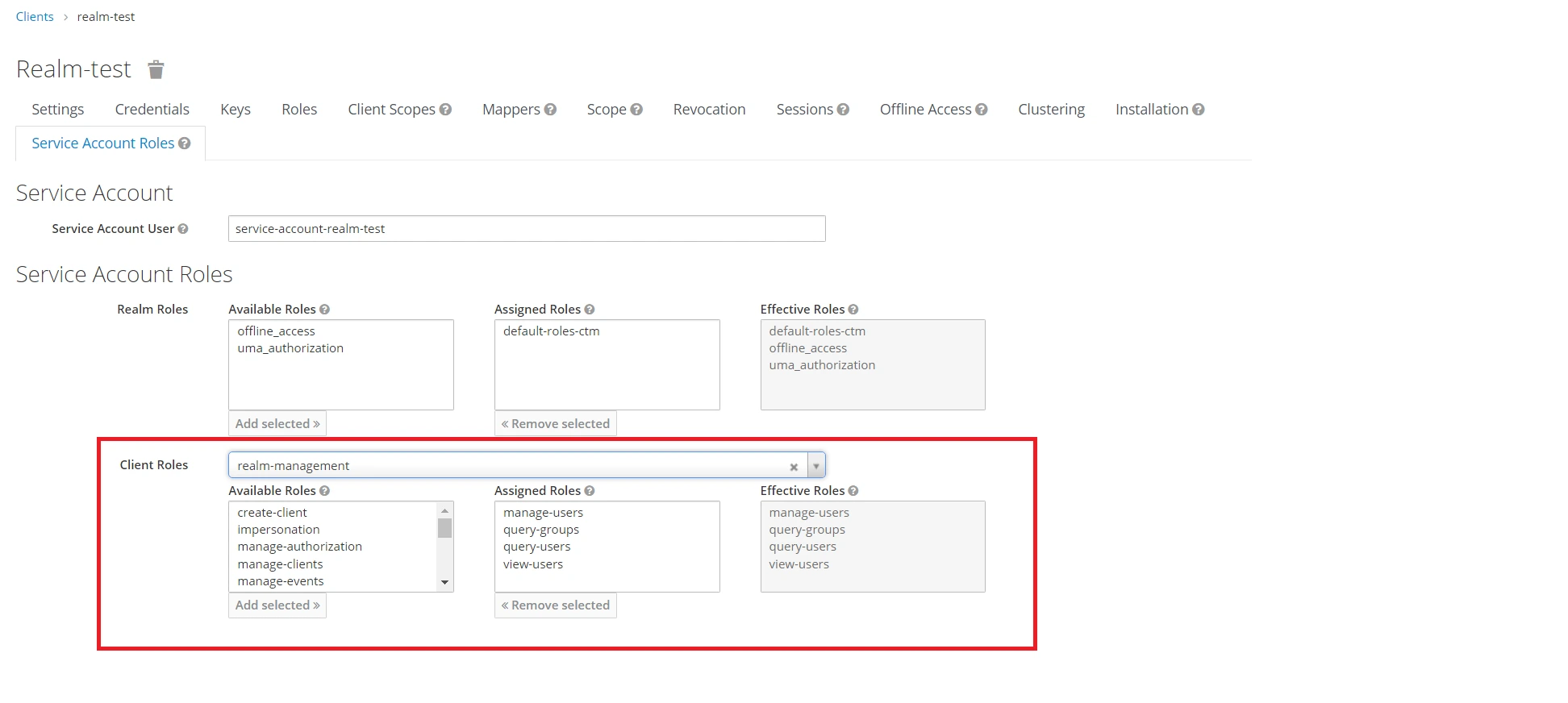
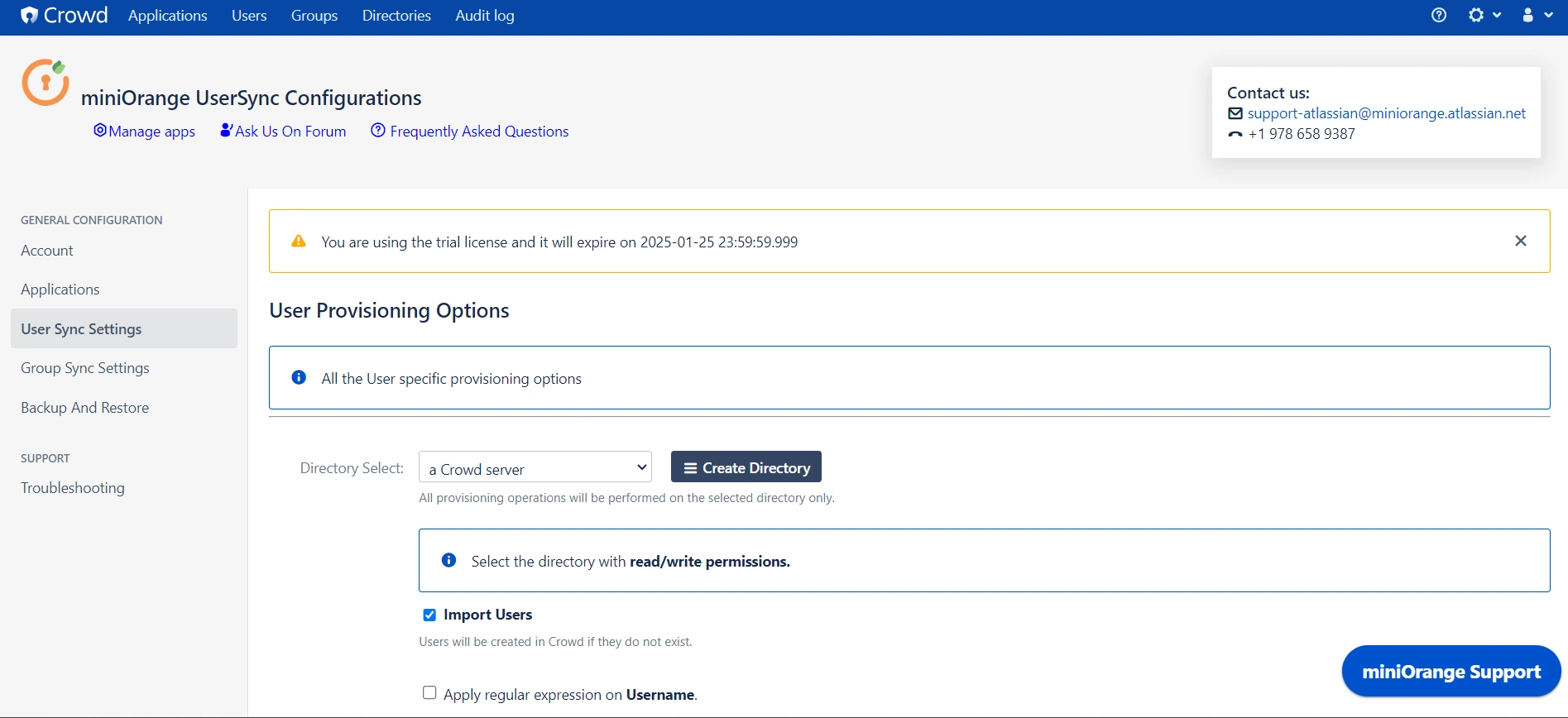
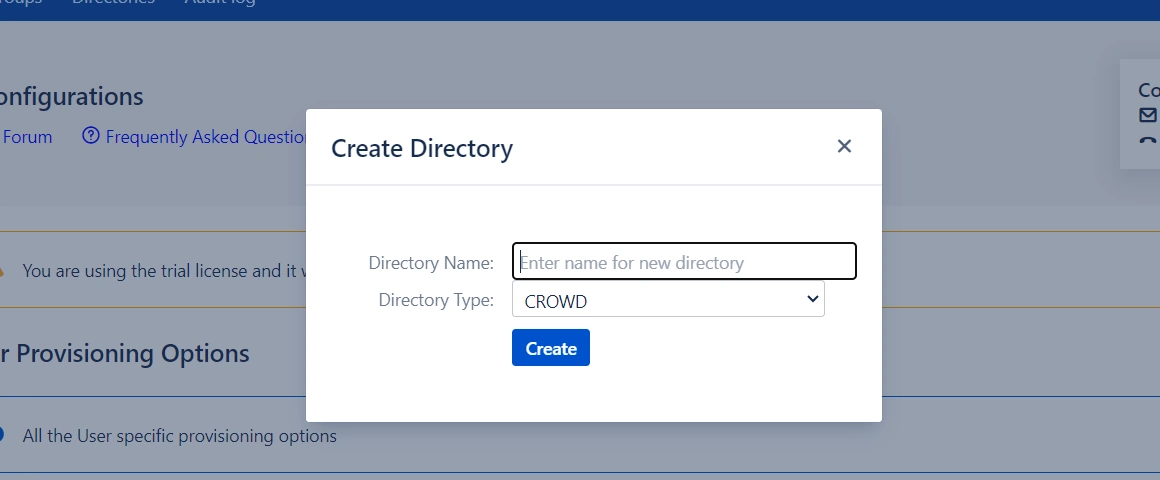
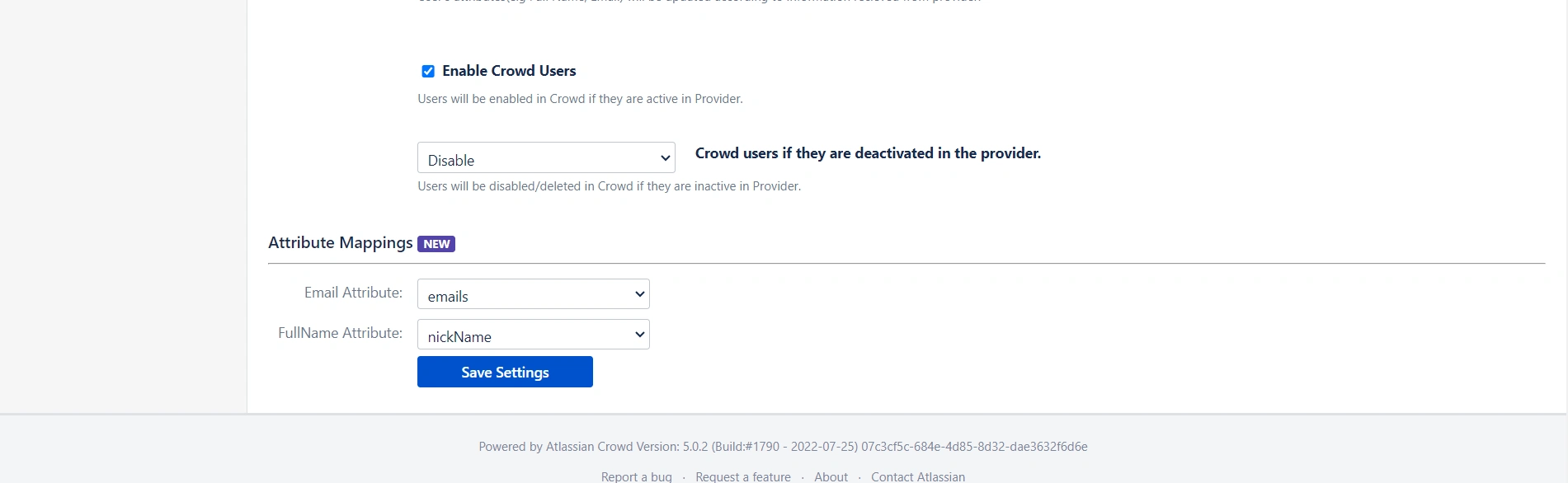
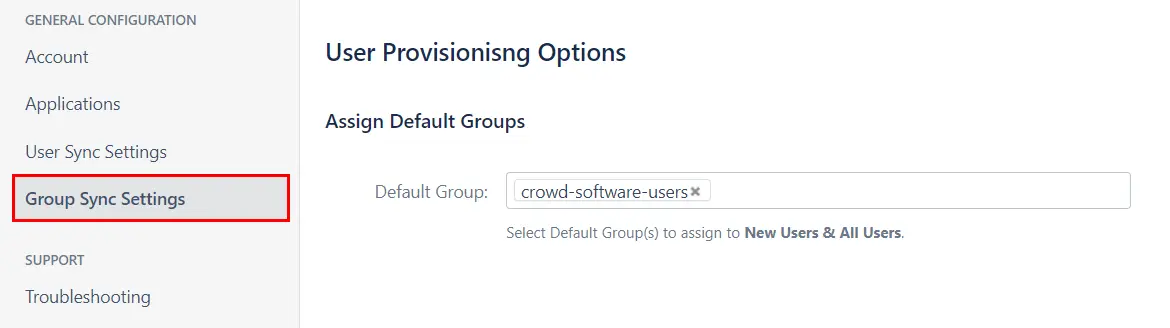
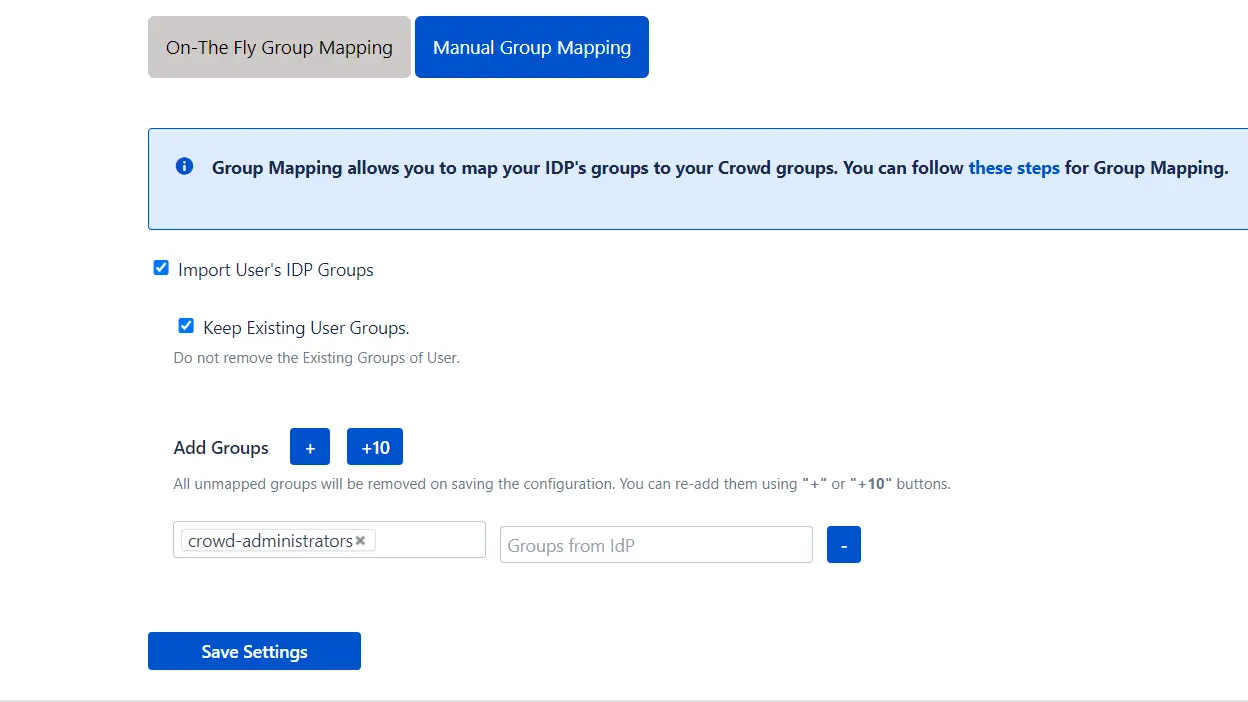
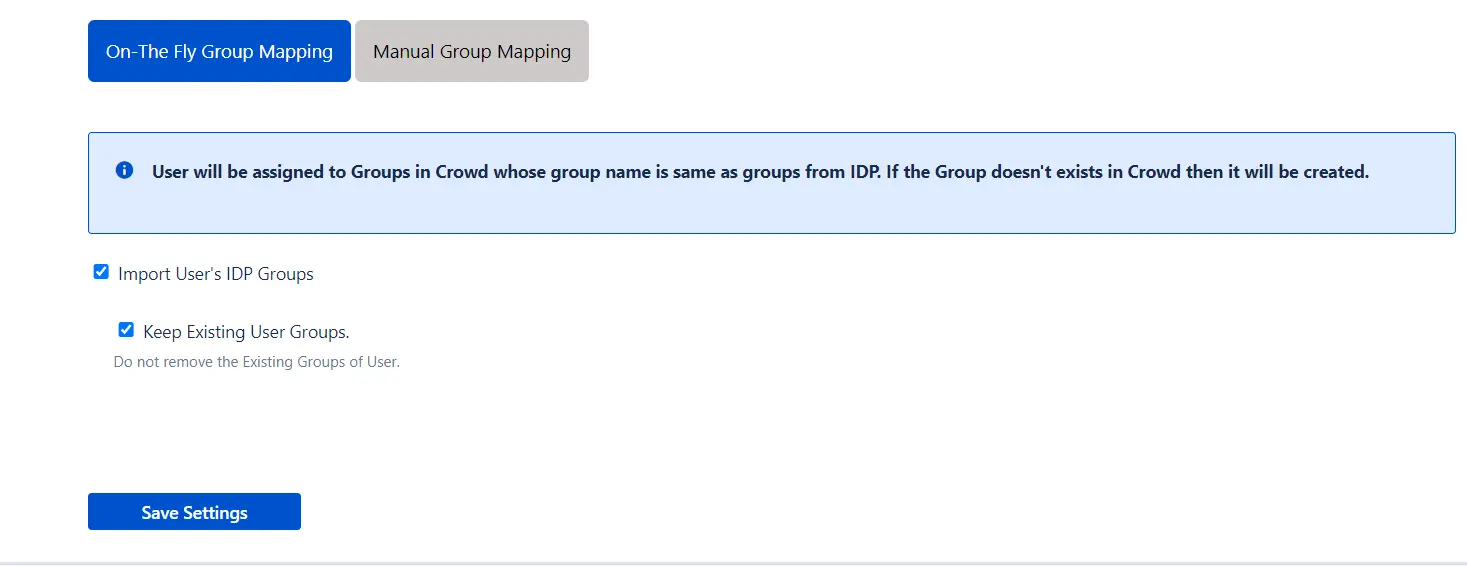
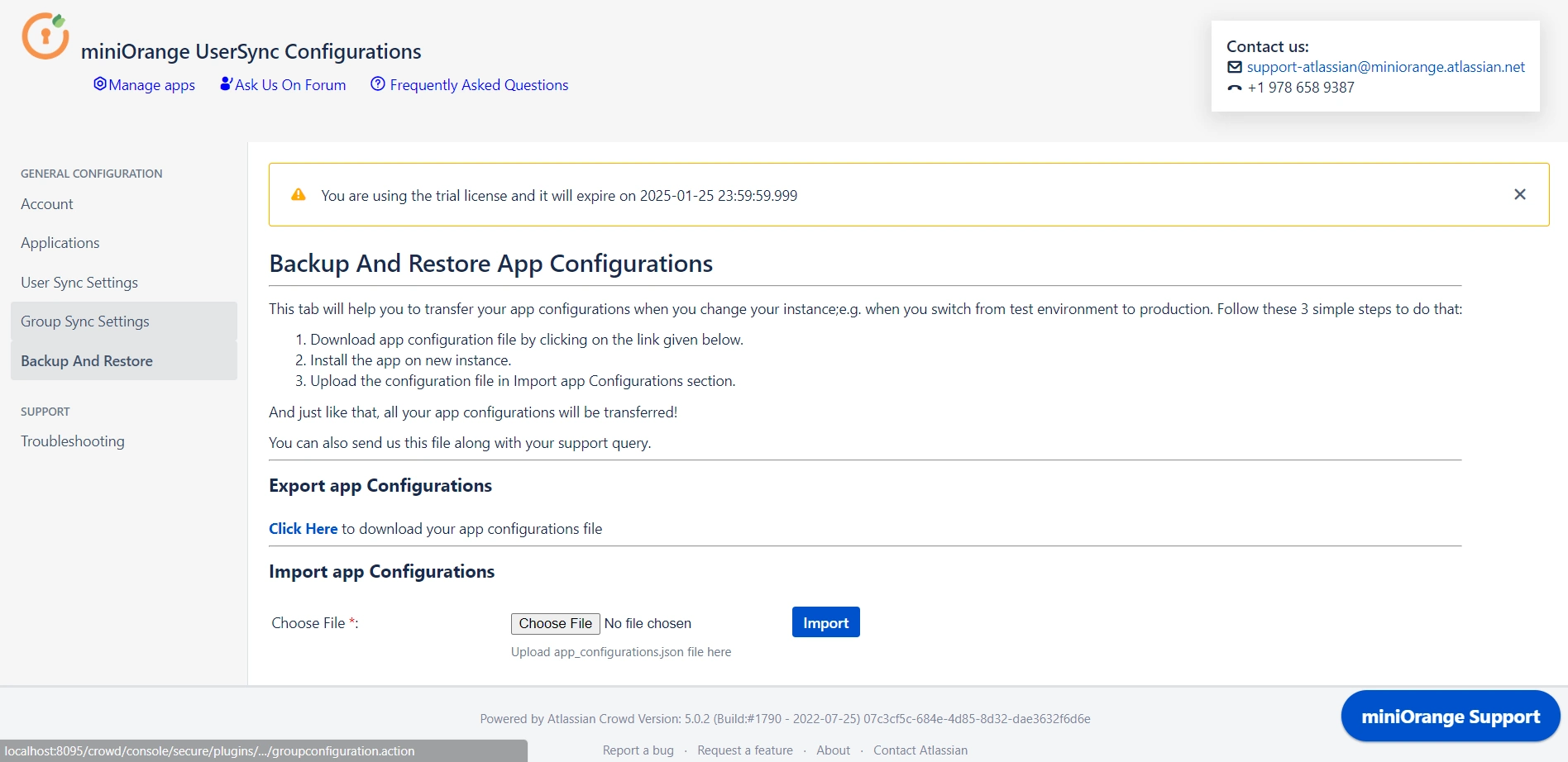
User Sync & Group Sync app provisions user and group information from Keycloak to Crowd. Users, groups, and directory details can be provisioned using SCIM. SCIM provisioning works based on events performed on IDP. This way the administrator only needs to manage user accounts in Keycloak. This reduces the administration time required to create users and groups in Atlassian modules such as Crowd.
Download And Installation
- Log into your Crowd instance as an admin.
- Navigate to the Administration menu and Click Manage Apps.
- Click Find new apps or Find new add-ons from the left-hand side of the page.
- Locate SCIM for Crowd via search and click on install.