Let us take an example of a situation where your organization faces a sudden IT outage, locking out key accounts from critical systems. All of this leads to productivity halts, customers growing restless, and every minute costs you valuable time and resources. In moments like these, having an emergency plan is crucial—but does yours include a way to regain access to your digital systems?
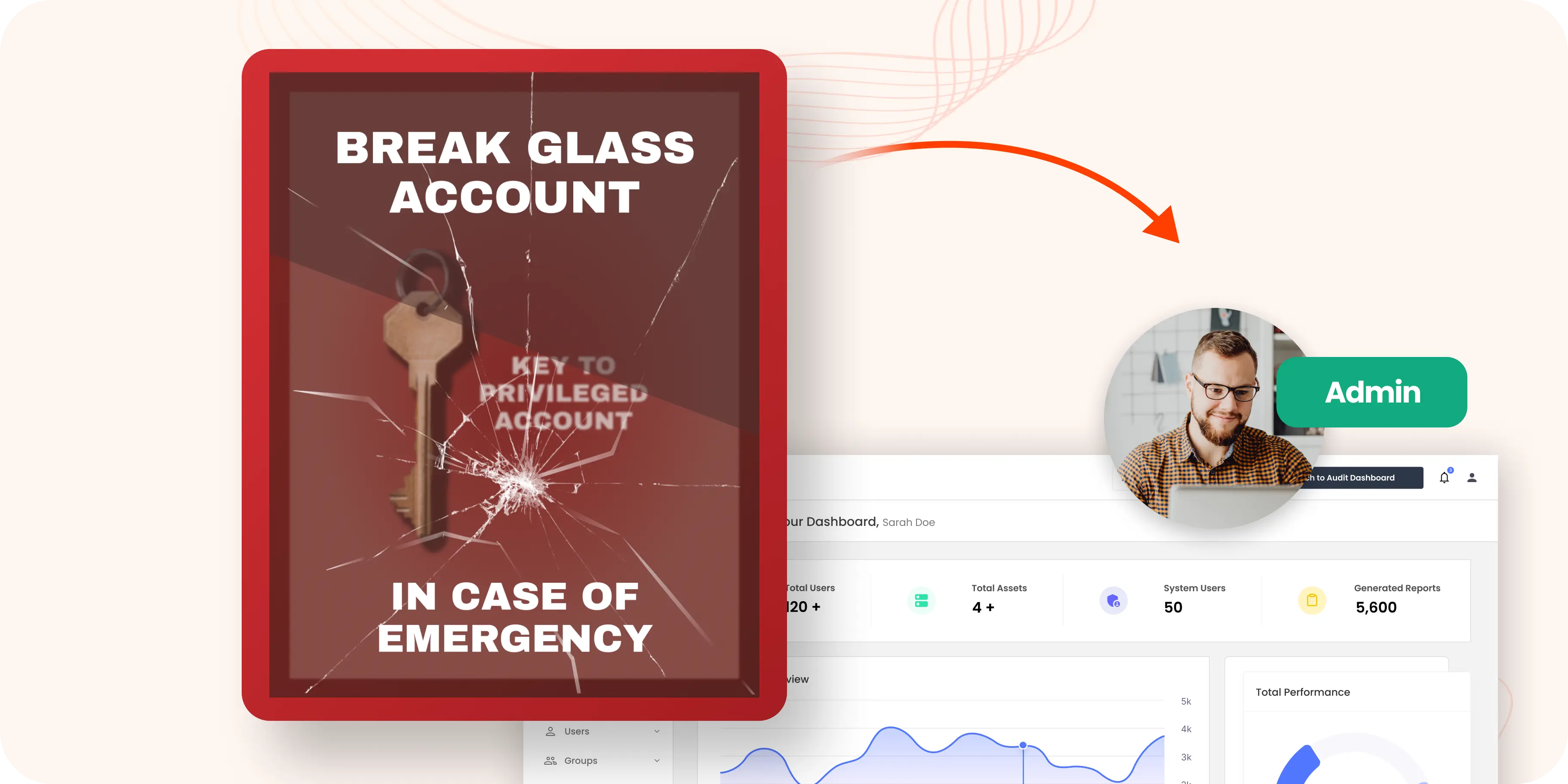
This is where break-glass accounts come into play. Often referred to as emergency access accounts, these are your lifeline to restoring control during crises like cyber-attacks or system failures/ system halts. Similar to a fire alarm in a building, a break-glass account serves as your emergency override to regain access to important systems and ensure business continuity.
In this blog, we’ll explore the concept of break-glass accounts, their meaning, why they are important for modern organizations, and best practices for managing them effectively.
What is a Break Glass Account?
A Break Glass Account is a specially designated, high-privilege account reserved for critical situations where regular access methods fail or immediate intervention is necessary. This account serves as a temporary bypass to standard access controls, on a temporary basis. It enables administrative access to essential IT systems during emergencies like data breaches, system malfunctions, or password lockouts.
The term "break glass" draws inspiration from the act of shattering a glass panel to activate a fire alarm in urgent situations. Similarly, this account acts as a fail-safe, allowing organizations to regain control of essential systems during crises like data breaches, tool malfunctions, or password lockouts.
A break glass account is pre-configured with elevated privileges, granting emergency access to critical infrastructure, such as root or administrative systems. These accounts bypass regular Identity and Access Management (IAM) or Privileged Access Management (PAM) controls, ensuring operational continuity in exceptional circumstances.
To maintain security, break glass credentials are stringently managed. They are stored securely, accessible only to authorized personnel, and designed with a limited lifespan to prevent misuse. Regular monitoring, documentation, and testing ensure that the account remains functional and is used solely for its intended purpose—addressing emergencies with precision and control.
Why Do Organizations Need Break Glass Accounts?
Break glass accounts serve as critical safety measures for organizations, enabling access to systems during emergencies when standard access methods fail. These accounts are essential for maintaining operations across various unexpected scenarios, such as natural disasters, technical disruptions, or security breaches.
Reasons for Implementing Break Glass Accounts
- Operational Recovery: Break glass accounts provide critical access during system outages or failures, facilitating rapid troubleshooting and minimizing downtime to maintain business continuity.
- Emergency Response: These accounts are essential for swift disaster recovery and incident response, allowing quick access to restore services and address vulnerabilities following cyber-attacks or natural disasters.
- Security and Compliance: During security incidents or when key staff are unavailable, break glass accounts ensure continued access to crucial systems. This access supports compliance needs by enabling secure, audited actions to safeguard and manage sensitive data.
- Versatile Accessibility: Whether it's handling DDoS attacks on cloud services or ensuring healthcare providers can access patient records in emergencies, break glass accounts provide necessary and controlled access to defend, manage, and operate essential functions across various scenarios.
The Importance of Break Glass in Technical Security Environments
Modern security measures, such as Privileged Access Management (PAM) and multi-factor authentication (MFA), are designed to enforce strict access controls, effectively blocking unauthorized users and potential cyber threats. However, these very controls can inadvertently lock out legitimate users, posing risks to business continuity and emergency response efforts.
In high-stakes industries like healthcare or critical infrastructure, being unable to bypass these controls during emergencies can lead to severe consequences, including risks to lives or vital operations. This is where break glass accounts become an indispensable backup mechanism, ensuring uninterrupted access when normal authentication methods fail.
Break glass is essential for scenarios like:
- System Downtime: When PAM tools or authentication servers are unavailable due to maintenance or technical failures.
- Authentication Failures: Situations where MFA cannot be accessed because of a network outage or infrastructure failure.
- Cyberattacks: For instance, during a DDoS attack that disrupts login capabilities across critical systems.
- User Lockouts: Cases where a user is locked out due to incorrect password attempts or conditional access policies.
- Service Disruptions: Failures in federation services or other system outages requiring immediate intervention.
While PAM and IAM solutions are critical for robust security, having a secure and well-regulated backup like break glass access ensures that organizations are prepared for the unexpected. A strong break glass strategy not only safeguards business operations during crises but also complements your IAM/PAM tools by providing a controlled and auditable emergency access solution.
Break-Glass Procedures for IT Security: A Step-by-Step Guide
Let us have a look at the step-by-step guide to setting up and managing break-glass access effectively.
1. Defining Emergency Access Scenarios
Clearly define the conditions under which emergency access is authorized to prevent unnecessary activation. Therefore prior identification of the situation is required where break-glass accounts will be used, such as service outages/ DDoS attacks/ lost administrative credentials or a combination of any.
2. Pre-Stage Break-Glass Accounts
To effectively manage emergency access, it's crucial to create dedicated break-glass accounts equipped with global admin rights, deliberately exempt from standard access protocols such as multi-factor authentication (MFA). These accounts should remain unlinked to other systems or individuals to mitigate risks associated with dependency failures. Additionally, maintaining at least one break-glass account per platform is advisable, complemented by a second backup account as a wise measure to safeguard against unforeseen emergencies.
3. Assign Emergency Account Managers
Designate an emergency account manager responsible for overseeing and granting break-glass access during operating hours. This individual should ensure that access is only granted after verifying the requestor’s identity and recording all activities for auditing.
4. Implement a Secure Storage System
Store the credentials for break-glass accounts in a highly secure environment, such as:
- Physical vaults for hardware-based keys (e.g., Yubikeys). Or
- Encrypted digital vaults with limited access.
Care should be taken to ensure the storage mechanism aligns with your organization's IT infrastructure (on-premises, cloud, or hybrid).
5. Emergency Activation Procedure
- Step 1: The user initiates a request for break-glass access, citing the specific emergency.
- Step 2: The emergency account manager reviews and validates the request, verifying the user’s identity through pre-approved methods.
- Step 3: Access credentials are provided to the requester, and their activity is continuously monitored throughout the session.
6. Post-Emergency Clean-Up
After resolving the emergency, it is essential to immediately disable or delete the credentials of the break-glass account that was used. This step is followed by a thorough audit of all actions performed during the session to identify and address any suspicious or inappropriate activities. Finally, generate new credentials for the account and ensure they are securely stored, and ready for use in future emergencies, thereby maintaining the integrity and security of your systems.
7. Regular Maintenance and Testing
Periodically review and test the break glass process to ensure it functions smoothly when needed. Regular updation of policies, credentials, and training based on organizational changes or new security challenges.
Common Challenges with Break Glass Accounts
1. Mismanagement or Lack of Defined Policies
Break glass accounts often face challenges due to the absence of clear policies outlining their purpose, access conditions, and usage protocols. Without well-defined guidelines, these accounts can be misused or improperly configured, leading to potential security vulnerabilities.
2. Overuse and Privilege Creep
When break glass accounts are accessed too frequently or for non-emergency situations, they can suffer from privilege creep—a scenario where unauthorized or excessive permissions accumulate over time. This undermines their intended purpose and increases the risk of exploitation.
3. Absence of Monitoring and Alerts
A lack of real-time monitoring and alerting mechanisms can leave break glass accounts vulnerable to unauthorized access. Without proper tracking, organizations may fail to detect misuse or suspicious activities, making it difficult to maintain security and accountability.
Best Practices for Managing Break Glass Accounts: miniOrange
At miniOrange, we understand that break glass accounts are critical for maintaining operational continuity during emergencies. However, their high-privilege nature also makes them a potential risk if not managed correctly. To ensure secure and effective management, organizations should follow these best practices:
Define and Document Policies
Establish clear guidelines for when, how, and by whom break glass accounts can be used. Document these policies in detail to ensure accountability and consistency during emergency situations.
Implement Naming Conventions
Use intuitive yet secure naming conventions like "Emergency_Admin" or "BG_Admin" to differentiate break glass accounts from standard accounts. This approach ensures they are easily identifiable without revealing sensitive details to unauthorized users.
Regular Audits and Access Reviews
Conduct periodic reviews to ensure the accounts are not misused. Audit access logs, review account activity, and verify that these accounts are only accessed under legitimate circumstances.
Automated Password Rotation
Use miniOrange's automated password rotation feature to frequently update break glass account credentials. This reduces the risk of unauthorized access and ensures passwords are current for emergency use.
Conclusion
Effectively managing break glass scenarios is critical to ensuring operational continuity and maintaining security during emergencies. Tools like miniOrange Privileged Access Management (PAM) offer streamlined solutions that simplify and enhance break-glass account management.
With secure enterprise vault storage, organizations can protect sensitive credentials, ensuring they are accessible only to authorized personnel during emergencies. Automated policy enforcement eliminates the risk of mismanagement by applying predefined rules, while real-time monitoring ensures all account activities are tracked and flagged for potential risks. Additionally, compliance reports help meet regulatory standards, providing detailed records of broken glass usage for audits and reviews.
By leveraging advanced tools like miniOrange PAM, organizations can mitigate risks, ensure accountability, and maintain seamless access to critical systems when it matters most.
FAQs
1. How many break glass accounts should an organization have?
The number of break glass accounts an organization needs depends on its size, infrastructure complexity, and operational requirements. Generally, one or two break glass accounts are sufficient for smaller setups, while larger organizations may need additional accounts to cover distributed teams.
2. What tools support break glass accounts?
Break glass accounts can be supported and managed using robust Privileged Access Management (PAM) solutions, Identity and Access Management (IAM) systems, and credential vaulting tools. Platforms like miniOrange offer built-in features to create, monitor, and secure break-glass accounts. These tools often provide automated auditing, access control policies, and expiration settings to ensure compliance and prevent misuse.
3. How to name break glass accounts?
Naming conventions for break glass accounts should prioritize clarity, relevance, and security. A common practice is to include a prefix like "BreakGlass" or "Emergency" in the account name, followed by the associated system or role (e.g., "BreakGlass_Admin" or "Emergency_AWS_Access"). Avoid overly descriptive names that might reveal sensitive information about the account's purpose to potential attackers. Consistent naming also simplifies account identification and management during audits or emergencies.
Author


Leave a Comment