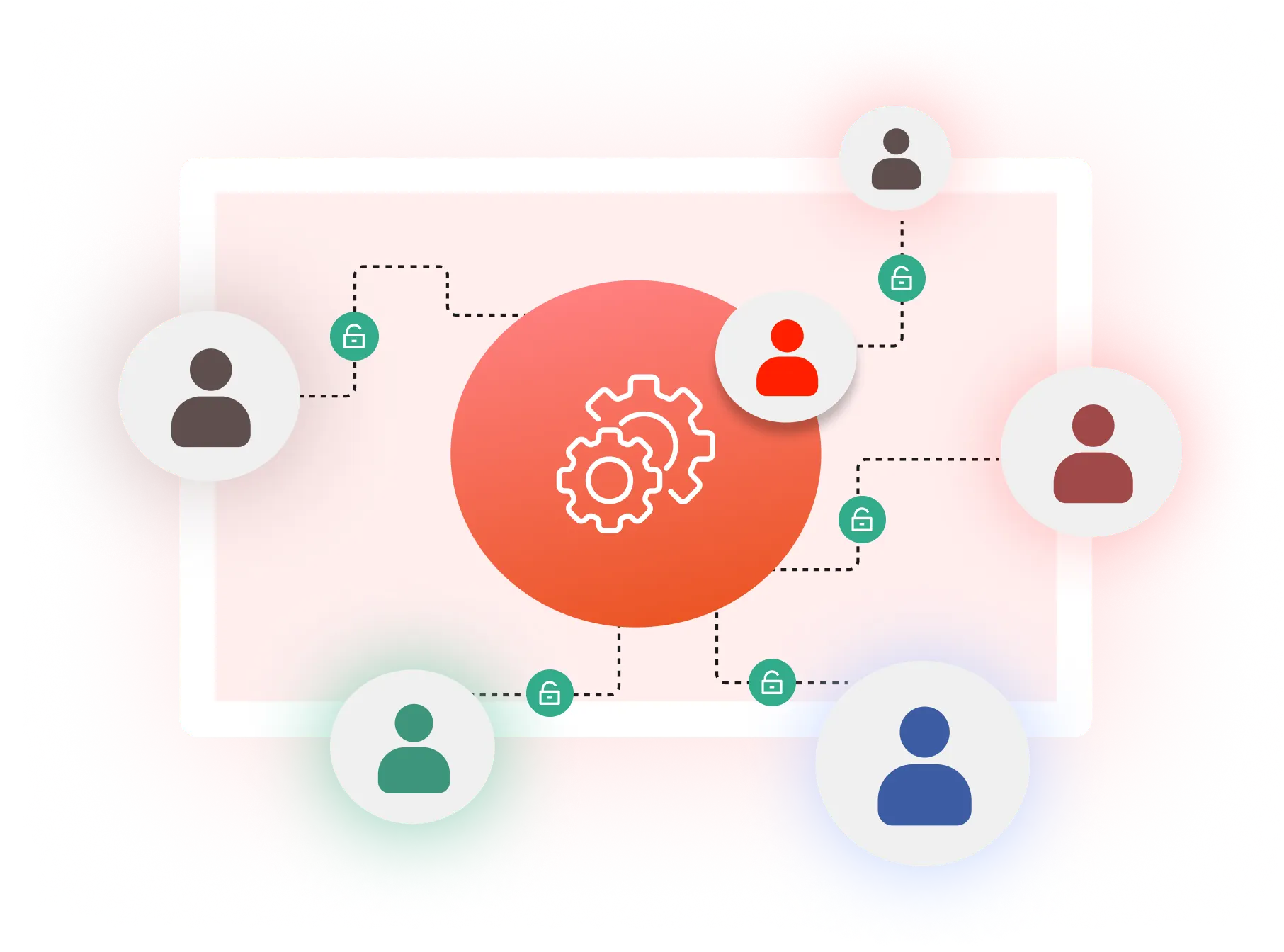
The principle of least privilege enforces strict access controls, allowing users and applications only the essential permissions needed, enhancing security without hindering productivity. Least privilege access control minimizes risks by restricting privileged accounts while maintaining seamless operations without IT help desk intervention.
What is the principle of least privilege (POLP)?
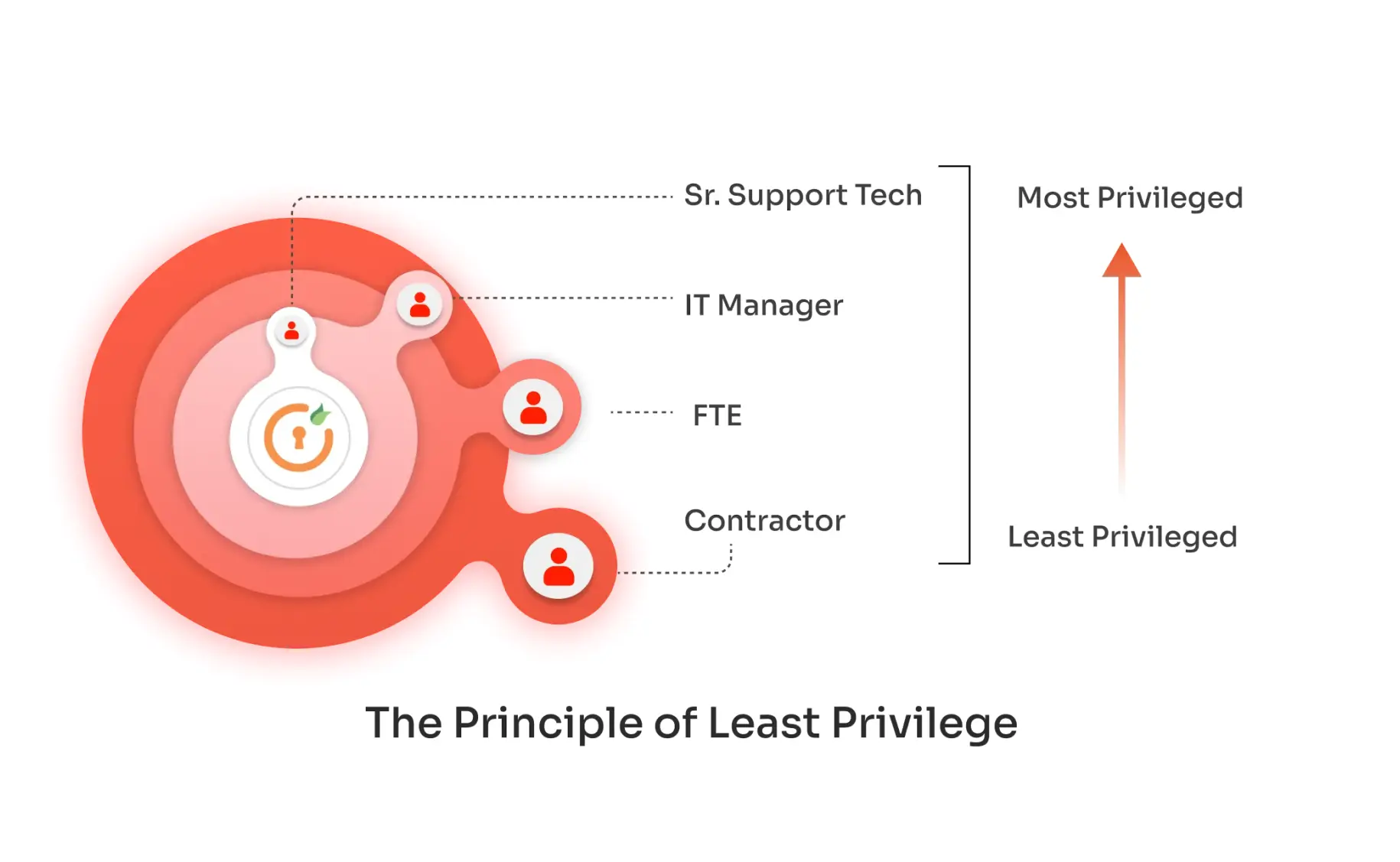
The Principle of Least Privilege (PoLP) is a fundamental concept in least privilege security, where users, processes, or systems are granted only the minimum access rights necessary to perform their tasks. This targeted access not only reduces attack surfaces and minimizes the risk of a least privilege security breach, but it also streamlines access management, leading to cost efficiency by lowering the chances of costly security-related breaches or accidents.
For example, in a corporate setting, an employee in the finance department should only have access to financial data and tools, not to the entire company’s database. This least privilege access control model ensures that even if the user's account is compromised, the potential damage is contained, protecting the broader system. Additionally, by granting only necessary permissions, operational efficiency is increased, as users have clear, role-based access to the tools they need, reducing confusion and minimizing errors.
What is privilege creep?
Privilege creep occurs when users gradually acquire more access rights than necessary for their current tasks, often violating the principle of least privilege. This typically happens when organizations revoke all administrative rights initially but later re-grant privileges to allow users to run essential legacy, homegrown, or commercial off-the-shelf (COTS) applications. Once these elevated privileges are re-granted, they are rarely revoked, leading to an accumulation of excessive access rights.
This excessive access contradicts the least privilege access principle and reopens security vulnerabilities, making organizations more susceptible to threats. To address privilege creep, implementing least privilege access controls is crucial. By adhering to the least privilege access model, organizations can ensure that users maintain only the minimum access necessary, reducing security risks and enhancing overall protection.
What is the principle of least privilege in cybersecurity
The principle of least privilege (PoLP) is a fundamental cybersecurity concept that ensures users, applications, or systems are granted only the minimum level of access necessary to perform their functions. By adhering to this least privilege access principle, organizations can significantly reduce the risk of accidental or intentional misuse of privileges.
Implementing least privilege access control helps to limit access rights, thereby minimizing the potential attack surface and enhancing overall security. A Privileged Access Management (PAM) solution automates and streamlines the enforcement of PoLP, making it easier to manage privileges across diverse systems and ensuring that users maintain only the access they truly need. This approach not only fortifies security but also simplifies the administration of access rights, promoting a more secure and efficient IT environment.
How does the principle of least privilege (PoLP) work?
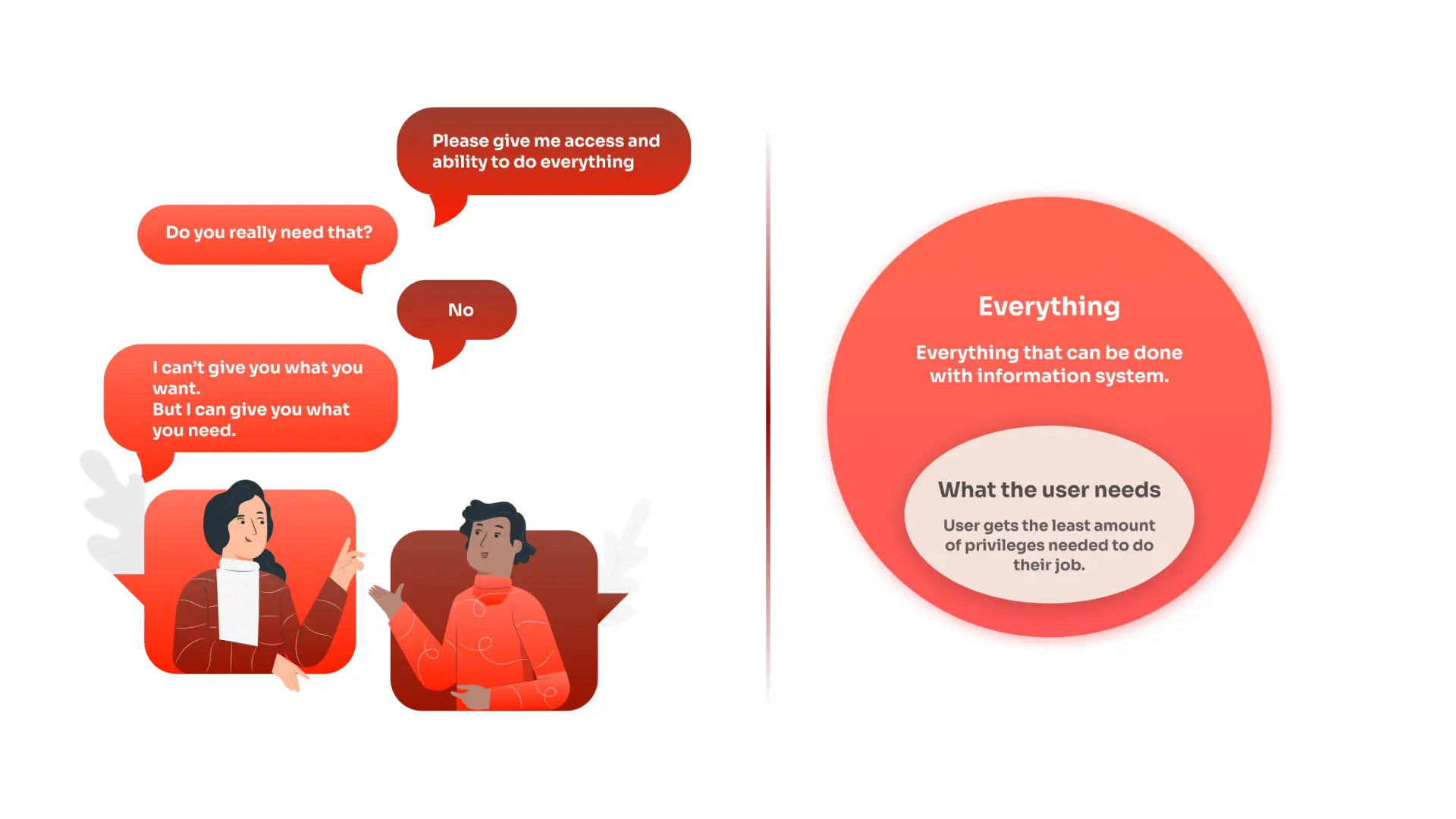
The Principle of Least Privilege (PoLP) functions by granting users, applications, and systems only the minimum level of access necessary to perform their required tasks. This approach minimizes the risk of unauthorized access to critical systems or sensitive data, as it limits the potential attack surface. By containing compromises to their area of origin, PoLP prevents security breaches from spreading throughout the entire system, thereby elevating the overall security posture.
In comparison to PoLP, Zero Trust Network Access (ZTNA) operates on the premise of "never trust, always verify." ZTNA ensures that every access request, whether from a user, device, or application, is continuously verified and authenticated before being granted access to the network or specific resources. This model categorizes users and systems based on trust risks, applying different security controls depending on their classification. For example, employees, contractors, and suppliers might each have different access policies based on their associated risk levels.
PoLP vs. Zero Trust Security: What's the Difference?
While both PoLP and Zero Trust aim to enhance security by limiting access, their approaches differ. PoLP focuses on minimizing access to essential permissions, reducing the risk of unauthorized actions within an organization. Zero Trust, on the other hand, goes a step further by continuously validating every access request, regardless of the user's previous trust level.
These models are not mutually exclusive; in fact, integrating least privilege access control within a Zero Trust architecture can provide a comprehensive security framework. By combining PoLP's emphasis on minimal access with Zero Trust's ongoing verification process, organizations can significantly enhance their defenses against potential threats.
The PoLP limits the number of "keys" (access permissions) distributed within an organization. Zero Trust ensures that every time a key is used, it is thoroughly checked and verified.
Why Is the Principle of Least Privilege Important?
The Principle of Least Privilege (PoLP) is a fundamental cybersecurity concept that restricts users, applications, and systems to the minimum level of access necessary to perform their tasks. This approach offers several benefits that enhance organizational security, stability, and compliance.
Benefits of the Principle of Least Privilege
1. Better Security: A notable example is the case of Edward Snowden, who leaked millions of NSA files due to his admin privileges, which far exceeded his actual job requirements. After the incident, the NSA implemented the principle of least privilege, revoking elevated access rights from 90% of its employees, significantly reducing the risk of insider threats.
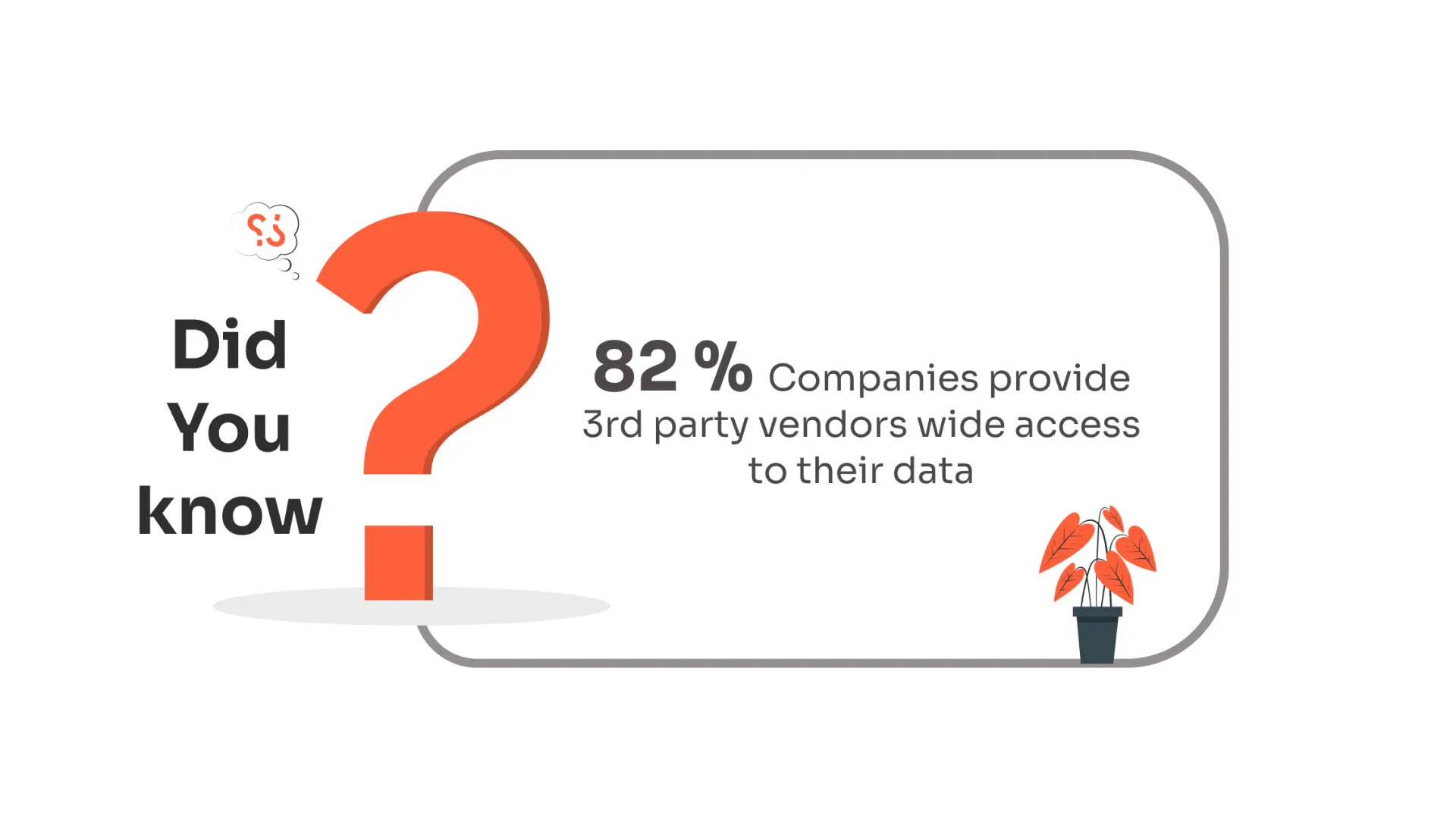
2. Minimized Attack Surface: The 2013 Target data breach, where hackers accessed 70 million customer accounts, serves as another case study. The breach occurred through an HVAC contractor who had excessive permissions. By not adhering to PoLP, Target inadvertently created a broad attack surface, which the attackers exploited. Had PoLP been implemented, the access given to the contractor would have been limited, potentially preventing the breach.
3. Limited Malware Propagation: Implementing PoLP helps contain malware within the specific area where it first infects a system. By restricting user and system privileges, malware finds it more challenging to propagate throughout the network, thereby minimizing the overall impact of an attack.
4. Better Stability: Beyond security, PoLP contributes to system stability by ensuring that any changes or updates are confined to specific zones, limiting the potential for widespread disruption.
5. Improved Audit Readiness: Systems built on the principle of least privilege are easier to audit, as the scope of the audit is naturally reduced. Moreover, many regulations and compliance standards require PoLP implementation, making it a critical factor in maintaining compliance.
Lessons Learned
Organizations like the NSA and Target have shown that failure to implement PoLP can lead to catastrophic security breaches. However, these same organizations have also demonstrated the effectiveness of PoLP when properly applied. The NSA’s drastic reduction in elevated privileges post-Snowden is a testament to the importance of aligning access levels with actual job requirements. Target’s experience underscores the necessity of regularly reviewing and limiting third-party access to essential systems.
How to Implement PoLP in your organization
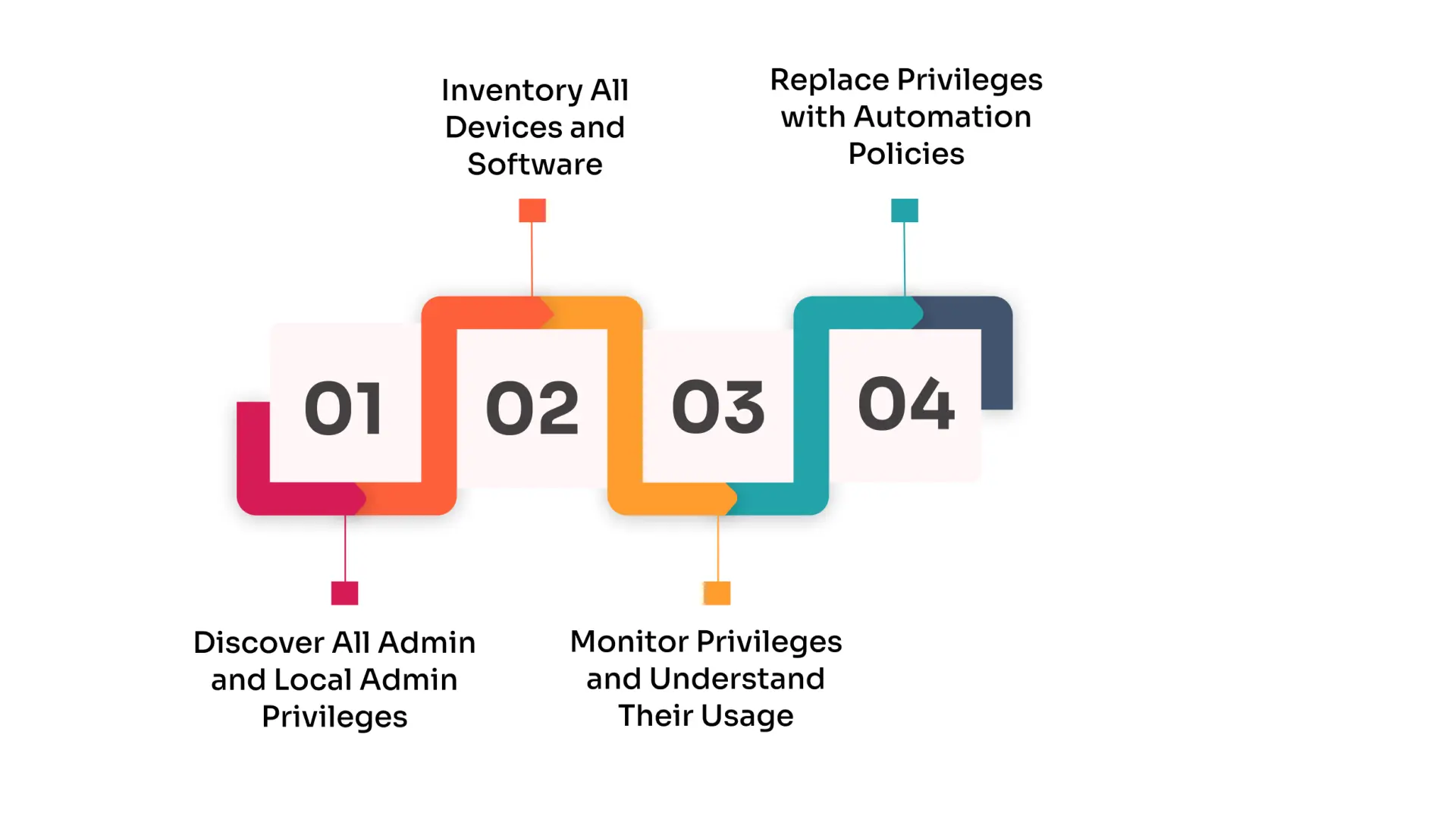
Implementing the principle of least privilege (PoLP) in your organization involves a strategic approach to minimize access rights and enhance security. Here's how to effectively implement least privilege:
1. Discover All Admin and Local Admin Privileges: Begin by automatically discovering all admin and local admin privileges within your environment. Understanding which employees, devices, and services have privileged accounts is crucial to ensuring compliance with the principle of least privilege in information security. This step also helps identify gaps where the least privilege management needs to be tightened to prevent a privilege security breach.
2. Inventory All Devices and Software: Conduct a thorough inventory of all devices and software across your organization. This helps you understand how software is deployed, identify potential risks, and ensure compliance with the least privilege security principle. By knowing where software originates, you can better manage trusted vendors and restrict unauthorized installations, aligning with the least privilege access principle.
3. Monitor Privileges and Understand Their Usage: Before enforcing the concept of least privilege, monitor current privileges to see how they are used. Identify which employees actively require elevated access and who may be over-privileged. This understanding allows you to enforce the least privilege by replacing unnecessary administrative rights with policies that align with the least privilege access control model, ensuring that users maintain only the least permissions needed to perform their jobs.
4. Replace Privileges with Automation Policies: After auditing your environment, begin reducing privileges for users who no longer require them. For users who still need elevated access, implement automation policies that allow tasks to be elevated on-demand. This approach supports the least privilege concept by ensuring that users have the minimum necessary access without becoming over-privileged. By integrating least-privilege access with Privileged Access Management (PAM) and Application Control, you can effectively manage and secure access across devices, services, and applications, reducing the risk of a least-privilege security breach.
Best Practices and Recommendations
Implementing the principle of least privilege (PoLP) effectively requires a strategic approach to managing and minimizing access rights within an organization. Here are some best practices to ensure robust least privilege access across your systems:
1. Conduct a Privilege Audit: Start by auditing all existing accounts, processes, and programs to ensure they only have the permissions necessary for their specific roles. This audit should encompass user accounts, SSH keys, system groups, and hardcoded passwords.
2. Set Default Access to Minimum: For all new accounts, start with the minimum necessary privileges. Only grant higher-level access as needed for specific tasks, rather than providing default administrative rights.
3. Enforce Separation of Privileges: Differentiate between standard and administrative accounts. Ensure that high-level system functions are kept separate from lower-level operations. This segregation helps reduce the risk of security breaches by limiting access.
4. Use Just-in-Time (JIT) Privileges: Implement just-in-time privileges to grant elevated access only when needed and for a limited time. This approach minimizes the risk of privilege misuse by eliminating always-on or standing privileges.
5. Make Individual Actions Traceable: Implement monitoring, auditing, and user ID systems to ensure all actions can be traced back to individual users. This increases accountability and allows for better oversight of privileged activities.
6. Regularly Audit Privileges: Regularly review and update privileges to prevent the accumulation of unnecessary access rights. This ensures that users, accounts, and processes maintain only the permissions they need.
7. Remove Admin Rights on Endpoints: By default, assign standard user privileges to all employees. Elevate access only when necessary for specific tasks or applications, and consider removing admin rights entirely from sensitive servers to reduce the attack surface.
8. Segment Systems and Networks: Divide your systems and networks into segments based on different levels of trust, needs, and privilege sets. This segmentation limits the potential spread of a breach and enhances security.
9. Implement One-Time-Use Credentials: Use password safes to generate one-time passwords for privileged accounts, which are checked out for specific tasks and retired immediately afterward. This reduces the risk of compromised credentials being reused.
10. Replace Hardcoded Credentials: Replace static, hardcoded credentials with APIs that retrieve dynamic secrets from secure password safes, especially in DevOps and CI/CD environments.
11. Extend Least Privilege Beyond the Perimeter: Apply least privilege access controls not just internally, but also to vendors, contractors, and remote access sessions, ensuring that external users also adhere to strict access limitations.
12. Analyze and Report on Privileged Access: Continuously monitor and report on all privileged accounts, including shared admin accounts, service accounts, and cloud accounts. Auditing should capture detailed activities, such as keystrokes and screen actions, to maintain thorough oversight.
Conclusion
Implementing the principle of least privilege (PoLP) is essential for enhancing your organization's security posture. By restricting access to only what is necessary for each user, application, or system, you can significantly reduce the risk of unauthorized access, privilege misuse, and security breaches. miniOrange's Privileged Access Management (PAM) solutions automate and streamline the enforcement of PoLP, making it easier to manage and secure privileges across diverse systems. This not only fortifies your defenses but also ensures compliance with industry standards and improves overall operational efficiency. Adopting PoLP with miniOrange PAM will help your organization achieve a robust, secure, and well-managed IT environment.
Author

Leave a Comment