SAML Single Sign On (SSO) into Bitbucket using Microsoft Entra ID (Previously known as Azure AD) as IDP
Bitbucket SAML app gives the ability to enable SAML Single Sign On for Bitbucket Software. Bitbucket Software is compatible with all SAML Identity Providers. Here we will go through a guide to configure SSO between Bitbucket and your Identity Provider. By the end of this guide, users from your Identity Provider should be able to login and register to Bitbucket Software.
Pre-requisites
To integrate your IDP with Jira, you have to ensure the following prerequisites are met:
- Bitbucket should be installed and configured.
- Bitbucket Server is https enabled (optional).
- Admin credentials are set up in Bitbucket.
- Valid Bitbucket Server and Data center Licence.
Download and Installation
Now, let’s look at how you can download and install the miniOrange Jira SAML Single Sign On (SSO) plugin for your Jira Data Center.
- Log into your Bitbucket instance as an admin.
- Navigate to the settings menu and Click Manage Apps.
- Click Find new apps or Find new add-ons from the left-hand side of the page.
- Locate Single Sign-On (SAML SSO) Bitbucket SSO SAML+User Sync/SCIM via search.
- Click Try free to begin a new trial or Buy now to purchase a license for Single Sign-On (SAML SSO) Bitbucket SSO SAML+User Sync/SCIM.
- Enter your information and click Generate license when redirected to MyAtlassian.
- Click Apply license.
- SP Entity ID
- ACS URL
 Prerequisites:
Prerequisites:
Copy these values from the Service Provider Info tab of the Plugin .
 Instructions:
Instructions:
Note: Enterprise app configuration is the recommended option for SAML . If you do not have Azure subscription or using free account please setup App Registration Configuration.
To perform Single Logout using Microsoft Entra ID (Previously known as Azure AD), the Atlassian instance (E.g. Jira,Confluence) must be https enabled.
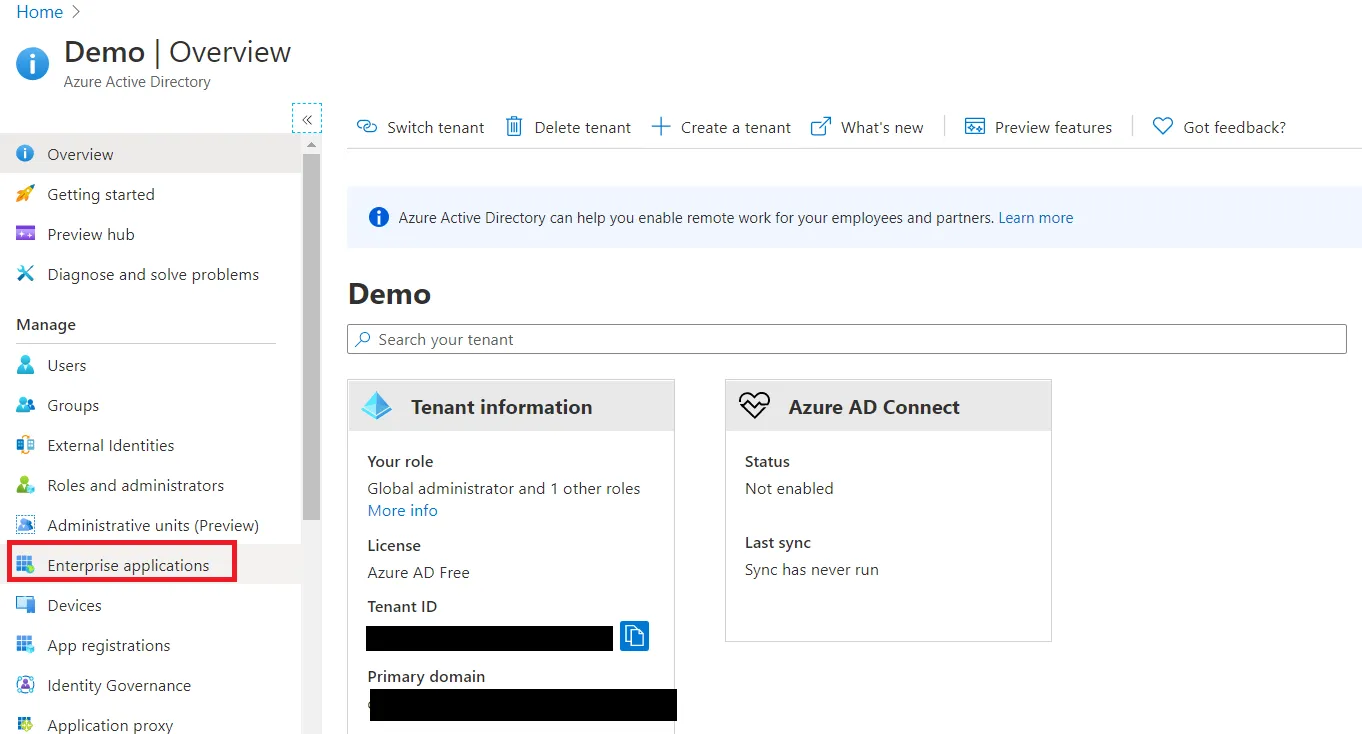
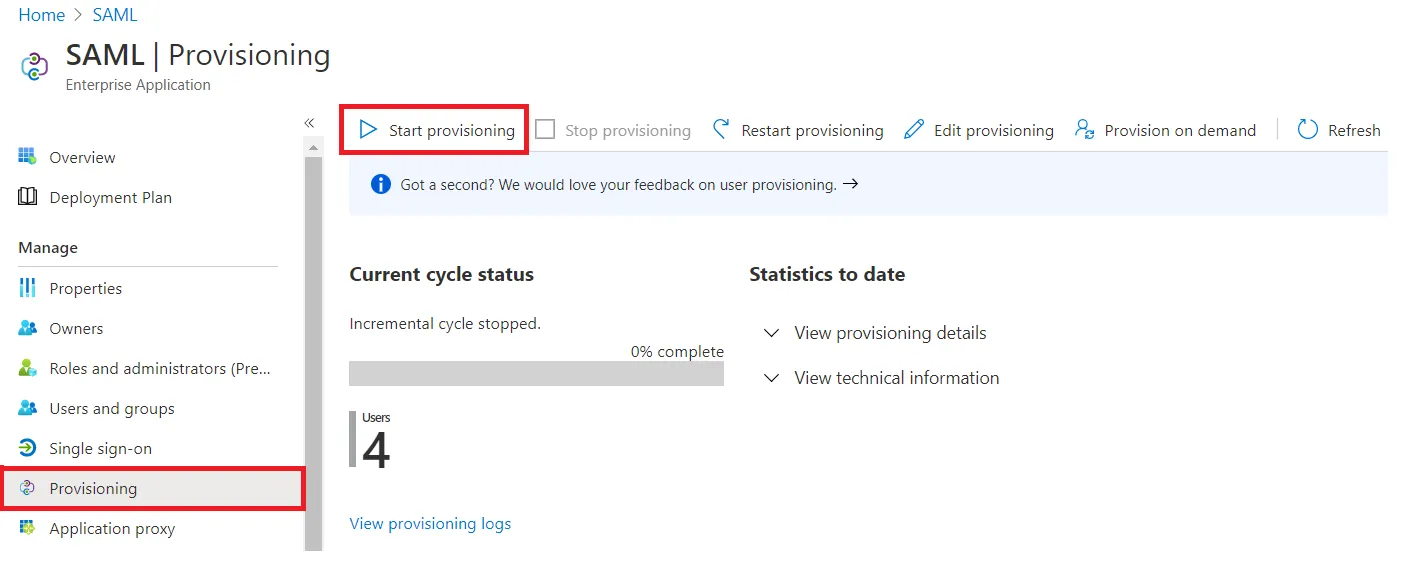
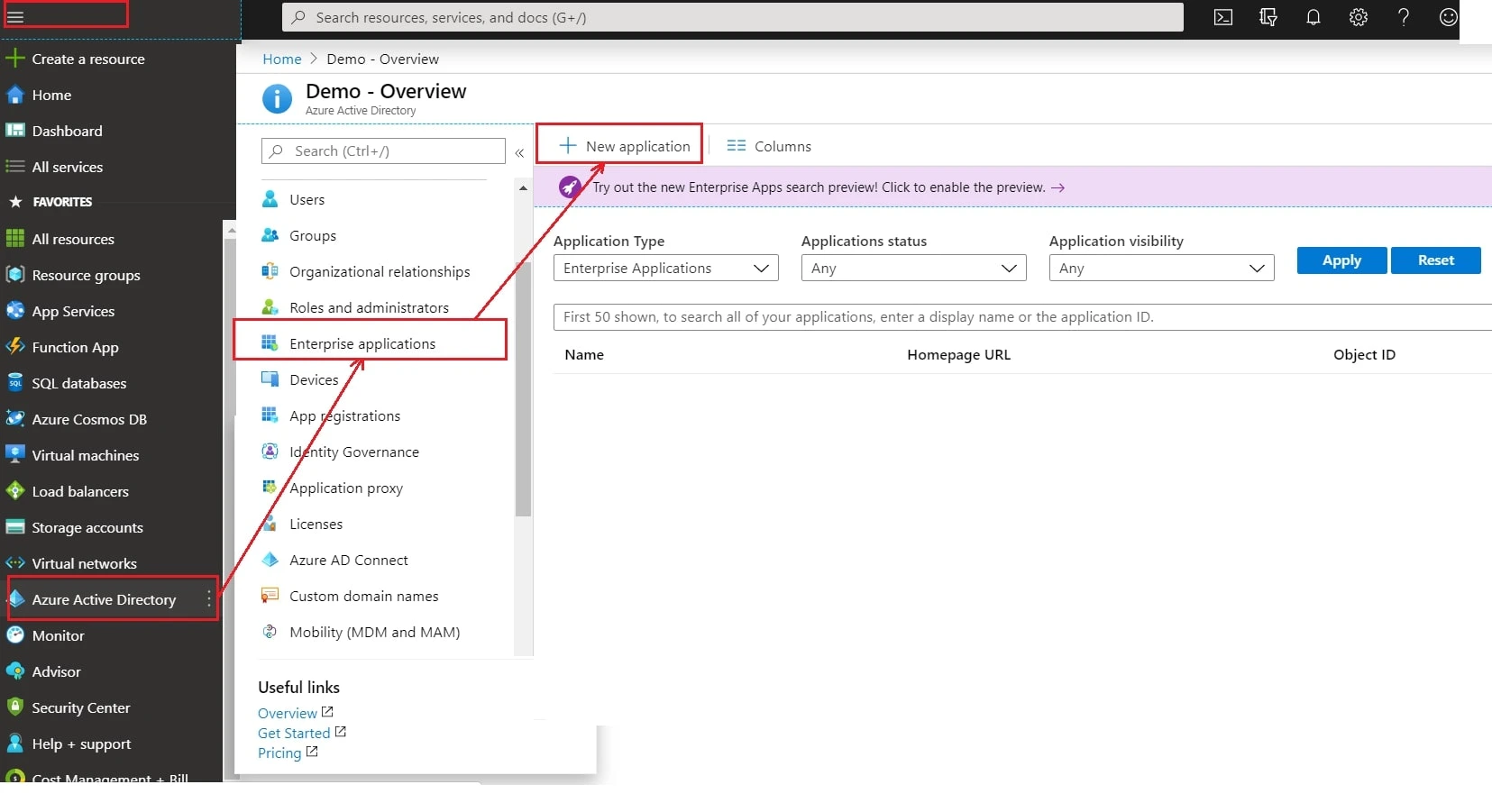
- Log in to Microsoft Entra ID (Previously known as Azure AD) Portal
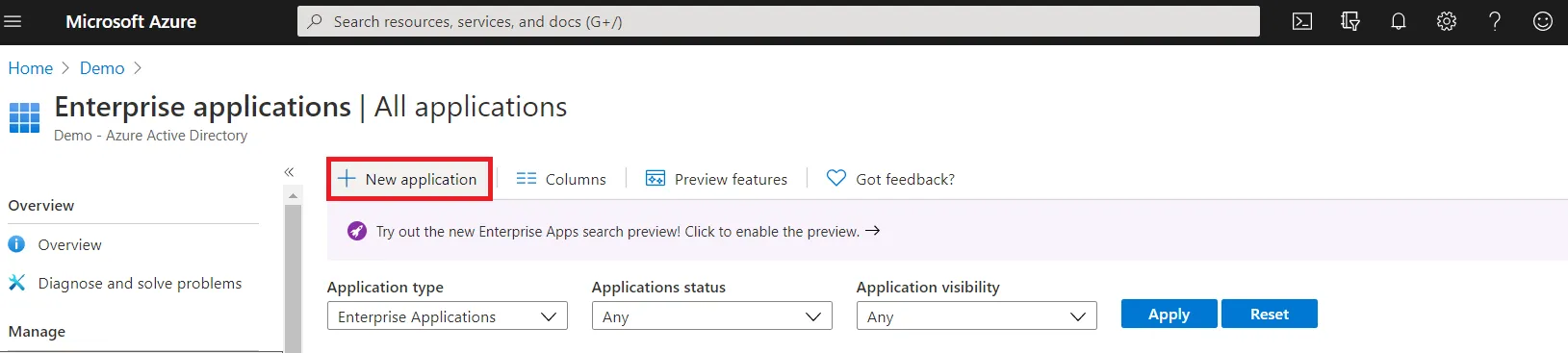
- Select ⇒ and Azure Active Directory ⇒ Enterprise Applications.
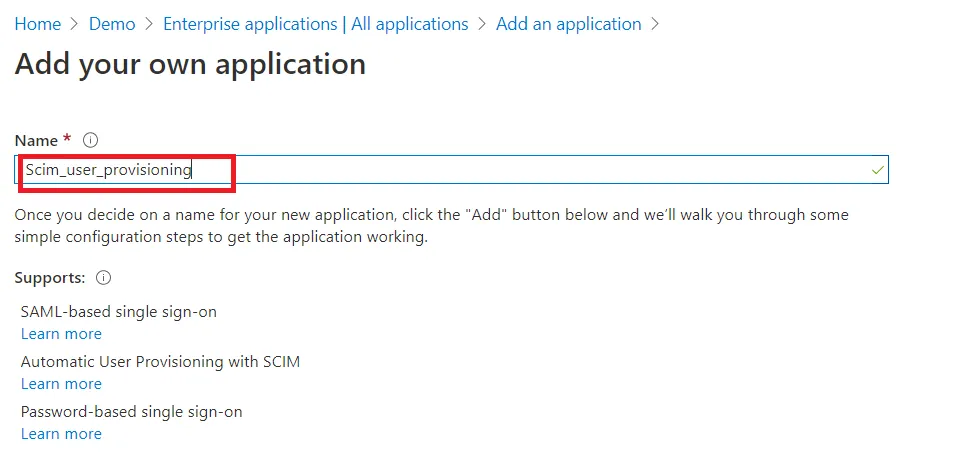
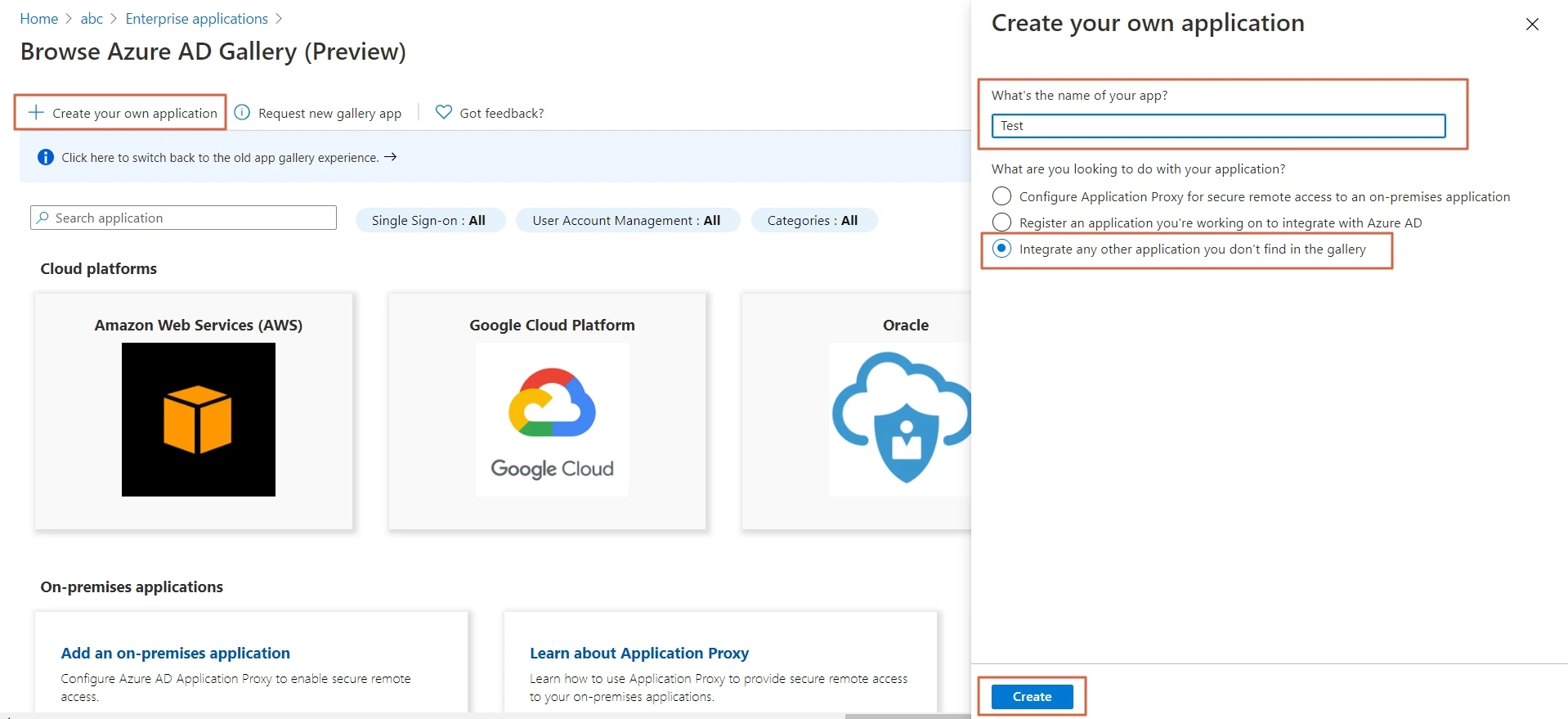
- Click on Create your own application. Then enter the name for your app, select the Integrate any other application you don't find in the gallery checkbox and click on Create button
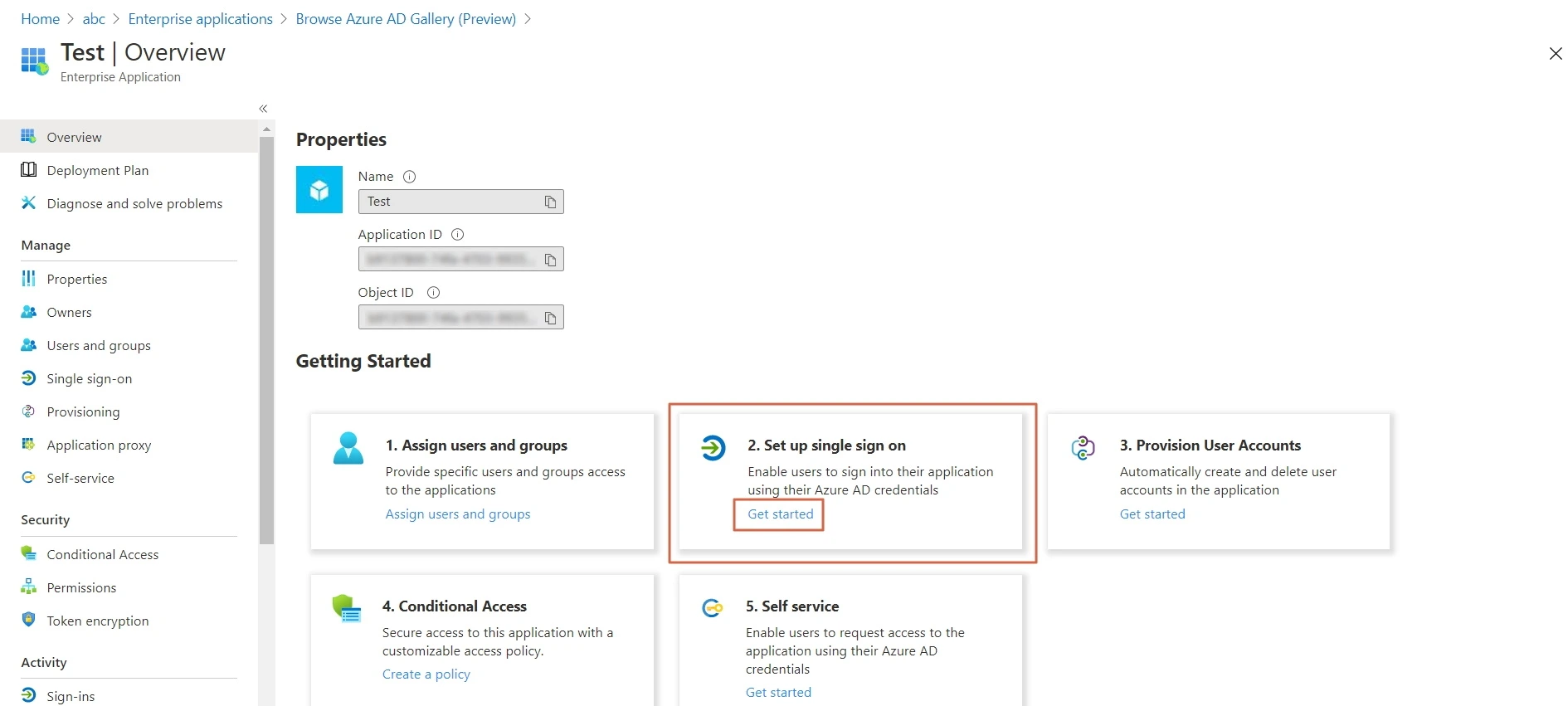
- Click on Set up Single sign-on.
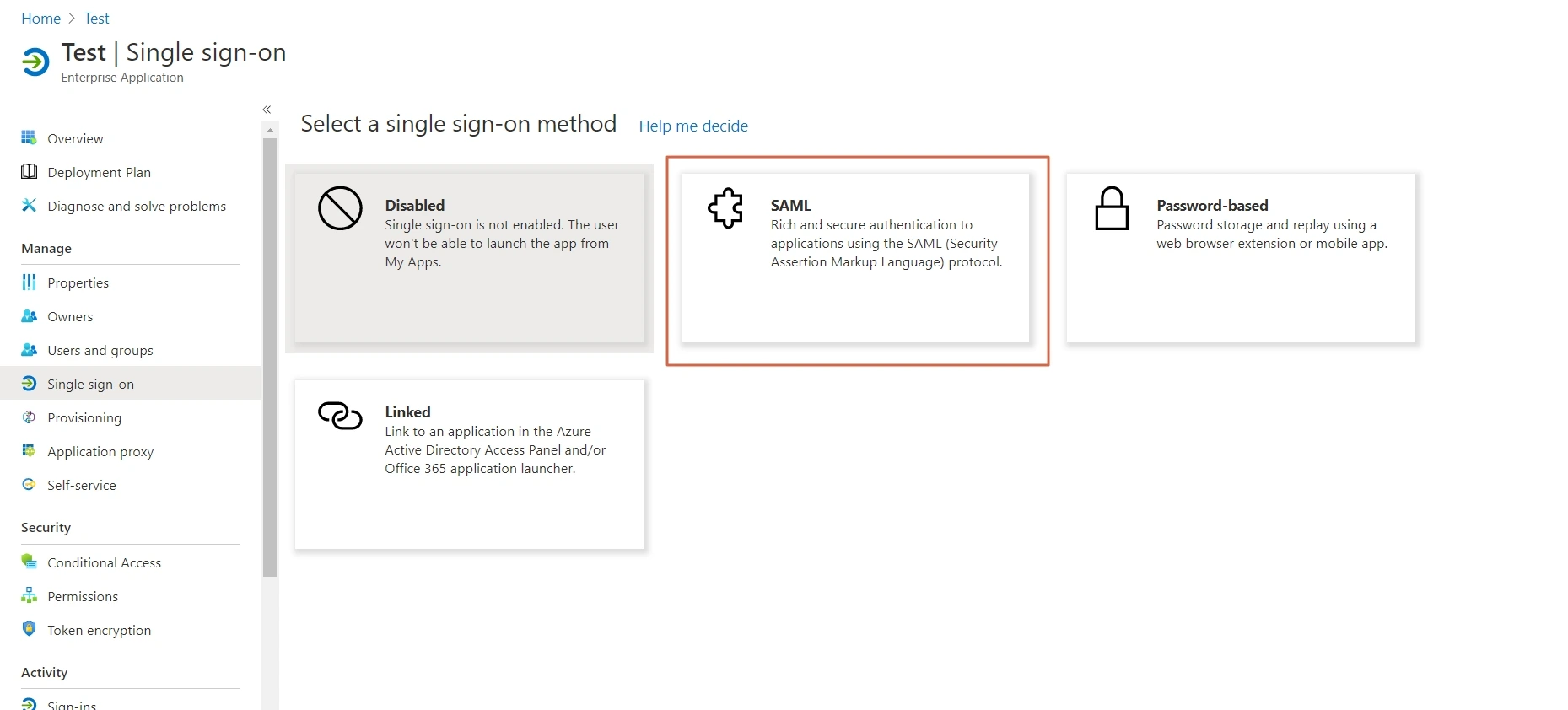
- The next screen presents the options for configuring single sign-on. Click on SAML.
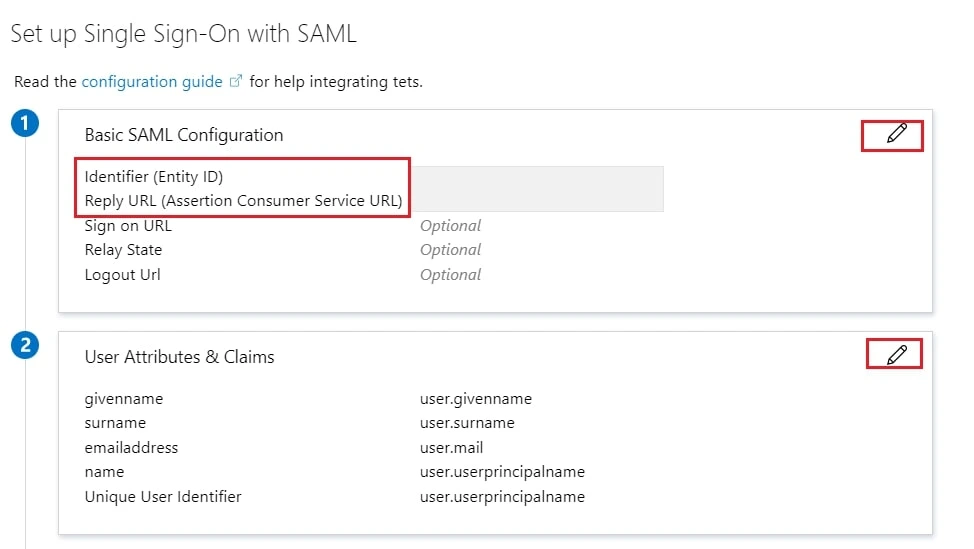
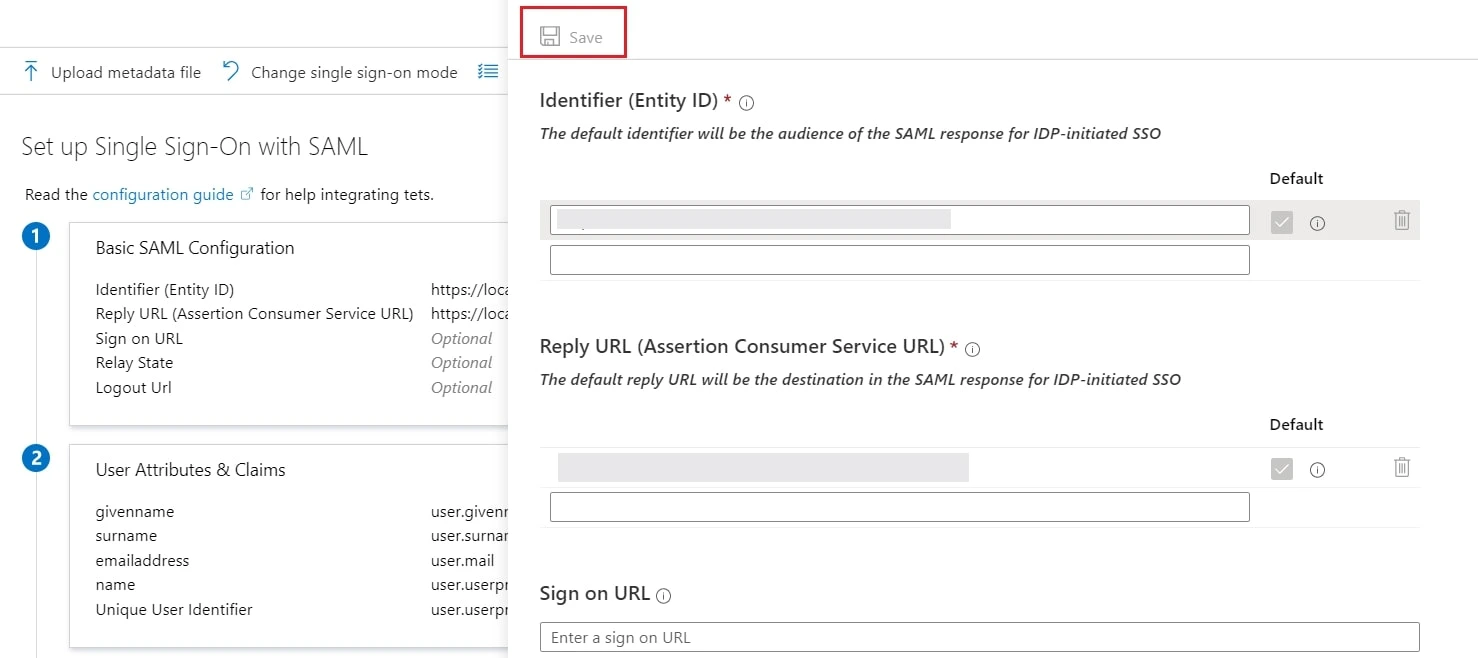
- Edit the option 1 :Basic SAML Configuration to configure plugin endpoints.
- Enter the SP Entity ID for Identifier and the ACS URL for Reply URL from Service Provider Info tab of the plugin.
- Click on Save icon.
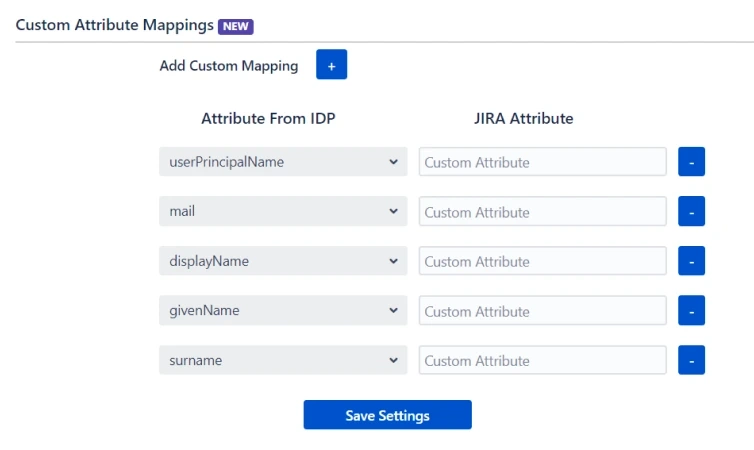
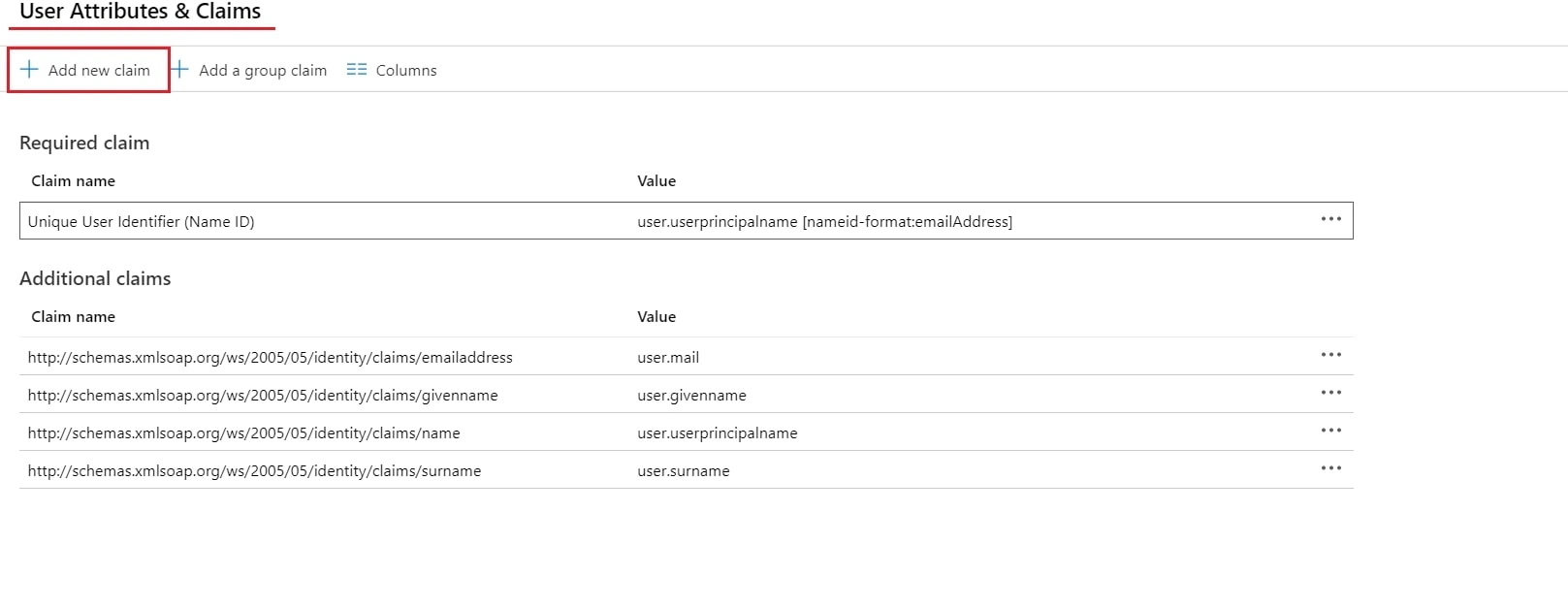
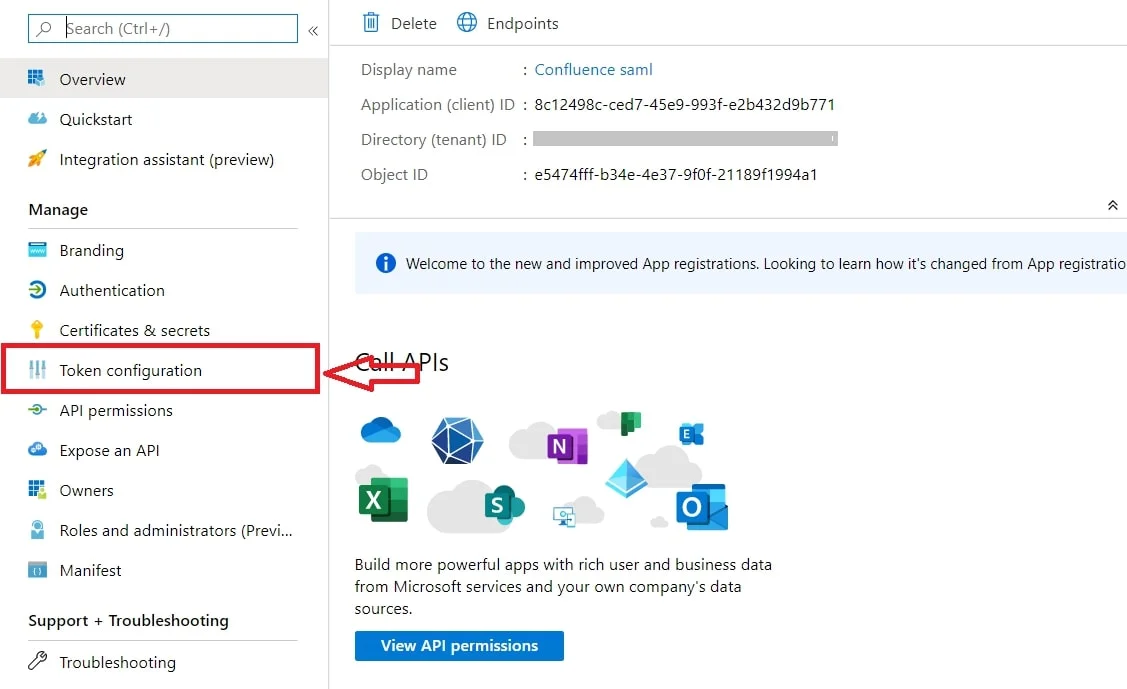
- By default, the following Attributes will be sent in the SAML token. You can view or edit the claims sent in the SAML token to the application under the User Attributes & Claims tab.
- You can add attribute using Add new claim
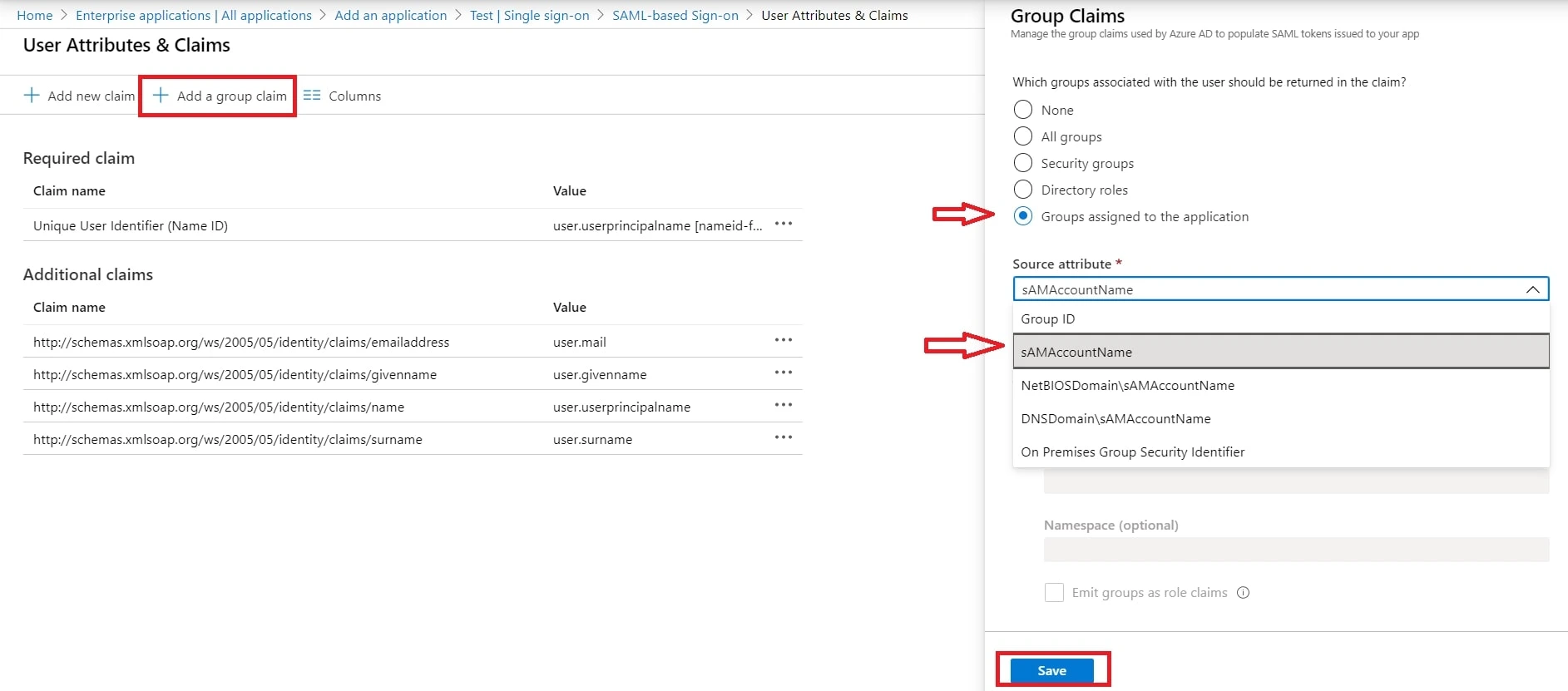
- You can add group attribute claim using Add a group claim
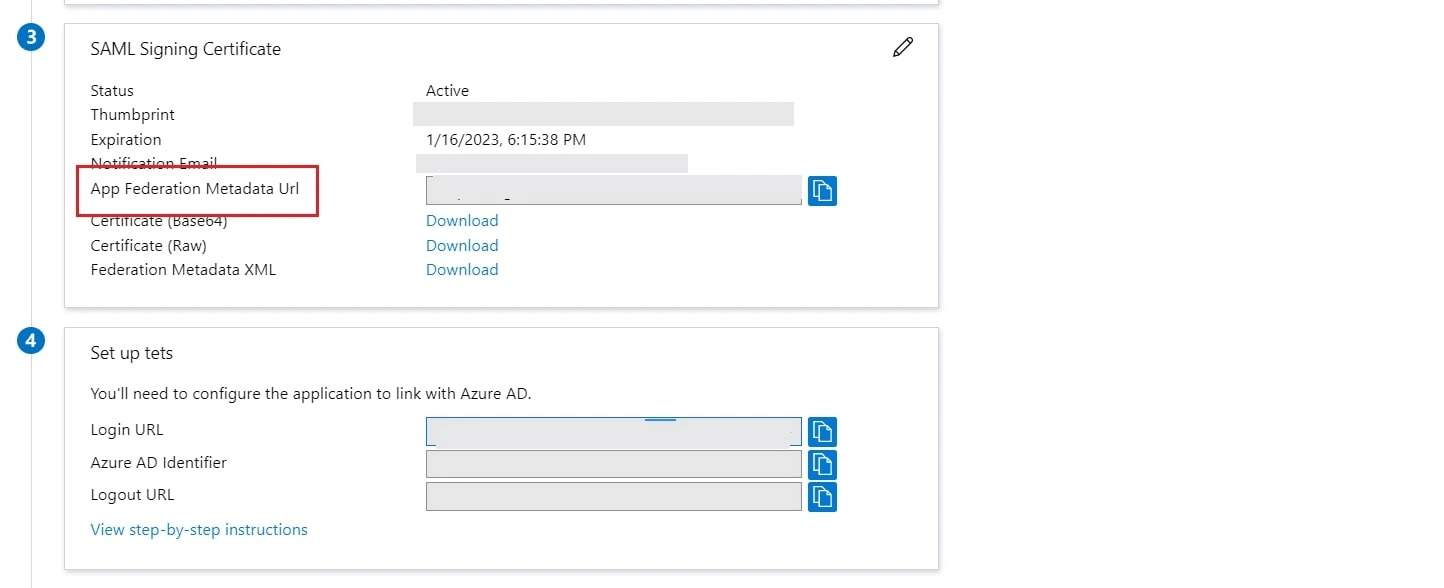
- Copy App Federation Metadata Url from setup tab.
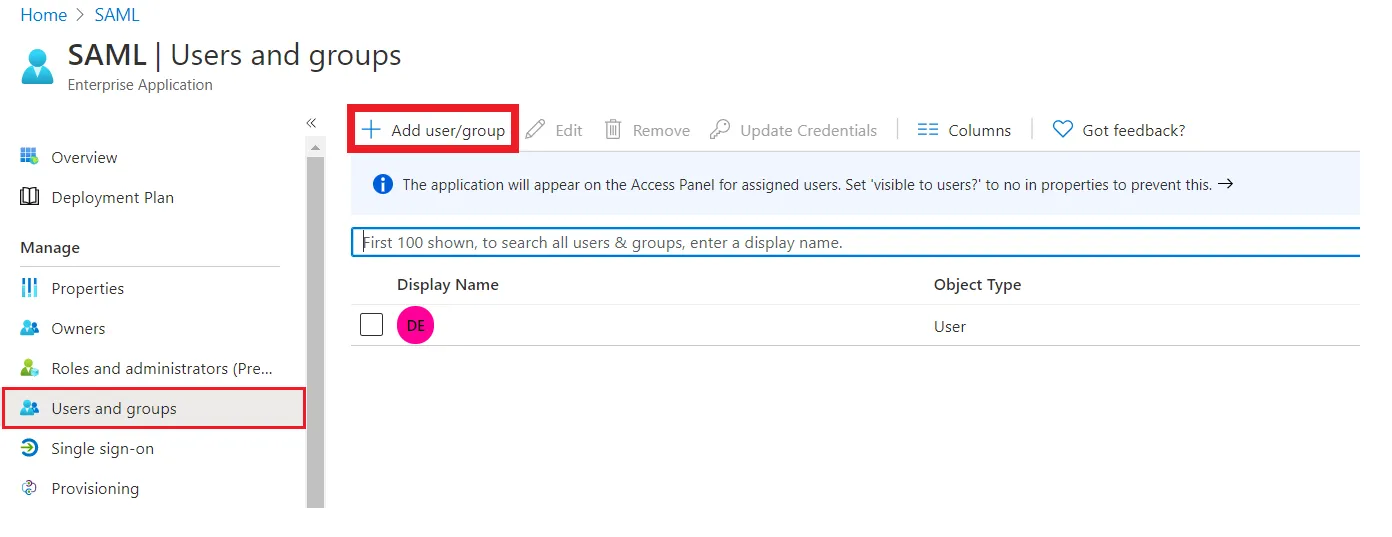
- Click on User and groups from the applications left-hand navigation menu. The next screen presents the options for assigning the users/groups to the application.
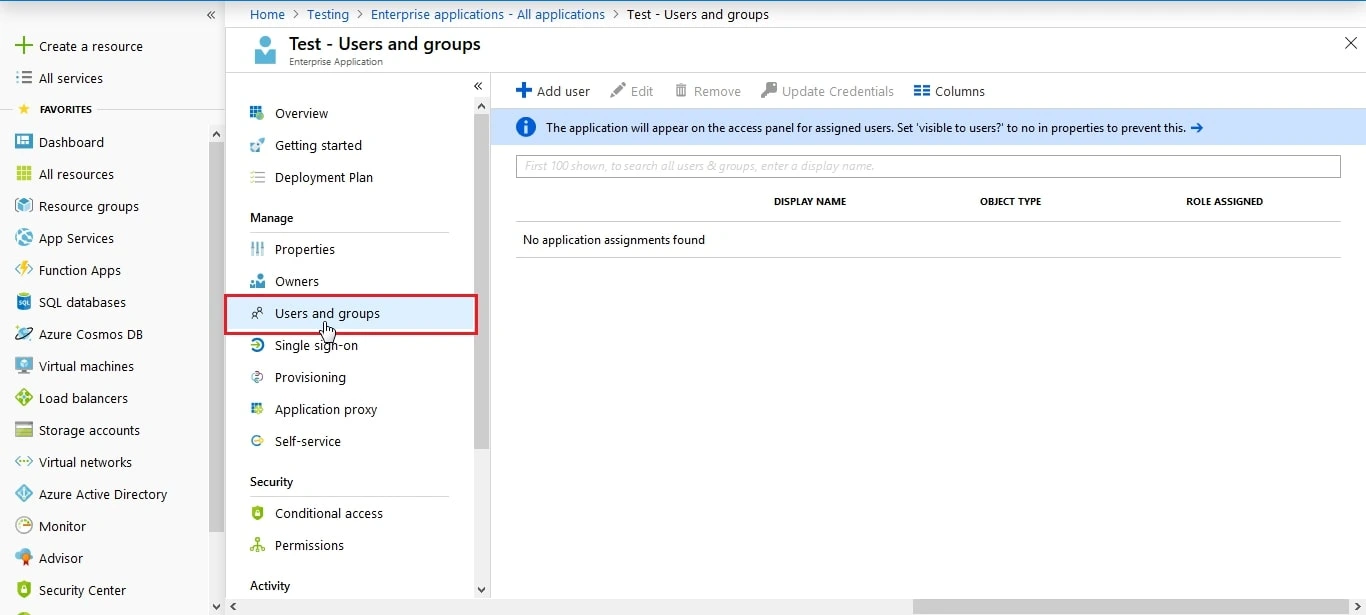
- Log in to Microsoft Entra ID (Previously known as Azure AD) Portal
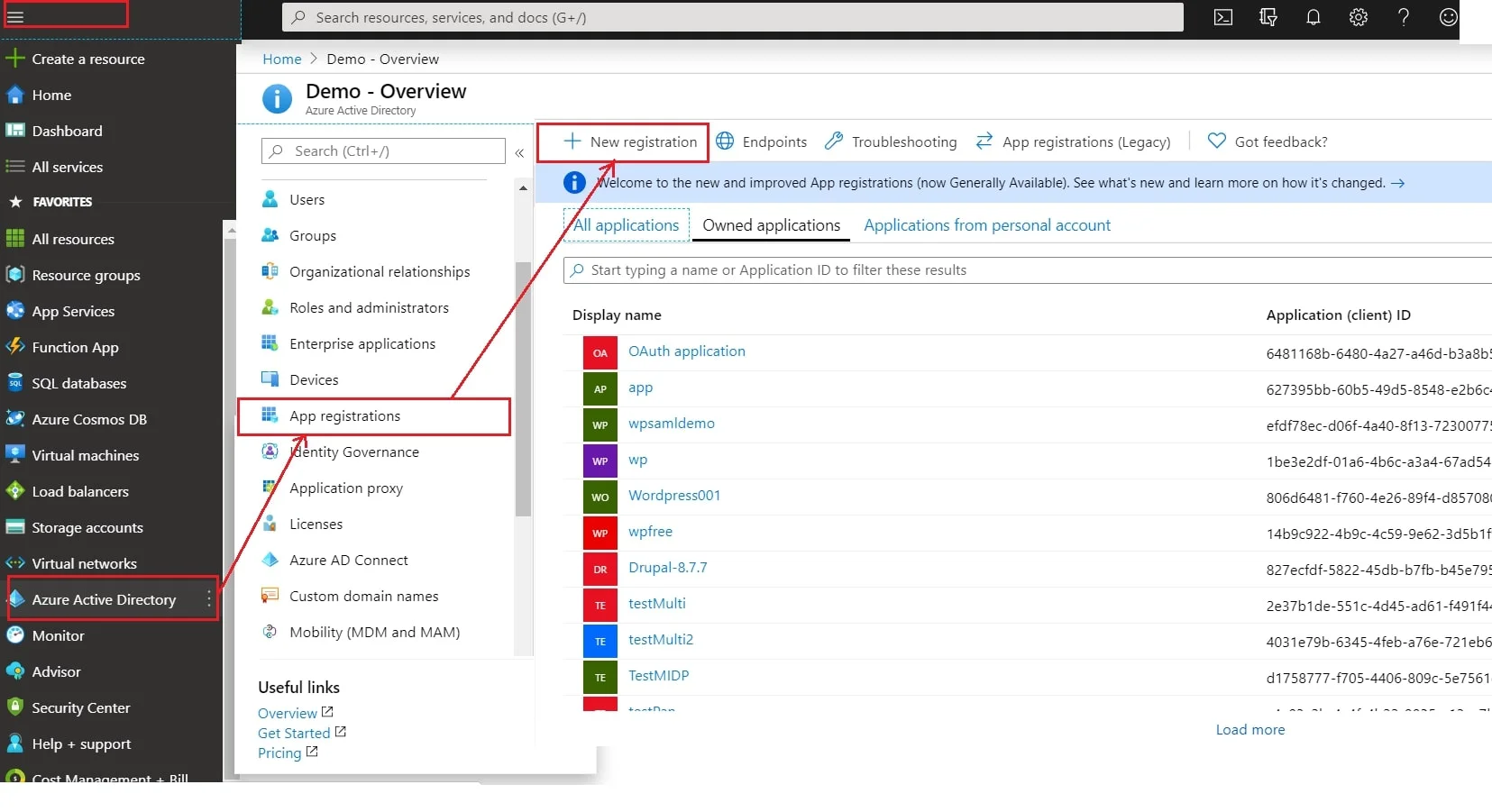
- Select ⇒ Azure Active Directory ⇒ App Registrations. Click on New Application Registration.
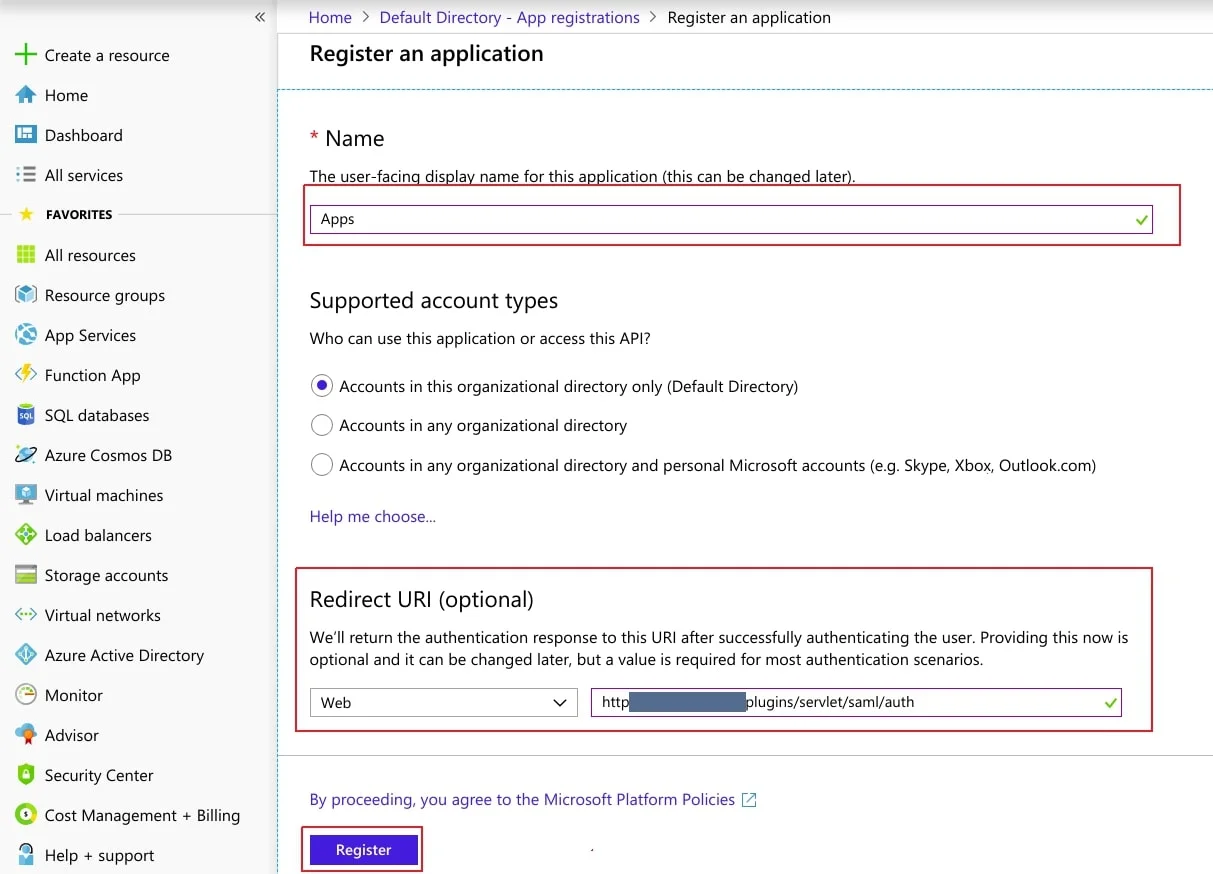
- Assign a Name and choose the account type. In the Redirect URI field, provide the ACS URL provided in Service Provider Info tab of the plugin and click on Register button.
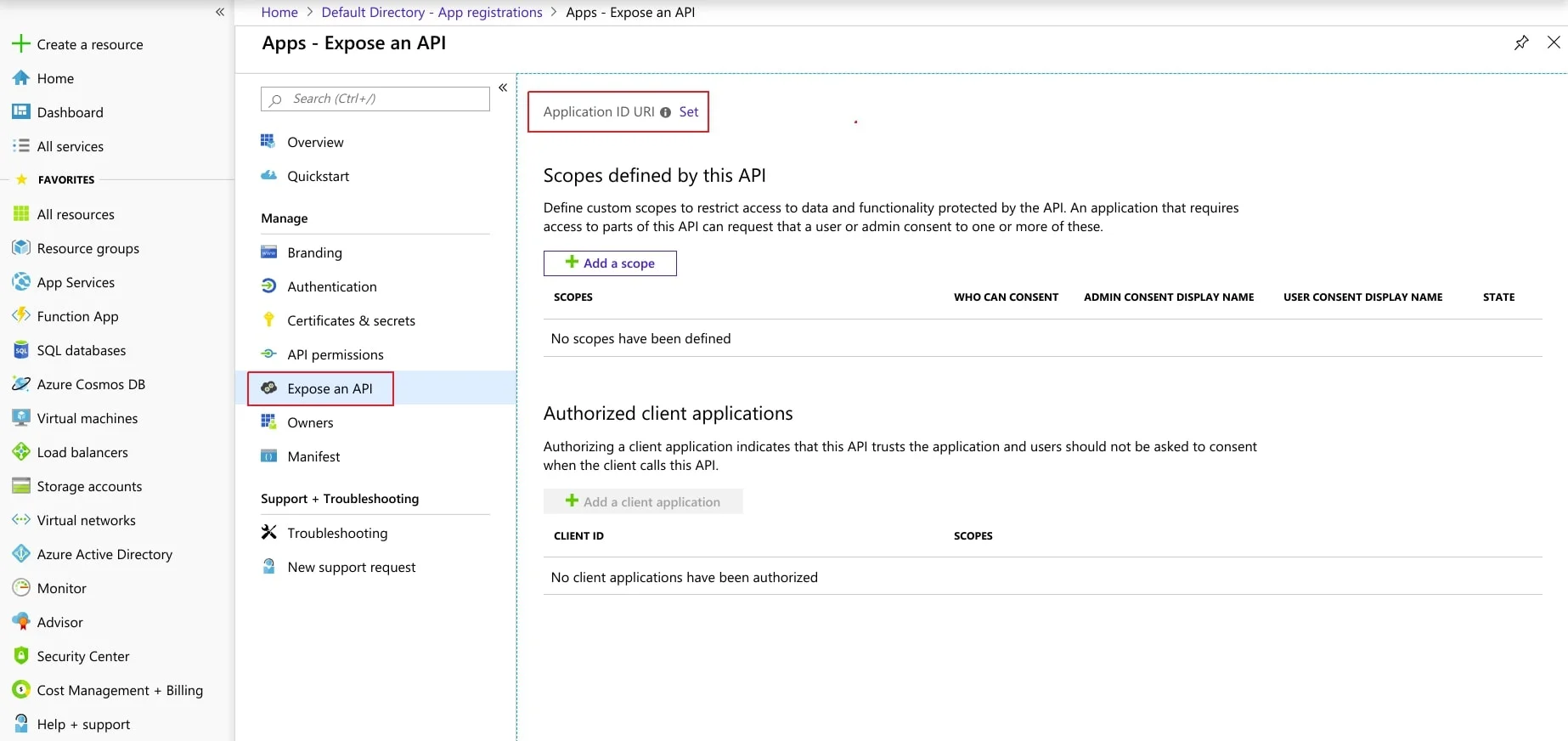
- Now, navigate to Expose an API menu option and click the Set button and replace the APPLICATION ID URI with the plugin's SP Entity ID
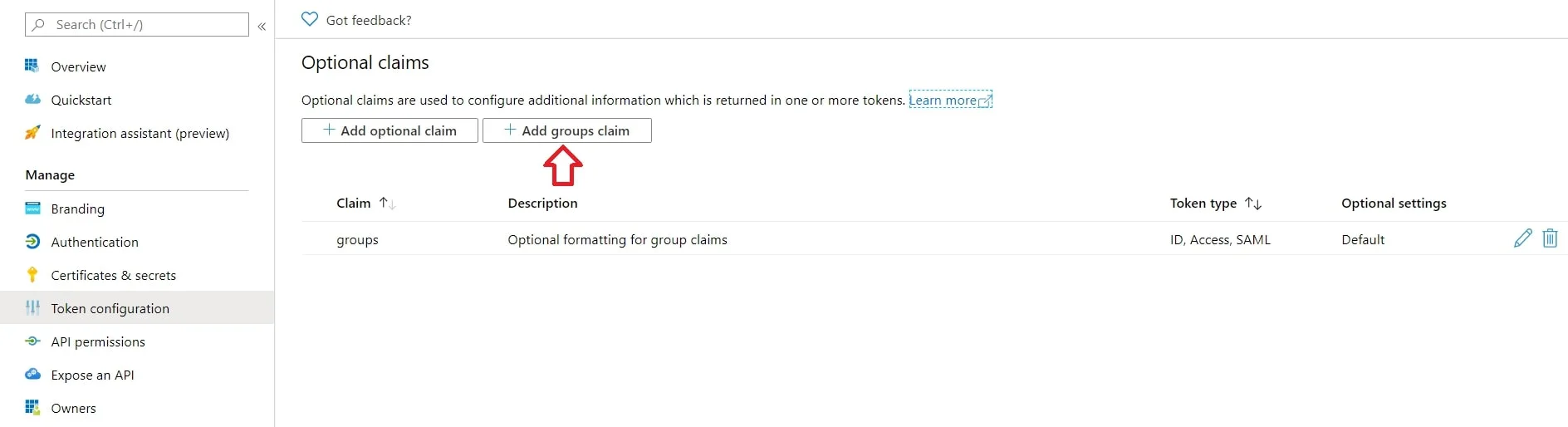
- By default, some Attributes will be sent in the SAML token. If you're not getting group information. Then, add Token configuration for Group information.
- Click on Add groups claim
- Copy the Federation Metadata URL given below. Replace the '{tenant_ID}' part with your
Directory/Tenant ID. This will be required while configuring the SAML plugin.
Federation Metadata URL https://login.microsoftonline.com/{tenant_ID}/federationmetadata/2007-06/federationmetadata.xml
Step 2: Set Up Bitbucket as Service Provider
With the Quick Setup method, you can get the SP metadata from the first step of adding an IDP. The steps to initiate Quick Setup are given below :
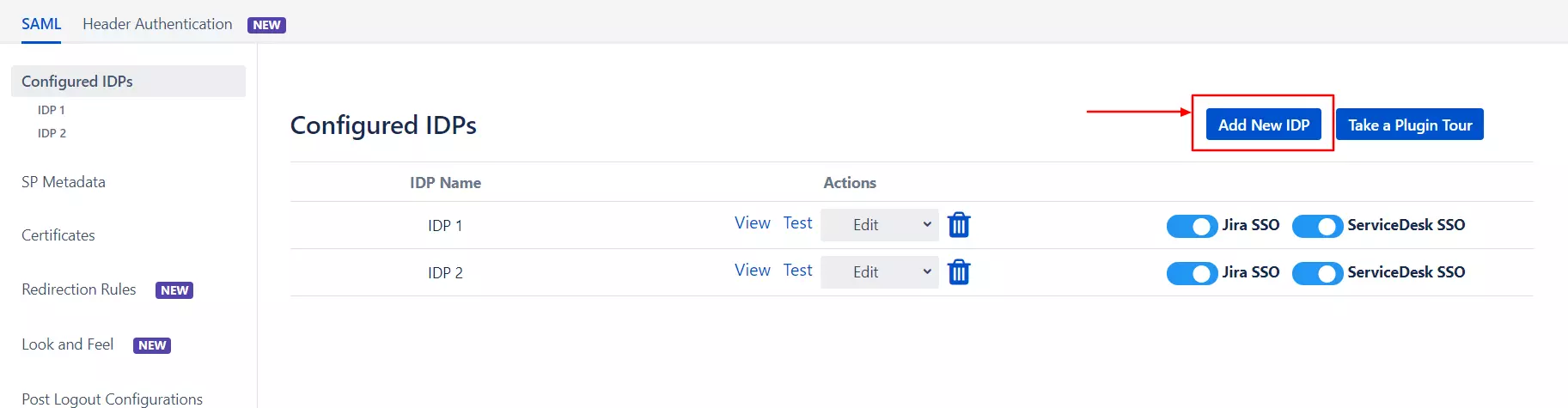
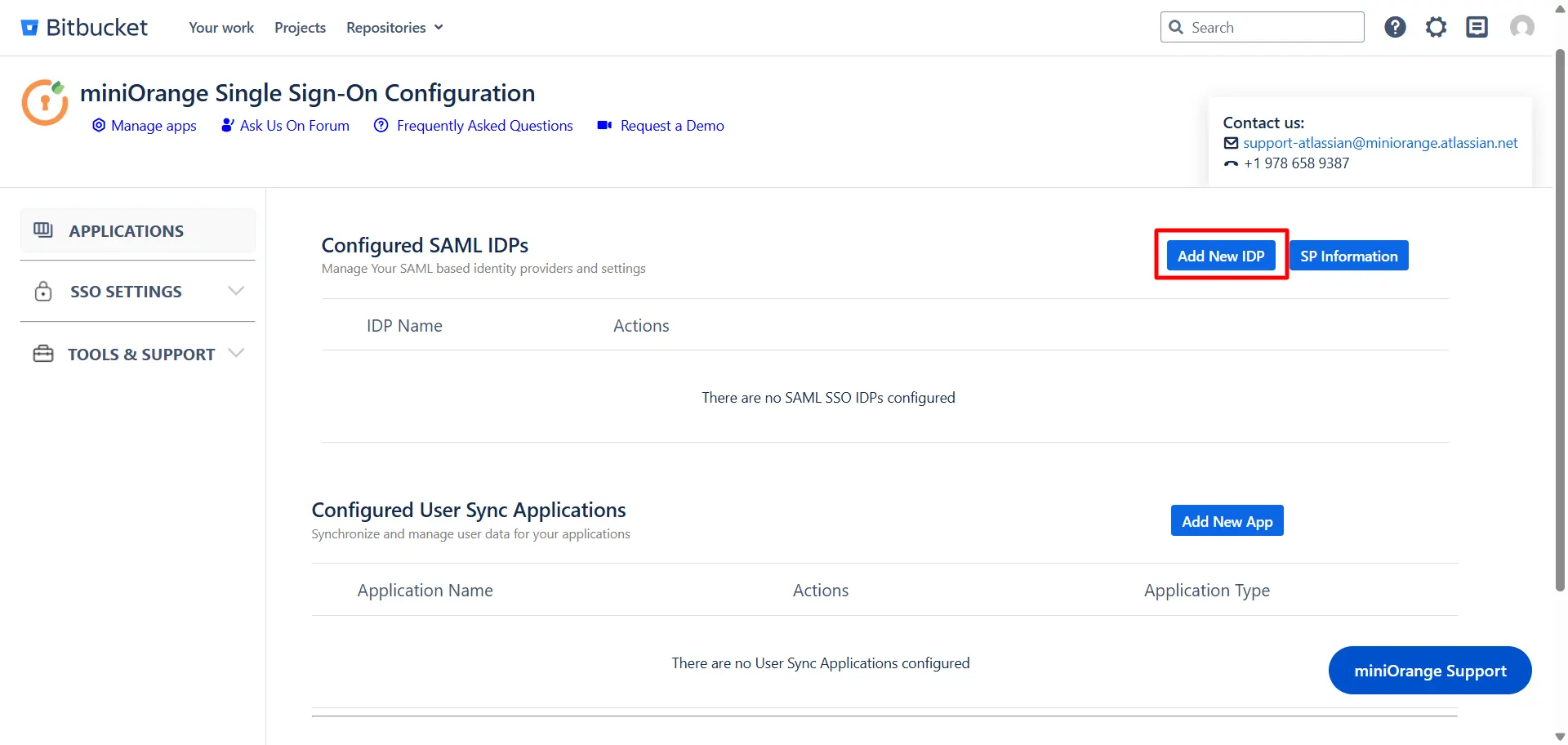
- Click on the Add New IDP button in the Configured IDPs section.
- Select the Quick Setup option in the pop-up that opens.
- Select your IDP from the list of IDPs displayed.
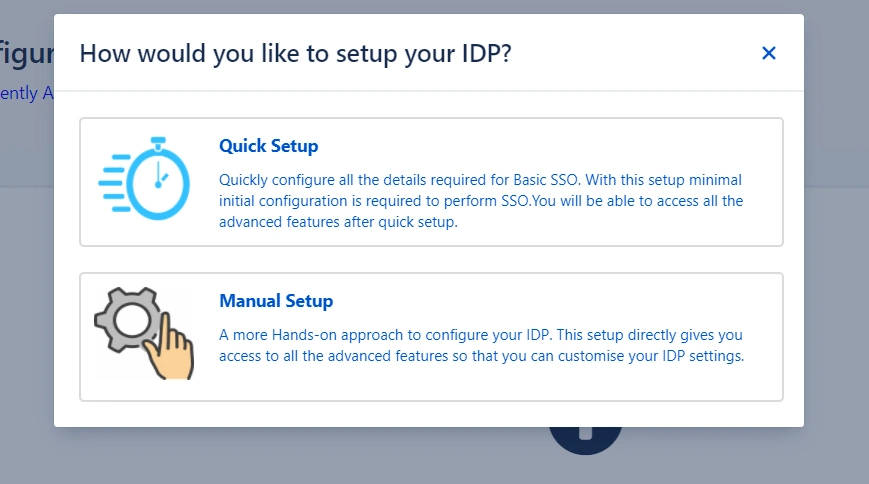

After completing the above steps, you will see the first step of the Quick Setup process. This step deals with setting up your IDP.
 Service Provider Metadata
Service Provider Metadata
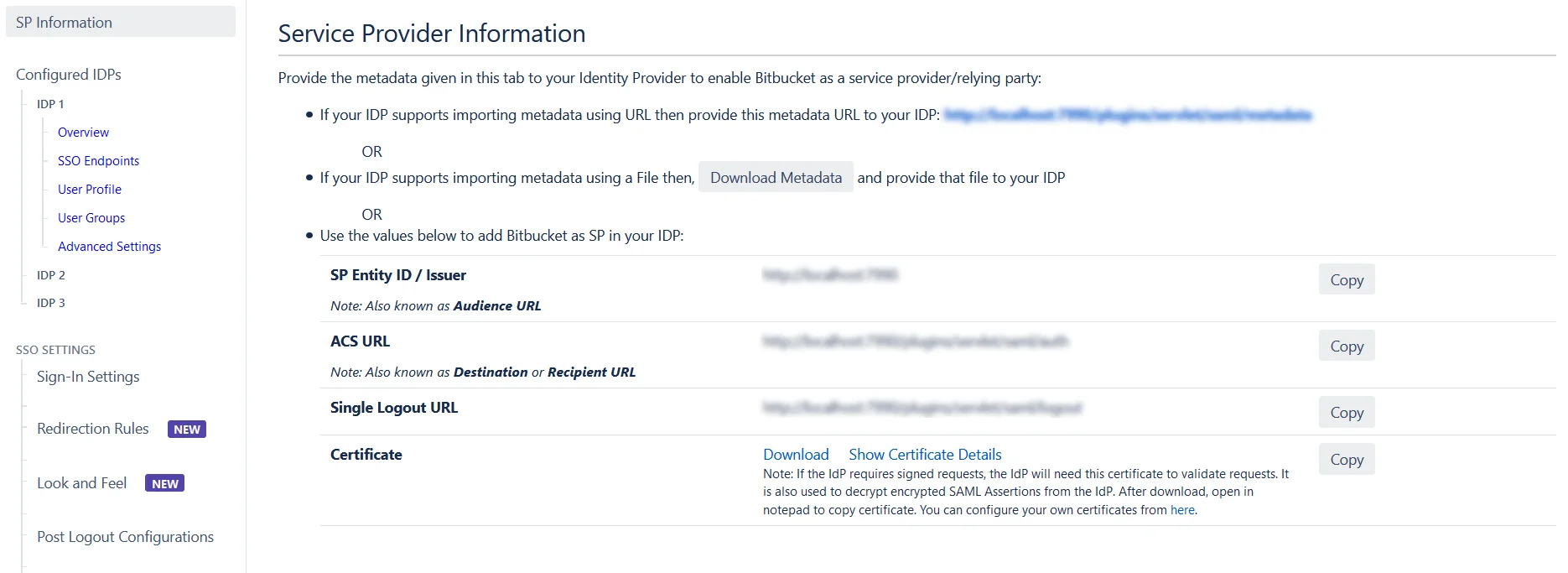
Here you will find your SP's metadata. You will need to provide this metadata to your IDP. There are two ways to add this metadata to your IDP.
- Importing the metadata
- If your IDP supports importing the metadata, then you can choose By providing a metadata URL to the IDP.
- Depending on how your IDP accepts the metadata, you can either provide the metadata URL or you can use the Download Metadata button to download an XML file for the same.
- Manually adding the metadata
- SP Entity ID
- ACS URL
- SP Certificate
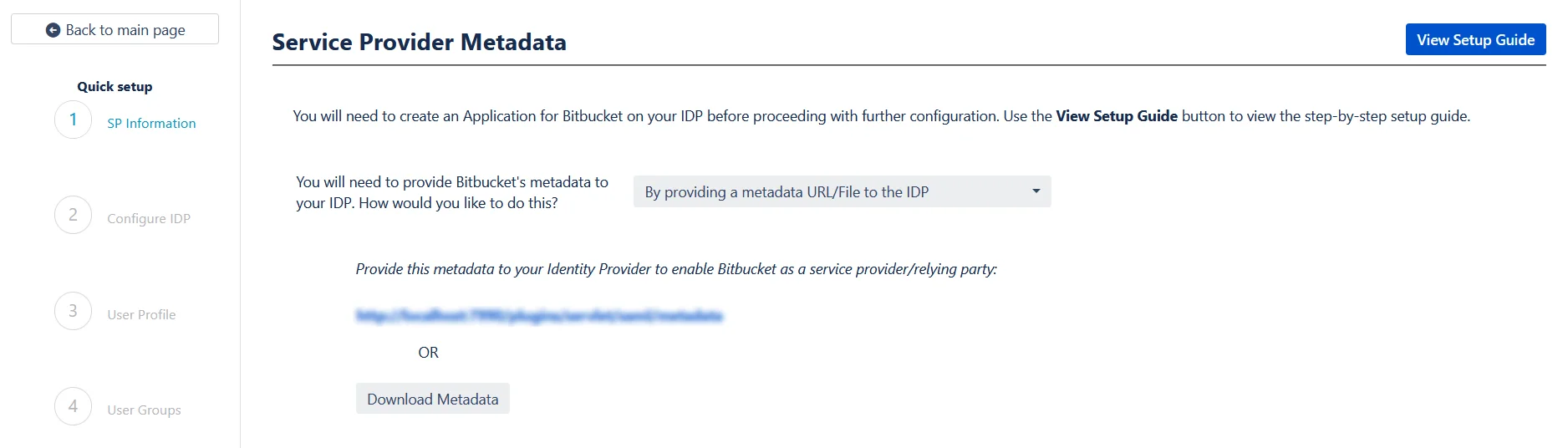
If you wish to add the metadata manually, then you can choose By manually configuring the metadata on your IDP You will find the following information. These details will need to be provided to your IDP
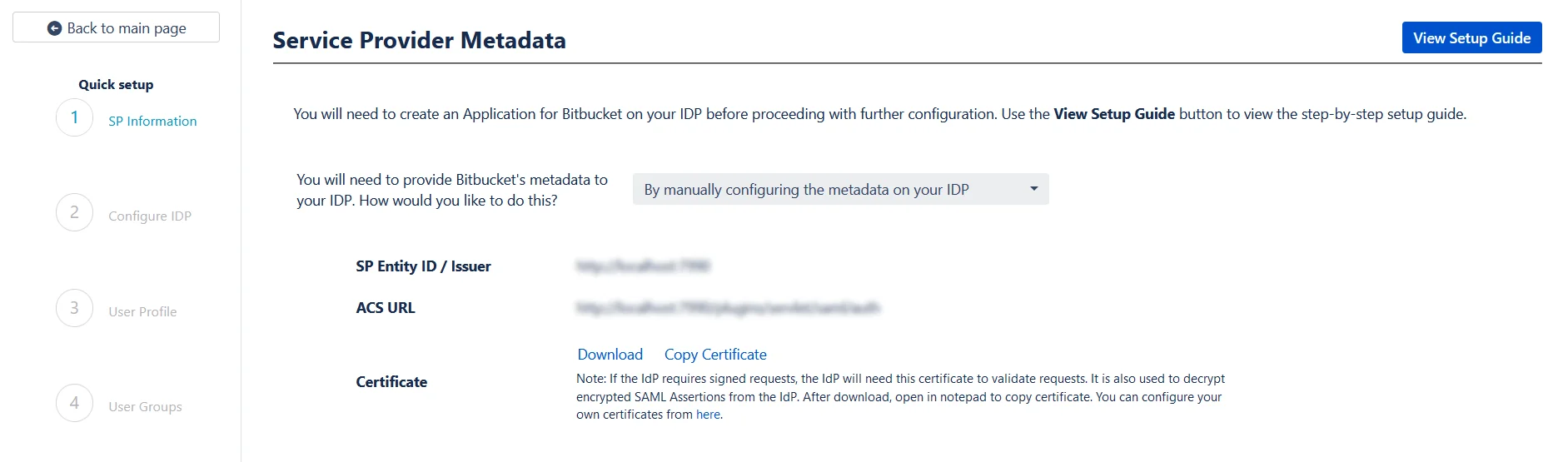
The next step of the Quick Setup flow deals with setting up IDP metadata on SP. We will pick this up in the next section of the setup guide.
If you have chosen to add your IDP using the Quick Setup flow then you have already completed the first step, which is to add SP metadata to your IDP. Now you can proceed with the second step of the Quick Setup method
 Configuring your Identity Provider
Configuring your Identity Provider
This step is where you will be adding your IDP metadata.
- Custom IDP name
- Adding the IDP metadata
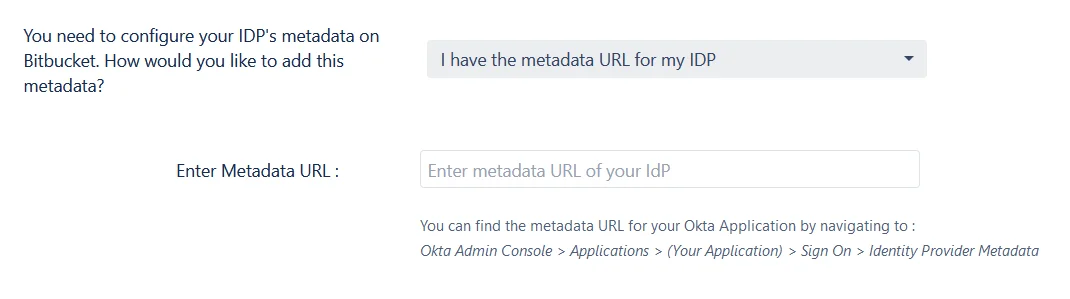
- I have the metadata URL for my IDP
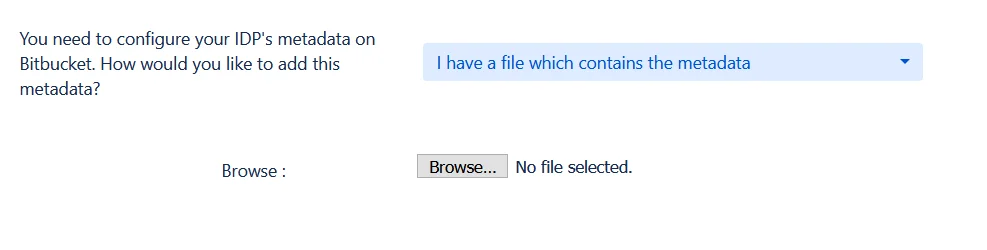
- I have a file which contains the metadata
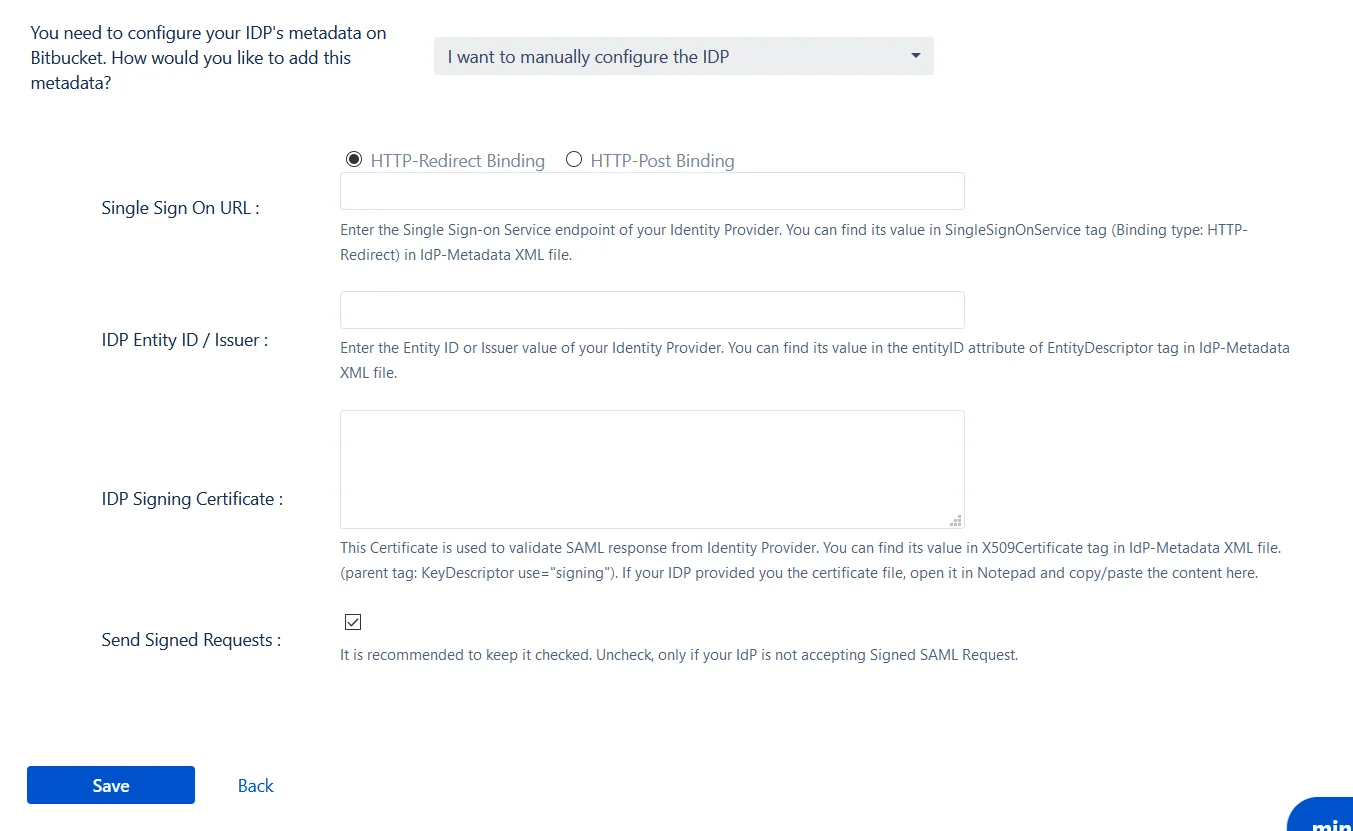
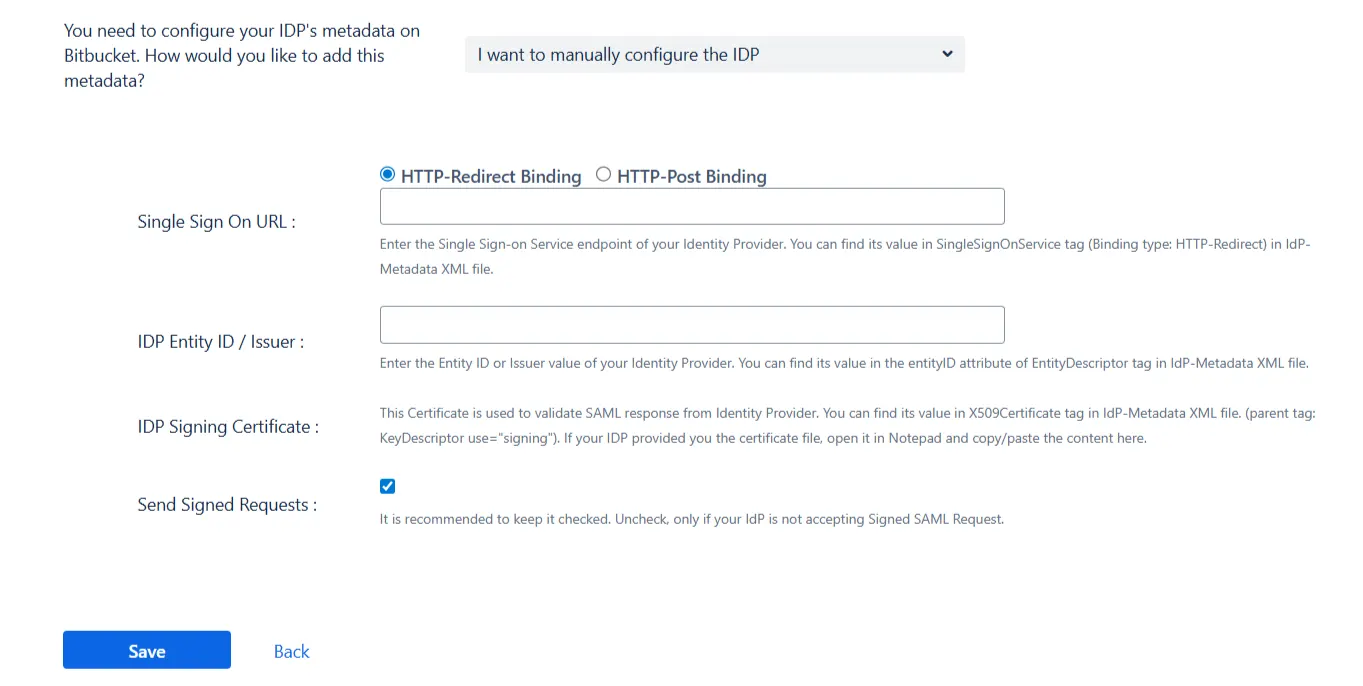
- I want to manually configure the IDP
- Single Sign On URL
- IDP Entity ID
- IDP Signing Certificate
- Testing the configuration
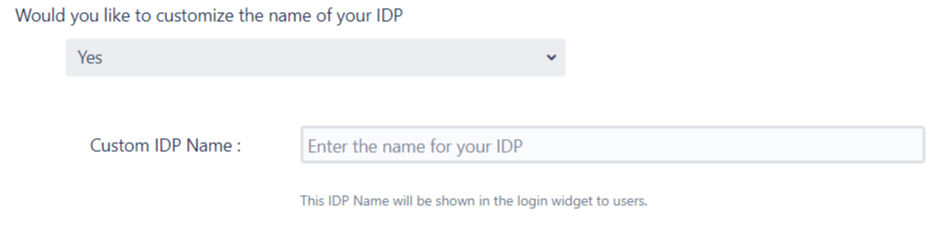
You can enter a name for your IDP int the Custom IDP Name field. In-case your use-case requires multiple IDPs, the SSO button for this IDP on the login page will display the custom name. If you do not wish to add a custom name, simply click on the corresponding drop-down and select no.
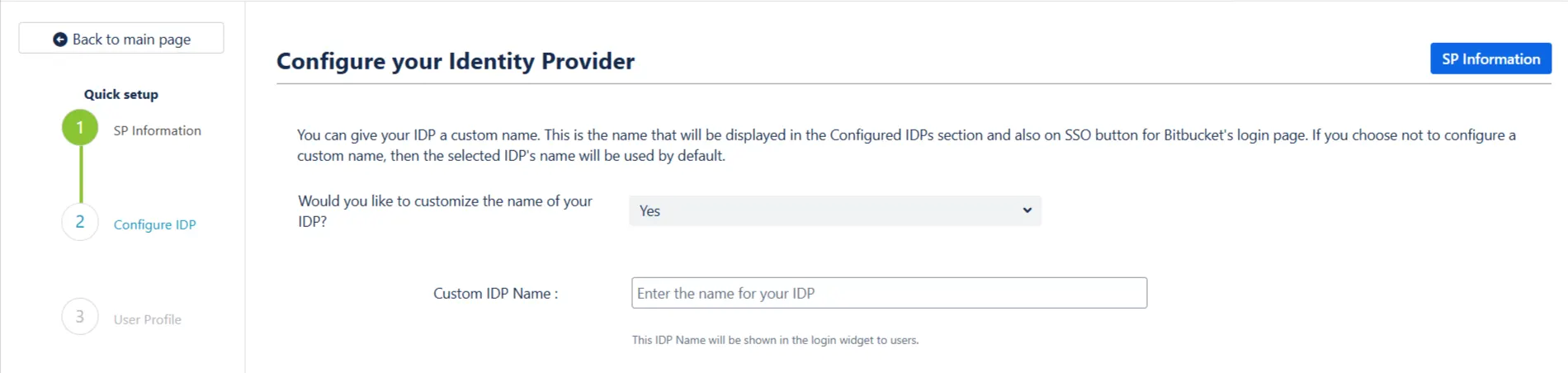
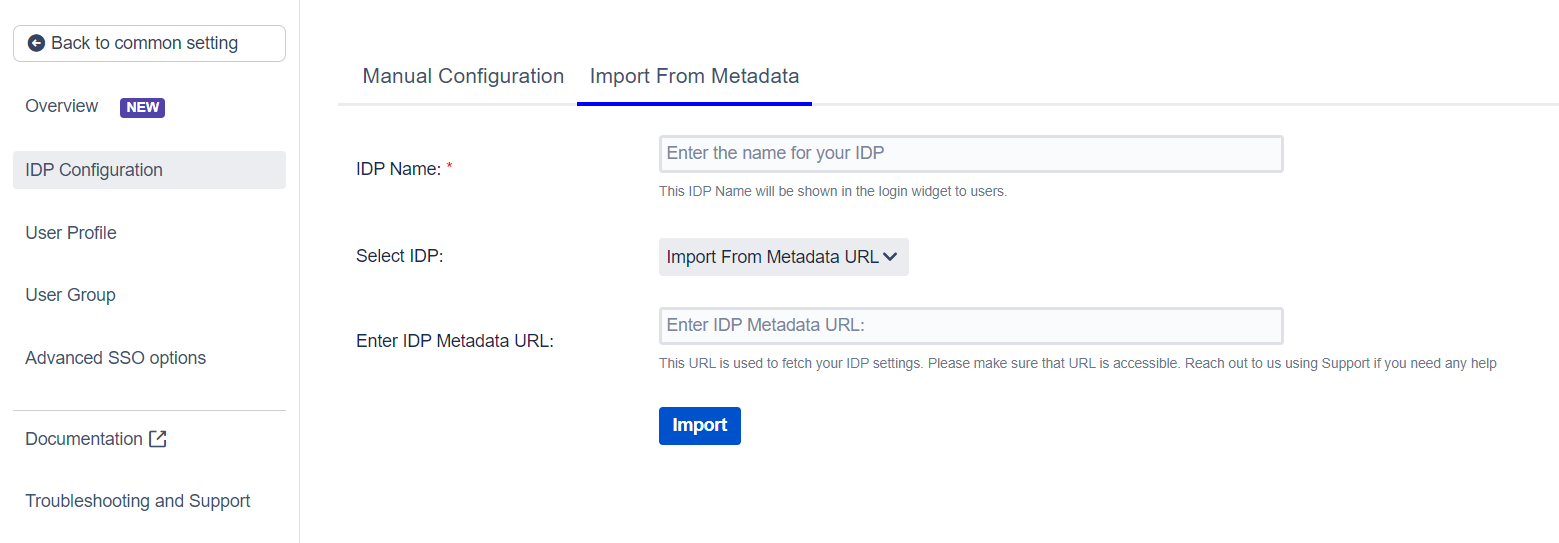
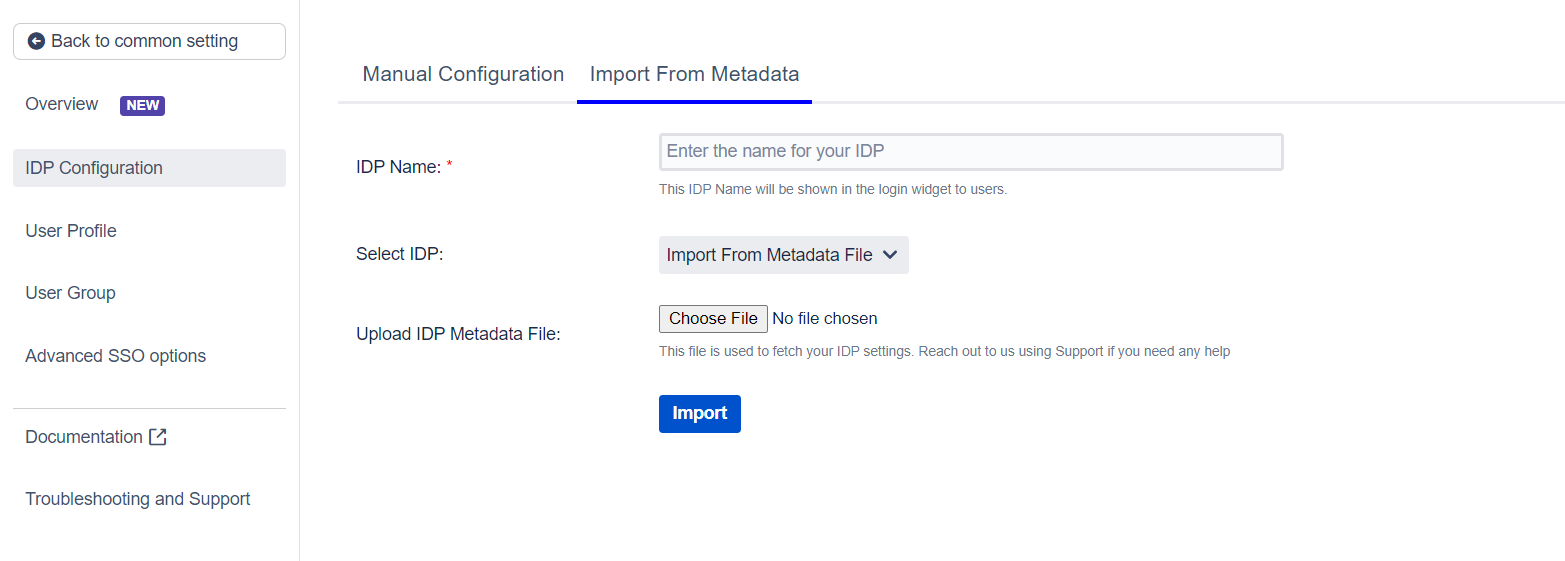
There are 3 ways in which you can add your IDP metadata. Use the drop-down to select any of the following methods :
Let’s look at the three options individually:
Add your metadata URL in the Enter Metadata URL field.
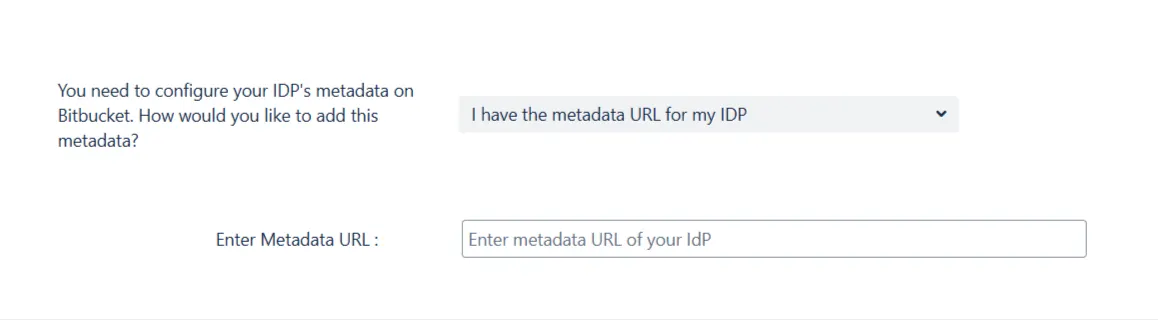
Use the Choose File button to browse for your metadata file.
To configure the IDP manually, you will need to have the following details from your IDP's metadata.
Once you have added the IDP metadata, click on Save. If the IDP has been added successfully, then you will see a Test and Get Attributes URL. Copt this Url and paste it in separate window to Get the Attributes from IDP.
 User Profile
User Profile
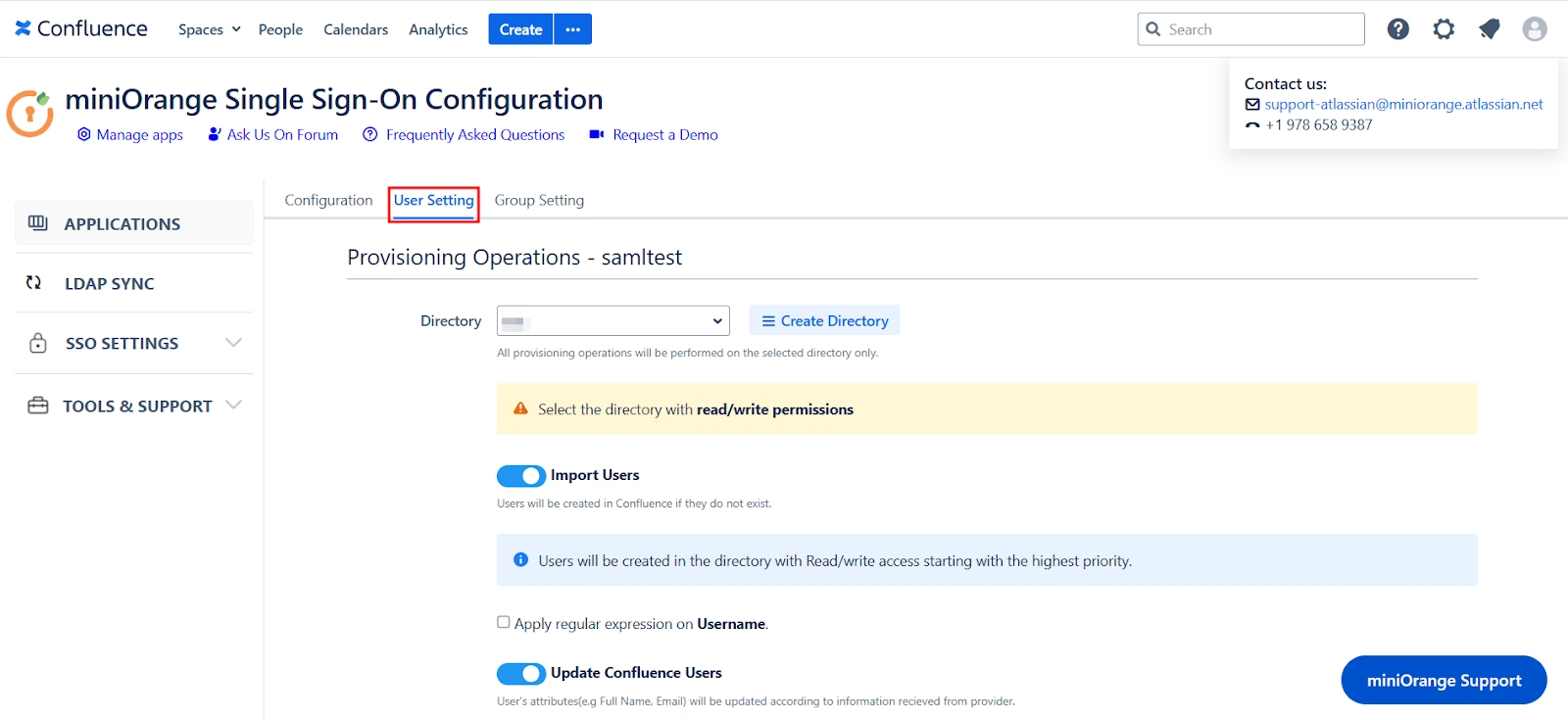
In this step you will be setting up basic user profile attributes for your SP
- Matching a user
- Setting profile attributes
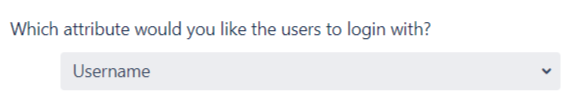
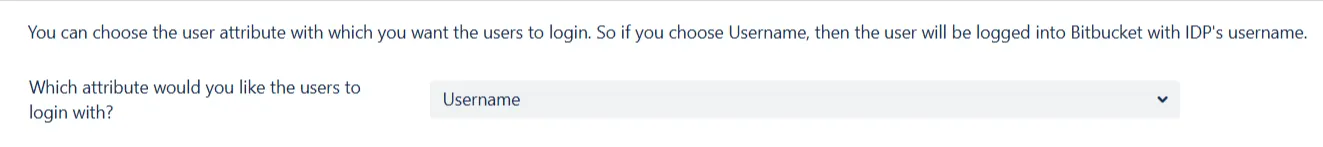
When the user logs into Atlassian Application, one of the user's data/attribute coming in from the IDP is used to search the user in Atlassian Application. This is used to detect the user in Atlassian Application and log in the user to the same account. You can choose which attribute will be used for this purpose using the drop-down provided.
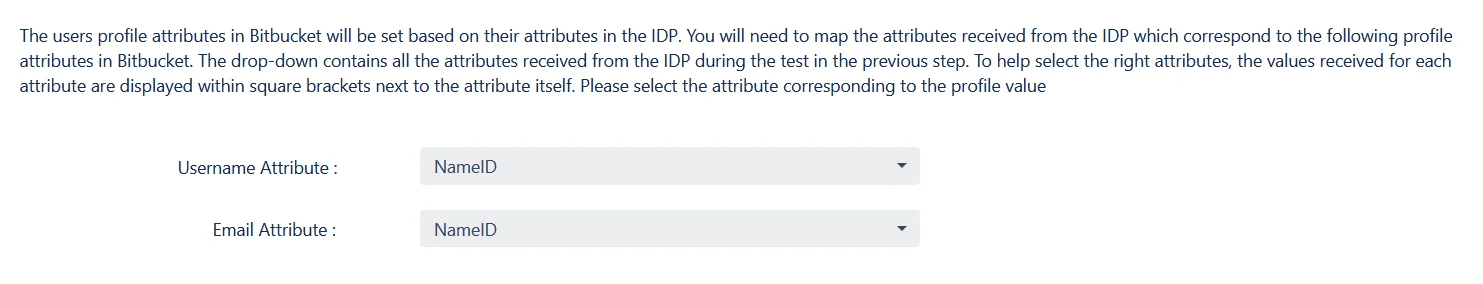
Setting up both Username and Email is required if you want to let users register. If the Test Configuration performed in the previous step was successful, then the inputs for the username and email attributes will be drop-downs. These drop-downs will contain all of the user's attribute names sent from the IDP. You will need to select the appropriate options containing the user's username and email.
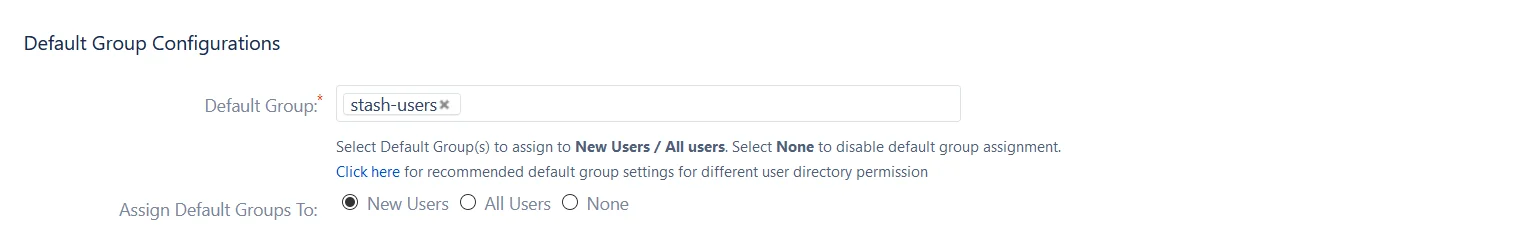
 User Groups - Default groups
User Groups - Default groups
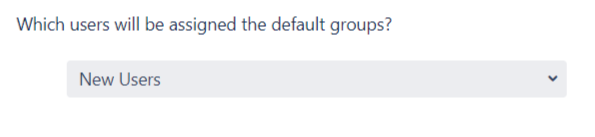
Select the users's default groups in this step. You can use the Default Groups to do this. Multiple groups can be set as default groups. The user will be assigned to these groups by default after successfully logging in via SSO.
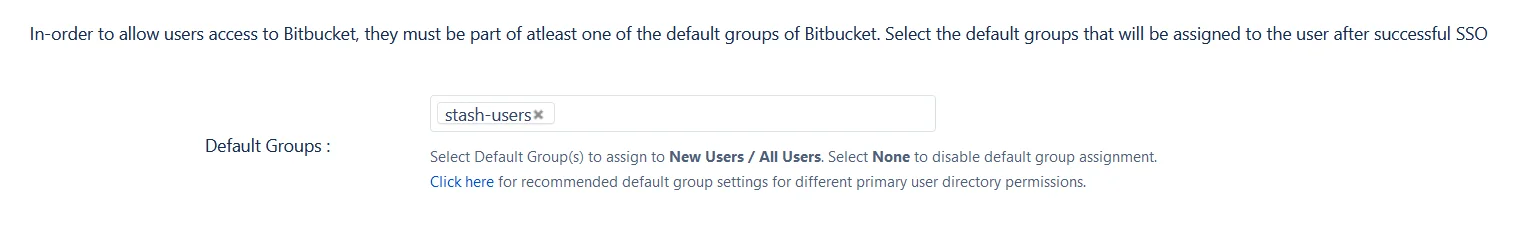
You can enable default groups for All Users or New Users using the Enable Default Groups for drop-down. Select None if you don't want to assign any default group to SSO users.
This concludes the Quick Setup flow. If you encountered any issues or errors while setting up your Identity Provider (IDP), refer to the Troubleshooting section for guidance or contact our support.
 Troubleshooting and Support
Troubleshooting and Support
- This step marks the end of the Quick Setup flow. In case you faced any issues or encountered any errors while setting up your IDP you can use the steps given in the Troubleshooting section to get in touch with us.
- You will also be able to see the results of a successful test configuration on this page. This includes the attributes received from your IDP, the SAML request sent and the SAML response received.
- Adding your IDP via this method will setup basic SSO for your end-users. You can always customise your setup further using the full set of features that we provide. To do this use the Edit drop-down for your IDP in the Configured IDPspage. From here you will be able to access your SP Metadata and customise your User Profile and User Groups settings. You can read more about these settings in the Custom Setup section of this guide.
For detailed information on customizing User Profile and User Groups settings, refer to the Custom Setup section of this guide.
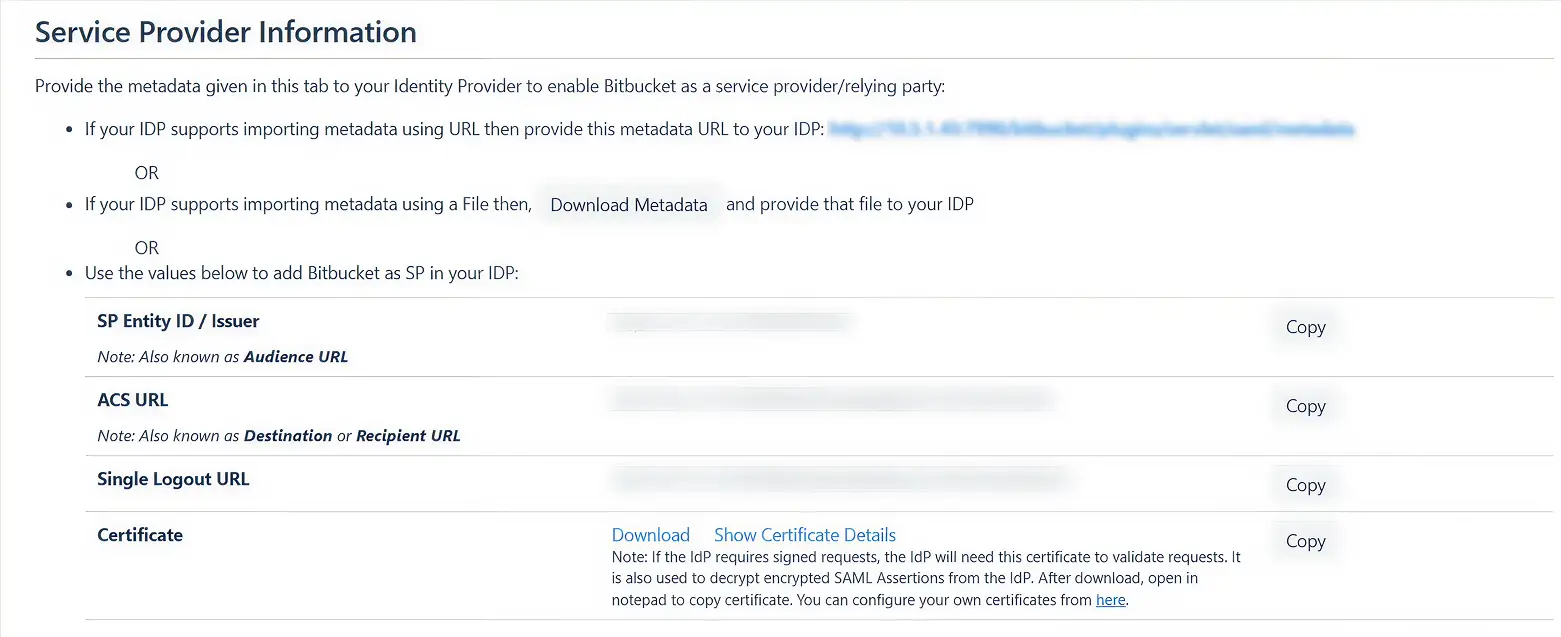
If you intend to customize your IDP setup from the start, you can find the required Service Provider (SP) metadata under the SP Metadata section. It contains essential information about your SP configuration that you will need to provide to your IDP for seamless integration.
There are multiple ways to add this metadata to your IDP:
 Service Provider Metadata
Service Provider Metadata
If you plan on customizing your IDP setup from the get go, you can find the metadata in the SP Metadata. Here you will find your SP's metadata. You will need to provide this metadata to your IDP. There are multiple ways to add this metadata to your IDP :
There are multiple ways to add this metadata to your IDP:
- Importing the metadata
- Manually adding the metadata
- SP Entity ID
- ACS URL
- SP Certificate
Depending on how your IDP accepts the metadata, you can either provide the metadata URL or you can use the Download Metadata button to download an XML file for the same.
If you wish to add the metadata manually,you will find the following information in this section. These details will need to be provided to your IDP.
 Configuring your Identity Provider
Configuring your Identity Provider
The custom setup flow allows you to dive into the complete set of configurations that we provide to add a SAML Identity Provider. The steps to configure an IDP using the Custom Setup option are :
The steps to configure an IDP using the Manual Setup option are:
- Adding IDP Metadata
- By Metadata URL
- Navigate to the Advanced SSO options from the menu on the left-hand side of the page.
- Enter your metadata URL in the Certificate Rollover field.
- Select the Refresh Certificate periodically option.
- Use the drop-down provided to set the interval for a periodic refresh.Select 5 minutes for the best results.
- By Uploading Metadata XML File
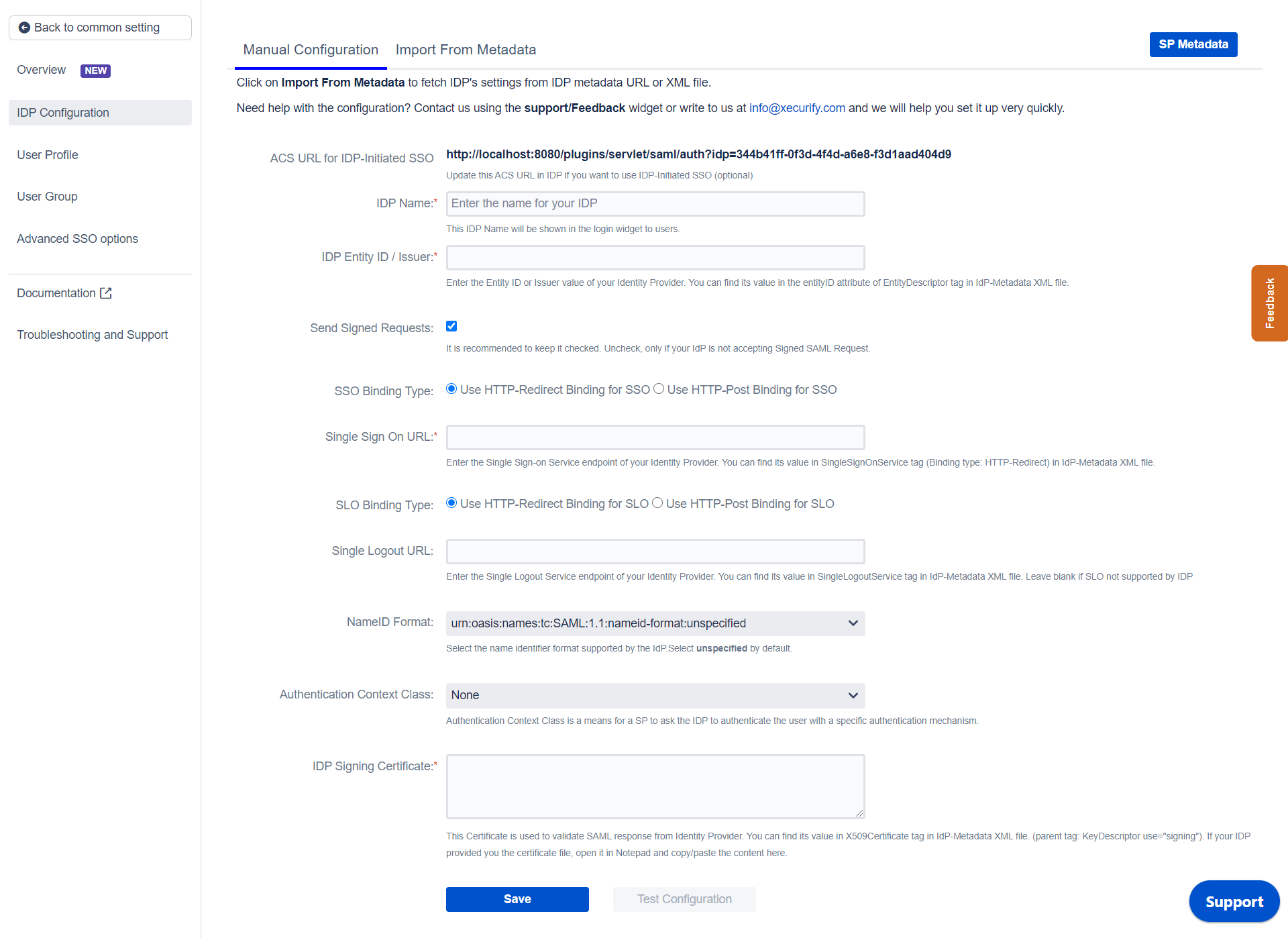
- Manual Configuration
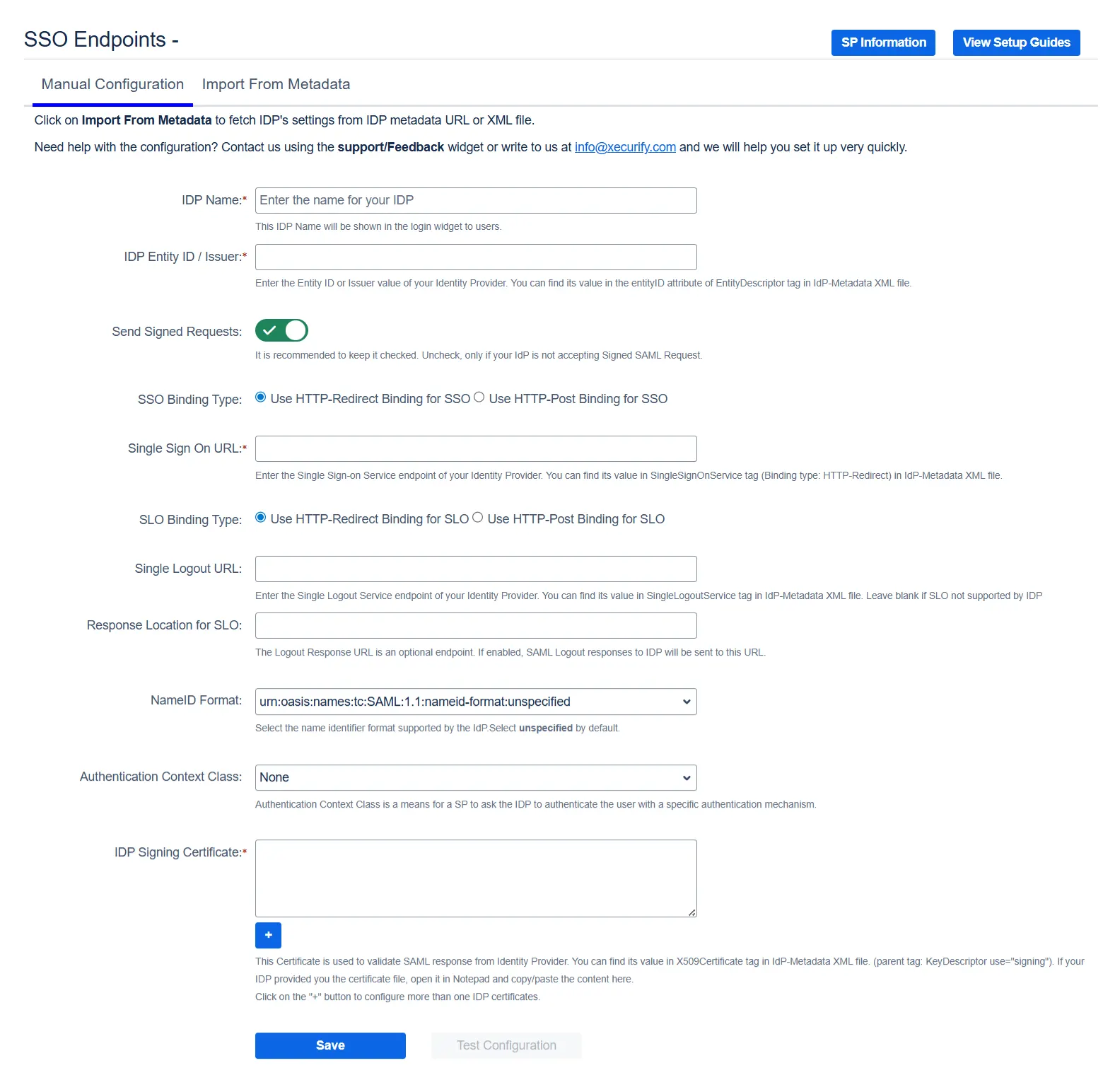
- IDP Entity ID.
- Single Sign On URL.
- Single Logout URL.
- X.509 Certificate.
With the information you have been given by Your IDP team, you can configure IDP settings in 3 ways:
1. Click on the Import from Metadata tab.
2. Select IDP: Import From Metadata URL.
3. Enter IDP metadata URL: Enter your metadata URL.
4. If your IDP changes certificates at intervals (Eg. Azure AD), you can refresh your IDP metadata accordingly :
5. Click Import.
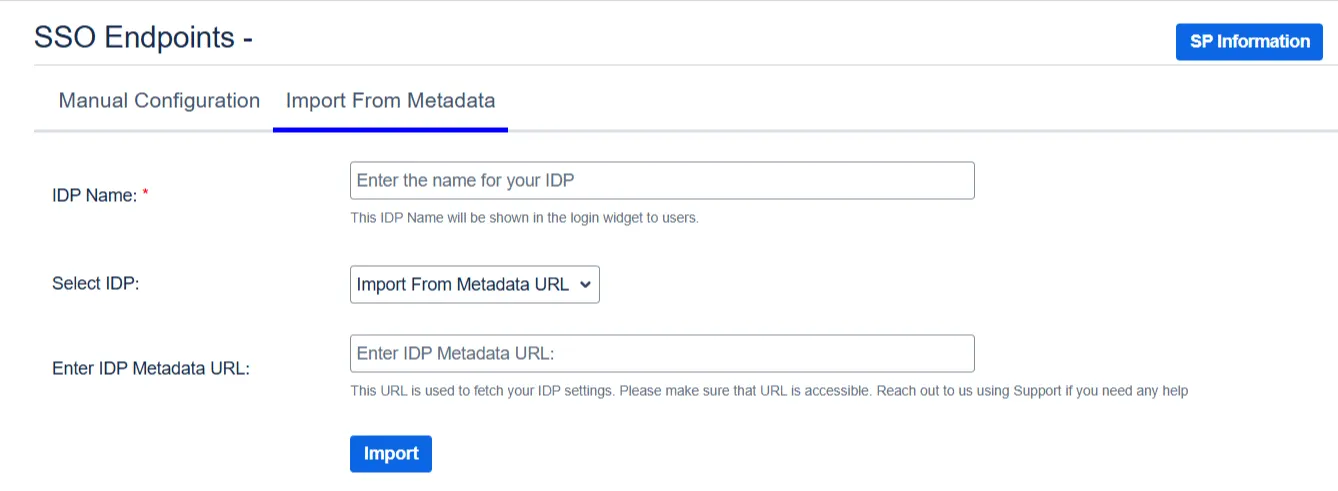
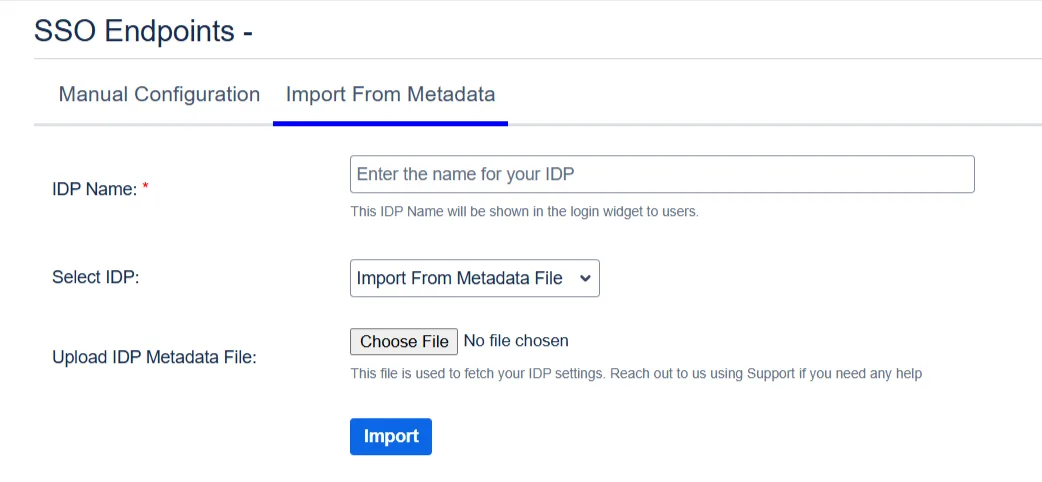
Click on the Import from Metadata tab.
Select IDP: Import from Metadata File.
Upload metadata file.
Click Import.
Go to Manual Configuration tab and enter the following details:
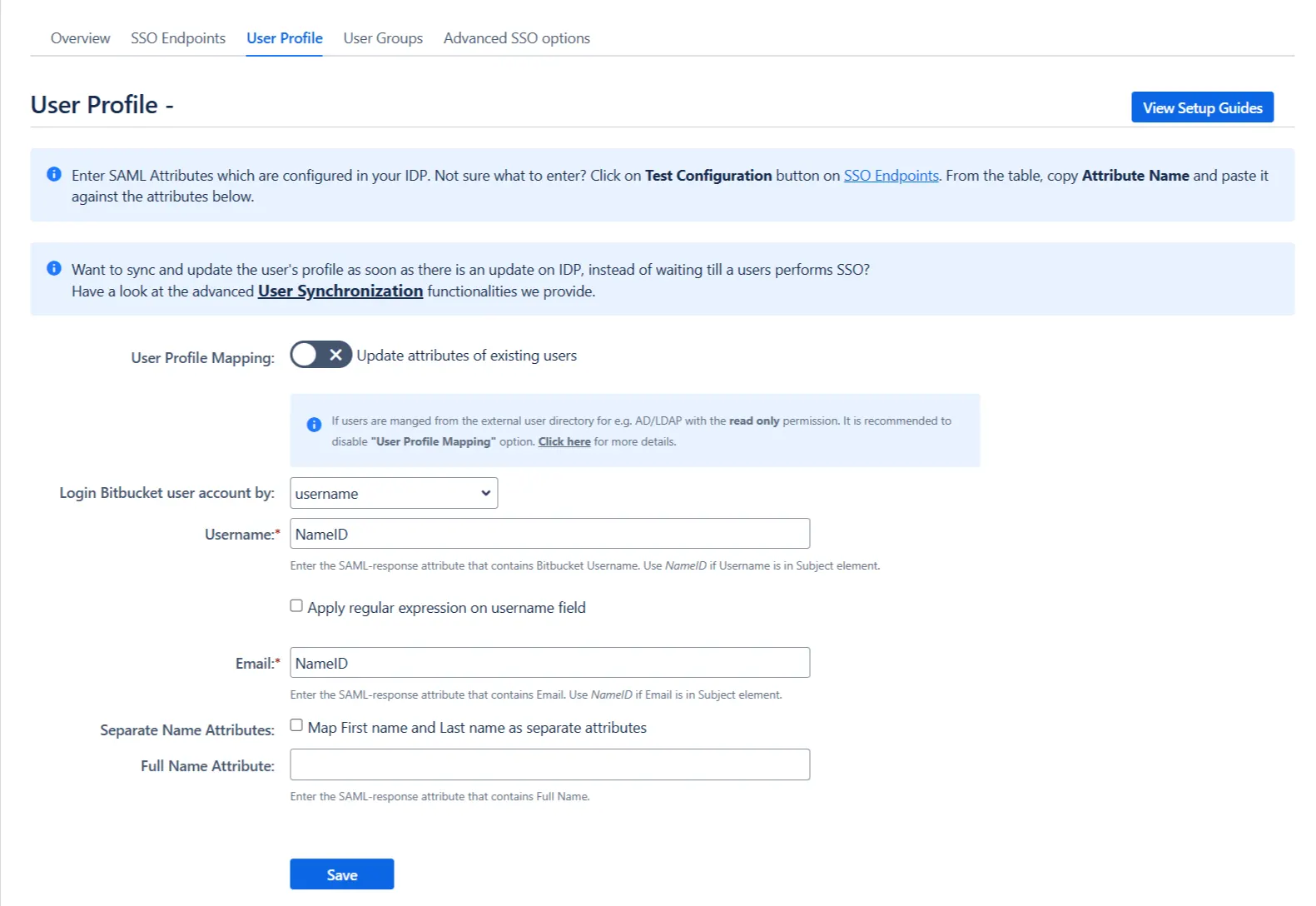
 User Profile
User Profile
Next we will be setting up user profile attributes for Atlassian Application. The settings for this can be found in the User Profile section.
- Finding correct attributes
- Setting profile attributes
- Matching a user
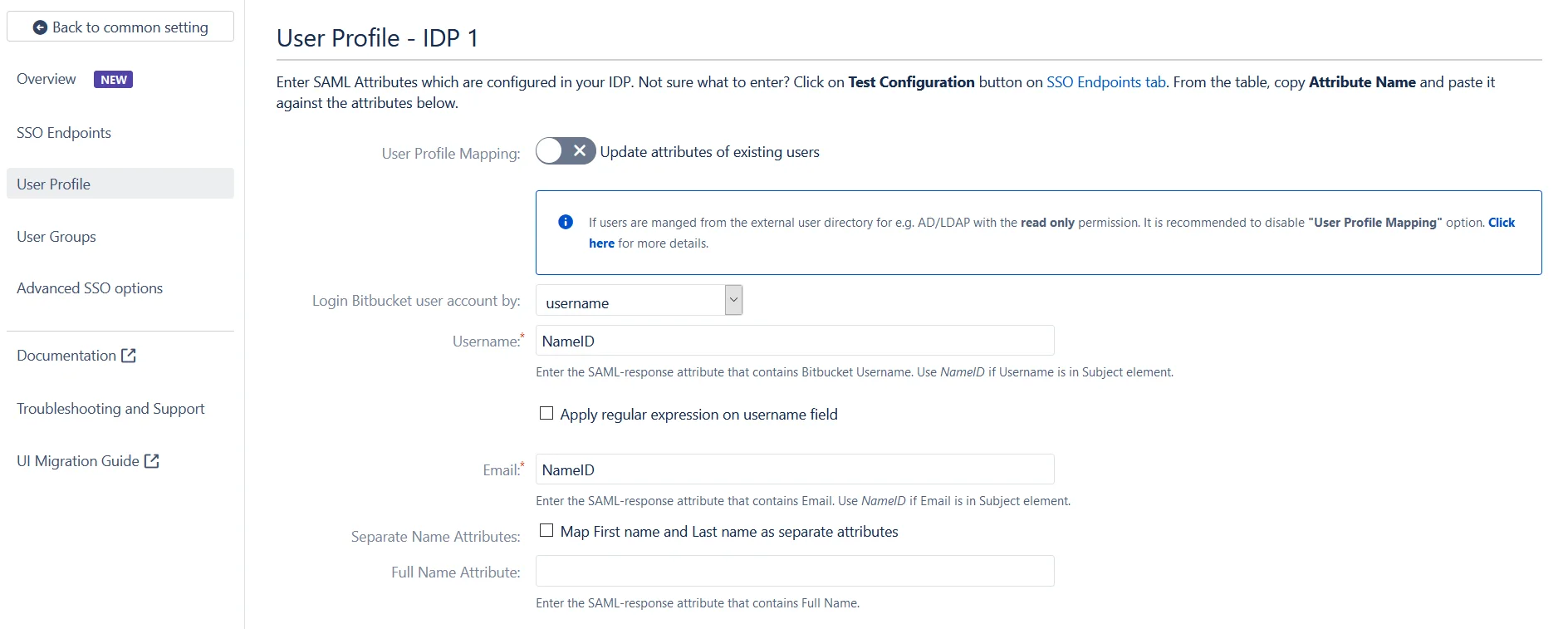
- Select Username or Email for Login user account by
- Enter the attribute name from IDP which corresponds to Username or Email using Finding Correct Attributes
Go to the IDP Configuration section. Scroll down and click on Test Configuration.
You will see all the values returned by your IDP to Atlassian Application in a table. If you don't see value for First Name,Last Name, Email or Username, make the required settings in your IDP to return this information.
Once you see all the values in Test Configuration, keep the window open and go back to the User Profile section.
In this tab, fill the values by matching the name of the attribute. For instance, if the Attribute Name in the Test Configuration window is NameID, enter NameID against Username
Setting up both Username and Email is required if you want to let users register. If you want existing users to only login, configure the attribute using which you will match the user in Atlassian Application.
When the user logs into Atlassian Application, one of the user's data/attribute coming in from the IDP is used to search the user in Atlassian Application. This is used to detect the user in Atlassian Application and log in the user to the same account.
You can configure it using steps given below:
 User Groups
User Groups
Now we will be setting up user group attributes for Atlassian Application. You can replicate your user's groups present on IDP in your SP. There are multiple ways of doing this.
You can accomplish this in the following ways:
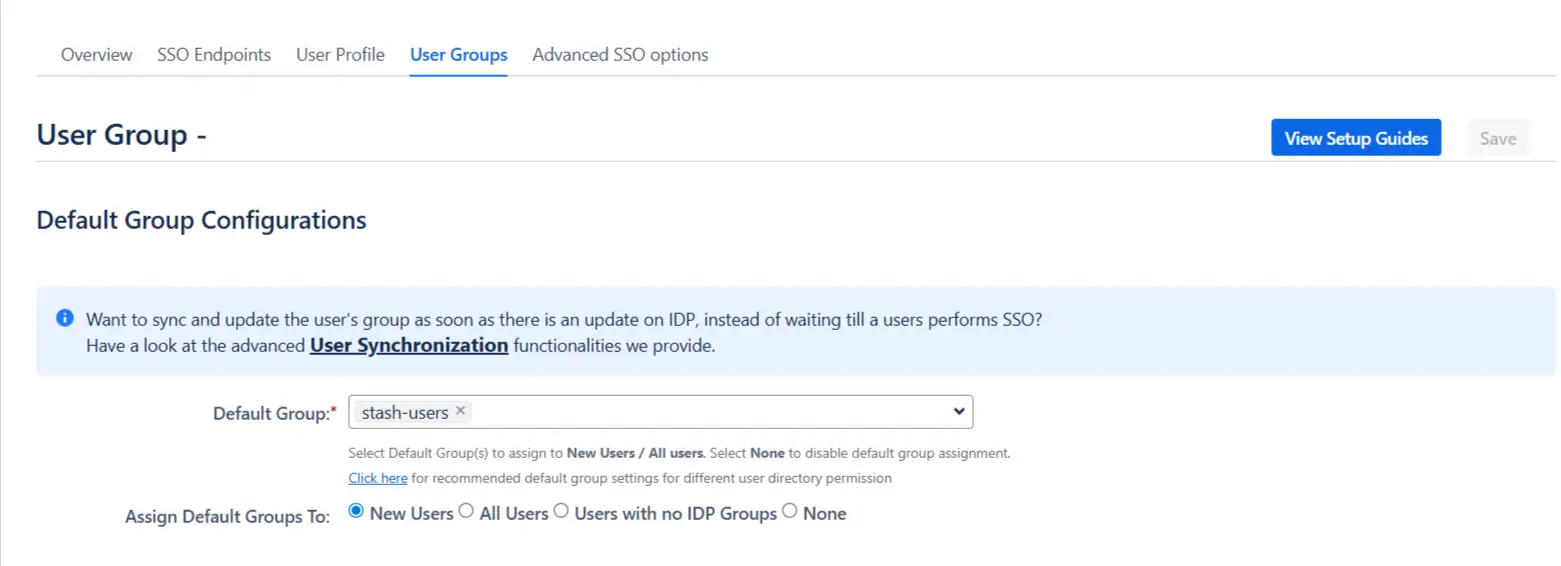
- Setting default group
- Select the users' Default Group in the tab User Groups. If no group is mapped, users are added by default to this group.
- You can enable default groups for All Users or New Users using the option.Select None if you don't want to assign any default group to SSO users. Using the option Enable Default Groups for.
- Finding Group Attribute
- Just like we found Attribute Name for User Profile attributes, we find the group attribute.
- Go to IDP Configuration section. Scroll down and click on Test Configuration.
- You will see all the values returned by your IDP to Atlassian Application in a table. If you don't see value with groups, make the required settings in your IDP to return group names.
- Once you see all the values in Test Configuration, keep the window open and go to User Groups tab.
- Enter the Attribute Name of group against Group Attribute.
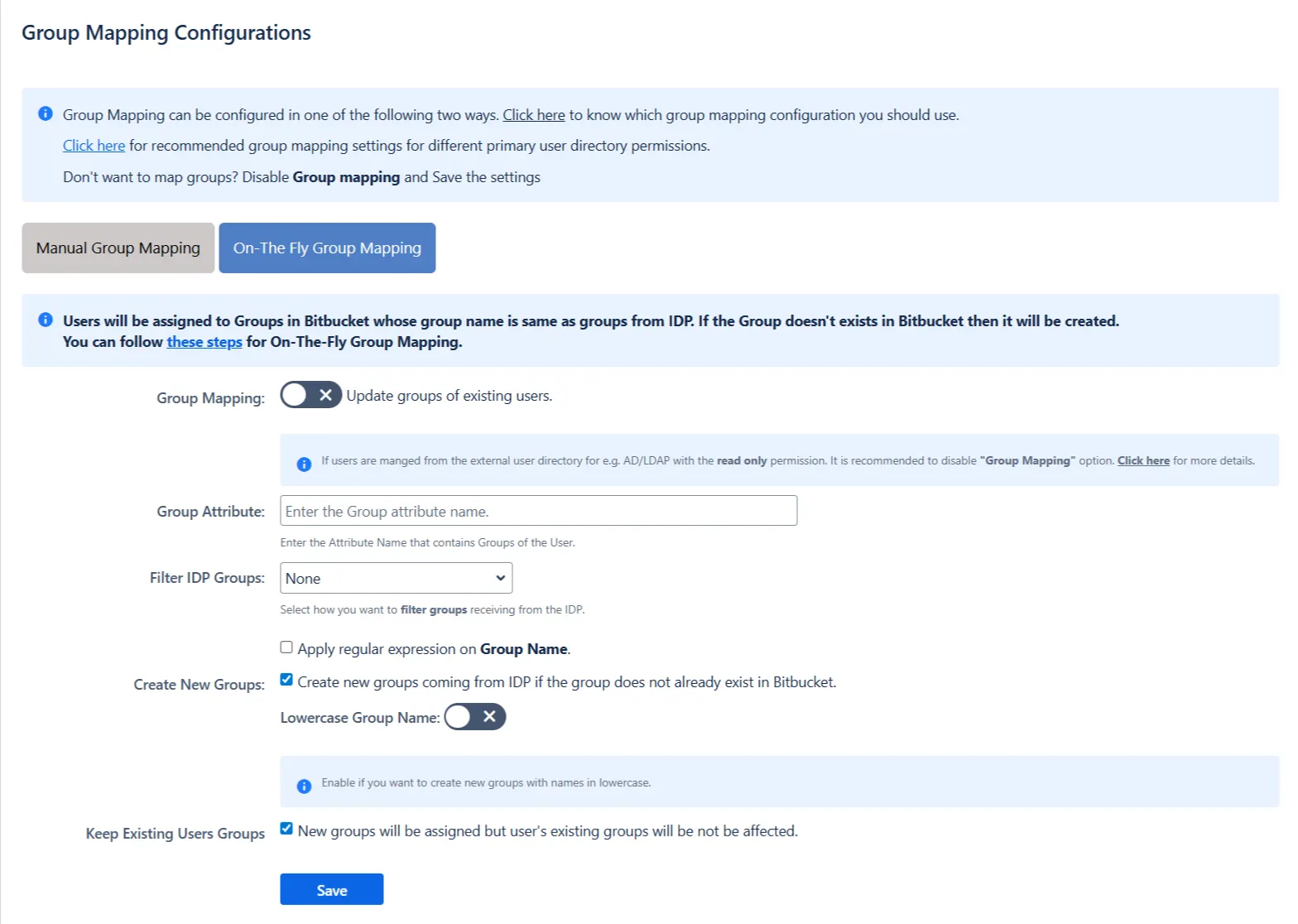
- Check Disable Group Mapping option if you don't want to update groups of existing users.
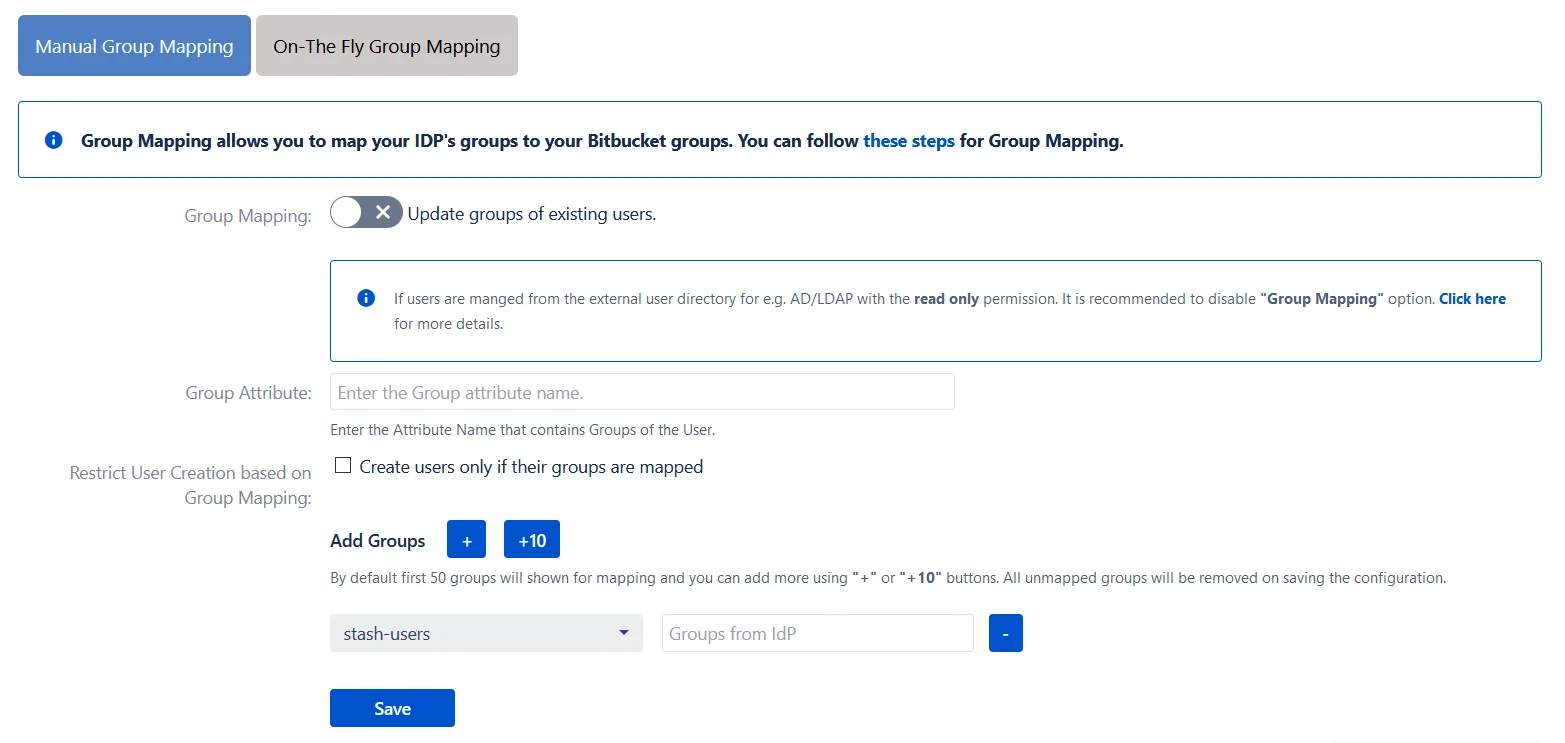
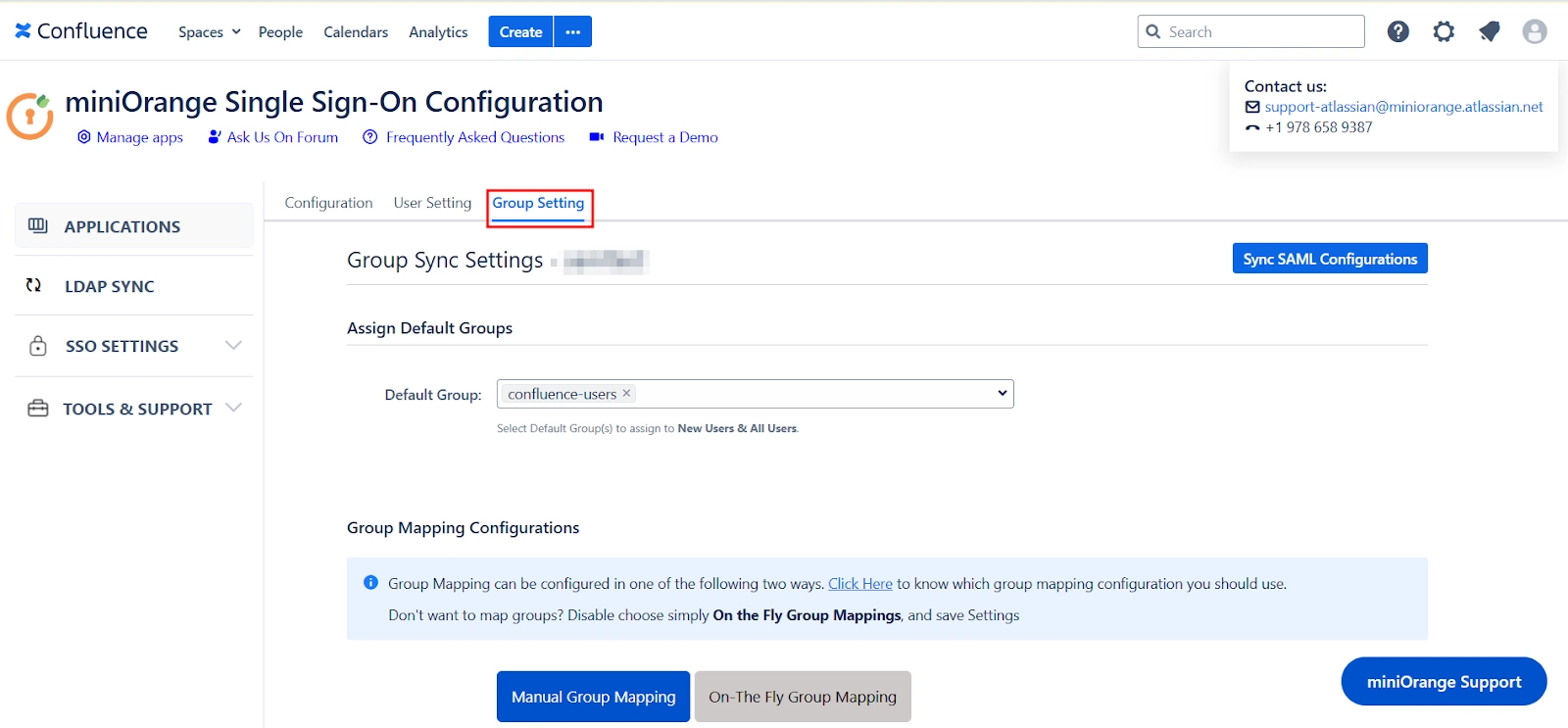
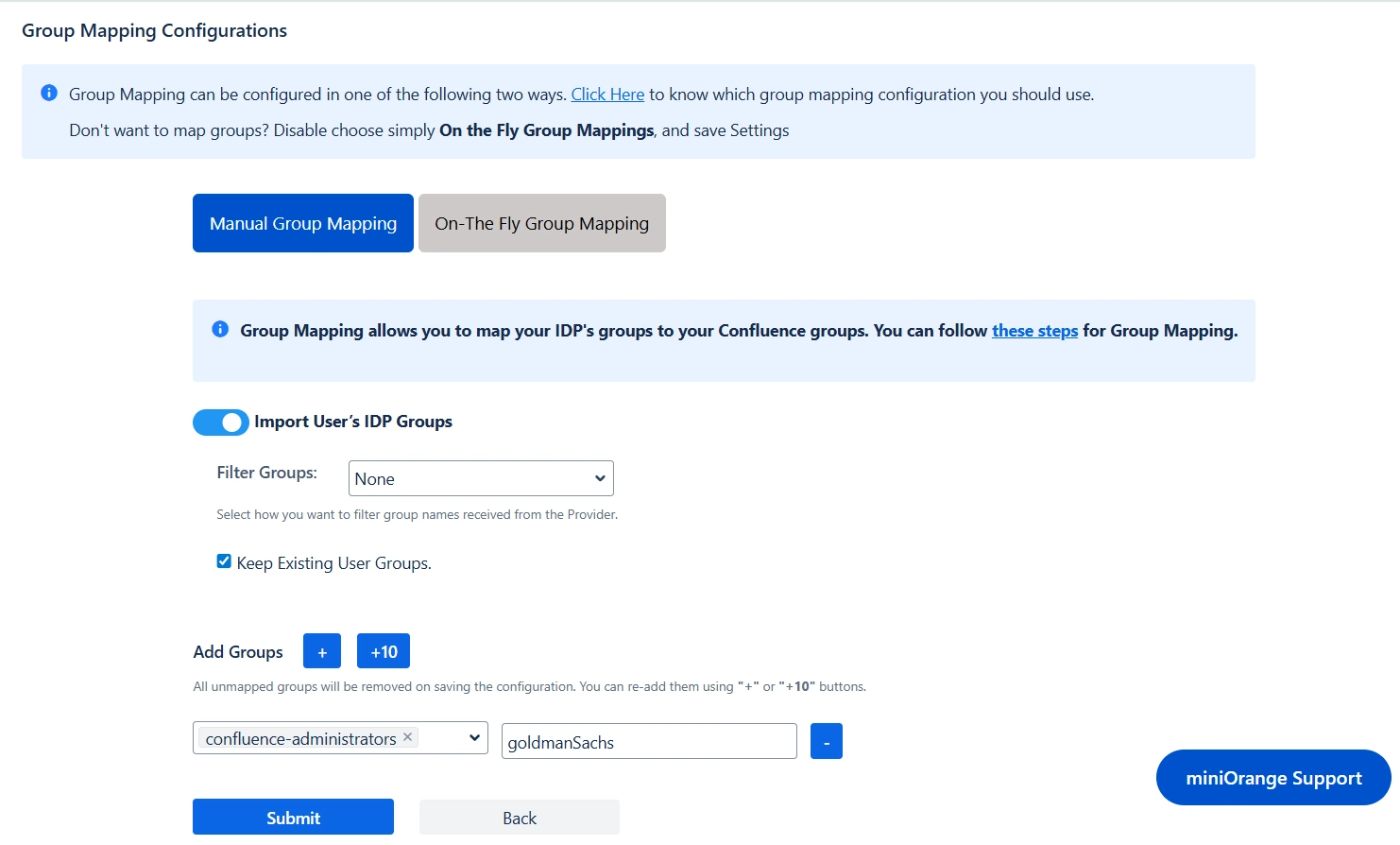
- Group Mapping
- Manual Group Mapping
- Check Restrict User Creation Based on Group Mapping option if you want new users to be created only if at least one of the user's IDP groups is mapped to a group in the application.
- For mapping, first select a Atlassian Application group from the dropdown which lists all groups present in that application and then enter the name of the IDP group to be mapped in the textbox beside.
- For example, if you want all users in 'dev' group in IDP to be added to software-users, you will need to select software-users from the dropdown and enter 'dev' against software-users.
- Use '+1' and '+10' buttons to add extra mapping fields.
- Use '-' button next to each mapping to delete that mapping.
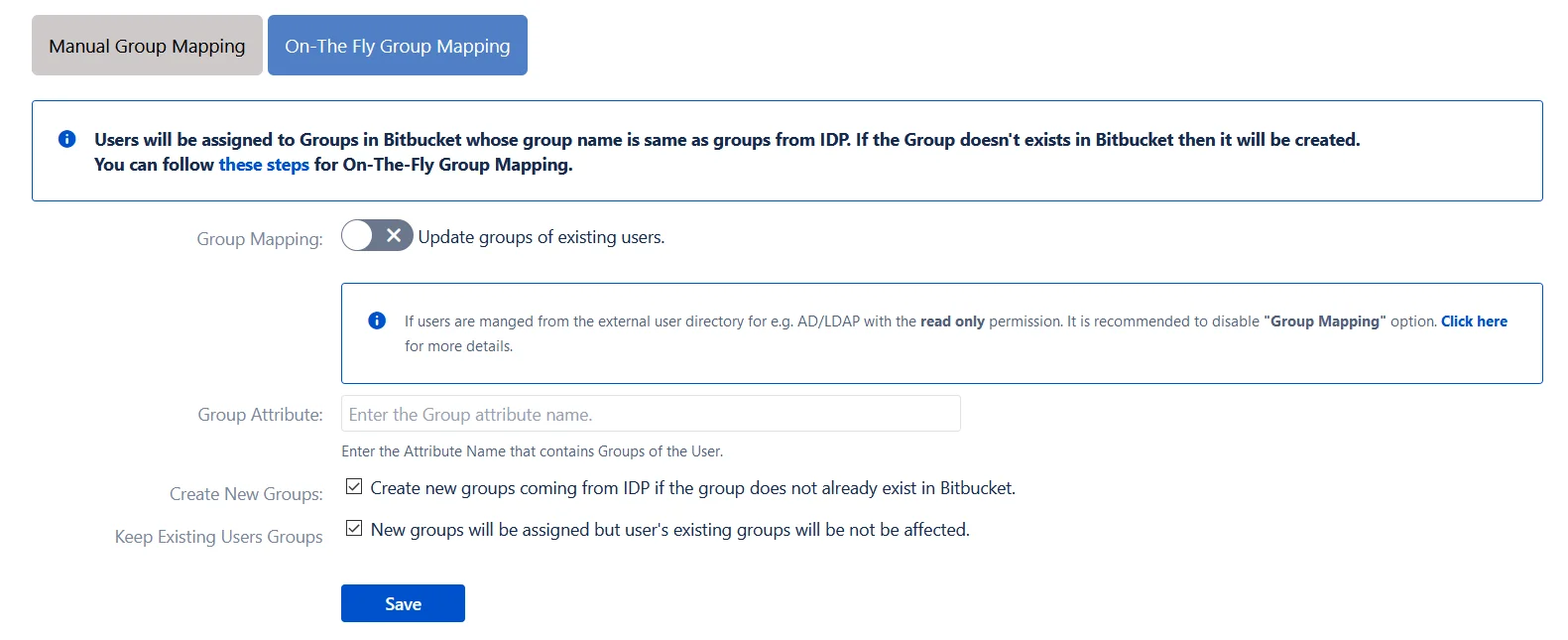
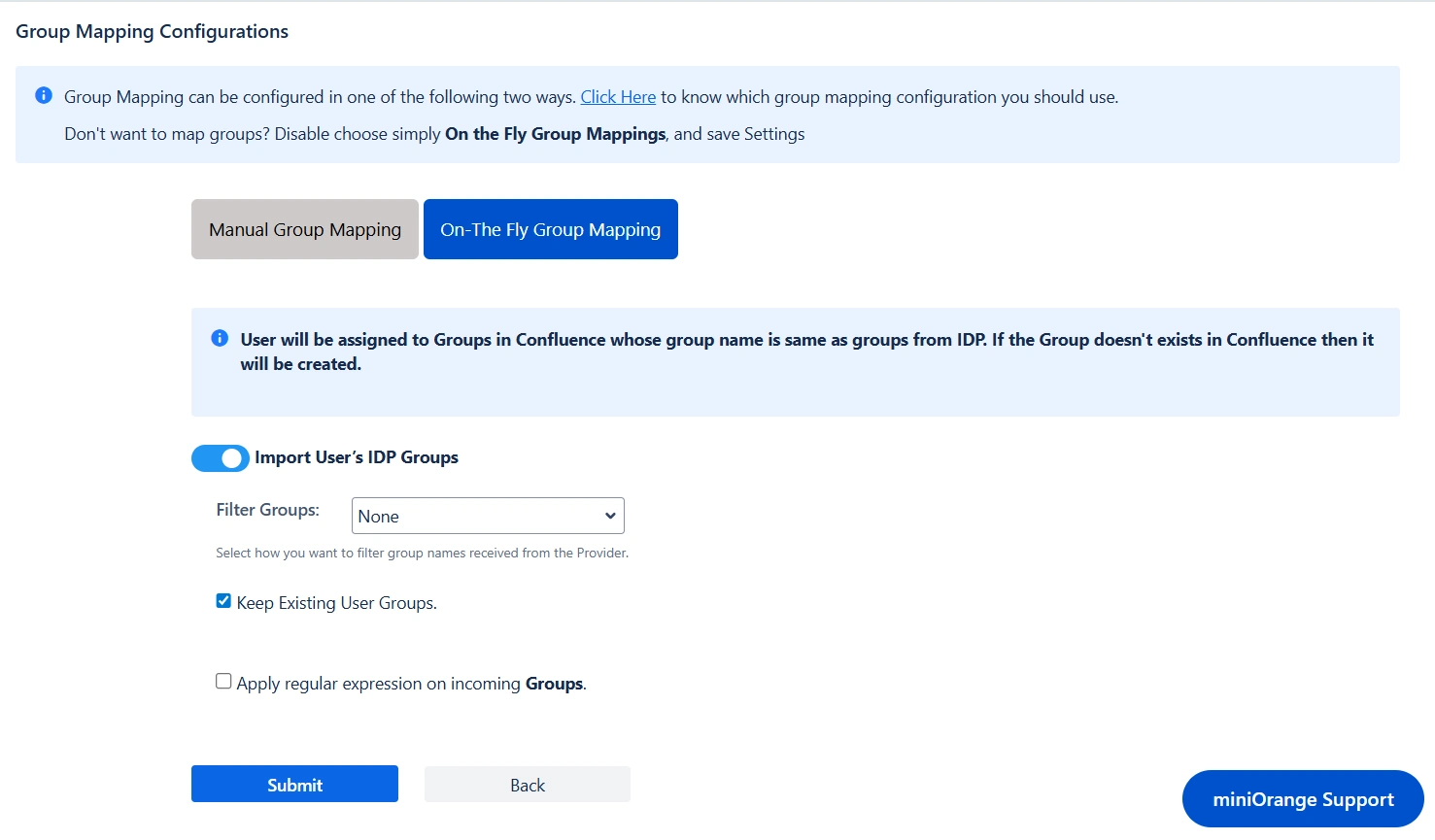
- On-The-Fly Group Mapping
- Check Create New Groups option if you want new groups from IDP to be created if not found in Atlassian Application.
- If the user is part of some group in Atlassian Application and that group is not present in the SAML response returned by IDP, then the user will be removed from that group in Atlassian Application.
- If you don't want On-The-Fly group mapping to affect Atlassian Application's groups which are managed locally then add those groups in Exclude Groups field.
Group Mapping can be done in two ways:

 Troubleshooting and Support
Troubleshooting and Support
Step 3: Redirection on Login Page
- If you have only one IDP configured, then you can use the features provided on the SSO Settings tab and Redirection tab of the plugin to manage the redirection on the login page.
- Enable the Auto Redirect to IDP option on the SSO Settings tab if you want to allow users to log in only using IDP.
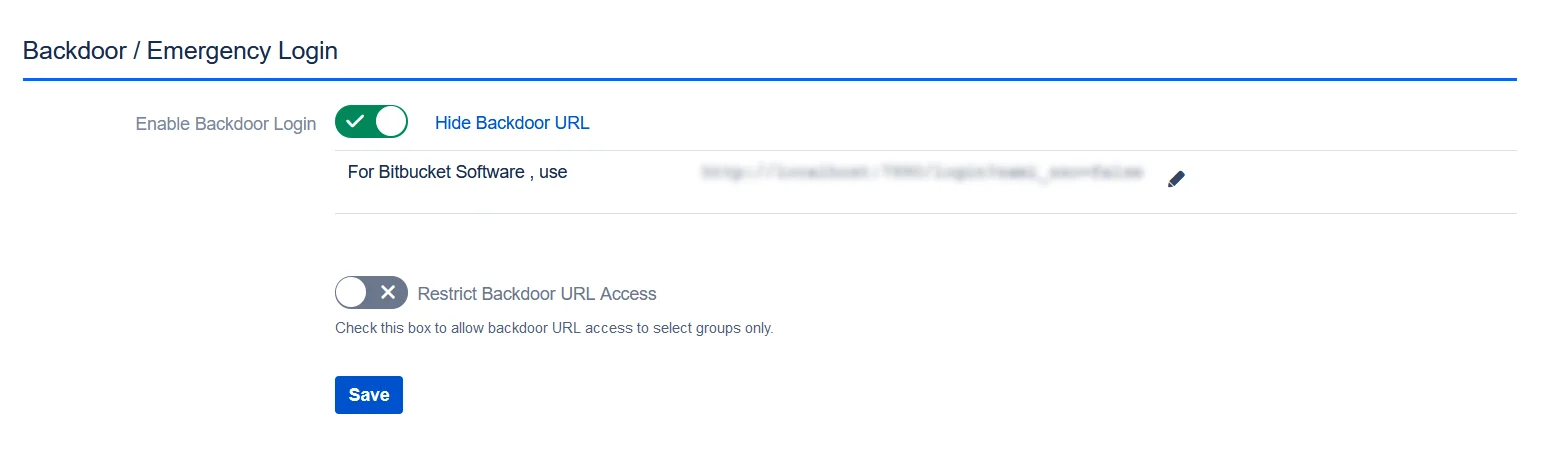
- Use the Emergency/Backdoor Login URL to allow all admins to access the Atlassian Application's default login page and log in using Atlassian Application's local credentials. You can also Restrict the access of this URL to some specific set of users (i.e users of particular groups).
- Use the settings given on Redirection Rules tab to redirect the users on login page based on their email domains, groups and directories. This feature is more useful in case you have multiple IDPs configured. Please refer to the next section.
Step 4: Multiple IDPs
Our plugin offers the flexibility to configure multiple identity providers (IDPs) on your service provider (SP), expanding your options for authentication.
 4.1 Configuring Multiple IDPs
4.1 Configuring Multiple IDPs
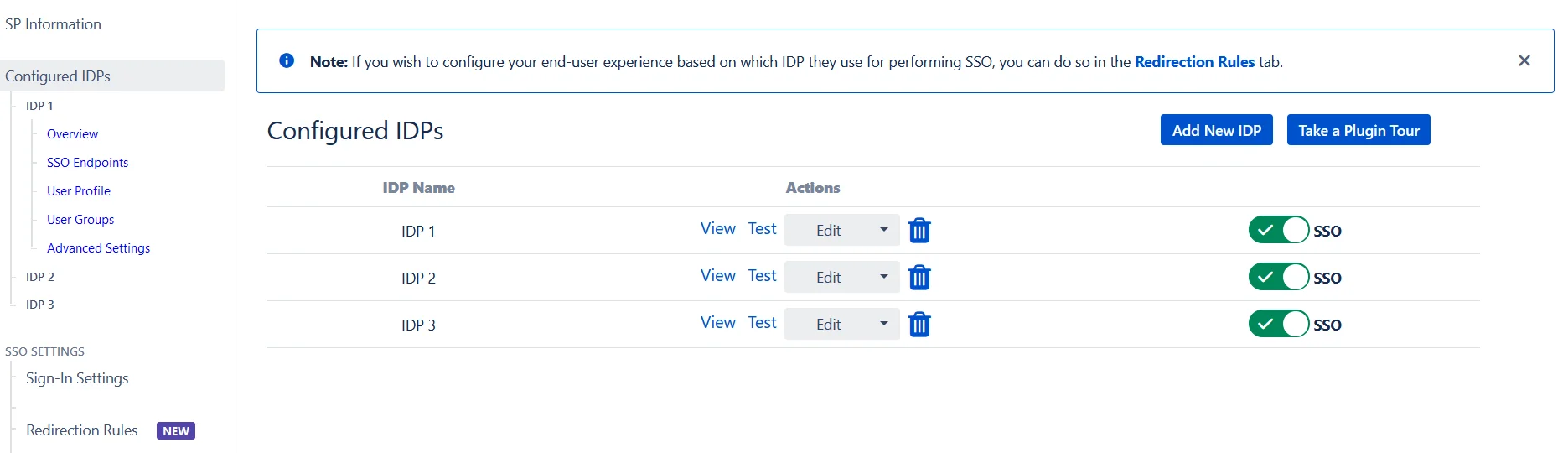
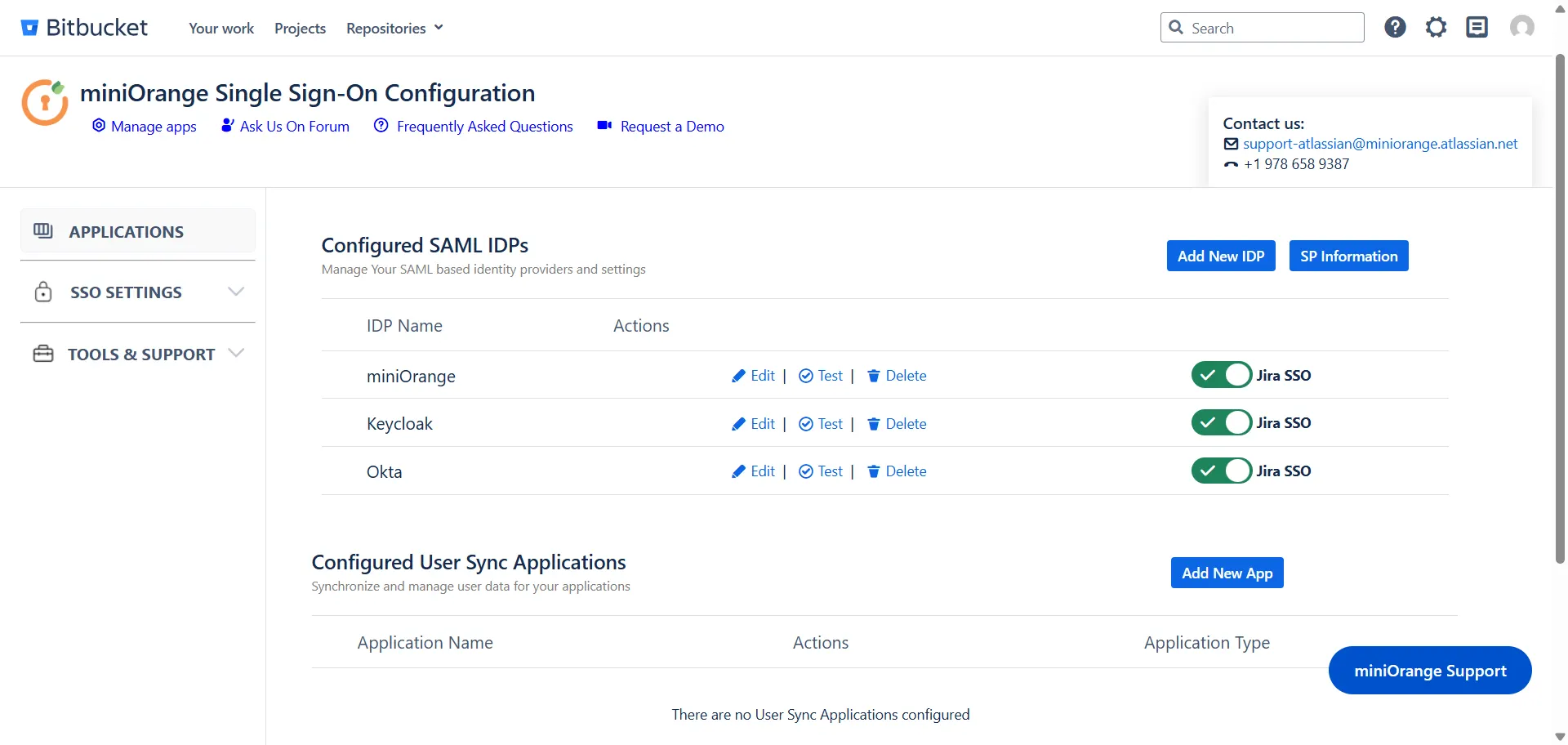
- If your use case requires multiple IDPs to be configured on your SP, the plugin supports that as well. You can add another IDP by going to the Configured IDPs section and using the Add New IDP button.
 4.2 Managing SSO with Multiple IDPs
4.2 Managing SSO with Multiple IDPs
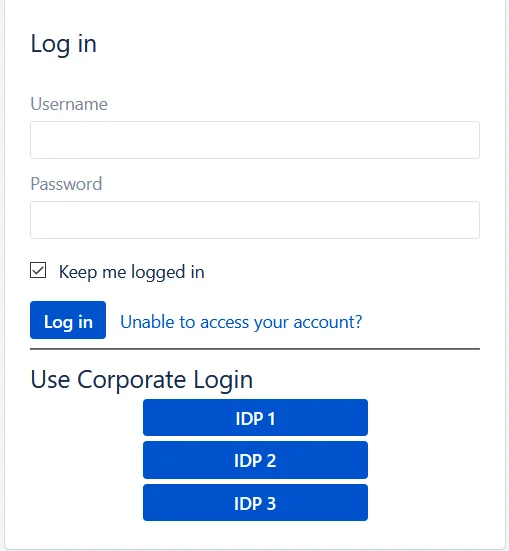
- If you have multiple IDPs configured, you can choose how you want your end users to use these IDPs to perform SSO. IDPs to perform SSO.
- For example you can show the buttons for the different IDPs configured on the login page nad let the users decide which IDP to use for SSO.
- Or you could force certain users to user a specific IDP based on the domain of their username/email.
- You will be able to configure these rules in the Redirection Rules section, under the Redirection Rules tab.
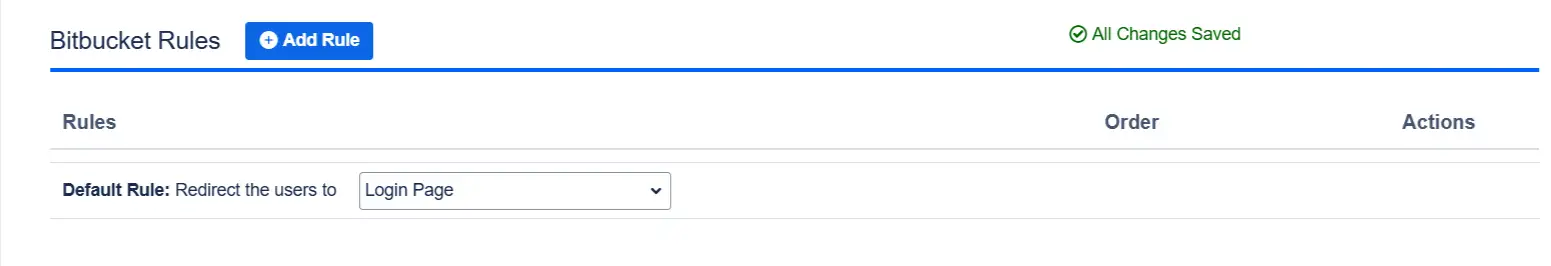
- By default one rule is always configured that will be applicable to all the users, irrespective of their user domains.
- For instance, if you want to display the login page with SSO buttons for each of the IDPs then your Default Rule will be as follows :
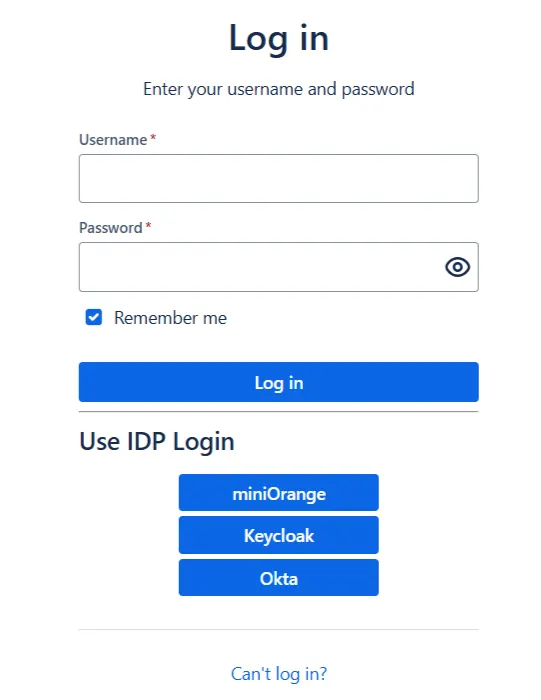
- Based on the default rule mentioned above, the login form will contain buttons for each IDP. The users will be free to choose whichever IDP they want to use to initiate SSO.
- You can also configure a rule so that your users will automatically be redirected to an IDP based on their email domains.
-
For example, if you want users with miniorange.com as domain to
be redirected to
miniOrange
you can add a rule by :
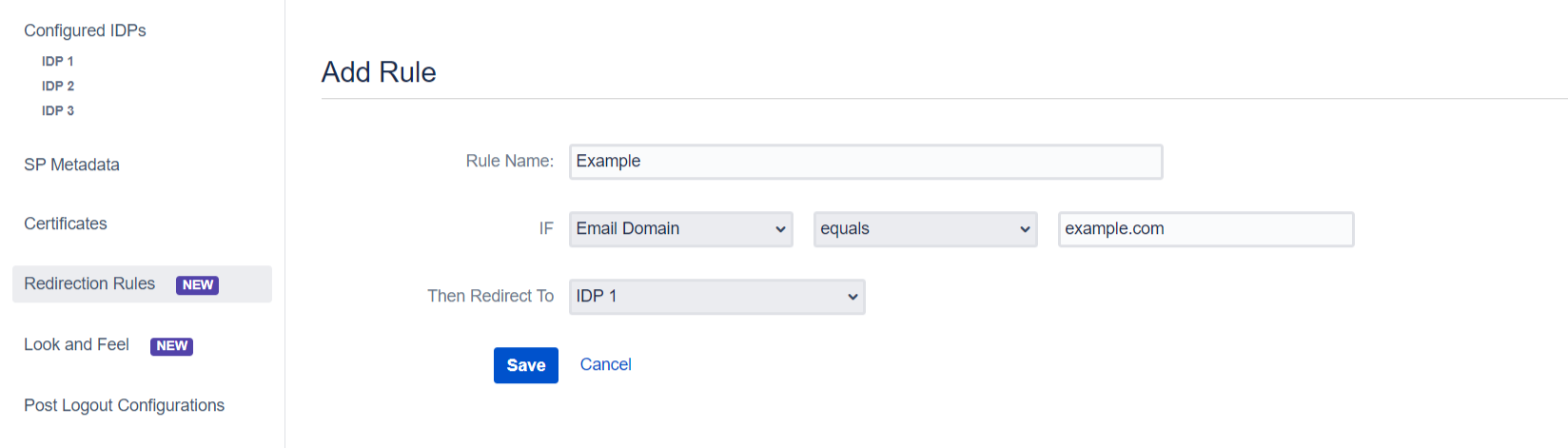
- Click on the Add Rule button in the Redirection Rules tab
- Enter a name for your rule in Rule Name
- In the IF statement select Email Domain in the first drop-down
- For the same statement select equals in the second drop-down.
- In the last field of the IF statement, enter the email domain(example.com for the purpose of this example)
- In the Then Redirect To drop-down, select the IDP you want the users with example.com to be redirected to(IDP 1 in this case)
- Click on Save

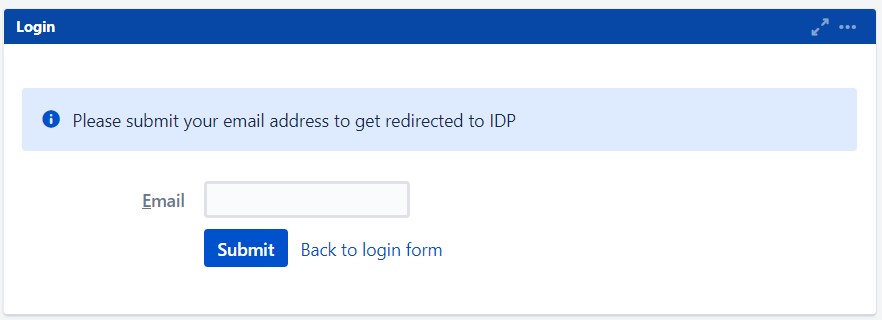
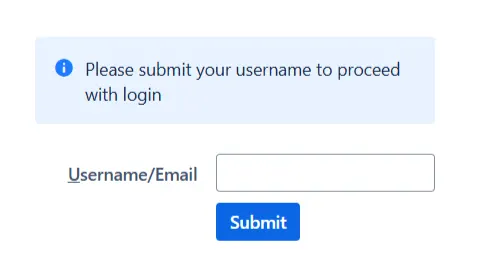
- When a rule such as an example given above is configured, a login form will be displayed to the users where they will have to input their email address.
- In this section you will also configure an emergency URL to by-pass SSO. This setting can be found under the Sign-In Settings tab in the left side menu.
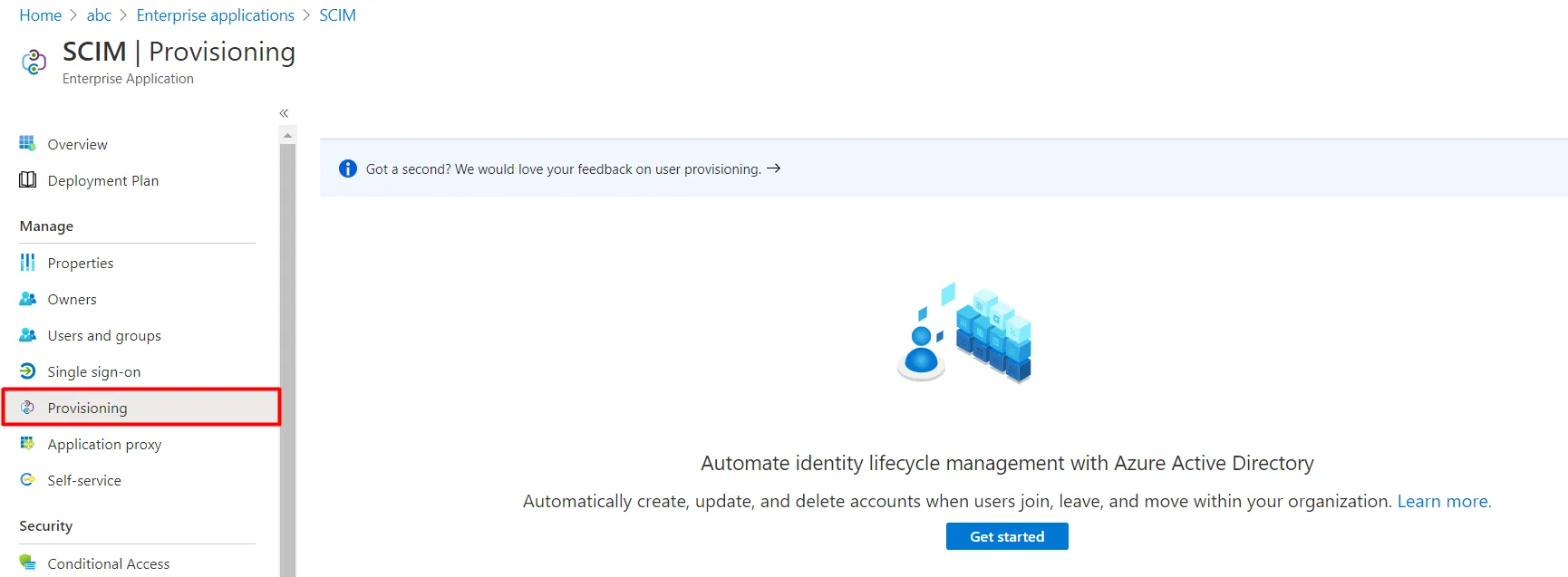
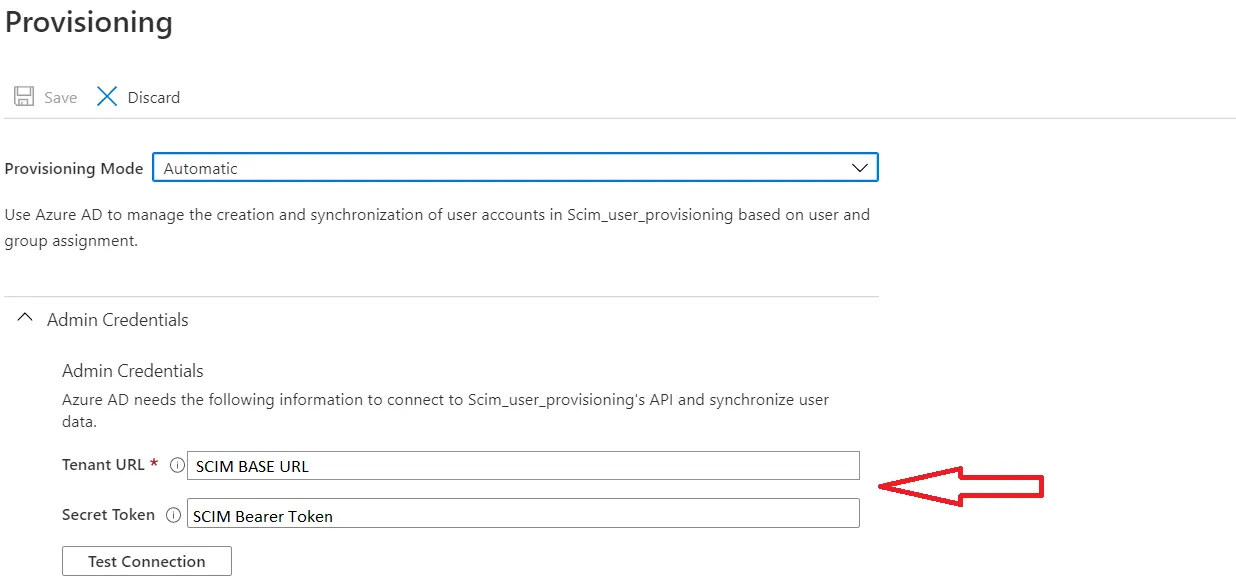
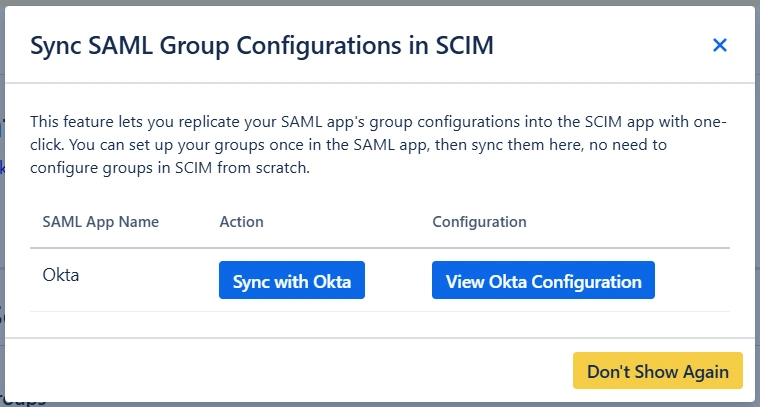
Configure SCIM with SAML
Additional Resources
Did this page help you?


 Try it for free
Try it for free