Imagine one of your clients logging into your e-commerce platform or a team member accessing work-related data as usual on your business portal. Everything seems secure—until an attacker intercepts their session and cookies, hijacking access to your systems.
Shocking, right?
Session hijacking via cookie manipulation are stealthy cyberattacks that exploit web applications to steal user data, compromise accounts, and disrupt business operations. According to a Google report, session hijacking attacks happen as often as password-based attacks. For organizations, this can lead to devastating consequences like financial loss, regulatory penalties, and damage to brand reputation.
In this blog, we’ll break down what is session hijacking, how these attacks work, and, most importantly, how to prevent session hijacking to protect your business.
What Is Session and Cookie Hijacking?
Session hijacking and cookie session hijacking are forms of cyberattack wherein a hacker steals or manipulates the session token to gain unauthorized access to your information or services. The hijacking process typically begins when an attacker intercepts your user’s token. Once in possession of this token, attackers can now impersonate them, view sensitive data, or even manipulate privileges to cause greater damage to your business.
According to a Microsoft report, around 147,000 token replay attacks were detected by the company in 2023, a 111% increase year-over-year. In most applications, after successfully executing a session hijacking attack, the attacker gains access to all the user’s data and can perform operations as earlier done by the compromised user.
The Impact of Session Hijacking on Businesses
With a significant portion of the population now relying on the Internet for online banking, shopping, and social interactions, session hijacking in cyber security can be catastrophic. By hijacking a session, attackers can commit digital fraud, steal user identities, and breach confidential interactions online.
The repercussions of session hijacking are far-reaching, affecting both individuals and organizations. For organizations, the consequences of session hijacking include financial loss, damage to customer trust, and legal challenges. An organization may even face regulatory fines and legal challenges. Thus, understanding the nuances of session and cookie hijacking is essential to safeguard your business.
How to Prevent Session Hijacking with CASB Solution?
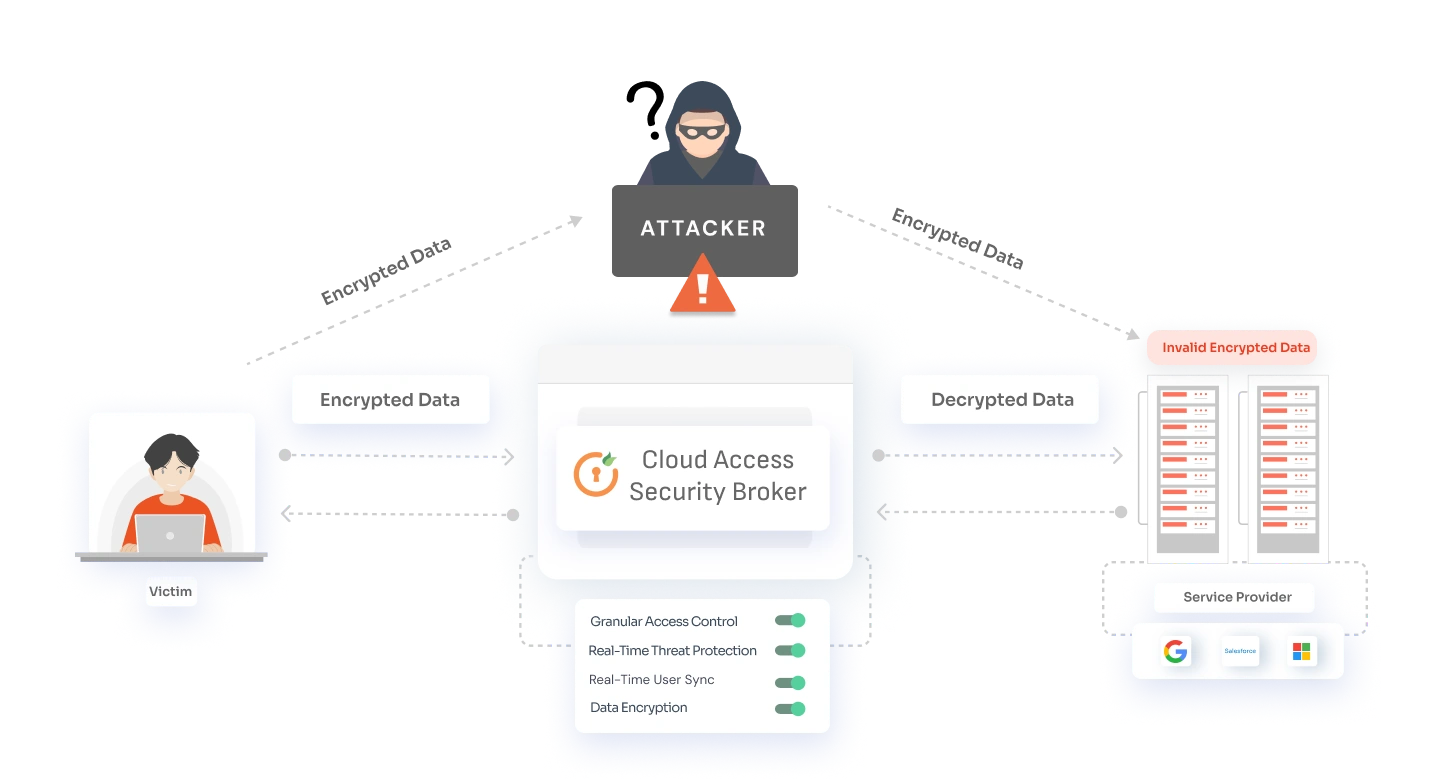
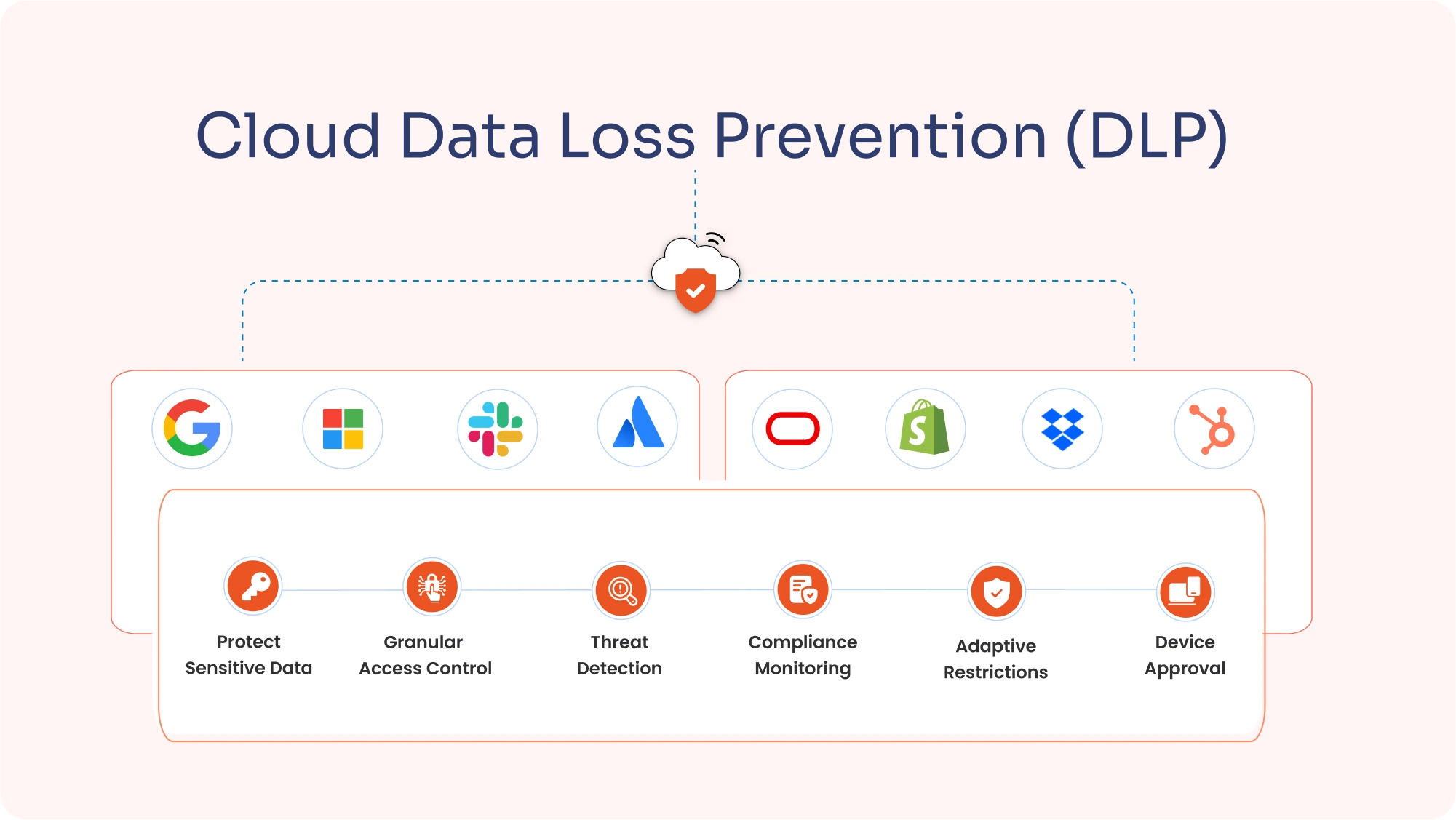
A Cloud Access Security Broker (CASB) provides a centralized platform to enforce security policies, monitor user activity, and mitigate session hijacking risks. Here’s how CASB security helps prevent session hijacking attacks:
1. Real-Time Threat Detection
A CASB solution monitors user activity 24/7 to detect session hijacking attempts in real time. Suspicious behaviors, such as access from unfamiliar locations or multiple failed login attempts, are flagged instantly, helping prevent cookie session hijacking.
2. Data Encryption
CASB enforces end-to-end encryption of your data both during transit and at rest, making it difficult for attackers to manipulate cookies or hijack sessions during transit. This is crucial for preventing session hijacking in cyber security. Whether employees are working from a coffee shop Wi-Fi or your office network, the data remains secure.
3. Granular Access Controls
With CASBs, admins can enforce context-aware policies based on user behavior, location, network type, or even the time of access. For instance:
- Block a login attempt from an unknown country.
- Deny access if the network isn’t secure.
- Trigger multi-factor authentication (MFA) for high-risk scenarios.
These granular controls significantly reduce the chances of a session hijack, making it much harder for attackers to misuse a stolen session or cookie.
4. Visibility into Shadow IT
CASB provides visibility into unsanctioned applications and user activities, ensuring protection from session hijacking via cookie manipulation. It helps admins identify vulnerabilities and enforce compliance.
For the uninitiated, Shadow IT refers to those unsanctioned apps your employees might be using. While these apps might seem harmless, they often leave gaping vulnerabilities. A CASB solution identifies shadow activity, helping you identify risky behavior and enforce compliance before hackers exploit these cracks. According to reports, 80% of employees admit to using unauthorized SaaS apps, making visibility crucial.
5. Encrypted Session Cookies
Session cookies are like the backstage passes to your accounts—they’re gold for hackers. CASB secures session cookies with encryption, rendering them useless even if intercepted. This is a critical measure for cookie session hijacking prevention. Even if they somehow intercept the cookies, encryption ensures that they’re rendered useless.
CASB Security: Securing Workforces from Session Hijacking
Scenario
A mid-sized technology firm with a distributed workforce relies on cloud applications like Microsoft 365, Google Workspace, and Salesforce for day-to-day operations. Employees access these tools through various devices, often from unsecured public networks during business travel.
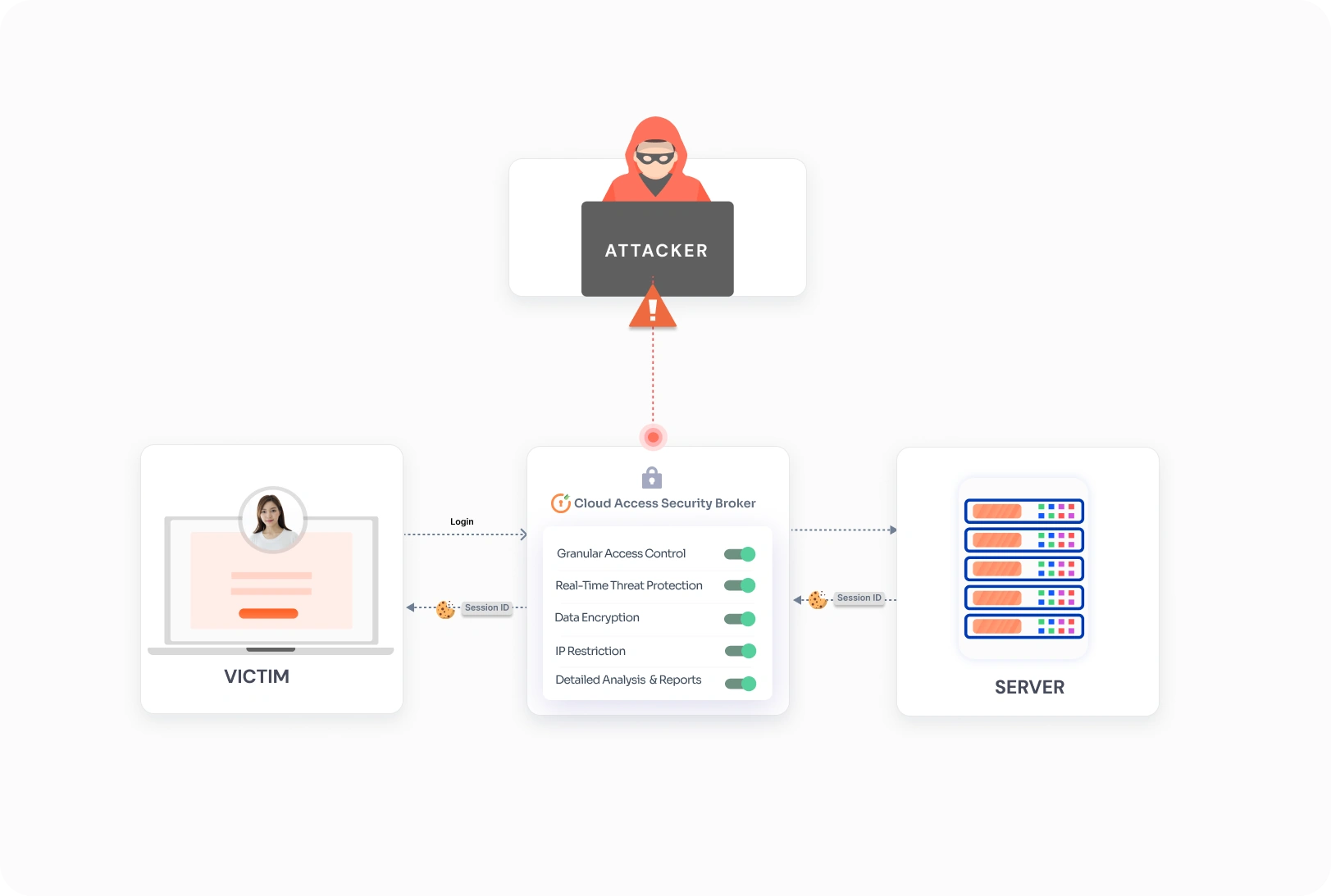
One day, a senior manager faced a severe session hijacking attack where his session on a cloud platform was hijacked, offering the attacker unauthorized access to sensitive customer data, disrupting operations, and damaging client trust.
Problem Statement
The company’s existing security measures were unable to detect such session hijacking attacks due to a lack of real-time session monitoring, behavior-based threat detection, or anomalous activity management.
Attackers exploited the lack of visibility into session behavior and intercepted the employee’s session cookies to gain access to the company’s sensitive data.
CASB Solution
The company deployed a Cloud Access Security Broker (CASB) solution to strengthen its security posture and protect its workforce from session hijacking. Key CASB features implemented included:
- Real-Time Session Monitoring: CASB continuously monitored active user sessions for abnormal behavior, such as access from unusual locations or simultaneous logins from multiple IP addresses.
- Granular Access Control: The CASB enforced granular access policies based on user behavior, network posture, and geolocation, restricting access when anomalies were detected.
- Session Revocation: In case of suspicious activity, the CASB could terminate compromised sessions instantly, preventing further damage.
- Data Loss Prevention (DLP): Additional DLP features ensured sensitive information was not shared or accessed during hijacked sessions.
Outcome
By implementing a CASB, the firm prevented further session hijacking attempts, ensured real-time monitoring, and minimized risks, safeguarding sensitive data and ensuring business continuity. Moreover, automated session termination capabilities enabled the IT team to respond to threats instantly, reducing the attack's impact.
The implementation of CASB security not only safeguarded the firm’s data but also enhanced its overall cybersecurity framework, ensuring business continuity in an increasingly cloud-driven world.
To Sum Up
Session hijacking via cookie manipulation are significant threats to modern online businesses. As a business owner, website admin, or developer, your priority is to protect your users while maintaining seamless access to your services.
With CASB solutions, you can:
- Secure sessions from session hijacking attacks.
- Prevent cookie session hijacking with real-time monitoring and encryption.
- Build trust and comply with regulations.
Don’t wait for a session and cookie hijack attack to happen. Contact us at info@xecurify.com to explore how CASB solutions can fortify your website’s security and protect your users' sessions from hijackers.
Reference links
Author

Leave a Comment