What Is an IAM Framework?
An Identity and Access Management (IAM) framework is the security structure that ensures only the right individuals have access to the right resources at the right time for the right reasons. The IAM system does this by verifying user identity through a secure identity management database. Once the identity is confirmed, access management steps in to determine user entitlements, governing what resources and actions are permitted based on the verified identity.
The key components of identity and access management include user authentication, authorization, and auditing. These IAM components ensure the secure flow of data and control over user permissions. Within cloud environments, the components of IAM in cloud computing are essential for managing access to cloud-based resources while maintaining security.
IAM policy components define the rules for user permissions and resource access, making sure that only authorized users can perform specific actions. In simpler terms, the basic components of IAM are authentication (who you are), authorization (what you can access), and auditing (tracking what was accessed and by whom).
Understanding the components of IAM helps organizations build a secure infrastructure, ensuring that sensitive data and systems remain protected while allowing authorized access when needed.
How Does an Identity and Access Management Framework Work?
Identity Management Systems (IMS) are essential for managing user identities and access within an organization. Let us take a step-by-step breakdown of how this operates:
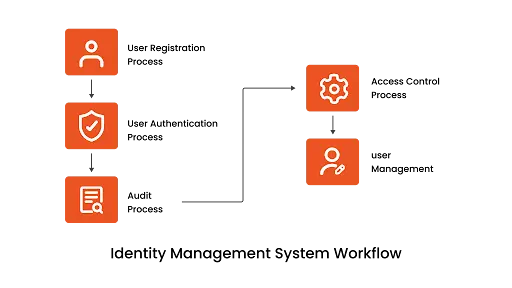
- User Registration Process - The first step is to register new users. During this phase, the system collects important information from users through a form, which it then stores securely. This information is used to verify who the user is and to set up their access rights in the system. Users are given login credentials like a username and password to access the system.
- User Authentication Process - After registration, every time a user tries to log in, the system must confirm their identity through a process called authentication. This is typically done using the credentials they were given during registration. For better security, additional methods like fingerprint scans, security tokens, or a code sent to their phone (known as multi-factor authentication) might also be used.
- Access Control Process - Once the system confirms the user's identity through authentication, it then checks what parts of the system the user is allowed to access. This process, known as access control, uses the user's credentials to look up their permissions in a database and grants or denies access accordingly. This ensures users only get into parts of the system they need for their work.
- User Management - User Management manages users by overseeing and adjusting their activities and access rights within the system. It's helpful to have a central dashboard where administrators can see and manage all user activities. This helps keep the system secure and makes sure that access rights are always appropriate and up-to-date.
- Audit Process - Finally, regular audits are an essential part of an IMS. They help check for security issues and ensure the system works as it should. This is `especially important in cloud-based services where the system’s use and the regulatory environment are constantly changing.
Key Components of Identity and Access Management Framework
- User Identity Management - User Management is a crucial element of any IAM system, user identity management focuses on creating, updating, and maintaining user profiles and their access rights. This includes user provisioning new accounts, managing profiles as roles evolve, de-provisioning accounts when users leave or change roles, and ensuring proper access control and security across the organization.
- User Authentication - It is the process of verifying a user's identity to ensure that only authorized individuals can access systems and data. MFA Methods include traditional passwords, which are common but less secure, Multi-Factor Authentication (MFA), which combines two or more verification steps for increased security, and biometric verification, which uses physical attributes like fingerprints or facial recognition to authenticate users, offering a higher level of protection.
- User Authorization and Access Control - After authenticating a user's identity, it's essential to manage their access to resources and capabilities within the system. This is achieved through methods such as Role-Based Access Control (RBAC), where permissions are assigned based on the user's organizational role, and Attribute-Based Access Control (ABAC), which allocates rights based on specific attributes like department or location. Additionally, the principle of Least Privilege is applied to ensure that users are granted only the minimum access necessary to perform their duties, enhancing the overall security posture.
- Single Sign-On (SSO) - Single Sign-On streamlines access across multiple applications by enabling users to log in once and gain entry without needing to re-authenticate for each service. This not only simplifies the user experience but also enhances security by reducing the number of passwords users must manage. By minimizing password fatigue, SSO decreases the likelihood of users adopting weak security practices, such as reusing passwords. As a result, SSO is a vital feature of contemporary IAM solutions, balancing ease of access with robust security.
- Directory Services - Directory services serve as a centralized repository for storing, organizing, and managing critical information about users, groups, and systems. These services ensure that this data is easily accessible to applications and services that depend on it for authentication, authorization, and other IAM-related functions. By providing accurate and up-to-date information, directory services support informed access control decisions. Examples of commonly used directory services include Microsoft Active Directory, LDAP, and cloud-based solutions like Azure AD.
- Audit and Compliance Reporting - IAM systems are equipped with tools for detailed auditing and generating compliance reports, which are crucial for complying with various regulatory standards. This includes maintaining activity logs that record user actions, access times, and attempted security breaches. Additionally, these systems offer compliance reporting capabilities to create necessary documentation for regulations such as GDPR, HIPAA, and others, ensuring organizations meet legal and security obligations.
- Identity Governance and Administration (IGA) - IGA refers to the framework and tools that oversee and manage the lifecycle of user identities within an organization. This includes setting up new identities (provisioning), conducting regular access reviews, and enforcing compliance with regulatory standards. By automating these processes, IGA ensures that only authorized personnel have access to specific resources, thereby enhancing security and compliance. This is especially critical in sectors like finance, healthcare, and government, where precise management of identity and access data is mandatory to meet strict regulatory requirements.
Importance of a Solid Identity and Access Management Solution
A robust Identity and Access Management (IAM) solution is essential for several critical aspects of organizational management and security. Here’s the significance:
- Security Enhancement: IAM limits access to sensitive information to authorized users only, thereby reducing the likelihood of data breaches and mitigating insider threats. This tight control over access safeguards an organization's data assets.
- Compliance Assurance: By managing and logging user activities and access, IAM facilitates adherence to various industry regulations and standards, helping organizations avoid penalties and legal issues.
- User Experience Improvement: With features such as Single Sign-On (SSO) solution and automated user provisioning, IAM simplifies how users interact with multiple systems, reducing the hassle of remembering multiple passwords and streamlining the login process.
- Operational Efficiency: IAM automates many routine tasks related to identity verification and access management, thereby freeing up IT staff to concentrate on more strategic initiatives. This automation not only speeds up processes but also reduces errors associated with manual interventions.
Implementing an IAM solution empowers organizations to protect sensitive data, comply with regulatory requirements, enhance user satisfaction, and optimize operational workflows.
Enhance Security with advanced IAM
Implementing a robust Identity and Access Management (IAM) system is crucial for maintaining security and enhancing the operational efficiency of any organization. Such systems are essential not just for safeguarding sensitive information but also for ensuring that access is appropriately aligned with user roles and responsibilities. As the landscape of technology and cybersecurity threats continues to evolve, IAM systems must also progress, adopting cutting-edge technologies such as artificial intelligence and machine learning. These advancements help to improve security measures and optimize the user experience, keeping the organization ahead of potential security risks.
For those looking to stay at the forefront of this evolution, miniOrange provides advanced IAM solutions tailored to meet these dynamic needs.


Leave a Comment