Cyber threats are surging, making your Atlassian ecosystem security more critical than ever. In 2026, protecting your Jira and Confluence REST APIs isn't just a best practice—it's essential for business survival.
Without strong API authentication, you risk exposing sensitive data, project information, and valuable intellectual property to unauthorized users.
This all-inclusive blog by miniOrange Atlassian experts walks you through proven security methods, explains why outdated practices put you at risk, and shows how to implement bulletproof protection using miniOrange's Enhance API Authentication app.
Why Atlassian REST API Security Is Critical in 2026
Securing REST APIs is vital for preventing unauthorized access to critical business data. Atlassian provides strong authentication and authorization mechanisms to safeguard these APIs.
Key threats: In Jira and Confluence, APIs serve as gateways to sensitive actions—updating issues, creating pages, retrieving user data, and accessing project details.
Impact of breaches: A security incident can lead to data theft, project compromise, system disruption, reputational damage, and significant financial and legal consequences.
According to industry reports, 92% of organizations experienced at least one API security incident in 2023, with 50% of all API traffic remaining unmonitored. The cost of ignoring API security extends far beyond immediate data loss.
Essential Security Best Practices for 2026
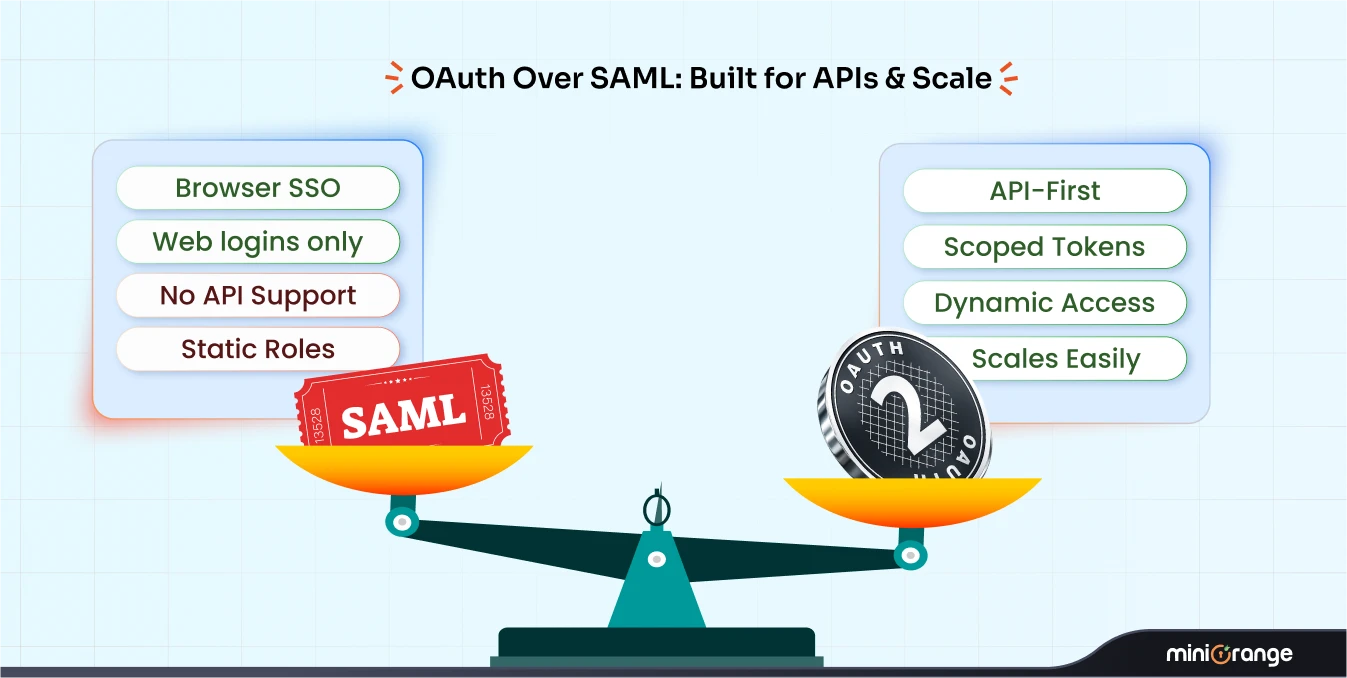
Authentication methods: Use strong authentication, like API tokens and OAuth 2.0, instead of basic authentication.
Access controls: Implement IP whitelisting to restrict access to trusted networks.
Traffic management: Apply rate limiting to prevent denial-of-service attacks.
Encryption: Ensure all data uses HTTPS/TLS encryption to protect against interception.
Monitoring: Establish all-inclusive, logging and real-time monitoring for suspicious activities.
Atlassian officially deprecated basic authentication in 2019 and strongly recommends migrating to more secure alternatives.
Comparing REST API Authentication Methods
Avoid Basic Authentication (Obsolete and Risky)
Basic authentication transmits credentials as easily-decoded Base64 strings with every request. This creates significant security vulnerabilities, especially without HTTPS protection.
Why it's dangerous:
- Credentials are sent in reversible encoding
- High vulnerability to credential theft
- No built-in expiration or revocation
- Deprecated by Atlassian since 2019
When to avoid: Production environments, public-facing APIs, or any security-sensitive application.
API Token Authentication: Simple and Secure
API tokens replace passwords with unique, randomly generated keys that can be easily managed and revoked.
Benefits:
- Easy revocation: Instantly deactivate compromised tokens without changing user passwords
- Script-friendly: Perfect for automation and third-party integrations
- Granular control: miniOrange's app enables user-specific tokens with group-based restrictions
- Audit capability: Track and monitor token usage through all-inclusive logging
OAuth 2.0: Industry Standard for Enterprise Security
OAuth 2.0 provides secure authorization through access tokens without sharing user credentials. It's the recommended method for enterprise applications requiring delegated access.
How OAuth 2.0 works:
- Application requests an access token from the identity provider (Azure AD, Okta, etc.)
- Identity provider verifies the user and issues a short-lived token
- Application uses a token to authenticate API requests with specific permissions
Key advantages:
- No credential sharing: Users never expose passwords to third-party applications
- Scoped access: Tokens grant specific, limited permissions
- Token refresh: Short-lived tokens can be automatically renewed
- Enterprise integration: Works seamlessly with existing identity providers
JWT (JSON Web Tokens): Stateless and Scalable
JWT tokens are self-contained and digitally signed, enabling efficient authentication without database lookups.
Why JWT is powerful:
- Stateless operation: Reduces server load and improves performance
- Self-contained: Includes all necessary information within the token
- Tamper-proof: Digital signatures ensure token authenticity
- Scalable: Ideal for distributed systems and microservices
miniOrange's Enhance API Authentication app simplifies JWT implementation while integrating advanced security features like IP restrictions and group-based restrictions.
Advanced Security Features for Atlassian APIs
Modern API security requires layered protection beyond basic authentication. miniOrange's Enhance API Authentication app provides all-inclusive security for Jira and Confluence Cloud/Data Center.
Core Security Features
IP and Group Restrictions: Control API access based on network location or user groups, effectively blocking unauthorized external access.
Read-Only Permissions: Prevent data modification by enforcing read-only access for user groups.
Popular IDP Support: Integrate with various identity providers (Okta, Azure AD, AWS Cognito) for centralized security management.
Token Management: Instantly revoke compromised tokens or disable all tokens for specific users.
Rate Limiting: Protect against abuse and denial-of-service attacks with customizable request limits on API Tokens.
Audit Logging: Maintain all-inclusive records of all API requests, including user, timestamp, and response status.
Advanced Access Controls
Public API Protection: Add authentication layers to APIs that are public by default.
Admin-Only Token Creation: Restrict token generation to administrators, with secure email delivery to users.
Get Started with Secure Atlassian APIs
Ready to protect your Atlassian REST APIs with enterprise-grade security?
Step 1: Install miniOrange's Enhance API Authentication app from the Atlassian Marketplace (free 30-day trial available).
Step 2: Configure your preferred authentication method—OAuth 2.0, API tokens, or JWT—using our Complete setup guides.
Step 3: Implement security policies including IP restrictions, group-based access controls, and rate limiting.
Step 4: Enable complete audit logging and monitoring to track API usage and detect threats.
Don't wait for a security incident to take action.
Secure your Jira and Confluence APIs today and protect your organization's most valuable digital assets with minOrange’s Enhanced API Authentication App.
Frequently Asked Questions
Q: Can I still use basic authentication with Atlassian APIs in 2026?
While basic authentication may technically work on some on-premise instances, it's strongly discouraged for production use. Atlassian deprecated this method in 2019 due to significant security risks. You should migrate to secure alternatives like OAuth 2.0 or API tokens immediately.
Q: What's the difference between OAuth 2.0 and JWT?
OAuth 2.0 is an authorization protocol that defines how applications get permission to access resources, while JWT is a token format for securely transmitting information. They work together—OAuth 2.0 often uses JWT as its token format to provide both secure authorization and efficient token validation.
Q: How do I generate API tokens in Jira?
For Jira Cloud, navigate to your profile settings and find the "API Token" section to create new tokens. Atlassian provides options like PAT tokens or application links. You can also use our plugin to authenticate using OAuth 2.0 tokens or JWTs.
Q: How does rate limiting improve API security?
Rate limiting controls request frequency to prevent abuse, denial-of-service attacks, and system overload. Atlassian's Data Center products include built-in rate limiting to maintain instance stability.


Leave a Comment