As businesses transition to the cloud, the need for strong security measures becomes more important than ever. Cloud adoption brings immense benefits like scalability and cost efficiency, but it also introduces critical challenges, particularly in security and compliance. According to a recent survey, 80% of companies have experienced at least one cloud security incident in the last year.
This is where the Cloud Access Security Broker (CASB) solution comes into play, providing organizations with the necessary tools to safeguard their cloud environments. Among the most powerful features of a CASB is its Auditing Feature, which provides businesses with real-time visibility into user activities across their cloud applications.
In this blog, we will explore the CASB Auditing feature in-depth, focusing on its core functionalities, benefits, use cases, and how it helps businesses stay ahead of security threats and compliance requirements.
What is CASB Auditing?
CASB auditing is a security feature that provides real-time insights into user activities within cloud applications. It records detailed logs of every action a user performs, including file access, uploads, downloads, data sharing, and other interactions within the cloud. These logs serve as an essential record for both security monitoring and compliance auditing.
The key strength of this feature is its ability to track all user actions in real-time, providing administrators with the ability to detect security issues, violations, or anomalies as soon as they occur. Whether it’s detecting unauthorized data access or ensuring that employees are following internal policies, CASB auditing makes it possible to stay one step ahead.
Why is Real-Time Monitoring Important?
Traditional security systems, like firewalls and antivirus software, typically focus on preventing attacks but may not monitor issues. This is where CASB auditing stands out—it allows organizations to proactively monitor and respond to suspicious activities as they unfold.
Here’s why real-time monitoring is essential:
1. Identify Abnormal Behavior
CASB security solution can detect irregular activities such as accessing sensitive files outside of normal working hours or downloading large volumes of data unexpectedly. By identifying these behaviors in real-time, security teams can take action before the activity escalates.
2. Better Threat Response
Real-time alerts enable teams to respond to potential threats quickly, helping prevent damage or data loss.
3. Continuous Security
Cloud environments are constantly changing, and threats evolve rapidly. Continuous monitoring ensures that organizations can adapt their security measures to meet emerging threats.
Key Benefits of CASB Auditing
CASB auditing offers several compelling advantages to organizations, especially when it comes to maintaining control over sensitive data in the cloud. Some of the primary benefits include:
- Better Security:
By monitoring user activities in real-time, CASB auditing helps identify abnormal or suspicious behavior that may indicate a security breach, such as unauthorized data sharing, file access, or abnormal login patterns. Detecting these anomalies early helps mitigate the risk of a breach. - Detailed Insights:
With CASB auditing, organizations gain granular insights into how cloud applications are being accessed and used. This visibility can help organizations understand which users are accessing specific data, from where, and under what circumstances. This data is crucial for identifying security gaps and improving overall security posture. - Active Risk Management:
Rather than waiting for a breach to occur, CASB auditing allows organizations to identify potential threats and vulnerabilities before they manifest. By monitoring cloud activity and user behavior, security teams can anticipate and address issues proactively. - Audit Readiness:
For organizations subject to compliance regulations, CASB auditing helps maintain detailed logs of user actions, making it easier to demonstrate adherence to industry standards. Pre-compiled logs and activity reports make it easy for businesses to prepare for audits, saving time and effort. - Insights on Security Triggers:
CASB auditing provides detailed insights into how often a security policy is invoked during user actions. This allows organizations to identify patterns of risky behavior, assess the effectiveness of their security policies, and make data-driven adjustments to enhance overall security posture.
Real-Life Example of CASB Auditing in Action
Consider a healthcare organization that manages sensitive patient records through a cloud-based system. With the CASB auditing feature, the organization can monitor user activity and detect potential security threats.
One day, the system flags an employee downloading an unusually high number of patient records. The security team investigated and discovered that the employee was trying to export the data to an unauthorized location. Thanks to CASB auditing, the incident was detected early, and appropriate action was taken before any data was leaked.
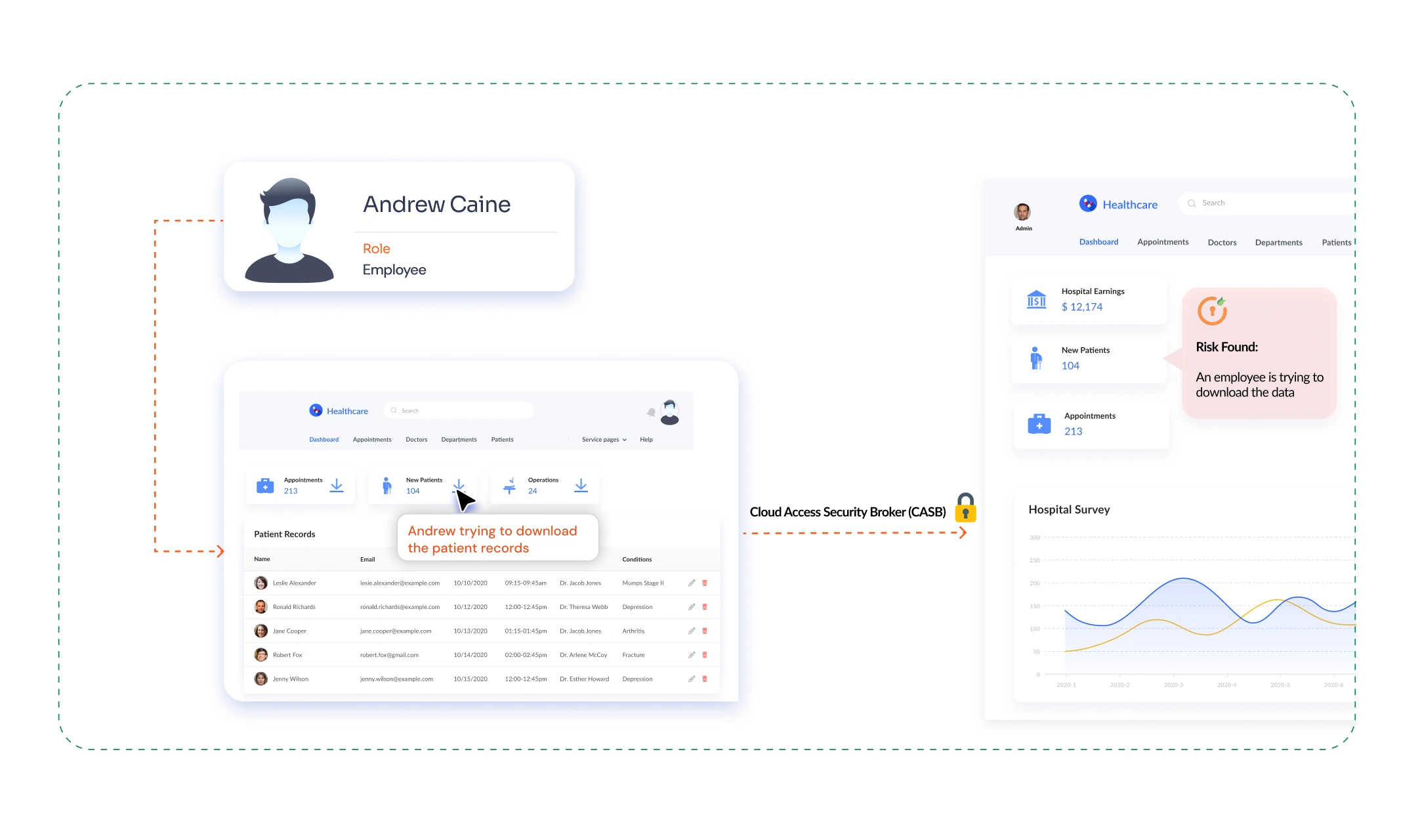
Implementing the CASB Auditing Feature in Your Organization
Adopting CASB auditing is an essential step toward enhancing your cloud security framework. When implementing CASB auditing, organizations should consider the following:
1. Choose the Right CASB Solution
Pick a solution like miniOrange CASB security that integrates seamlessly with your existing cloud applications and systems.
2. Customize Logs and Alerts
Tailor the logs to meet your organization’s specific security needs and define thresholds for alerts.
3. Training and Awareness
Educate your security team on how to review and respond to the logs generated by the CASB auditing tool.
4. Set Regular Audits
Even with continuous monitoring, scheduling regular internal audits ensures that your cloud security protocols are effective and up-to-date.
Use Case of CASB Auditing
- Tracking Sensitive Data Interactions
One of the most important applications of CASB auditing is its ability to track interactions with sensitive data. In industries like healthcare, finance, and legal services, maintaining control over sensitive data is a top priority. CASB auditing can log every instance when sensitive data, such as customer information or financial records, is accessed, downloaded, or shared. This helps organizations ensure that only authorized users are interacting with sensitive data, and any suspicious activity can be flagged immediately. For example, if an employee accesses confidential financial data without a valid reason, the system will alert security teams in real-time.
- Preparing for Compliance Audits
In addition to improving security, CASB auditing is a powerful tool for businesses that need to comply with regulations such as GDPR, HIPAA, and SOC 2. Compliance audits are a significant part of many organizations’ operational procedures, and CASB auditing ensures that companies are always audit-ready. CASB systems automatically generate logs of user activity, which can be compiled into comprehensive reports. These reports provide detailed insights into how data is being accessed and used, making it easy to demonstrate compliance to auditors. The ability to produce these reports on demand also streamlines the audit process, reducing stress and saving time.
- Detecting Insider Threats
Insider threats—whether intentional or unintentional—pose a significant risk to organizations. Employees or contractors with authorized access to cloud systems can potentially misuse their access to steal or leak sensitive data. CASB auditing helps mitigate insider threats by providing detailed visibility into user actions. If an employee starts accessing files they typically don’t interact with or attempts to download a large volume of sensitive data, CASB auditing will flag this as unusual behavior. This allows security teams to investigate the activity before it results in a breach or data leak.
Conclusion
CASB Auditing feature is a vital tool for modern organizations seeking to enhance their cloud security and compliance efforts. By providing real-time monitoring, detailed activity logs, and proactive risk management, CASB auditing empowers businesses to stay ahead of potential threats and meet regulatory requirements with ease. Whether you are preparing for an audit, tracking sensitive data interactions, or identifying insider threats, CASB auditing has you covered.
Ready to try the miniOrange CASB auditing solution? Contact us at info@xecurify.com to learn more.
Reference links
- What is Cloud Access Security Broker? CASB Solutions?
- CASB for Salesforce Data Security, Compliance, and User Visibility
- Cloud access security broker (CASB) solutions
- Google Workspace CASB Integration | Cloud Security
- Cloud access security broker (CASB) Integrations
- Microsoft Office 365 CASB Integration | Enterprise Security
- CASB Security for Salesforce Cloud Apps
- CASB Integration for Oracle Apps
- What are the 4 Pillars of CASB?
- Microsoft Office 365 CASB: An Overview
- Atlassian CASB Integration for Enterprise Security




Leave a Comment