Privileged Access Management (PAM) is your organization's security control center for managing and monitoring high-level access to critical systems. Think of it as a sophisticated vault system that safeguards your most powerful administrative credentials while maintaining detailed audit trails of their usage.
As we head into 2026, PAM has become crucial. Here's why:
Cyberattacks are getting scarier and more complicated. As per a recent report, in 2025 alone, 53% of breaches involved the use of stolen credentials. With a single stolen login, especially a privileged one, it becomes an open doorway for attackers to access your most sensitive systems.
But here's what makes PAM a game-changer:
- It automatically rotates privileged passwords, so even if credentials leak, they're already invalid
- Provides just-in-time access, meaning no standing privileges hanging around as security risks
- Records every privileged session, so you know exactly who did what and when
- Integrates with zero-trust frameworks—essential for today's hybrid cloud environments
The best part? Organizations using mature PAM solutions report 48% fewer security incidents and save an average of $3.3M in breach-related costs annually. In today's threat landscape, that's not just strong security—it's smart business.
Let us look into some of the top-notch privilege security use cases of PAM.
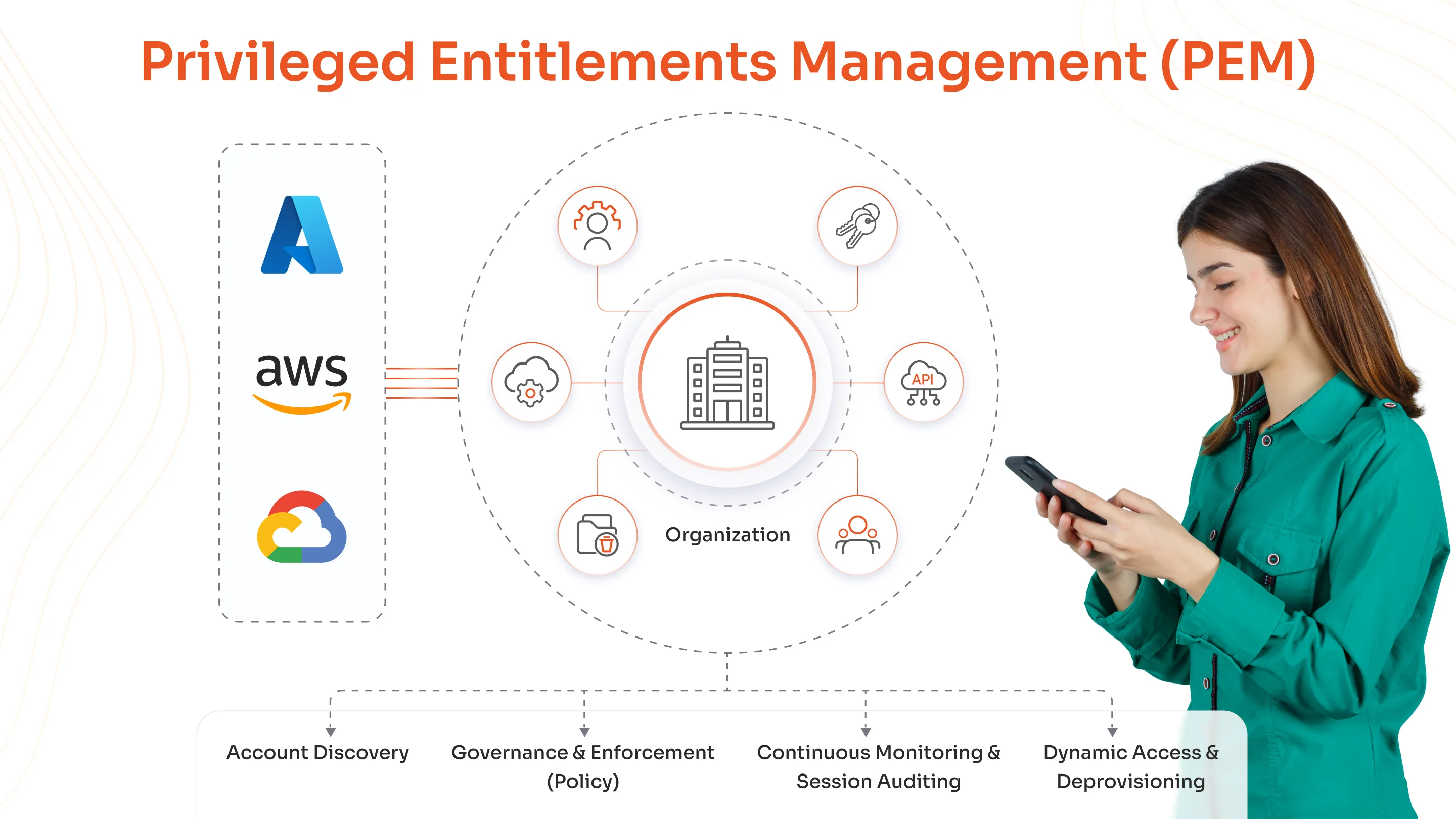
1. Securing Privileged Accounts & Credentials
Unmanaged privileged accounts can pose serious security risks because they often have too many permissions and not enough oversight. Hackers can exploit these accounts to access sensitive data. Many organizations discover they have more privileged accounts than they thought, which increases their vulnerability.
Privileged Access Management (PAM) solutions help automate these accounts' management. PAM creates strong passwords, stores them securely, and changes them regularly to minimize the risk of breaches. It also enforces strict access controls, ensuring users only have the permissions they need for their roles. Using PAM boosts security, reduces administrative work, and promotes accountability within the organization.
One bad PAM purchase can cost more than a breach. Download our comprehensive buyer’s guide to gain a clear understanding before making a commitment.
Get the Free PAM Buyer’s Guide
2. Applying the Principle of Least Privilege
PoLP makes sure people only have the access they need to do their jobs, which helps prevent unauthorized access and data breaches. By limiting access rights, companies can cut down on threats from both inside and outside. With cyber threats on the rise in 2026, following PoLP protects sensitive data and keeps up with regulations.
Cybersecurity is constantly changing, and using the principle of least privilege (PoLP) is key. Remote work and cloud services have increased vulnerabilities. Many breaches happen due to compromised privileged accounts, so strict access controls are essential. By enforcing the least privilege, the attack surface is reduced, malware spread is limited, and only authorized personnel can access sensitive information.
PAM plays a crucial role in enforcing least privilege. It helps monitor and manage user privileges to make sure they align with job needs. Regular audits and automated workflows in PAM can spot and correct overprivileged accounts. This approach boosts security, ensures regulatory compliance, and keeps detailed logs of access activities. Combining PAM with PoLP safeguards critical assets and minimizes risks from excessive user privileges.
3. Secure Remote Access for Hybrid Workforces
Remote work brings major security risks from hackers potentially gaining broad network access through compromised home devices or unsecured connections. When employees log in from various locations and personal devices, it becomes harder to spot unusual activity, making it easier for attackers to move undetected through company systems and access sensitive data.
Check out how miniOrange Privileged Remote Access & Management works
To protect against these threats, modern privileged access management (PAM) tools offer two key safeguards: they record every action taken during remote sessions for audit trails, and they require multiple verification steps (like combining passwords with fingerprints or security tokens) before granting access to critical systems. This approach helps verify that only the right people can access sensitive resources while maintaining detailed records of all activity.
4. Auditing and Ensuring Compliance
PAM systems automatically track and document all privileged access activities, generating detailed audit trails required by regulations like SOX, GDPR, and CCPA. These systems enforce access policies, manage user permissions, and provide evidence of who accessed sensitive data, when they accessed it, and what actions they took. This automated documentation significantly reduces compliance costs and audit preparation time.
Session monitoring in PAM solutions records privileged user activities in real-time, including keystrokes, commands, and system changes. Security teams can watch active sessions, receive alerts about suspicious behavior, and maintain complete video-like recordings of all privileged access. This level of monitoring helps organizations quickly detect potential security incidents and provides concrete evidence for auditors and investigators when needed.
5. Managing Third-Party Vendor Access
Giving vendors unrestricted access to company systems creates significant risks, as they could accidentally or intentionally access confidential data beyond their job needs. Without proper limits, vendors might view sensitive financial records, customer data, or intellectual property they don't need for their work, increasing the chance of data breaches.
To minimize these risks, companies should grant vendors access only when needed and limit it to specific systems required for their tasks. This means setting up automatic access expiration after job completion and creating detailed permission levels—for example, allowing a software vendor to update only their assigned applications rather than having broad system access. This controlled approach protects company assets while still letting vendors do their work efficiently.
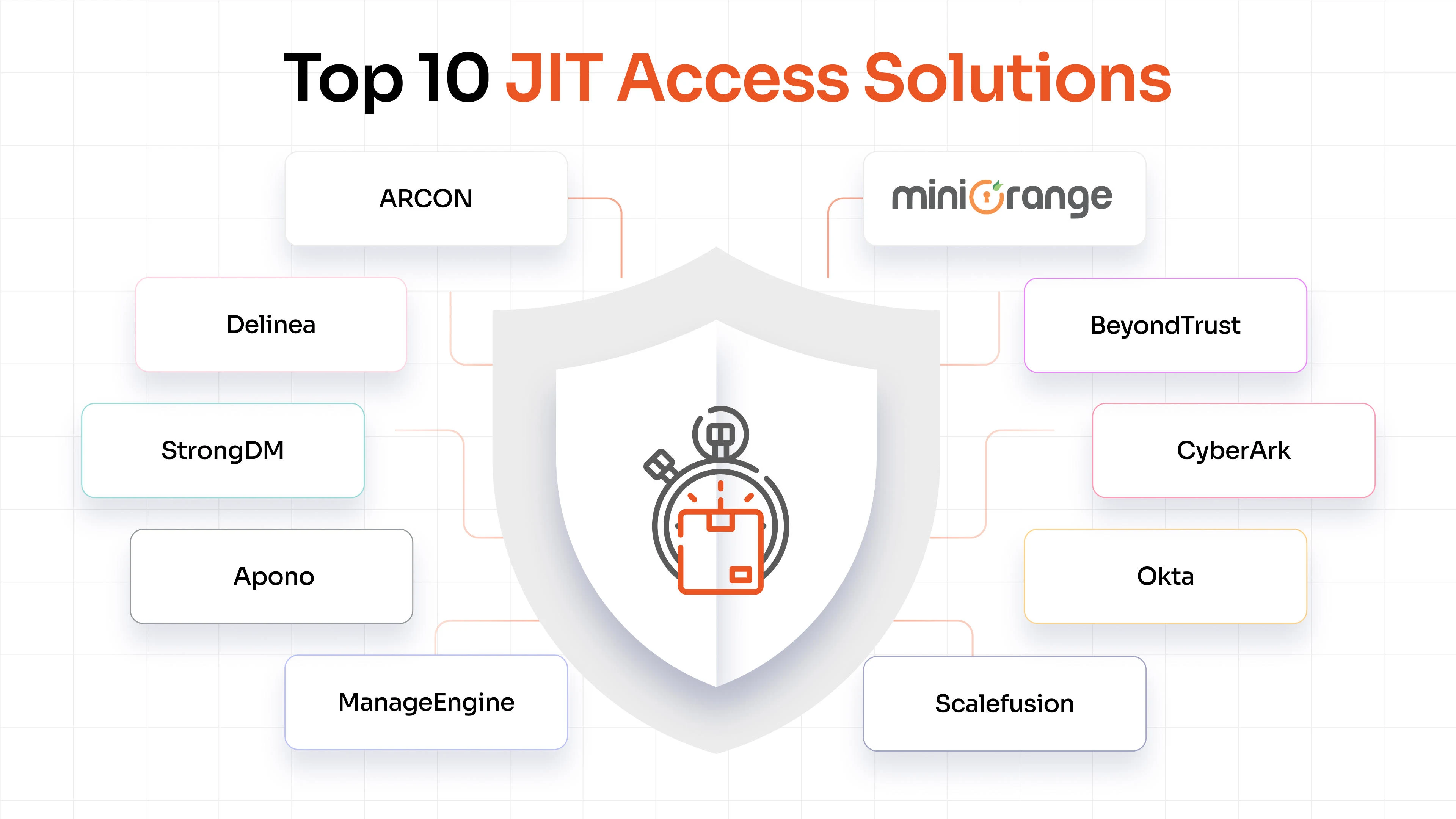
6. Enforcing Just-in-Time (JIT) Privileged Access
In organizations, users often require elevated access to perform certain tasks, but due to oversight, these privileges sometimes remain active even after the task is completed. Most breaches and insider threats occur because of these standing privileges that stay active longer than necessary.
Modern PAM solutions like miniOrange offer JIT access capabilities, which address this by granting temporary, time-bound access only when required. All user activity during this access period is monitored and recorded, and if any suspicious behavior is detected, the session is automatically terminated. Once the task is completed, the time-bound privileges are revoked without any manual intervention.
7. Protecting Cloud and Multi-Cloud Environments
Managing multiple cloud platforms creates unique security challenges since each has different security settings, access controls, and APIs. Companies often struggle to maintain consistent security policies across platforms, making it easier for attackers to exploit gaps or misconfigurations in their cloud infrastructure.
PAM solutions help by providing a single control point to manage access across AWS, Azure, and GCP. They automatically enforce consistent security policies, like requiring approval for high-risk actions or limiting which cloud resources each admin can access. For example, a developer might get temporary access to specific AWS services for a project while being blocked from sensitive Azure databases or GCP storage buckets they don't need to use.
8. Securing Kubernetes & Containerized Environments
Kubernetes and container security are critical as more companies move their applications to cloud-native environments. The main risks include container escape attacks, unauthorized access to cluster resources, and vulnerabilities in container images. Organizations need proper network policies, role-based access controls, and regular security scans to protect their containerized infrastructure and prevent data breaches.
Privileged Access Management (PAM) helps secure container registries by controlling who can access, modify, and deploy container images. It creates an audit trail of all registry activities, automatically rotates credentials, and can detect unusual access patterns that might indicate a security threat. Major cloud providers like AWS, Azure, and Google Cloud have built-in PAM features that integrate with their container services, making it easier for companies to implement strong security controls.
9. Strengthening DevOps Environments
DevOps teams frequently hardcode passwords, API keys, and other credentials directly into their code or CI/CD pipeline configurations, creating major security risks. When these secrets get pushed to code repositories or stored in build logs, attackers can steal them to access critical systems. Even if repositories are private, former employees or contractors may retain access to these credentials long after they should have been revoked.
PAM tools like miniOrange Vault, HashiCorp Vault, AWS Secrets Manager, and Azure Key Vault are among the reputable PAM solutions that help secure DevOps workflows by safely storing and managing secrets. These tools automatically rotate credentials, provide temporary access tokens, and log all secret access. Instead of hardcoding secrets, applications request them through secure APIs with proper authentication. This approach lets DevOps teams maintain rapid deployment cycles while significantly reducing the risk of credential exposure or misuse.
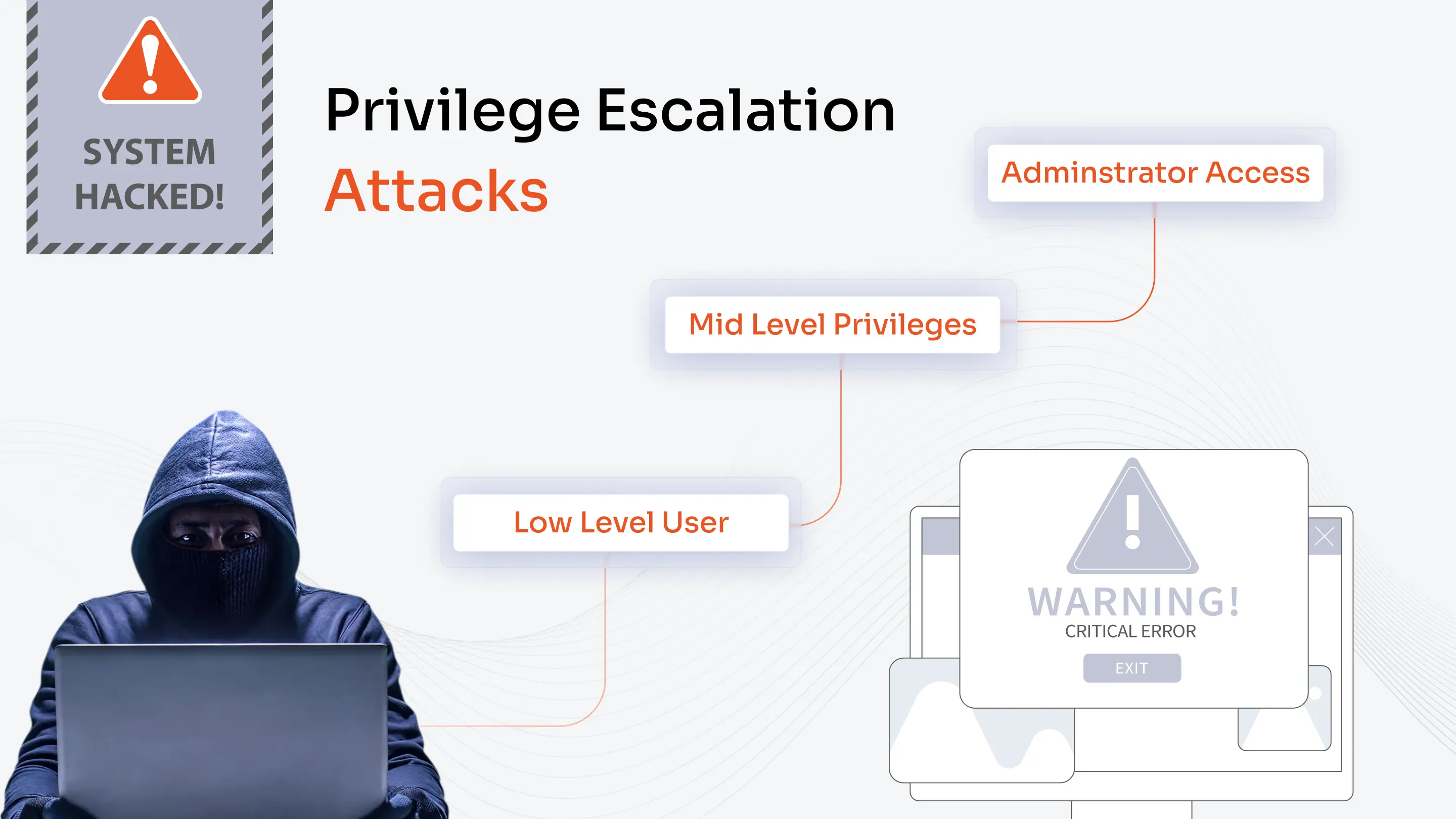
10. Detecting Privilege Escalation & Threat Monitoring
PAM systems use AI and behavioral analytics to spot unusual privileged account activities like off-hours logins, accessing sensitive data, or running unexpected commands. These capabilities help organizations prevent privilege escalation by flagging anomalies, alerting security teams, and automatically suspending suspicious sessions before damage occurs. This proactive monitoring helps catch both malicious insiders and compromised credentials.
PAM can detect major data thefts, like the one at a major financial institution, where an IT administrator was discovered downloading customer records at 2 AM using their privileged access. Their PAM system detected this unusual behavior pattern, alerted security, and automatically blocked further downloads. Investigation revealed the admin was collecting data before joining a competitor.
The PAM system's quick detection prevented a significant data breach, and the company avoided potential regulatory fines and reputation damage.
11. Automating Privileged Access Governance
Manual privileged access management becomes unsustainable as organizations grow, leading to access delays and security gaps. Modern PAM platforms automate access workflows, credential rotation, and compliance reporting—reducing manual effort by up to 80% while improving security. This automation handles routine access requests instantly while escalating unusual cases for review.
AI-powered PAM systems analyze historical access patterns, user behavior, and risk scores to make real-time access decisions. The system can automatically approve low-risk requests (like a developer accessing their usual code repository) while denying or flagging suspicious ones (like accessing sensitive data from an unusual location). Machine learning models continuously improve by learning from past decisions and security incidents.
12. Integrating Privileged Access Management with ITSM Tools
Integrating PAM with IT Service Management (ITSM) platforms like ServiceNow, Jira Service Management, or Freshservice helps organizations enforce strict access controls while maintaining streamlined workflows.
When privileged access is tied to ITSM processes, every access request, approval, and session is automatically tracked through existing ticketing systems. This ensures privileged access is granted only through approved, documented change or incident tickets, and also helps create audit-ready records for compliance and governance.
PAM tools integrate with ITSM APIs to validate ticket numbers, automate approvals, generate session logs, and revoke access when a ticket closes. This aligns security with operational efficiency and reduces manual oversight.
Getting Started with PAM for Your Business
Starting with a solid PAM solution is easier than you might think. With security becoming more critical, miniOrange PAM solutions offer a comprehensive way to manage and monitor user privileges. Our solutions fit your business needs, integrate seamlessly with your existing systems, and boost both security and compliance.
By choosing miniOrange, you're not just getting a tool—you're getting a partner dedicated to protecting your critical assets. Our PAM solutions help you reduce your attack surface, limit malware spread, and make sure only authorized personnel access sensitive information. With regular audits and automated workflows, we keep you ahead of potential threats, ensuring smooth and secure business operations.
Don't wait for a security breach to show you the importance of access controls. Get started with miniOrange PAM solutions today and strengthen your defenses against the rising cyber threats. Join the growing number of businesses that trust us to protect what matters most. Request a trial for miniOrange PAM today!



Leave a Comment