PAM
IAM
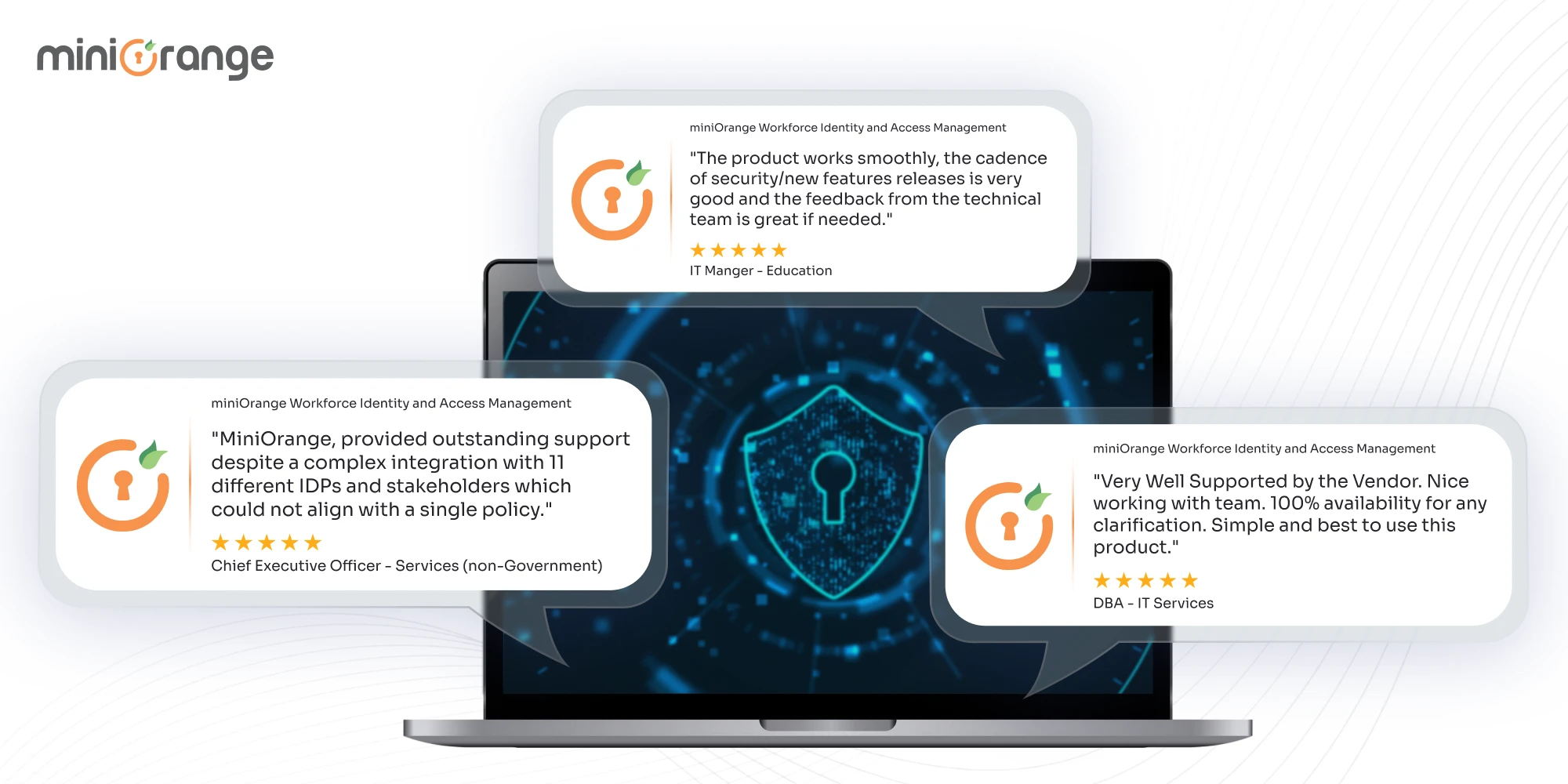
miniOrange Recognized as a Strong Performer in Gartner Voice of the Customer 2025
Sep 8, 2025
PAM
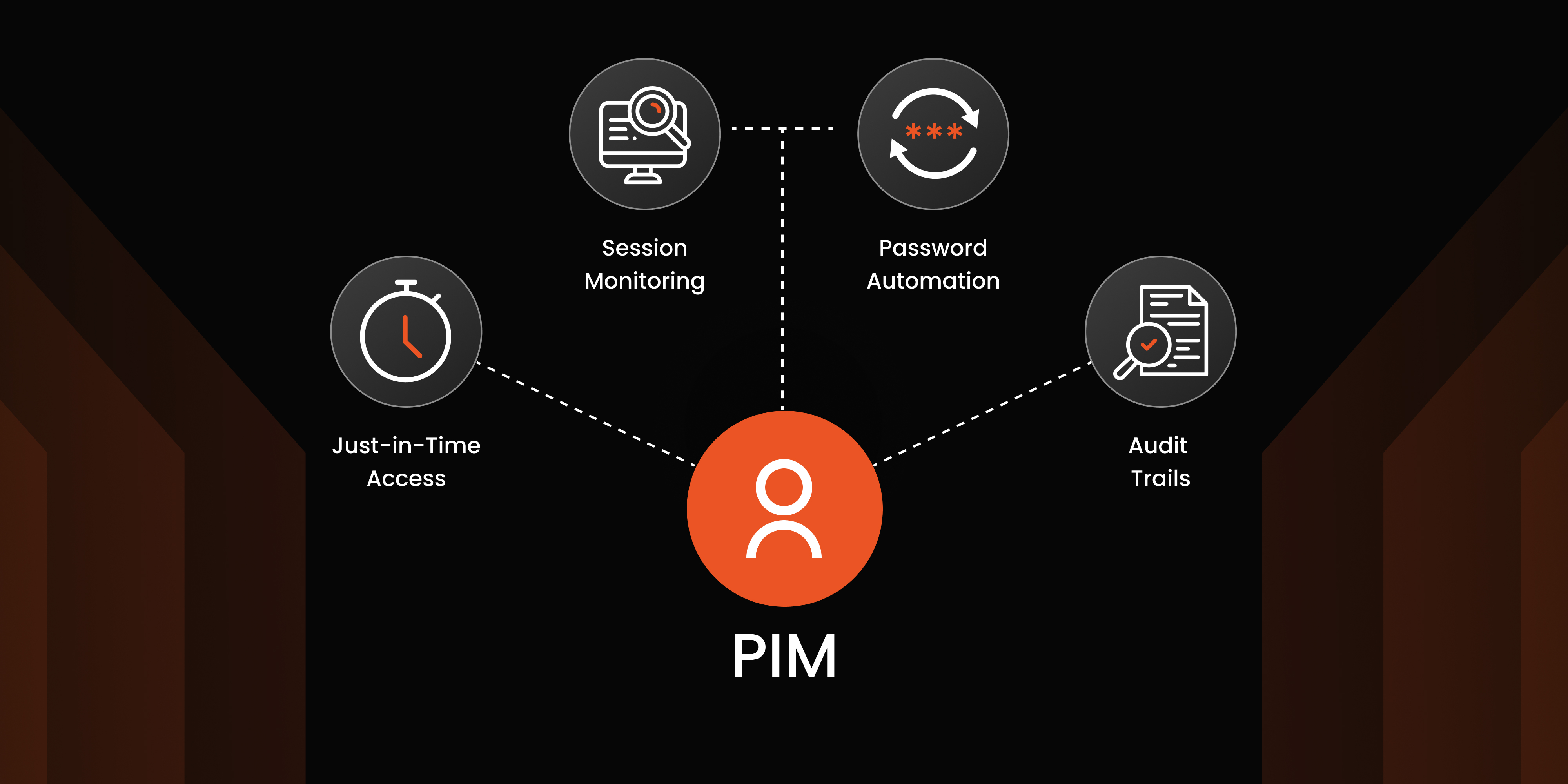
Privileged Identity Management (PIM) Solutions: A Complete Guide for 2025
Aug 24, 2025

PAM
Top 10 Benefits of Privileged Access Management (PAM)
Aug 20, 2025

PAM
Best Privileged Access Management (PAM) Solutions in 2025
Jul 28, 2025
PAM
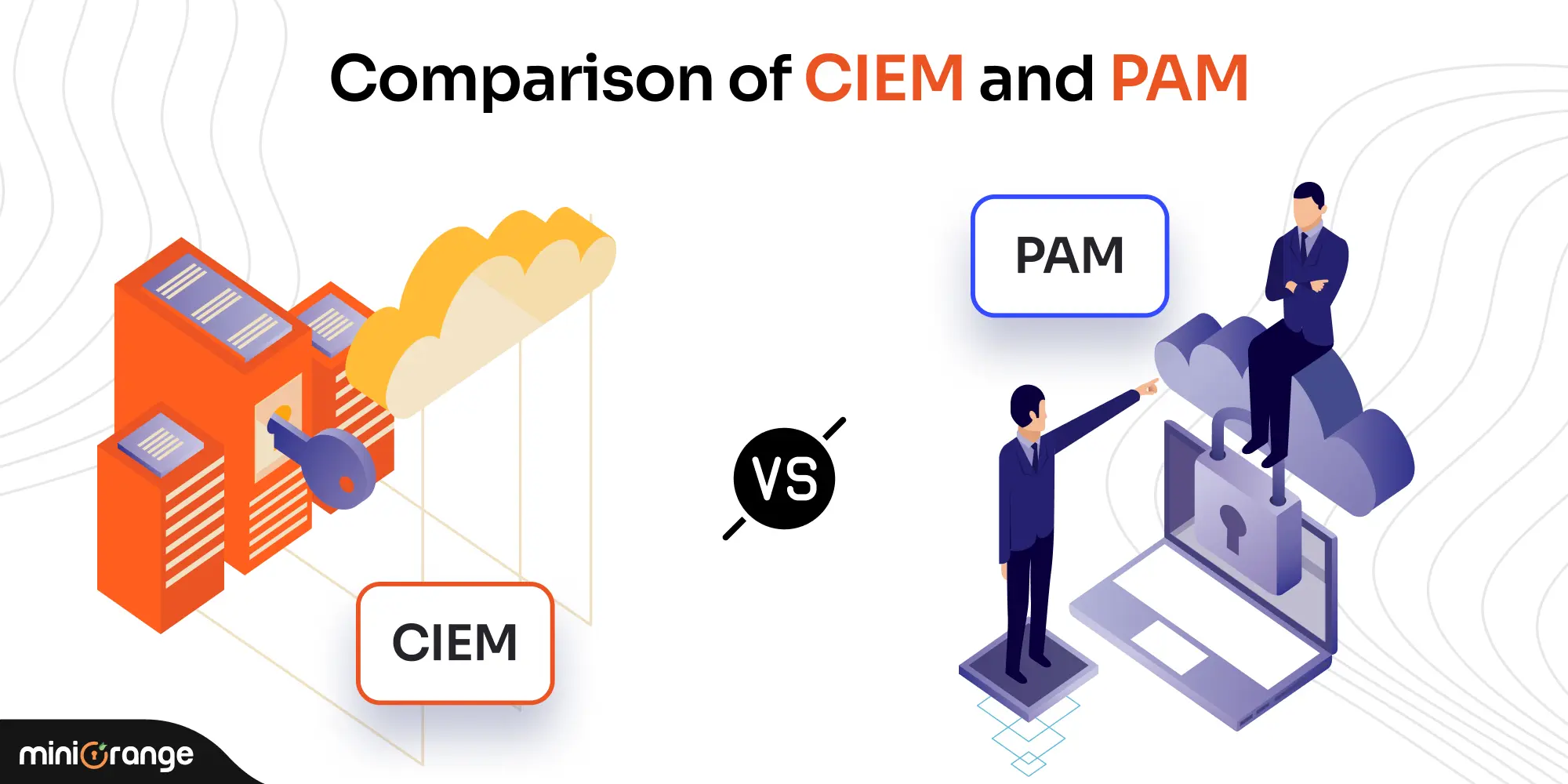
CIEM vs PAM: Which Is Better for Privileged Access Management?
Jul 15, 2025

IAM
What is a Ransomware Attack? Definition, Types & Prevention Strategies
Jul 1, 2025

PAM
What is Privileged Task Automation? | Explained
May 19, 2025

PAM
Zero Trust PAM Explained: Secure Privileged Access in 2025
May 19, 2025

concepts
10 Privileged Access Management Best Practices in 2025
Feb 20, 2025
PAM
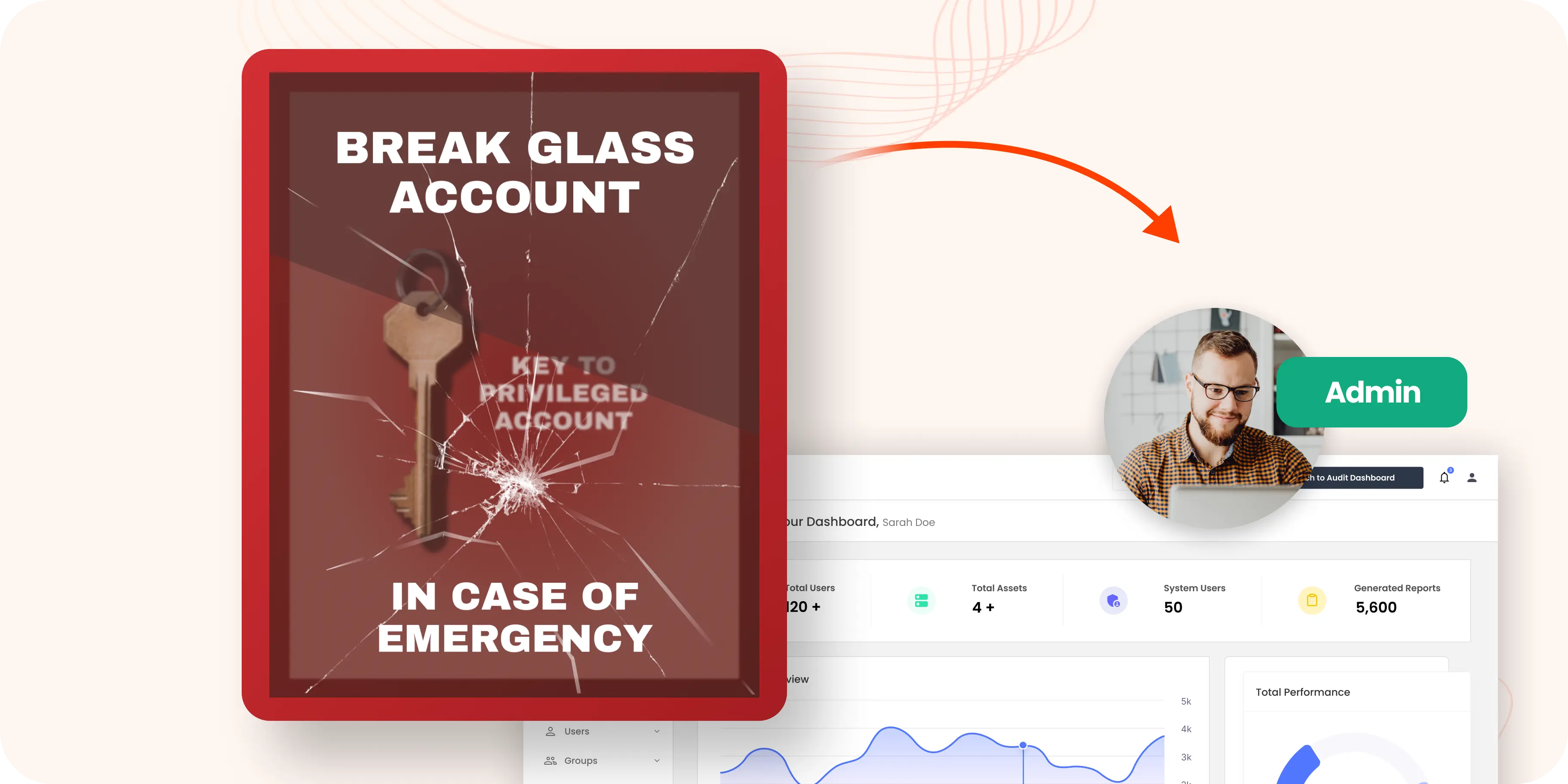
Break glass privileged account
Jan 22, 2025
PAM
Cloud Privileged Access Management (PAM) - Challenges & Benefits
Dec 5, 2024
PAM
Top 10 Privileged Access Management (PAM) Use Cases in 2025
Dec 3, 2024

PAM
Privileged Access Management for Linux and Unix | PAM Linux
Nov 22, 2024
iam
4 Pillars of Identity and Access Management
Oct 18, 2024

PAM
SWIFT Customer Security Programme (CSP) in Banking
Sep 16, 2024
PAM
What Is the Principle of Least Privilege?
Sep 5, 2024

PAM
What is Privileged Access Management (PAM)?
Aug 7, 2024
concepts
What Zero Standing Privileges (ZSP)? Explained
Jul 25, 2024

PAM
What is Privileged Account Management?
May 30, 2024

IAM
IAM vs. PAM: What’s the difference?
May 20, 2024

PAM
PIM vs. PAM: What’s the difference?
Apr 23, 2024

concepts
What are Privileged Accounts? and its Types
Apr 23, 2024
