
IAM
Two-Factor Authentication – 2FA Security
Oct 21, 2022

IAM
5 Reasons to Deploy Context-Based Authentication
May 12, 2022

IAM
A Comprehensive Guide to Implement AAA with TACACS Server for Enterprise Networks
Sep 26, 2023

IAM
Adobe Connect Single Sign-On with HTTP Header Authentication
Sep 4, 2023
iam
Unlocking Seamless Transitions with App-to-App SSO
Oct 9, 2024

IAM
Authorization Code Flow with Proof Key for Code Exchange (PKCE)
Dec 26, 2022

IAM
What is the difference between Authentication and Authorization?
Dec 29, 2022
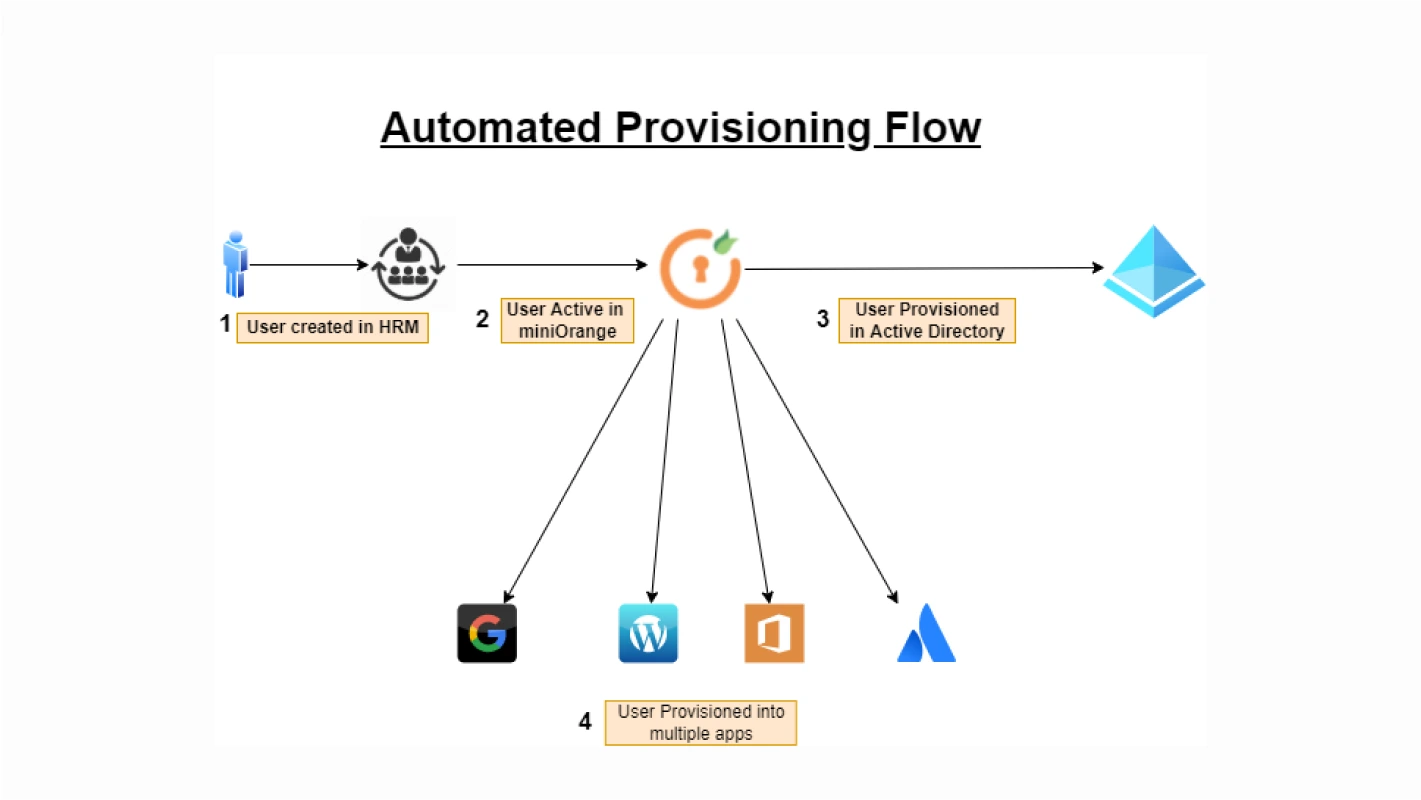
IAM
Automated Provisioning | 4 main benefits of Automated User Provisioning
May 12, 2022

IAM
Azure Active Directory SSO for Enterpises | Azure AD Integration
Feb 17, 2022

IAM
Organizations are moving to modern authentication, and why should you too?
Jan 27, 2022

IAM
Switching to Headless System – What’s in it for you?
May 12, 2022
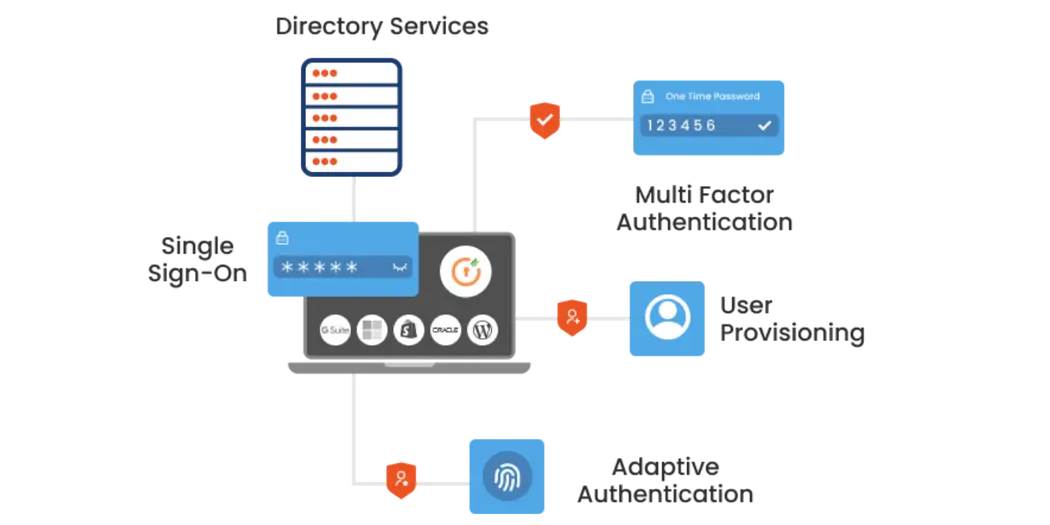
IAM
5 Best IAM Tools for Better Identity Security in 2025
Dec 30, 2022

IAM
The Importance of Centralized Identity Management
Oct 22, 2024
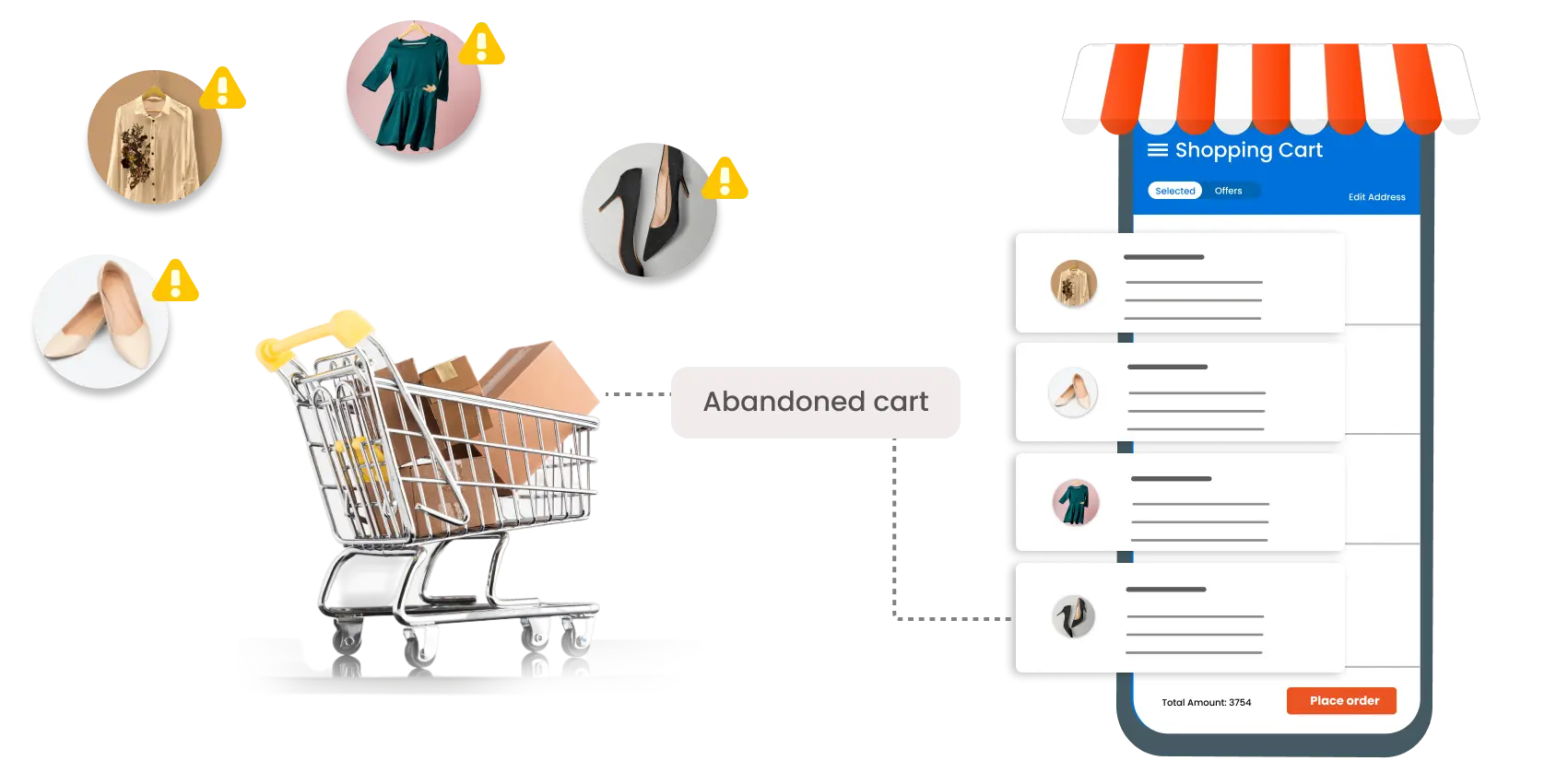
iam
How CIAM Can Prevent Abandoned Carts for Ecommerce Businesses
Jul 29, 2024

IAM
IAM vs. CIAM - What’s the difference?
Jan 8, 2024

IAM
Setting up OTP Verification for Oracle cloud application security
Sep 4, 2023

IAM
Custom Database Connection
May 12, 2022
IAM
Crowd User Management at your fingertips
May 12, 2022

IAM
Do you have an IAM setup? Cybersecurity Awareness Month, Focuses on how and where IAM is used
Dec 26, 2022

IAM
What is a DDoS Attack and how can you protect DDoS Attack?
Sep 4, 2023

IAM
What is Authentication? Different Types of Authentication
Dec 29, 2022

IAM
Duo push notification and webauthn as 2FA for atlassian apps
Nov 30, 2022
IAM
What is Enterprise Identity Management(EIM)?
Sep 11, 2024

IAM
Enterprise SSO – What is Enterprise Single Sign-On?
Oct 4, 2022

IAM
Know Everything About Biometric Authentication
May 12, 2022

IAM
What is Federated Identity Management (FIM) and best practices?
Feb 3, 2023

IAM
What is Federated Single Sign-On (SSO) | Federated Identity Management (FIM)
Aug 25, 2022
IAM
What is FIDO2 Web Authentication, and How Does it Secure Identities?
Sep 11, 2024

IAM
Is your organizations G-Suite access Secure Enough?
Aug 22, 2023
IAM
Google Drive Security for Education: Prevent Unauthorized Sharing
Aug 22, 2023

IAM
10 IAM Best Practices for the Security of Every Enterprise
Mar 30, 2022

IAM
What are Key Identity and Access Management (IAM) Capabilities?
Jan 8, 2025

IAM
5 IAM Controls for Better Protected Systems
Nov 27, 2024
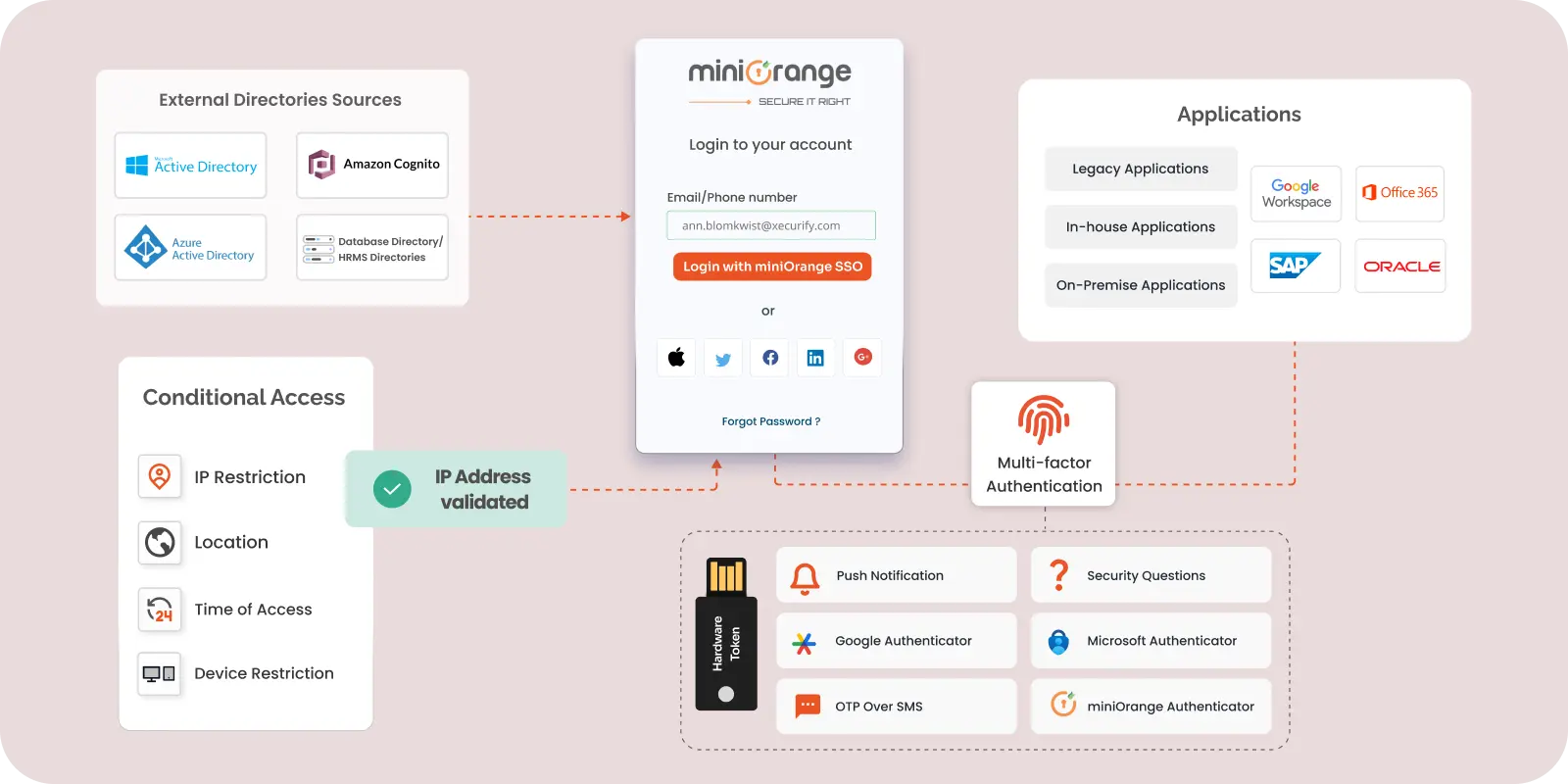
IAM
9 Essential Features for Identity and Access Management (IAM) Solution
Jan 1, 2025

IAM
Building 6 Effective Identity and Access Management (IAM) Strategies
Dec 5, 2024

iam
IAM vs. PAM: What’s the difference?
Sep 25, 2023

IAM
IDAM for Banking and Finance Sector to ensure regulatory compliance
Mar 17, 2023

iam
Identity and Access Management (IAM) Market After Economic Turndown
May 12, 2022

iam
What is Identity Federation Services? How To Secure Applications with SAML and OpenID Connect
Sep 25, 2023

Concepts
SP Initiated SSO vs. IdP Initiated SSO
Jul 9, 2022

IAM
IAM Framework: 5 Key Components
Oct 23, 2024

concepts
LDAP Authentication with Active Directory
Aug 30, 2022

IAM
Migrating from Microsoft Azure Multi-Factor Authentication (MFA) Server
Oct 21, 2022

iam
How to enable secure Mobile App authentication - SSO for Mobile apps
Jul 19, 2023

concepts
Multi-Factor Authentication (MFA) for Active Directory (AD)
Aug 29, 2022
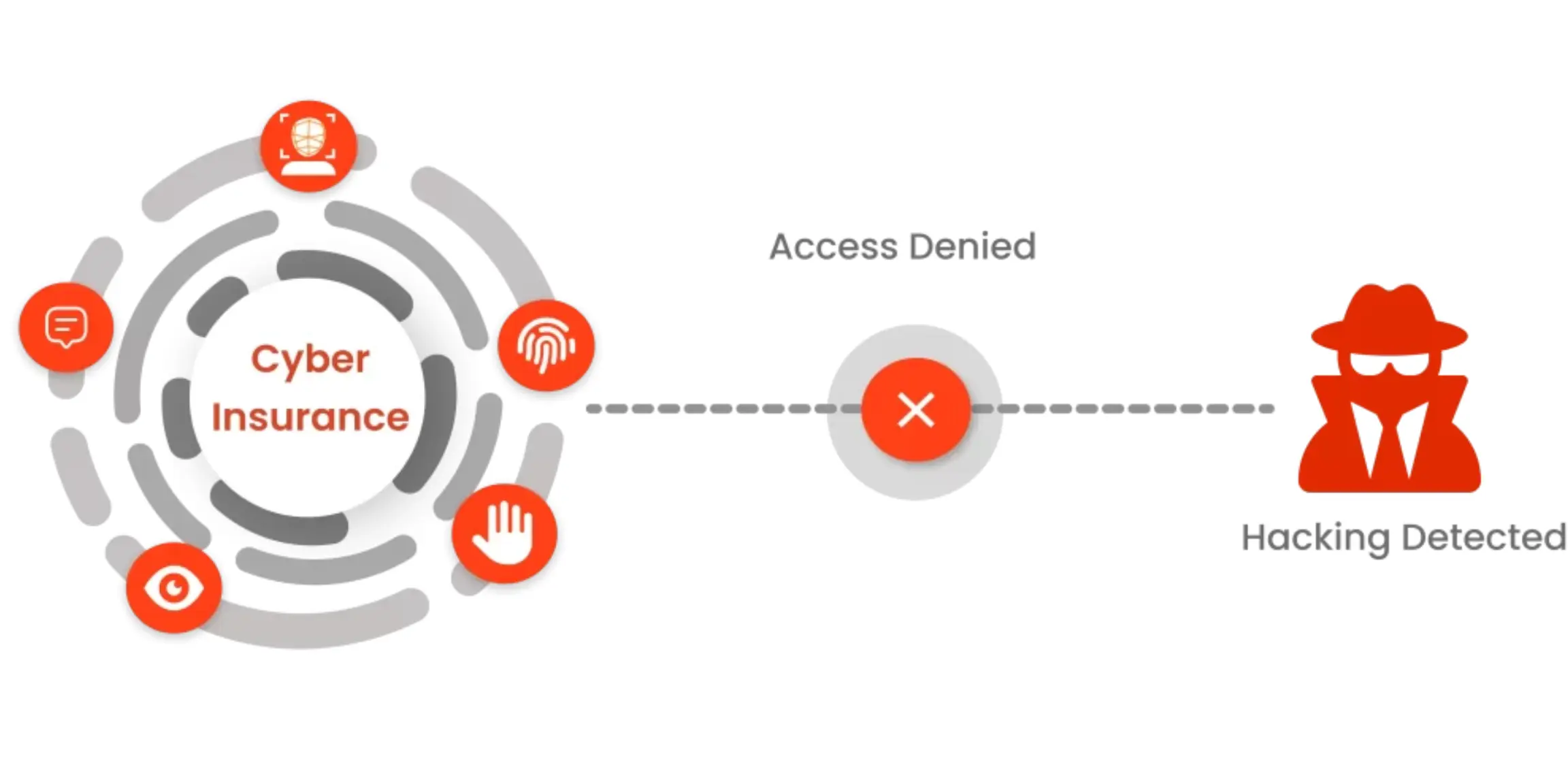
IAM
Everything You Need to Know About Cyber Insurance MFA for Business Protection
Nov 15, 2022

iam
The necessity of Banking Cybersecurity
Mar 1, 2023

IAM
How does miniOrange help organizations to comply with NYDFS Cyber Security Guidelines?
Dec 20, 2022

IAM
Office 365 Multi-Factor Authentication (MFA)
May 29, 2022
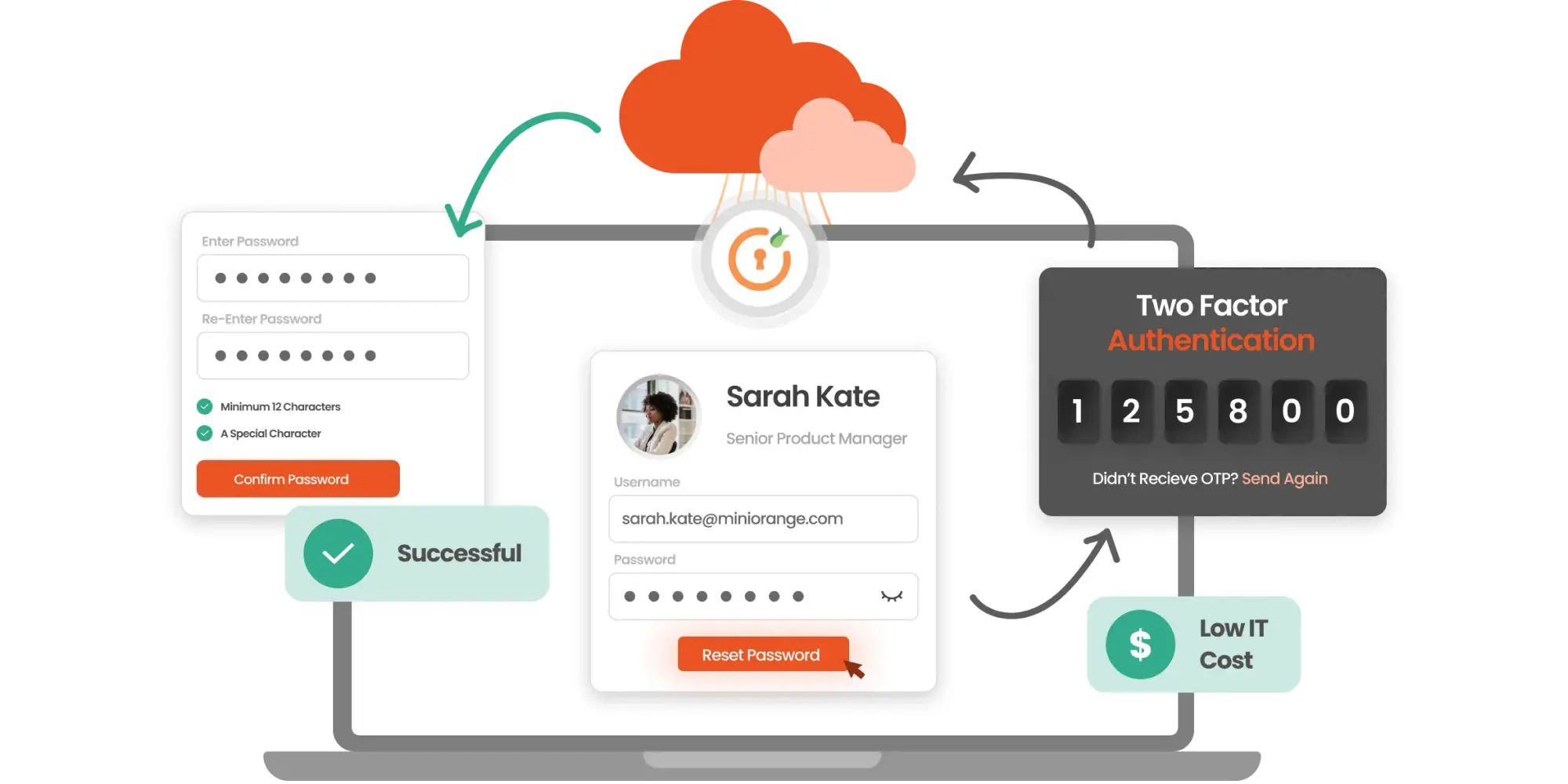
IAM
10 Password Management Best Practices to know in 2024
Sep 12, 2024
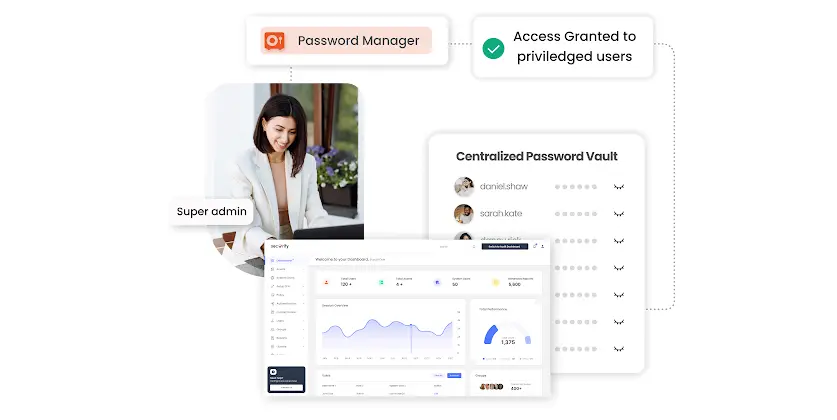
IAM
How to Secure Multiple Passwords with Password Manager and SSO?
Aug 12, 2024

IAM
What is RADIUS Server and how does RADIUS Server Authentication work?
Jul 21, 2022

IAM
RADIUS Vs. TACACS+: What to Choose For Enterprise Networks?
Oct 4, 2023

IAM
How does rate limiting work to protect APIs from DOS attacks?
Apr 20, 2023

IAM
Regulatory Compliance and IT Security in Companies: Understanding Article 89 of the Securities Law 2019
Jun 19, 2024
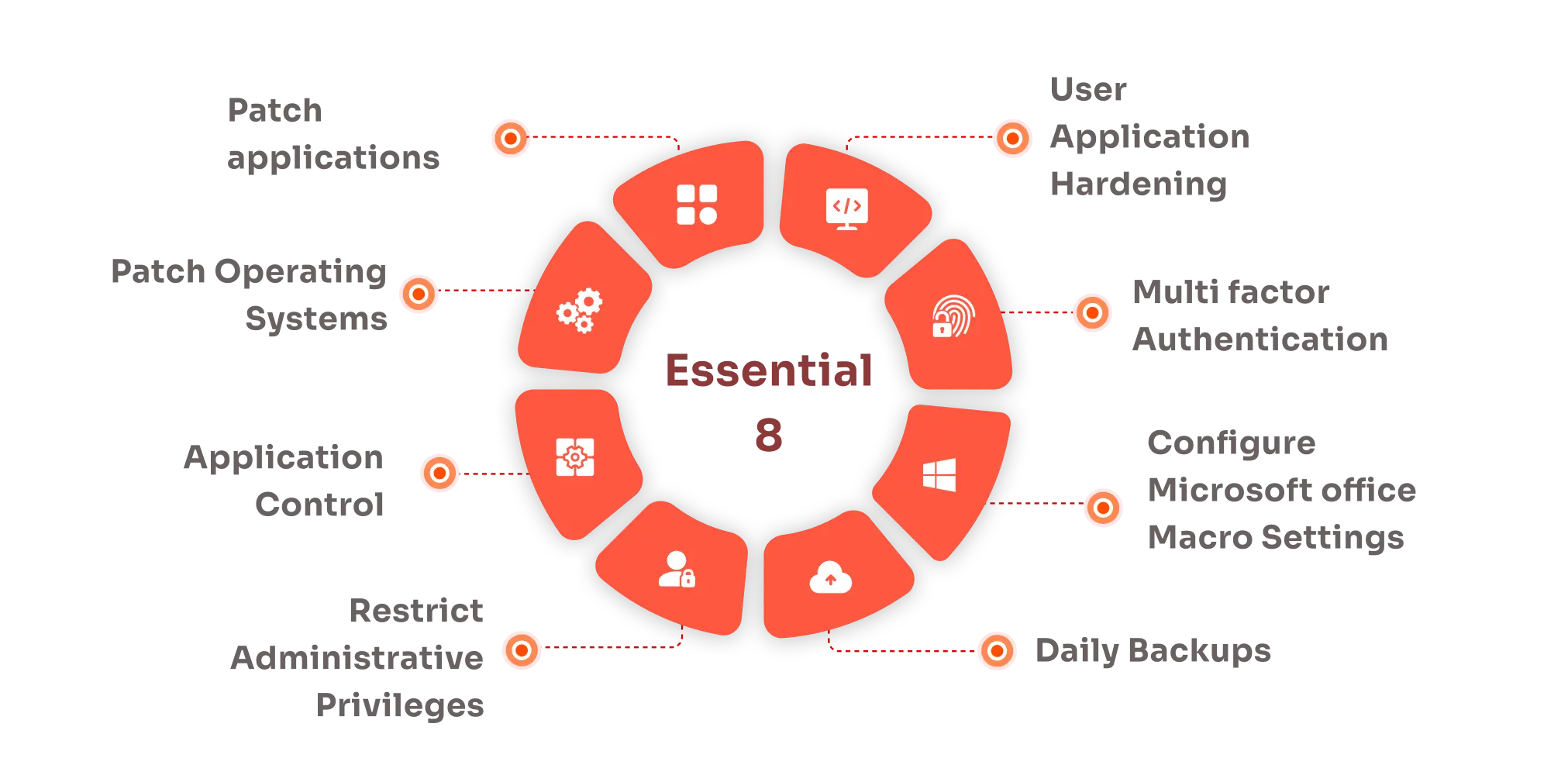
IAM
Restrict Administrative Privileges For ACSC Essential Eight Maturity Model
Jul 3, 2024
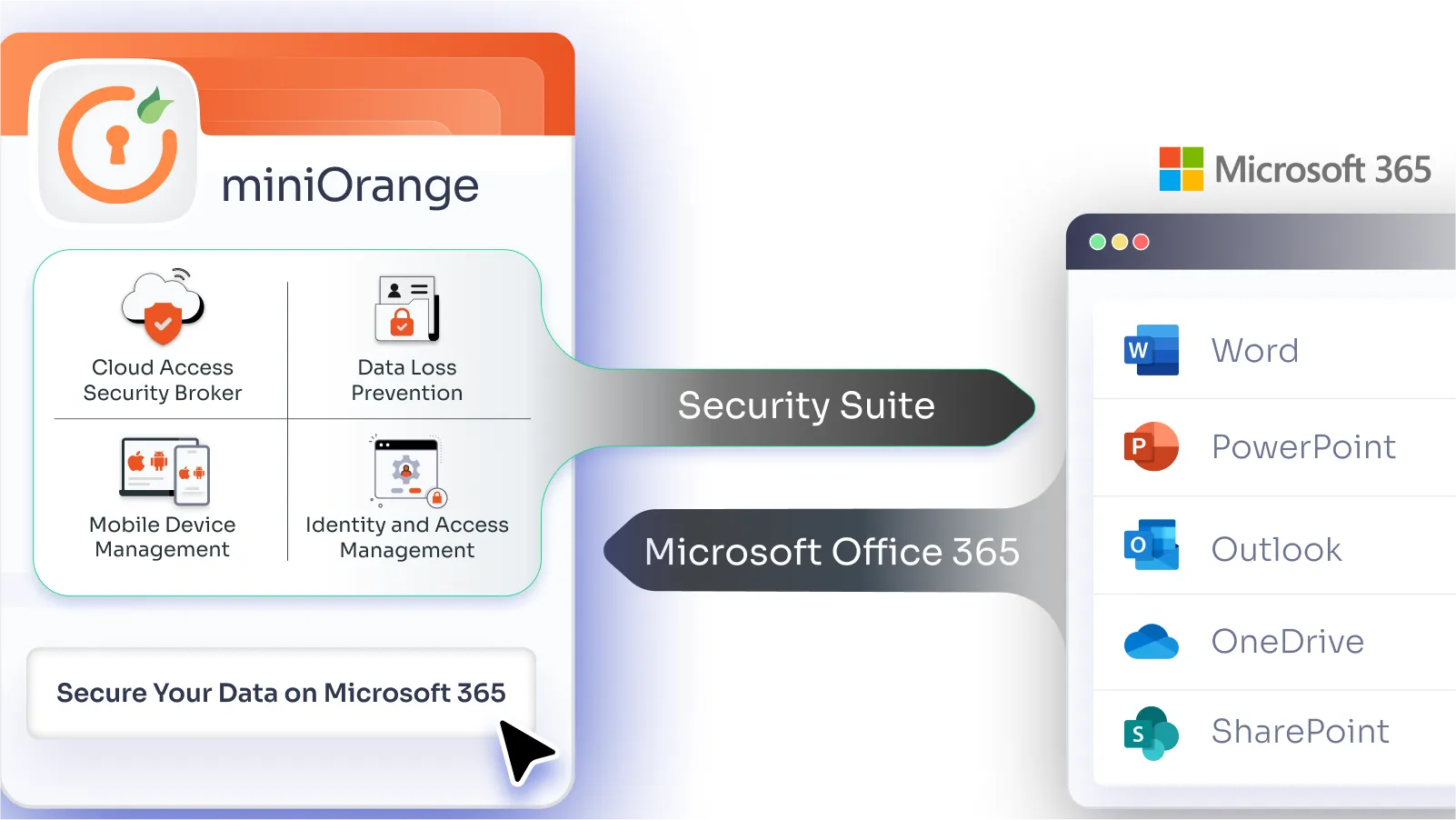
IAM
How to Secure Your Data on Microsoft Office 365 Apps?
Jun 28, 2024

IAM
Salesforce Multi-factor Authentication | Salesforce MFA
May 12, 2022

IAM
How to secure G-Suite apps with IP restriction?
Aug 22, 2023

IAM
Secure your Remote Work Future with Zoom Single Sign-On (SSO)
Mar 14, 2022

IAM
Secure VPN with Multi-Factor Authentication
Feb 26, 2023

IAM
Securing Your Jenkins Pipeline with miniOrange Two-Factor Authentication (2FA)
Apr 8, 2024

iam
What are Single Sign-On (SSO) Examples?
Dec 11, 2024

IAM
Implementing SSO Support For Enterprise Apps
Jul 1, 2024

iam
6 Best Practices for Implementing SSO for SaaS Authentication in 2024
Oct 23, 2024

IAM
SSO Implementation: Need of the Hour For Modern Enterprises
Sep 13, 2023

IAM
SAML/OAuth SSO for JSM Customers
Oct 1, 2022

IAM
Migrating from RSA Access Manager to miniOrange Identity Platform
Mar 5, 2022

solutions
Thick Client SSO Solution
Nov 7, 2022

IAM
Thinkific Single Sign-On (SSO): Secure Best Online Course Platform
Oct 21, 2022

IAM
VPN Security: How 2FA helps to secure your VPN?
Mar 10, 2022

IAM
Want extra features on top of Native SSO?
Nov 8, 2022

IAM
Streamlining Access: Exploring the Power of Single Sign-On for Web Applications
Sep 25, 2023
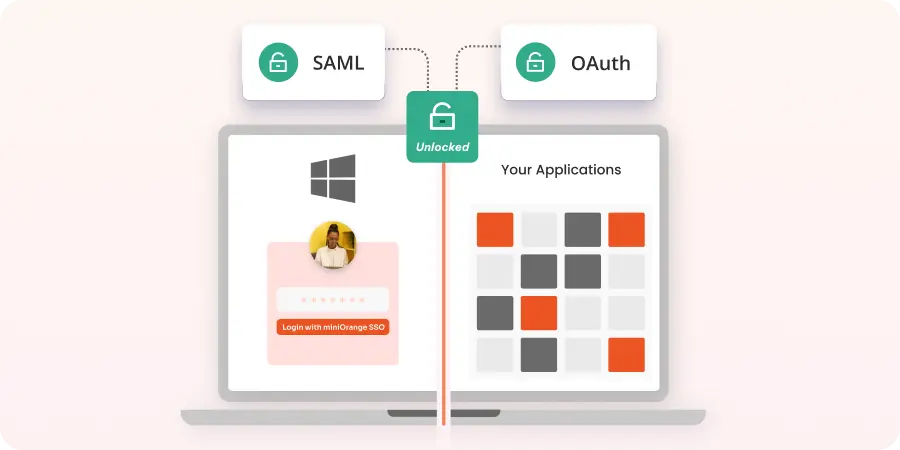
iam
How to Add SSO to Your Website for Enhanced Security
Oct 9, 2024
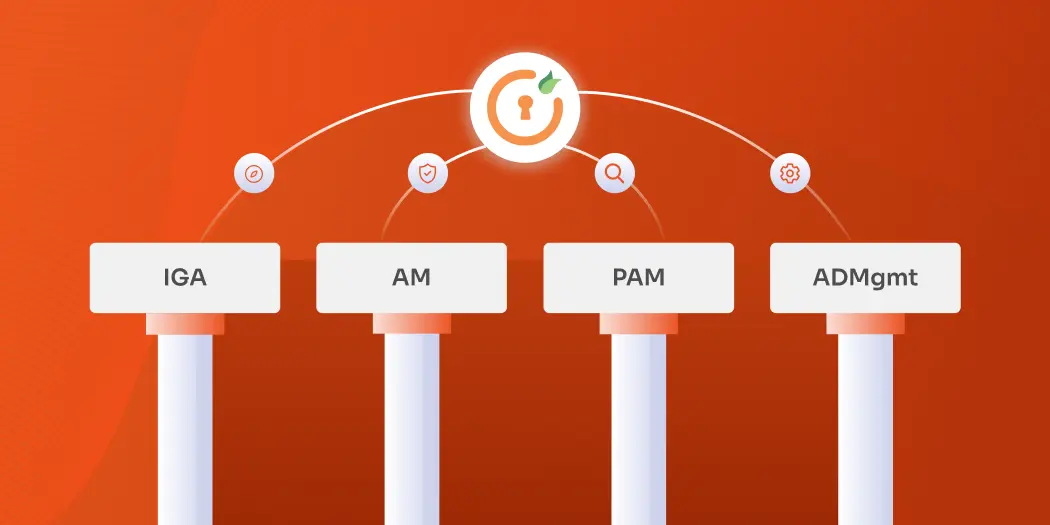
iam
4 Pillars of Identity and Access Management
Oct 18, 2024

concepts
What is a Directory service and Why do you need one?
May 12, 2022
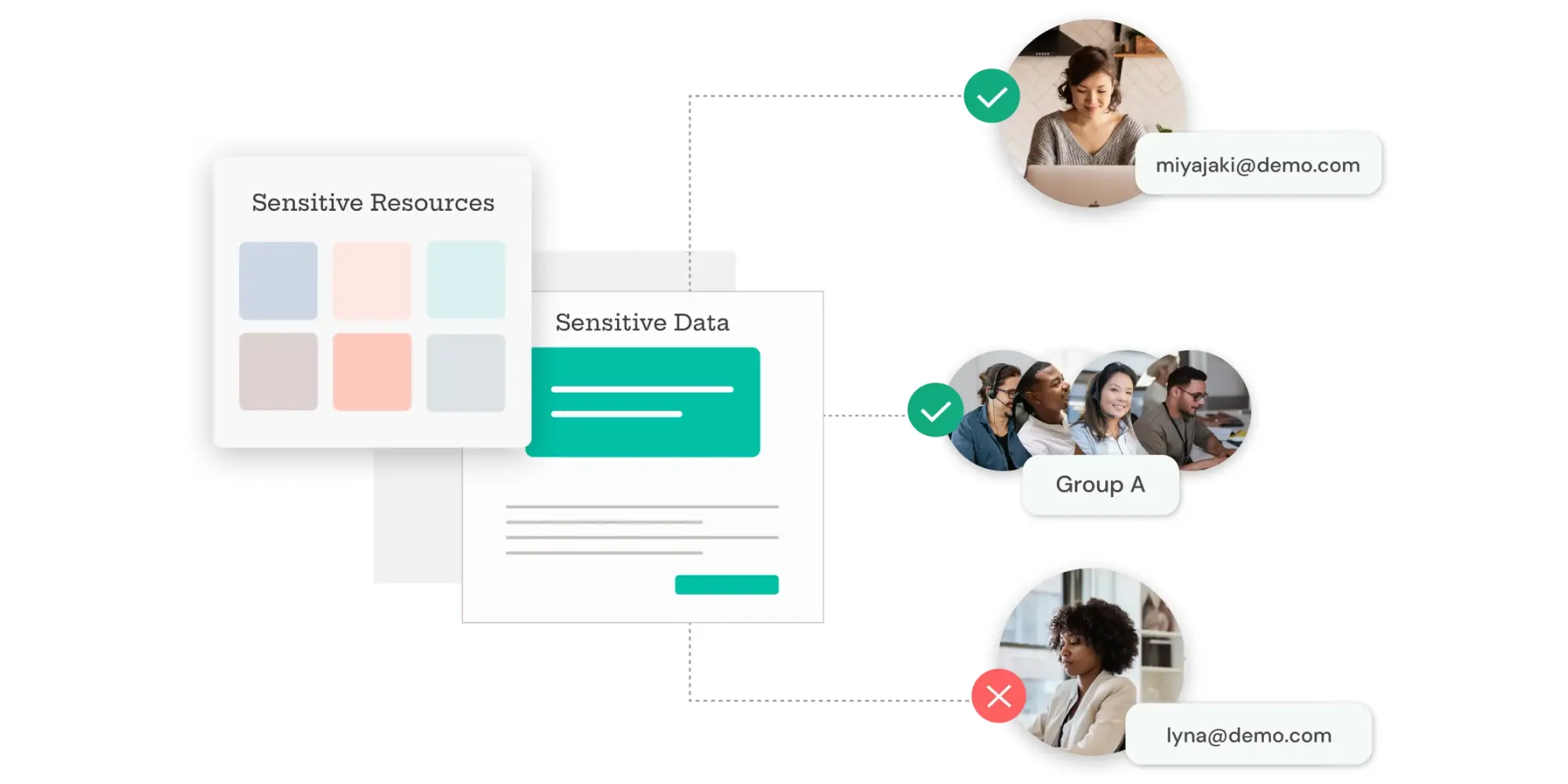
IAM
Why Access Control is Key to Preventing Data Breaches?
Sep 19, 2024

IAM
Understanding Access Management: Risks, Technologies, and Best Practices
Oct 24, 2024

iam
Adaptive Authentication
Jun 19, 2024

concepts
What is ADFS?
Feb 18, 2022

concepts
What is an Identity Provider (IdP)? - miniOrange
May 12, 2022

iam
What is Attribute-Based Access Control (ABAC)? – A Complete Guide
Oct 23, 2024

concepts
What is Azure Active Directory? | Microsoft Azure AD
Feb 17, 2022
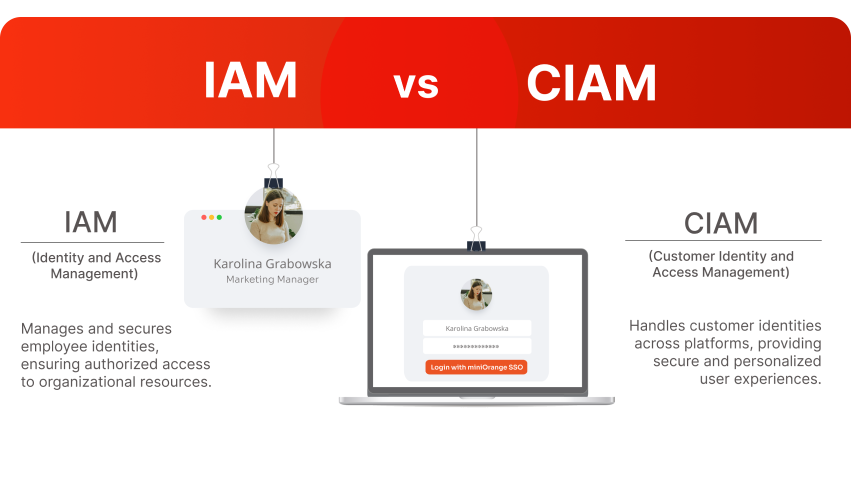
IAM
What is CIAM? Customer Identity and Access Management Solution
Oct 21, 2022

concepts
What is Deprovisioning & why is it important?
Aug 19, 2022

concepts
What is G Suite IP Restriction? Enable IP Restriction for G Suite
May 12, 2022

IAM
What is Identity as a Service (IDaaS)? - Exploring through a comprehensive guide
Mar 30, 2022

IAM
What is JWT (JSON Web Token)? How does JWT Authentication work?
Dec 29, 2022

concepts
Kerberos NTLM Windows SSO
May 12, 2022

concepts
What is LDAP (Lightweight Directory Access Protocol)?
Feb 19, 2022
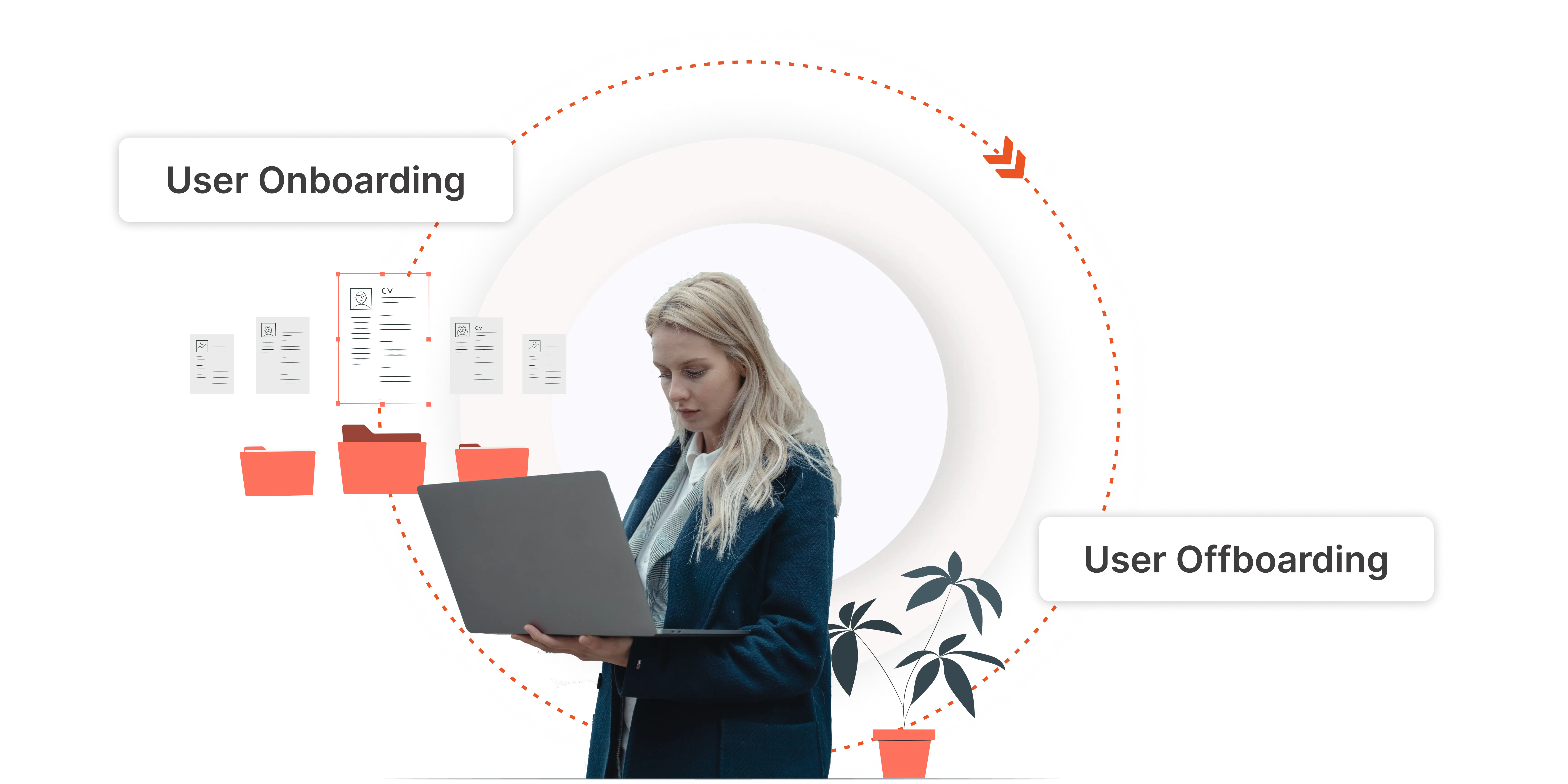
IAM
What is Identity Lifecycle Management?
Oct 21, 2022

concepts
What is Multi-factor Authentication for Improved Identity Security?
Feb 26, 2023

IAM
What is Provisioning and how does it work?
Oct 21, 2022
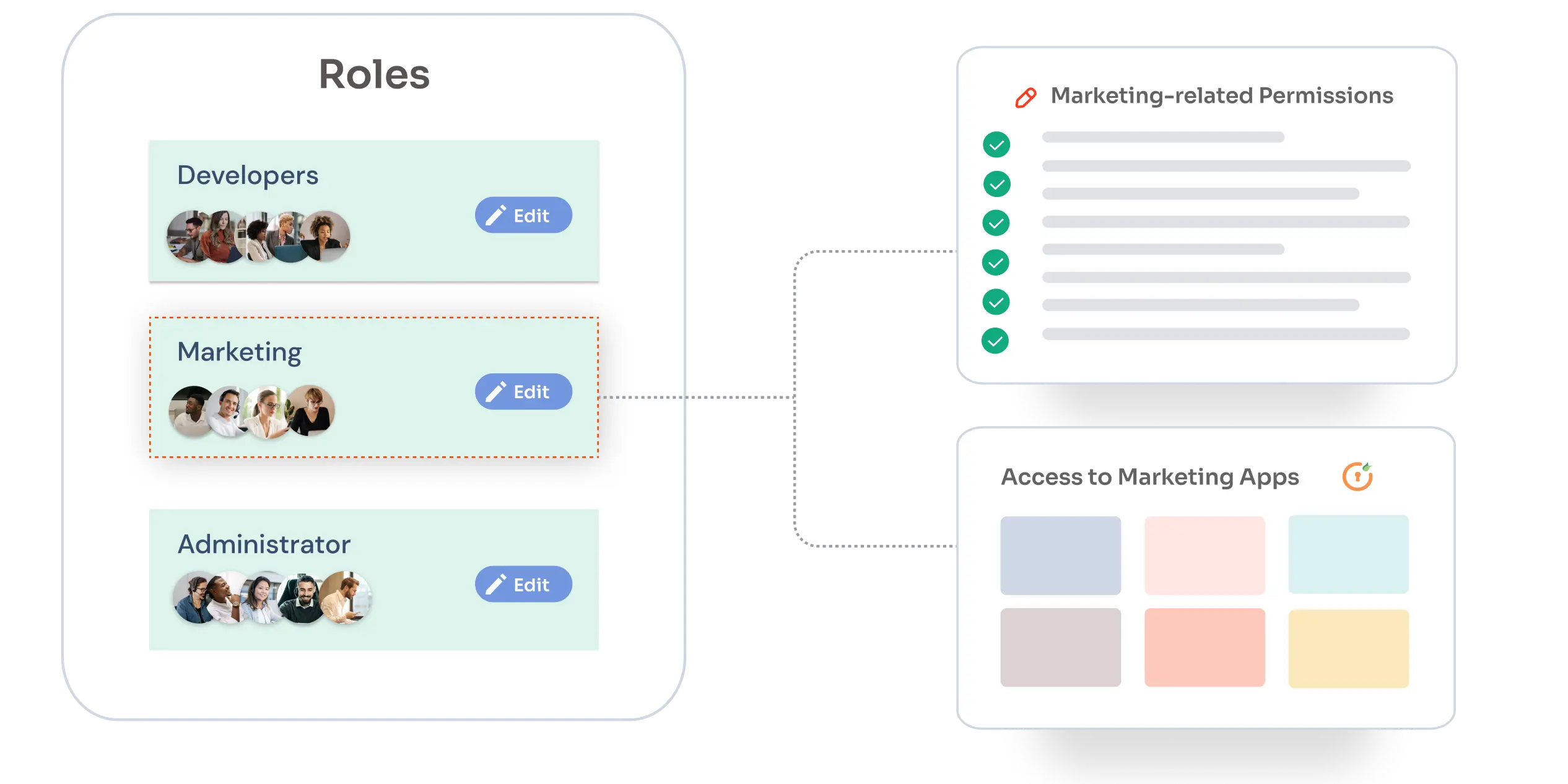
IAM
What is Role Based Access Control (RBAC)?
Jun 27, 2024

IAM
What is Shibboleth?
Dec 23, 2023

concepts
What is Single Sign-On (SSO) and How does SSO Work?
Feb 26, 2023

Concepts
What is the difference between SAML and OAuth?
Apr 7, 2023

iam
Why is Multi-factor Authentication (MFA) necessary for Banks and Financial Institutions?
Jul 22, 2023

iam
5 Reasons Why Your Business Needs Multifactor Authentication
May 12, 2022

concepts
What is Zero Trust Security & How does it work?
May 12, 2022
