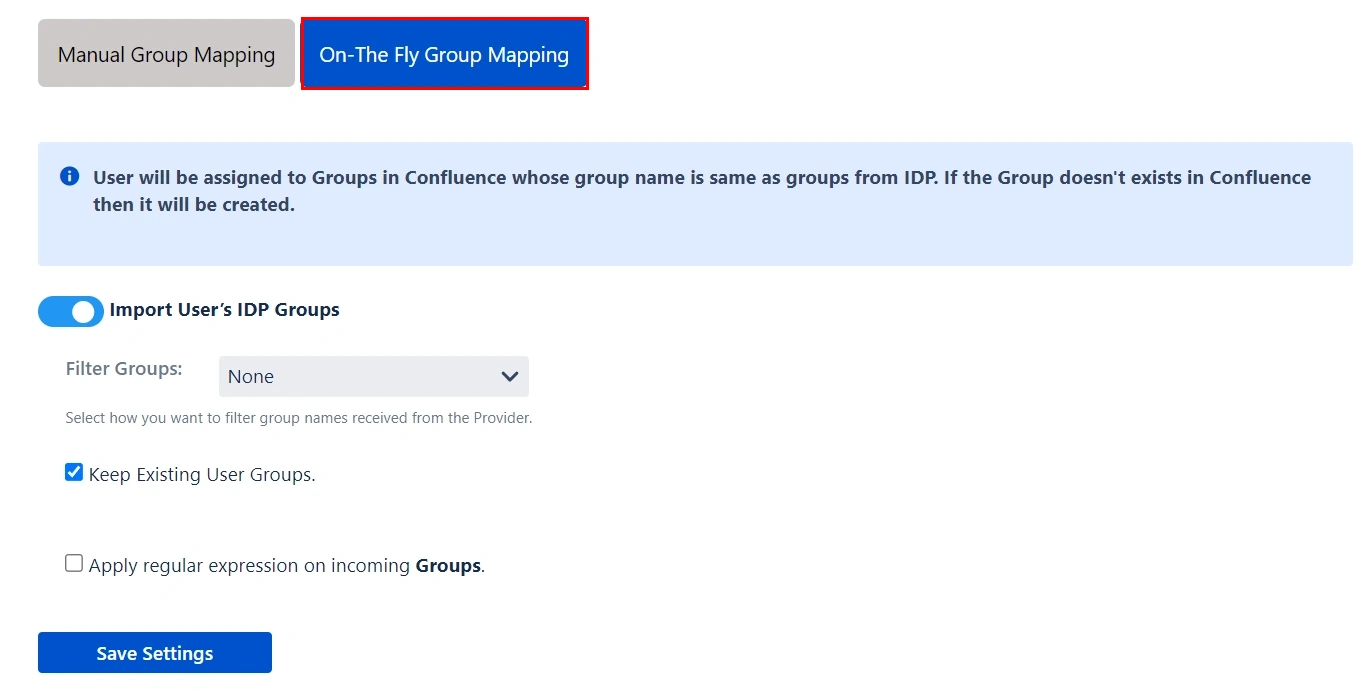
- Here users will be assigned to groups in Confluence whose group name is the same as groups from IDP. If the group doesn't exist in Confluence then it will be created.
- You can configure to keep the existing user groups, filter groups and apply regular expressions on the groups.
1. Manual Group Mapping -
2. On-The Fly Group Mapping -
Step 6: Synchronization Process
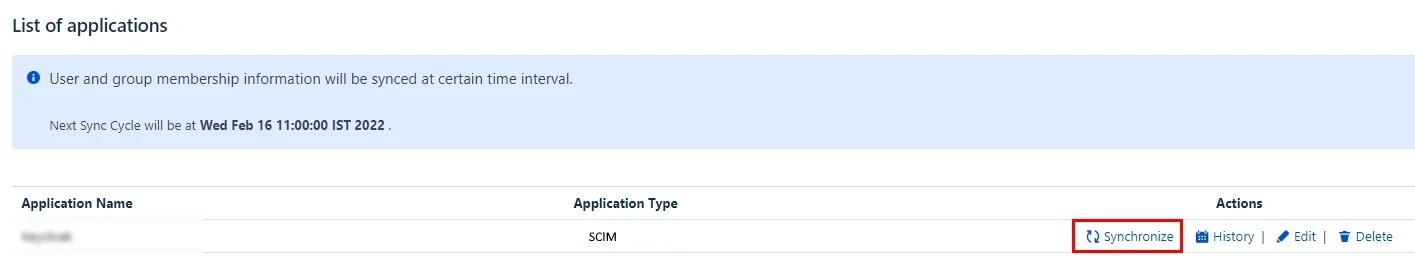
- To perform user sync, click on the Synchronize option of your newly created app.
- When the synchronization is complete, you will be able to view newly created and updated user information in Confluence's User Management section.
Step 7: Multiple IDPs
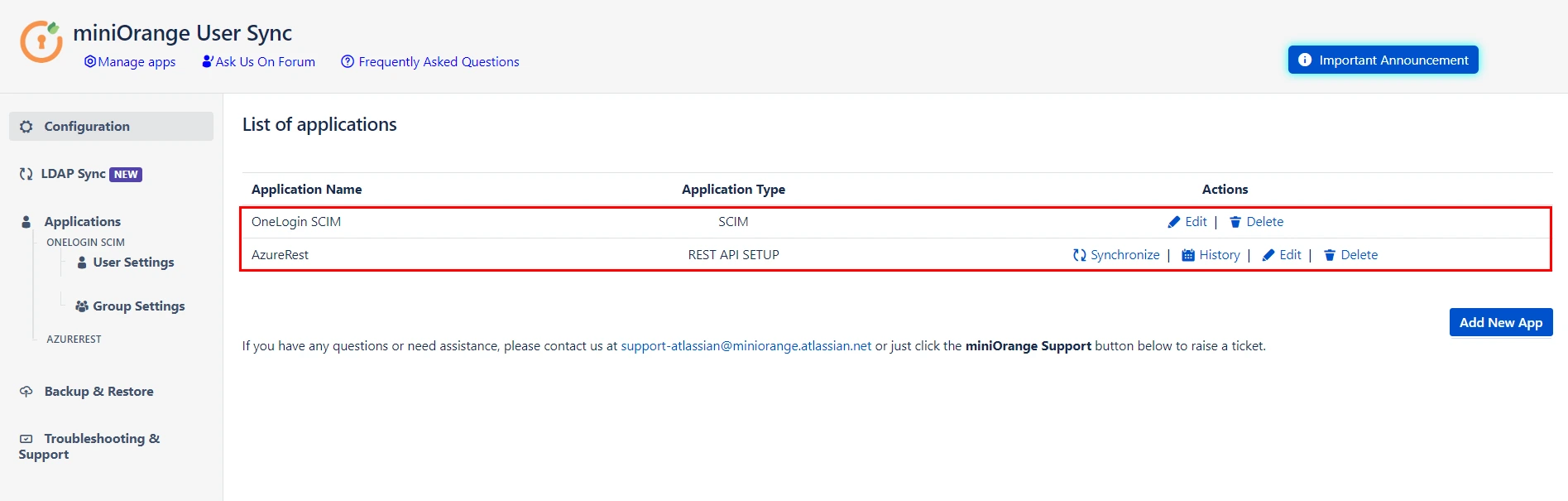
- The plugin allows for configuring SCIM provisioning on your Confluence to accommodate your specific use case. To add another IDP, simply navigate to the "Configured IDPs" section. Select on Add new App to configure multiple provisioning connections.
Did this page help you?

×
![]()

 Try it for free
Try it for free