When choosing between IdP and SP-initiated SSO, it isn't just tech talk – it's a game-changer for your company's security and productivity. The stats are eye-opening: Verizon reports 74% of data breaches stem from human error or credential misuse. Meanwhile, Gartner predicts that by 2025, 70% of companies will use unified platforms for access management. Bottom line? The right SSO approach isn't just smart – it's your ticket to the big leagues. Fall behind, and you'll be playing catch-up while your competitors sprint ahead.
The Power of Single Sign-On (SSO)
Single Sign-On (SSO) allows users to access multiple applications with one set of credentials, enhancing convenience and security. It operates on federated identity principles, sharing identity attributes across trusted systems using protocols like OpenID Connect and SAML 2.0. Originating in the 1990s with tools like Active Directory (AD) and LDAP SSO has evolved to meet modern authentication needs.
What is an IdP-Initiated SSO?
An Identity Provider (IdP) is a trusted service that authenticates user identities and grants secure access to multiple applications. It centralizes authentication, enhancing security and simplifying access management.
IdP-Initiated Single Sign-On (SSO) is a process where the authentication request is initiated by the Identity Provider (IdP). In simpler terms, the IdP is the starting point for the user’s login journey.

IdP-Initiated SSO Workflow
- User Authentication at IdP
- User visits IdP portal and logs in with credentials
- IdP verifies user identity against its database
- SAML Token Creation
- IdP generates signed SAML assertion containing user's authentication info
- Assertion includes necessary user attributes for SP
- Token Transmission
- IdP packages assertion into SAML response
- Sends digitally signed response to SP via HTTP POST
- SP Verification
- SP receives SAML response
- Validates IdP's digital signature
- Extracts and verifies SAML assertion
- Access Authorization
- SP checks user permissions against access policies
- Grants access to requested service if validation is successful
This workflow ensures a seamless and secure login experience, reducing the need for multiple logins across different services.
Key Benefits of IdP-Initiated SSO
- Streamlined Access: Users often face "password fatigue" due to the need to remember multiple login credentials for different applications. However, according to a Statista survey from 2023, 74% of organizations noted that implementing SSO improved user experience and reduced login issues. SSO solution allows users to log in once and access multiple applications, significantly reducing the time spent on logging in.
- Enhanced Security: Managing multiple passwords increases the risk of weak or reused passwords, leading to potential security breaches. However, SSO minimizes the number of passwords users need to remember, reducing the likelihood of weak or reused passwords. Implementing SSO can reduce password-related risks by up to 50%, enhancing overall security.
- Reduced IT Workload: Fewer password resets and easier account management. Pain Point: IT teams spend significant time managing password resets and account provisioning. SSO simplifies the login process and reduces the need for frequent password resets. Organizations using SSO report a 30% reduction in IT support tickets related to password issues.
- Compliance: Centralized audit trails for regulatory needs. Ensuring compliance with data security regulations can be challenging with decentralized authentication systems. However, SSO provides centralized control over user access, making it easier to monitor and audit user activities. Companies using SSO have seen a 25% improvement in compliance with data security regulations.
Exploring SP-Initiated SSO
A Service Provider (SP) in IAM is an entity that offers services and relies on an Identity Provider (IdP) to authenticate users and grant secure access. This ensures that only verified users can access the services.
Service Provider-Initiated Single Sign-On (SP-Initiated SSO) is a process where the authentication request is initiated by the service provider (SP).
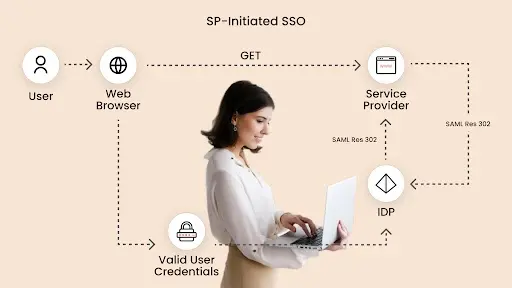
SP-Initiated SSO Workflow
- Initial SP Access & Redirect
- User attempts to access SP service
- SP redirects unauthenticated user to IdP with SAML request
- User Authentication
- User arrives at IdP login page
- Provides credentials for verification
- IdP validates against user database
- SAML Token Generation & Packaging
- IdP creates SAML assertion with user's auth info
- Packages assertion into signed SAML response
- Includes necessary user attributes for SP
- Token Transmission & Receipt
- IdP sends signed SAML response to SP via HTTP POST
- SP receives and extracts SAML assertion
- Verifies IdP's digital signature
- Validation & Authorization
- SP validates assertion against access policies
- Checks user permissions and roles
- Grants access to requested service if validation passes
Benefits of SP-Initiated SSO
- Access to the Services Directly: Users only need to log in once to access multiple services, reducing password fatigue. Users get frustrated when they have to go through multiple login pages to reach the service they need. However, SP-initiated SSO can cut login times by up to 50%. Extra login steps mean more time taken to access services. However, According to Gartner, 70% of users prefer direct access to services without intermediate steps made possible with SP-initiated SSO solutions.
- Hardened Security and Compliance: Centralized authentication reduces the risk of password-related breaches. Traditional login methods expose users to phishing attacks and credential theft. However, SP-initiated SSO can reduce phishing attacks by 60%, according to the SANS Institute. Organizations often struggle to meet regulatory requirements with decentralized authentication methods. However, Companies using SP-initiated SSO have a 30% higher compliance rate with industry standards like GDPR and HIPAA.
- Customizability for Users: Simplifies the management of user access across various services. Users often have to stick to a predefined set of services within a centralized dashboard. However, organizations using SP-initiated SSO report a 40% increase in the adoption of new services. Navigating multiple dashboards can be a hassle. However, A study by Forrester found that 65% of users feel more empowered when they can choose services directly without navigating through a dashboard.
Practical Use Cases of IdP and SP-Initiated SSO
IdP-Initiated SSO Use Cases
- Corporate: Easy access to various internal and external apps.
- Education: Seamless access to learning resources.
- Healthcare: Quick, secure access to patient records.
- E-commerce: Smooth shopping experience across devices.
SP-Initiated SSO Use Cases
- Corporate Environments: Employees can access different internal applications with a single login.
- Educational Institutions: Students and staff can use one set of credentials to access various educational tools and resources.
- Healthcare Systems: Medical professionals can securely access patient records and other critical systems without multiple logins.
How is IdP-Initiated Different from SP-Initiated SSO?
| Aspect | IdP-initiated SSO | SP-initiated SSO |
|---|---|---|
| Login Process | User starts at the Identity Provider (IdP) | User starts at the Service Provider (SP) |
| Authentication Flow | IdP authenticates and redirects to SP | SP redirects to IdP for authentication |
| Common Use Case | Enterprise environments with central portal access | Consumer-facing applications |
| Pros | Centralized user management, simplified experience | Flexibility, easier integration |
| Cons | Requires robust IdP infrastructure, potential single point of failure | More complex with multiple redirects, dependency on SP’s ability |
miniOrange SP-Initiated and IdP-Initiated SSO Solutions
miniOrange offers comprehensive SSO solutions, including SP-initiated, IdP-initiated, and Federated SSO to cater to diverse authentication needs including SAML, OAuth, JWT, and OpenID Connect, and allows for seamless integration with various applications.
- SP-Initiated SSO: Here, the user initiates the login request directly from the Service Provider (SP). miniOrange redirects the user to the Identity Provider (IdP) for authentication. Once authenticated, the user is redirected back to the SP with a SAML assertion, granting them access to the application.
- IdP-Initiated SSO: In this flow, the user begins the login process from the Identity Provider (IdP). miniOrange, acting as the IdP, presents the user with a dashboard of accessible applications. Upon selecting an application, the IdP sends a SAML assertion to the SP, facilitating secure access.
Both methods ensure seamless and secure access to applications, enhancing user experience and security. Additionally, miniOrange’s SSO solution provides enhanced security features, such as multi-factor authentication and adaptive risk-based authentication, to ensure secure access to applications.
Simplify authentication and boost security with miniOrange’s SP and IdP-initiated SSO. Get started today with miniOrange!
FAQs
1. When to use both IdP- and SP-initiated SSO?
Use IdP-initiated SSO when users start authentication from the Identity Provider (IdP) dashboard, enabling seamless access to multiple applications.
Use SP-initiated SSO when users access an application directly, and it redirects them to the IdP for authentication before granting access.
Both are useful based on user flow—IdP-initiated SSO is ideal for centralized access, while SP-initiated SSO ensures seamless login from specific applications.
2. How to Mitigating the Risk of SAML IdP-Initiated SSO?
- Enforce Signed Assertions – Ensure SAML assertions are signed and validated to prevent tampering.
- Enable Audience Restriction – Configure the assertion to be valid only for specific Service Providers (SPs).
- Implement Strong Authentication – Use Multi-Factor Authentication (MFA) to strengthen security at the IdP.
- Restrict Untrusted IdPs – Allow SSO only from trusted identity providers to prevent unauthorized access.
- Monitor and Log SSO Events – Continuously track login attempts and anomalies for quick incident response.
- Limit Session Lifetime – Set expiration times for SAML tokens to reduce risks from session hijacking.
- Use Secure Binding Methods – Prefer HTTP Redirect or POST binding with encryption to avoid interception.
Further Reading
Author



Leave a Comment