Contents
SAML Single Sign On (SSO) Into Bamboo Using Oracle Cloud
Bamboo SAML app gives the ability to enable SAML Single Sign On for Bamboo Software. Bamboo Software is compatible with all SAML Identity Providers. Here we will go through a guide to configure SSO between Bamboo and your Identity Provider. By the end of this guide, users from your Identity Provider users should be able to login and register to Bamboo Software.
Pre-requisites
To integrate your Identity Provider(IDP) with Bamboo, you need the following items:
- Bamboo should be installed and configured.
- Bamboo Server is https enabled (optional).
- Admin credentials are set up in Bamboo .
- Valid Bamboo Server Licence.
Download And Installation
- Log into your Bamboo instance as an admin.
- Navigate to the settings menu and Click Manage Apps.
- Click Find new apps or Find new add-ons from the left-hand side of the page.
- Locate Bamboo SAML Single Sign On/SSO, SAML SSO via search.
- Click Try free to begin a new trial or Buy now to purchase a license for Bamboo SAML Single Sign On/SSO, SAML SSO.
- Enter your information and click Generate license when redirected to MyAtlassian.
- Click Apply license.
Step 1: Set Up Oracle Cloud as Identity Provider
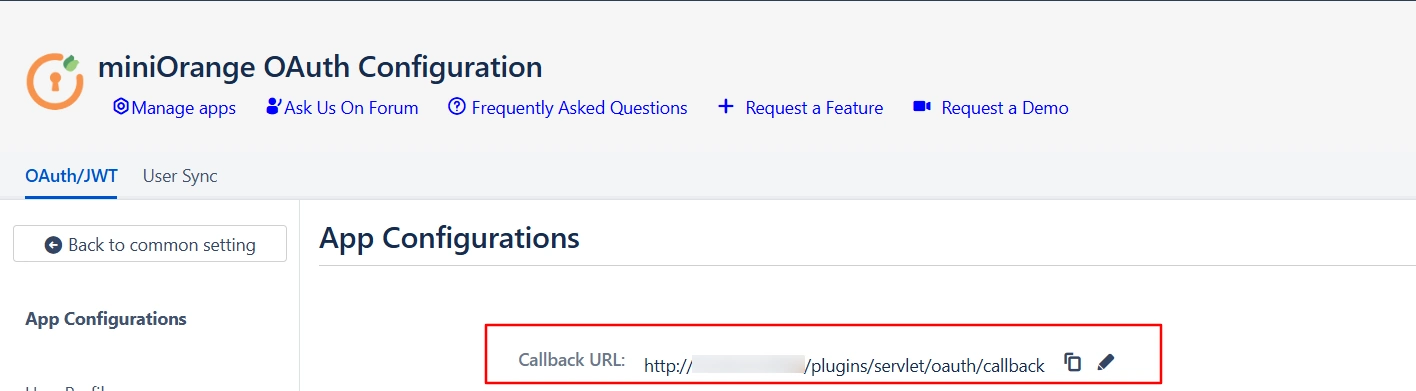
- Navigate to the plugin configuration page, click the "Add New Provider" button (located either in the middle or top-right corner), select Oracle Cloud as the application, and copy the callback URL from the plugin and keep it handy, as you'll need it to configure Oracle Cloud as the OAuth provider.
- Access the Oracle Identity Cloud Service (IDCS) administration console, select Applications, and then click Add
- Click on SAML Application
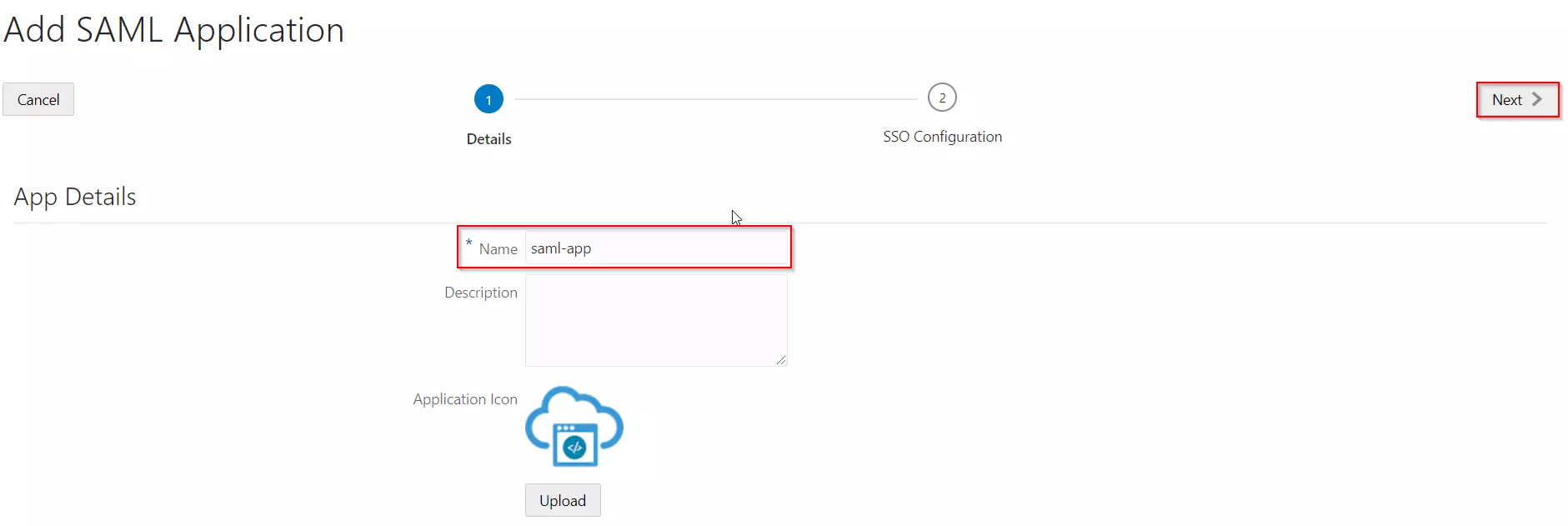
- Enter the name of your Application and select Display in My Apps option under Display Settings section. And then click on the Next button.
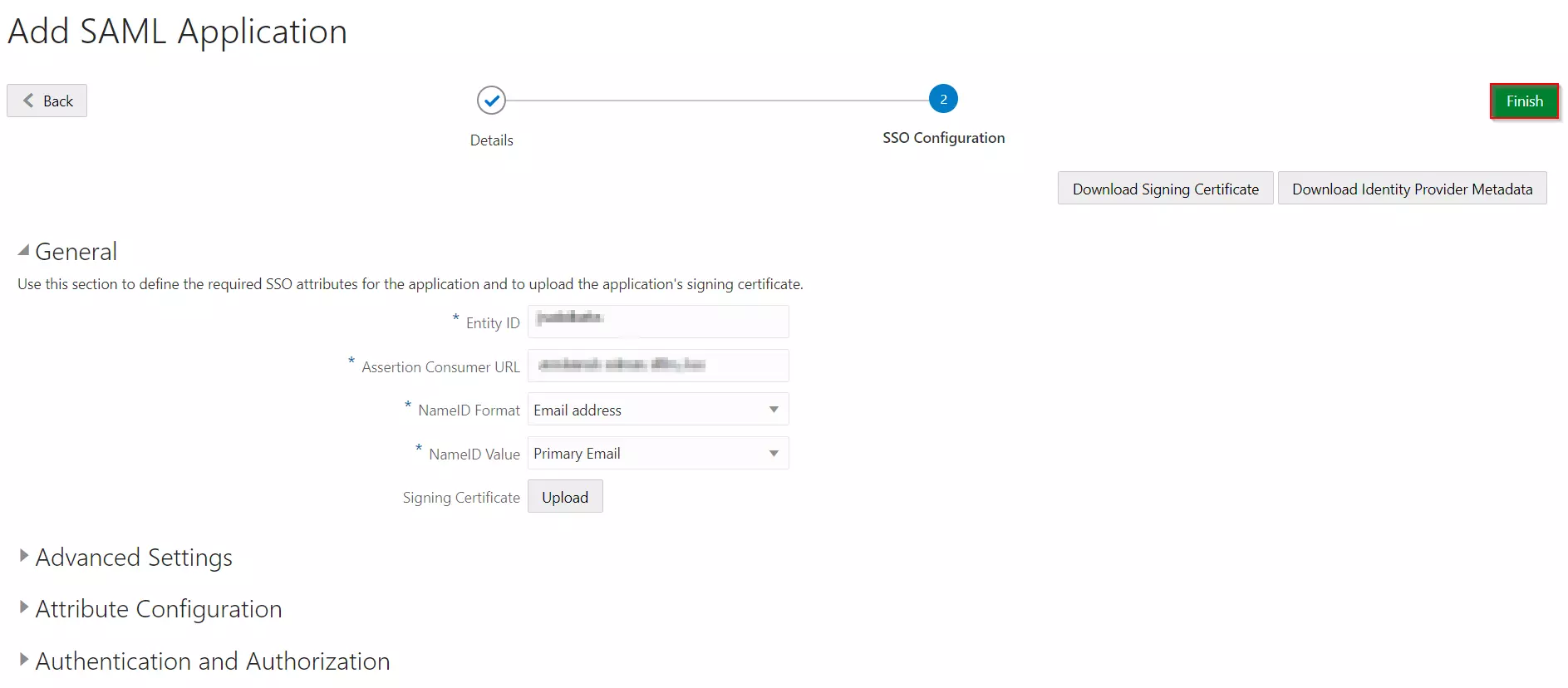
- In SSO Configuration, enter the following:
- Click on the Finish button to save the configuration.
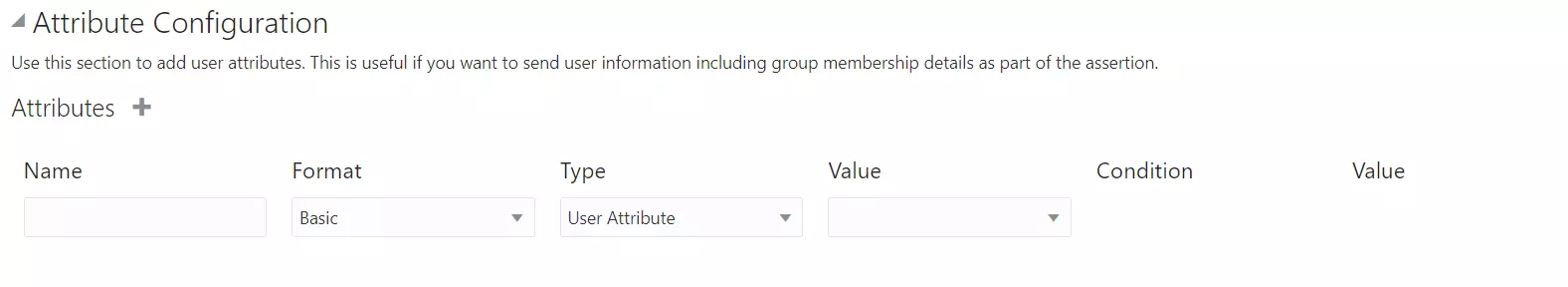
- Configure Attribute Configuration under SSO Configuration Tab (Optional).
- For example, enter the name of attribute as "firstName" and select Basic from the Format dropdown, select User Attribute from Type dropdown, select User Name from the Value dropdown and click on the Save button.
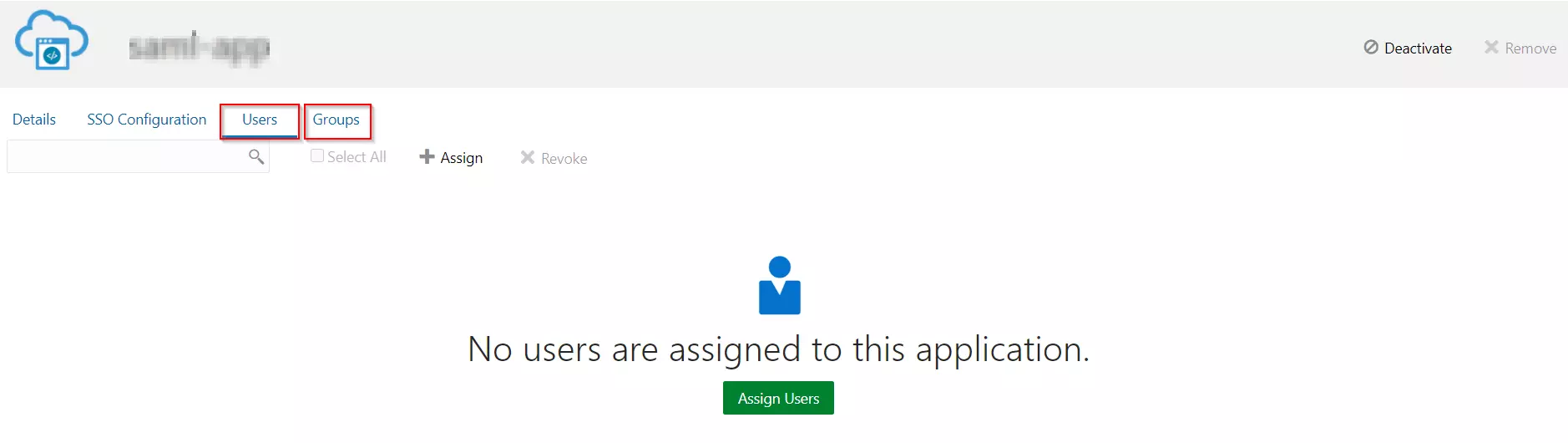
- After creating and configuring the app, go to Users / Groups tab.
- Here we can add the users and groups you want to give access to log in through this app. Assign this to the people/group you would to give access to.
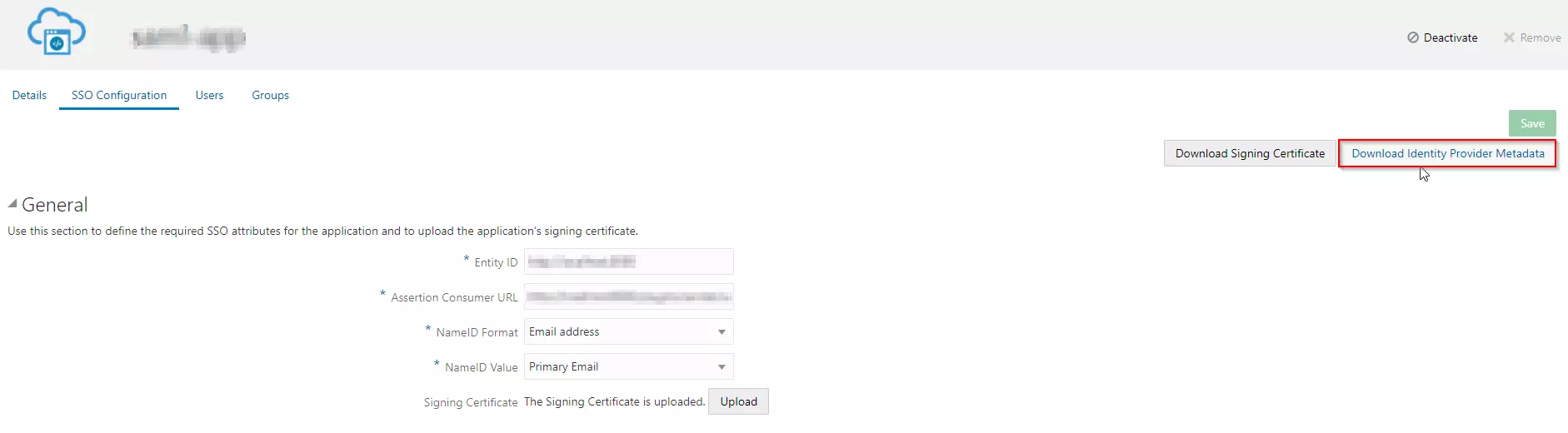
- Go to the SSO Configuration.
- Click on the Download Identity Provider Metadata button to download the metadata.
Follow the steps below to configure Oracle Identity Cloud Service (IDCS) as an Identity Provider (IDP).
 Configuring Oracle Identity Cloud Service (IDCS) as IdP
Configuring Oracle Identity Cloud Service (IDCS) as IdP
| Entity ID | Enter SP Entity ID / Issuer from the Service Provider Metadata tab of the module. |
| Assertion Consumer URL | Enter ACS URL from the Service Provider Metadata tab of the module. |
| NameID Format | Select Email address as a NameID Format from dropdown list. |
| NameID Value | Select Primary Email as a NameID Value from dropdown list. |
| Signing Certificate | Download certificate from Service Provider Metadata tab of the module. |
 Assigning Groups/People
Assigning Groups/People
 Import IDP Metadata
Import IDP Metadata
Step 2: Setup Bamboo as Service Provider
Quick Setup streamlines the initial configuration process by automatically handling all essential details required for a basic SSO setup. This allows you to quickly enable SSO functionality and then configure more advanced features at your own pace.
You can follow the steps provided below initiate a Quick Setup:
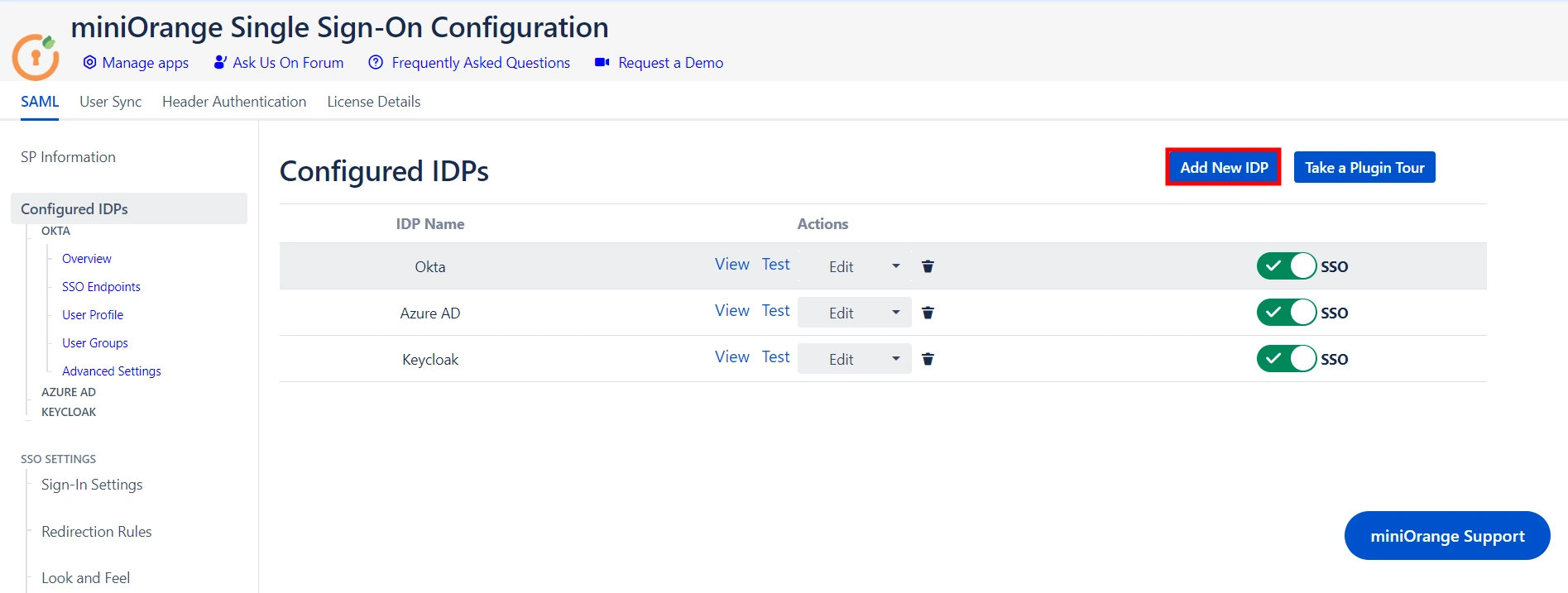
- Click on the Add New IDP button in the Configured IDPs section.
- Next, select the Quick Setup option in the pop-up that appears.
- Select your preferred IDP from the list of IDPs displayed. You can also search for an IDP using the search bar.

 2.1: Service
Provider Metadata
2.1: Service
Provider Metadata
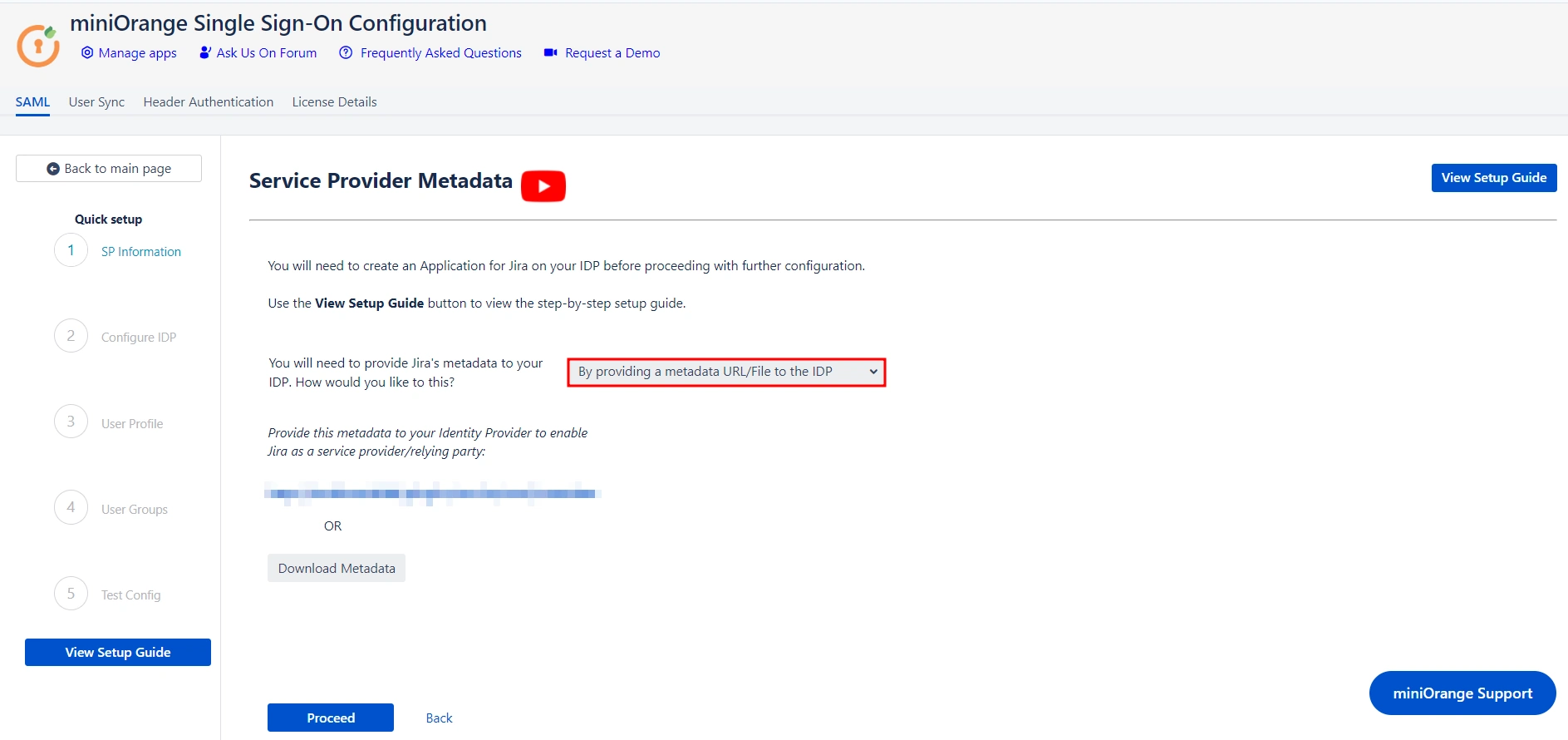
After selecting your preferred IDP, you’ll be taken to the Service Provider (SP) Metadata section. Here, you will find the metadata that you need to provide to your IDP.
The setup gives you two ways to add this metadata to your IDP. Let’s explore these two methods in depth:
- If your IDP supports importing of metadata, then you can select By providing a metadata URL/File to the IDP from the dropdown list.
- Based on your Identity Provider's requirements, you can either provide the metadata URL or download an XML metadata file. To obtain the XML file, click on Download Metadata.
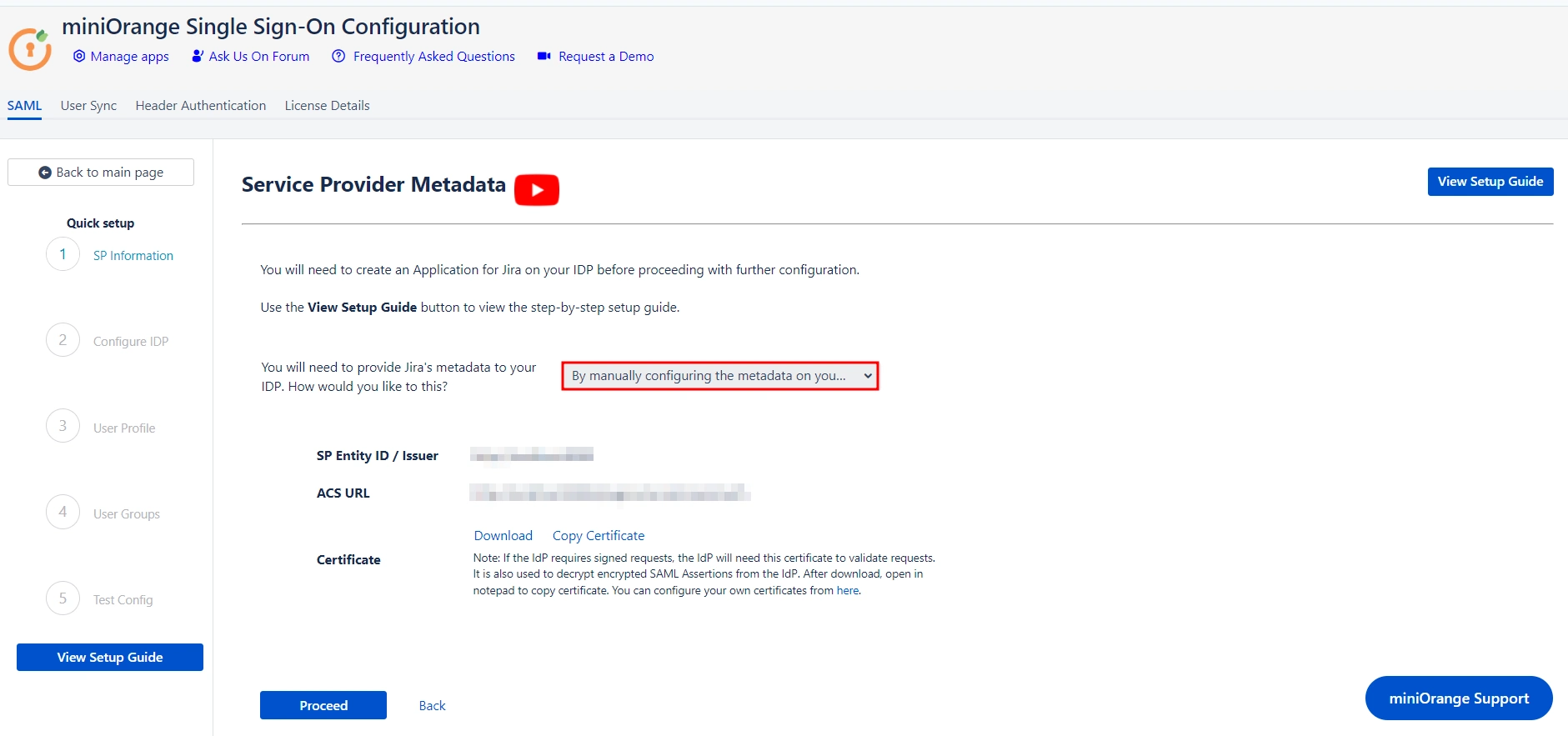
- If you wish to add the metadata manually, then you can select By manually configuring the metadata on your IDP from the dropdown list.
- If you select the manual method the screen will provide you with SP Entity ID, ACS URL, and SP Certificate. You will have to provide these details to your IDP.
- Click on Proceed once you’re done.
 2.1.1:
Importing the metadata
2.1.1:
Importing the metadata
 2.1.2:
Manually adding the metadata
2.1.2:
Manually adding the metadata
 2.2: Configuring
your Identity Provider
2.2: Configuring
your Identity Provider
Let’s explore how you can configure your IDP using the metadata.
- Our plugin gives you the option to name your IDP through the Custom IDP Name field. This feature is useful if you need to set up multiple IDPs. It will display the custom name on the SSO button on the login page for each configured IDP.
- If you do not wish to set a custom name, simply select No from the dropdown menu.
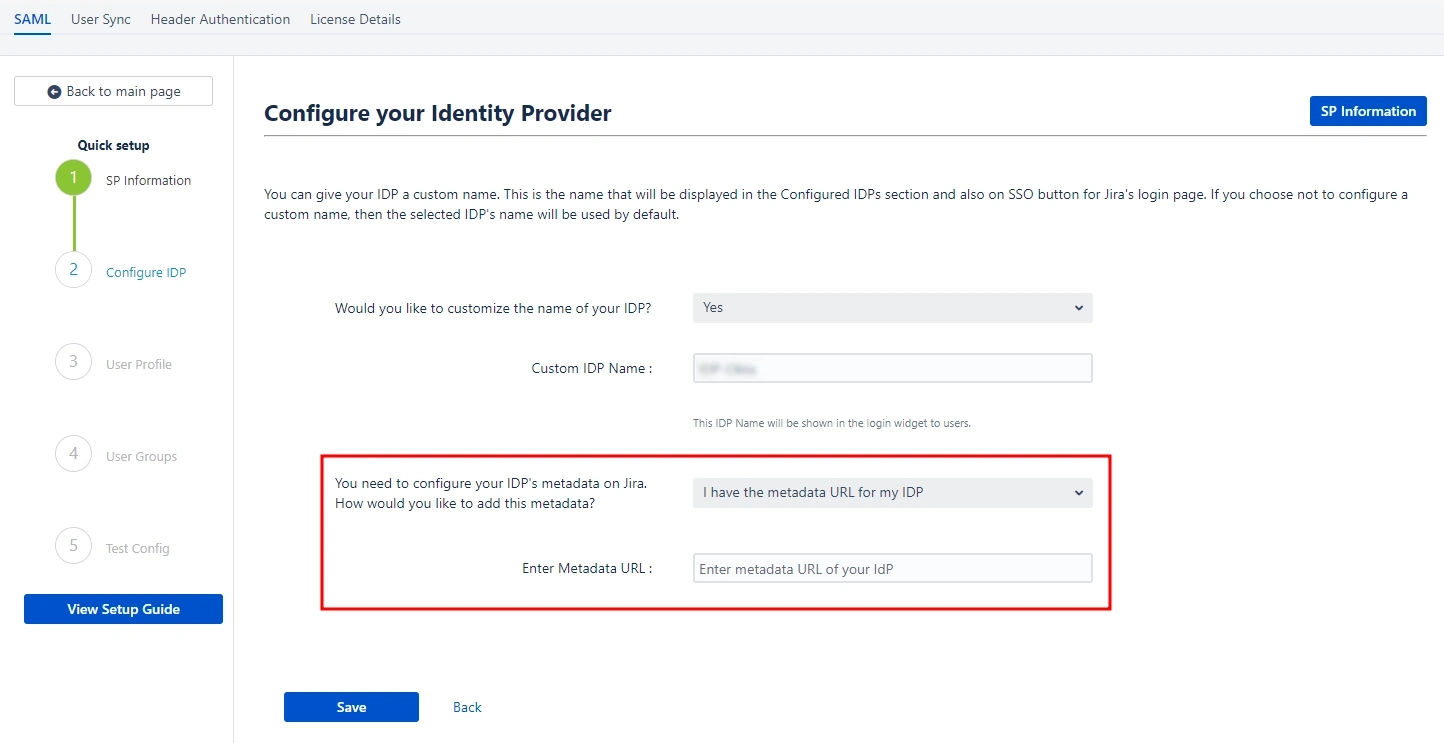
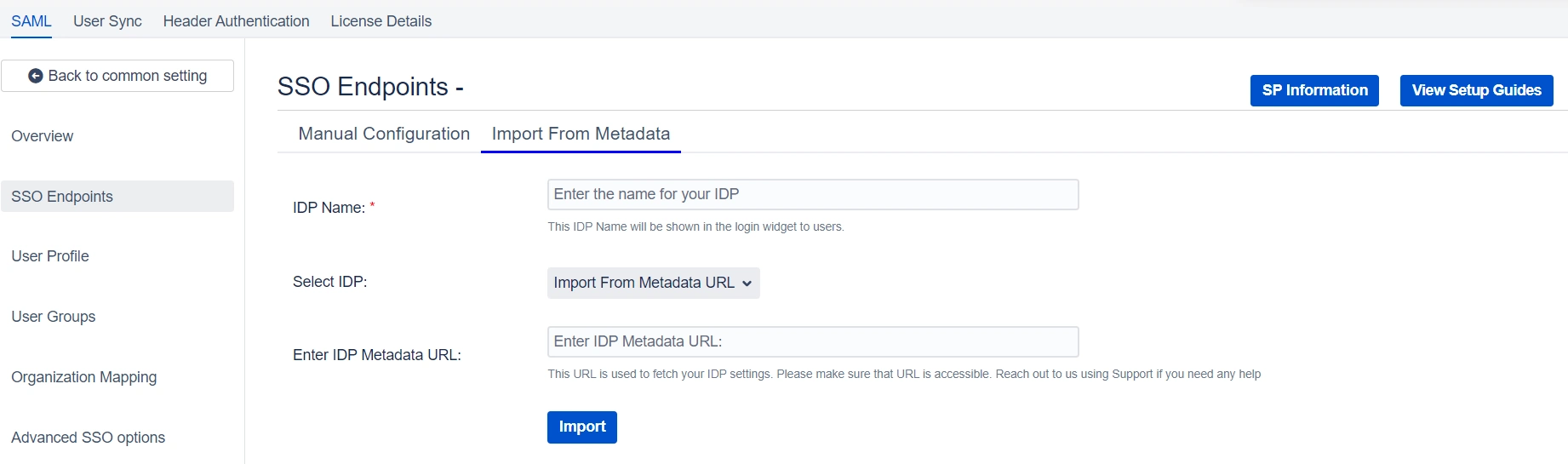
- If you select this option from the dropdown list, you just need to paste your metadata URL in the Enter Metadata URL field. This is the same URL we fetched before initiating the Service Provider setup step.
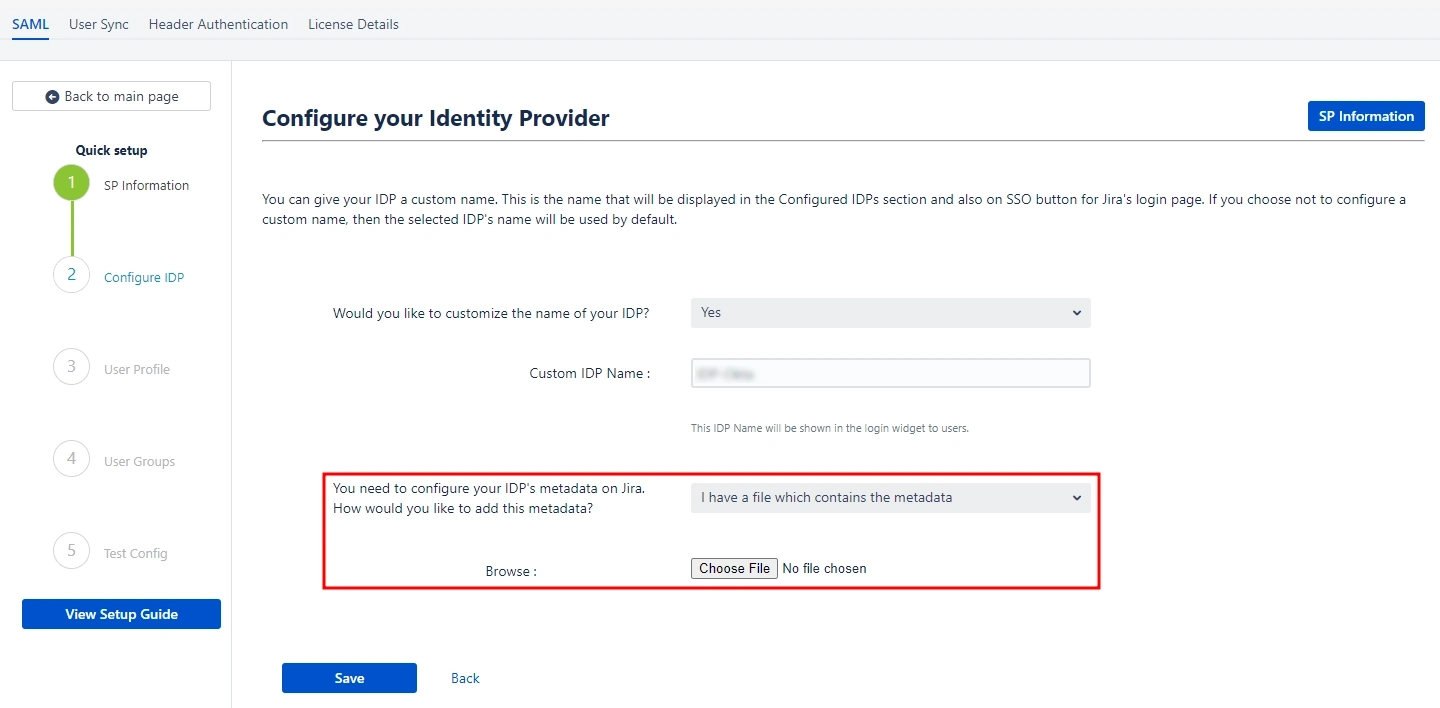
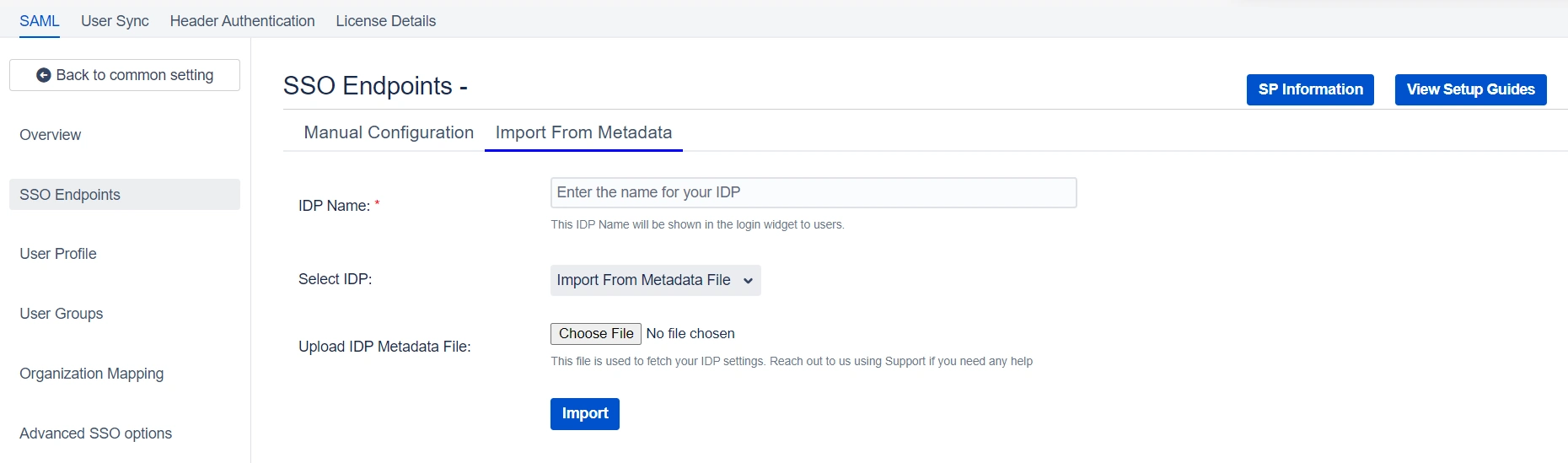
- If you select this option, you just need to upload the metadata file to the plugin using the Choose File button.
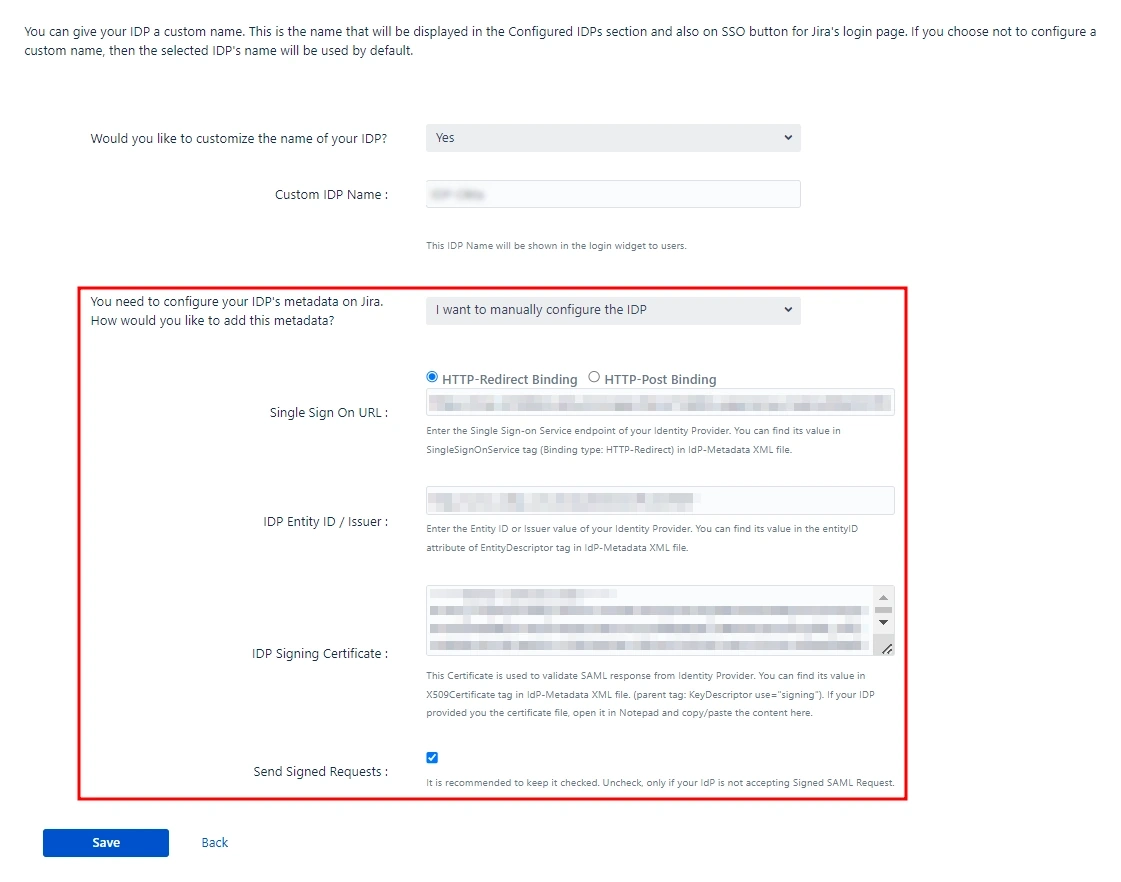
- Selecting this option requires manually configuring the IDP details. To do so, you will need to obtain the following information from your IDP's metadata:
- Single Sign On URL.
- IDP Entity ID.
- IDP Signing Certificate.
- After adding the IDP metadata, click Save. If the IDP was added successfully, you will see a field labeled Test and Get Attributes URL. To verify the configuration, open the URL in an incognito window to Get the Attributes from IDP. This will test if the IDP integration was set up correctly.
 2.2.1:
Custom
IDP name
2.2.1:
Custom
IDP name
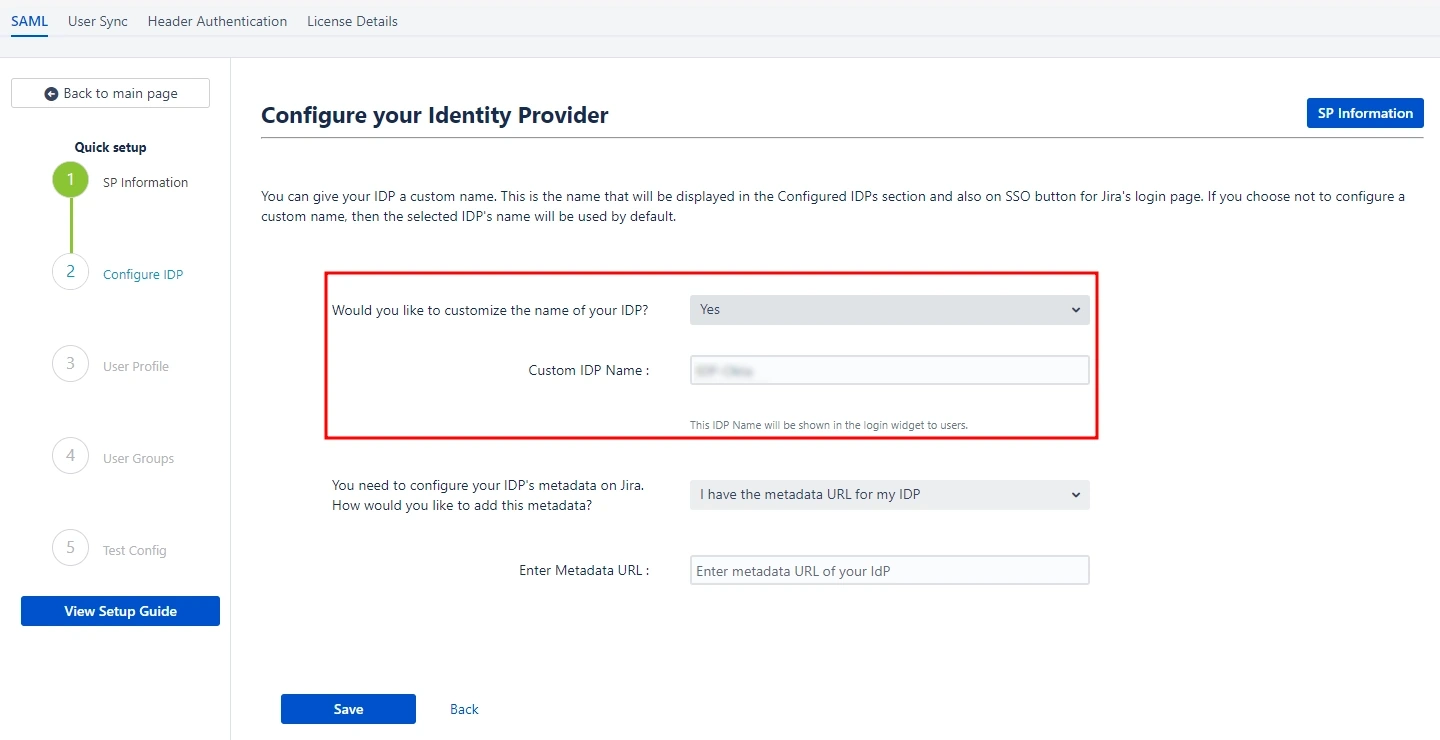
 2.2.2:
Adding
the IDP metadata
2.2.2:
Adding
the IDP metadata
Next, you can scroll down on the same page to add IDP metadata. Our plugin provides three ways for you to add your IDP metadata. You can select any one of the three methods using the corresponding dropdown list.
Let’s look at the three options individually:
 2.2.2.A: I
have the metadata URL for my IDP
2.2.2.A: I
have the metadata URL for my IDP
 2.2.2.B: I
have a file which contains the metadata
2.2.2.B: I
have a file which contains the metadata
 2.2.2.C: I
want to manually configure the IDP
2.2.2.C: I
want to manually configure the IDP
 2.2.3:
Testing the configuration
2.2.3:
Testing the configuration
 2.3: User
Profile
2.3: User
Profile
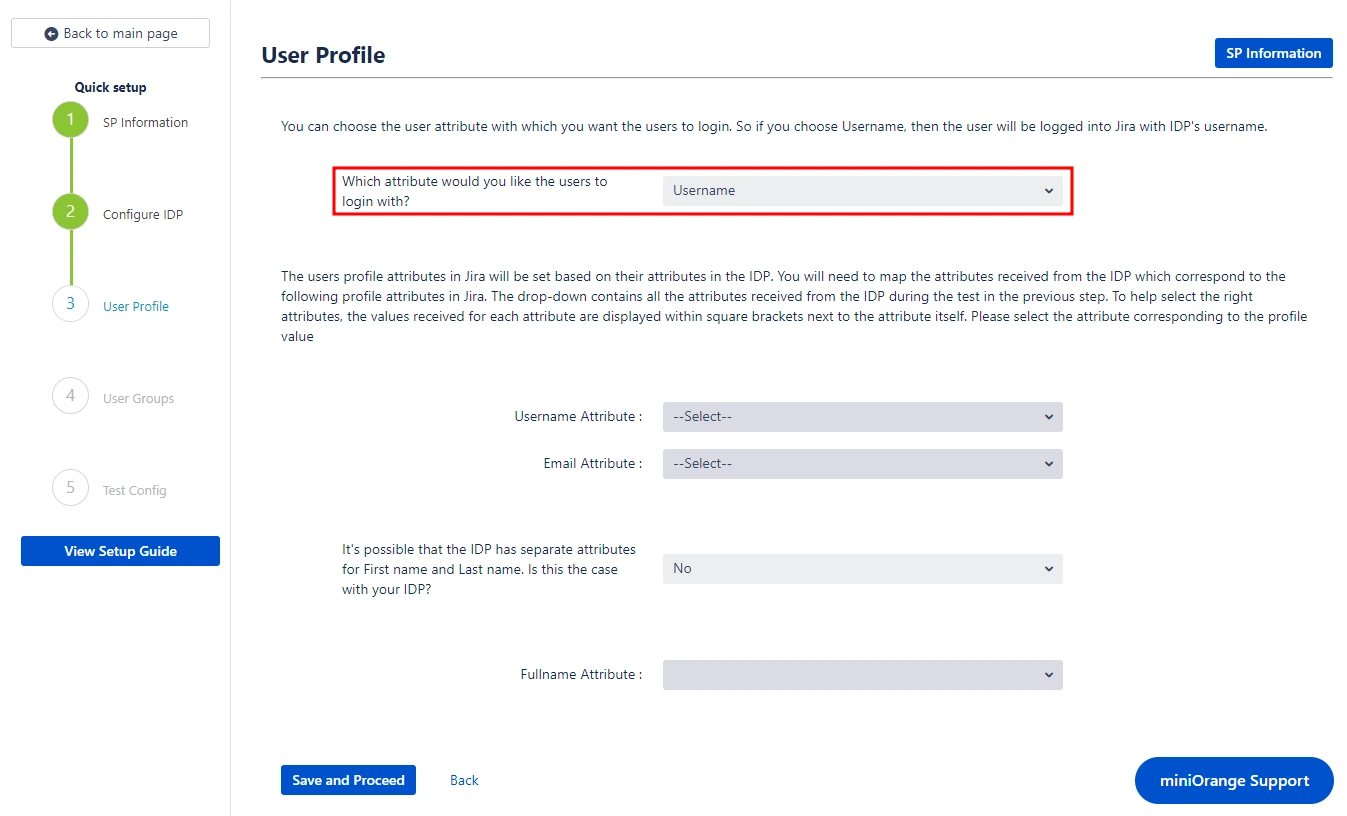
With the Identity Provider (IDP) configured, we will now set up the basic user profile attributes for your Service Provider (SP).
- During the Jira SSO process, the user's account is identified based on an attribute received from the Identity Provider (ISP).
- This attribute value is used to locate the corresponding user account in Jira and log the user into that account. You can select which specific attribute should be used for this user mapping by choosing from the provided dropdown menu.
- Setting up both Username and Email is required if you want to let users register. If the test configuration performed in the previous step was successful, then the inputs for the username and email attributes will be dropdowns.
- These dropdowns will contain all of the users’ attribute names sent from the IDP. You will need to select the appropriate options containing the user's username and email.
 2.3.1:
Matching a user
2.3.1:
Matching a user
 2.3.2:
Setting profile attributes
2.3.2:
Setting profile attributes
 2.4: User Groups
- Default groups
2.4: User Groups
- Default groups
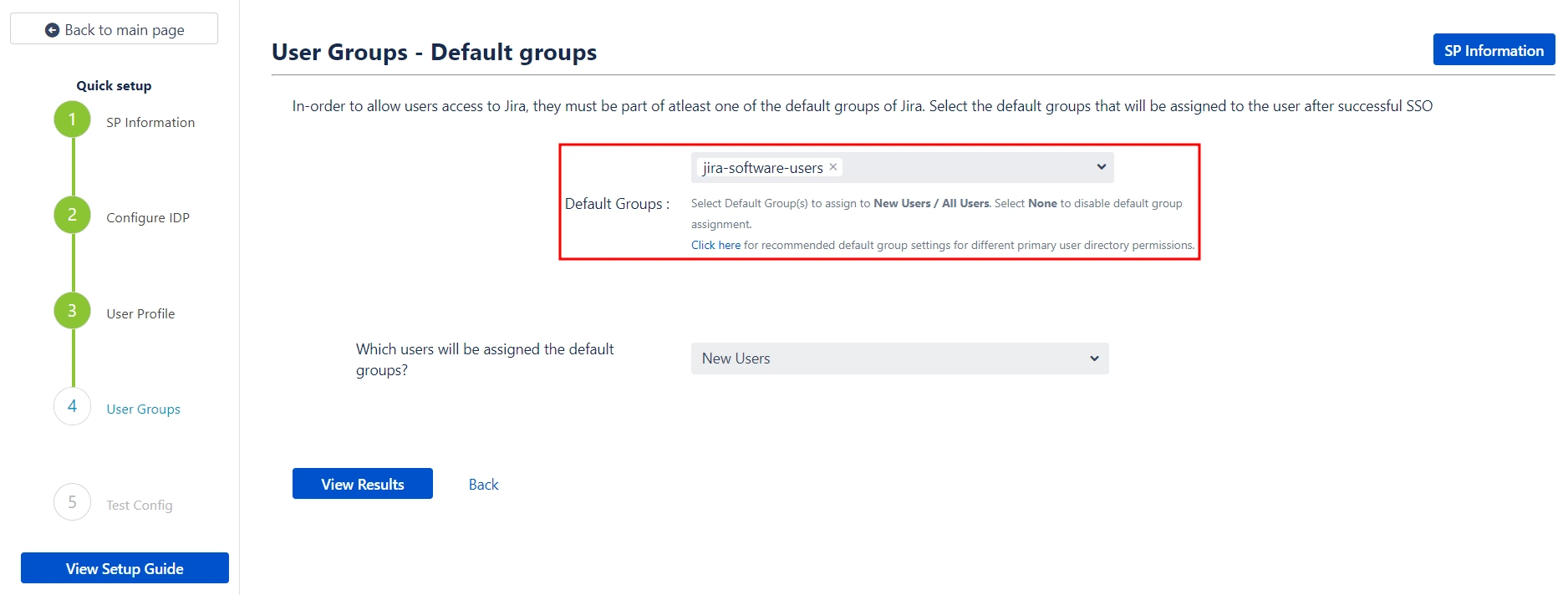
- To grant users access to Jira, they must be members of at least one of the default Jira groups. This step allows you to select the default groups that will be automatically assigned to users upon successful SSO authentication. You can set multiple groups as default groups.
- Our plugin gives you the option to enable default groups for All Users, New Users, or Users with No IDP Groups using a dropdown list. If you don't want to assign any default group to SSO users, you can select None.
- This concludes the Quick Setup flow. If you encountered any issues or errors while setting up your Identity Provider (IDP), refer to the Troubleshooting section for guidance or contact our support.
 2.5:
Troubleshooting and Support
2.5:
Troubleshooting and Support
- Navigate to the Configured IDPs page.
- Locate the Edit dropdown menu for your configured IDP.
- From here, you can access your SP Metadata and customize settings for User Profile and User Groups.
- For detailed information on customizing User Profile and User Groups settings, refer to the Custom Setup section of this guide.
Here, you can review the results of a successful test configuration, including the attributes received from your IDP, the SAML request sent, and the SAML response received.
The Quick Setup method establishes basic SSO functionality for your end-users. However, you can further customize your setup by utilizing the full set of features provided by the plugin.
To access advanced configuration options:
 2.1: Service
Provider Metadata
2.1: Service
Provider Metadata
If you intend to customize your IDP setup from the start, you can find the required Service Provider (SP) metadata under the SP Metadata section. It contains essential information about your SP configuration that you will need to provide to your IDP for seamless integration.
There are multiple ways to add this metadata to your IDP:
- Depending on how your IDP accepts the metadata, you can either provide the metadata URL or you can use the Download Metadata button to download an XML file for the same.
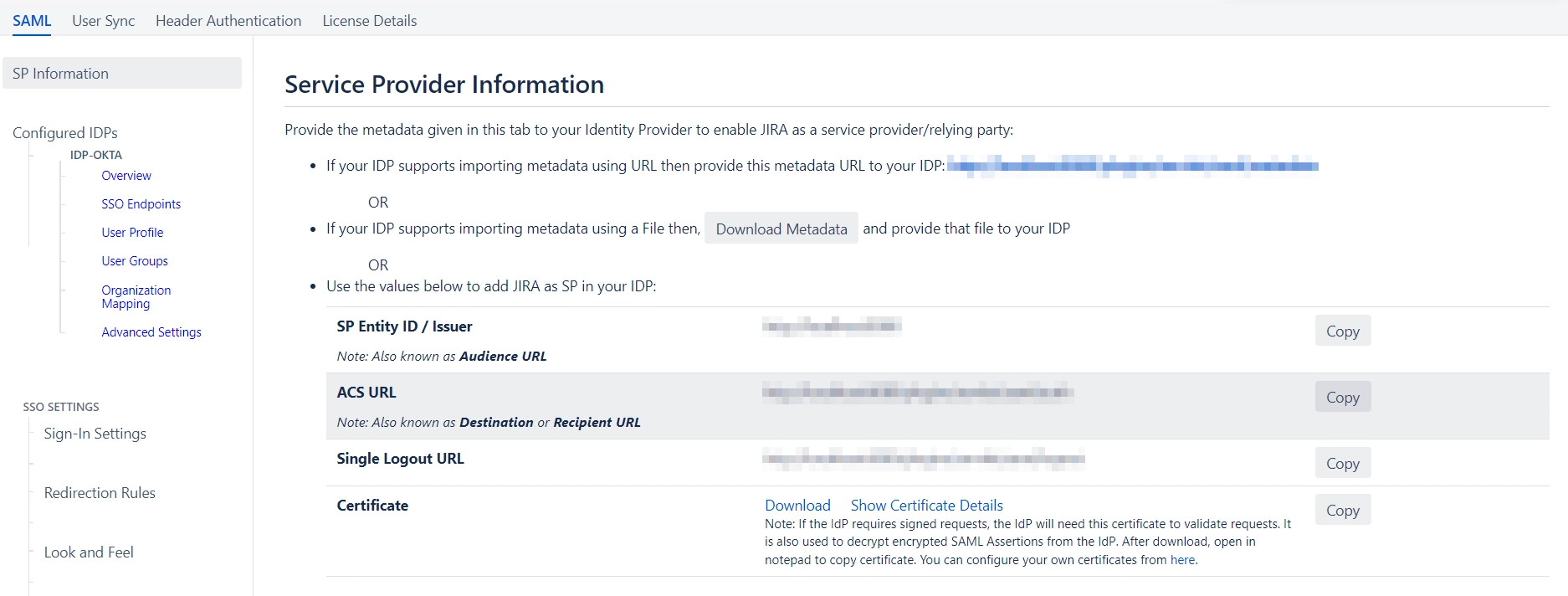
- SP Entity ID
- ACS URL
- SP Certificate
 2.1.1:
Importing the metadata
2.1.1:
Importing the metadata
 2.1.2:
Manually add the metadata
2.1.2:
Manually add the metadata
If you wish to add the metadata manually, you will find the following information in this section. You will need to provide these details to your IDP.
 2.2: Configuring
Your Identity Provider
2.2: Configuring
Your Identity Provider
The manual setup flow allows you to dive into the complete set of configurations provided by the plugin to add a SAML IDP.
The steps to configure an IDP using the Manual Setup option are:
- Click on the Import from Metadata tab.
- Select IDP – Import From Metadata URL.
- Enter IDP metadata URL – paste the metadata URL that we fetched before initiating the Service Provider .
- If your IDP changes certificates at intervals (Eg. Azure AD), you can refresh your IDP metadata accordingly:
- Navigate to the Advanced SSO options from the menu on the left-hand side of the page.
- Enter your metadata URL in the Certificate Rollover field.
- Toggle the Refresh Certificate periodically option on.
- Use the drop-down provided to set the interval for a periodic refresh. We recommend you select five minutes for the best results.
- Click Import.
- Click on the Import from Metadata tab.
- Select IDP: Import from Metadata File.
- Upload metadata file.
- Click Import.
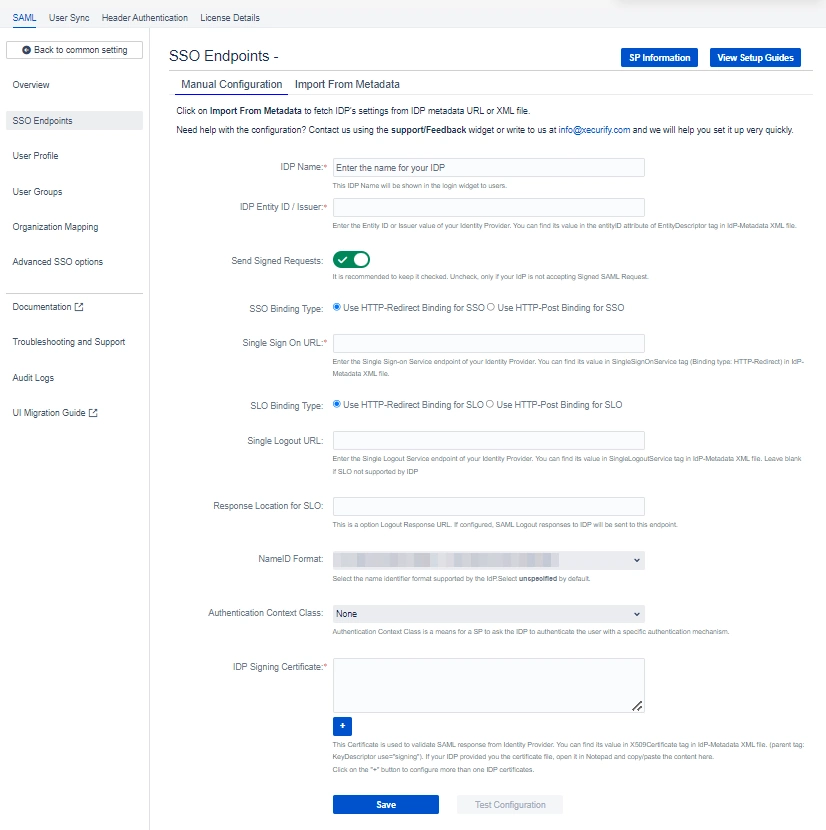
- IDP Entity ID.
- Single Sign On URL.
- Single Logout URL.
- X.509 Certificate.
 2.2.1:
Adding IDP Metadata
2.2.1:
Adding IDP Metadata
There are three ways you can configure IDP settings with the information you have been given by your IDP team:
 2.2.1.1: By
Metadata URL
2.2.1.1: By
Metadata URL
 2.2.1.2: By
Uploading Metadata XML File
2.2.1.2: By
Uploading Metadata XML File
 2.2.1.3:
Manual Configuration
2.2.1.3:
Manual Configuration
Go to Manual Configuration tab and enter the following details:
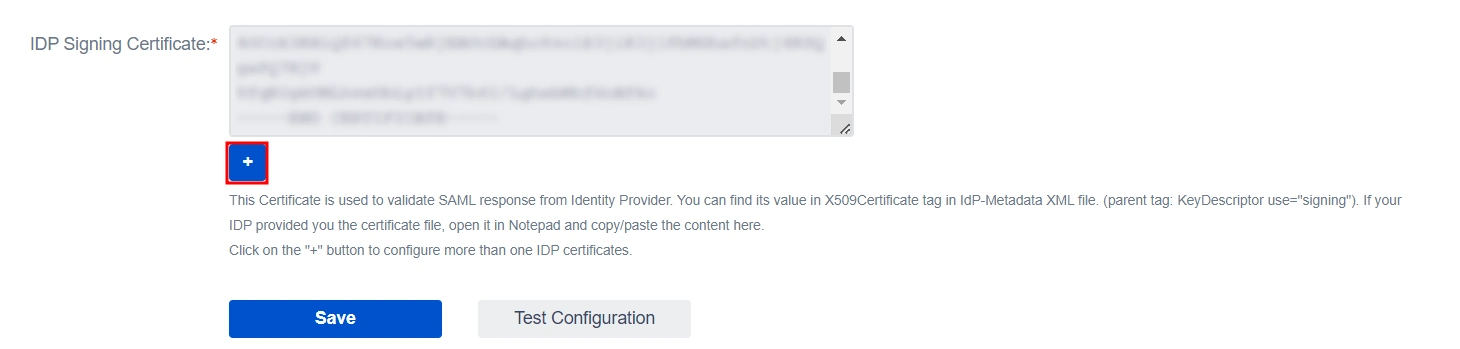
Note: If you need to add an additional X.509 Certificate, you can do so by clicking on the Add button below the textbox.
 2.3: User
Profile
2.3: User
Profile
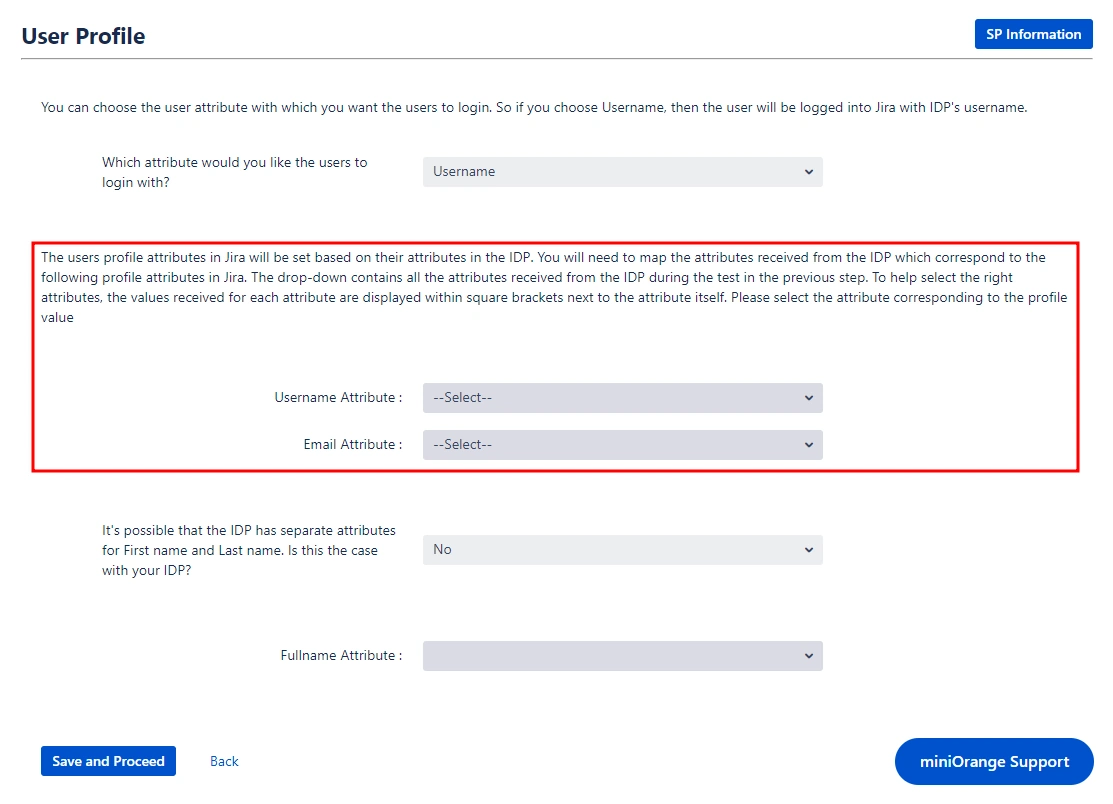
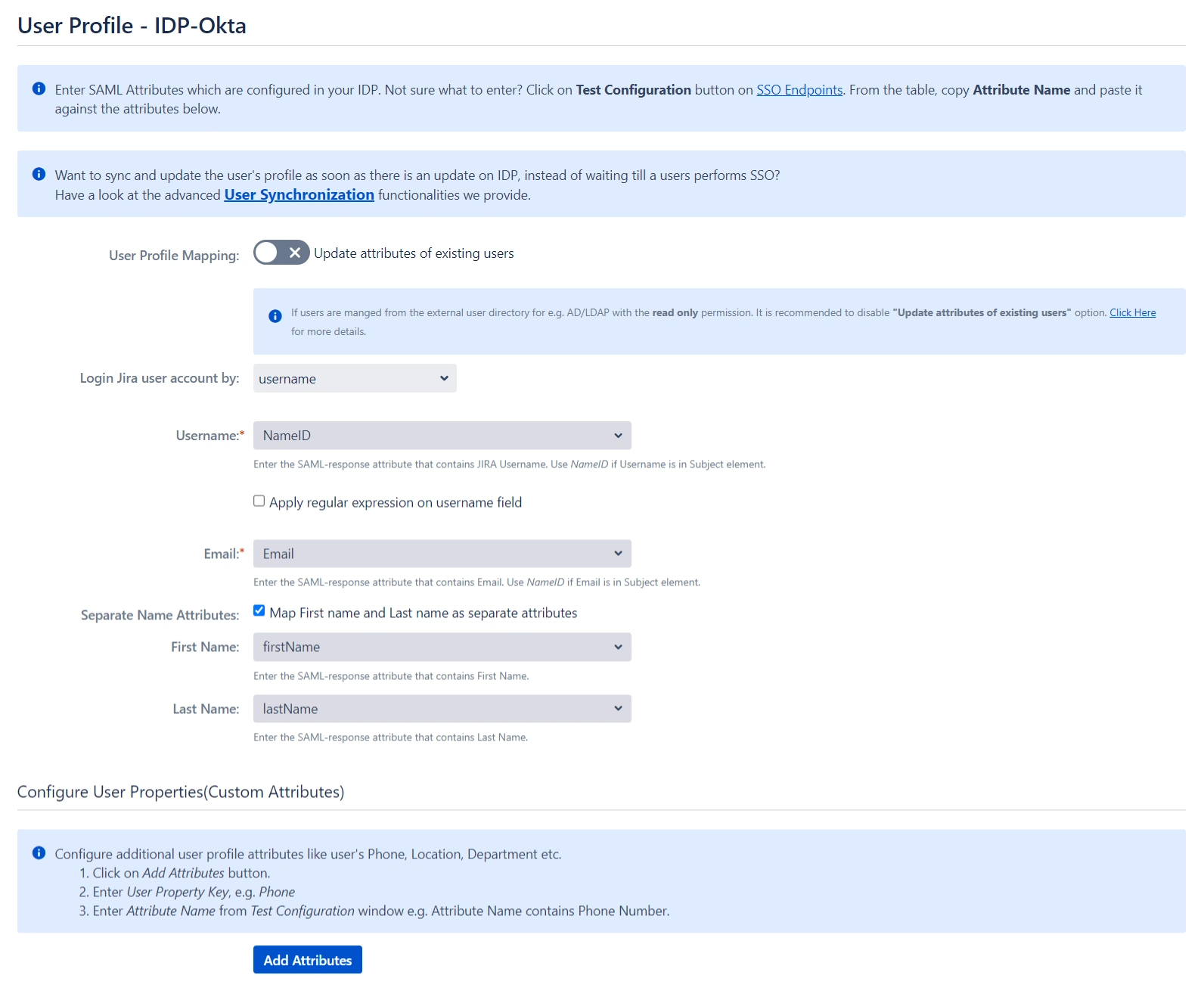
- Next we will be setting up user profile attributes for Jira. The settings for this can be found in the User Profile section.
- Go to the IDP Configuration section. Scroll down and click on Test Configuration.
- You will see all the values returned by your IDP to Jira in a table. If you don't see value for First Name, Last Name, Email, or Username, change the required settings in your IDP so that it returns this information.
- Once you see all the values in Test Configuration, keep the window open and go back to the User Profile section.
- In the User Profile section, fill the values by matching the name of the attribute. For instance, if the Attribute Name in the Test Configuration window is NameID, enter NameID against Username.
- For user registration, ensure both the Username and Email fields are set up. If you're only allowing existing users to log in, configure the attribute that will match the user in Jira.
- Select Username or Email for the Login user account by option.
- Enter the attribute name from IDP which corresponds to Username or Email using Finding Correct Attributes.
 2.3.1:
Finding correct attributes
2.3.1:
Finding correct attributes
 2.3.2:
Setting profile attributes
2.3.2:
Setting profile attributes
 2.3.3:
Matching a user
2.3.3:
Matching a user
When a user logs into Jira, one of their attributes from the IDP is used to search for their account. This enables Jira to detect the user and log them into the corresponding account.
You can configure it using the steps given below:
 2.4: User Groups
2.4: User Groups
Now, let's move on to configure user group attributes for Jira. This feature allows you to replicate the user groups present in your IDP within your Service Provider (SP) environment.
You can accomplish this in the following ways:
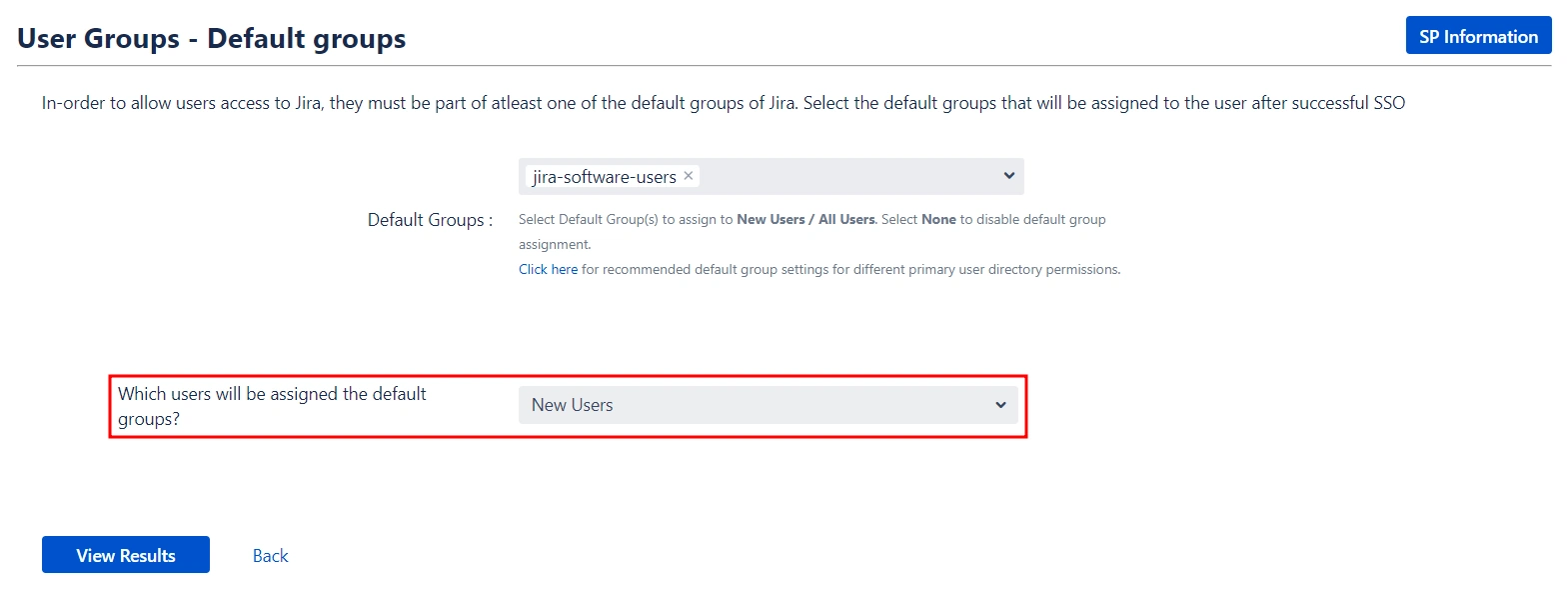
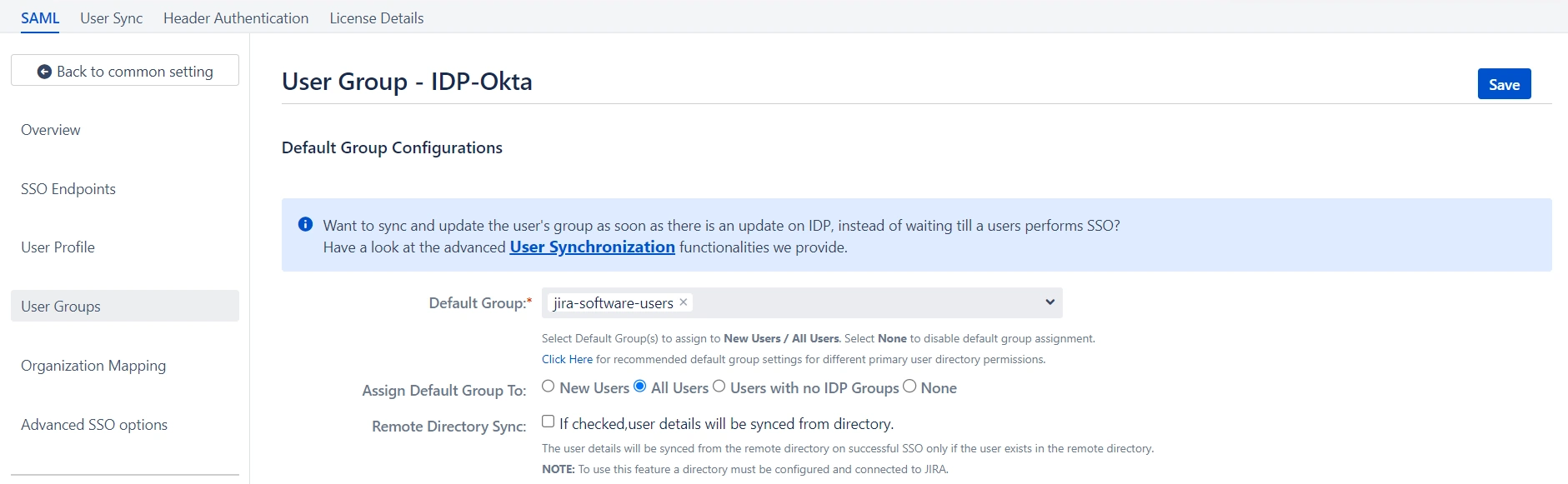
- Select the users' Default Group in the User Groups tab. If no group is mapped, users are added to this group by default.
- You can enable default groups for All Users or New Users using the option. Select None if you don't want to assign any default group to SSO users.
- Go to the IDP Configuration section. Scroll down and click on Test Configuration.
- A table will display all the values returned by your IDP to Jira. If you don't see group information in this table, you'll need to adjust your IDP settings to ensure it returns the appropriate group names.
- In the User Groups tab, enter the Attribute Name for groups in the Group Attribute field.
- Enter the Attribute Name of the group against Group Attribute.
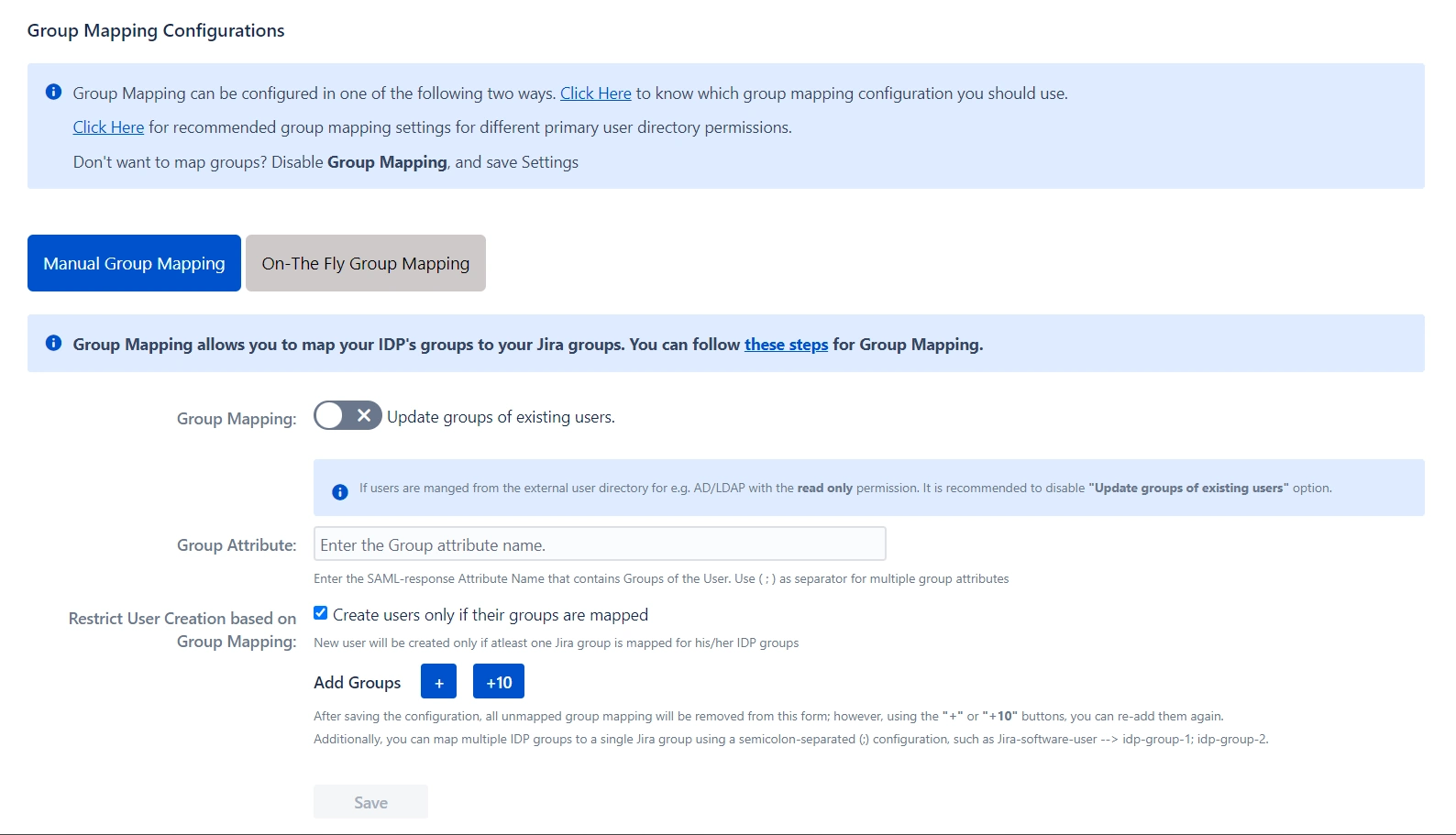
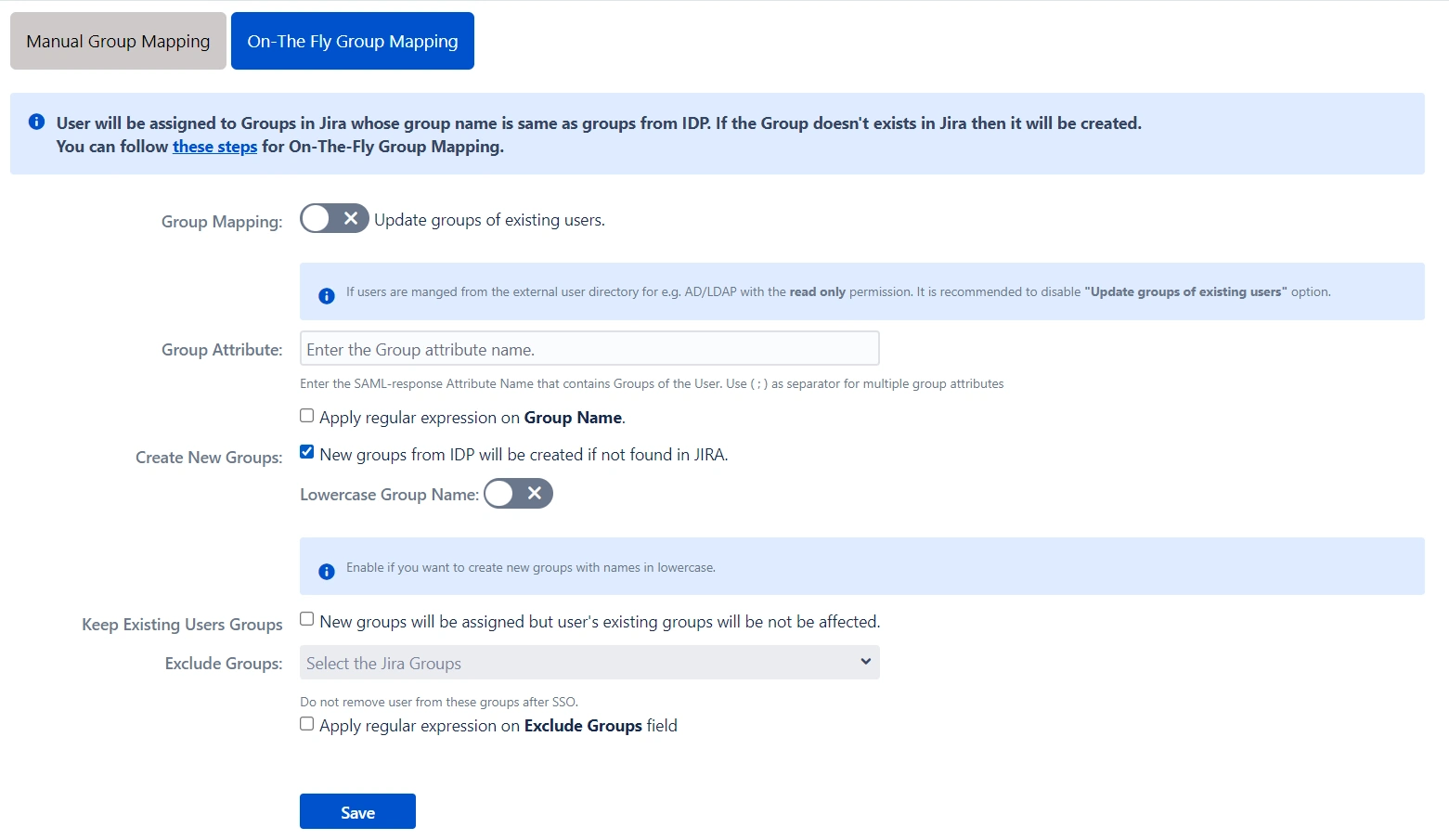
- If you don't want to update groups of existing users, check the Disable Group Mapping option.
- If the names of groups in Jira are different from the corresponding groups in IDP, then you should use Manual group mapping.
- Check Restrict User Creation Based on Group Mapping option if you want new users to be created only if at least one of the user's IDP groups is mapped to a group in the application.
- To do the mapping, first select a Jira group from the dropdown which lists all groups present in Jira and then enter the name of the IDP group to be mapped in the textbox beside.
- For example, if you want all users in the 'dev' group in IDP to be added to Jira-software-users, you will need to select Jira-software-users from the dropdown and enter 'dev' against Jira-software-users.
- Use '+1' and '+10' buttons to add extra mapping fields.
- Use the '-' button next to each mapping to delete that mapping.
- If the names of groups in Jira and IDP are the same, we recommend you use On-The-Fly group mapping.
- Check Create New Groups option if you want new groups from IDP to be created if not found in Jira.
- If the user is part of some group in Jira and that group is not present in the SAML response returned by IDP, then the user will be removed from that group in Jira.
- If you don't want On-The-Fly group mapping to affect Jira groups which are managed locally then add those groups in the Exclude Groups field.
 2.4.1: Setting
default group
2.4.1: Setting
default group
 2.4.2: Finding
Group Attribute
2.4.2: Finding
Group Attribute
Similarly to how you identified the Attribute Names for User Profiles, you will need to locate the attribute name corresponding to group information.
Here’s how you can do this:
 2.4.3: Group
Mapping
2.4.3: Group
Mapping
Group Mapping can be done in two ways:
 2.4.3.1:
Manual Group Mapping
2.4.3.1:
Manual Group Mapping
 2.4.3.2: On-The-Fly Group Mapping
2.4.3.2: On-The-Fly Group Mapping
 2.5:
Troubleshooting and Support
2.5:
Troubleshooting and Support
- You can verify if your SAML SSO configuration is correct by clicking the Test Configuration button on the IDP configuration tab of the plugin.
- After a successful test configuration, you will be able to review the results on the Troubleshooting and Support page. This includes the attributes received from your Identity Provider (IDP), the SAML request sent, and the SAML response received.
- In case you encounter any issues or errors while setting up your IDP, refer to the Troubleshooting section for guidance on how to contact our support team.
Step 3: Redirection on Login Page
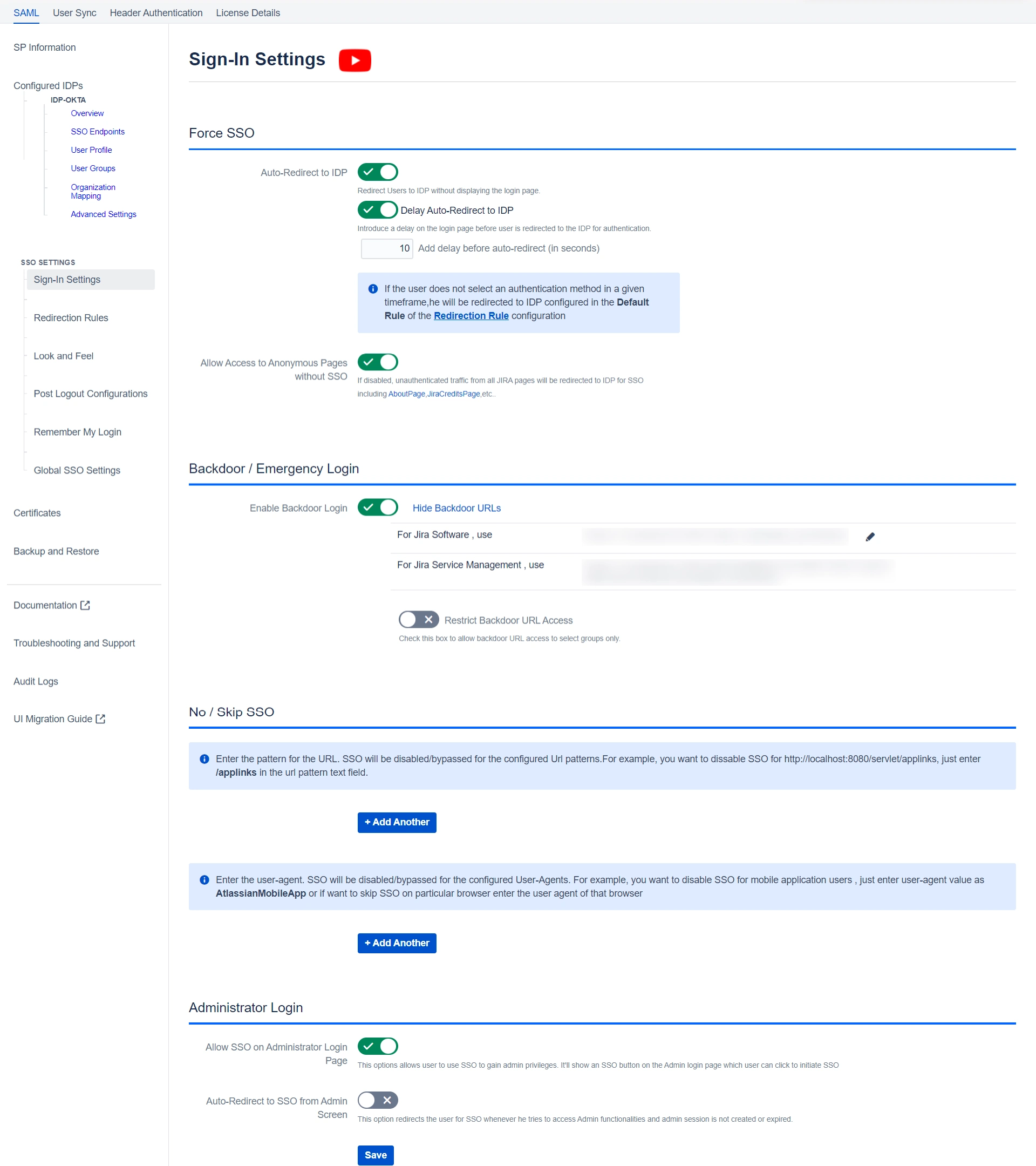
- If you have only one IDP configured, then you can use the features provided on the SSO Settings tab and Redirection Rules tab of the plugin to manage the redirection on the login page.
- Enable the Auto Redirect to IDP option on the SSO Settings tab if you want to allow users to log in only using IDP.
- Use the Emergency/Backdoor Login URL to allow all admins to access the default login page of Jira/Confluence and log in using Jira local credentials. You can also restrict access to this URL for certain users.
- Use the settings given on the Redirection Rules tab to redirect users to their specific IDPs based on their email domains, groups, and directories. This feature is particularly useful in instances where you have multiple IDPs configured.
Step 4: Multiple IDPs
Our plugin offers the flexibility to configure multiple identity providers (IDPs) on your service provider (SP), expanding your options for authentication..- If you need to configure multiple IDPs on your SP you can do so by going to the Configured IDPs section and clicking on Add New IDP.
- If you have multiple IDPs configured, you can choose how you want your end users to use these IDPs to perform SSO.
- For instance, you can display individual buttons for different IDPs on the login page and let the users decide which IDP to use for SSO. Additionally, you can force certain users to use a specific IDP based on the domain of their username/email.
- You’ll be able to configure these rules in the Redirection Rules section.
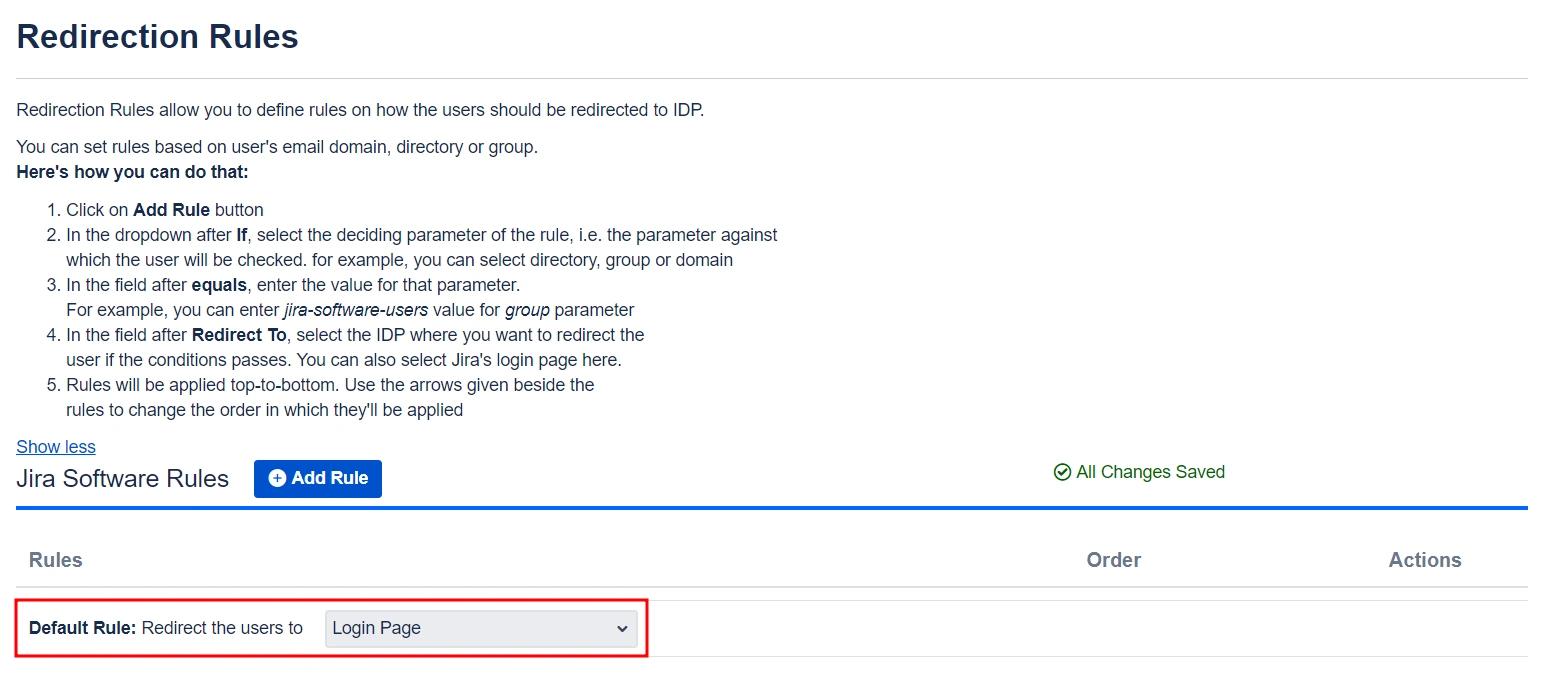
- The plugin has a default rule that is pre-configured and applied to all the users irrespective of their domains. For instance, if you want to display the login page with SSO buttons for each of the IDPs then your Default Rule will be as follows:
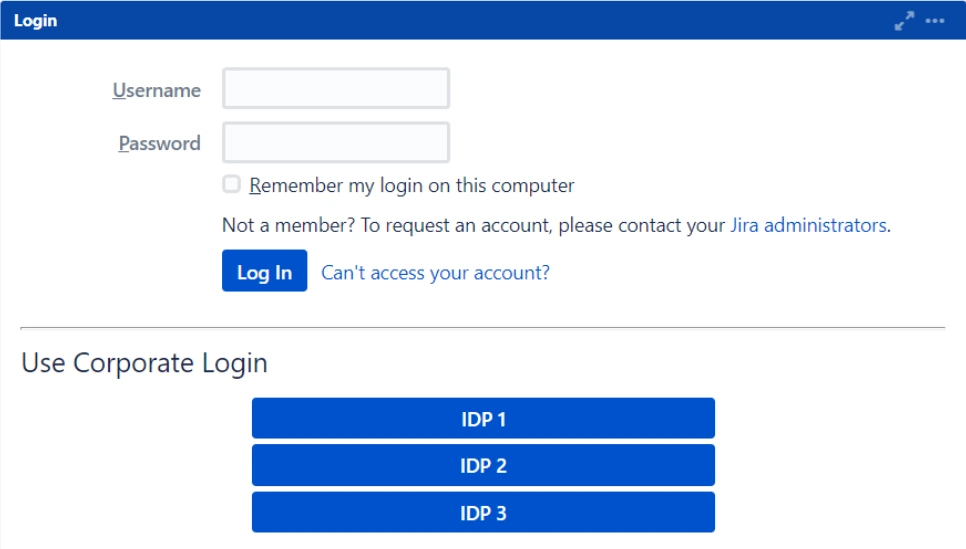
- Based on the default rule mentioned above, the login form will contain buttons for each IDP. Users will have the freedom to choose any of the configured IDPs to initiate SSO.
- You can also configure a rule so that your users will be automatically redirected to an IDP based on their email domains.
- For instance, if you want users that have example.com as their domain to be redirected to IDP 1, you can add a rule for that as follows:
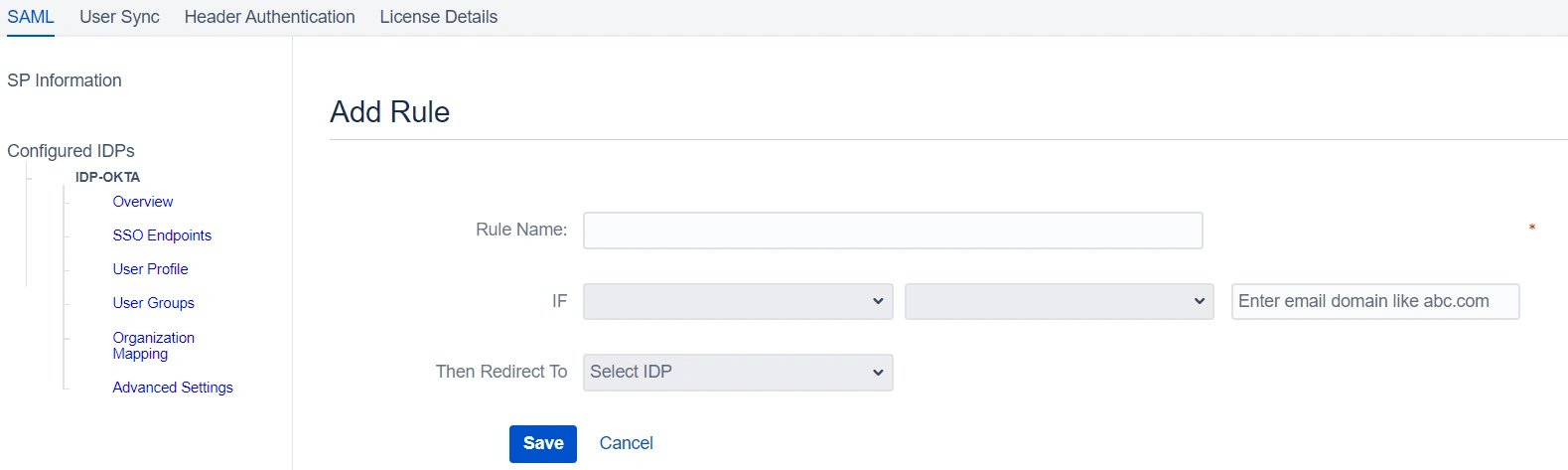
- Click on the Add Rule in the Redirection Rules tab.
- Enter a name for your rule in Rule Name.
- In the IF statement select Email Domain in the first drop-down.
- For the same statement select equals in the second drop-down.
- In the last field of the IF statement, enter the email domain(example.com for the purpose of this example)
- In the Then Redirect To drop-down, select the IDP you want the users with example.com to be redirected to(IDP 1 in this case)
- Click on Save.
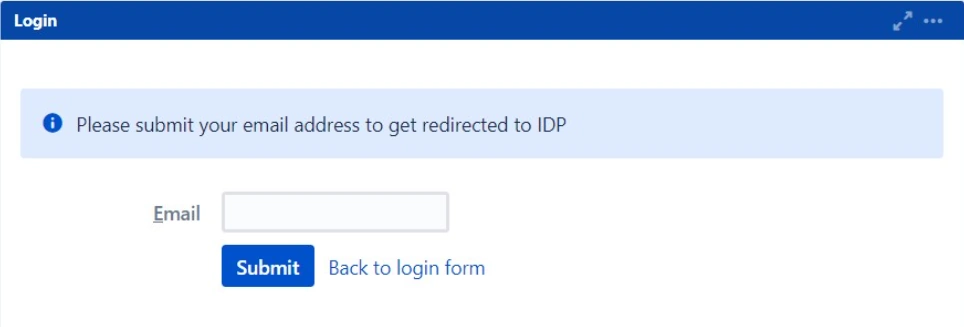
- When a rule like the one described above is configured, users will see a login form where they will have to input their email address.
- Additionally, within the Sign-In Settings, you have the option to configure SSO for administrators, grant access to anonymous pages, and establish an emergency URL for bypassing SSO. These settings can be found in the left-hand side menu bar.
Step 4.1: Configuring Multiple IDPs
Step 4.2: Managing SSO with Multiple IDPs
Configure SCIM with SAML
 Hi! Do you need help with this guide?
Hi! Do you need help with this guide?
Thank you for your response. We will get back to you soon.
Something went wrong. Please submit your query again

Recommended Add-Ons

Two Factor Authentication
Enable 2FA/MFA for users & groups and let users configure 2FA during their first login.
Know More
OAuth/OpenID Connect SSO
Secure your Bamboo instance with OAuth/OpenID Connect SSO.
Know More
Bamboo Crowd Connector
Crowd SAML & Connectors is the only SSO solution for Crowd SSO-enabled Atlassian apps.
Know MoreAdditional Resources
Bitbucket Git Authentication App | Kerberos/NTLM Apps | Word/PDF Exporter | WebAuthn | SonarQube SSO | Jenkins SSO
If you don't find what you are looking for, please contact us at support-atlassian@miniorange.atlassian.net or raise a support ticket here.
