IAM

IAM
Two-Factor Authentication – 2FA Security
Oct 21, 2022

Concept
Log in to Adobe Captivate Prime with SSO
Dec 23, 2023

IAM
Organizations are moving to modern authentication, and why should you too?
Jan 27, 2022
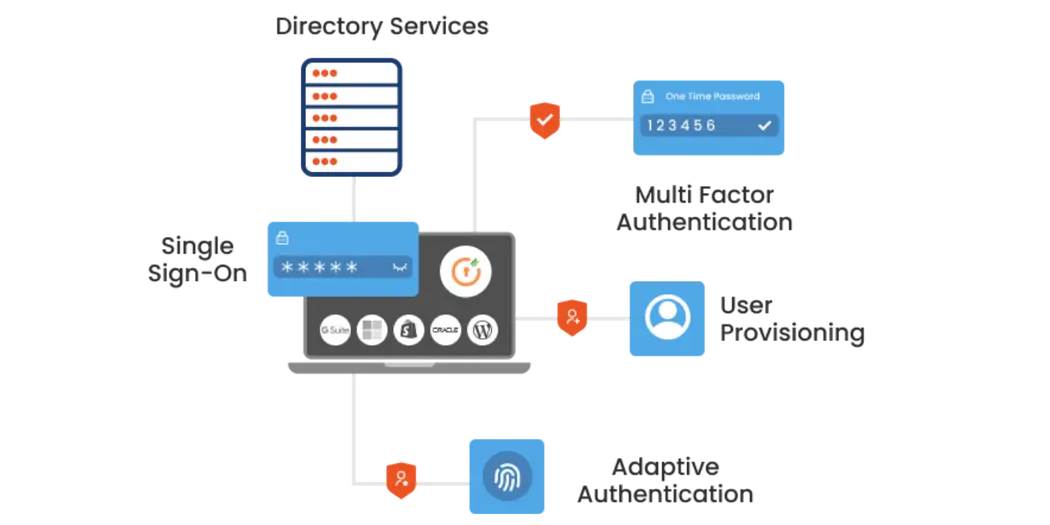
IAM
5 Best IAM Tools for Better Identity Security in 2025
Dec 30, 2022

IAM
The Importance of Centralized Identity Management
Oct 22, 2024

IAM
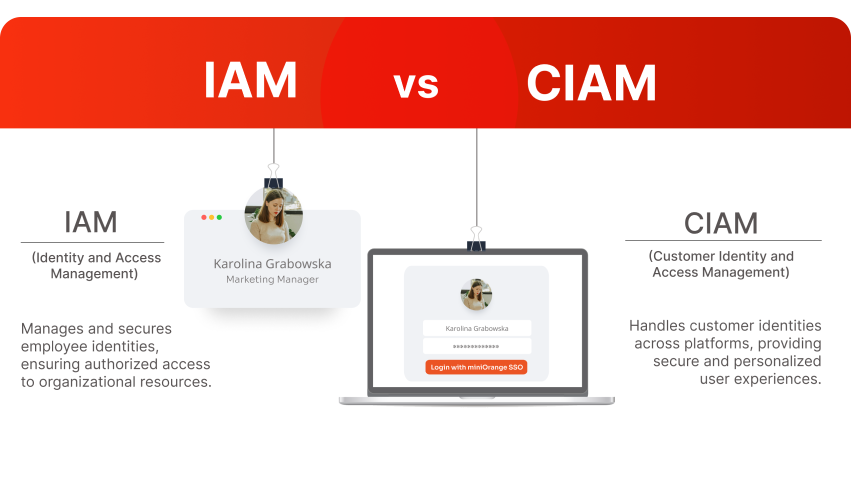
IAM vs. CIAM - What’s the difference?
Jan 8, 2024
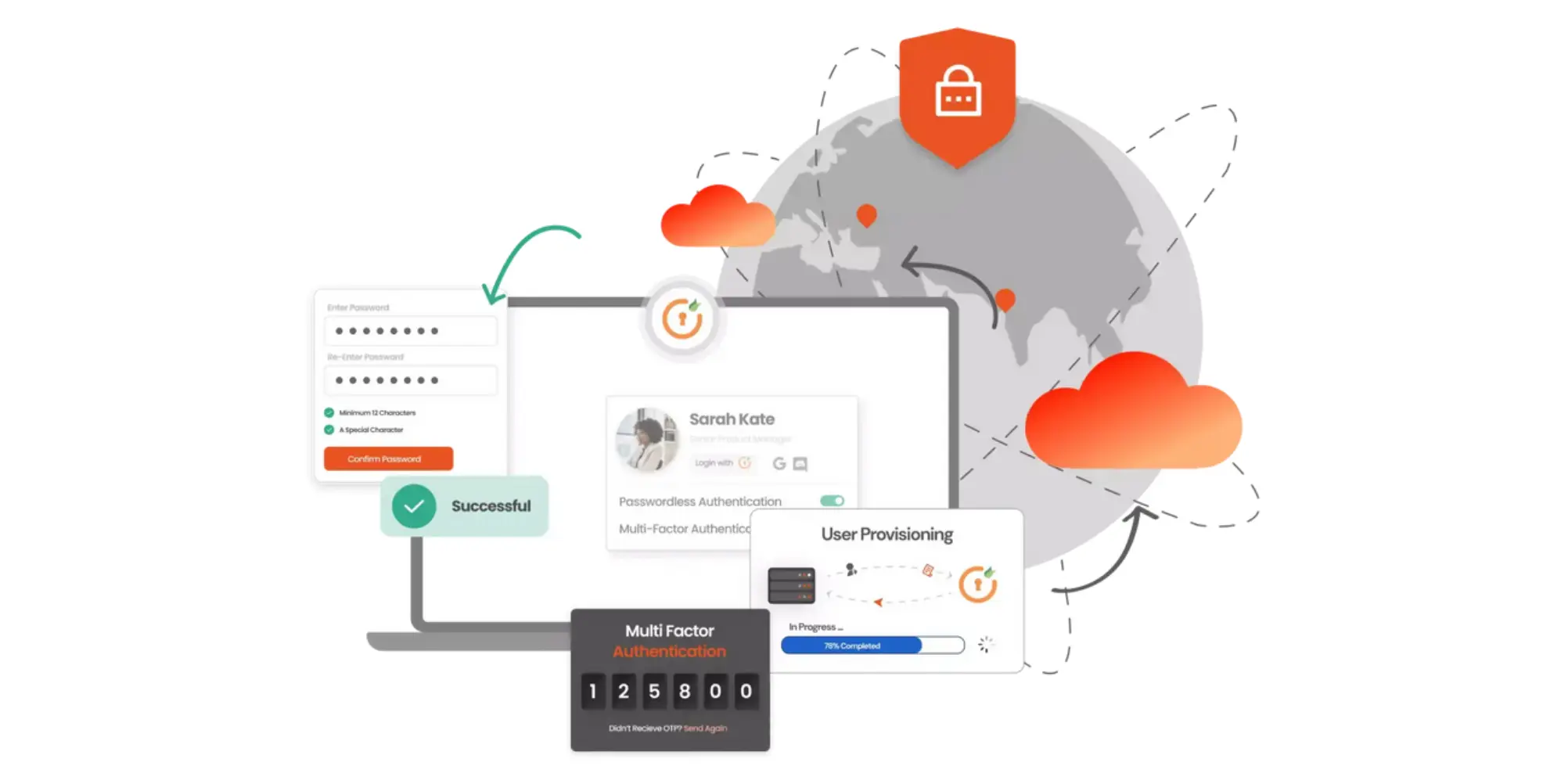
IAM
The Ultimate Guide to Cloud-Based Access Control
Feb 11, 2025

IAM
Do you have an IAM setup? Cybersecurity Awareness Month, Focuses on how and where IAM is used
Dec 26, 2022

IAM
What is Federated Identity Management (FIM) and best practices?
Feb 3, 2023
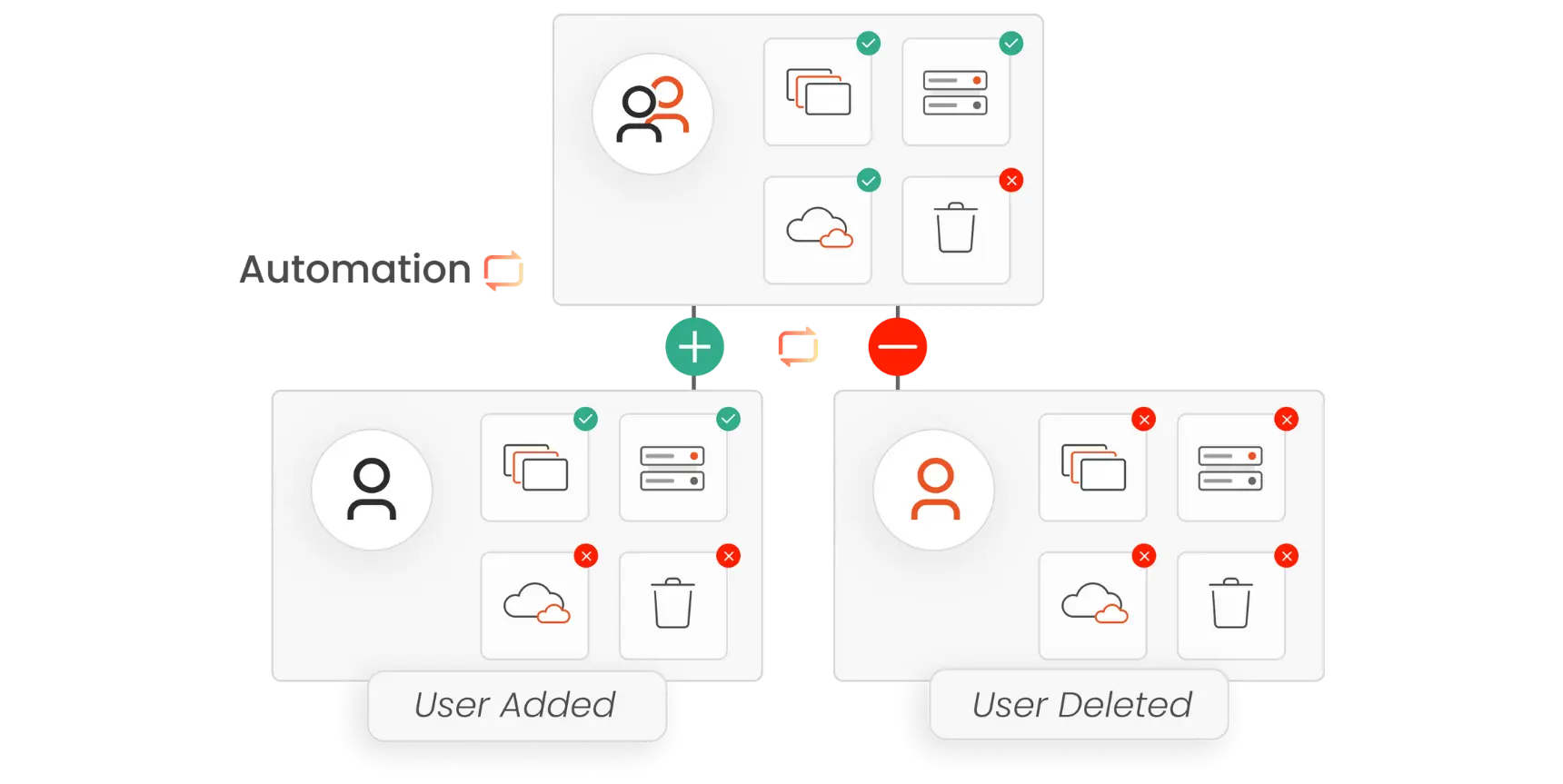
IAM
What is IAM Automation for Better Identity Management?
Jan 2, 2025
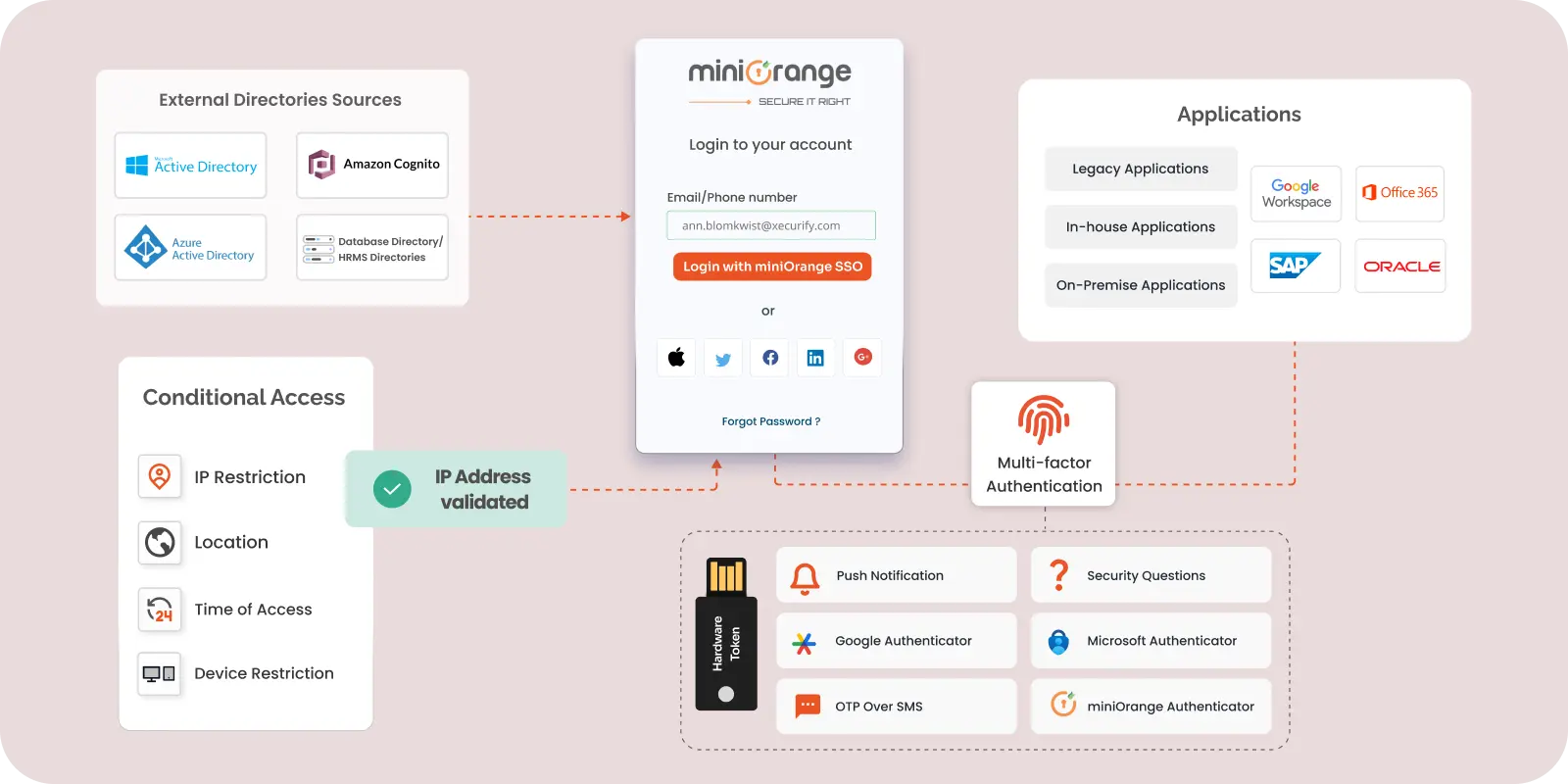
IAM
9 Essential Features for Identity and Access Management (IAM) Solution
Jan 1, 2025

iam
IAM vs. PAM: What’s the difference?
Sep 25, 2023

IAM
IDAM for Banking and Finance Sector to ensure regulatory compliance
Mar 17, 2023

iam
Identity and Access Management (IAM) Market After Economic Turndown
May 12, 2022
atlassian
Integration of Two Factor Authentication (2FA) with INFOSYSTA Mobile Apps
Sep 28, 2021

IAM
IAM Framework: 5 Key Components
Oct 23, 2024

concepts
Multi-Factor Authentication (MFA) Checklist- Enhancing Your Digital Security
Jan 8, 2024

IAM
Migrating from Microsoft Azure Multi-Factor Authentication (MFA) Server
Oct 21, 2022

IAM
How does miniOrange help organizations to comply with NYDFS Cyber Security Guidelines?
Dec 20, 2022

concepts
Cloud Hybrid & On-Premise Deployment Options for miniOrange’s Oracle EBS SSO & MFA Solution
Jul 5, 2022

solutions
Password-Based Authentication and Best Practices
Feb 5, 2023
IAM
How to Secure Multiple Passwords with Password Manager and SSO?
Aug 12, 2024

concepts
Passwordless MFA and Secure Login Solutions
Jan 8, 2024

IAM
RADIUS Vs. TACACS+: What to Choose For Enterprise Networks?
Oct 4, 2023

IAM
Regulatory Compliance and IT Security in Companies: Understanding Article 89 of the Securities Law 2019
Jun 19, 2024
IAM
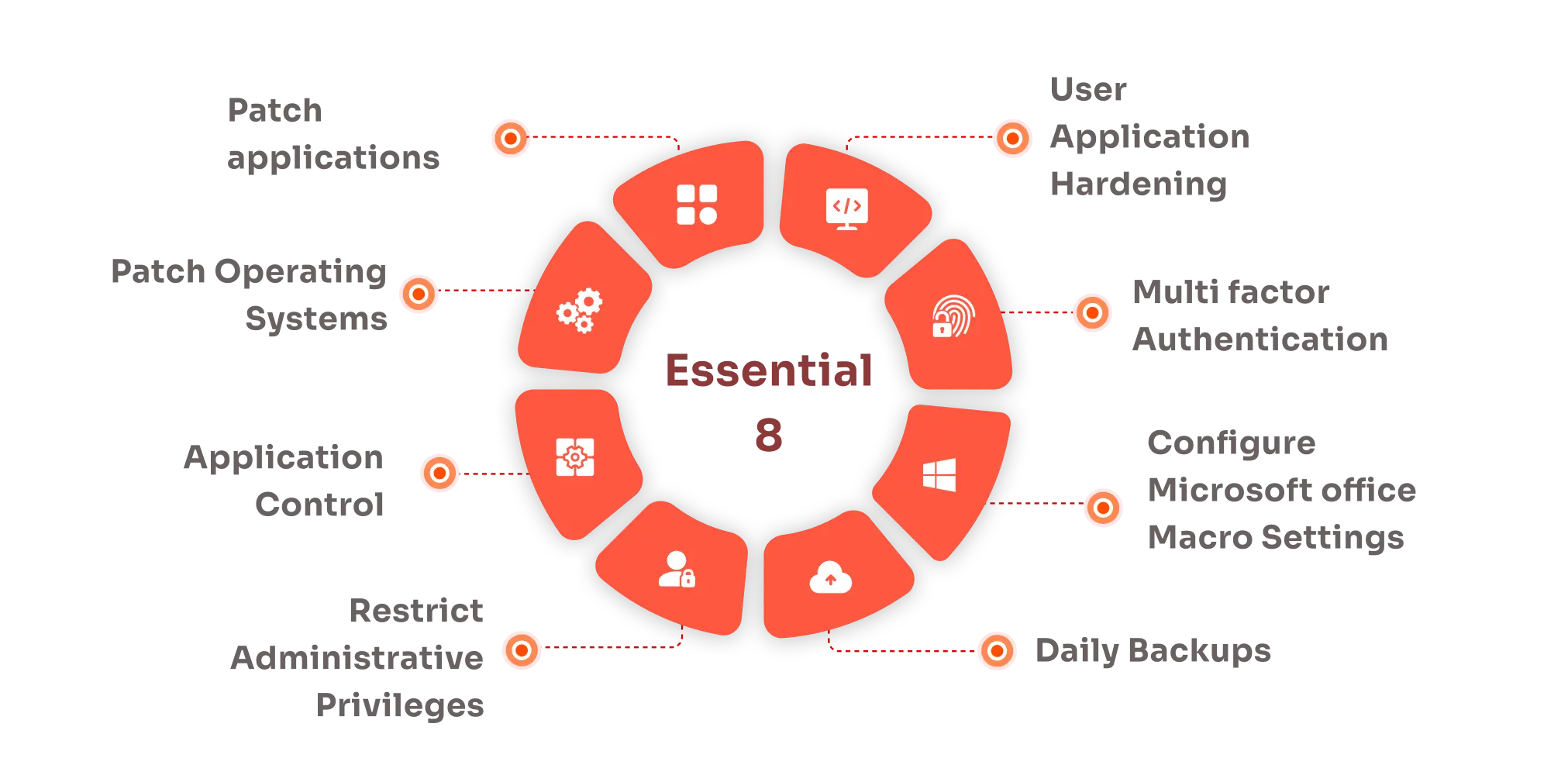
Restrict Administrative Privileges For ACSC Essential Eight Maturity Model
Jul 3, 2024

IAM
10 Fantastic SSO Platforms for the Best Enterprise Security
Feb 17, 2025

IAM
Thinkific Single Sign-On (SSO): Secure Best Online Course Platform
Oct 21, 2022

IAM
VPN Security: How 2FA helps to secure your VPN?
Mar 10, 2022
iam
4 Pillars of Identity and Access Management
Oct 18, 2024

iam
What is Attribute-Based Access Control (ABAC)? – A Complete Guide
Oct 23, 2024
IAM
What is CIAM? Customer Identity and Access Management Solution
Oct 21, 2022

concepts
What is Deprovisioning & why is it important?
Aug 19, 2022

solutions
What is Fine Grained Access Control (FGAC) and why is it important?
Nov 19, 2024

concepts
Header Based Authentication
Jun 13, 2022

IAM
What is Identity as a Service (IDaaS)? - Exploring through a comprehensive guide
Mar 30, 2022
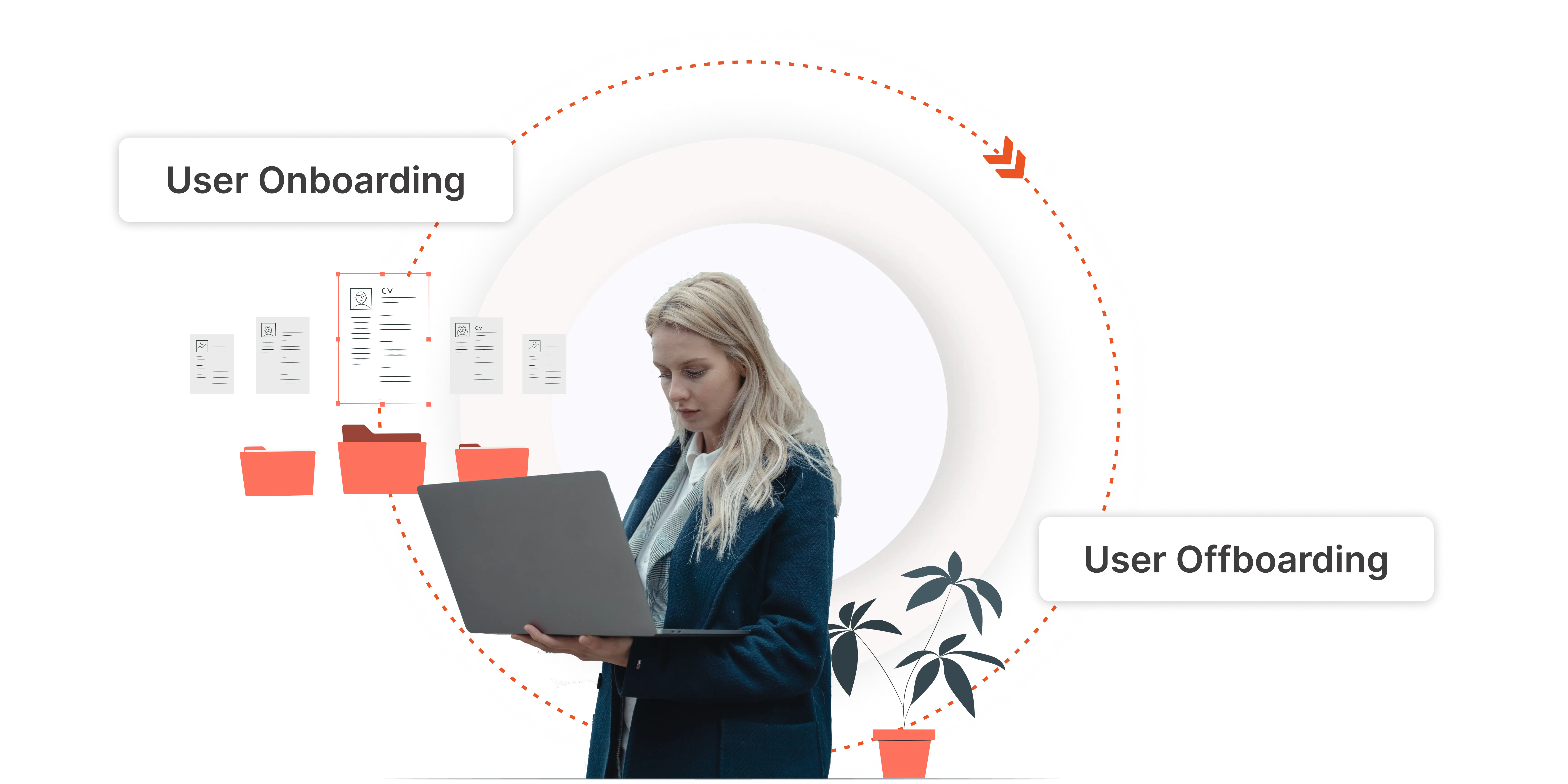
IAM
What is Identity Lifecycle Management?
Oct 21, 2022

concepts
What is Out-Of-Band Authentication (OOBA)?
Jun 29, 2022

IAM
What is Provisioning and how does it work?
Oct 21, 2022
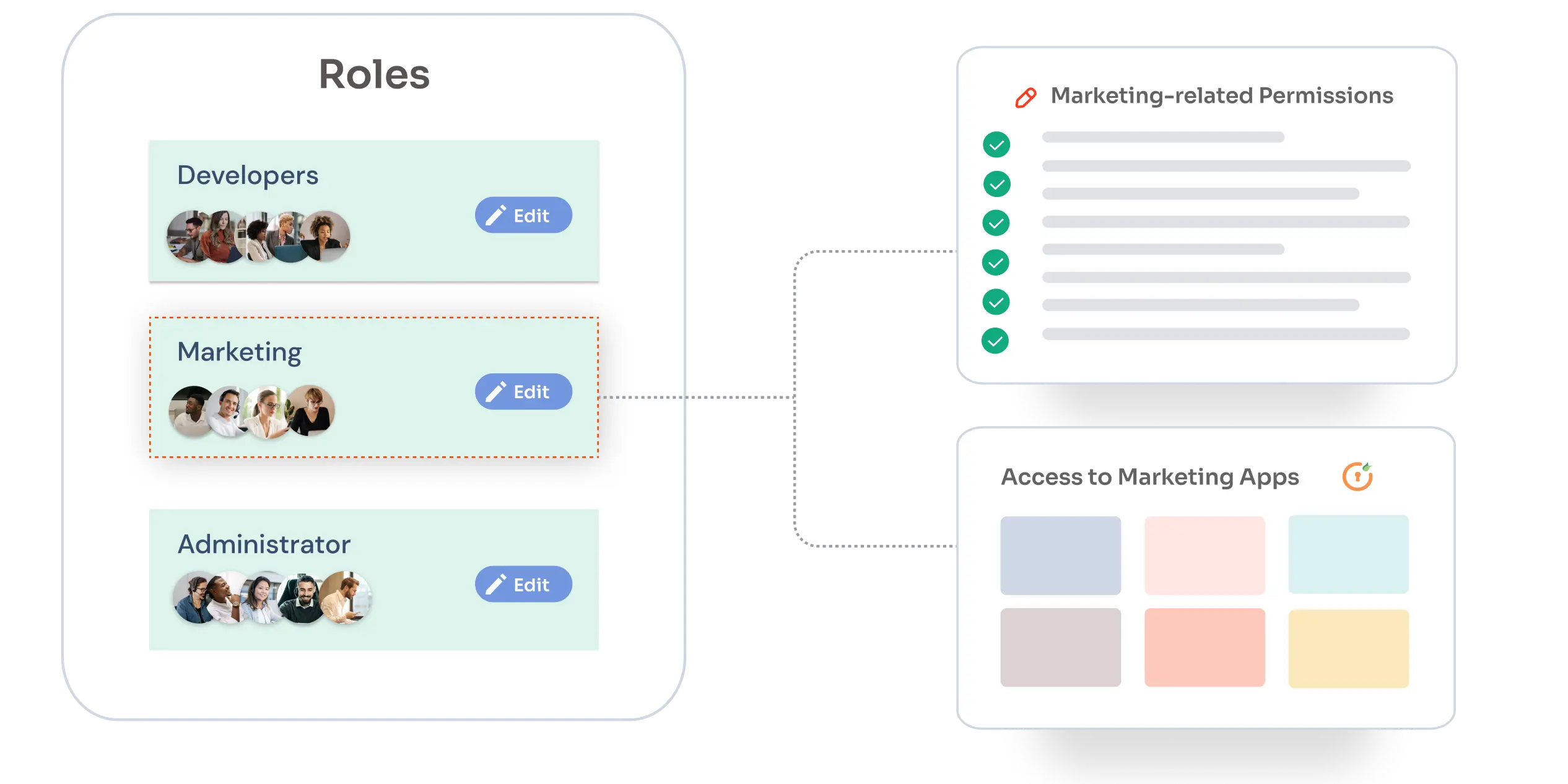
IAM
What is Role Based Access Control (RBAC)?
Jun 27, 2024

IAM
What is Shibboleth?
Dec 23, 2023
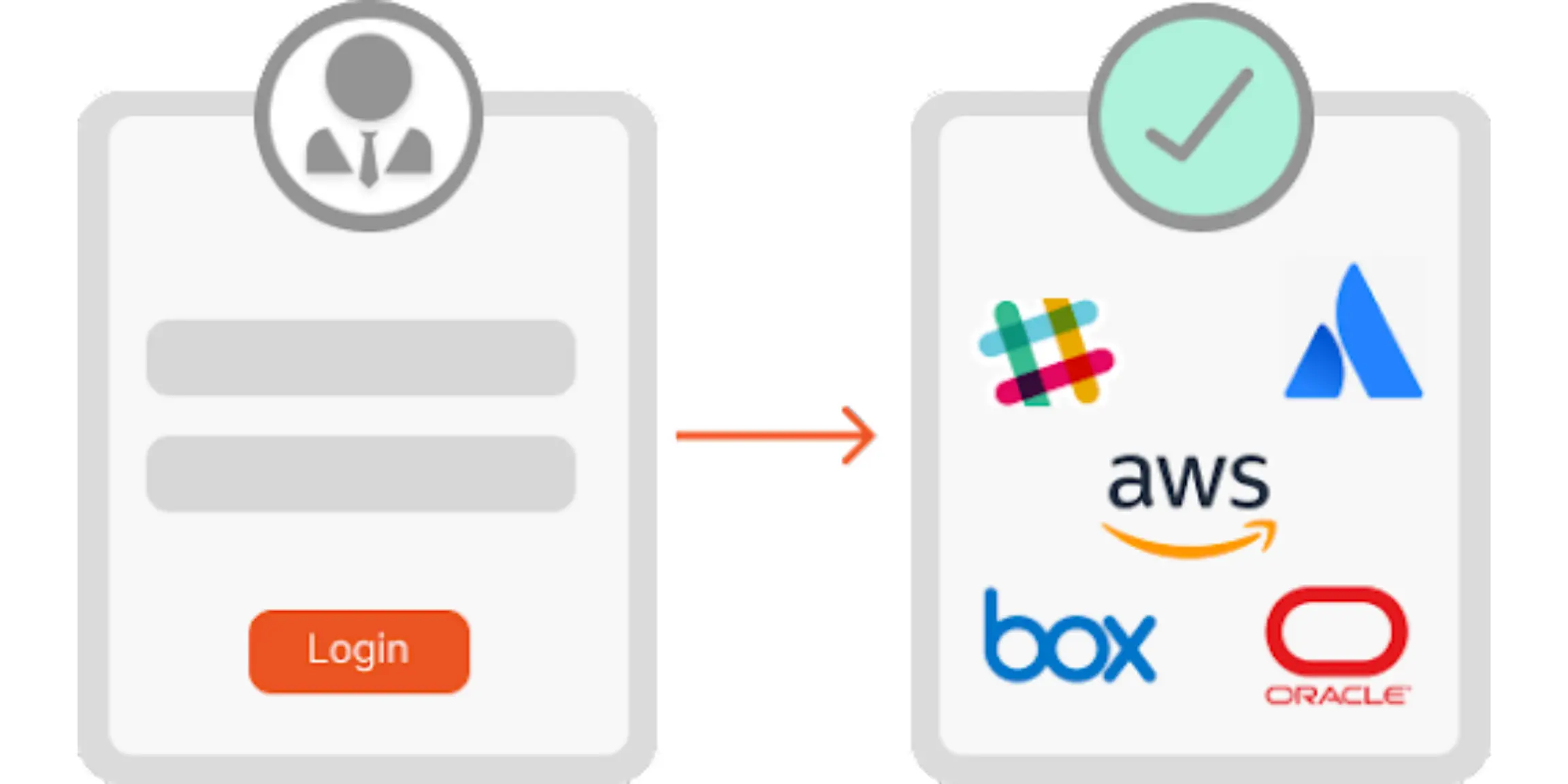
concepts
Web SSO: What is it and How does it Work?
Jun 27, 2022
IAM
What is WebAuthn? Web Authentication Explained
Feb 28, 2025

concepts
Why is Multi-Factor Authentication (MFA) important?
Jan 8, 2024

iam
Why is Multi-factor Authentication (MFA) necessary for Banks and Financial Institutions?
Jul 22, 2023
