Introduction
Businesses increasingly use cloud services like Google Workspace, Amazon Web Services (AWS), Hubspot, and Dropbox to improve work productivity and drive innovation. However, this accelerated shift to cloud platforms has exposed businesses to new security challenges, such as unauthorized data breaches and compliance violations.
A Cloud Access Security Broker (CASB) is a powerful tool against these issues, delivering unmatched visibility and control over data to protect enterprises against these threats.
What is Cloud Access Security Broker (CASB)?
A Cloud Access Security Broker (CASB) is a security solution that monitors, controls, and secures all the interactions your users have with work applications, either on-premise or cloud-delivered.
CASB defined in simplest terms: it's a security tool that applies enterprise-grade policies across all cloud environments, like SaaS platforms. That includes file-sharing, messaging, collaboration tools, cloud storage, CRM software, and more.
Problems with Traditional Perimeter Security
1. Limited Control Over Cloud Apps
Traditional perimeter security focuses on protecting the network's edge, often neglecting the visibility and control needed for cloud-based applications and remote devices. This gap can leave sensitive data exposed and unmonitored.
2. Inadequate Protection for Cloud Services
Traditional security measures may not effectively cover the complexities of cloud services and applications, leading to potential security gaps and vulnerabilities.
3. Challenges with Remote and Mobile Access
As organizations embrace remote work and mobile devices, traditional perimeter security struggles to secure data accessed from outside the corporate network, increasing the risk of breaches.
4. Difficulty in Preventing Shadow IT
Employees often use unauthorized cloud services (shadow IT) that bypass traditional security measures, leading to unmonitored data access and potential security risks.
5. Compliance and Data Privacy Issues
Traditional perimeter security may not address the specific compliance and data privacy requirements for cloud environments, risking regulatory violations and data breaches.
The 4 Pillars of Cloud Access Security Broker (CASB)
Let’s dive deeper into the four pillars of Cloud Access Security Broker (CASB). These are the essential capabilities that a complete CASB solution must offer:

1. Visibility
CASB provides detailed reports on app usage, user behavior, and security risks. Whether it’s Google Drive, Dropbox, or Trello, you get a clear picture of everything in use.
Shadow IT remains a significant issue, with employees often using unapproved tools. CASB tools identify hidden usage, allowing organizations to make informed decisions and secure all digital activity.
2. Compliance
CASB tools help enforce standards like GDPR, HIPAA, PCI DSS, ISO 27001, and more, with audit trails and automated policy enforcement.
They simplify regulatory reporting and prevent accidental violations by flagging non-compliant activities in real time.
3. Data Security
With built-in Data Loss Prevention (DLP),CASB protects sensitive data from being leaked, shared, or mishandled. Policies can restrict file sharing, enforce encryption, and apply redaction.
4. Threat Protection
From ransomware to insider threats, CASBs monitor for suspicious behavior and protect your cloud environment in real time.
Together, these four pillars deliver a holistic defense against cloud threats while enabling productive, compliant usage of cloud platforms.
How Does CASB Work? A Step-by-Step Breakdown
If you’re wondering how a CASB works, here’s a simple breakdown:
Step 1: Monitor and Analyze User Activity
CASB solutions continuously monitor user activity in real-time across those apps. It looks for behavioral patterns, such as unusual login times or mass file downloads, and flags anything suspicious.
Step 2: Enforce Security Policies
Based on what it observes, the CASB then enforces your security policies. These might include blocking file downloads to personal devices, restricting access from untrusted IP networks, encrypting sensitive documents, or preventing unauthorized sharing or uploads.
Step 3: Detect and Respond to Threats
Modern CASBs are equipped with a threat detection feature. They check for login attempts from unusual locations or insider data theft. Once a threat is detected, CASB can trigger alerts or take automated action, like suspending the user account.
Step 4: Ensure Data Compliance
CASB tools help your organization meet regulatory requirements like GDPR, HIPAA, SOC 2, or PCI-DSS by ensuring that all data interactions follow compliance rules. They log every user action, enforce retention policies, and generate audit-ready reports automatically.
Step 5: Integrate Directly via APIs for Deep Visibility
Some CASBs offer API-level integrations with cloud services like Google Workspace or Microsoft 365. This means they can directly access logs and metadata, providing deeper insights and more accurate control than traditional, network-only tools.
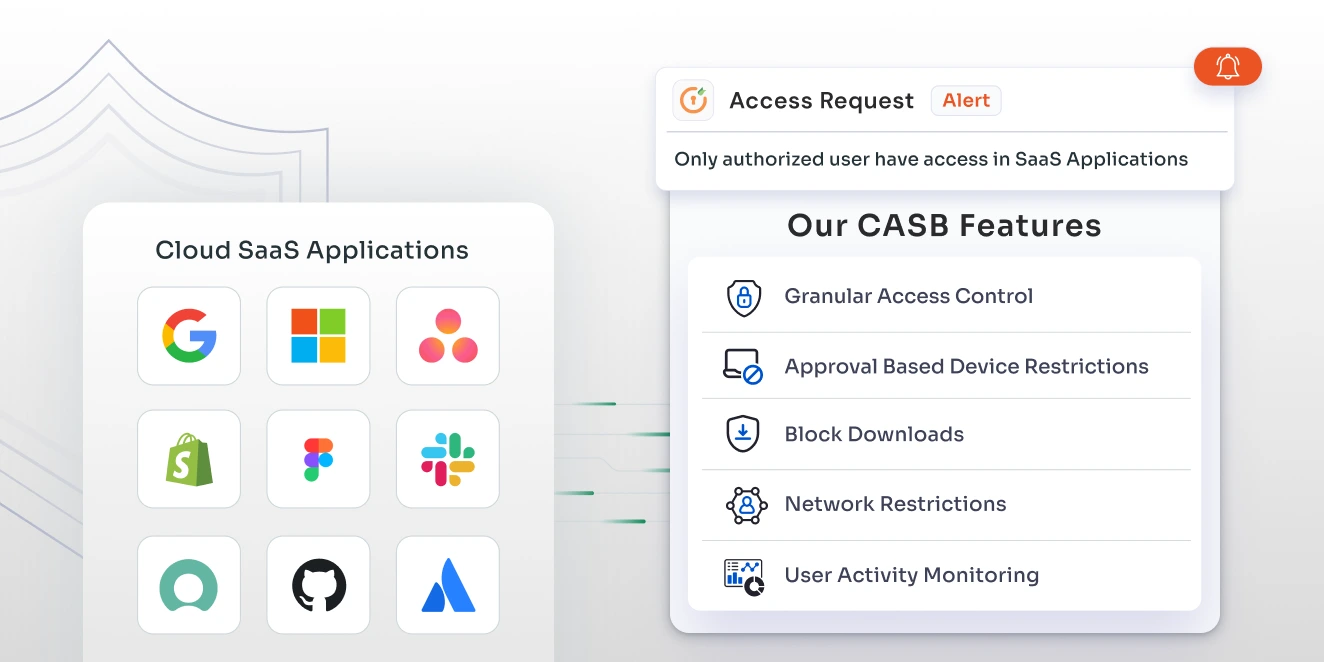
Key Features of CASB Security
1. Controls Access with Precision
CASB cyber security offers advanced access controls to ensure that only the right people can access your data. Features like Single Sign-On (SSO) and Multi-Factor Authentication (MFA) make it tough for unauthorized users to sneak into your cloud applications.
2. Monitors and Detects Threats in Real-Time
Cloud security broker continuously monitors all activities and detects any suspicious behavior in real-time. If something seems off, like an unusual login attempt or data access request, CASB security springs into action to alert you and take preventive measures.
3. Enforces Data Policies
CASB security helps enforce your organization's data policies across all cloud services. Whether you need to ensure that sensitive information is stored securely or that data sharing complies with regulations, Cloud App Security Broker makes it easy to set and enforce these rules.
4. Protects against Insider Threats
Not all threats come from the outside. Sometimes, the risk comes from within your organization. Cloud access broker helps mitigate these insider threats by providing detailed visibility into user activities. If an employee starts accessing data they shouldn't, or if there's a sudden surge in data downloads, the CASB security will alert you so you can take action before it's too late.
5. Shields Your Data with Encryption
One of the most vital roles of CASB software is encrypting your data. Imagine encryption as a lock that keeps your data safe from prying eyes. Whether your data is at rest or in transit, CASB security ensures that it's encrypted and secure. This means even if someone manages to intercept your data, it will be utterly unreadable without the proper decryption key.
Key CASB Benefits for Your Organization
When it comes to securing your cloud environment, the benefits of CASB go far beyond basic monitoring.
Let's break down the key CASB functions and the value they bring:
- Full Visibility & Control
CASB gives you complete visibility and control over user sessions in real-time, whether the apps are IT-approved or not. You'll know who's accessing what, on which device, and from where. That kind of visibility makes it easy to spot risky behavior, patch up security gaps, and cut down on Shadow IT.
- Smarter Access Policies
CASB makes smart decisions based on context. You can, for example, allow Salesforce access only if someone's using a company laptop within your country. If they're logging in from a personal device or sketchy location? Access denied or restricted. Simple, smart, secure.
- Keep Sensitive Data Safe (Data Leakage Protection)
CASB's built-in Data Loss Prevention (DLP) steps in to stop sensitive data from being copied, downloaded, or shared without permission. You can block uploads, restrict external sharing in real time. It's like having a digital safety net for your data.
- Spot Threats Instantly
CASB keeps an eye out 24/7 for suspicious activity. Whether it's a weird login time or a massive file download, it'll flag it. And thanks to machine learning and threat intel feeds, it can even catch malware or insider threats before they do damage.
- Works with All Your Favorite Cloud Tools
Using Microsoft 365, Google Workspace, Salesforce, AWS, or Slack? CASB plugs into these platforms directly, using APIs or proxy-based methods, to apply your security policies without disrupting workflows.
- One Dashboard Control (Multi-Tenant Management)
If you manage multiple departments or clients, especially as an MSSP, CASB makes your life easier. You get one centralized dashboard to apply consistent policies, track activity, and generate reports across every tenant.
- Audit-Ready Reports
CASB automatically logs user activity, generates compliance dashboards, and keeps everything organized for frameworks like HIPAA, PCI-DSS, SOC 2, or GDPR. Saves you hours and a whole lot of stress.
How to Choose a CASB? 3 Points to Keep in Mind
When it comes to adopting a Cloud Access Security Broker (CASB) solution, it's crucial to view it as just one piece of your broader cybersecurity puzzle. A CASB can be incredibly powerful, but its effectiveness depends on how well it fits with your existing security setup and meets your specific needs.
Here's how to choose the right CASB for your organization:
1. Match the Solution to Your Specific Needs
Every organization's cloud security needs are unique. To make sure you're choosing the best CASB, start by identifying your specific use cases. When evaluating potential CASB vendors, focus on those who specialize in the areas that matter most to you. Look for CASB vendors with proven expertise in your priority areas.
For example, if insider risk management is a key concern, check if CASB offers strong features in that category. This ensures that the CASB you choose has the right tools to handle your unique security challenges.
2. Assess the Vendor Landscape
To find the best fit, dive into media coverage and analyst reports. Look for CASB vendors with a solid track record of preventing breaches and effectively managing security events. Check testimonials and case studies from organizations similar to yours to see how these vendors have performed in real-world scenarios.
Be aware of potential limitations in the CASB you're considering. Some may excel in certain areas but fall short in others. If you have multiple use cases, ensure that the CASB can handle all of them without compromising on any front.
3. Test Before You Commit
A trial run can be a game-changer. Many CASB vendors offer the opportunity to pilot their solution before you make a full commitment. This trial period allows you to see how well the CASB cloud security integrates with your existing cloud infrastructure and whether it aligns with your company's resources and needs.
Why Choose miniOrange CASB?
miniOrange CASB is built with simplicity, power, and flexibility in mind. Whether you're a growing business or an enterprise with complex cloud environments, here's what makes it stand out:
- Quick & Guided Setup
Unlike many enterprise-grade tools, miniOrange CASB offers a fast and intuitive setup experience. From account sync to pre-built policy templates, everything is streamlined to reduce onboarding time.
- Granular Policies
Fine-tune exactly who can do what. Allow users to view files but block downloads, or permit uploads only from corporate devices or approved locations. Rules can be customized based on user, role, device, time, or geography.
- Threat Intelligence
miniOrange CASB integrates with multiple threat intelligence feeds and uses smart anomaly detection to identify suspicious behavior. Get proactive alerts before risks turn into real threats.
- Integration Across Clouds
Whether your team uses Google Workspace, Microsoft 365, Salesforce, Shopify, or Atlassian, miniOrange CASB connects with them all and enforces your policies without disrupting productivity.
- Custom Role-Based Access
Control access based on department, function, or user role. HR, developers, vendors, and interns can all get tailored access that matches their responsibilities.
- Detailed Reporting
Access real-time alerts, weekly summaries, and compliance dashboards, all formatted to meet the needs of both your IT team and external auditors.
- Flexible Pricing Options
miniOrange offers pricing plans that adapt to your business size and needs. Whether you're a startup or a multi-tenant enterprise, you'll get enterprise-grade security without overpaying.
- Personalized Custom Policies
Create policies that fit your exact workflows and compliance needs. You're not stuck with generic templates; miniOrange lets you define custom rules that align with your business model.
- Adaptive Restrictions
Apply restrictions that automatically adjust based on the situation. For instance, limit access when a user is on a public network or deny file downloads during non-business hours. Security adapts in real time without interrupting productivity.
How miniOrange CASB Helps?
miniOrange Cloud Access Security Broker (CASB) offers a one-stop solution to protect your organization’s cloud apps and data. As one of the leading CASB vendors, miniOrange provides CASB security capabilities like real-time threat detection, data encryption, and policy enforcement. The solution gives you deep visibility into user activities, precise control over data access, and strong protection against insider threats.
miniOrange CASB tools are designed to integrate seamlessly with your existing cloud services, like AWS, Google Workspace, and Office 365. Whether you need to prevent unauthorized access, manage shadow IT, or ensure compliance with data privacy regulations, miniOrange has you covered.
Examples & Use Cases of Cloud Access Security Broker (CASB)
Here are some actual cloud access security broker examples that make a big impact:
1. Finance: Blocking Personal Downloads
Fintech firms facing regulatory audits can use CASB security to prevent sensitive financial reports from being downloaded to personal laptops. The policy can apply only to non-corporate devices and be enforced within minutes.
2. Education: Student Data Privacy
Universities can implement CASB to protect student data on platforms like Zoom and Teams. With CASB, they can encrypt file transfers, restrict external sharing, and enable alerts for unauthorized logins from outside the campus network.
3. Healthcare: Detecting Unusual Behavior
Hospitals can use CASB to detect unusual activity, such as late-night data transfers to external drives. CASB’s behavior-based alerts can flag these anomalies. If a compromised account is identified, access can be locked before any data is leaked.
4. E-commerce: Controlled Access for Vendors
Online marketplaces with multiple vendors can use CASB to enable secure collaboration. Access tiers can be created so that external suppliers only view product images, without accessing inventory or financial data.
CASB vs DLP
| Feature | CASB (Cloud Access Security Broker) | DLP (Data Loss Prevention) |
|---|---|---|
| Definition | CASB acts like a security guard for cloud services, monitoring and controlling user activity in the cloud. | DLP prevents sensitive data from being leaked or mishandled from any given device in an organization. |
| Main Purpose | Ensures secure cloud usage by enforcing policies, monitoring activity, and providing visibility. | Protects sensitive data from being lost, stolen, or accessed improperly. |
| Focus Area | Cloud applications and data, including SaaS and IaaS platforms. | Data in transit, at rest, and during use across various environments. |
| Granular Controls | Offers detailed visibility and control over cloud-based activities and data sharing. | Focuses on safeguarding data by enforcing rules and preventing unauthorized access. |
| Use Case | Ideal for managing and securing cloud applications like Office 365, Salesforce, and AWS. | Perfect for protecting sensitive data such as personal information, financial records, and intellectual property. |
| Threat Detection | Detects suspicious activities and potential threats in cloud environments. | Identifies and responds to potential data breaches or leaks. |
Read more: CASB vs DLP
CASB vs SASE
| Feature | CASB (Cloud Access Security Broker) | SASE (Secure Access Service Edge) |
|---|---|---|
| Definition | Acts as a gatekeeper, ensuring that cloud applications are used securely. | A comprehensive framework that combines network security and WAN capabilities. |
| Primary Focus | Secures access to cloud applications and data. | Secures both cloud and on-premises access, blending security and networking. |
| Core Functions | • Visibility: Monitors cloud usage. • Control: Enforces policies. • Compliance: Ensures regulations are met. |
• Networking: Provides optimized network access. • Security: Combines multiple security functions. • Cloud Integration: Integrates with cloud services. |
| Security Capabilities | • Compliance • Threat Protection • Access Control |
• Firewall-as-a-Service (FWaaS) • Secure Web Gateway (SWG) • Zero Trust Network Access (ZTNA) |
| User Experience | Can introduce some complexity due to the need for integration with various cloud apps. | Streamlined user experience with integrated security and network services. |
| Best For | Organizations focused on securing cloud applications and data. | Companies seeking an all-in-one solution for secure access and optimized networking. |
CASB vs SIEM
| Feature | CASB (Cloud Access Security Broker) | SIEM (Security Information and Event Management) |
|---|---|---|
| Purpose | Protects cloud services by monitoring and controlling access, enforcing policies, and ensuring data security. | Collects, analyzes, and correlates security event data from various sources for real-time monitoring. |
| Focus Area | Cloud applications and data protection. | Overall IT infrastructure security, including network, systems, and applications. |
| Threat Detection | Detects threats related to cloud services, such as unauthorized access and data breaches. | Detects a wide range of threats by analyzing logs and events for suspicious patterns or anomalies. |
| Compliance | Helps ensure compliance with regulations and policies specific to cloud services. | Ensures compliance with broader IT security regulations by providing comprehensive logging and reporting. |
| Alerting | Provides alerts for cloud-specific issues such as risky user behavior or unauthorized data access. | Generates alerts based on detected security events and anomalies across the entire IT infrastructure. |
| Reporting | Delivers insights on cloud usage patterns, potential risks, and compliance status. | Produces detailed reports on security events, incident investigations, and compliance status. |
Summary
A Cloud Access Security Broker, or CASB acts as a gatekeeper between your organization and the cloud services you use. It watches over all the data going in and out, making sure everything stays secure.
miniOrange CASB comes as an ideal cloud security solution that helps protect against data breaches, cyber threats, and unauthorized access. It even ensures your organization complies with all the necessary regulations and policies.
Think of it as the all-in-one security tool that gives you peace of mind while you enjoy the flexibility of the cloud. Whether you're working from home, the office, or anywhere in between, CASB makes sure your data is locked up tight and only accessible to those who should have access.
Frequently Asked Questions
1. What is CASB in Cyber security?
CASB stands for Cloud Access Security Broker. CASB in cybersecurity means a policy enforcement point between users and cloud applications to protect data and ensure secure cloud access.
2. How do you choose a CASB?
Look for a solution that integrates easily with your existing apps, offers strong data protection policies, supports compliance, and provides intuitive visibility dashboards. Ease of setup and support also matter.
3. Who needs a CASB solution?
Any business that uses SaaS platforms like Google Workspace, Slack, Dropbox, Zoom, or Microsoft 365. Whether you’re a startup or a global enterprise, cloud security is a universal need.
4. Why is CASB important for modern businesses?
Cloud is the new normal, and traditional firewalls don’t offer protection beyond your on-premises network. CASB ensures your data stays protected, compliant, and under control wherever it goes.
5. Is CASB only for large enterprises?
Not at all. Small and medium businesses also benefit from CASB tools, especially if they use multiple SaaS tools or manage sensitive customer data.
6. Can CASB work with on-premises systems?
While CASB is designed for cloud environments, it can be part of a hybrid architecture by integrating with your identity provider or on-prem security tools.
Additional Resources
- Google Workspace CASB Integration | Cloud Security
- Atlassian CASB Integration for Enterprise Security
- Shopify Security with CASB Solutions
- Microsoft Office 365 CASB Integration | Enterprise Security
- Oracle CASB Integration for Secure Oracle Cloud Apps
- CASB vs DLP: Understanding the Differences
- Remote Work Security with CASB
- Hybrid Work Security | CASB Solution
- CASB Corporate Network Security






Leave a Comment