In the current digital era, where data breaches are a constant threat and regulatory demands grow increasingly rigid, the importance of a well-defined Identity and Access Management (IAM) strategy cannot be overstated. IAM is important for securing an organization's critical data by regulating who can access specific resources and when. This control mechanism is not just about enhancing security; it is crucial in aligning with business goals and maintaining compliance as per the industry standards.
IAM involves the detailed management of individual identities within an organization, ensuring that each user has the appropriate access rights based on their role. This precise alignment helps prevent unauthorized access to sensitive information, significantly reducing the risk of security breaches. Moreover, an effective IAM strategy streamlines operations and enhances productivity by ensuring that the right individuals have the right access at the right times.
By integrating IAM deeply into the business strategy, organizations can not only safeguard their data against unauthorized access. This alignment proves essential as companies navigate the complex landscape of digital transformations where efficiency and security go hand in hand.
What is an Identity and Access Management (IAM) Strategy?
An Identity and Access Management (IAM) strategy is a comprehensive framework that combines technology, policies, and procedures to manage digital identities and regulate access within an organization. This strategic approach is crucial in ensuring that only authorized personnel have access to specific resources, such as SaaS applications, data, and other critical business assets but also prevent unauthorized access that could lead to major security breaches.
An effective IAM strategy lies in its ability to integrate seamlessly with an organization's cybersecurity practices. It employs advanced technological solutions and rigorous procedures to authenticate and authorize users, thereby safeguarding sensitive information from both external and internal threats. By defining and implementing strict access controls, IAM helps maintain operational integrity and protects against the potential risks associated with data breaches and other security incidents.
Moreover, an IAM strategy is not just about security; it is also about efficiency and compliance. Without a robust IAM framework, organizations may struggle with inefficient manual processes related to user account management, authentication, and access permissions. Furthermore, adhering to compliance and regulatory requirements becomes more manageable with an effective IAM strategy, helping avoid legal and financial penalties associated with non-compliance.
Things to Consider Before Implementing an IAM Strategy
When preparing to roll out an Identity and Access Management (IAM) strategy, there are several crucial aspects to consider:
- Ensure Compatibility: Verify that the new IAM system is compatible with existing data structures and can handle the required data migration without compromising security or functionality.
- Document Infrastructure: Thoroughly map and document existing network resources and IT infrastructure to identify potential challenges and integration points for the IAM system.
- User Access Levels: Catalogue all users and clearly define their access levels to ensure the IAM system adequately reflects organizational roles and security needs.
- Critical Asset Identification: Conduct risk assessments focusing on identifying and securing high-value assets/data/files/roles thus, prioritizing them within the IAM framework.
- Compliance Alignment: Develop IAM policies that align with regulatory requirements and industry standards, ensuring legal and security compliance.
- Choosing the Right IAM Tools: Evaluate and choose IAM solutions that best meet the specific needs of the organization. Look for tools that offer core functionalities like:
- Authentication
- Authorization
- Single Sign-On (SSO)
- Auditing systems
- Identity Federation
Steps to Build an Effective IAM Strategy
Developing a robust Identity and Access Management (IAM) strategy is essential for securing sensitive data and ensuring efficient operations within modern organizations. Here is a comprehensive guide to creating an effective IAM strategy:
Step 1: Define IAM Objectives
Begin by identifying your organization’s core business goals. Align your IAM objectives with these goals to enhance compliance, reduce risks, and improve operational efficiency. This foundational step ensures that your IAM strategy directly contributes to your organization's broader objectives, such as maintaining regulatory compliance, minimizing the risks of data breaches, and streamlining user operations.
Step 2: Assess Your Current IT Environment
Evaluate your existing IT infrastructure to understand the current state of systems, user access methods, and IT processes. Conduct thorough risk assessments for high-value assets to identify vulnerabilities and areas requiring improvement. This evaluation should encompass all critical elements, including HR systems, identity lifecycle processes, and provisioning systems like Active Directory or Azure environments.
Step 3: Develop IAM Policies and Procedures
Craft detailed policies that govern password management, user provisioning, access controls, and more. These policies should be regularly updated and aligned with industry standards to ensure they remain effective against emerging threats. This step involves creating a clear framework for identity management that addresses both everyday operations and exceptional circumstances.
Step 4: Choose the Right IAM Tools and Technologies
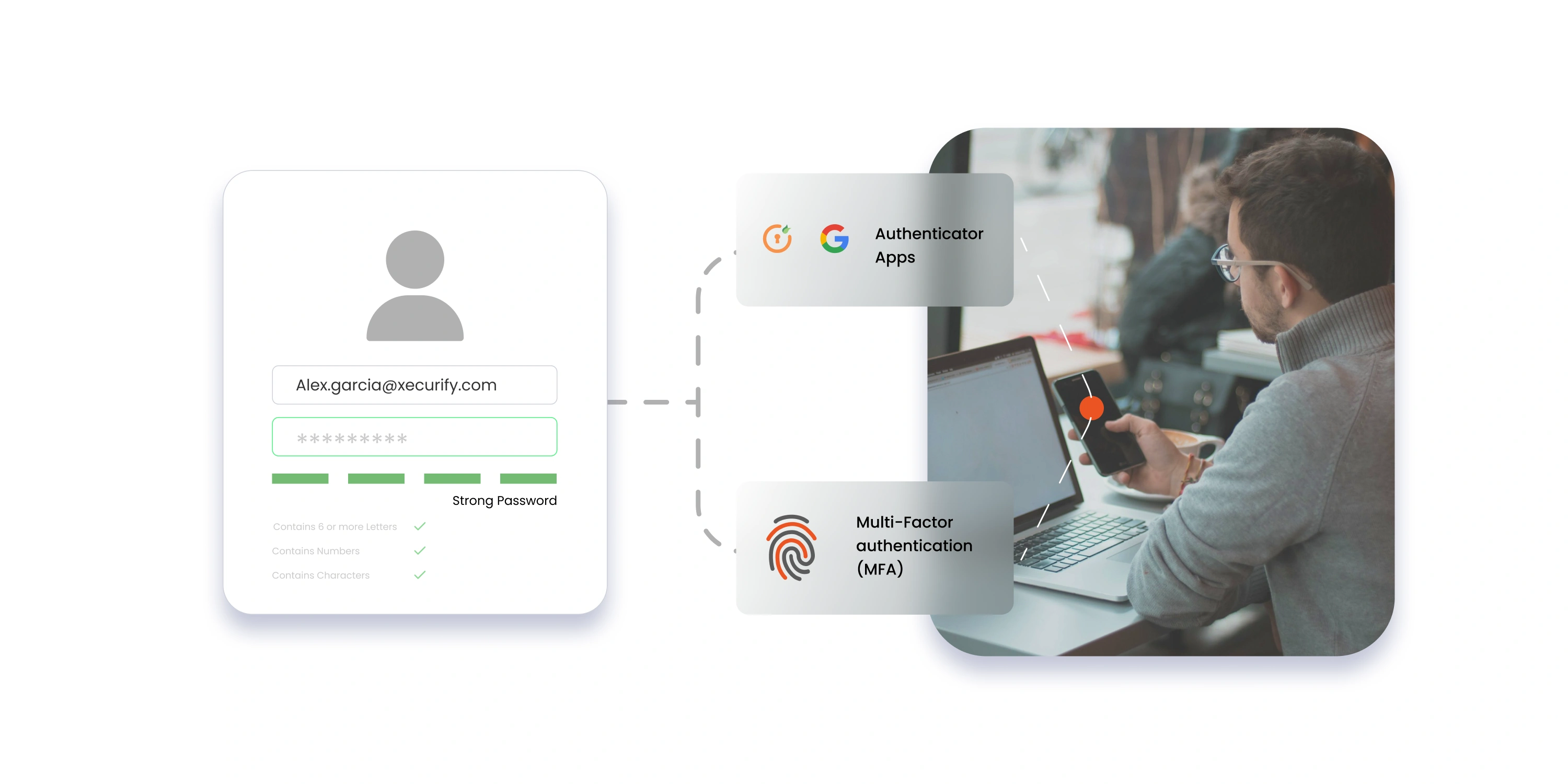
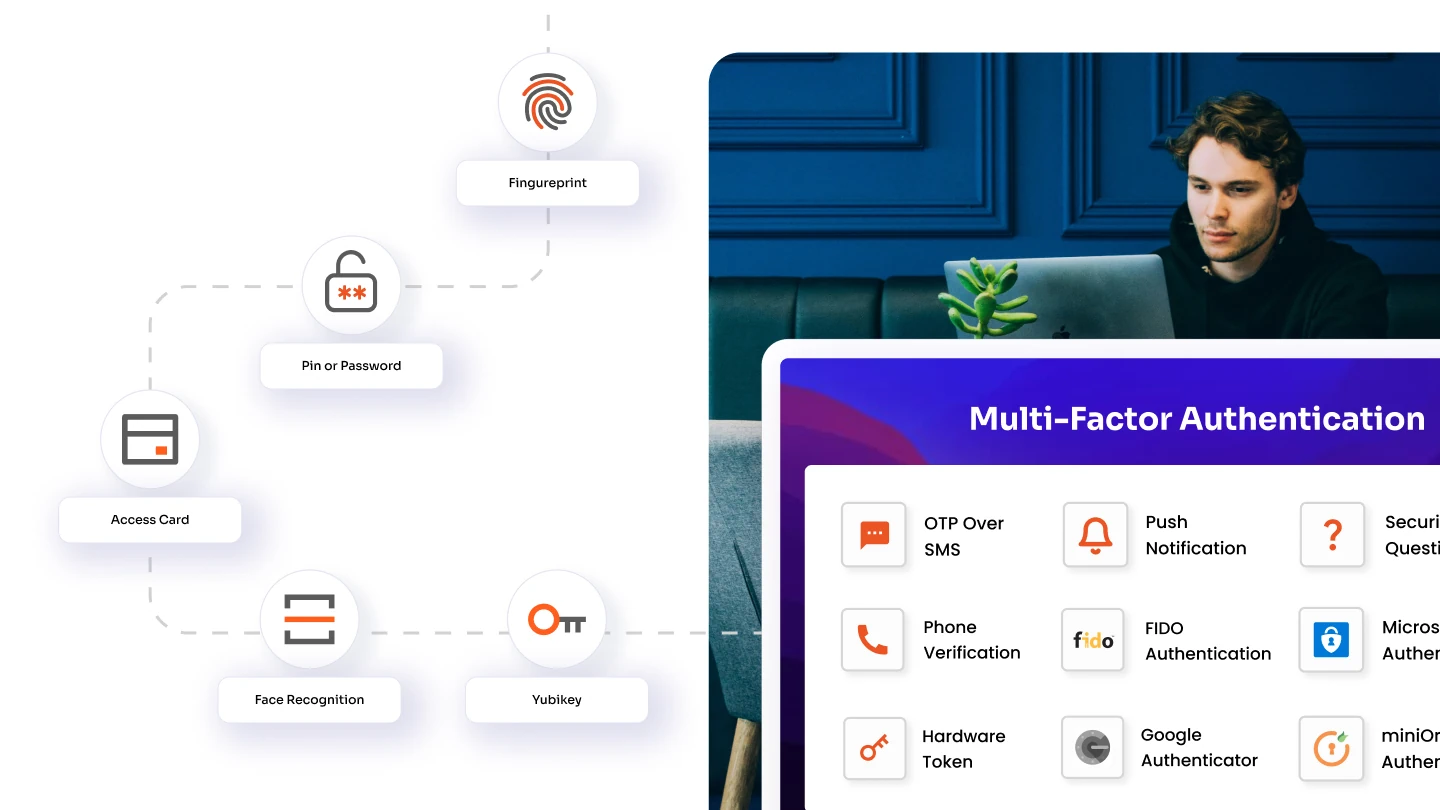
Select appropriate IAM tools and technologies that support the needs of your organization. This includes implementing Single Sign-On (SSO), Multi-Factor Authentication (MFA), and identity governance solutions. Consider factors such as scalability, integration capabilities with existing systems, and the impact on user experience to ensure the tools enhance security without compromising usability.
Step 5: Implement Identity Federation and Conduct Regular Audits
Incorporate identity federation to facilitate seamless access across various platforms and applications, both internally and externally. This step enhances interoperability and user convenience while maintaining security boundaries. Regularly audit your IAM processes to ensure compliance with regulations like GDPR or HIPAA and to identify any potential security issues. These audits should focus on user activities, access controls, and system alerts to continuously refine and improve the IAM strategy.
Common Challenges and Mistakes to Avoid in IAM Implementation
Implementing an Identity and Access Management (IAM) strategy involves intricate planning and execution. To ensure a smooth and effective deployment, it's crucial to be aware of common pitfalls and actively work to avoid them. Here are key challenges and mistakes that organizations commonly encounter:
- Lack of Stakeholder Buy-in - Implementing IAM can be perceived as disruptive by executives and department managers who may not be fully aware of its benefits. Without their support, the implementation process can face significant obstacles.
- Poorly Defined Business Goals - IAM implementations that do not align with specific business needs can introduce unnecessary complexity and inefficiencies, making daily operations more difficult for employees.
- Inadequate Training for Employees and IT Staff - A lack of proper training on the new IAM systems can lead to non-compliance with security protocols and inefficient use of IAM tools, potentially increasing the risk of security breaches.
- Overlooking Regular Audits and Policy Updates - Failing to conduct regular audits and update IAM policies can lead to outdated practices that no longer meet security or compliance standards, leaving the organization vulnerable to new threats.
Best Practices for a Successful IAM Strategy
- Involve All Stakeholders from the Start : Engage and communicate with stakeholders at all levels early on to ensure alignment with business goals and facilitate comprehensive support for the IAM initiative.
- Implement the Principle of Least Privilege and Role-Based Access Control : Apply the principle of least privilege and role-based access control to ensure users only have the access necessary for their roles, minimizing potential security risks.
- Regularly Review and Refine the Strategy to Address Emerging Threats : Continuously evaluate and update the IAM strategy to adapt to new security challenges and ensure it remains effective in safeguarding digital assets.
- Invest in Employee Training to Use IAM Tools : Provide thorough and ongoing training for all users/employees to ensure effective and secure use of IAM tools, enhancing the overall security posture of the organization.
Conclusion: The Path to Secure and Efficient Identity Management
Implementing a strong Identity and Access Management (IAM) strategy is crucial for protecting sensitive data and streamlining operations in any organization. Effective planning, stakeholder involvement, rigorous access controls, and ongoing training are key to maintaining a secure IAM system.
Organizations aiming to enhance their security should consider expert solutions like those offered by miniOrange, known for their comprehensive and adaptable IAM tools. To strengthen your security measures and improve your operational efficiency, explore the IAM solutions from miniOrange today.
Author



Leave a Comment