Cybercrime is at an all-time high, and the numbers are alarming. By 2025, experts predict that the annual damage caused by these attacks can soar to around $10.5 trillion. With numbers like these, it’s clear organizations should not rely solely on traditional security measures to protect their online operations.
While tools like antivirus software, anti-malware, and firewalls have improved over the years, they're still limited to detecting known, file-based endpoint threats. Most importantly, traditional endpoint security tools can't detect or neutralize advanced threats like ransomware attacks, zero-day exploits, or other large-scale cyberattacks.
Endpoint Detection and Response (EDR) picks up where these traditional endpoint security solutions leave off. It provides the tools that security teams can use to discover, investigate, and, prevent suspected and emerging threats on their own.
This blog explores everything you need to know about EDR, including its importance, key capabilities, and how it can help safeguard your business.
Let’s dive in!
What is Endpoint Detection and Response (EDR)?
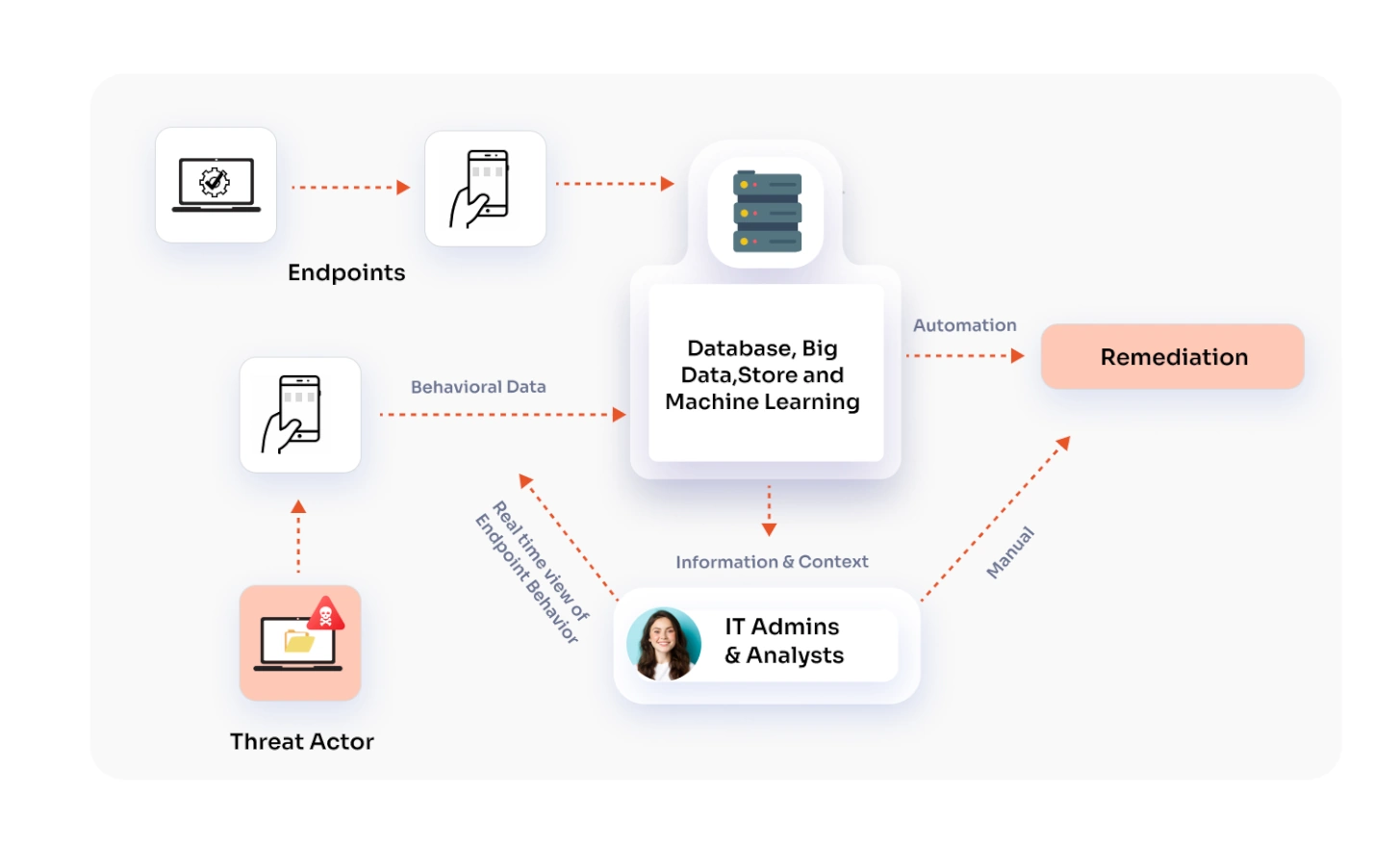
Endpoint Detection and Response (EDR) is a powerful cybersecurity solution designed to combat modern cyber threats that businesses face more often. It continuously detects threats across endpoint devices—such as laptops, servers, and mobile phones, investigating the entire lifecycle of the threat.
EDR is not just about detection; it’s also about understanding the full context of an attack. It provides insights into what happened, how it got in, where it has been, what it's doing now, and what to do about it. By containing the threat at the endpoint, EDR helps eliminate the threat before it can spread.
Importance of EDR: Why Businesses Must Use It
1. Real-Time Monitoring
Imagine having eyes on all your devices—laptops, servers, mobile phones—24/7. That’s exactly what EDR does. It keeps tabs on endpoint activities around the clock, ensuring no suspicious behavior slips through the cracks. It’s like having a security camera for your digital ecosystem.
2. Swift Incident Response
What if you could neutralize a cyber threat before it even had a chance to wreak havoc? EDR’s automated responses act fast—often within seconds—shutting down attacks before they cause any serious damage. This quick action keeps your business running smoothly without any hiccups.
3. Active Threat Detection
EDR equips security teams to actively eliminate potential weaknesses and threats before they can be exploited by hackers. This proactive approach is crucial, especially for defending against zero-day attacks.
Moreover, according to a study by the Ponemon Institute, organizations with EDR solutions cut their data breach costs by up to 45%. That’s a tangible benefit for businesses and their operational resilience.
Why Businesses Should Deploy EDR?
1. Keeping Up with Compliance
Whether it’s GDPR for customer data or HIPAA for healthcare, businesses are under constant pressure to meet strict security standards—or risk heavy fines.
How EDR helps:
Take a healthcare business for example. With all the sensitive patient data around, hackers can easily use it to launch attacks like ransomware. EDR ensures this information stays secure by providing advanced security measures, helping healthcare providers prove they’re compliant with regulations.
2. Securing the Remote Workforce
With remote work becoming the new norm, your security perimeter has stretched far beyond the office walls. Home networks and coffee shop Wi-Fi? They’re not exactly secure.
How EDR helps:
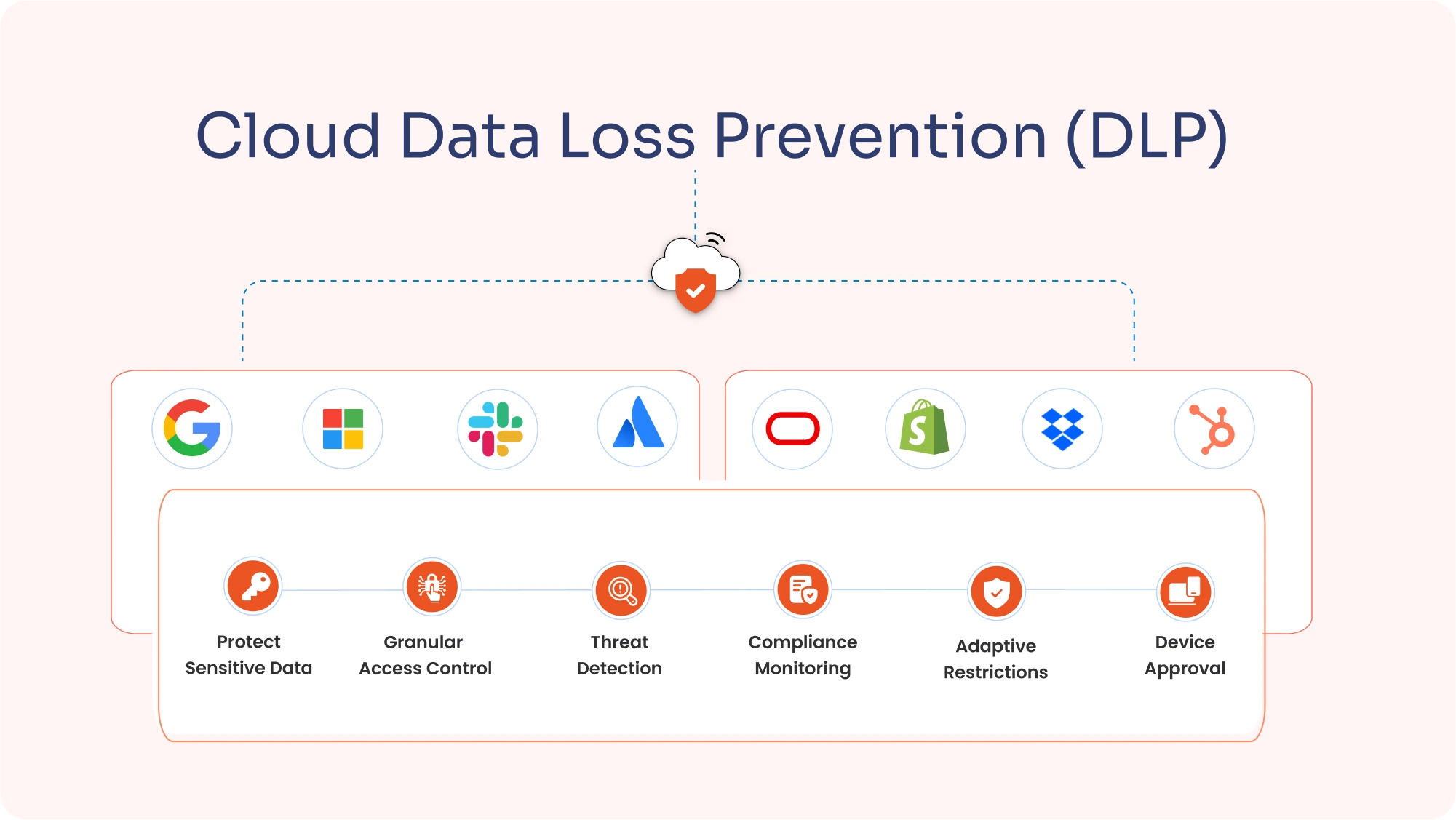
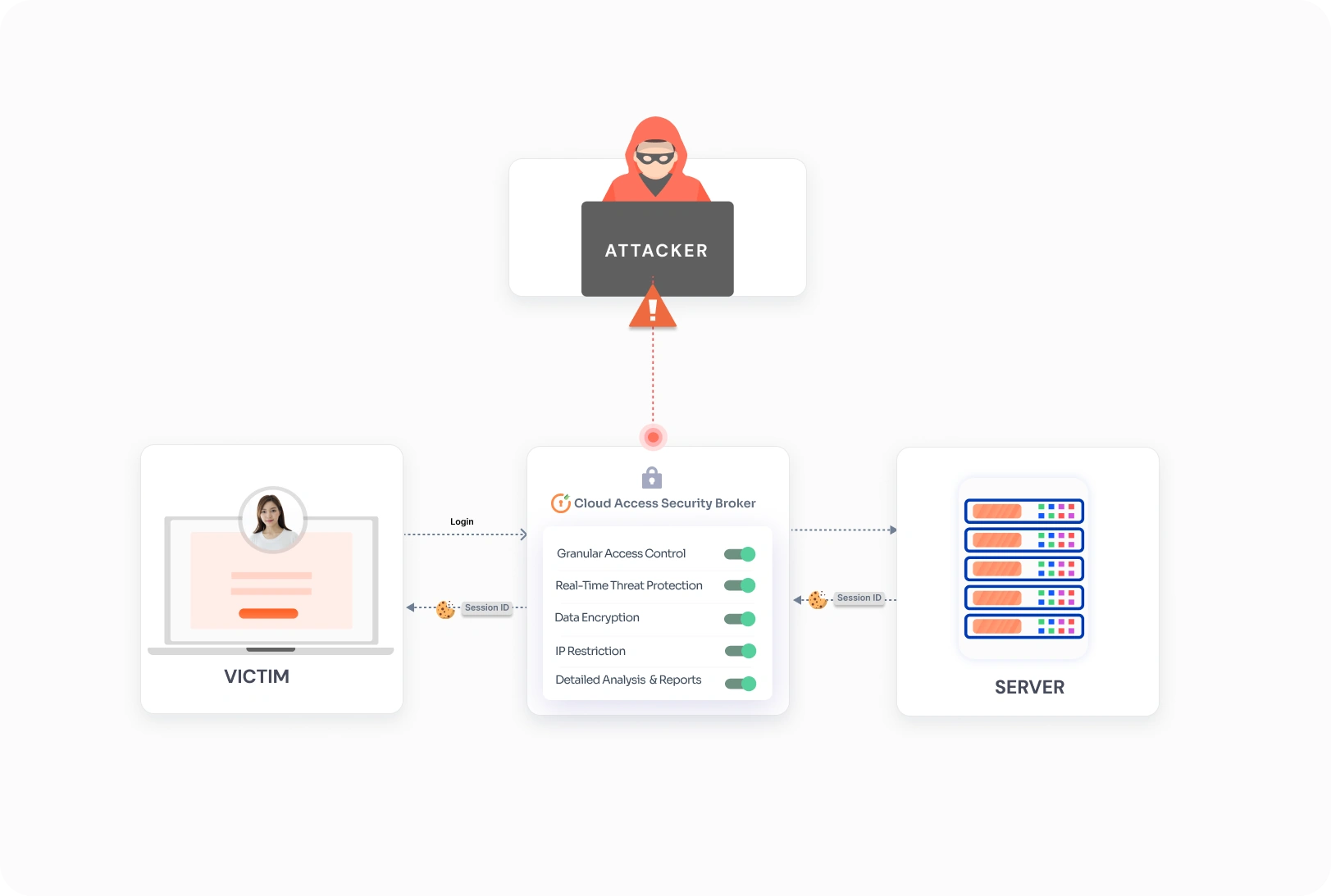
EDR ensures every device—whether it’s in your office or at an employee's kitchen table—is protected. It adds a consistent layer of security using solutions like Cloud Access Security Broker (CASB) security or Data Loss Prevention (DLP) to guard against threats like unsecured networks, keeping your data safe no matter where work happens.
Key Functions & Capabilities of EDR Security
- Reduce Security Risks
EDR helps find unknown devices, gadgets, and apps on your network, along with their vulnerabilities. It follows risk-based policies to manage these devices, control their communication, or apply virtual patches. - Stop Advanced Attacks
EDR detects and blocks threats like ransomware in real time. It also has anti-tampering features to stop malware from disabling its protection. - Find and Fix Threats Automatically
EDR uses smart behavior analysis to spot unusual activity, hunt for threats, and track signs of cyberattacks. It can also automate fixes using pre-designed response plans. - Work Faster and Smarter
EDR prioritizes serious threats, automates initial responses, and helps security teams act quickly. It detects threats in real time, contains attacks, and starts investigations right away.
Key Components Of EDR Security Solutions
1. Detection
Detection is where the battle begins. EDR continuously scans every file interacting with your endpoints. Sometimes, a file might seem harmless at first but later reveals malicious behavior. When that happens, your EDR raises a red flag, notifying your IT team.
What makes detection even more powerful is global cyber threat intelligence. EDR taps into vast databases of existing and evolving cyber threats, using AI to detect anything resembling hacker tools. It’s like having a vast library of criminal profiles to cross-reference at lightning speed.
2. Containment
Once a threat is detected, the next step is containment. Here’s where EDR isolates the problem, preventing it from spreading across your network. This could mean segmenting a part of the network or cutting off access to infected endpoints.
For example, in the case of ransomware, containment stops the threat from locking up more files or devices, giving you time to plan your next move.
3. Investigation
Containment buys you time for a deeper dive. Investigation is all about understanding what happened:
- How did the threat get in?
- What applications or data were affected?
- Did the malware replicate itself elsewhere?
This step isn’t just about solving the immediate problem. It’s about learning from the attack to strengthen your defenses.
4. Elimination
Finally, we get to elimination—the grand finale. Everything you’ve learned in the previous steps comes together to remove the threat completely.
Here’s the kicker: elimination isn’t just about deleting malware. It’s about figuring out where it came from and how it behaved, so you can prevent similar attacks in the future. Some advanced EDR systems even let you roll back infected endpoints to their pre-attack state. That means less downtime and fewer headaches for your team.
Simple Benefits of EDR
EDR plays a key role in keeping businesses secure by helping security teams respond quickly to cyberattacks. It improves how threats are detected, offers real-time ways to fight back, and strengthens an organization’s security to reduce data breaches and keep operations running smoothly. Here’s how EDR helps:
- Stops Security Breaches Early
EDR constantly monitors devices to catch threats, stops them from spreading, and automatically takes action like isolating threats, investigating, and fixing issues. - Finds Hidden Threats
Using advanced tools like machine learning and behavior analysis, EDR detects complex attacks that regular antivirus programs might miss. - Provides Useful Data
EDR gives security teams detailed insights into what’s happening on devices, including logs and forensic data, to better understand and respond to threats. - Automates Threat Responses
When a threat is detected, EDR can automatically isolate infected devices, block harmful processes, and remove malware, making the response faster and more efficient. - Reduces Vulnerabilities
With tools to hunt for risks, EDR identifies weak spots in your network before hackers can take advantage of them. - Helps Meet Security Rules
EDR provides detailed reports and logs to show compliance with industry standards and regulations, proving proper security actions were taken. - Prepares for Future Attacks
After an attack, EDR analyzes how it happened and shares threat intelligence to strengthen defenses and prevent similar issues.
In short, EDR keeps businesses safe by detecting, stopping, and preventing cyberattacks while helping teams stay compliant and prepared for the future.
How Does EDR Work?
Endpoint Detection and Response (EDR) tools monitor devices like computers and servers to quickly spot and respond to cyber threats. Here’s a simple breakdown of how they work:
- Constant Monitoring
EDR installs software on each device to keep track of its activities. This software uses advanced security tools like CASB, MDM, and DLP to analyze behavior and identify anything unusual. It logs important actions, like file access or software use, and ensures security teams can see all devices and users in real-time. - Collecting and Sharing Data
The software sends the activity data from each device to a central system, either in the cloud or on-site. This includes things like login attempts, app usage, and other events. The system stores this data, so if behavior changes, EDR can act immediately. - Finding Problems
EDR analyzes the collected data to detect anything suspicious, such as malicious files or unusual behavior. When a problem is found, the system alerts the security team and starts investigating how the threat got in. - Taking Action
When EDR identifies a potential threat, it sends alerts to security teams and, if necessary, takes immediate action, like isolating a device or part of the network. This containment prevents the threat from spreading. Once the issue is investigated, EDR removes the threat and restores the affected devices. - Keeping Records
EDR keeps detailed records of past activities and threats. These logs help security teams investigate incidents and understand broader attack patterns. This historical data is useful for preventing future issues.
Types of EDR Deployments
When it comes to protecting your organization’s endpoints, choosing the right deployment model for your Endpoint Detection and Response (EDR) solution is crucial. Each deployment type offers distinct advantages, so let’s dive into the options and explore which one might be the best fit for your needs.
1. On-Premises Deployment
What It Is:
This deployment model involves installing and managing the EDR solution directly within your organization’s own data centers.
Best For:
Companies with strict data privacy regulations, like those in healthcare or finance, or organizations with legacy infrastructure.
What’s Great About It:
- Full control over data storage and processing.
- Ability to customize configurations to fit your business needs.
- You can manage and upgrade the system in-house, offering total control.
Challenges to Consider:
- High upfront costs for hardware, software, and skilled staff.
- Potential scalability issues as your company grows.
2. Managed EDR Services
What It Is:
With this deployment, you outsource the management of your EDR solution to a Managed Security Service Provider (MSSP).
Best For:
Organizations with limited cybersecurity expertise or those looking to offload some of the operational responsibilities.
What’s Great About It:
- 24/7 monitoring and incident response from experienced security professionals.
- Access to advanced threat intelligence and tools.
- Takes the load off your internal IT team.
Challenges to Consider:
- You rely on a third party for timely responses, which can affect your control.
- Lack of full visibility into the provider’s processes and actions.
Choosing the Right EDR Solution
Understanding what makes a good Endpoint Detection and Response (EDR) solution is crucial to finding one that works best for your needs. The right EDR should offer strong protection with minimal effort and cost, helping your security team stay effective without being overwhelmed. Here are six key features to look for in an EDR solution:
- Endpoint Visibility: Real-time monitoring of all your devices is essential to spot and stop attackers before they can do damage. This capability allows you to see what’s happening as it happens.
- Threat Database: A good EDR collects and analyzes large amounts of data from devices. This enables the detection of potential attacks through advanced analysis methods.
- Behavioral Protection: Instead of relying solely on known attack patterns (signatures), seek an EDR that monitors unusual behaviors (indicators of attack). This proactive approach helps alert you to threats before they cause harm.
- Insight and Intelligence: Your EDR should include threat intelligence to provide additional details, such as identifying potential attackers and their methods. This empowers you to respond more effectively.
- Fast Response: The faster your EDR can detect and handle issues, the less damage attackers can inflict. A quick response minimizes downtime and speeds up recovery.
- Cloud-Based Solution: Cloud-based EDR tools don’t slow down your devices and can handle tasks like searching, analyzing, and investigating threats in real time without interruptions.
Conclusion
Endpoint Detection and Response (EDR) is no longer optional; it’s a necessity for any business serious about cybersecurity. With its advanced detection, real-time monitoring, and automated responses, EDR ensures your organization stays one step ahead of cybercriminals. By choosing an EDR solution, you’re not just investing in a tool—you’re safeguarding your business’s future.
Want to take control of your endpoint security! Contact us at info@xecurify.com to learn more about EDR solutions and safeguard your organization against advanced cyber threats.
Reference links
Author

Leave a Comment