Managing 5,000+ identities across your enterprise? Each one is a potential entry point for attackers—and your IAM security is only as strong as your weakest access point. This is where the most effective IAM best practices and data-driven strategies come into play.
What is IAM and What are the Best Practices in IAM?
Identity and Access Management (IAM) ensures the right individuals access the right resources at the right moment. Key IAM best practices include the implementation of Multi-Factor Authentication (MFA), adopting a Zero Trust Model, regularly updating systems, conducting audits, and educating employees.
For example, a company can use IAM best practices to ensure only authorized personnel access sensitive customer data by using MFA, updating systems, and conducting audits. This protects data from unauthorized access and breaches.
The State of IAM: Hard Truths and Real Opportunities
The message is clear: 83% of enterprise breaches involve identity-related vulnerabilities. The average cost of an identity-related breach is $4.5M. Yet most solutions create more problems than they solve. But here's what the analysts aren't telling you—most organizations are overcomplicating their IAM strategy while missing the fundamentals that actually work. They need a set of robust identity access management best practices to begin with.
Cybersecurity Challenges in Organizations that IAM Fixes
Identity and Access Management (IAM) addresses several critical cybersecurity challenges in organizations:
- Unauthorized Access: IAM ensures that only authorized users can access sensitive information and systems, reducing the risk of data breaches.
- Insider Threats: By monitoring and managing user access, IAM helps detect and prevent malicious activities from within the organization.
- Compliance: IAM supports regulatory compliance by enforcing policies and maintaining audit trails of user activities.
- Password Management: IAM simplifies password management, reducing the risk of weak or reused passwords that can be exploited by attackers.
- Access Control: IAM provides granular access control, ensuring users have the minimum necessary permissions to perform their tasks.
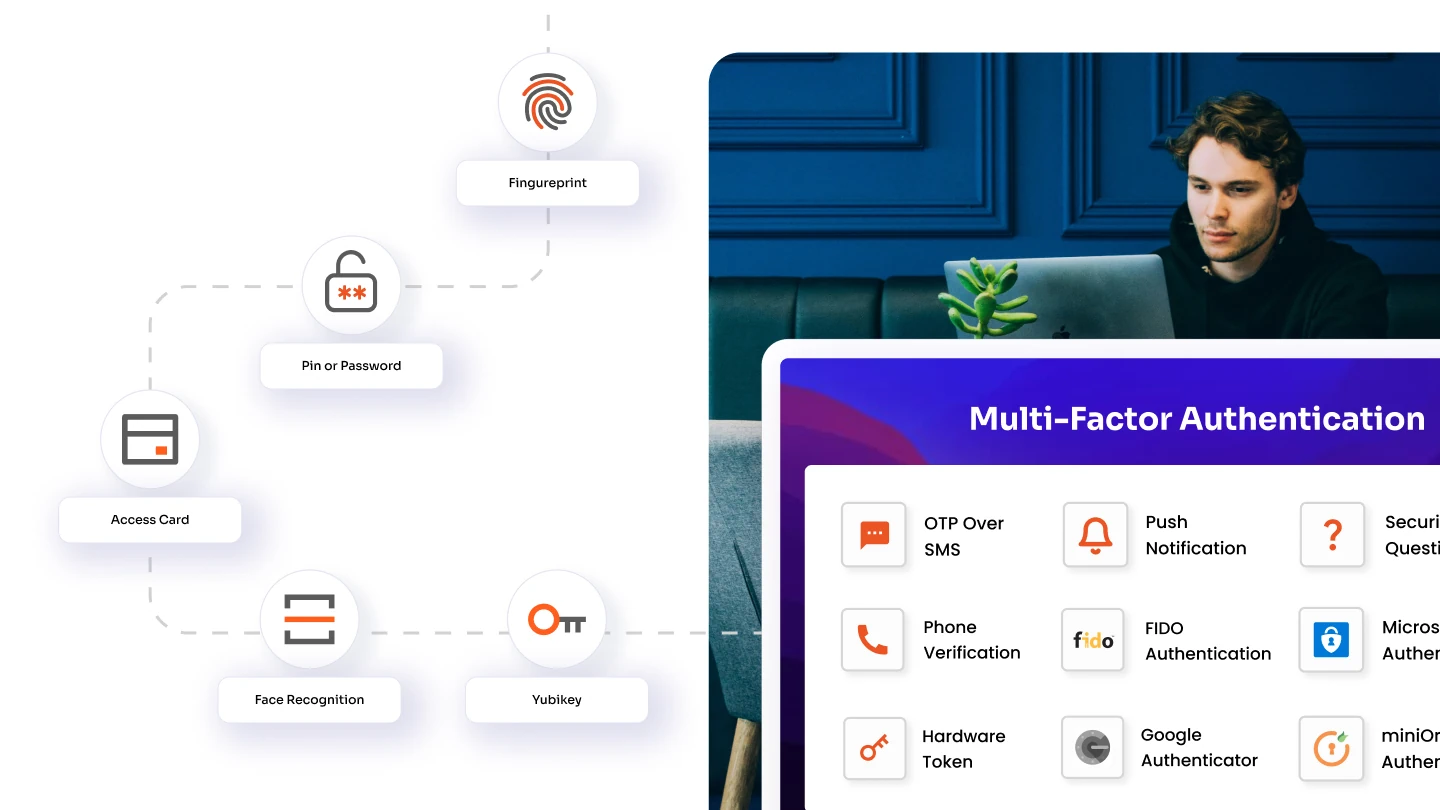
- Security Breaches: IAM enables SSO, improving the user experience and reducing the risk of password fatigue. IAM implements MFA, adding an extra layer of security to user authentication processes.
Top 10 Best Practices in Identity and Access Management
Some of the best-known user access management strategies include zero trust implementation, privileged access management, identity governance, and access management.
Here are the most important IAM best practices that lead to refined results:
1. Build a Zero Trust Architecture
Zero Trust is your new security foundation - trust nothing, verify everything. This approach treats every access request as potentially risky, whether it's from your CEO or a new intern. By verifying every user and device each time they request access, you significantly reduce your attack surface.
- Remove automatic trust for internal networks
- Verify every access request in real-time
- Implement continuous authentication
- Monitor and log all access attempts
- Reduce attack surface by 60% on average
2. Set Up Automated User Management
Stop managing user access manually and let automation handle the heavy lifting. Modern systems can sync with HR to automatically create and remove access across all systems. This cuts down onboarding time from weeks to hours and eliminates forgotten accounts when people leave.
- Sync access management with HR systems
- Automate account creation and removal
- Save $2M annually for large enterprises
- Eliminate manual provisioning errors
- Cut onboarding time by 90%
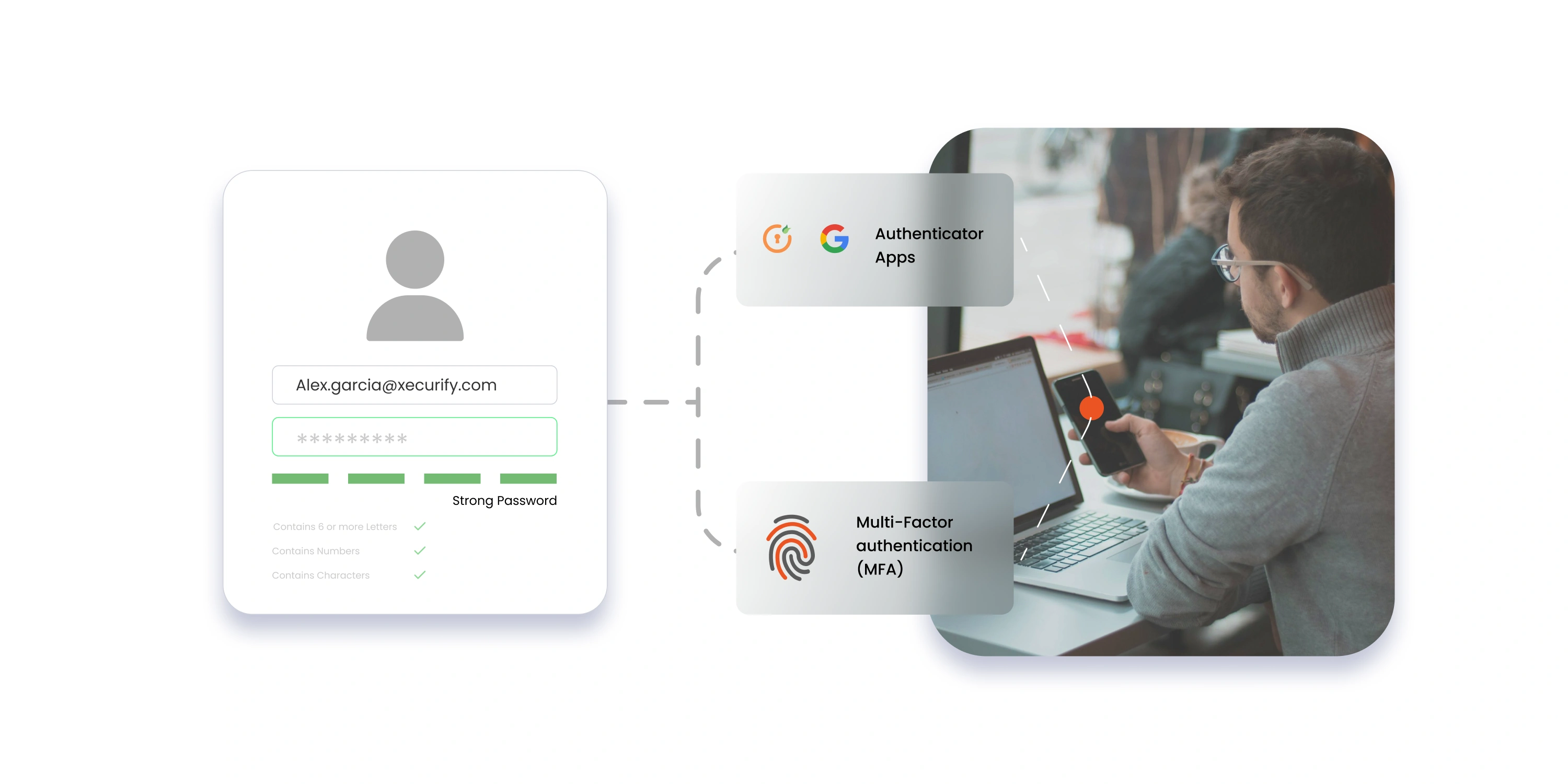
3. Roll Out Smart Authentication
Basic MFA isn't enough anymore - upgrade to intelligent authentication that adapts to risk levels. Smart systems know when to ask for more verification and when to keep it simple. This balance between security and usability leads to higher adoption rates.
- Implement passwordless authentication options
- Use risk-based verification levels
- Enable biometric and security key options
- Achieve 99% MFA adoption rates
- Reduce password reset tickets by 80%
4. Control High-Level Access
Privileged accounts are your biggest risk - protect them accordingly. Use a central system to manage all high-level access, watch admin sessions in real-time, and keep detailed logs of every privileged action.
- Centralize privileged access management
- Monitor admin sessions in real-time
- Set up emergency access procedures
- Track all privileged account usage
- Reduce admin account abuse by 75%
5. Watch Everything in Real Time
Don't wait for reports - catch threats as they happen. Use principle of least privilege to restrict user access and monitor user sessions in real time. This approach stops attacks before they cause damage.
- Deploy threat detection
- Focus on behavior patterns
- Correlate events across systems
- Reduce false positives by 85%
- Stop attacks in progress
6. Enforce Rules Automatically
Let software handle your security policies consistently and continuously. Automated enforcement scales better than manual checks and never misses a violation.
- Automate policy enforcement
- Ensure consistent security standards
- Scale rules across all systems
- Reduce manual review time by 70%
- Maintain continuous compliance
7. Give Access Only When Needed
Stop giving out permanent access - use time-limited permissions instead. Just-in-time access reduces risk by limiting how long anyone has permissions.
- Implement time-based access controls
- Grant task-specific permissions
- Automate access expiration
- Reduce standing privileges by 90%
- Cut exposure time in half
8. Kill Access Fast When People Leave
Create a single-click process to remove all access when someone leaves. This prevents security gaps from forgotten accounts and ensures clean offboarding.
- Enable one-click access removal (deprovisioning)
- Cover all systems and applications
- Verify complete access termination
- Eliminate zombie accounts
- Reduce unauthorized access by 95%
9. Match Security to Risk Level
Use context to determine how much security each access request needs. This makes routine work easier while protecting sensitive resources.
- Consider location and device context
- Adjust verification requirements dynamically
- Use behavior patterns to assess risk
- Reduce user friction by 60%
- Increase security for high-risk actions
10. Track What Matters
Build dashboards that show real security improvements and ROI. Focus on metrics that help make decisions and show value to leadership.
- Track security improvements
- Measure actual risk reduction
- Show clear ROI metrics
- Generate automated compliance reports
- Demonstrate 40% cost savings
This approach balances strong security with practical usability, helping organizations protect assets while enabling productivity.
Challenges and Solutions in IAM Best Practices Implementation
| Challenge | Solution |
|---|---|
| Complex integration | Use standardized protocols and APIs for seamless integration. |
| User resistance for IAM adoption | Provide training and support to ease the transition. |
| Scalability issues | Implement scalable IAM solutions that grow with the organization. |
| Compliance requirements | Regularly update IAM policies to meet regulatory standards. |
| Managing privileged access | Use role-based access control (RBAC) and least privilege principles. |
| Password fatigue | Implement Single Sign-On (SSO) and Multi-Factor Authentication (MFA). |
| Monitoring and auditing | Use automated tools for continuous monitoring and auditing. |
The Bottom Line
Identity management in 2024 isn't just about security—it's your business accelerator. These identity management best practices carve a clear path in your IAM journey. These tried and tested modern user management best practices allow you to secure your organization from the worst nightmares in time successfully. Start with your biggest pain points, measure what matters to your business, and build for scale. Perfect IAM doesn't exist, but practical, effective IAM does.
Ready to Transform Your IAM and PAM Strategies?
Start your free 30-day trial of miniOrange IAM and PAM today. No credit card is required; full enterprise features are included. See firsthand how modern IAM can impact your business metrics and apply the IAM best practices for your business.
Start Free IAM and PAM Trial
Experience miniOrange's comprehensive IAM solution, trusted by 25,000+ businesses worldwide.
Author



Leave a Comment