Our blogs

IAM
What is Identity and Access Management (IAM)?
Sep 26, 2025
MDM
Lockdown Android Tablet for Business with miniOrange MDM
Feb 17, 2026
PAM
Top 10 Benefits of Privileged Access Management (PAM)
Aug 20, 2025
Concepts
What is the Difference Between SAML vs OAuth vs OpenID Connect?
Aug 14, 2025
concepts
Zero Trust Security Model: Complete Guide to Implementation in 2025
Jul 1, 2025
Latest Posts

IAM
Prompt Injection Attacks: Why AI Security Starts with IAM
Feb 26, 2026

MDM
UEM vs. EMM: What’s The Difference?
Feb 25, 2026

MDM
What Is Kiosk Mode and How Does It Work?
Feb 25, 2026

DLP
Blocking USB Devices and Whitelisting Authorized Peripherals with DLP
Feb 23, 2026

Atlassian
How a SaaS Company Cut Access Provisioning Time with Access Governance
Feb 23, 2026
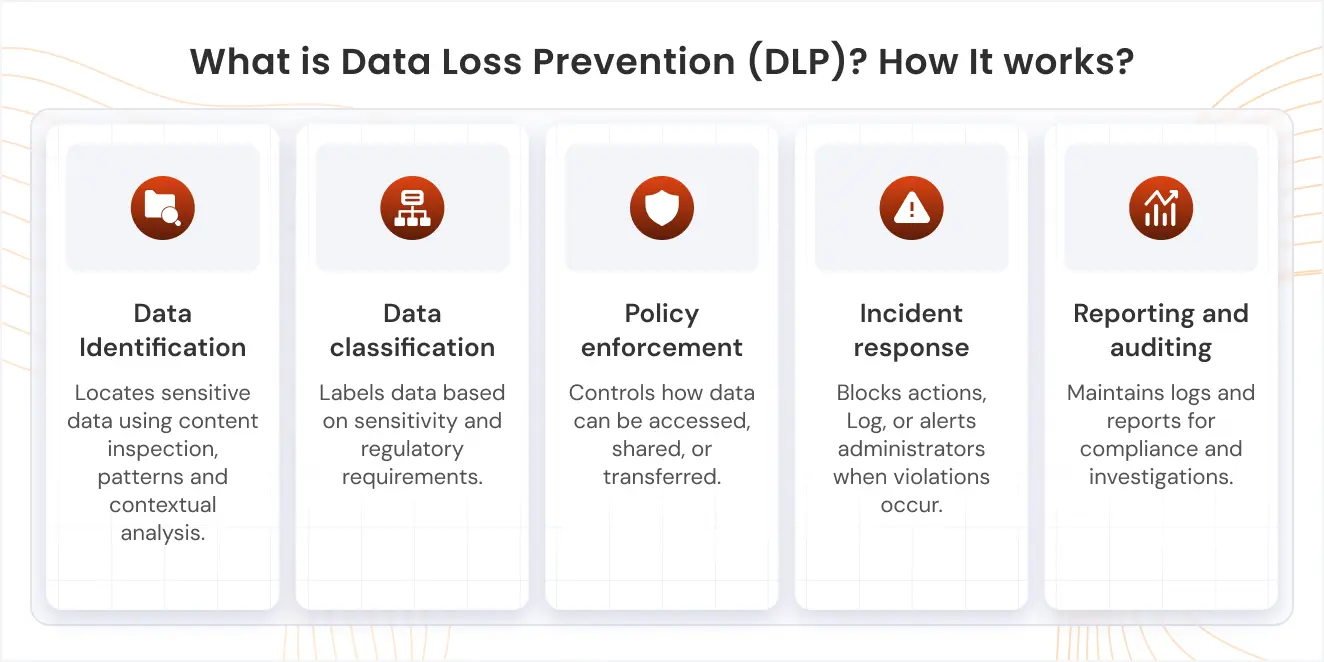
DLP
Difference between Network DLP vs Endpoint DLP vs Cloud DLP
Feb 23, 2026

