miniOrange Single Sign On (SSO) apps offer crucial features which help companies keep pace with ever changing security regulatory requirements. Companies can connect their Atlassian application to their existing Identity Provider (IdP) using miniOrange SSO apps.
Our SAML SSO Data Center Apps
We will be looking at the crucial SSO features which are covered by the miniOrange Single Sign On applications in terms of -

Make user account creation and updation automatic. Automate update of group membership through SSO.

Manage user, agent, and customer SSO logins. Once you log out of one application, all others will follow

Send Signed Request and support for encrypted response. An Emergency URL for admins to login using local credentials when SSO is not working.
Advanced User & Group Provisioning
1. Just In Time Provisioning (JIT)
Just-in-time provisioning automates new user creation in the Atlassian application using SSO without interfering with existing setup and provides a smooth Single Sign On experience for all new users. With just-in-time provisioning, administrators don’t need to worry about adding each and every user in an Atlassian application to give login access. They can simply setup Single Sign On with our SAML SSO apps and users will get automatically created. The user’s email, username and name information is generally fetched from the Identity Provider.
2. Autoactivate Users on SSO
Many times administrators deactivate users who do not access the system for a long time. But what if they need to access the system? In this case, the administrator will need to manually activate the user again. This can be easily automated with SSO.
With a flick of a switch, you can allow users to get automatically activated and login when on successfully using SSO. This reduces administrator’s manual work and also helps to keep licensing count in check.
3. Automated Permission Management
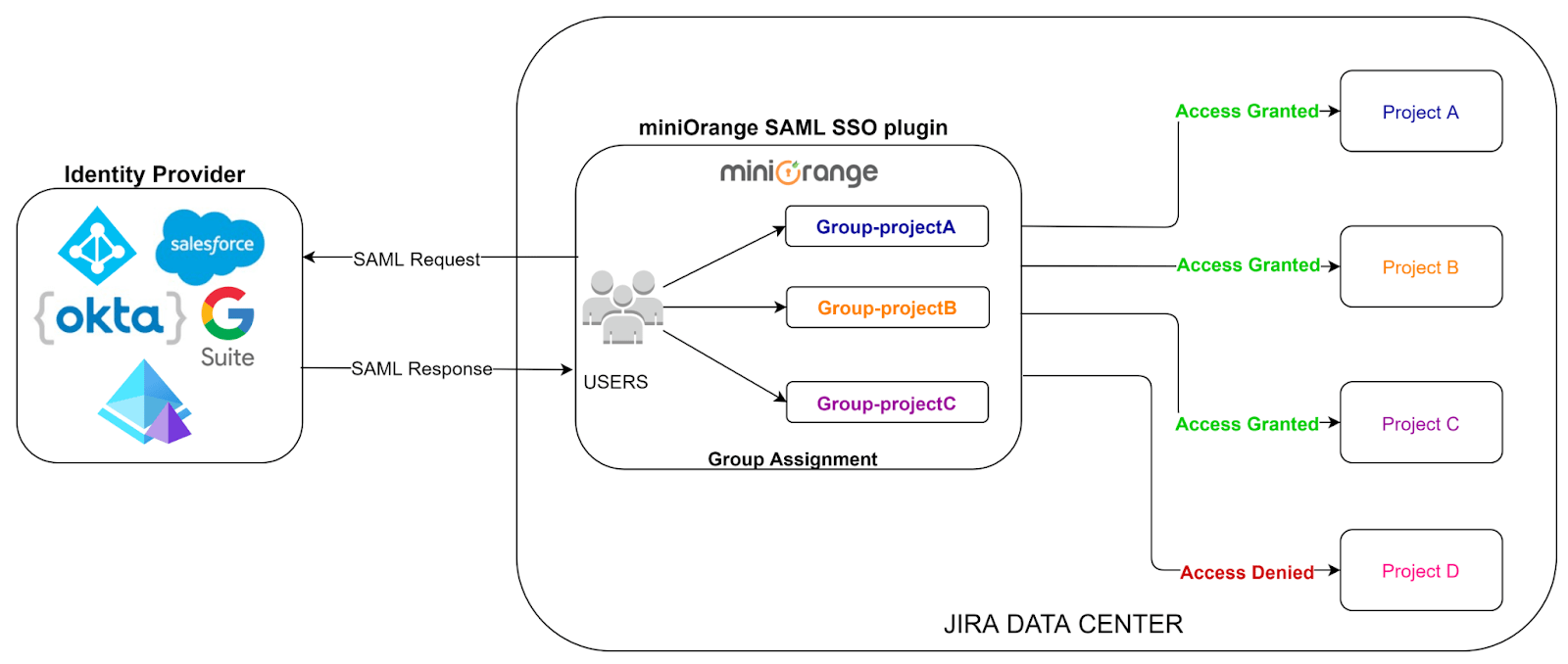
In any Atlassian applications like Jira or Confluence, you need to manage which user will access what project or space and the level of access they have. That is user permission management, and it's mainly done by assigning appropriate groups to the user.
Generally, the administrator manages groups of each user for each of the applications. By introducing SSO into the picture, the administrator can manage groups directly in Identity Provider (IdP) and sync or provision that in SSO connected Atlassian applications (using Just-in-time provisioning).
In realistic cases with different departments handling different applications, the administrators may not be responsible for managing the groups in both Identity Provider (IDP) and Atlassian applications and would manage all or some of the groups locally. This has been taken care of with miniOrange SSO.You can choose to sync all groups or selective groups from Identity Provider (IDP) based on your requirements.
Here is a brief of a few cases which are supported -
- Some groups are present in IDP and the rest are locally created to manage users
- All local groups are different than IDP
- All or some groups in IDP are present in local Atlassian application but with different name
- All groups in IDP are present in local Atlassian application with the same name
When using miniOrange SSO for Data Center, you get the flexibility to include local groups and configure a few important groups as Default groups. These groups will automatically get assigned to the user after Single Sign On (SSO).
Permission management with external Directory -
When Jira/Confluence is synced with an external directory, and permissions for directory is Read Only with Local Groups, you can simply assign local Jira and Confluence groups to the user and manage your user permissions within Jira and Confluence itself while turning on SSO for all your users.
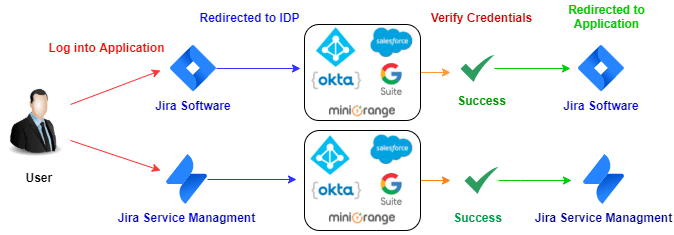
4. SAML SSO for Jira Service Management (JSM/JSD):
Jira Service Management comes along with Jira Software and is widely used by many organizations as a ticketing tool for external customers. Since it is an external end user interaction tool, the user base is huge and along with a big user set, the responsibility of handling and managing users is sizable.
Here comes miniOrange solution with great end user Single Sign On experience for Jira Service Management. The best thing about miniOrange SSO solution is that you don’t have to configure an IdP again if you have an Identity Provider which is common for both Jira Software and Service Management. The same SAML SSO settings will work out of the box for Jira and Service Management. If you have another IdP, you can also configure a separate Identity Provider for your Service Management users.
You can enable and disable Jira Service Management SAML Single Sign On (SSO) using a simple toggle button.
If you are wondering about how user experience would be if you want to use multiple identity sources or have dedicated identity sources for Jira Software and Service Management login then you don’t need to worry about it, we already have a provision for that.
Multiple Identity Providers (IDPs) -
Here you can configure dedicated IDPs for Jira Software and Jira Service Management and user roles and permissions will be managed by that particular Identity Provider. This integration will provide you a seamless and smooth login experience and it will be easy to manage and maintain users.
SSO for only Service Management Agents (Agent based login) -
You can choose to restrict SSO for only agents. This ensures that only Jira Service Management agents are allowed to login into the Data Center through SSO if they belong to the roles or groups specified under the Jira Service Management settings. Other users will be asked to login with their local Jira and Confluence credentials.
Advanced Security
In today's world, everybody understands the importance of data security. Due to the huge rise in the number of cyberattacks, data security has become a top priority for each and every business. In SAML SSO, encrypting and signing the SAML assertions is the way to ensure that your sensitive information is never visible in plain sight.
A number of organizations and standard bodies either recommend or require sensitive data to be encrypted in order to prevent unauthorized third parties or threat actors from accessing the data. Encryption is the method by which information is converted into secret code that hides the information's true meaning. Signing verifies the sender of the data. Encryption plays an important role in securing many different types of assets. Encryption provides Confidentiality, Nonrepudiation, Data Integrity, and Authentication.
1. Prevention against SAML replay attack (Restrict Duplicate SAML Assertion)
Replay attack is the common man-in-the-middle security threat which includes repeatedly sending SAML assertions to the system. This will allow the attacker to login into a secure application with user privileges of the username/ email mentioned in the SAML response.
miniOrange prevents such an attack by tagging each session with a time bound ID. This ID is further checked for duplication when a user tries to SSO. So, in case, an attacker reads a SAML Response assertion of a valid user and tries to use it again, the miniOrange SSO apps reject the SAML Response despite being valid due to the ID already being used once.
2. Restriction on password change
Passwords for users created through the Just in time provisioning are randomly generated, and this functionality prevents users from resetting their Atlassian local password using “forgot password” or “change password” functionality from their profile. A restriction on password change prevents users from bypassing SSO and logging in with local credentials, or fetching/updating any information using the authentication REST API call.
3. Secure login for admin users
In Atlassian, administrators have to login and reauthenticate to get privileged access. In keeping with this and to add more protection to admin functionality, you can configure the miniOrange SSO app to force all users to login as a user without the admin privileges. Admin users will have to authenticate again to get the admin privileges, resulting in increased security.
4. Secure SAML using Signed Request and Encrypted Assertion using miniOrange!
You can protect your data with encryption and signature checks using miniOrange. The sensitive data sent by the Identity Provider will be encrypted and signed with a key. This data will be accepted only if it passes all the security checks. miniOrange also provides you with the ability to configure your own secret keys for encryption and signature verification. miniOrange sends signed SAML Authentication Requests to the SAML IDP during SSO which is verified by the IDP before it authorizes the user to perform SSO. The miniOrange plugin makes your SAML SSO more secure than it has ever been.
miniOrange plugin also has the capability to enable SSO for Atlassian applications running behind the proxy which allows the plugin to update the SAML endpoints to work with internal as well as external (proxied) URL.

Ease & Flexibility of Access
1. Single Logout
Terminate sessions from all the connected applications using a single click?
Generally, users don’t have a habit of logging out from each application if they are working on multiple applications. It is simply annoying to login and logout daily from all the applications. Imagine using Jira and Confluence Data Center which are connected to your Identity Provider (IdP). So
- when you log out from Jira and Confluence, you also get logged out from Identity Provider and the other applications connected to the IDP such as Confluence.
- when you log out from Identity Provider, you get logged out from Jira and Confluence at the same time.
This can be achieved with Single Logout (SLO) functionality and is supported by SAML SSO protocol.
In Single Logout, all applications which are connected to the IDP get logged out automatically if one logout operation is performed for any of the applications.

If we don’t have an option of Single Logout then we would need to always depend on the user to logout of each application individually. Generally, the login sessions for these Atlassian applications (Jira, Confluence) are very long and users may end up being active for a long time. Single Logout terminates all sessions created through SSO by initiating Logout from one Service Provider (SP) so the user won’t have a neglected session in other connected applications.
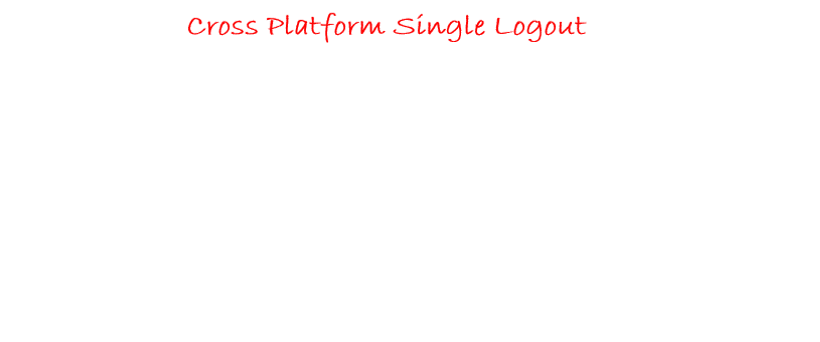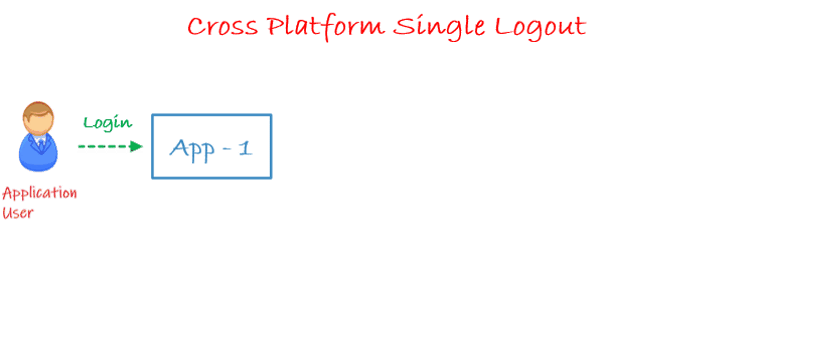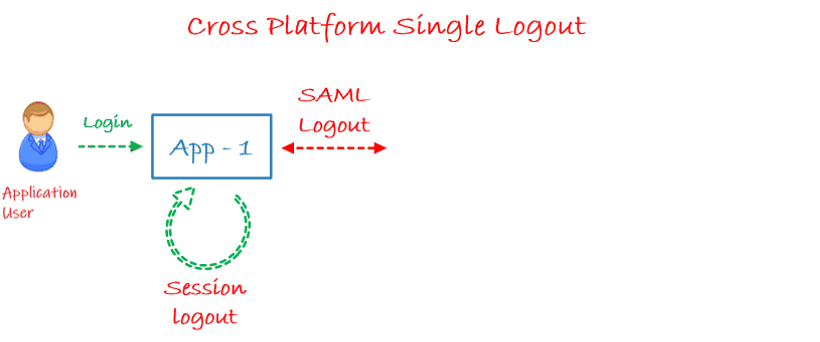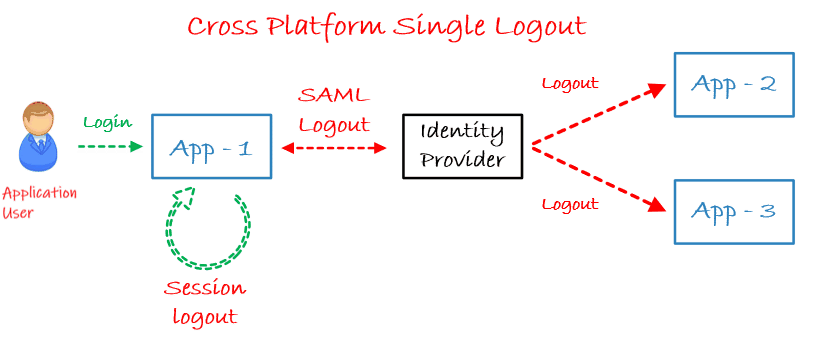
2. Metadata/Certificate Rollover
IDP updated their certificate? Not to worry! Would it not be tiresome to have to delegate with the IDP provider for each iteration when it’s time to update the metadata content. Having to follow procedures for replacing certificates to allow SSO without any service disruptions. Some IDPs update their certificates regularly as a security measure so only trusted service providers are in possession of the updated certificate.
The miniOrange SAML plugin comes in very handy with the certificate rollover feature which makes it possible to perform a certificate rollover to ensure no interruption during Single Sign On. In order for Service Providers to be aware of an IdP certificate, SAML metadata includes the certificate of the IdP. Simply enable the metadata rollover and set up the frequency of update less than or equal to that of the IDP update frequency. This will ensure seamless uninterrupted SSO functionality all while you lounge without you having to manually configure a thing.
3. Auto Redirect to Application
Once the Single Sign On integration for Atlassian Jira Data Center is successful, what will be the next step? Seamless and good User Login Experience? Yes, ofcourse!
For easy and convenient login, you can simply separate out the Data Center local user and Identity Provider user login page. Local users can login via Jira Data Center Login page and others can ask to authenticate through SSO, who will get to see the IDP login page instead of the default one. So some users will be restricted from accessing the Software by using the local credentials.
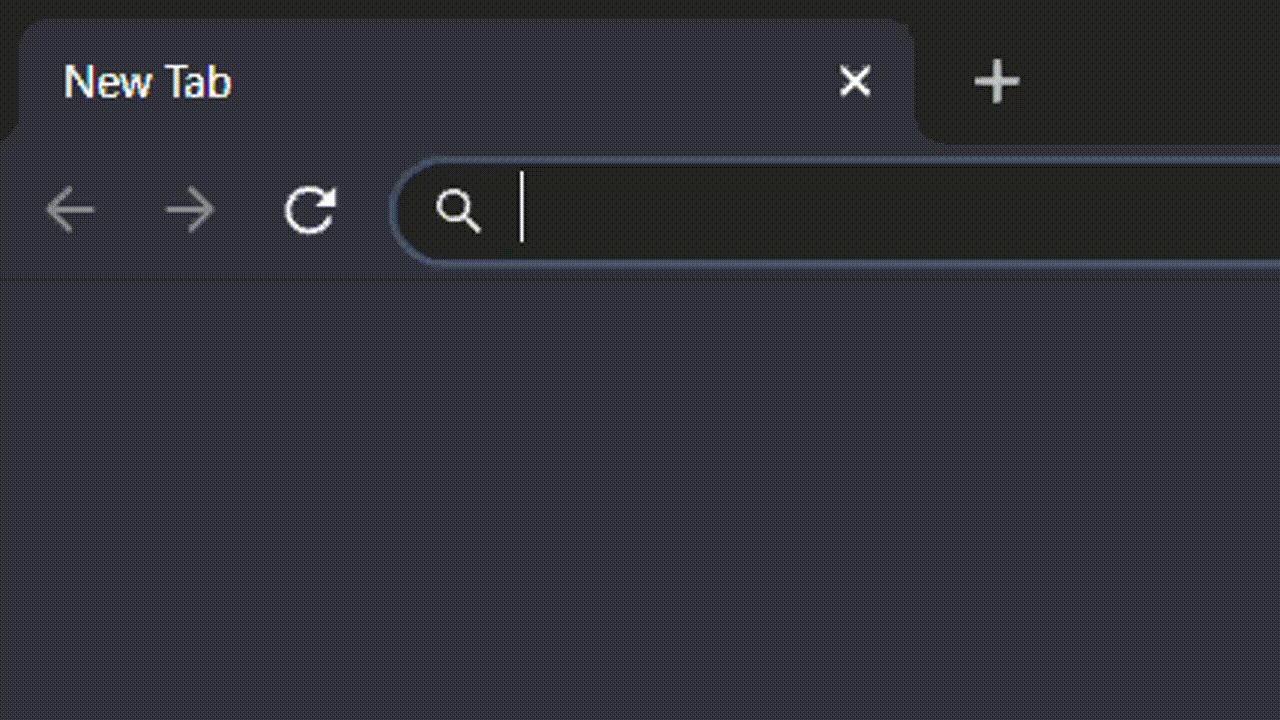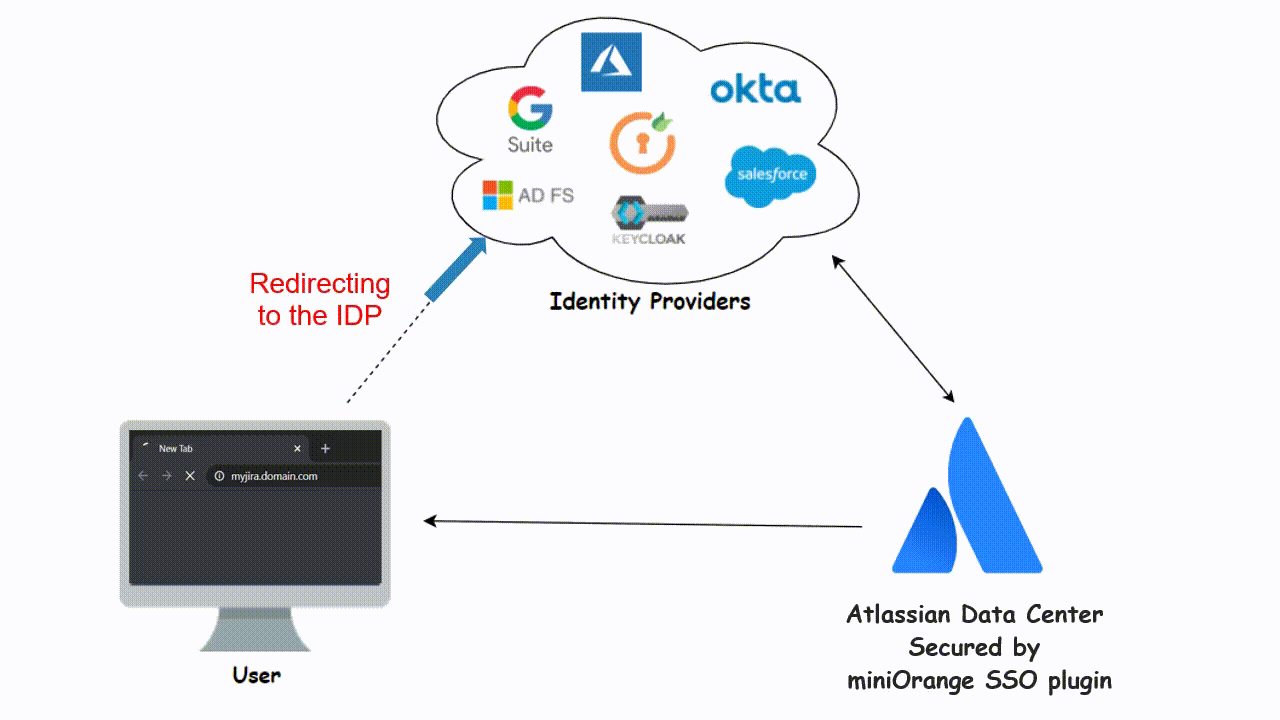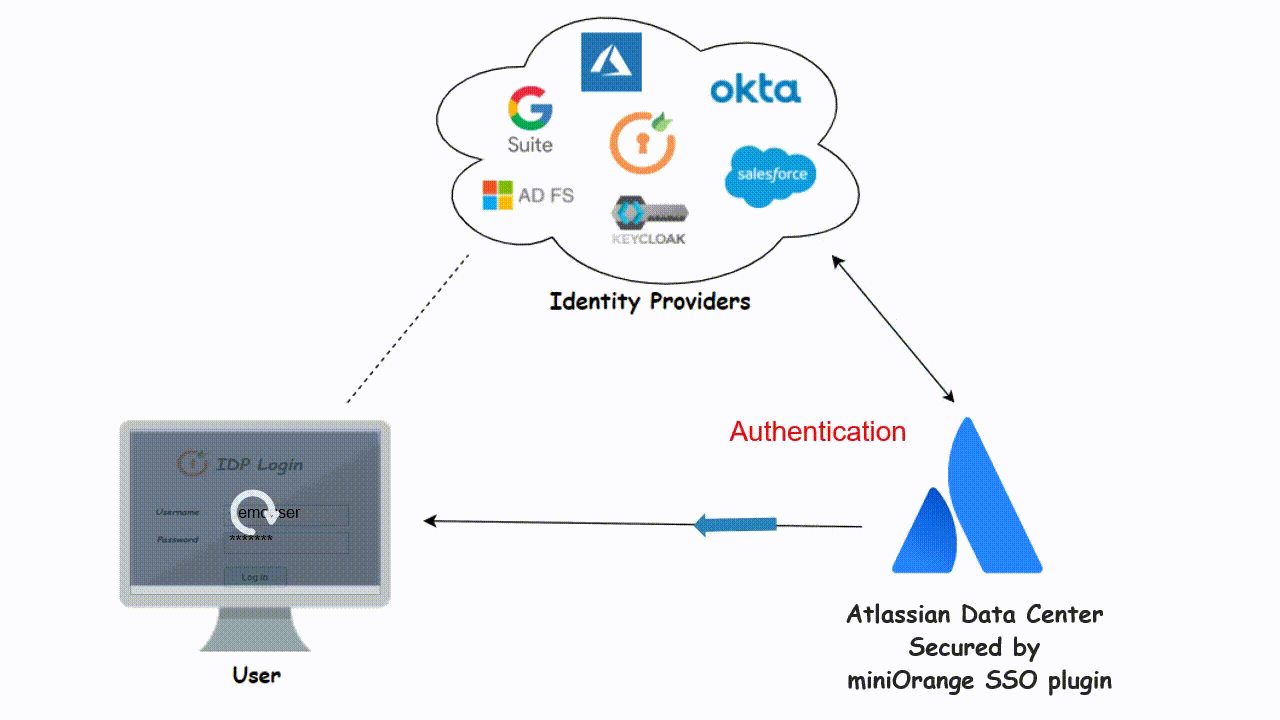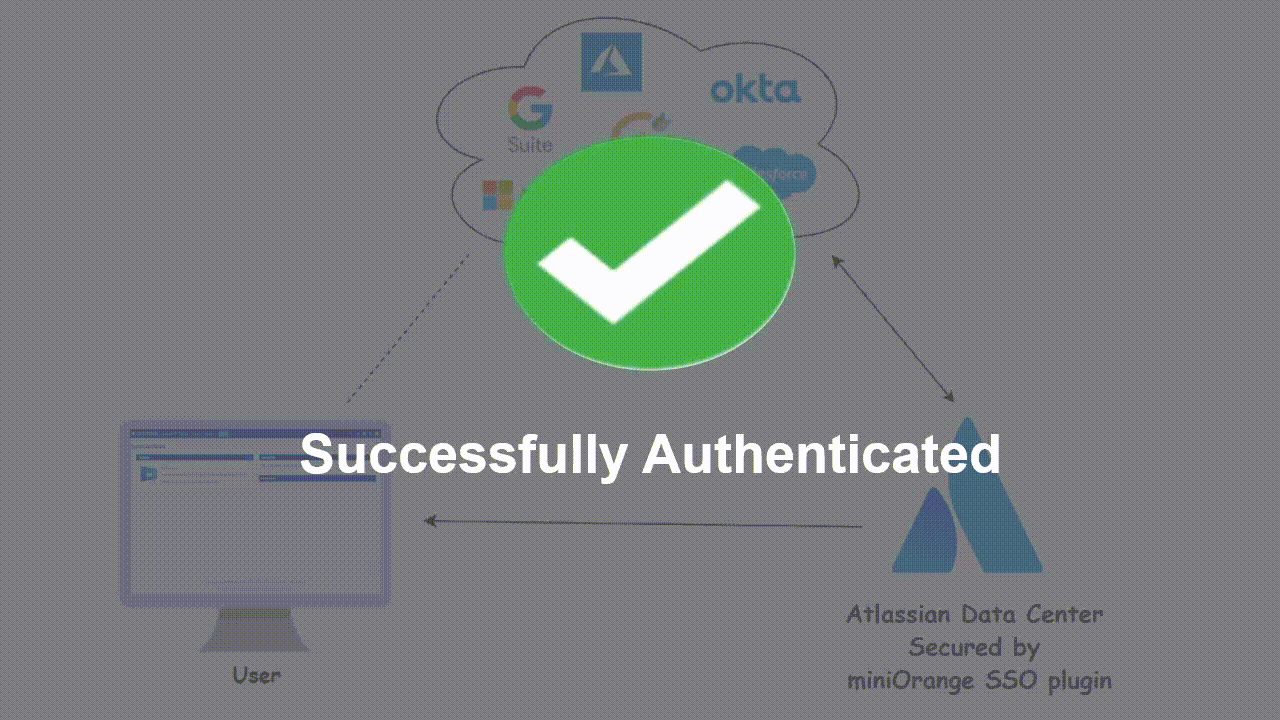
Image: Forced SSO (Auto Redirect)
4. Emergency URL/Backdoor URL to bypass Data Center SSO
Let’s say, unfortunately your IDP goes down or you have messed up something which causes an error while performing Atlassian SSO, then what? Your users will be locked out and won't be able to access their own account and data. And things will not stop here, even you being the admin won't be able to access the default login page, to get into the Jira/Confluence. And then you'll be thinking if by any chance you could bypass the SSO for the time being.
That's where the miniOrange SAML SSO comes up with a useful feature called Backdoor URL or more specifically Emergency URL. It lets you access the Jira/Confluence's default login page even if SSO is enforced for all the users.
Basically it is a URL that enables you to bypass the Single Sign On (SSO), and use the local credentials. Also, it is configurable so the admin gets to decide what it should be. Thinking about more security? We got you! For that you can enable group restriction upon the Emergency URL, so that only users belonging to particular groups will be able to access the default login page.
5. Managing Internal & External Users
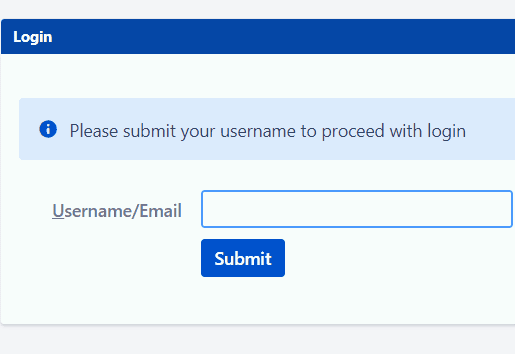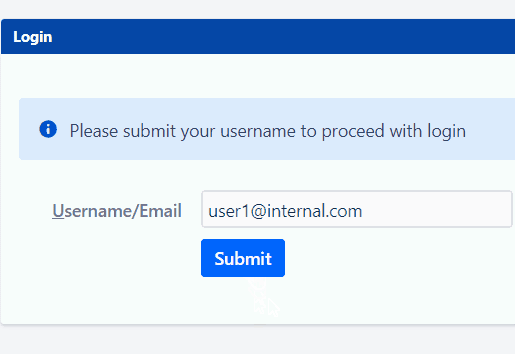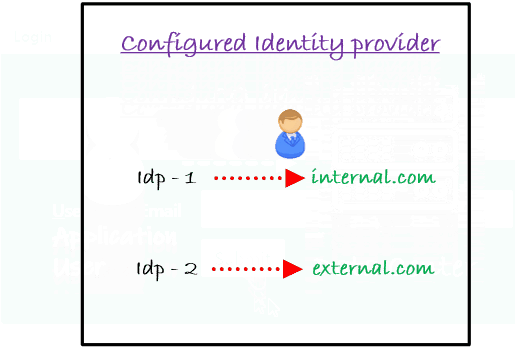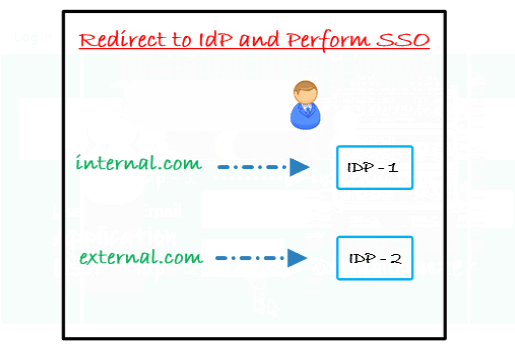
Enterprise organization infrastructure is complex and there is always a big problem of how to manage internal and external user login in the Data Center. Sometimes user identities are stored in multiple Identity Providers or sometimes multiple directories are under the same Identity Provider.
So how would you solve this critical problem and make sure of a smooth user login experience? Well, it is not that difficult when it comes to the miniOrange SSO apps.
You have to define certain rules on the user set to manage internal and external users. These rules can be based on the application groups, directories or even email domain of the users. Some of these rules can be -
- Mapping set of groups or permissions to internal and external users
- Assigning internal and external users to specific directories
- Having fixed email domains for internal and external users
- Or even having different application URL for internal and external user login
You just have to define differentiator factors for users and the rest will be handled by the miniOrange SSO plugin.
One more differentiator factor can be IPs or IP Range. You need to set an IP range in the miniOrange SSO plugin for internal and external users and you are good to go.
For any users not falling into any of the rules, a default setting can be set for the rest of the users.
Let’s consider an example of Email Domain based mapping for Internal users and External users.
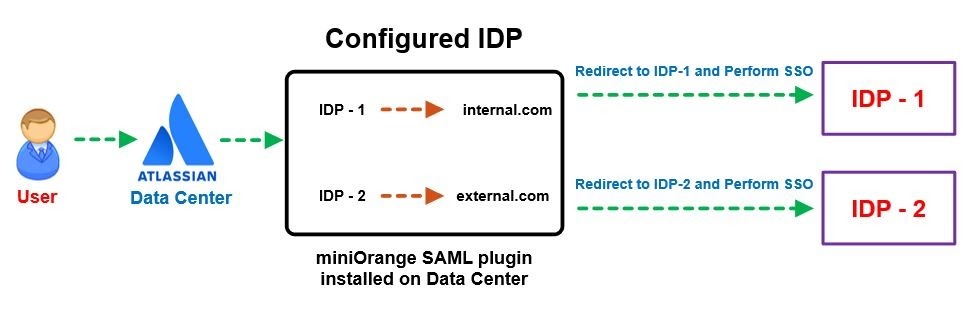
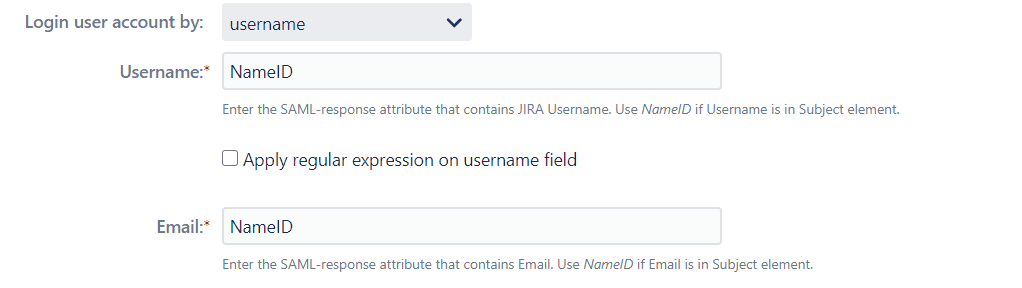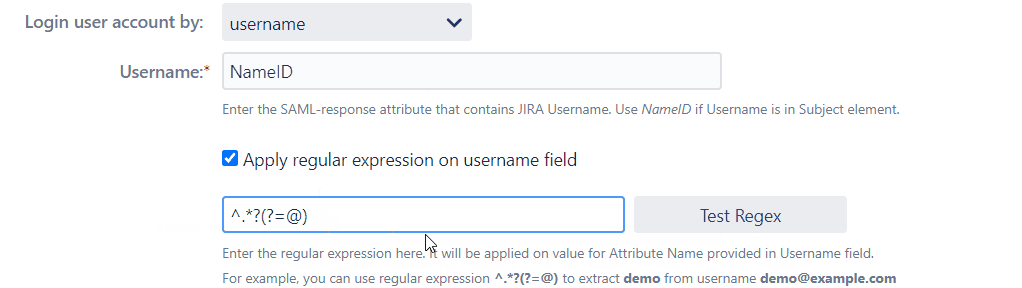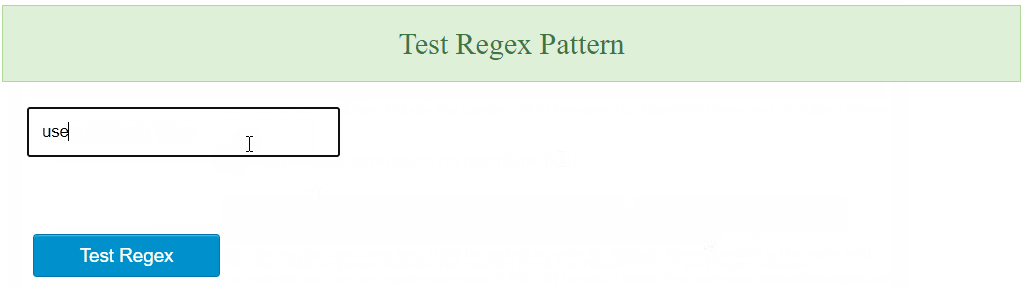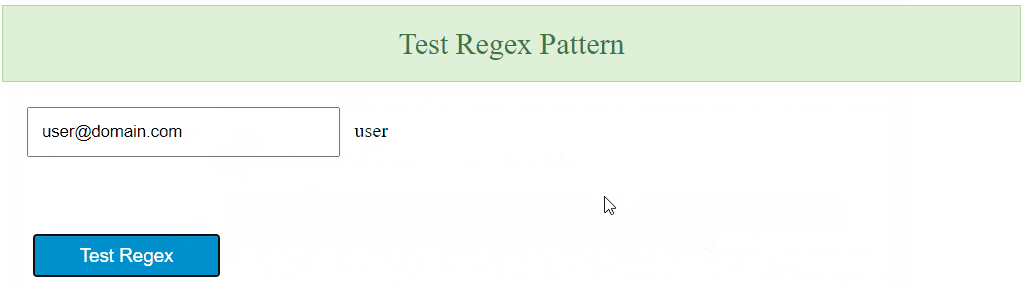
6. Conveniently Modify Username and get logged in with Regular Expression!
Regular Expression, regex for short, is a strong tool for performing string search and manipulation operations. There might be some cases where you want your attribute value in some particular format but your IDP’s SAML response attribute values are not the same as the format you want or you prefer. In such scenarios Regex comes in very handy.
Consider a situation where the user's username needs to be extracted from his or her email id “user@domain.com”. Apply Regular expression on username field, the attribute name containing the user's email as a value in the Username field. After applying the regex.*?(?=@) in the regex field, the entered expression will extract the value “user” and display the username in the user's profile.
7. One-click configuration setup
SSO Setup is a complex procedure which requires correct configuration. It is essential to make sure every user’s access and permissions are set up properly. This is a time-consuming and tedious process and prone to errors which may lock you out!
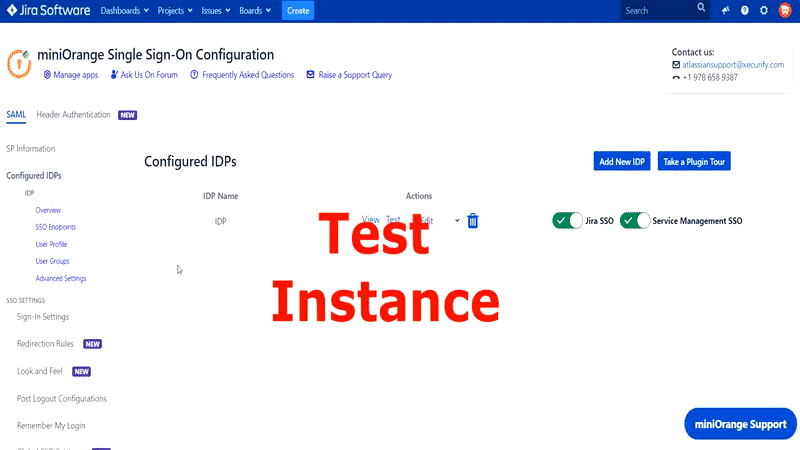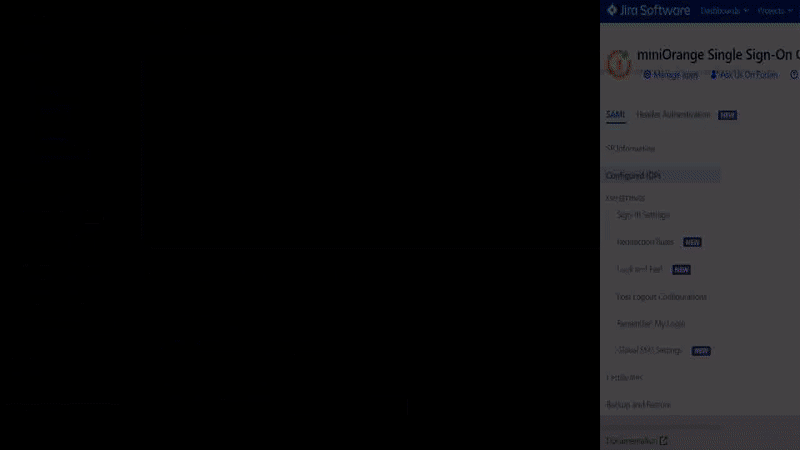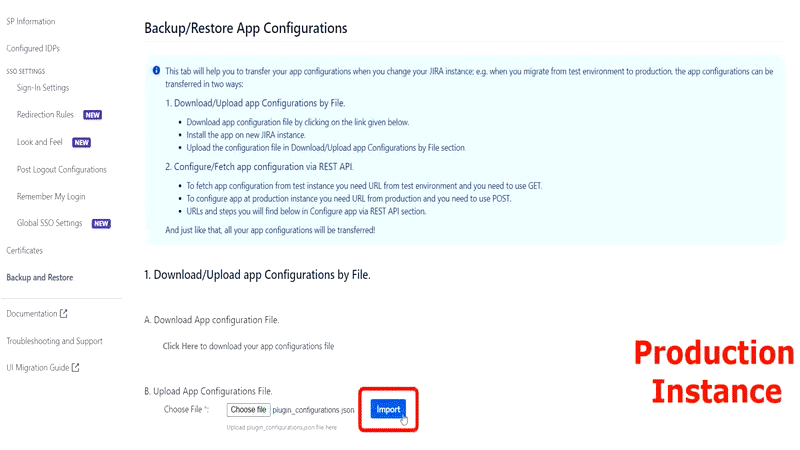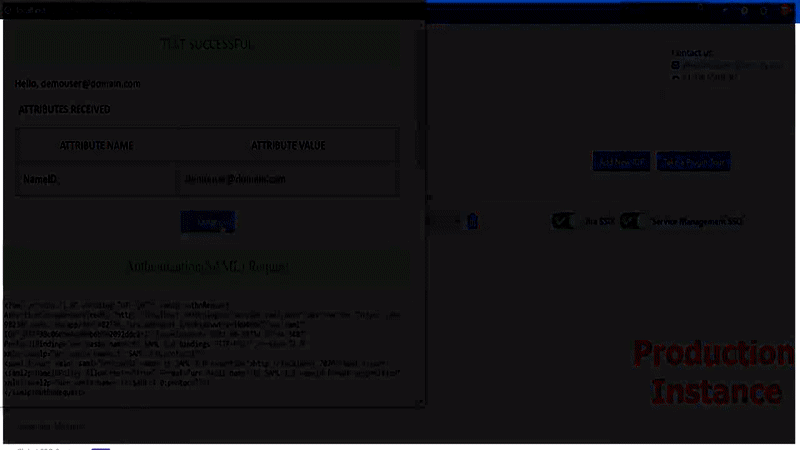
If you are testing the setup at your test environment, you can use the same configuration to deploy to the production environment. With exported data, administrators do not need to reconfigure the entire setting again. This reduces entire setup time and chances of messing up configuration at the very critical system.
Export configuration from Test Instance using Backup plugin configuration file:
Administrators can export all plugin configurations in JSON format and import them at another instance via file transfer. The entire procedure can be done within minutes and is accessible to only administrators.
8. Design your own Login, Logout and Error page
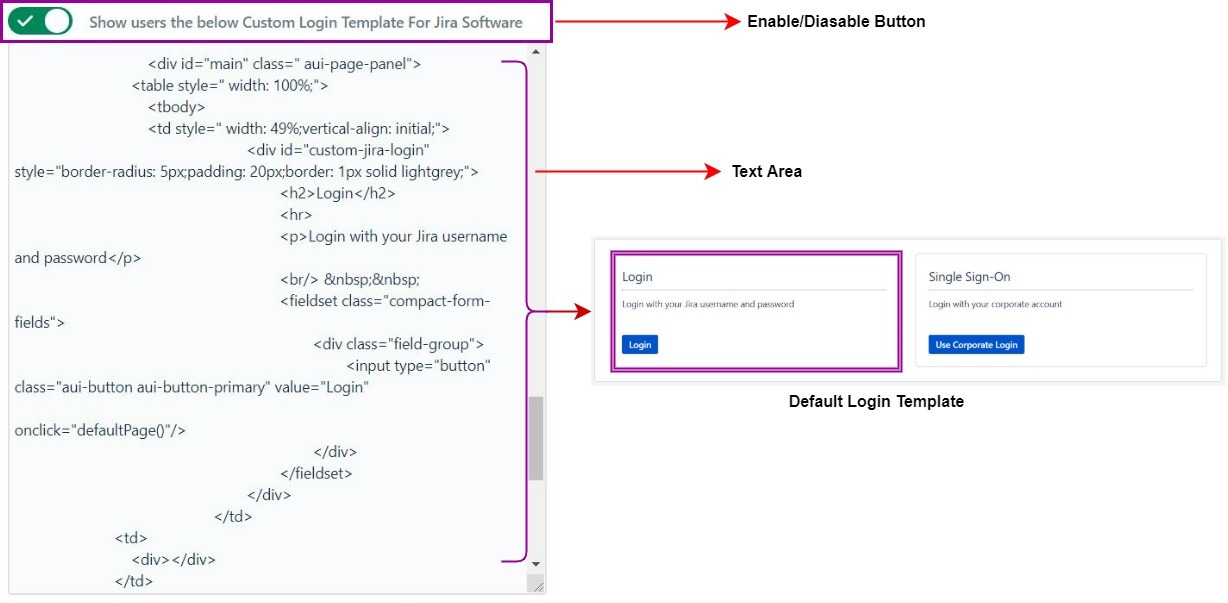
A product that is static in its existence either in terms of language or User Interface creates a bad impact on user experience. miniOrange SAML SSO add-on breaks these boundaries by providing customizable Login, logout and Error Templates. This feature will help users around the globe to configure their own template depending on their use and their needs.
Each Customizable Template section either be it Login or Error Template has an enable/disable button. Enabling that button gives users the ability to make changes in the Template Design Area. Now administrators, depending upon their interest and need, can code their own designed template and input it in this section and Save their changes by clicking on Save Button. Once changes are saved, they will be reflected when the user tries to login to the application again, from there on users can view the enabled logout and error templates too. So go on and create lasting impressions over the onlooking users from a simple login to a memorable logout. By default miniOrange SAML SSO add-on provides a Custom Login and Error Template but they can be modified by the user.
9. Configurations using REST APIs
Use of the Rest API makes people's lives very easy. As it is built to make remote calls to the server and easier to embed in the program, it is just an effortless way to communicate with the system you want.
The miniOrange SSO plugin lets you use the Rest API for your plugin configuration bringing lots of scope to automate manual and tedious work. You can couple this with your own system which updates your plugin configuration, with the data which can be fetched using the Rest API as well or download the file.
As Rest API is a widely accepted protocol you won’t have much difficulty using it, and as far as your security is concerned miniOrange plugin provides Advanced Authorization for Rest API so rest assured that only verified admins have access to it.
Table of Contents
- Advanced User & Group Provisioning
- Just In Time Provisioning (JIT)
- Autoactivate Users on SSO
- Automated Permission Management
- Jira Service Management SSO
- Advanced Security
- Prevention against SAML replay attack
- Restriction on password change
- Secure login for admin users
- SAML Signed Request and Encrypted Assertion
- Ease & Flexibility of Access

