As organizations increasingly migrate to the cloud, security concerns have become more critical than ever. According to the World Economic Forum, cyberattacks surged by 50.1% during the pandemic, with cloud platforms emerging as a primary target for cybercriminals. In March 2020 alone, phishing attacks increased by a staggering 600%.
Cloud-based access control has become an essential component of cloud security, enabling organizations to manage and restrict user access to sensitive resources securely.
In this guide, we will explore how cloud-based access control works, its benefits and challenges, and how you can implement it to safeguard your cloud environment.
What is Access Control for Cloud Security?
Securing cloud environments requires strict control over who can access specific resources. Access control systems ensure that permissions are granted only to authorized users, safeguarding critical data and systems.
Access control is divided into two primary categories:
- Physical Access Control: Protects tangible aspects of IT infrastructure, such as buildings and hardware.
- Logical Access Control: Secures digital resources like networks, systems, and data.
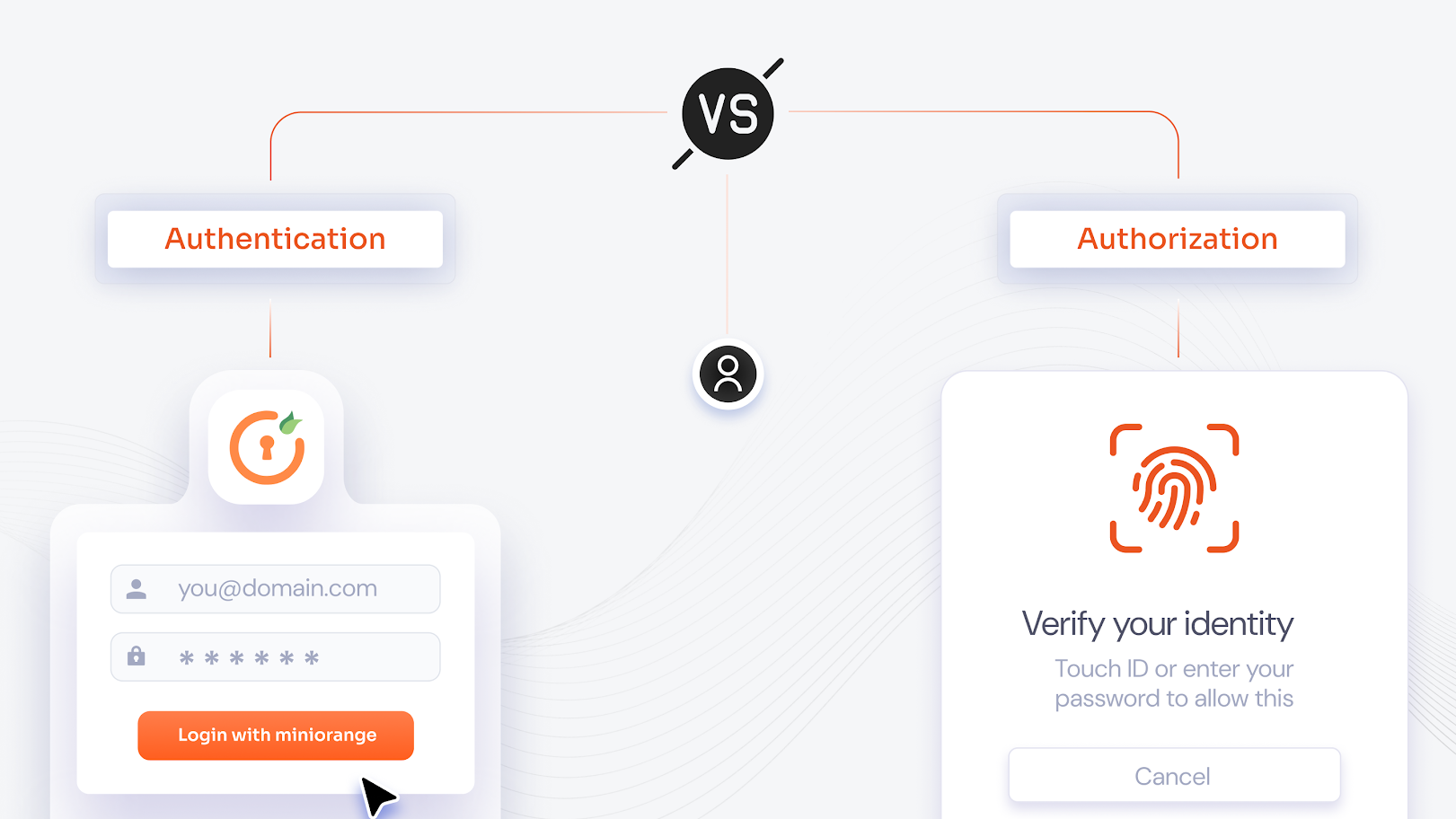
Logical access control is a cornerstone of Identity and Access Management (IAM). It governs how users interact with sensitive digital assets using authentication and authorization protocols. This ensures compliance with frameworks like the NIST Cybersecurity Framework and PCI DSS, which mandate robust access control measures to protect sensitive information.
How Access Control Works?
Access control systems identify and authenticate users or entities, ensuring they are who they claim to be, and then authorize the appropriate level of access to resources. This process is supported by directory services and protocols like Lightweight Directory Access Protocol (LDAP) and Security Assertion Markup Language (SAML), which help manage and verify user identities. The enforcement of these rules is done through different access control models, each designed to meet varying security requirements.
Here’s a breakdown of the key types of access control models:
Mandatory Access Control (MAC)
- Centralized control: Access is determined by the system, not the user.
- Security labels: Resources are classified (e.g., "Top Secret"), and access is based on security clearance.
- Strict enforcement: Users cannot modify permissions; access is rigidly controlled.
- Use cases: Primarily used in high-security environments like military or government systems.
Discretionary Access Control (DAC)
- User-based control: Resource owners assign access permissions to other users.
- Flexibility: Owners can grant or revoke rights, such as read, write, or execute.
- Potential risks: Increased vulnerability due to the reliance on users to manage permissions.
- Common use: File-level access control in operating systems like Linux and Windows.
Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is a model where access to resources is determined by the roles assigned to users, such as admin, HR, or employee. This system streamlines the management of permissions, as roles are tied to specific sets of access rights, rather than assigning individual permissions to each user.
RBAC is particularly efficient for businesses with well-established roles and functions, ensuring that users only have access to the resources necessary for their jobs. This approach enhances security by reducing the chances of unauthorized access and minimizes administrative overhead in managing permissions.
Rule-Based Access Control (RBAC extension)
- Contextual rules: Defines access based on conditions like time, IP address, or device type.
- Conditional access: Ensures access policies are flexible and responsive to environmental factors.
Attribute-Based Access Control (ABAC)
- Granular permissions: Access is granted based on attributes like user, location, device, or time.
- Dynamic and adaptable: Best suited for modern, cloud-based systems with complex access scenarios.
How to Implement Access Control?
Implementing access control is essential for safeguarding sensitive resources and ensuring that only authorized individuals can access critical systems and data. By establishing clear policies, selecting appropriate models, and utilizing tools like IAM, LDAP, and SAML, organizations can enforce strict access rules.
1. Define Access Control Policies:
Identify critical resources and define who should access them. Set clear access levels based on job roles and enforce security measures such as authentication and access conditions. This ensures consistent and controlled access management across the organization.
2. Choose the Right Access Control Model:
Select an access control model based on organizational needs. Use MAC for strict environments, DAC for flexibility, RBAC for role-based access, and ABAC for dynamic, attribute-based control. Choose the model that best suits your security requirements.
3. Set Up Identity and Access Management (IAM) Tools:
Implement IAM tools that integrate with directory services like LDAP or Active Directory to manage user identities and permissions centrally. Use SSO for simplified authentication and MFA to strengthen security by requiring multiple forms of verification.
4. Assign Roles and Permissions:
Assign roles based on job functions, ensuring users only have access to necessary resources. Apply the Principle of Least Privilege (PoLP) to limit access. Enhance flexibility with RBAC or ABAC to apply conditional or attribute-driven access.
5. Integrate Access Control with Directory Services:
Integrate LDAP or Active Directory for centralized management of user roles and permissions. Use SAML for Single Sign-On (SSO), enabling seamless authentication across multiple systems, reducing complexity while maintaining centralized control and strong security.
6. Monitor and Audit Access:
Continuously monitor access by tracking successful and failed login attempts, and log modifications to critical systems. Regular audits help identify improper access, ensure compliance, and quickly detect unauthorized activities, reducing the risk of security breaches.
7. Review and Update Regularly:
Regularly review and update access policies and roles to reflect organizational changes. Conduct audits to ensure appropriate access permissions and revoke unnecessary access, ensuring compliance with security standards and mitigating new threats. Challenges of Access Control
Dynamically Managing Distributed IT Environments
As organizations adopt cloud services and remote work, managing access across a diverse range of distributed IT environments becomes increasingly complex. This requires integrating various platforms, applications, and networks while ensuring consistent security policies are enforced across all endpoints.
Password Fatigue
Users often struggle with remembering multiple passwords for various systems, leading to password fatigue. This can result in weaker password choices, reuse, or the bypassing of security protocols. Implementing solutions like Single Sign-On (SSO) and Multi-Factor Authentication (MFA) can help mitigate this issue.
Compliance Visibility through Consistent Reporting
Ensuring access control aligns with regulatory requirements is a challenge for organizations, especially with evolving compliance standards. Achieving consistent visibility through automated reporting and audits is critical for monitoring and demonstrating compliance with frameworks like GDPR, PCI DSS, or NIST.
Centralizing User Directories and Avoiding Application-Specific Silos
In many organizations, different applications manage user access independently, creating silos of user data. Centralizing user directories through platforms like Active Directory or LDAP helps streamline user management and reduces complexity, ensuring that access control policies are uniformly applied across all systems.
Data Governance and Visibility through Consistent Reporting
Proper data governance is critical to ensure that sensitive data is accessed only by authorized individuals. Maintaining visibility into access rights and generating consistent, real-time reporting enables organizations to track, audit, and control access to sensitive information, ensuring that data governance policies are upheld.
Although access control for cloud security comes with the aforemention challenges, they can be tackled by access control softwares.
It addresses challenges by centralizing user directories, integrating across distributed environments, and simplifying authentication with tools like SSO and MFA. It ensures compliance through detailed reporting, enhances data governance with consistent policy enforcement, and reduces password fatigue, providing organizations with efficient and secure access management across systems.
Let’s understand how access control software improve cloud security.
Understanding Access Control Softwares
Access control software forms a critical part of a comprehensive Identity and Access Management (IAM) strategy. These tools can be deployed on-premises, in the cloud, or in hybrid environments. Some solutions focus on managing internal access, while others cater to external customer access. Key types of access control software include:
- Reporting and Monitoring Applications: Provide insights into access patterns, detect anomalies, and ensure compliance.
- Password Management Tools: Help reduce password fatigue by securely managing credentials.
- Provisioning Tools: Automate user onboarding and manage access rights efficiently.
- Identity Repositories: Centralize user data for streamlined management.
- Security Policy Enforcement Tools: Ensure consistent implementation of access policies across systems.
Access control is vital for safeguarding organizational resources and ensuring only authorized individuals can access sensitive data.
miniOrange Cloud Based Access Control Solutions
miniOrange provides robust security features to streamline access control and safeguard sensitive resources, ensuring comprehensive protection against unauthorized access:
- IP Restriction: Allows access only from approved IP addresses, preventing unauthorized attempts from unknown or untrusted networks.
- Browser Restriction: Limits access to specified browser types or versions, enhancing security against unsupported or vulnerable browsers.
- Device Restriction: Grants access only from registered or authorized devices, reducing risks from compromised or unknown endpoints.
- Geo-Fencing: Restricts access based on geographical locations, ensuring security by denying login attempts from unauthorized regions.
- Time Restriction: Controls access during specific timeframes, preventing unauthorized access outside designated operational hours.
With these advanced access control features, miniOrange empowers organizations to enforce tailored security policies, meet compliance standards, and maintain seamless yet secure operations.



Leave a Comment