As the number of online accounts and digital services continues to skyrocket, so does the risk of password-related breaches. Shockingly, hacking tools can crack 96% of the most common passwords in less than a second. This alarming reality highlights the critical vulnerabilities in password security, which is further made worse by users' struggles to create and remember complex passwords, leading to poor password management practices such as password reuse and insecure storage.
Implementing enterprise password management best practices, such as centralizing and automating password processes, can minimize this burden, ensuring stronger security, and better compliance, and reducing the risk of breaches caused by human error.
In order to secure your digital ecosystem in 2024, let's look at 10 Password Management Best Practices
1. Centralize Password Management
Centralizing password management under the IT team ensures consistent enforcement of security policies and enhances oversight across the organization. By adopting enterprise password management best practices, you can ensure that all passwords meet stringent security requirements and have audibility into password hygiene throughout the business. This approach not only strengthens security but also simplifies management and compliance efforts.
2. Enable Multi-Factor Authentication (MFA)
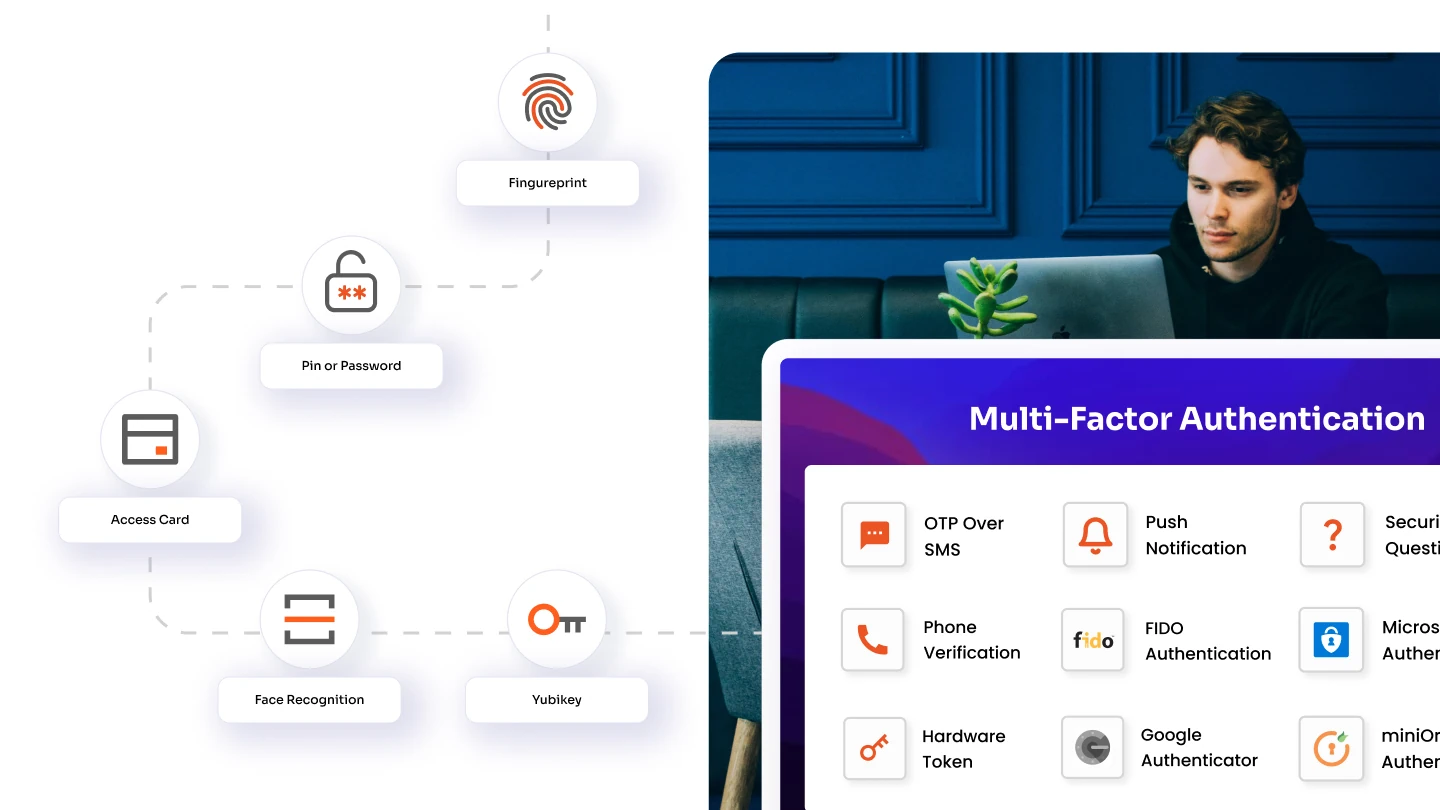
Implementing Multi-Factor Authentication (MFA) is a crucial component of any password management strategy. MFA adds another layer of security by requiring users to provide more than just a password, such as a one-time code or biometric authentication. This significantly reduces the risk of unauthorized access, as even if a password is compromised, the attacker would still need the second authentication factor to gain access. Integrating MFA is one of the best practices for password management to protect against modern threats.
3. Implement Single Sign-On (SSO)
Single Sign-On (SSO) simplifies the user experience by allowing users to authenticate once and gain access to multiple applications. However, to further strengthen security, SSO should be paired with Multi-Factor Authentication (MFA) and Privileged Access Management (PAM). This combination ensures that even if an SSO credential is compromised, the attacker’s access remains limited, maintaining both authentication and authorization security.
4. Refrain from Storing Passwords in Browsers
Browsers are not designed for secure password management, and most lack security features by default. Relying on browser-based password storage can pose significant risks, as passwords can be easily accessed if the device is stolen or if the browser is compromised through cyberattacks or malware.
If your organization allows browser-based password storage, it’s essential to enforce a secure approach by enabling all available security features. However, a more secure solution is to use enterprise password management tools or Privileged Access Management (PAM) solutions that offer browser extensions. These extensions securely manage and autofill credentials for websites and web applications, ensuring passwords are stored in a central, encrypted vault. This integration not only enhances security but also minimizes password reuse by keeping passwords in the background, reducing the risk of user error.
5. Streamline Your Security with a Password Manager
Managing multiple passwords across various accounts can be a tedious task. A password manager provides an effective solution by securely storing all your passwords in an encrypted vault, eliminating the need to remember them. It also generates strong, unique passwords for each account, reducing the risk of password reuse and enhancing your overall security. It securely stores and manages all your credentials in a single, encrypted vault. This approach centralizes password management, integrating seamlessly with existing tools. Additionally, by keeping these credentials hidden from end users, an extra layer of security is added.
6. Implement and Enforce Password Expiration Policies
Even the most secure passwords can become vulnerable if they fall into the wrong hands. Password expiration policies are essential in ensuring that unauthorized access isn’t granted indefinitely. By requiring users to change their passwords after a set period, these policies help to refresh credentials regularly, reducing the risk of unauthorized access due to stolen or compromised passwords. Leverage advanced features for managing and enforcing password expiration policies. These include customizable settings that allow administrators to define parameters like password age and expiration intervals, ensuring that policies are tailored to your organization's needs.
7. Continuous Monitoring and Auditing
Effective password management is not just about setting policies; it requires ongoing attention Continuous monitoring and regular auditing of user accounts are crucial to maintaining security. Real-time monitoring, along with frequent reviews of user activity logs and conducting security audits, can help identify suspicious or unauthorized access attempts. By swiftly detecting and addressing any security breaches, you can minimize potential damage and enhance your overall security posture. Utilize comprehensive monitoring and auditing tools that provide continuous visibility into user activity and enforce access policies effectively. These tools allow you to detect errors or malicious activity in real-time, enabling quick response before issues escalate.
8. Integrate Your Password Vault with Other Business Solutions
For streamlined password management, it's essential to ensure that your password manager or Privileged Access Management (PAM) solution integrates smoothly within your enterprise IT ecosystem. By doing so, you can simplify the workload for your IT and security teams and ensure seamless operation with tools that manage user identities and system access.
A best practice is to integrate your vault with identity management solutions like Active Directory or Azure AD which ties users to unique identities. Additionally, consider integrating with workflow tools to efficiently route help desk requests, such as password resets, and with Identity Governance and Administration (IGA) systems for comprehensive identity governance.
9. Implement an Enterprise Password Management Solution
For individuals and small businesses, a robust password manager is usually sufficient to manage and secure personal passwords. It should incorporate several of the password management best practices discussed here.
However, for larger businesses and enterprises, a Privileged Access Management (PAM) solution is the way to go. PAM not only includes all these password management best practices but also adds advanced features tailored to the complex needs of large organizations. With PAM, you can rest assured that passwords are managed securely, relieving your users from the burden of password management so they can focus on their core responsibilities.
10. Store Passwords in a Password Management System
Using a password management system is one of the most effective ways to keep your passwords secure and organized. Instead of remembering multiple passwords, you only need to recall one master password. This master password unlocks a secure vault where all your other passwords are stored.
Password managers not only store your passwords but also generate strong, unique passwords for each new account you create. When it’s time to log in, the password manager can automatically fill in your credentials or allow you to copy and paste them effortlessly. Many password managers also offer encrypted synchronization across devices, ensuring that your passwords are available to you wherever you go, even on your mobile phone.
Transforming Your Password Management with miniOrange
Adopting these password management best practices is a critical step in fortifying your defense against cyber threats, ensuring compliance with data privacy regulations, and significantly boosting the security of your online accounts. However, managing passwords across various systems and platforms can be a complex and overwhelming challenge for any IT team.
Author


Leave a Comment