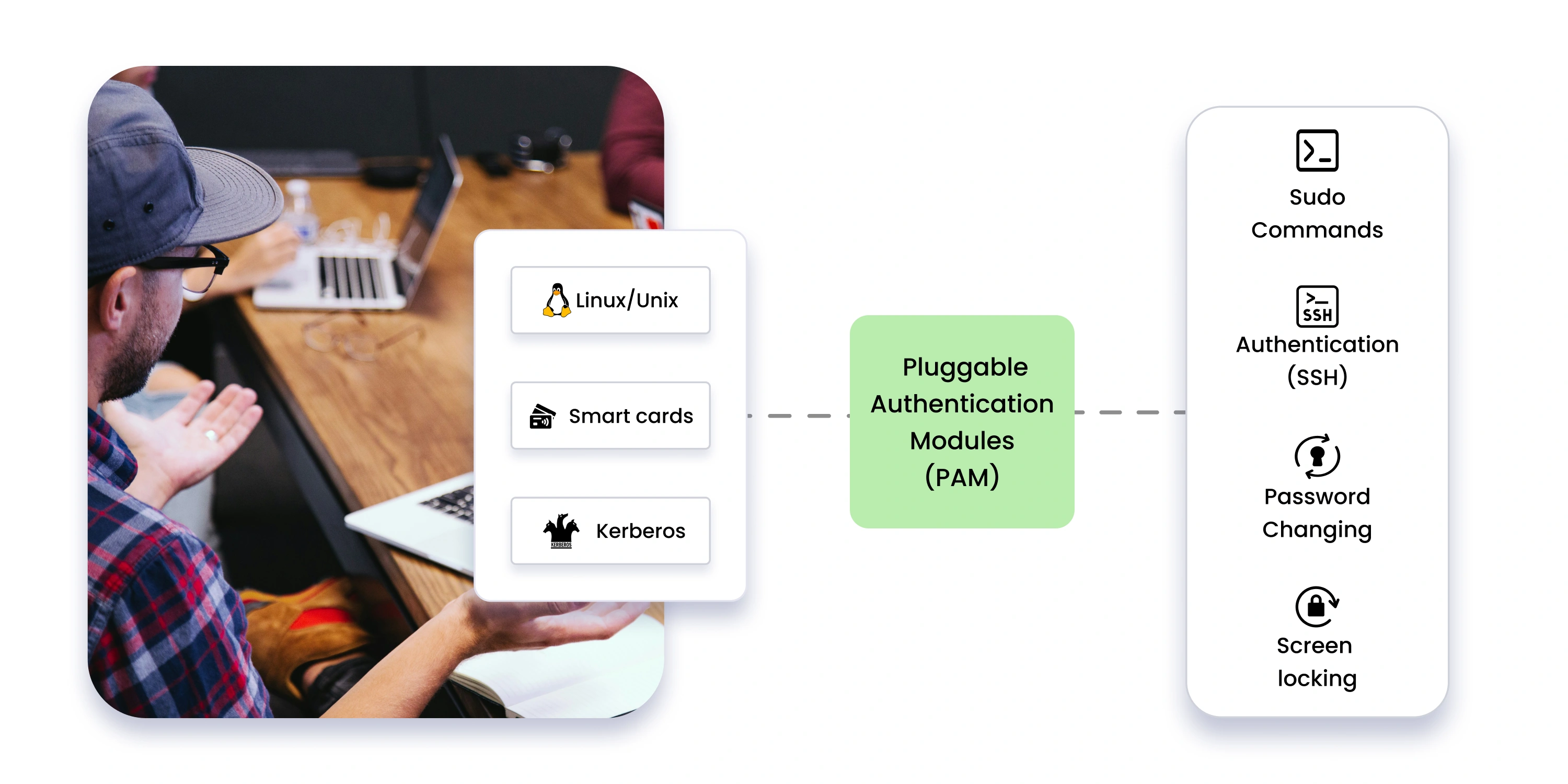
In today’s evolving digital landscape, managing authentication securely and efficiently is a top priority. Pluggable Authentication Modules (PAM) provide a robust framework that simplifies and centralizes the way Linux and Unix-based systems handle authentication. PAM is a powerful framework that allows system administrators to integrate a wide range of authentication methods into their systems without needing to modify the underlying application code.
Originally developed by Sun Microsystems, PAM is now a critical component in Linux, macOS, and other Unix-based environments, offering flexibility and modularity for authentication management. PAM is widely used in Linux and macOS environments for user authentication, offering a flexible and modular approach to security. It simplifies the implementation of different authentication methods—from traditional password checks to more advanced options like biometrics or multi-factor authentication—by providing a standard interface between applications and authentication services. This modularity ensures that different authentication mechanisms can be easily swapped out or customized as needed, without disrupting the overall system.
Why is PAM so Important?
- Customizable Authentication for Applications - PAM allows system administrators to create unique authentication rules for different applications. For instance, logging into the system might only require a password, while accessing a secure database could mandate multi-factor authentication (MFA).
- Support for Multiple Authentication Methods - With PAM, you can stack various authentication mechanisms, ranging from traditional passwords to advanced options like biometrics and MFA, enhancing security across systems.
- Cross-System Compatibility - PAM is widely supported across Unix-based systems, including Linux, Solaris, HP-UX, and AIX, making it a universal solution for diverse environments.
- Flexibility and Control - System administrators can enable or disable PAM modules based on specific security needs, ensuring the system remains both secure and adaptable.
What is PAM (Pluggable Authentication Modules)?
Pluggable Authentication Modules (PAM) is a flexible authentication framework used in Linux and UNIX-based systems to manage user authentication efficiently. It acts as a bridge between applications and authentication mechanisms, allowing system administrators to configure authentication without modifying the application code.
Instead of hardcoding authentication methods into applications, PAM provides a modular design, where authentication rules are stored separately and can be updated independently of the application. This makes it easy to add, remove, or modify authentication methods without disrupting system functionality.
For example, PAM is commonly used in:
- Login prompts (console and GUI-based)
- SSH authentication
- Sudo command authorization
- Password changes
- Screen locking
Let us have a look at few of the Authentication Mechanisms Supported by PAM
- Multi-Factor Authentication (MFA)
- Password-based authentication
- Biometrics (Fingerprint, Face Recognition)
- One-Time Passwords (OTP)
- Smart Cards & Security Tokens
With PAM, administrators can define authentication rules dynamically, making it a powerful tool for securing Linux and UNIX systems.
How Does PAM Work?
PAM (Pluggable Authentication Modules) operates as a middleware layer that connects system applications with different authentication mechanisms. Instead of hardcoding authentication methods into each application, PAM enables flexible authentication policies that can be modified without altering the application code.
How Authentication Works with PAM
When a user attempts to log in (via SSH, console, or sudo), the authentication process follows these steps:
- The application requests authentication (e.g., login, ssh, su).
- PAM loads the relevant authentication modules as specified in its configuration files (found in /etc/pam.d/).
- Each module verifies credentials based on the defined rules.
- If authentication succeeds, access is granted; otherwise, it is denied.
PAM makes authentication modular, scalable, and customizable, allowing system administrators to define multiple authentication methods, mentioned above.
The Anatomy of a PAM Configuration File
PAM uses configuration files to define authentication policies for different applications. These files are typically stored in:
📂 /etc/pam.d/ – Contains individual configuration files for different system services (e.g., login, sshd, sudo).
📂 /etc/pam.conf – A single-file configuration (less common, used on some UNIX systems).
Let's look at an example PAM configuration file for login authentication:
📄 Example: /etc/pam.d/login
plaintext
CopyEdit
auth required pam_unix.so try_first_pass
account required pam_unix.so
password required pam_unix.so use_authtok
session optional pam_lastlog.so silent
Each line consists of four parts:
- Module Type – Defines the authentication stage:
- auth → Verifies user identity (e.g., password, MFA).
- account → Checks account validity (e.g., expiration, access policies).
- password → Handles password updates or resets.
- session → Manages session-related activities (e.g., logging last login time).
- Control Flag – Specifies how PAM should handle module results:
- required → Must pass for authentication to succeed.
- requisite → Must pass, but if it fails, authentication stops immediately.
- sufficient → If successful, authentication continues without checking further modules.
- optional → Used if no other required module is present.
- Module Path – Specifies the PAM module (e.g., pam_unix.so for UNIX-based authentication).
- Module Arguments – Additional options passed to the module (e.g., silent, use_authtok).
Common PAM Modules and Their Functions
| Module Name | Function |
|---|---|
| pam_unix.so | Handles traditional UNIX authentication (passwords, shadow file). |
| pam_tally.so | Tracks failed login attempts and locks accounts after multiple failures. |
| pam_google_authenticator.so | Implements Two-Factor Authentication (2FA) using Google Authenticator. |
| pam_ldap.so | Enables authentication through LDAP directories. |
Key Features of PAM
- Modular and Configurable – Authentication policies are defined in separate configuration files, making customization easy.
- Supports Multiple Authentication Methods – Works with passwords, biometrics, OTPs, smart cards, and Multi-Factor Authentication (MFA).
- Application Independence – PAM ensures authentication happens without changing individual applications.
- Security Enhancement – Administrators can stack multiple authentication methods for added security, such as requiring both a password and an OTP.
Real-World Use Cases of PAM
PAM is widely used across enterprise IT environments to enhance authentication security and improve user management.
- Centralized Authentication with LDAP/Kerberos - Organizations managing multiple servers and users often rely on centralized authentication using LDAP (Lightweight Directory Access Protocol) or Kerberos. PAM enables single sign-on (SSO) by allowing users to authenticate once and access multiple systems without separate credentials.
- Enforcing Multi-Factor Authentication (MFA) - To enhance security, PAM can integrate MFA solutions like Google Authenticator, miniOrange MFA, or hardware tokens. Adding MFA ensures that even if a user's password is compromised, an additional authentication step (such as an OTP or biometric verification) is required to gain access.
- Preventing Brute-Force Attacks with Failed Login Attempts - PAM can track failed login attempts and lock accounts after multiple failed authentication attempts, mitigating brute-force attacks. The pam_tally2.so or pam_faillock.so module helps enforce automatic account lockouts after a defined number of failed attempts.
This ensures:
1. Accounts lock after 5 incorrect login attempts
2. They automatically unlock after 15 minutes
Integrating Linux and macOS MFA with PAM Using miniOrange
Multi-Factor Authentication (MFA) is essential for enhancing system security, and miniOrange provides a seamless way to integrate MFA with PAM on both Linux and macOS. By implementing miniOrange’s PAM module, administrators can enforce authentication factors like OTP, push notifications, and biometric verification for login processes.
Integrating Linux MFA with PAM Using miniOrange
miniOrange provides a robust solution for implementing Multi-Factor Authentication on Linux systems via PAM. Here’s a high-level view of how miniOrange integrates MFA with PAM on Linux:
- Install miniOrange PAM Module:
miniOrange offers a PAM module that integrates MFA with Linux. It supports a variety of authentication factors such as OTP (One-Time Password), push notifications, and biometric authentication. By installing the miniOrange PAM module, you enable MFA for your login processes. - Configure MFA Providers:
You can choose from various MFA providers available through miniOrange, including:- Time-based OTP (TOTP): One-time passwords generated via apps like Google Authenticator.
- Push Authentication: Push notifications sent to a user’s mobile device for approval.
- FIDO2/WebAuthn: Secure authentication via hardware tokens like YubiKeys.
- PAM Configuration:
After installing the module, you need to modify the PAM configuration to integrate miniOrange’s MFA into your login process. Typically, this involves editing the PAM configuration files located in/etc/pam.d/. - Testing:
Once the setup is complete, test the configuration to ensure that the MFA challenge is triggered during login. A successful login will require both the password and the second authentication factor (e.g., OTP or push notification).
Integrating MFA on macOS with miniOrange
Similar to Linux, macOS also supports PAM, allowing you to integrate MFA into your system login process. Here’s how miniOrange’s MFA connectors can be configured for macOS:
- Install miniOrange PAM Module for macOS:
miniOrange provides a compatible PAM module for macOS that allows the integration of MFA. - Choose Your MFA Method:
Select from different MFA methods such as OTP, push authentication, or biometric options. miniOrange supports MFA solutions that work across different platforms, providing flexibility for macOS users. - Modify PAM Configuration Files:
On macOS, PAM configuration files are usually located in/etc/pam.d/. These files define the authentication methods that are applied when a user logs into the system. To integrate MFA, the miniOrange PAM module must be added to the configuration. - Test Your Configuration:
After modifying the configuration, test the setup by attempting to log into the macOS system. During the login, the system should prompt for the second factor (OTP, push, etc.).
Why Organizations Rely on PAM
Pluggable Authentication Module (PAM) is crucial for organizations looking to safeguard their critical IT infrastructure, whether on-premises or in the cloud. By providing scalable authentication management, multi-layered security controls, and centralized access governance, PAM ensures that only authorized users can access sensitive systems. Moreover, it helps businesses stay compliant with industry security standards by enforcing robust authentication policies. It offers:
- It offers scalable authentication management across multiple applications
- Provides support for multiple authentication technologies (LDAP, MFA, biometrics)
- Additionally, it also offers enhanced security with centralized access control
- Adherence to compliance with security standards by enforcing authentication best practices
With miniOrange's PAM solutions, enterprises can take security a step further—integrating LDAP, MFA, biometrics, and more—to protect privileged accounts without complexity. Strengthen your security posture today with miniOrange.


Leave a Comment