For accounts that possess the utmost sensitive information and critical systems, managing who gets access to what is vital. This is where the PAM solution plays an important role. Privileged Access Management is a lucrative branch of IAM designed to monitor, record, and protect critical resources for accounts.
However, have you thought about the repercussions of choosing the wrong PAM? It can lead to solutions that cause headaches, such as systems that don’t work well together, teams that are reluctant to use the tool, or worse, security gaps that hackers can exploit.
The question arises: how to evaluate the best PAM solutions suitable for your organization’s needs? Choosing a PAM solution isn’t just ticking boxes on a checklist. It’s about making sure the solution fits your company’s size, needs, and future plans.
To simplify the research process and provide complete transparency without overwhelming you, we screened dozens of PAM solutions available in the market. The parameters included were different vendors, features, security strengths, and real customer feedback. We want to make sure we simplify access and future-proof your business with PAM.
Keeping this in mind, let’s explore the top PAM solutions of 2025 and the factors that make them stand out.
10 Best PAM Software Solutions in 2025
1. miniOrange PAM Solution

miniOrange Privileged Access Management is a leading solution in the cybersecurity space, recognized for its unified and scalable platform that helps organizations manage, monitor, and secure privileged credentials across cloud, on-premises, and hybrid environments. With a focus on user experience and security, miniOrange powers businesses to implement least privilege policies, reduce attack surfaces, and maintain compliance with industry regulations.
Their PAM solution is designed to streamline deployment and minimize complexity, offering agentless architecture and seamless integration with existing IT ecosystems. Whether you're a small business, a large enterprise, or part of a cybersecurity team, miniOrange provides the flexibility and control needed to protect sensitive systems and data from unauthorized access.
Key Features
- Credential vaulting with automated password rotation
- Just-in-Time (JIT) access for temporary privilege elevation
- Granular access control based on roles and policies
- Real-time session monitoring and recording
- Privileged account discovery across endpoints and servers
- Multi-Factor Authentication (MFA) for secure access
- Endpoint privilege management for remote devices
- Integration with SIEM, IAM, and ITSM platforms
- Compliance-ready audit logs and reporting tools
Are you compliant with the changing regulatory requirements? Know more with miniOrange
miniOrange PAM Pros
- Simplified deployment with agentless architecture
- Strong support for hybrid and cloud-native environments
- Intuitive interface and centralized dashboard
- Competitive pricing and flexible licensing options
- Scalable for both SMBs and large enterprises
- Continuous innovation in Zero Trust and adaptive access controls
miniOrange PAM Cons
- Advanced customizations are in the planning phase
- Certain enterprise-grade features are for specific businesses
miniOrange Ratings & Reviews:
- G2: 5.0
2. ManageEngine PAM360
ManageEngine PAM360 is an enterprise-grade Privileged Access Management solution developed by Zoho Corporation. Designed to secure, manage, and monitor privileged accounts across IT infrastructure, PAM360 offers centralized credential vaulting, session recording,
access workflows, and integrations with SIEM and identity platforms. As part of the broader ManageEngine suite, PAM360 works well in IT ecosystems already using products like ADManager, ServiceDesk Plus, or OpManager.
ManageEngine PAM Pros
- The feature set includes password vaulting, session monitoring, approval workflows, and audit-ready reporting.
- Offers role-based access with just-in-time elevation and command-level restrictions.
- Compatible with SIEM tools, ITSM platforms, and other ManageEngine products.
ManageEngine PAM Cons
- Users found the scalability to be limited, especially when dealing with a large number of servers
- Documentation for setup is inadequate, requiring users to troubleshoot
- Limited customer support
ManageEngine Ratings & Reviews:
- G2: 4.5
3. CyberArk PAM
CyberArk PAM is a leading enterprise solution designed to secure, monitor, and manage privileged accounts and credentials across hybrid, cloud, and on-premise environments. It helps organizations reduce risk by enforcing least privilege, isolating sensitive sessions, and automating credential rotation.
CyberArk PAM includes features like Vaulting Technology for secure credential storage, Privileged Session Manager (PSM) for session isolation and recording, and Privileged Threat Analytics (PTA) for real-time anomaly detection.
CyberArk PAM Pros
- Advanced threat detection with behavioral analytics and session monitoring
- Strong compliance support with detailed audit trails and access certification
- Flexible deployment options and broad integration ecosystem
CyberArk PAM Cons
- CyberArk's solutions are generally considered expensive.
- The initial setup and configuration can be challenging and require significant planning, expertise.
- Users new to CyberArk may find the interface unintuitive.
CyberArk Ratings & Reviews:
- G2: 4.5
4. BeyondTrust PAM
BeyondTrust is another PAM solution provider, offering a suite that includes Password Safe, Privileged Remote Access, and Endpoint Privilege Management. It supports Zero Trust, session recording, and least privilege enforcement across cloud, on-prem, and hybrid environments.
BeyondTrust PAM Pros
- Full-featured PAM suite with strong session monitoring and credential management
- Supports both cloud and on-prem deployments
- Granular access control and policy enforcement
- Scalable architecture for large enterprises
BeyondTrust PAM Cons
- Initial setup and policy configuration can be complex for new users
- Licensing flexibility and cost optimization are areas of ongoing refinement
- Potential gaps in integration with certain systems and security tools
BeyondTrust Ratings & Reviews:
- G2: 3.3
5. Okta PAM
Okta PAM is a modern solution designed to secure and govern privileged access across cloud and on-premise environments. As part of the Okta Workforce Identity Cloud, it eliminates standing credentials like static SSH keys and passwords, replacing them with dynamic, policy-driven access controls. Okta PAM centralizes the management of privileged accounts, service accounts, and secrets, while offering session recording, approval workflows, and real-time auditing.
Okta PAM Pros
- Okta PAM integrates seamlessly with Okta’s broader identity ecosystem, offering unified governance and visibility.
- It supports customizable approval flows, time-bound access, and session monitoring for compliance.
- The platform is cloud-native, scalable, and user-friendly, making it ideal for organizations embracing digital transformation.
Okta PAM Cons
- The integration doesn't extend to web applications, databases, or Kubernetes clusters.
- Being server-centric can be a limitation for organizations with diverse infrastructure and applications.
- Okta's PAM solution can be expensive.
Okta Ratings & Reviews:
- G2: 4.5
6. Delinea
Delinea Privileged Access Management (PAM) is a robust, enterprise-grade solution designed to secure and manage privileged identities across hybrid IT environments. Formerly known as Thycotic, Delinea offers a suite of tools like Secret Server, Privilege Manager, and DevOps Secrets Vault. They help organizations enforce least privilege, automate credential rotation, and monitor privileged sessions. Its platform supports both cloud and on-premise deployments, making it flexible for diverse infrastructure needs.
Delinea PAM Pros
- known for its intuitive interface and fast implementation, often requiring fewer resources than traditional PAM solutions.
- It supports granular access controls, dynamic privilege elevation, and detailed audit logging.
- The platform integrates well with Active Directory, SIEM tools, and DevOps pipelines, and offers strong support for compliance and cyber insurance requirements.
Delinea PAM Cons
- Issues with its platform's completeness and stability.
- Delinea may not fully support modern technologies.
- The more advanced features of Delinea can be challenging and require significant learning time.
Delinea Ratings & Reviews
- G2: 4.8
7. Microsoft PAM
Microsoft offers Privileged Access Management capabilities through solutions like Microsoft Entra ID and Microsoft Purview PAM, which are tightly integrated into the Microsoft 365 and Azure ecosystems. These tools focus on enforcing Zero Trust principles, enabling Just-in-Time access, and providing granular control over privileged tasks. Microsoft’s PAM is particularly effective for organizations already invested in Azure Active Directory and Microsoft cloud services.
Microsoft PAM Pros
- Seamless integration with Microsoft 365, Azure, and Entra ID
- Strong support for Just-in-Time and time-bound access workflows
- Built-in session monitoring and audit capabilities
- Automated policy enforcement and access approvals
- Ideal for cloud-native and hybrid environments
Microsoft PAM Cons
- Limited visibility across non-Microsoft platforms
- Evolving advanced reporting and analytics
- High cost of implementation
Microsoft Ratings & Reviews
- G2: 4.5
8. StrongDM
StrongDM is a Zero Trust PAM platform known for its dynamic access control, agentless architecture, and real-time session monitoring. It centralizes access to infrastructure like databases, servers, and Kubernetes clusters, making it a popular choice for DevOps and security teams. StrongDM emphasizes ease of use, fast deployment, and compliance-friendly audit trails.
StrongDM Pros
- Agentless setup with fast deployment across cloud and on-prem environments
- Real-time session logging and granular role-based access control
- Strong support for Just-in-Time access and credential injection
- Excellent customer support and intuitive interface
- Built for modern infrastructure and DevOps workflows
StrongDM Cons
- Complexity in the initial setup and configuration
- Integration with legacy systems is an area of expansion
- Lack of support for certain functionalities
StrongDm Ratings & Reviews
- G2: 4.6
9. IBM Security
IBM Security is a well-established name in enterprise cybersecurity, offering a comprehensive suite of tools to protect identities, data, and infrastructure. Its PAM solution, the IBM Security Verify Privilege, is designed to manage privileged credentials, enforce least privilege, and monitor high-risk activities across hybrid environments. With components like Privilege Vault and DevOps Vault, IBM provides centralized control and visibility for large-scale organizations.
IBM Security Pros
- Strong session monitoring and credential vaulting capabilities
- Scalable architecture for complex enterprise environments
- Supports Zero Trust and hybrid cloud deployments
- Offers both cloud-based and on-premises deployment options
IBM Security Cons
- Difficult Setup and Administration
- Complex Licensing
- Lack of Customization
IBM Security Ratings & Reviews
- G2: 4.5
10. HashiCorp Boundary
HashiCorp Boundary is an identity-aware proxy built for cloud-native environments, offering secure, least-privileged access to dynamic infrastructure. It replaces traditional access methods like VPNs and bastion hosts with identity-driven controls, session recording, and credential injection. Boundary integrates with trusted identity providers for single sign-on and supports Just-in-Time access to virtual machines, databases, and Kubernetes clusters. It’s especially suited for DevOps teams and organizations managing distributed systems.
HashiCorp Boundary Pros
- Identity-based access with dynamic host discovery and session recording
- Just-in-Time credential injection for passwordless access
- Seamless integration with HashiCorp Vault and Terraform
- Scalable architecture for multi-cloud and hybrid environments
- Open-source flexibility with enterprise-grade features
HashiCorp Boundary Cons
- Advanced policy management and RBAC granularity are evolving
- A steeper learning curve than some simpler, more traditional solutions
- Broader ecosystem integrations are part of the product’s strategic growth
HashiCorp Ratings & Reviews
- G2: NA
How to Choose the Best PAM Solution
In the previous section, you understood the best PAM solutions available in the market, but do you know the factors that should also be considered? To break it down, our expert Pradeep Kumar, Senior Software Engineer (PAM Solution), has listed a few pointers to keep in mind while choosing a PAM solution.
“People have the time and skills, and if they decide to hack your system, they’ll do whatever it takes to achieve it. That’s why PAM is so important. It helps you control who gets access to what, when & where and keeps your systems safe.”
-Pradeep Kumar
(Senior Software Engineer – PAM Solutions, miniOrange Inc.)
Proven Track Record of Security
Choose a PAM solution with a solid track record in defending against advanced cyber threats. Check for a history of real-world protection against privilege escalation, insider attacks, and credential misuse. Moreover, look for platforms that evolve rapidly with emerging technologies such as behavioral analytics, threat detection, and integration with Zero Trust frameworks.
Core PAM Features & Capabilities
The fundamentals of PAM include the features that manage, monitor, and secure privileged access. Essential capabilities include centralized credential vaulting, session recording, just-in-time access provisioning, and granular role-based controls. These functions help reduce the attack surface by limiting over-privileged accounts and tracking every action taken during sensitive sessions.
Audit, Compliance, and Cyber Insurance
A robust PAM platform or solution will help you meet regulatory requirements like GDPR, HIPAA, ISO/IEC 27001, and PCI-DSS. It should provide detailed audit trails, tamper-proof logging, and customizable reports to satisfy audit demands and insurance providers. Effective reporting not only supports legal compliance but also enables risk management and visibility into who has accessed what, when, and why.
Integration With Your Tech Stack
Modern IT environments include a suite of apps, servers, and databases. A good PAM solution must integrate seamlessly with existing tools like Active Directory, Azure AD, LDAP, SIEM platforms, DevOps pipelines, ticketing systems, and cloud services like AWS and GCP. Compatibility ensures faster deployment, fewer disruptions, and stronger security coordination across departments and systems. Also, ask for documentation clarity for a simplified setup.
Deployment Flexibility
Organizations differ in their infrastructure and risk posture, so your PAM solution should adapt to your preferred deployment model. If you need an on-premise installation for strict control, a cloud-native setup for scalability, or a hybrid model to bridge legacy systems and modern workflows, the vendor should offer options that suit your architecture.
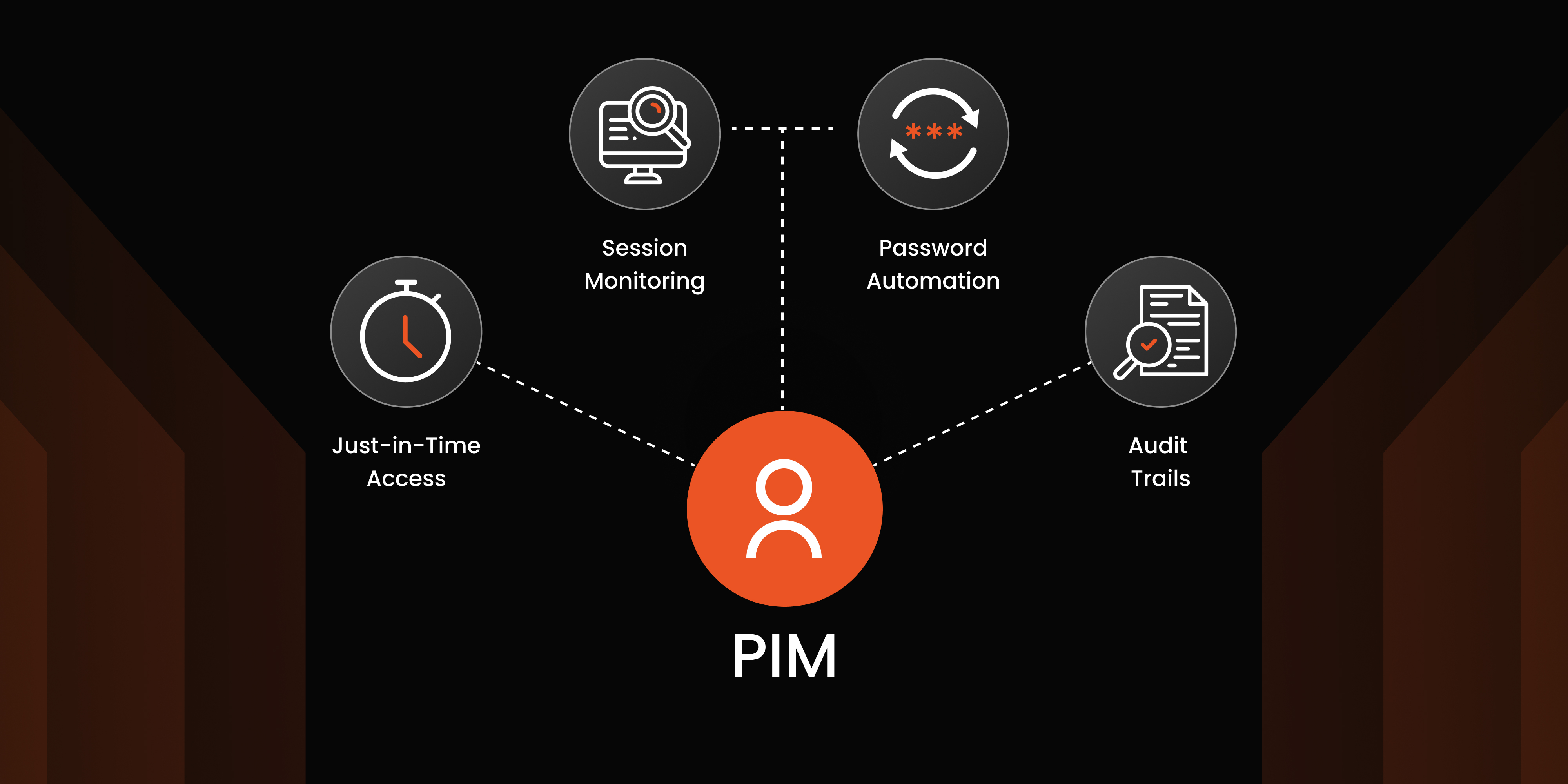
Essential Elements of Privileged Access Management
PAM is an identity security solution that helps businesses control and monitor access to critical systems and sensitive data and avoid potential cyber threats lurking around them. It focuses on managing privileged accounts, those with elevated permissions like system administrators, database managers, or cloud admins.
A PAM solution typically includes:
- Password vaults to securely store passwords and keys
- Session monitoring to track what privileged users do
- Just-in-time access to grant temporary permissions only when needed
- Integration with other tools like Identity and Access Management (IAM), SIEM, and DevOps platforms.
Why Your Business Needs PAM?
1. Prevents Security Breaches
Privileged accounts are the primary target for cyber attackers. PAM solutions minimize the risk of breaches by restricting access to sensitive systems, enforcing strong authentication, and recording privileged activity. Organizations can reduce potential entry points for attackers and restrict the damage if an account is compromised by managing who has access to which resource or system.
2. Enhances Visibility and Control
PAM allows organizations to track all actions taken by privileged users. Every login, command, and configuration change can be recorded and reviewed. This level of visibility not only deters misuse but also helps identify unusual behavior early before it leads to serious consequences.
3. Ensures Regulatory Compliance
Many compliance standards, such as GDPR, HIPAA, and PCI DSS, require strict controls over access to critical systems and data. PAM supports these requirements by creating auditable trails, implementing role-based access controls, and enabling centralized reporting. The PAM compliance thus simplifies audits and helps avoid costly penalties.
4. Reduces Risk of Insider Threats
Whether intentional or accidental, insider misuse of privileged access can be just as damaging as external threats. PAM reduces this risk by implementing the principle of least privilege and granting elevated access only when necessary and for a limited time.
How PAM Will Work for You?
Step 1: Secure the Keys with Credential Vaulting
The first step in a PAM solution is to store all privileged credentials, such as passwords, SSH keys, and certificates, in an encrypted vault. This ensures that sensitive login details are never openly visible or shared. Access to these credentials is tightly controlled and logged.
Step 2: Provide Access Only When Needed
Rather than granting users permanent admin rights, PAM gives access only when it's needed for a specific task or time window. Once the task is complete, the elevated access is revoked automatically. This reduces the opportunity for misuse or unauthorized changes.
Step 3: Monitor Every Session in Real Time
PAM tools record the actions of privileged users during their sessions. This includes commands entered, files accessed, and system changes made. Security teams can monitor these sessions live, and if any suspicious behavior is detected, the session can be paused or terminated immediately.
Step 4: Enforce Rules with Access Policies
PAM applies rules to determine who can access what and under which conditions. These policies might depend on a user's job role, time of access, or type of device. This ensures everyone only gets the level of access they genuinely need.
Step 5: Record and Review All Actions
All privileged activity is automatically logged by the PAM system. These audit logs help security teams investigate incidents, ensure accountability, and stay compliant with industry regulations.
Step 6: Automate Key Security Tasks
Many PAM solutions automate repetitive but crucial tasks such as rotating passwords, disabling unused accounts, and managing access approval workflows. This automation largely reduces errors and improves operational efficiency.
In a Nutshell
PAM is not something you can look over in 2025. The lack of security around privileged accounts can cost you millions. Choosing the right PAM solution can make all the difference in protecting your organization’s most critical assets. As 2025 continues to raise the bar for data protection, the best privileged access management software will be one that offers strong security foundations, supports modern architectures, simplifies compliance, and scales with your growth.
FAQs
What are the risks of not using a PAM solution?
Organizations have a great risk of data breaches, ransomware attacks, and insider threats. Uncontrolled access to critical systems can result in unauthorized changes and data leaks, making it difficult to maintain security and regulatory compliance.
What makes a PAM solution modern or next-generation?
A modern PAM solution incorporates features like Just-in-Time access, Zero Trust principles, session monitoring, agentless deployment, and native support for hybrid and multi-cloud environments. These capabilities improve visibility, reduce standing privileges, and align with current cybersecurity strategies.
What features should you look for in a PAM solution?
Core features to look for include credential vaulting, session recording, least privilege enforcement, Just-in-Time access, audit logs, role-based access control, integration with SIEM and IAM tools, and support for regulatory reporting. These features ensure visibility, control, and accountability across privileged activities.
Can PAM solutions help with regulatory compliance?
PAM is crucial for achieving compliance with regulations in sectors like finance, healthcare, retail, and government. Compliance regulations such as HIPAA, SOX, GDPR, PCI-DSS, and NIST require strict access controls and auditing, all of which can be supported by a PAM solution through logging, policy enforcement, and access governance.





Leave a Comment