IAM automation is transforming how organizations manage digital identities, significantly enhancing security and operational efficiency. By automating tasks such as user account creation and access level assignments, businesses can reduce manual errors and ensure consistent enforcement of security policies. In fact, studies show that organizations implementing IAM automation can decrease provisioning time by up to 90% and improve compliance with regulations like GDPR and HIPAA. As cyber threats grow, adopting IAM automation not only streamlines processes but also fortifies defenses against unauthorized access, making it a crucial strategy for modern enterprises.
Identity and Access Management (IAM) and Why to Automate it?
Identity and Access Management (IAM) is a crucial framework that helps organizations manage digital identities and control user access to resources. It ensures that the right individuals—employees, contractors, and even devices—have the appropriate access to critical information and systems. IAM protects sensitive data from unauthorized access and helps meet compliance requirements, making it essential for modern businesses operating in diverse environments.
Why Automate IAM?
Automating IAM processes enhances efficiency and security. Automation allows organizations to streamline user onboarding and offboarding, ensuring that access rights are granted or revoked promptly as employees join or leave. This reduces the risk of human error and strengthens security by enforcing strict access controls based on user roles.
Moreover, automation can help identify potential security risks by continuously monitoring user activities and applying policies that adapt to changes in the environment. By automating IAM, organizations can improve productivity, maintain compliance more easily, and focus their IT resources on strategic initiatives rather than routine tasks.
What is IAM Automation?
IAM automation simplifies Identity and Access Management (IAM) by using technology to handle tasks like granting, changing, or removing user access without manual effort. It ensures users get the right access to systems and data securely and efficiently.
Key Elements of IAM Automation:
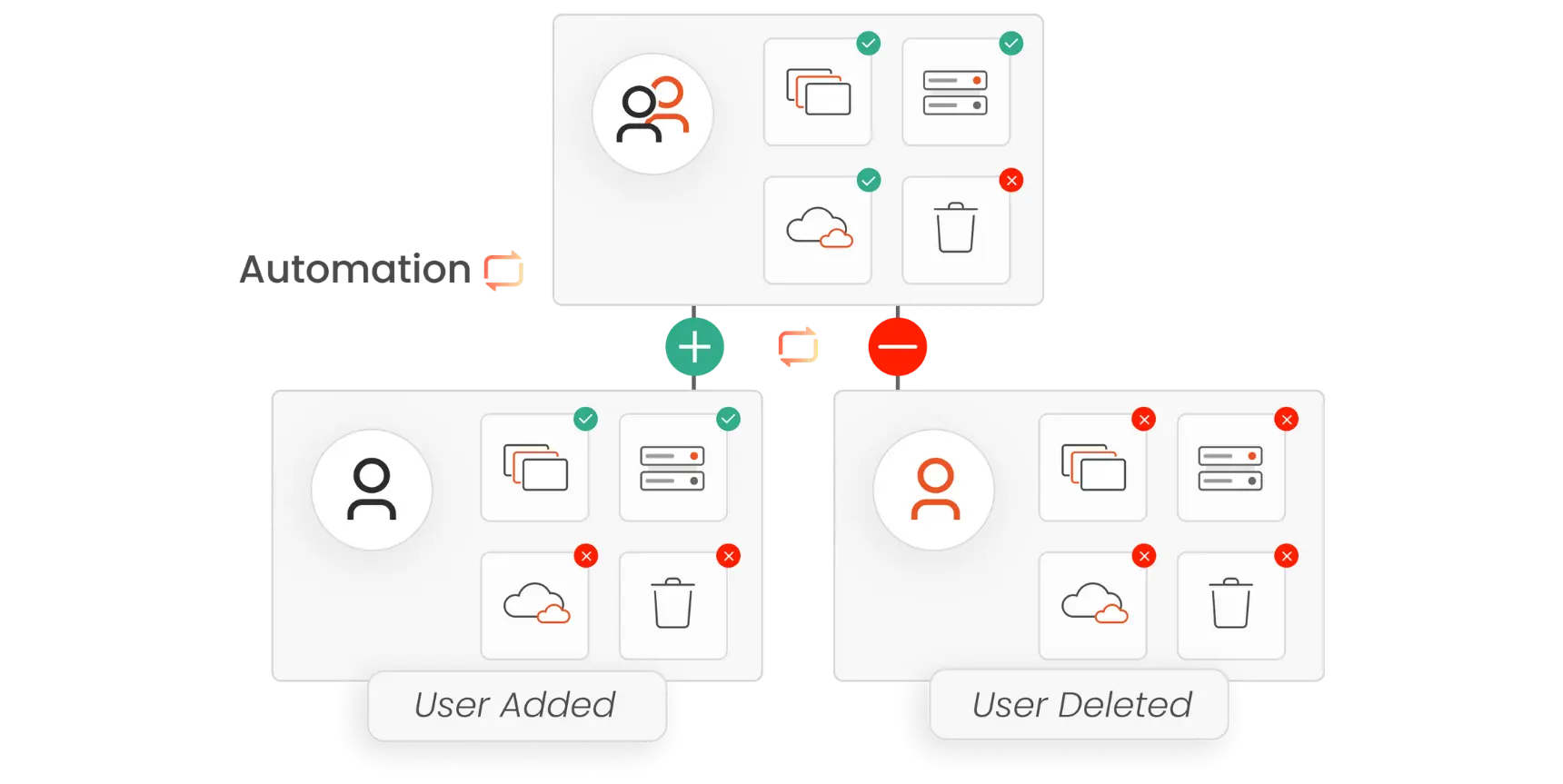
- User Provisioning: Automatically adds new users and assigns them access based on their roles.
- De-provisioning: Quickly removes access when users leave or change roles, reducing security risks.
- Access Requests: Automates approval workflows for granting access to resources, streamlining the process.
- Password Management: Simplifies password resets and enforces secure policies to enhance user experience.
- Access Reviews: Regularly checks and updates user permissions to maintain compliance and ensure users have appropriate access.
- Role Management: Automates the creation and management of user roles, ensuring consistent access rights across the organization.
- Audit Logging: Automatically tracks and records access activities for compliance and security audits, providing a clear trail of who accessed what and when.
Integration with Other Systems: Seamlessly connects with other IT systems (like HR or CRM) to ensure that user data is accurate and up-to-date across platforms. IAM automation saves time, reduces errors, enhances security, and adapts to business needs seamlessly.
Benefits of IAM Automation {benefits-of-iam-automation}
Automation makes Identity and Access Management (IAM) easier and more efficient. It helps organizations manage who can access their systems and data. Here are the main benefits:
- Faster Processes: Automation speeds up tasks like adding or removing users, so people get access quickly.
- Fewer Mistakes: By reducing manual work, automation lowers the chances of errors that can happen when people do things by hand.
- Better Security: Automated systems apply security rules consistently, making it harder for unauthorized users to gain access.
- Cost Savings: With less manual work, companies can save money and focus their resources on more important tasks.
- Easy to Scale: As a company grows, automated IAM can handle more users without needing a lot more staff.
- Adaptability: Automated IAM systems can quickly adjust to changes in business needs, such as new regulations or shifts in user roles, ensuring that security measures remain effective.
In short, IAM automation helps businesses manage user access more effectively, making processes faster, safer, cheaper, and more adaptable.
Key Features of an Ideal IAM Automation Solution
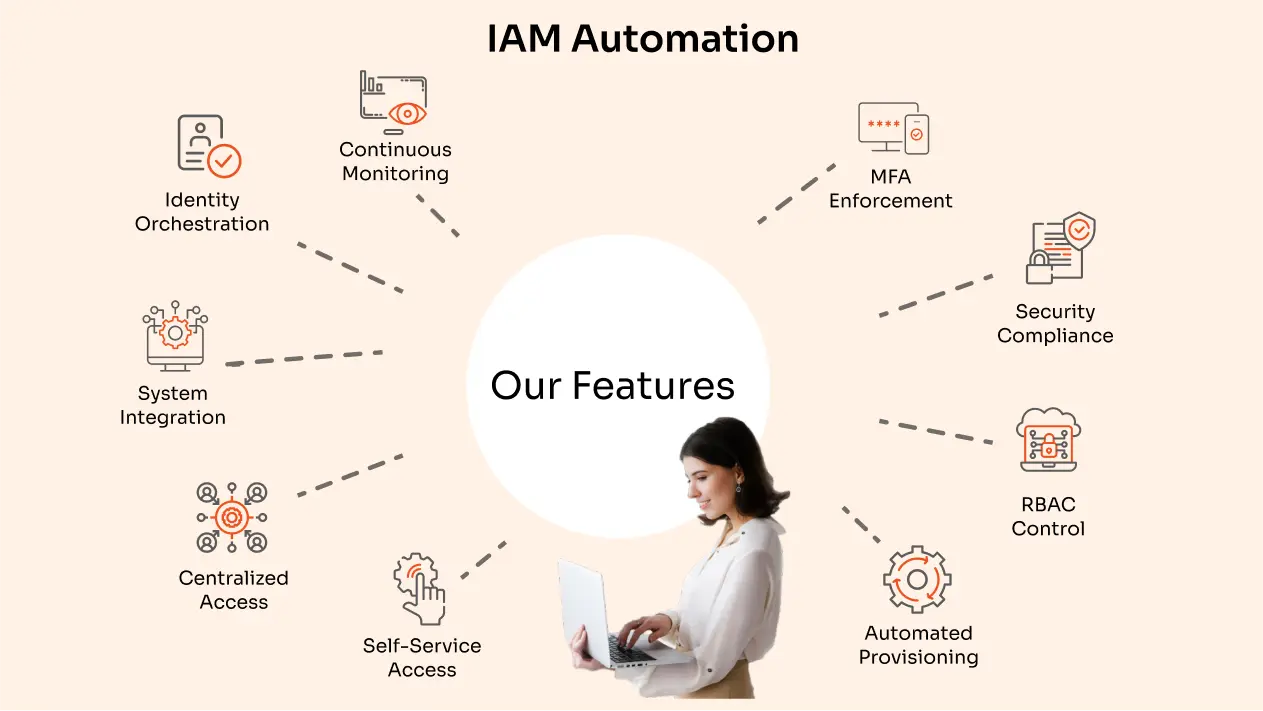
An effective Identity and Access Management (IAM) automation solution should include several essential features to ensure security, efficiency, and user satisfaction.
Identity Orchestration and Centralized Access Management
This feature allows organizations to manage user identities and access permissions from a single platform. It streamlines the process of granting access to various systems and applications, ensuring that users have the right permissions based on their roles.
Integration with Existing Systems
The solution must seamlessly integrate with current infrastructure such as Active Directory (AD), Single Sign-On (SSO), and cloud platforms. This integration helps maintain a consistent user experience and simplifies management across different environments.
Security Compliance and Policy Enforcement
An ideal IAM solution should enforce security policies and ensure compliance with industry regulations. This includes features like continuous monitoring, audit trails, and reporting capabilities that help organizations track user activities and access attempts.
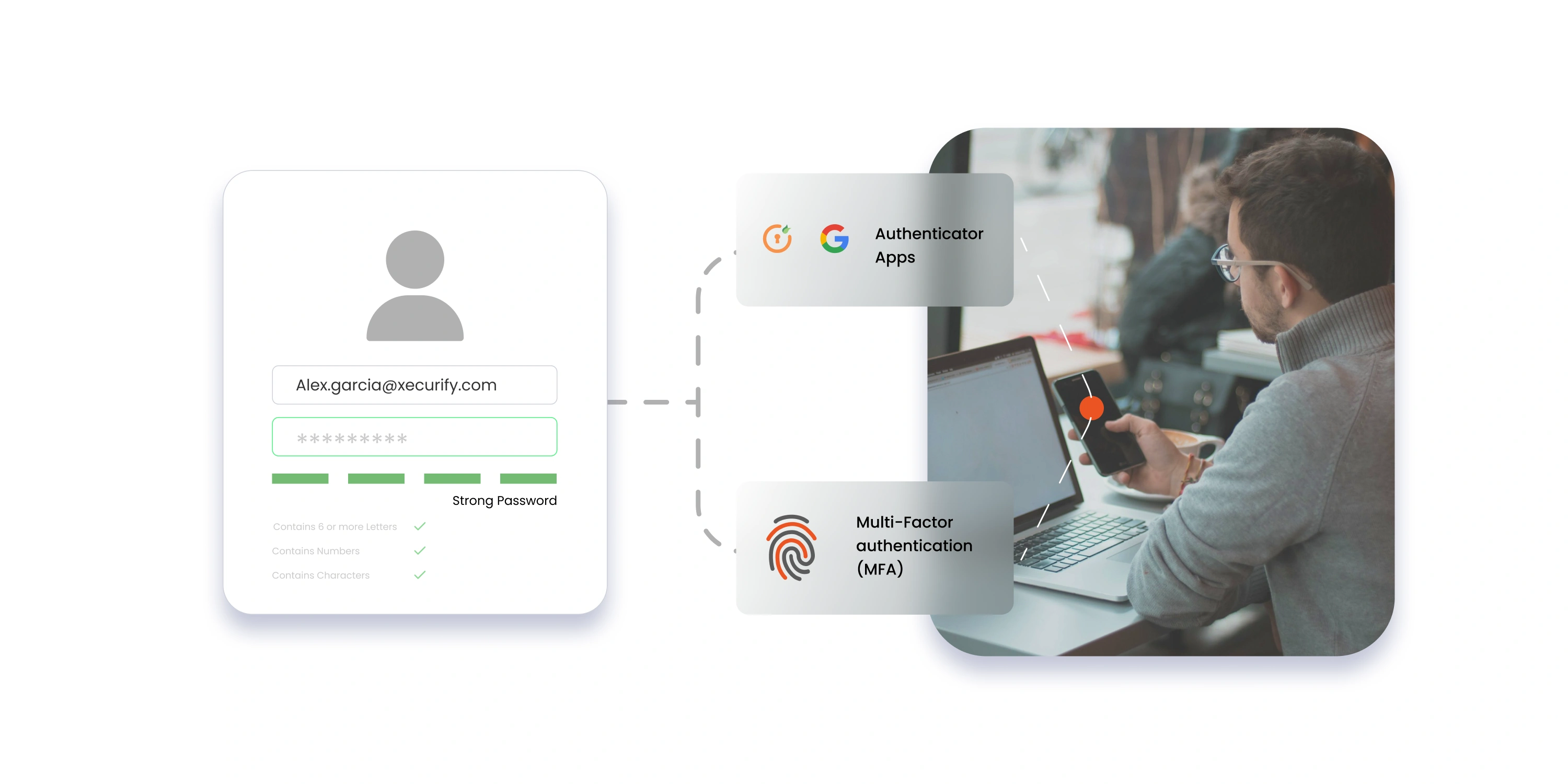
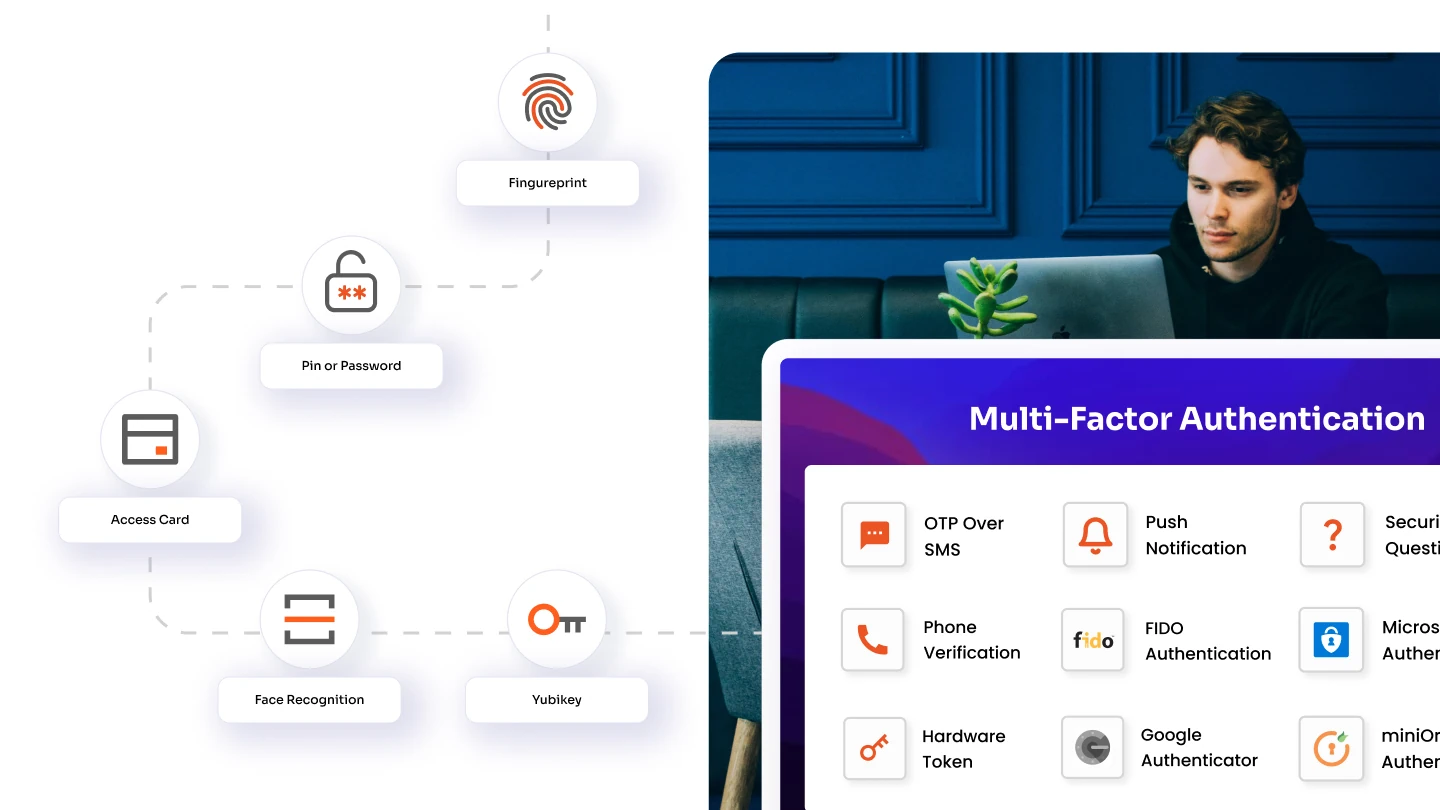
Multi-Factor Authentication (MFA)
MFA enhances security by requiring users to verify their identity through multiple methods before gaining access. This added layer of protection helps prevent unauthorized access.
Role-Based Access Control (RBAC)
RBAC simplifies permission management by automatically assigning access rights based on a user's role within the organization. This ensures that employees only have access to the resources necessary for their job functions.
Automated User Provisioning and Deprovisioning
Automation in user account management reduces manual errors and speeds up the onboarding and offboarding processes. New employees can quickly gain access to required resources, while departing employees can have their access revoked immediately.
Self-Service Capabilities
Allowing users to manage their own passwords and access requests reduces the burden on IT staff and enhances user satisfaction by providing faster resolutions to common issues.
Continuous Monitoring and Reporting
Regular monitoring of user activities helps identify potential security threats or compliance issues early on. Comprehensive reporting tools provide insights into access patterns and policy adherence.
These features collectively enhance the security, efficiency, and usability of IAM systems, making them crucial for modern organizations navigating complex digital environments.
Best Practices for Implementing IAM Automation
To effectively implement Identity and Access Management (IAM) automation, follow these best practices:
Assess Current IAM Processes
Start with a thorough evaluation of your existing IAM processes. Identify any manual tasks that can be automated to improve efficiency and security.
Identify High-Priority Areas for Automation
Focus on the most critical areas that will benefit from automation. This could include user account creation, access management, and compliance reporting.
Align Tools with Compliance and Business Goals
Ensure that the IAM tools you choose meet compliance requirements and support your business objectives. Look for features like multi-factor authentication and role-based access control to enhance security.
Develop a Pilot Program
Test your automation strategy in a controlled environment before full-scale implementation. This helps identify potential issues and allows for adjustments based on real-world performance.
Train Your Team
Provide training for your IT and security teams on how to use the new tools effectively. This ensures they are equipped to manage automated workflows and troubleshoot any problems.
Monitor and Optimize Continuously
Regularly review key metrics to assess the effectiveness of your automation efforts. Make adjustments as needed to improve performance and security. By following these steps, you can streamline your IAM processes, reduce manual errors, and enhance overall security within your organization.
Popular Tools and Frameworks for IAM Automation
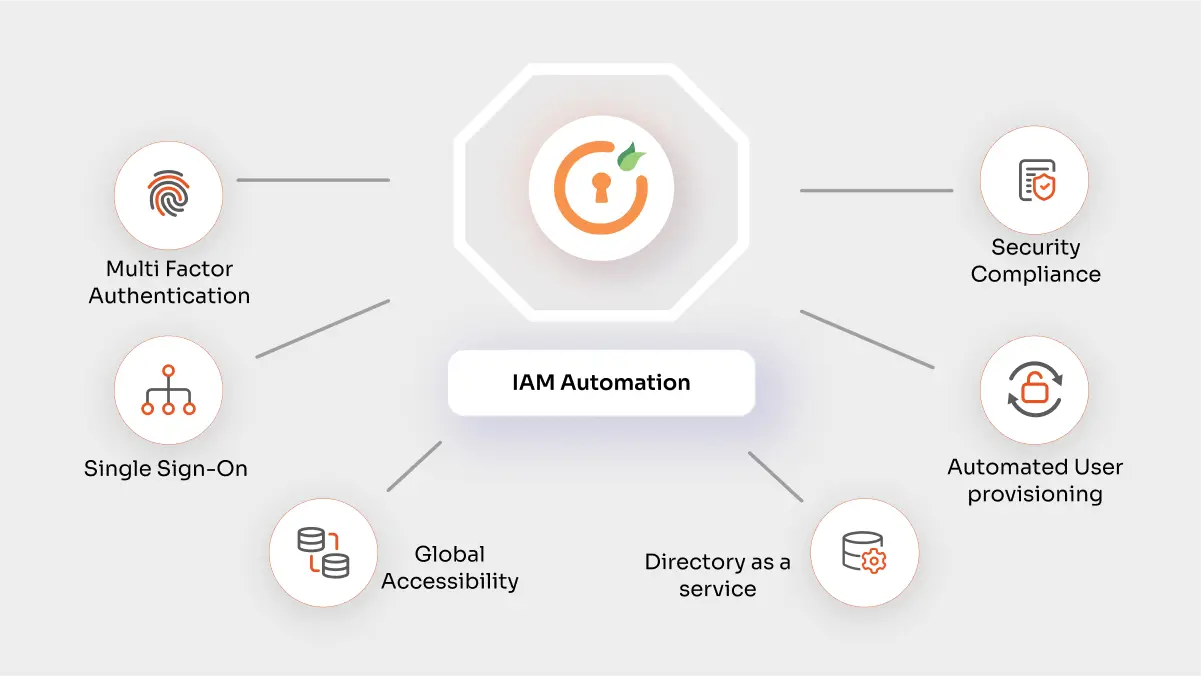
Why Choose miniOrange for IAM Automation?
miniOrange offers a comprehensive, cloud-based Identity and Access Management (IAM) solution designed to secure and simplify access to applications and data for organizations of all sizes. Its key features include:
- Single Sign-On (SSO): miniOrange enables one-click access to all applications using a single set of credentials. It supports over 6,000 pre-built integrations for cloud-based, on-premise, and custom apps, making deployment seamless.
- Multi-Factor Authentication (MFA): miniOrange provides 15+ MFA methods, including passwordless authentication, role-based MFA, and device-specific configurations. This ensures secure access to enterprise systems in high-risk scenarios.
- Automated User Provisioning: miniOrange automates user onboarding, offboarding, and access rights management. It synchronizes with HR systems like Workday and BambooHR to automatically update or revoke user access based on role changes or terminations, saving time and reducing costs.
- Directory as a Service (DaaS): Centralized management of user, device, and resource information simplifies data handling across the organization.
- Compliance and Security: With fine-grained permissions and robust auditing capabilities, miniOrange ensures compliance with industry standards while protecting sensitive resources from unauthorized access.
- Global Accessibility: miniOrange operates AWS data centers in the United States, the UK, and Australia to provide reliable service worldwide.
Factors to Consider When Selecting Automated IAM Solution
- Scalability: miniOrange supports businesses of all sizes, from SMEs to large enterprises.
- Integration Needs: Its vast catalog of pre-built integrations ensures compatibility with existing IT ecosystems.
- User Experience: The platform offers a customizable interface and self-service options for enhanced user satisfaction.
- Cost Efficiency: Automated provisioning reduces costs by freeing up unused application licenses.
- Global Support: With localized servers and 24/7 customer support, miniOrange ensures uninterrupted service.
miniOrange is a trusted IAM automation solution and an identity provider that combines advanced security features with operational efficiency to meet modern business needs.
Real-Life Success Stories of miniOrange IAM Automation
Al Hussaini Trading:
- Al Hussaini Trading faced challenges with user login and registration on their BigCommerce store, leading to a poor customer experience.
- miniOrange implemented a CIAM solution that streamlined the login and registration process, resulting in a seamless user experience and improved customer satisfaction.
DBS Bank:
- DBS Bank needed to enhance their security measures to ensure safe access to their financial services.
- miniOrange provided an IAM solution that bolstered their cybersecurity infrastructure, ensuring secure access for their users.
University of Aruba:
- The University of Aruba required a solution for students and staff to access their day-to-day applications both on and off university premises.
- miniOrange's Windows Single Sign-On solution allowed seamless access to applications, improving user convenience and operational efficiency.
The Future of IAM Automation
Automation in identity and access management should be a continuous process. Learning from what has worked for you helps you choose the right identity security tools that really work. Protecting your identity begins with protecting your login information effectively and IAM automation support each and every aspect of it. IAM automation solutions cater to identity lifecycle management, user provisioning and deprovisioning, password management and more. IAM automation will revolutionize identity management by integrating AI and machine learning for real-time threat detection and response. This will enhance security, streamline operations, and improve user experience.
FAQs
1. How does the IAM automation solution integrate with our existing systems?
miniOrange IAM integrates seamlessly with over 6000 pre-built applications, ensuring smooth SSO, MFA, and provisioning. It also supports custom integrations through APIs, making it adaptable to unique business needs.
2. How scalable is the IAM automation solution?
miniOrange IAM scales effortlessly to accommodate growing user volumes and evolving access requirements. It can handle both small businesses and large enterprises, ensuring consistent performance and security.
3. Can the solution automate the entire IAM lifecycle?
Yes, miniOrange IAM automates user onboarding, offboarding, and access rights management, enhancing productivity and security. It also provides role-based access control and automated policy enforcement.
4. What are the security features of the IAM automation solution?
miniOrange IAM offers advanced security features, including MFA, risk-based authentication, and IP restriction. It also includes real-time monitoring and alerts to detect and respond to suspicious activities.
Author


Leave a Comment