Right now, three out of four organizations are sitting on an IAM security time bomb: 75% have employees wielding excessive system privileges they never should have received. Imagine giving master keys to every employee in your building—that's exactly what's happening in global workspaces, with a dire need for IAM controls.
In 2024 alone, overprivileged accounts led to data breaches costing companies an average of $4.88 million. The silent killer? Not hackers with sophisticated tools, but simple mismanagement of who can access what. This is where robust IAM controls don't just protect your data—they save your enterprise.
User Access Controls in IAM
Effective identity and access management (IAM) is crucial for organizations to maintain the security and integrity of their systems and data. IAM controls are the mechanisms and policies that govern how users, devices, and applications can access and interact with resources.
In this comprehensive blog post, we'll explore five essential IAM controls that can help strengthen your security posture. We'll also discuss the importance of separating authentication controls and authorization controls, cover the various access control models, and examine the benefits of implementing robust IAM best practices. Finally, we'll take a look at emerging trends in the IAM space.
Need for Access Control in IAM?
Access control is a fundamental component of IAM. It ensures that only authorized individuals and entities can perform specific actions on protected resources. Effective access control mitigates the risks of unauthorized access, data breaches, and other security threats.
What are IAM Controls?
IAM controls are the policies, procedures, and technical measures that regulate and enforce access to systems, applications, and data. They encompass both authentication (verifying user identity) and authorization (granting specific permissions and privileges) mechanisms.
Types of Access Control Models in IAM
Each access control model has its strengths and weaknesses, and organizations often implement a combination of these approaches to achieve a robust and flexible IAM framework. The choice of model(s) should be based on the organization's security requirements, compliance needs, and the specific characteristics of the IT environment.
- Rule-Based Access Control (RBAC): RBAC grants access based on an individual's role within the organization. Access permissions are associated with specific job functions or responsibilities rather than individual users. This model simplifies the management of access rights as permissions can be easily assigned, updated, or revoked by modifying the roles themselves. RBAC is a widely adopted approach, as it provides a balance between security and usability.
- Attribute-Based Access Control (ABAC): ABAC uses a combination of user attributes, resource attributes, and environmental conditions to make dynamic access decisions. Rather than relying solely on predefined roles or rules, ABAC evaluates multiple contextual factors to determine whether a user should be granted access. This model offers greater flexibility and adaptability, as access can be tailored to the specific circumstances of each request. ABAC is particularly useful in complex, heterogeneous environments where access requirements can vary widely.
- Policy-Based Access Control (PBAC): PBAC controls access through the evaluation of policies that define the conditions under which a user can access a resource. These policies are centrally managed and can consider factors such as user identity, resource sensitivity, time of day, location, and device posture. PBAC provides a more comprehensive and adaptable approach to access control, as policies can be easily updated to address evolving threats and business requirements.
- Mandatory Access Control (MAC): MAC is a centralized, policy-driven approach where the system administrator defines and enforces access rules. In a MAC system, the organization's security policy dictates who can access which resources, and the system enforces these rules rigidly. Users have little to no control over permissions; all access is granted or denied based on the predefined security policies. MAC is commonly used in highly secure environments, such as government agencies and military organizations, where strict control over access is critical.
- Discretionary Access Control (DAC): In a DAC model, users have the ability to determine and manage access permissions for the resources they own or control. This gives individual users a high degree of control over their data and systems. However, this also introduces potential security risks, as users may inadvertently grant excessive permissions or fail to revoke access when necessary. DAC is more common in less regulated environments where flexibility and user empowerment are prioritized over centralized control.
IAM Implementation Controls in Action
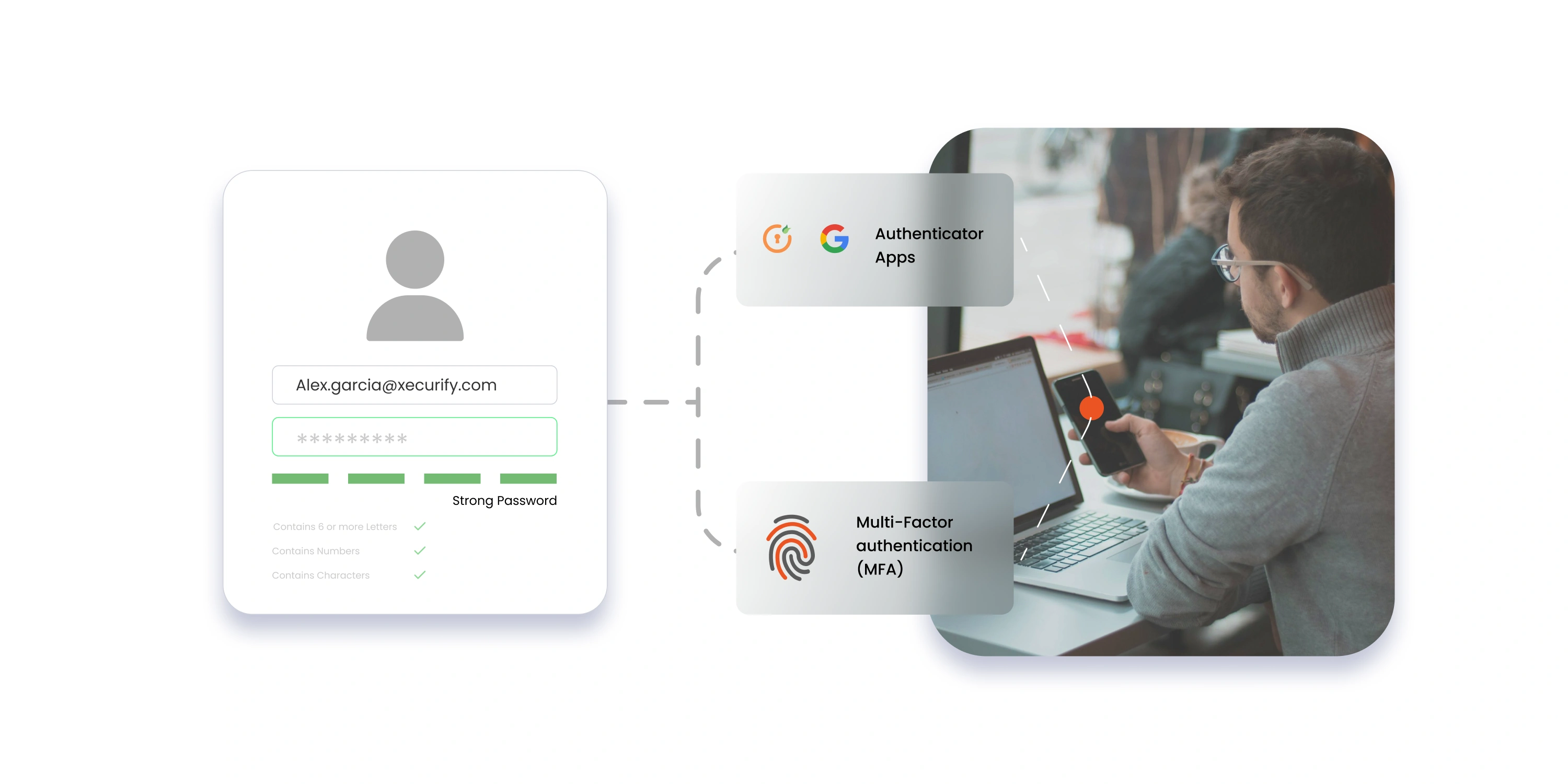
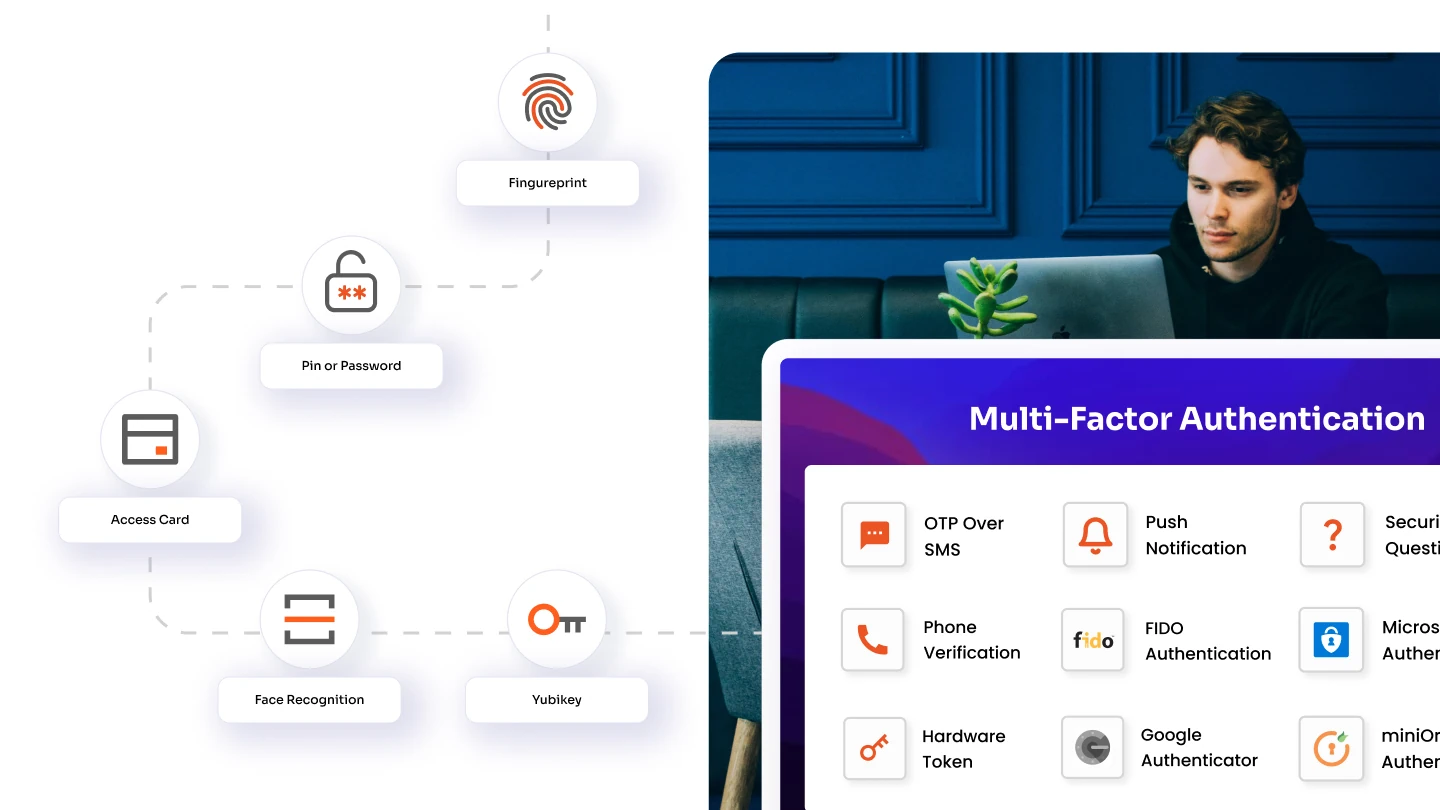
- Multi-Factor Authentication (MFA): Requires users to provide multiple forms of identity verification, such as passwords, biometrics, or one-time codes, to access systems and applications.
- Least Privilege: Grants users the minimum permissions necessary to perform their job functions, reducing the risk of unauthorized access.
- Segregation of Duties: Ensures that no single user has complete control over critical processes, mitigating the risk of fraud and errors.
- Privileged Access Management (PAM): Monitors and controls access to high-risk, sensitive, or critical resources, such as administrative accounts.
- Identity Lifecycle Management: Automates the creation, modification, and termination of user accounts, ensuring that access is granted and revoked in a timely and consistent manner.
Benefits of Effective IAM Controls
- Improved Security: IAM controls help prevent unauthorized access, data breaches, and other security incidents, protecting your organization's sensitive information and assets.
- Better Compliance: Effective IAM practices can help organizations meet regulatory requirements and industry standards, such as GDPR, HIPAA, and PCI DSS.
- Increased Operational Efficiency: Streamlined IAM processes and automation can improve productivity, reduce manual effort, and minimize the risk of human error.
- Better Visibility and Oversight: Comprehensive IAM controls provide organizations with real-time visibility into user activities, enabling more effective monitoring and auditing.
Future Trends in IAM
- Passwordless Authentication: Replacing traditional passwords with more secure and user-friendly alternatives, such as biometrics, hardware security keys, and passwordless protocols.
- Intelligent Access Management: Leveraging machine learning and artificial intelligence to automate access decisions, detect anomalies, and adapt to changing user and environmental conditions.
- Decentralized Identity: Blockchain-based approaches that empower individuals to own and control their digital identities, reducing the reliance on centralized identity providers.
- Convergence of IAM and Zero Trust: Integrating IAM controls with zero-trust principles to continuously verify user identities, device posture, and network context before granting access.
Conclusion
Implementing a robust set of IAM controls is crucial for organizations to safeguard their systems, data, and resources. By separating authentication and authorization mechanisms, leveraging the right access control models, and staying ahead of emerging trends, you can build a more secure and adaptable IAM framework. This blog post has provided a comprehensive overview of the key IAM controls to consider, empowering you to enhance your organization's security and compliance posture. Learn how your organization can benefit from effective identity and access management controls. Request a trial of miniOrange IAM today.
Author



Leave a Comment