SAML Single Sign On (SSO) into SonarQube using Okta as IDP
SonarQube SAML plugin gives the ability to enable SAML Single Sign On for the SonarQube. Here we will go through a guide to configure SSO between SonarQube and Okta. By the end of this guide, Okta users should be able to log in and register to the SonarQube Server.
Video Setup Guide
You can refer the steps from the video or documentation below to configure your IDP with SonarQube.
Step 1: Set Up Okta as Identity Provider
With the plugin installed, you can move on to setting up Okta as an IDP.
 1.1: Okta IDP Configuration
1.1: Okta IDP Configuration
- Log into Okta Admin Console.
- For developer account, switch to Classic UI to configure app.
- In the left hand menu, go to Applications → Applications and then click on Create App Integration.
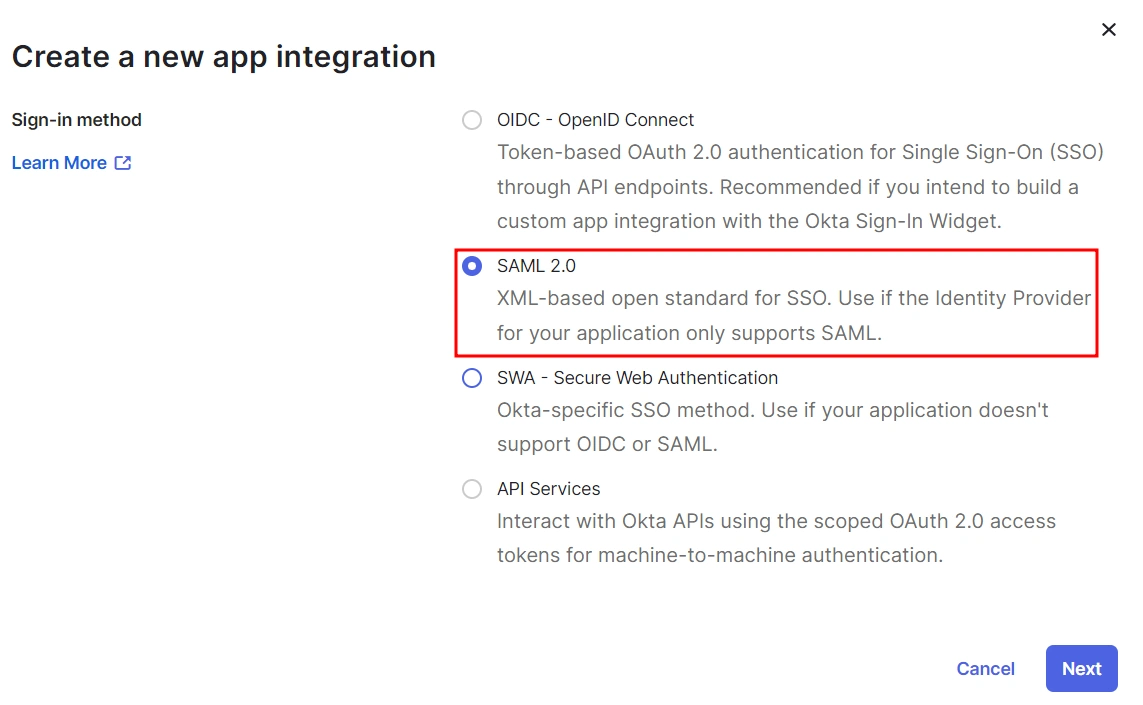
- Select SAML 2.0 as Sign on method and click Next.
- In General Settings, enter the app name and click on Next.
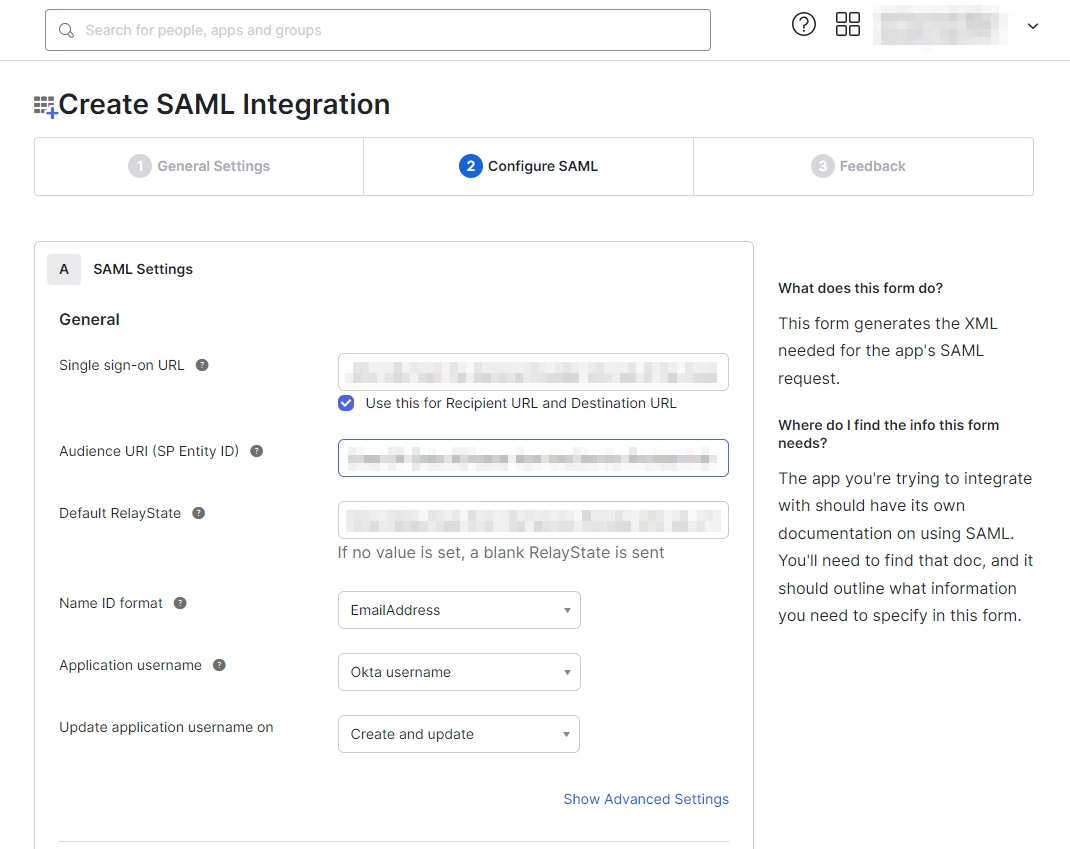
- Set up SAML parameters in the Configure SAML tab. You will find all the required information inside the SP Information tab of your plugin. The table below will help you map the right data to the fields.
- Next, scroll down inside the Configure SAML tab and fill out Attribute Statements and Group Attribute Statements (this step is optional).
- Here’s how you can populate these fields:
Follow the steps provided below:

| Single Sign On URL | Enter ACS (Assertion Consumer Service) URL from the Service Provider info tab of the plugin. |
| Audience URI (SP Entity ID) | Enter SP Entity ID/Issuer from the Service Provider info (or SP Information) tab of the module. |
| Default Relay State | Enter Relay State from the Service Provider info tab of the module. |
| Name ID Format | Select EmailAddress as the Name ID Format from the dropdown list. |
| Application Username | Set Application Username to Okta username. |
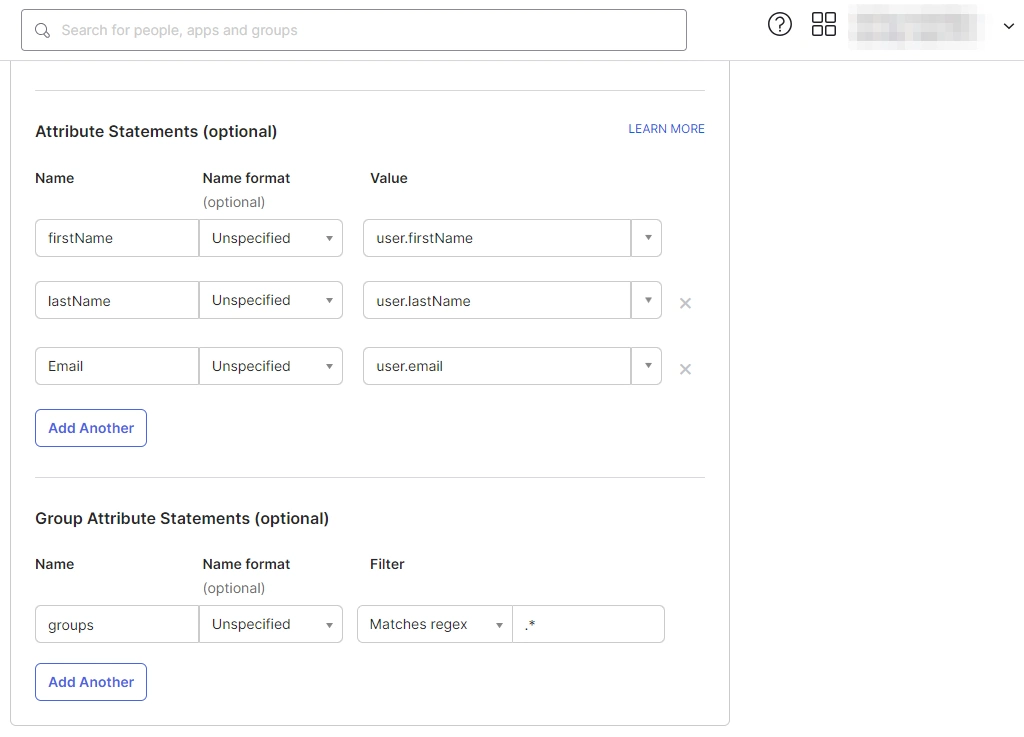
a. For Name, enter "firstName" and select user.firstName from the value dropdown.
b. For Name, enter "lastName" and select user.lastName from the value dropdown.
c. For Name, enter "Email" and select user.email from the value dropdown.
d. Under Group Attribute Statements, enter "groups" for Name and select Matches regex from the Filter dropdown and enter ".*" in the adjacent textbox.
 1.2: Assigning Groups/People
1.2: Assigning Groups/People
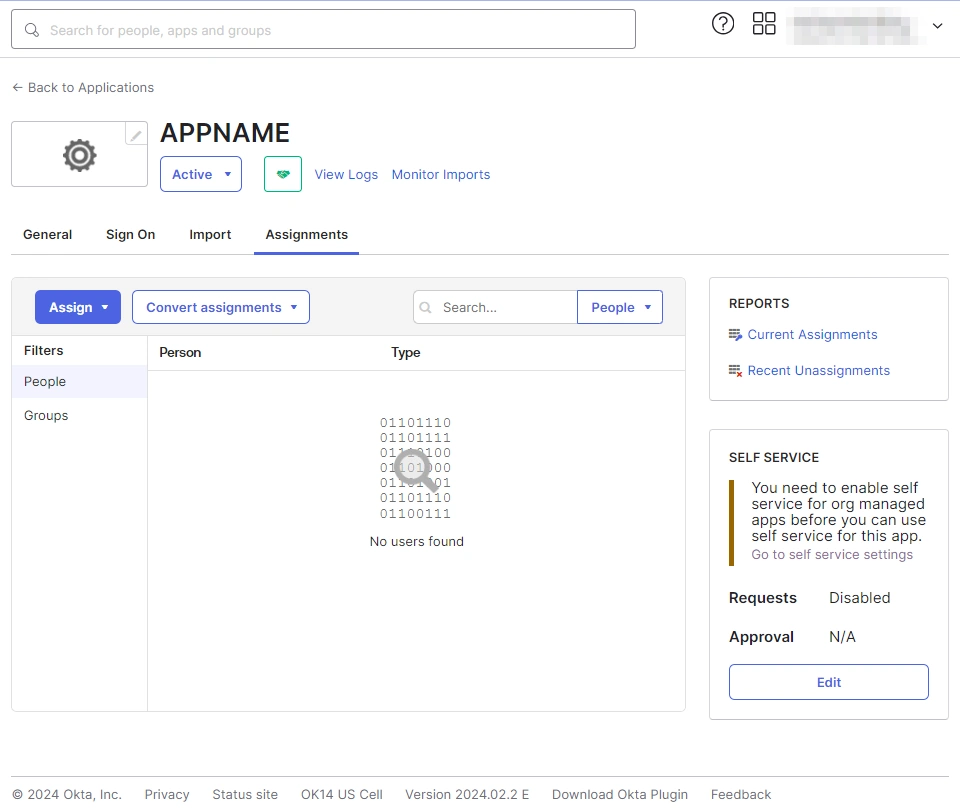
- After creating and configuring the app, you will be redirected to the Assignment Tab in Okta.
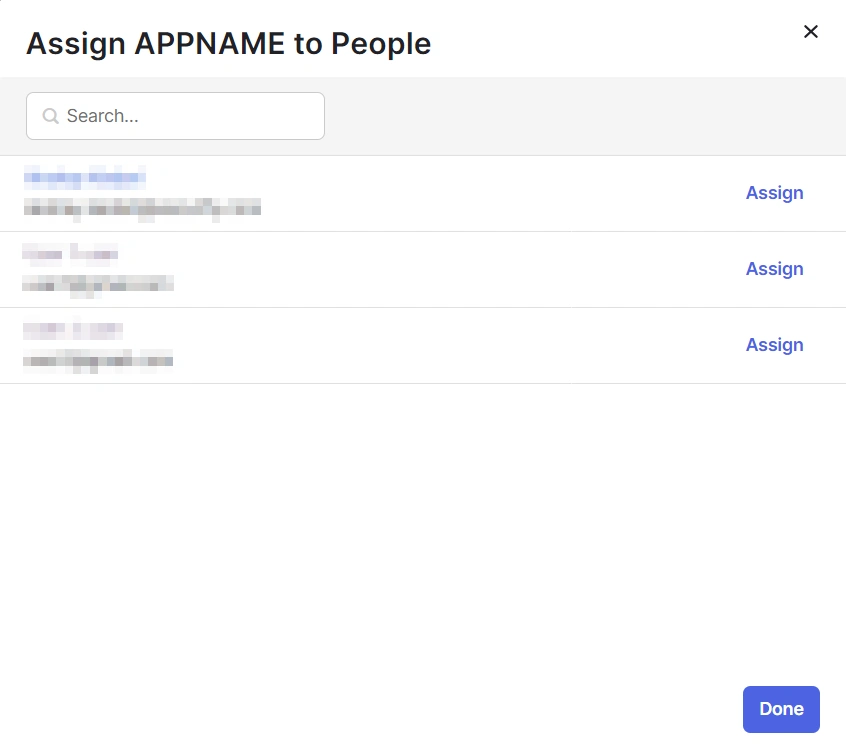
- Here, select the people and groups that you want to be able to log in through the app. You can do this by clicking Assign and selecting Assign to People to give access to specific people.
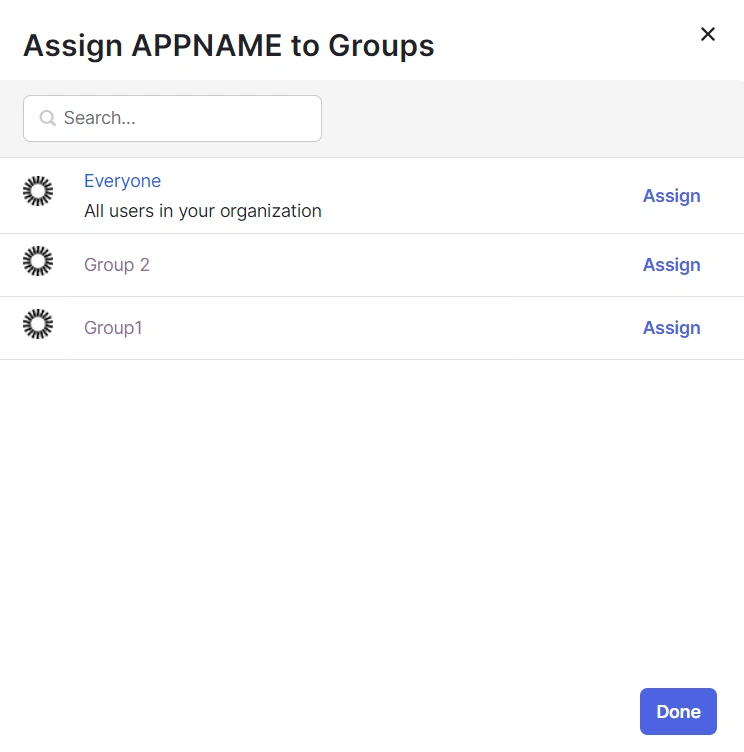
- You can also select Assign to Groups to give access to a specific group.
- Once you’re done assigning people and groups to your app, go to the Sign On tab.
- Here, click on View Setup Instructions to get the SAML Login URL (Single Sign on URL), Single Logout URL, IDP Entity ID, and X.509 Certificate. You will need these to configure the Service Provider.
 1.3: Fetching Metadata URL
1.3: Fetching Metadata URL
- Log into your Okta Admin Console
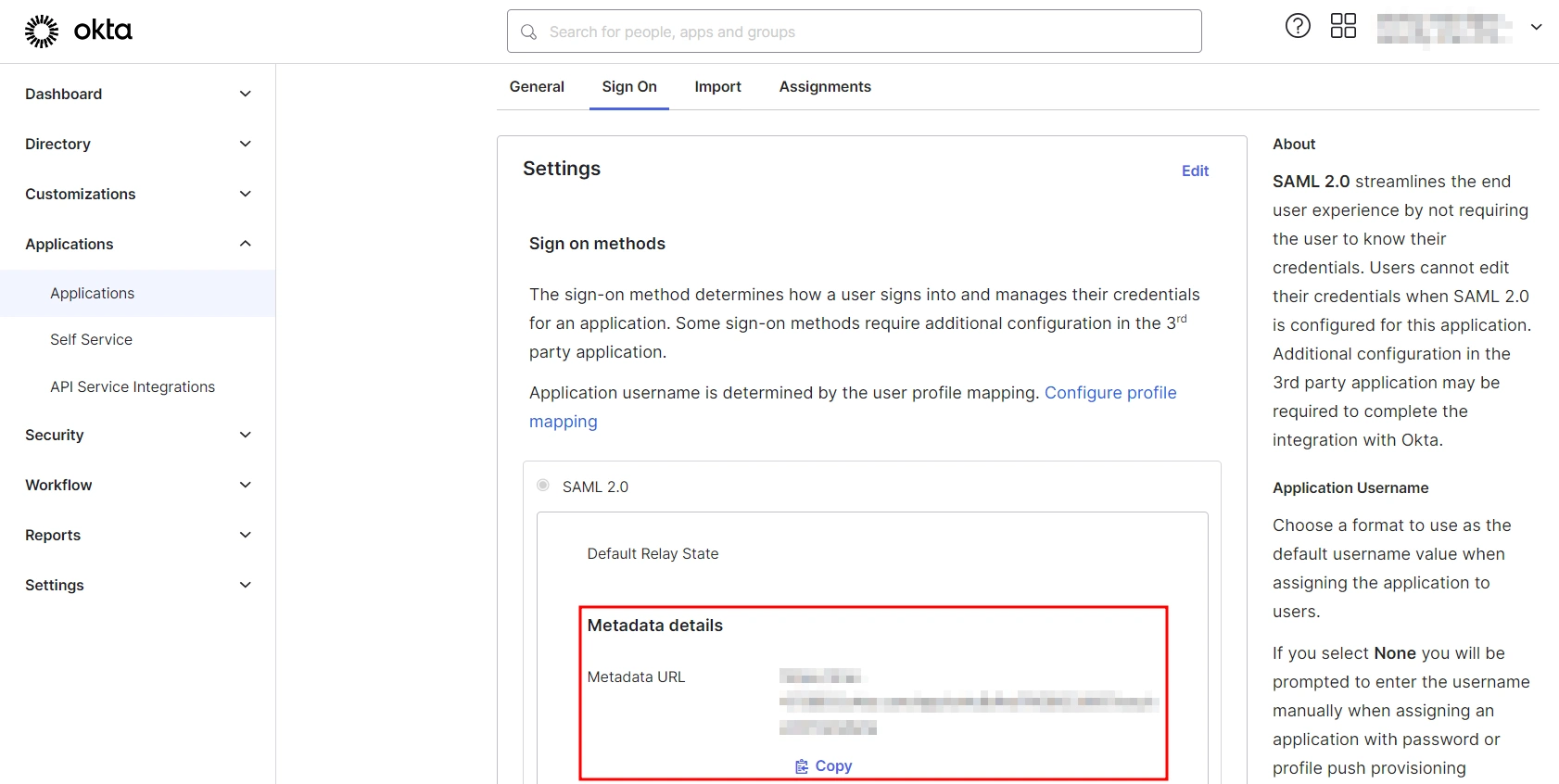
- Navigate to Applications → [Your Application Name] → Sign On
- You will find the metadata URL under the Metadata details section.
- You can either leave this window open in another tab or copy and paste the URL to a note while setting up the service provider.
One important component you’ll require while setting up your service provider is the metadata URL of your Identity Provider.
You can follow these steps to find the metadata URL for your Okta Application:
Step 2: Set Up SonarQube as Service Provider
 Fetch the Identity Provider (IdP) Details
Fetch the Identity Provider (IdP) Details
- After configuring the IdP, get its metadata to configure SonarQube as a Service Provider(SP).
-
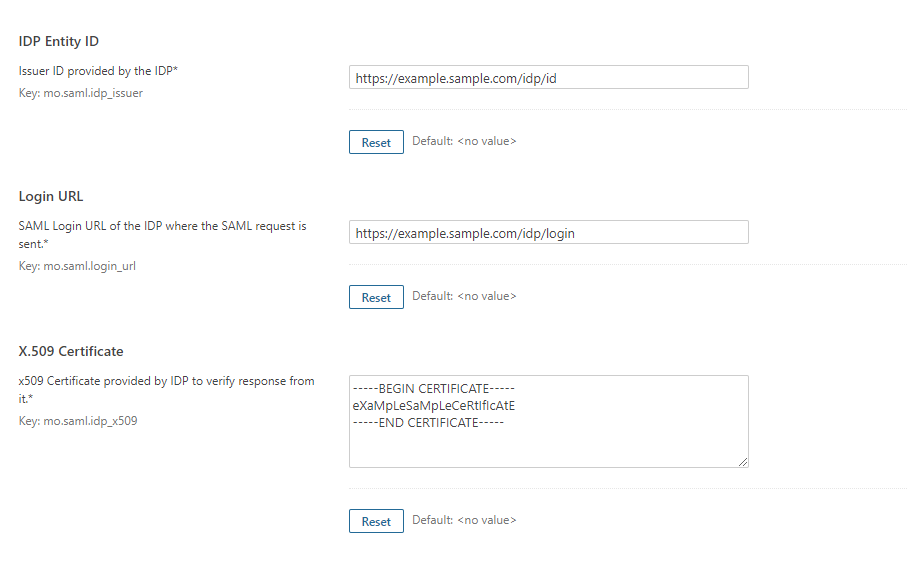
Copy the following details from the IdP metadata and paste them
into the corresponding text fields in the SonarQube plugin.
- IdP Entity ID
- Login URL
- X.509 Certificate
- Save all the details.
 Test Configuration
Test Configuration
- Once you have filled all the IdP details, go to Administration >>Configuration >>miniOrange SAML Support and then click on the Test Configuration tab.
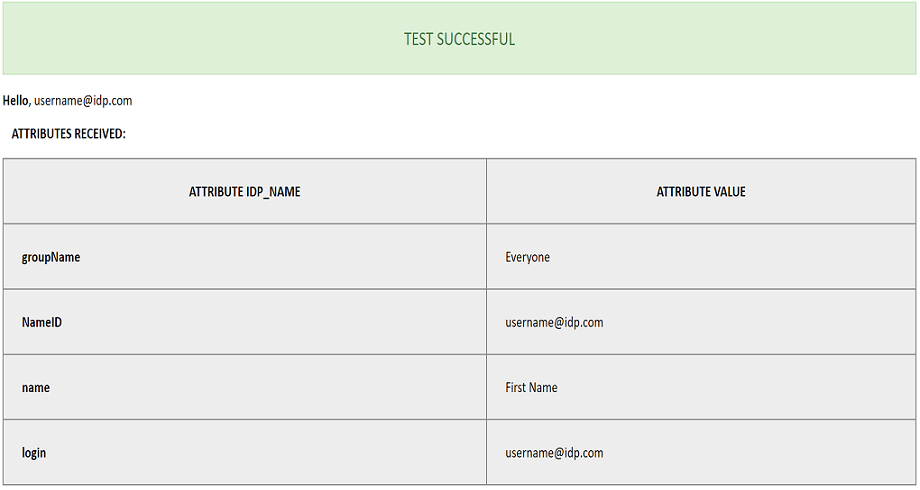
- It will show you the IdP login page. Enter your IdP credentials and log in.
- If all the configurations are correct, it will show you the user details received from the IdP.
- If the test fails, check if you have missed out any steps or try to debug through SonarQube .
- To be able to troubleshoot through logs, first you'll have to set a higher log level in your SonarQube application.
- To do so, go to the SonarQube Dashboard >> Administration >> System.
- Under the system settings, you'll find an option to change the log's level. Select DEBUG and save it. Now try to configure the plugin.
- If you face any problem during configuration, go to %SONARQUBE_HOME% / logs directory.
- Find and open the web.log file. Go through the logs recorded.
- You'll find the stacktrace of performed actions, along with date and time information.
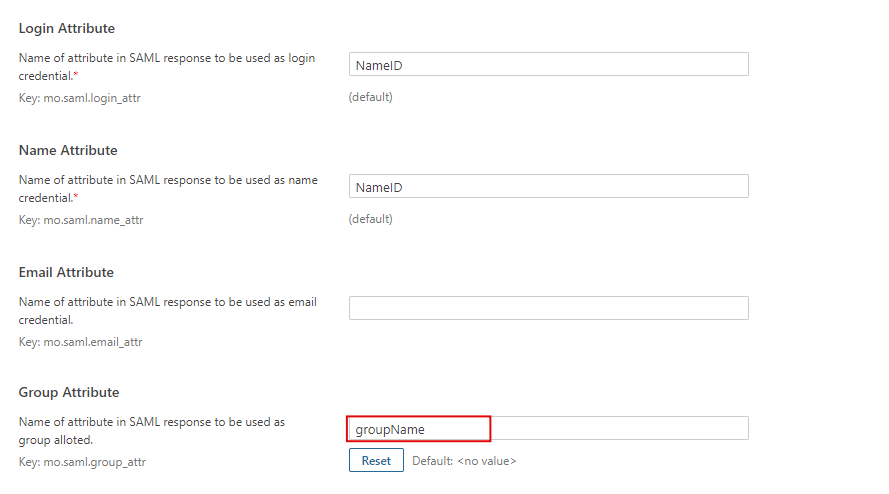
 Attribute & Group Mapping
Attribute & Group Mapping
- In order to map attributes from the Identity Provider to the application, the attribute names received in the SAML response need to be entered in their corresponding fields.
- To view these attribute names, click on the Test Configuration tab in the plugin support page.
-
Attributes used in SonarQube Application are described briefly as
below:
- Login Attribute is a unique name assigned to the user to identify them uniquely within the SonarQube system. It's a required attribute.
- Name Attribute is the full name of the user, to be mapped from the IdP to the SonarQube. It's a required attribute.
- Email Attribute is an optional attribute and represents an email address of the user, to be mapped from the IdP to the SonarQube.
- Group Attribute mapping requires the group names, in the application, to be same as the group names in the Identity Provider. Otherwise, the default SonarQube Group is assigned to the user.
- Eg. To map group value Everyone from SAML response we have to paste groupName in Group Attribute field.
Additional Resources
Did this page help you?


 Try it for free
Try it for free