A shocking 80% of security breaches involve privileged credentials. Yet, the crucial security measure, Privileged Access Management (PAM), is often overlooked, leaving sensitive data at risk.
Understanding PAM is not just beneficial, but essential for a strong cybersecurity strategy. It strengthens privileged accounts, prime targets for cyber threats. As these threats grow in complexity, PAM has become a business necessity.
This isn’t just about protecting your organization; it’s about safeguarding your business’s future. In 2024, the average cost of a data breach globally is estimated to be $4.45 million, a 2.3% increase from 2023, with the global cost of cyberattacks expected to rise to $9.5 trillion. The stakes are increasing highlighting the need for robust cybersecurity measures such as PAM and IAM
In this article, we explore the intricacies of privileged access management, such as what is PAM, its solutions, implementation, best practices, use cases, governance, and compliance.
What is Privileged Access Management (PAM)
Privileged Access Management (PAM) is a cybersecurity approach that focuses on controlling, monitoring, securing, and auditing the activities of privileged users who have access to an organization’s sensitive information within an IT environment. PAM ensures that only authorized users can access this critical information.
Privileged Access Management, PAM features include:
- Access Control: PAM ensures that only authorized individuals have access to critical systems and data.
- Monitoring: It keeps track of all actions performed by privileged accounts to detect any suspicious activities.
- Account Management: PAM helps in managing the lifecycle of privileged accounts, including creation, usage, and deletion.
- Security Enhancement: By limiting privileged access, PAM reduces the attack surface and enhances overall security.
- Compliance: PAM helps organizations meet regulatory requirements related to data security and privacy.
To understand this PAM definition, let us take a simple example. Imagine a company with a secure office building where only certain employees have keys to access sensitive areas. Privileged Access Management (PAM) works similarly in the digital sphere, controlling and monitoring who has digital “keys” (privileged accounts) to access critical systems and data. Now, the finance department of the same company is willing to secure its sensitive data. It uses PAM to manage access to its customer database, ensuring only senior IT administrators can view and modify sensitive information while granting temporary access to others as needed.
The main purpose of a PAM solution is to regulate and monitor privileged access, ensuring users have only the specific access needed to perform their tasks, thereby enhancing cybersecurity. This helps protect against data breaches by restricting privileged users from erasing their logs when they log in, as they have the right to do so.
PAM works on the Principle of Least Privilege (PoLP) framework, which ensures that users are granted only the specific access they need to perform their tasks.
In addition to enforcing PoLP, a PAM solution can also restrict access rights and permissions to only those individuals who are authorized for specific applications, systems, and IoT devices. This capability further strengthens an organization’s security posture by reducing the attack surface.
Privileged management is a subset of the broader Identity and Access Management (IAM) framework. While both PAM and IAM provide granular access control, auditability, and visibility over all credentials and privileges, PAM specifically focuses on managing and securing privileged access.
In essence, PAM is about giving the right access to the right people at the right time, and keeping a close eye on how that access is used. It’s a key component of a robust cybersecurity strategy.
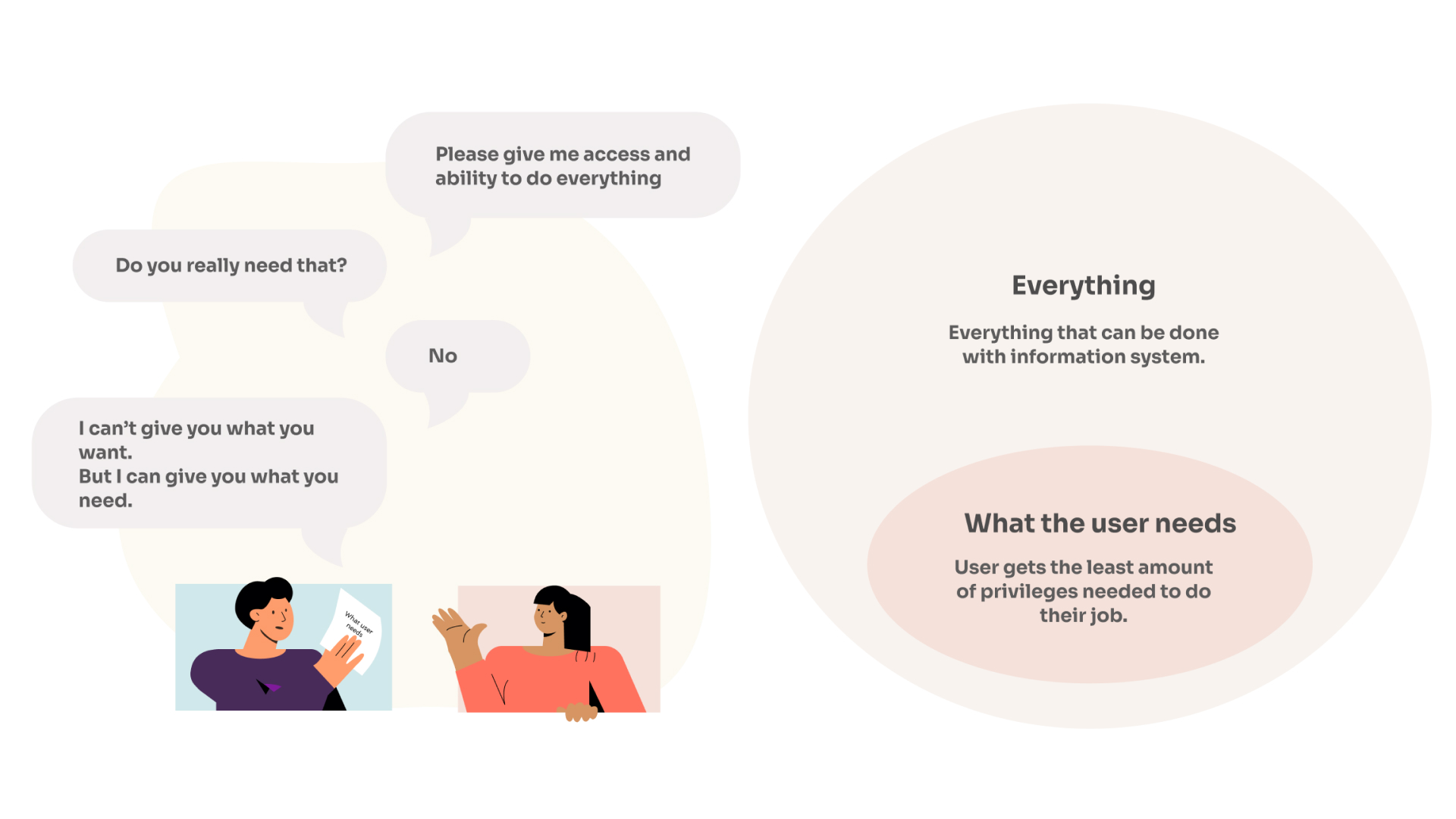
The Principle of Least Privilege (PoLP) in Privileged Access Management (PAM) is a computer security concept in which a user is given the bare minimum levels of access necessary to complete their job functions. This principle is used to reduce the risk of unauthorized or accidental changes, and it helps protect systems from malicious activities. It's a key strategy in a robust cybersecurity framework.
The Key Role of PAM in Cybersecurity and IT
Privileged Access Management (PAM) in cybersecurity and IT is a cornerstone of a strong cybersecurity posture. It helps by providing a protective layer over sensitive data and systems. Its major role includes:
- Preventing Data Breaches: By controlling and monitoring privileged access, PAM can prevent unauthorized access and potential data breaches.
- Mitigating Insider Threats: PAM helps mitigate risks associated with insider threats by limiting the access rights of users.
- Regulatory Compliance: PAM assists organizations in meeting various regulatory compliance requirements by providing audit trails and reports.
- Efficient Management: PAM simplifies the management of privileged accounts, reducing the workload of IT teams.
- Incident Response: In case of a security incident, PAM provides detailed activity logs that can aid in the investigation.
Introduction to Privileges and Privileged Accounts
“86% of large enterprise organizations either do not know or have grossly underestimated the magnitude of their privileged account security problem.”
This creates a need to understand what privileges are, how they are defined, what are privileged accounts, why they are being under the radar for hackers, types of privileged accounts, and the risks associated with their misuse.
What are Privileges, and How are They Defined?
In the context of Privileged Access Management (PAM), privileges refer to special access rights or permissions granted to users, applications, or systems that allow them to perform tasks beyond those of a standard user. These tasks often include accessing critical systems, sensitive data, and administrative functionalities.
Privileges are defined based on the level of access required to perform specific functions. For example:
- Super User Accounts: These accounts have the highest level of access, allowing full control over systems and applications.
- Domain Administrative Accounts: These provide administrative access across all workstations and servers within a network domain.
- Local Administrative Accounts: These allow users to make changes to their local machines or devices.
- Application Accounts: These are used by applications to interact with the operating system or other applications.
- Service Accounts: These are used by services to perform automated tasks.
PAM solutions help manage and monitor these privileges to ensure they are used appropriately and securely, reducing the risk of unauthorized access and potential security breaches.
What are Privileged Accounts?
Privileged accounts are special accounts in an organization’s IT infrastructure that have more permissions than regular user accounts. They are like the “master keys” of a system, giving the user the ability to access and control almost everything.
About privileged accounts:
- IT professionals and administrators use them to manage the system, network, and data.
- They can access all files, directories, and resources without any restrictions.
- They can make major changes in the network, like installing software, modifying the system, and managing users.
- Because they have so much power, they can be a big security risk. If someone misuses a privileged account, they could cause a lot of damage. So, these accounts need strong security measures to prevent breaches.
- Our solution helps to manage these privileged accounts securely and provides the necessary controls and monitoring to protect your important assets.
Why Do Hackers Target Privileged Accounts?
Privileged accounts are targeted by hackers because they provide administrative access to an organization's critical systems and data. With these accounts, hackers can bypass security measures, alter system configurations, access sensitive data, and potentially cause significant damage. In essence, privileged accounts are the 'keys to the kingdom', making them a prime target for cybercriminals. It's why Privileged Access Management (PAM) solutions, like those provided by miniOrange, are essential for protecting these high-value targets.
What are the Types of Privileged Accounts?
Privileged accounts provide high-level access to IT systems. Identifying these account types is important for effective Privileged Access Management (PAM). Here are some of the types of privileged accounts:

- Admin Account (Root/Administrator Accounts): These accounts provide complete control over systems and servers, typically used by IT administrators for high-level tasks.
- Domain Accounts: These accounts manage access across networked resources, providing permissions specific to network domains.
- Database (DBA) Accounts: These accounts offer comprehensive access to manage and maintain databases, ensuring data integrity and security.
- Network Accounts: These accounts facilitate the management of network resources and infrastructure, which is crucial for maintaining network health and security.
- Application Accounts: These accounts are tailored for specific applications, managing application settings and user interactions within defined parameters.
- Emergency Accounts (Break Glass): Reserved for crises, these accounts provide immediate access when regular administrative channels are unavailable.
- Privileged User Accounts: Designed for users who need elevated access for specific tasks, blending user flexibility with control.
- Service Accounts: These accounts support the operation of applications and services, running under specific credentials to perform tasks automatically.
- Application Service Accounts: Similar to service accounts but specifically for applications, enabling automated processes and tasks within applications.
- System Accounts: Low-level accounts used by the operating system to manage core system processes are essential for system stability and security.
The Threat of Misuse of Privileged Accounts
Privileged accounts are user accounts that have more permissions than regular users. They can install software, change system settings, access sensitive data, and perform other high-level tasks.
The misuse of privileged accounts refers to situations where these powerful accounts are misused. This can happen in several ways.
- Insider Threats: An employee with access to a privileged account might use it for malicious purposes, such as stealing sensitive data or disrupting system operations.
- External Attacks: Hackers often target privileged accounts because they provide the highest level of access to a system. If a hacker gains access to a privileged account, they can cause significant damage.
- Accidental Misuse: Even well-intentioned employees can cause problems if they accidentally misuse a PAM account. For example, they might unintentionally change a critical setting that causes a system outage.
The threat of misuse of privileged accounts is a serious concern in cybersecurity. Organizations need to monitor the use of privileged accounts and implement controls to prevent misuse. This can include measures like least privilege policies, regular audits, and advanced threat detection tools.
Why Do Organizations Need PAM Solutions?
Organizations need to evaluate the magnitude of security breaches on privileged accounts and consider the benefits of PAM software solutions that help protect them. Businesses must compare their benefits against popular cybersecurity options like IAM and PIM. Here is a detailed breakdown of it:
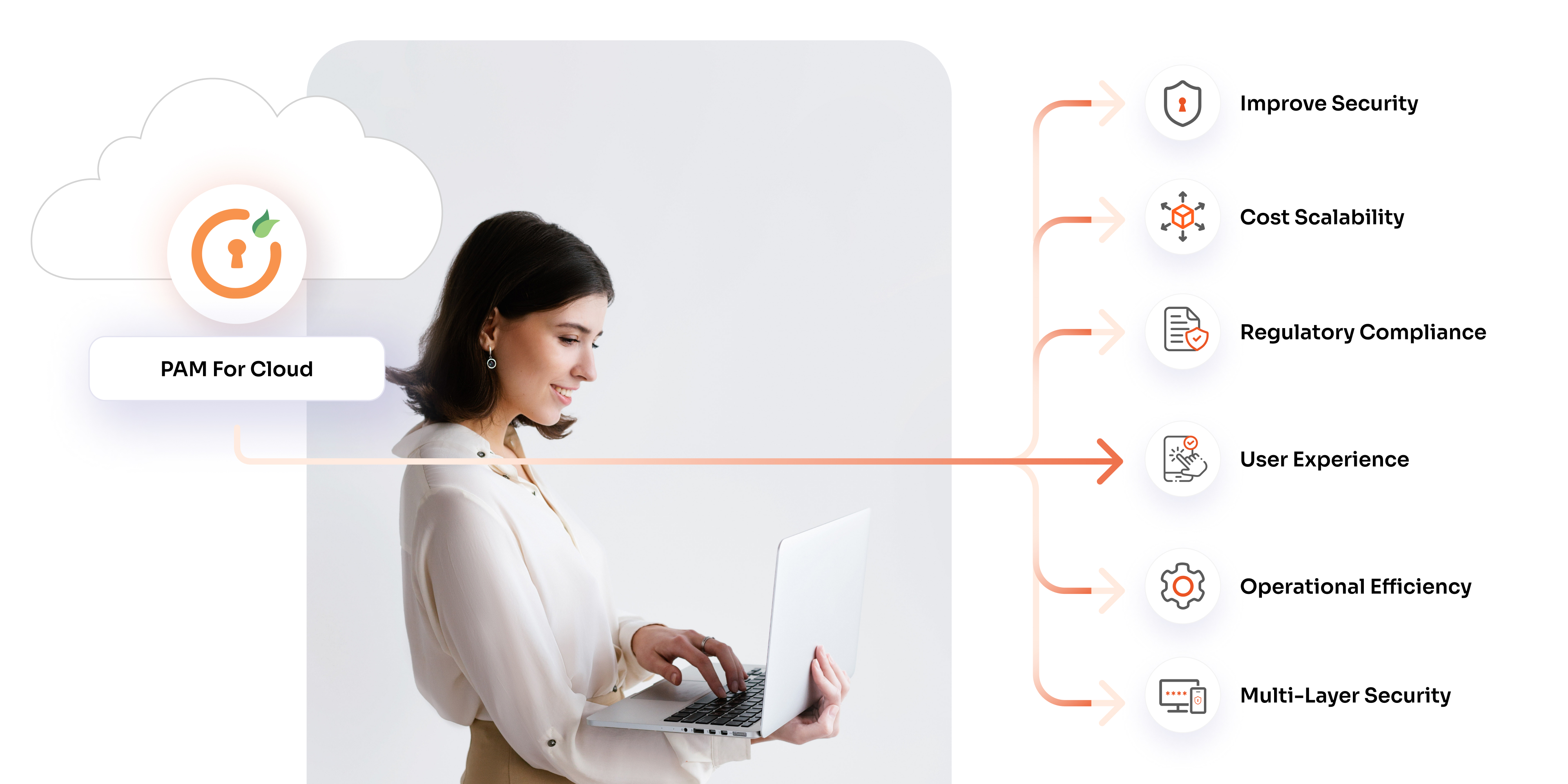
What are the Benefits of PAM Security Solutions for Enterprises?
Privileged user access management offers several benefits for enterprises:
- Superior Data Security: PAM improves data security by reducing system vulnerabilities. It restricts the ability of employees to install potentially harmful programs or inadvertently create network vulnerabilities.
- Better Control Over Access and Accounts: PAM allows only administrators to control employee accounts, privileges, and access. This ensures better security and allows for the auditing of administrative actions.
- Improved Regulatory Compliance: PAM helps organizations adhere to changing regulations, thereby avoiding fines and penalties. It reduces the chances of regulatory compliance issues by limiting employee access to only what they strictly need.
- Reduction in Self-Service IT: PAM prevents employees from installing third-party solutions on their own, which could compromise the network. Instead, they need to go through administrators for help.
- Lower Likelihood of Insider Threats: By limiting privileged access, PAM reduces the risk of insider threats.
- Operational Efficiency: PAM solutions enhance operational efficiency by automating the user lifecycle, including account creation, provisioning, and de-provisioning.
- Scalability: PAM solutions can scale with the growth of your business, providing security for an increasing number of users and devices.
- Better User Experience: PAM solutions can offer a better user experience by providing just-in-time access to critical resources.
- Visibility and Prevention of Privilege Abuse: PAM solutions provide complete visibility into your entire network, helping to prevent privilege abuse.
miniOrange is at the forefront of providing compliant PAM solutions for businesses. These include PAM solutions for monitoring, recording, controlling privileged sessions, password protection, governance and compliance, limited-time access, access promotion and demotion, endpoint protection, and more.
PAM Solutions
A trusted PAM solution provides multiple offerings within its suite of products. For instance, depending on the use cases of a business, they provide password vault and rotation, session monitoring and control, PASM, PEDM, JIT, agentless PAM, and EPM

Password Vault and Rotation
Password vaulting, also known as password management, is the practice of securely storing and managing credentials in a centralized system. It involves storing sensitive login credentials, like usernames and passwords, in an encrypted format within a vault. This approach enhances security by eliminating the need for users to remember multiple passwords and promoting the use of strong and complex passwords. It provides a centralized repository for managing and retrieving passwords, ensuring that they are securely stored and easily accessible when needed.
Password Rotation is a part of Password Management that resets a user's password on a predefined schedule or each time they access IT resources. It periodically resets passwords to limit their lifespan and reduce the window of opportunity for potential attacks. The passwords are centrally stored in an encrypted vault and automatically fetch the required credentials from the vault for accessing resources and password rotation. This credential management process enhances security and helps protect sensitive information. Together, these two features form a vital part of Privileged Access Management (PAM), enhancing overall security and compliance within an organization.
Session Monitor and Control
Session Monitor and Control allows real-time monitoring of the activities of privileged users. It records all the actions performed during a privileged session for audit. This includes command logs, video recordings, and more. It acts like a CCTV system for your IT infrastructure.
Controlling the session of a privileged user allows administrators to intervene if necessary. For example, if an administrator notices a user performing an unauthorized action, they can immediately terminate the session to prevent any potential damage.
This feature is crucial for maintaining security in an organization, as it helps to ensure that privileged access is used appropriately and provides a way to trace back actions if an issue arises. It’s a bit like having a supervisor in a factory watching over the work, ready to step in if something goes wrong.
Privileged Account and Session Management (PASM)
PASM is a part of Privileged Access Management (PAM) that focuses on privileged account monitoring and management for compliance, security, and data integrity purposes. It covers accounts that, by design, run on elevated privileges—administrative, system, and operational accounts.
PASM is the answer to the question, “Who watches the watchers?”. Privileged accounts are vital cogs in a company’s digital ecosystem, ensuring e-business continuity and operational readiness and safeguarding assets and resources against insider threats and malicious actors. PASM applies to privileged accounts, while PAM applies to ‘underprivileged’ accounts (non-administrative accounts).
Besides admin accounts, we have system-type accounts (i.e., user-type accounts that are automatically generated by your OS during or after the installation process ends; they grant you system-wide access), service accounts, app accounts, emergency accounts, and more.
PASM tools come with an encrypted vault that allows IT teams and other administrative users to store and manage privileged identities, such as user accounts, passwords, SSH keys, PKI certificates, and other authentication data.
PASM tools offer robust controls, such as a secure and dynamic vault to store and manage credentials, certificates, files, and keys; request-release workflows for validating and approving password access requests; role-based access provisioning for administrative privileges; and real-time monitoring and auditing of password-related user activities.
The primary purpose of any PASM solution is to monitor and protect privileged user accounts and sessions, which helps IT teams track, control, record, and audit access to critical information and endpoints.
PASM is a part of the privileged access management tools cluster that provides users with administrative access to critical accounts and business-sensitive endpoints, such as data centers, databases, and applications, via remote sessions.
Privilege Elevation and Delegation Management (PEDM)
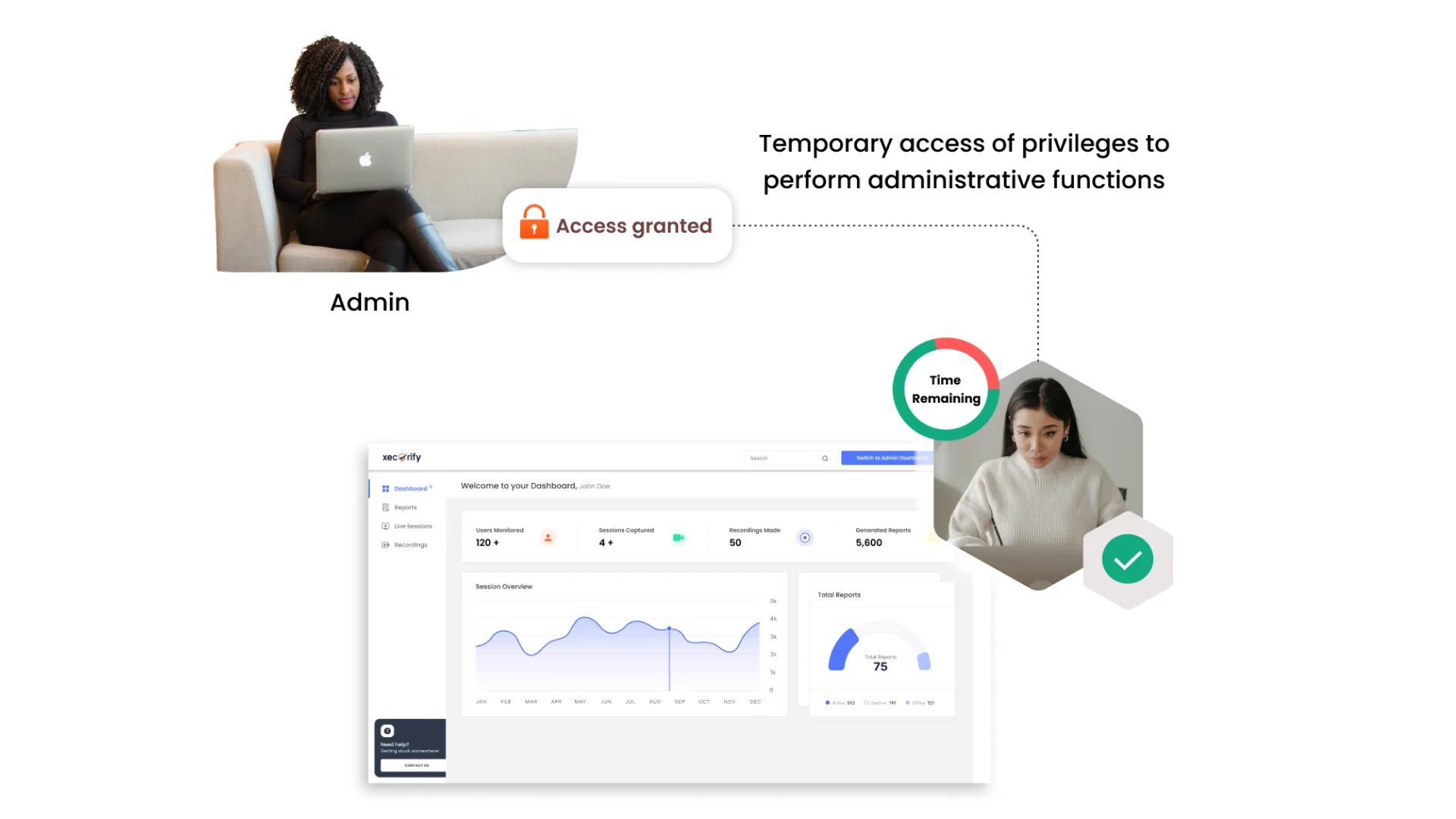
What is Privileged Elevation and Delegation Management (PEDM)?
Privilege Elevation and Delegation Management (PEDM) is a security approach that grants users temporary access to higher-level privileges or delegates specific tasks while maintaining security and adhering to the principle of least privilege (PoLP). Elevated privilege is a key feature of PEDM.
How does PEDM work?
Privileged elevation and delegation management, the PEDM solution, operates by providing time-limited access to sensitive data or systems based on validated needs. When users require elevated privileges to access critical systems, they submit a request to administrators. This request is carefully reviewed, and if considered necessary, elevation privileges are granted temporarily.
Key Components of PEDM:
- Authorization: Verifies user identities and determines the appropriate level of access and resources available to them.
- Privilege Elevation: Allows for temporary, controlled access for tasks requiring higher privileges.
- Delegation: Enables specific individuals to perform certain administrative tasks without full administrative rights.
- Access Reviews and Auditing: Regular reviews ensure that privileges are necessary and appropriate, with auditing providing a detailed account of access patterns.
miniOrange's PEDM
miniOrange’s PEDM lets you elevate and delegate access effortlessly while customizing and monitoring access levels in real time. It helps you stay regulatory-compliant with detailed audit reports and ensures secure access using password vaults based on the principle of the least privilege (PoLP).
Just in time (JIT)
Just-in-Time (JIT) Privileged Access Management (PAM) is a security approach that grants temporary access to privileged user accounts to utilize resources for a limited duration. This access is granted as needed and revoked upon task completion, reducing the attack surface.
Features of JIT PAM access:
- Limited on-demand access: Access is based on roles, adhering to the Principle of Least Privilege (PoLP).
- Granular privileges: Unlike continuous "always-on" access, JIT access offers specific, granular privileges over some time only.
- Temporary Elevation: It involves granting enhanced permissions to a process on an as-needed basis.
- Ephemeral Accounts: These are temporary accounts or zero-standing privilege accounts. These accounts are created based on specific needs, sometimes called "one-time" accounts.
This approach aligns with the principles of zero trust standing privileges and is often implemented as part of Identity Access Management (IAM) and Privileged Access Management (PAM) strategies. Just-in-time can be provided for network access control with the help of compliant just-in-time administration through JIT access requests. It ensures that privileged access is strictly controlled and limited to authorized individuals only when necessary.
Agentless PAM
Agentless PAM is a security solution that allows organizations to manage, monitor, and control privileged access without installing software agents on their target systems. It simplifies implementation while saving time and resources. This ensures scalability and helps boost cloud security.
- Hassle-Free Deployment: The solution eliminates the need for installing software agents on each endpoint, streamlining deployment and saving valuable time and resources.
- Reduced Risks: By eliminating the need for PAM agents, organizations can mitigate risks associated with agent vulnerabilities, ensuring a more secure privileged access management environment.
- Scalability and Reduced System Impact: This agentless approach enhances scalability, allowing organizations to adapt seamlessly to changing infrastructures. It also reduces system impact, avoiding potential interoperability issues associated with multiple agents.
- Browser Compatibility: The solution is compatible with various web browsers, ensuring flexibility and compatibility for end-users.
- Clientless Access: Users can access privileged resources directly via browser, providing enhanced in-browser user convenience and a seamless experience.
Agentless PAM is an efficient and effective choice for modern cloud environments, offering a streamlined approach to managing and securing privileged access.
Endpoint Privilege Management (EPM)
Endpoint Privilege Management (EPM) is a security solution that focuses on managing user privileges and restricting unauthorized access. It ensures that users receive only the necessary permissions, while unauthorized applications are either restricted or blocked.
Features of PAM EPM include:
- Least Privilege Principle (POLP): This principle removes unnecessary admin privileges, ensuring users have only the required level of access.
- Total Security for Windows, Mac, Linux & Unix: EPM specializes in privilege management for these operating systems. It removes local admin rights and applies the least privilege principles.
- Remove Local Admin Rights: EPM improves user experience and IT efficiency by removing local admin rights. It uses policy-based controls for easy privilege management.
- Enforce Least Privilege: EPM crafts precise, conditional policies for varying user groups by assessing the context and specifics of applications and operations.
EPM reduces endpoint risks through the process of least privilege and application control, protecting desktops, laptops, and servers from being compromised. It's a foundational tool for strengthening endpoint defenses against attacks exploiting privileged access.
AI in PAM: A Synergy for Privilege Security
The use of artificial intelligence techniques to enhance the capabilities of PAM solutions has been widely tested with success. For example, AI can be used to analyze user behavior and detect anomalies, which can help identify potential security threats. It can also automate routine PAM tasks, thereby improving efficiency and reducing the risk of human error.
AI can significantly enhance Privileged Access Management (PAM) in several ways:
- Proactive Anomaly Detection: AI’s ability to analyze user behavior patterns and detect anomalies is a cornerstone of AI security. Deviations from usual patterns could indicate potential security threats, such as privilege escalation or privileged access abuse. For instance, if a user who typically works 9–5 suddenly starts accessing sensitive systems at 2 am, AI can flag this as suspicious activity.
- Automated Responses: AI’s capacity for automated responses is significant in the face of potential threats. After detection, AI can take appropriate actions, such as alerting the security team, blocking access, or even triggering multifactor authentication for further verification.
- Risk Scoring: AI can assign risk scores based on user behavior and access patterns. Higher risk scores can trigger additional security measures, ensuring that high-risk users or actions do not compromise the system.
- Predictive Analytics: By analyzing historical data, AI can predict potential security threats before they occur. This predictive analysis allows organizations to proactively address vulnerabilities and strengthen their security posture.
- Efficiency and Scalability: AI can automate routine PAM tasks, such as provisioning and de-provisioning user access. This not only improves efficiency but also allows the PAM solution to scale as the organization grows.
- Continuous Learning: AI models learn continuously from new data. This means the more data they process, the better they become at detecting threats and protecting the system.
By integrating AI with PAM, organizations can create a more robust, efficient, and proactive cybersecurity strategy. It’s a powerful combination that can significantly enhance an organization’s ability to protect its critical resources. This AI-Powered Privileged Access Management is a testament to the power of AI algorithms and generative AI in enhancing data privilege and AI tool access.
In the era of AI-driven Identity and Access Management (IAM) and AI-driven Identity Governance and Administration (IGA), the role of AI in PAM is becoming increasingly important. From authentication, authorization, administration, and auditing to advanced threat protection and real-time risk mitigation, AI is revolutionizing the way we approach cybersecurity.
PAM vs. IAM vs. PIM: Comparing PAM with Leading Identity Security Solutions
PAM vs. IAM
| Aspect | Identity and Access Management (IAM) | Privileged Access Management (PAM) |
|---|---|---|
| Definition | IAM controls and manages user access across an organization. | PAM is a subset of IAM that focuses on managing access to critical resources and services. |
| Validation | IAM is based on credentials. | PAM is based on resource-access validation using attributes. |
| Scope | IAM broadly protects against data loss and unauthorized access. | PAM is focused on specific highly sensitive or privileged assets and information. |
| Users | IAM addresses all users. | PAM addresses privileged users. |
| Role | IAM enables policy automation, reduces the risk of data loss and unauthorized access, and facilitates user provisioning, de-provisioning, and onboarding. | PAM streamlines access management processes, minimizes administrative overhead, improves cybersecurity protection, and helps meet compliance requirements. |
PAM vs. PIM
| Aspect | PAM (Privileged Access Management) | PIM (Privileged Identity Management) |
|---|---|---|
| Definition | PAM is the process of controlling and monitoring access to critical company resources. | Privilege Identity Management is the process companies use to manage which privileged users have access to which resource. |
| Focus | PAM addresses how to monitor and control access whenever a user requests access to a resource. | Privileged identity management solution addresses what access a user is already granted. |
| Functionality | PAM solutions manage credentials, authenticate user identities when a user tries to access a company resource, and provide just-in-time access to identities that normally can’t access certain resources. | PIM solutions focus on controlling users with elevated permissions to change settings, provision or de-provision access, and make other significant changes without formal oversight. |
| Monitoring | PAM tools often offer detailed session monitoring and access logs to help companies report on usage patterns and meet compliance standards. | Some companies use privileged identity management systems to monitor user behavior and distribute access to prevent admins from having too many permissions. |
| Resource Management | PAM does not focus on resource management. | Privileged identity management software focuses on resource management and defining which roles or attributes determine whether a user gains access to particular resources. |
How Does Privileged Access Management Work?
Privileged Access Management (PAM) is an essential component of cybersecurity that protects an organization's most critical resources. It operates by identifying, managing, and supervising privileged accounts to avert unauthorized access and potential security incidents.
Let us take a look at PAM architecture,
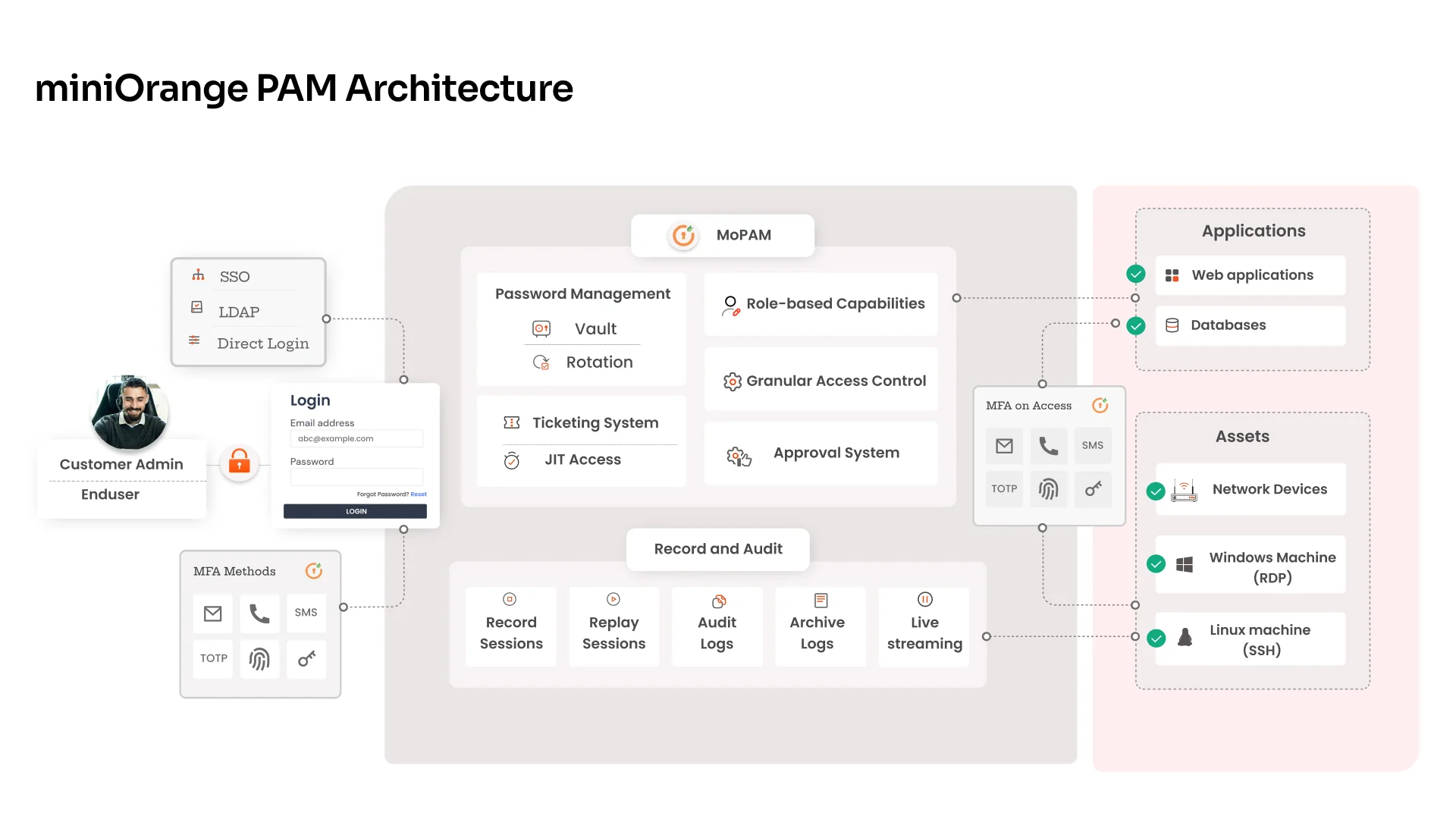
- Identification: It begins by identifying all privileged accounts across an organization's network. These could be admin accounts, service accounts, or any account with special access rights.
- Centralization: The next step is to centralize the management of these accounts. This means all privileged account credentials are stored securely in a centralized vault.
- Access Control: PAM solutions control who can access these privileged accounts. They use policies to determine who can request access, for what purpose, and for how long.
- Monitoring and Auditing: All privileged account activities are monitored and recorded. This helps in detecting any suspicious activities and aids in auditing and compliance.
- Alerting and Response: If any unusual activity is detected, alerts are generated. Depending on the severity, automatic responses like session termination or account lockdown can be triggered.
PAM access management works by identifying special access accounts, controlling who can use them, monitoring their use, and responding to any misuse. This helps organizations protect their most sensitive information from unauthorized access or breaches.
Challenges in PAM Implementation and How to Overcome Them?
Implementing privileged access management comes with its own set of challenges, such as managing the complexity of privileged accounts and ensuring continuous monitoring. However, these hurdles can be overcome by adopting a strategic approach, leveraging AI capabilities for anomaly detection, and ensuring regular audits and reviews.
- Complexity of Implementation: PAM solutions can be complex to implement due to the variety of systems and applications. Overcome this by planning a phased implementation, starting with the most critical systems.
- Resistance to Change: Employees may resist the change due to the perceived inconvenience. Address this by conducting awareness sessions to explain the importance of PAM.
- Integration with Existing Systems: PAM solutions need to integrate with various existing systems, which can be challenging. Choose a PAM solution that offers broad integration capabilities.
- Cost: The cost of PAM solutions can be high. Overcome this by demonstrating the potential cost of a security breach, which the PAM solution helps to prevent.
- Scalability: As the organization grows, the PAM solution must be able to scale. Ensure the chosen PAM solution is scalable and can handle the anticipated growth.
- Privilege Creep: Over time, users may accumulate more privileges than necessary. Regular audits and reviews can help to prevent this.
- Lack of Expertise: Implementing a PAM solution requires specific expertise, which may not be available in-house. Consider hiring external consultants or providing training to existing staff.
- Continuous Management: PAM is not a one-time activity but requires continuous management. Automate as much as possible and dedicate resources for ongoing management.
- Regulatory Compliance: Different industries have different regulatory requirements for access control. Ensure the PAM solution can meet these requirements.
- Securing Remote Access: With the increase in remote work, securing remote privileged access is a challenge. Implement multifactor authentication and secure VPNs for remote access.
Requirements for Installing PAM Software
The requirements for installing the Privileged Access Management software from miniOrange include:
- Operating System: Any operating system (Windows, Linux) that runs a minimum of Java 8.
- CPU Core: 4 Core.
- RAM: 8GB or above.
- Hard Disk (HDD): 80GB or above.
- Database: PostgreSQL 10.18, bundled with the product, MS SQL Server 2012 or above, Azure MS SQL,AWS RDS - PgSQL and MSSQL
- Python: Version 3.8 or above.
- JAVA Environment: JDK 1.8.0_251 and above.
- Browser: Any HTML-5-powered browser such as Google Chrome, Mozilla Firefox, Microsoft Edge, Safari, and Internet Explorer 10 or above.
Please ensure that these requirements are met before proceeding with the installation. If you need further assistance, please write us at info@xecurify.com.
How to Select a PAM Solution for Your Business?
Selecting the right PAM solution is easy by using a suitable guide, knowing what features to look for in a PAM product, and the type of deployment that your use case needs in your PAM software implementation.
A Guide to Selecting a Suitable PAM Solution
Selecting a suitable PAM solution involves understanding your business needs, industry requirements, and specific use cases. Here's a guide:
- Identify Your Needs: Understand the specific needs of your business. This could include the number of users, types of systems, and level of access required.
- Industry Requirements: Different industries have different regulatory requirements. Ensure the PAM solution you choose is compliant with your industry standards.
- Scalability: As your business grows, so will your need for managing privileged access. Choose a PAM solution that can scale with your business.
- Ease of Use: A solution that is easy to use will ensure quick adoption within your organization.
- Integration: The PAM solution should easily integrate with your existing IT infrastructure.
- Vendor Support: Look for a vendor that offers robust support and regular updates to their software.
Remember, the best PAM solution is the one that fits your business needs and enhances your cybersecurity posture.
What Features to Look for in a PAM Solution?
Choosing the right PAM solution is a smart business move when it comes to securing privileged accounts. Let’s discuss the key features to consider when evaluating different Privileged Access Management solutions.
- Password Vaulting: A PAM solution must prevent privileged users from knowing the actual passwords to critical systems and resources. Instead of giving passwords to privileged users, the PAM solution must protect privileged credentials in a secure vault.
- Password Management: PAM tools should allow you to automate and control the entire process of granting access and passwords to privileged accounts. Each time a privileged user requests access, a new password can be automatically generated by the PAM systems to avoid password reuse or leakage.
- Multi-factor Authentication: PAM solutions must add a layer of security with multifactor authentication protocols when a user requests access.
- Access for Remote Employees and Third Parties: PAM software must provide third-party personnel role-based access to systems without the need for domain credentials, thus limiting access to privileged resources.
- Mobile Access Points: PAM software that integrates with a secure application launcher can grant access to remote devices.
- Session Management: A PAM solution must establish sessions for every privileged user. You need the capability to record all privileged sessions, both command-line and video, in a searchable and comprehensive way.
- Real-time Visibility and Alerting: A good PAM solution offers a scalable and secure method to authorize and monitor privileged accounts and activity throughout your system.
- Disaster Recovery: A PAM solution needs to have a disaster recovery plan in place.
- Integration with Native Tools: A modern PAM solution should be able to integrate with native tools.
- Cloud-based Infrastructure: A cloud-based infrastructure is a key feature to look for in a modern PAM solution.
Implementation of PAM in Cloud, Hybrid, and On-premise Environments
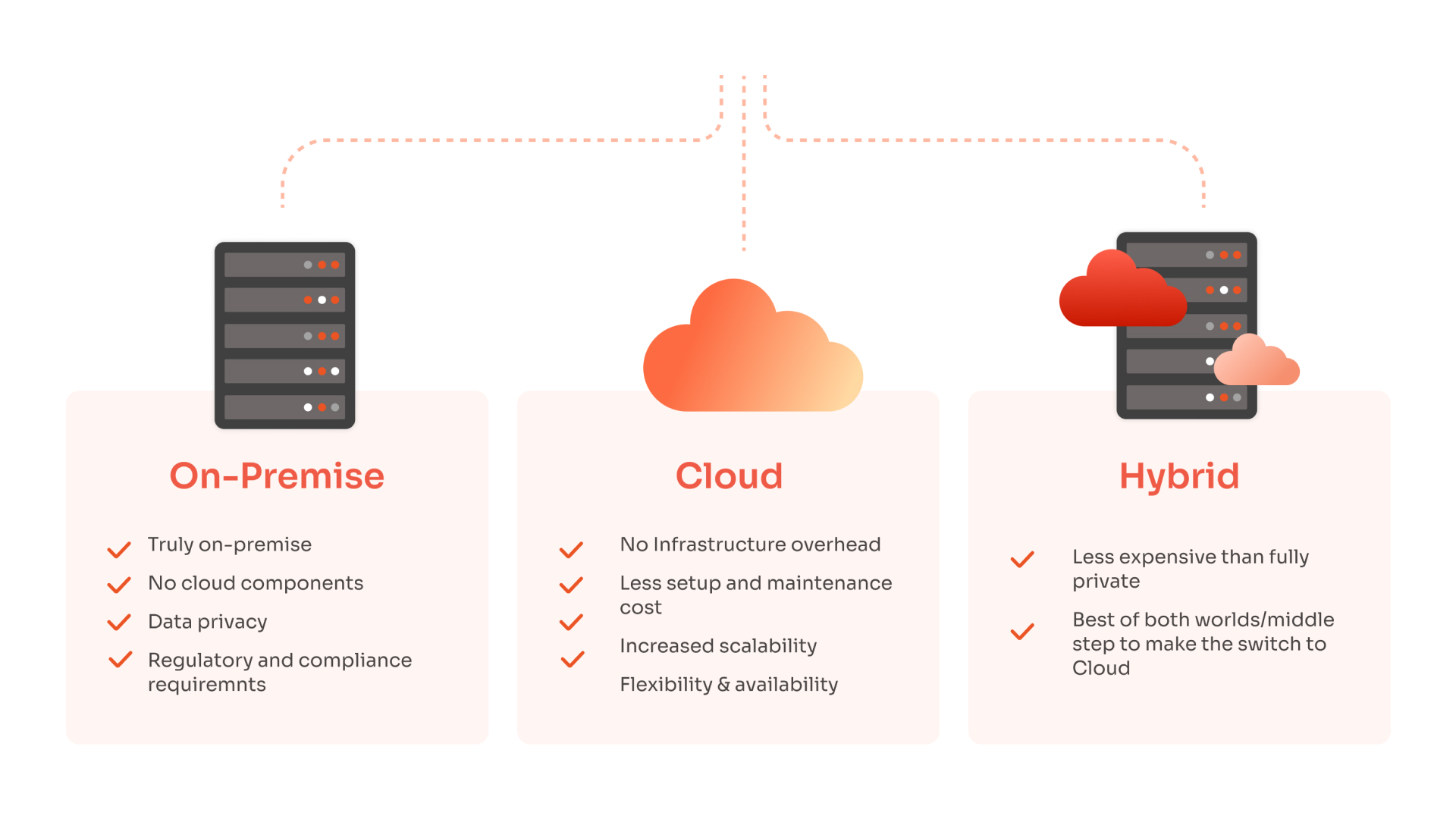
Cloud
PAM in the cloud replaces on-premises PAM infrastructure with cloud-based architecture.
It's important to apply principles of least privilege, role-based access control, and audibility of high-risk sessions.
PAM in the cloud should support cloud-native application program interfaces (APIs), DevOps, containers, and serverless computing models.
A modern open directory platform offers an efficient approach to PAM by converging directory services, privileged account management, directory extensions, web app SSO, and multifactor authentication into one optimized SaaS-based solution.
Hybrid:
In hybrid environments, the definition of a privileged account has widened to include containers, servers, and applications that have privileged access.
PAM tools play an important part in an organization’s zero-trust security strategy. Choose a PAM solution that includes comprehensive PAM services and integrations for your hybrid cloud environment.
PAM in hybrid environments must support cloud-native application program interfaces (APIs), DevOps, container, and serverless computing models.
On-Premise:
In this deployment option, the PAM solution is installed and hosted within the organization's own infrastructure or data center. The PAM solution is capable of integrating and connecting with cloud-based applications and services.
Establish a static VPN connection between your on-premise, AWS, and Azure environments.
Implement core PAM capabilities by deploying solutions that cover intended use cases while driving a zero-standing privilege operating model. The implementation of PAM should always be aligned with the organization's security policies and requirements. It's also crucial to regularly review and update these implementations to ensure they remain effective as the organization's needs evolve.
Best Practices for Effective PAM Implementation
Implementing privileged access management is essential for protecting sensitive data. This breakdown covers privileged access management best practices to enhance your comprehensive PAM strategy effectively.
- Least Privilege Policy: Grant users the minimum levels of access or permissions they need to perform their job functions.
- Regular Auditing: Regularly review and audit privileged activities. Keep track of who is accessing what, when, and why.
- Multi-factor Authentication: Implement multi-factor authentication for privileged accounts to add an extra layer of security.
- Password Management: Use automated tools to change privileged credentials regularly.
- Session Monitoring and Management: Monitor and manage active sessions in real time. Terminate any session that appears risky.
- Privilege Elevation Management: Allow users to elevate their privileges when needed, but with proper approval and for a limited period.
- Training and Awareness: Conduct regular training and awareness programs to educate employees about the importance of PAM.
- Integration with IAM: Integrate PAM with Identity Access Management (IAM) for a comprehensive approach to enterprise security.
Remember, effective PAM is not a one-time effort but an ongoing process. It's about continually assessing, improving, and maturing your security posture.
PAM Real-World Examples and Use Cases
Understanding the implications of PAM usage with examples and use cases is important for businesses. It accelerates the evaluation and decision-making process to validate the efficacy and effectiveness of PAM
PAM Case Study
Problem: Organizations often struggle with managing privileged accounts, which serve distinct roles within their IT infrastructure. These accounts, if not managed properly, can pose a significant security risk, providing potential pathways for malicious users and increasing the impact of a potential breach.
Solution: miniOrange offers a comprehensive PAM solution that ensures complete control and accountability over all privileged accounts within an organization. It simplifies granular access control without compromising security by controlling, monitoring, and securing privileged accounts. The solution is capable of discovering machines, accounts, and applications with admin rights, both on workstations and on cloud servers. It's a cost-effective solution, making it an ideal choice for small to medium-sized businesses.
Impact: The implementation of miniOrange's PAM solution can significantly suppress the risk of a potential security breach. Limiting privileges for people and processes in applications secures them from internal and external vulnerabilities. In case a breach does happen, the PAM solution can help minimize its impact on the system. This leads to a robust security posture, helping organizations manage operations and comply with regulations effectively.
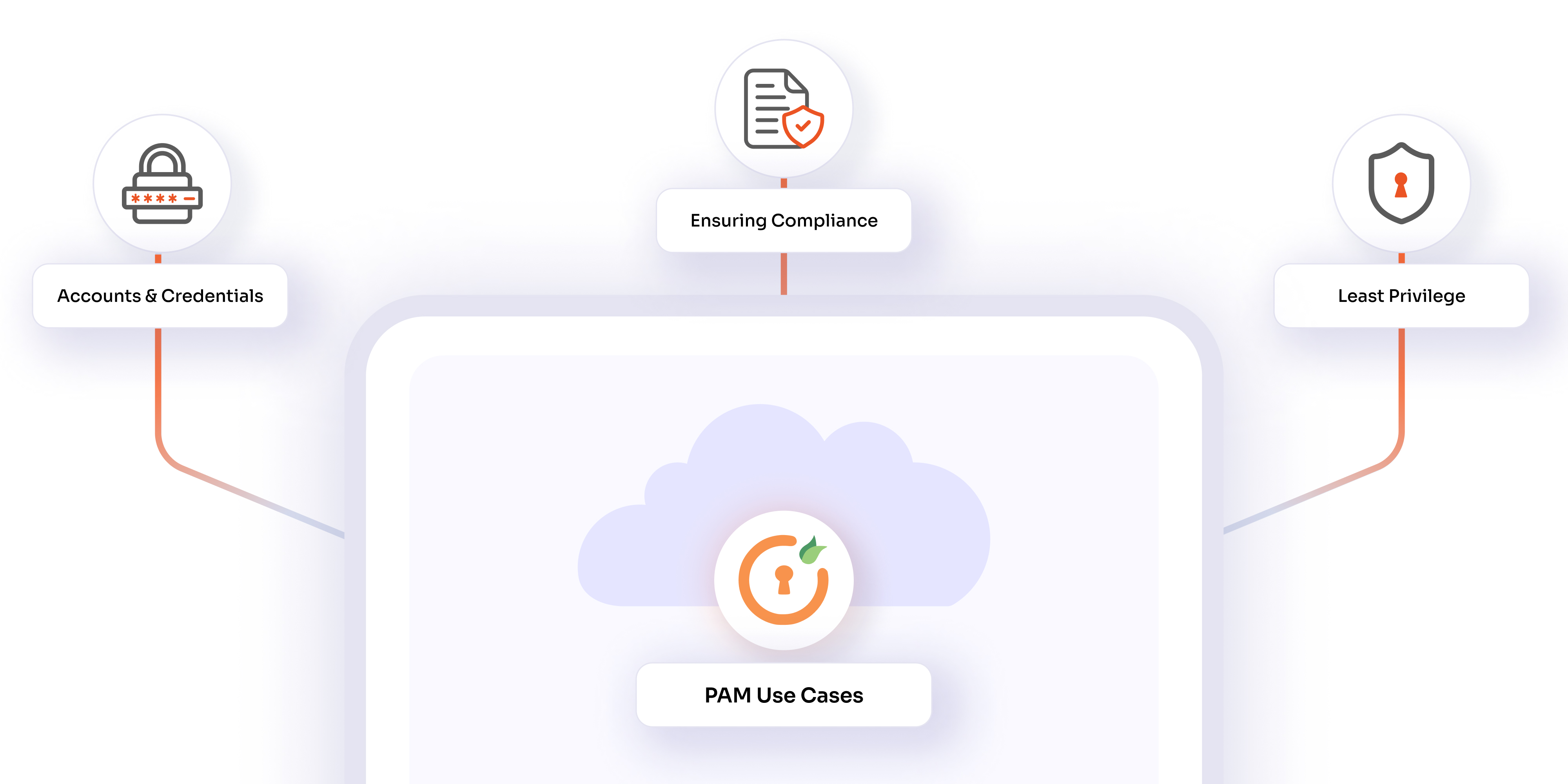
Use Cases of Privileged Access Management (PAM) Systems
Here are some common use cases for Privileged Access Management:
- Privileged Account Discovery: PAM solutions can automatically discover and inventory all privileged accounts across an organization's network, including local, domain, and service accounts.
- Access Control: PAM solutions can enforce granular access controls, ensuring that users only have access to the systems and resources necessary for their roles.
- Session Monitoring and Recording: PAM solutions can monitor and record all activities performed during a privileged session, providing a detailed audit trail for review or investigation.
- Password Management: PAM solutions can automatically rotate and manage the passwords of privileged accounts, reducing the risk of password-related security breaches.
- Least Privilege Enforcement: PAM solutions can enforce the principle of least privilege, ensuring that users and applications only have the minimum level of access necessary to perform their functions.
- Threat Analytics: PAM solutions can analyze user behavior and detect anomalies that may indicate a security threat, such as unusual login times or locations.
- Compliance Reporting: PAM solutions can generate detailed reports demonstrating compliance with various regulatory standards, such as GDPR, HIPAA, or PCI DSS.
- Secure Remote Access: PAM solutions can provide secure, controlled access to remote systems, ensuring that remote workers or third-party vendors do not pose a security risk.
- Integration with Identity Governance and Administration (IGA): PAM solutions can integrate with IGA systems to provide a unified approach to identity and access management.
- Emergency Access: In case of an emergency, PAM solutions can provide temporary, audited access to critical systems. Remember, the specific use cases can vary depending on the organization's size, industry, regulatory environment, and specific security needs. It's always best to conduct a thorough assessment of your organization's needs before implementing a PAM solution.
PAM Governance and Compliance
miniOrange Privileged Access Management (PAM) helps for governance and compliance within an organization to enable better security. It complies with a high level of security with global compliance that provides:
- Control and Accountability: PAM ensures complete control and accountability over all privileged accounts within an organization.
- International Standards and Laws: miniOrange complies with various international standards and laws including, GDPR ISO/IEC 27001, PCI DSS, HIPAA, SOX, NIST, and FedRAMP.
- Secure Endpoint Access: It manages privileges automatically by discovering machines, accounts, and applications with admin rights, both on workstations and on cloud servers.
- Password Management: PAM ensures strong password policies and allows auto password rotation.
- Granular Access Control: PAM allows you to structure your security infrastructure the way you want, giving, adjusting the level of access, and revoking access for whomever you wish, whenever you wish.
- Compliance with Regulations: By centralizing authentication and access control, miniOrange PAM enables organizations to enforce strict security policies, reduce the attack surface, and monitor privileged activities, ensuring compliance with industry regulations.
miniOrange PAM provides a comprehensive solution for managing and monitoring privileged access, enforcing strict access controls, and ensuring compliance with various cybersecurity regulations to enhance governance and compliance posture.
The Future of Securing Privileged Accounts with PAM
As cyber threats continue to rise, securing privileged accounts is a necessity. miniOrange's PAM solution is your shield in this battle. It's packed with features like password vaulting, multifactor authentication, and session management, providing robust security for your privileged accounts.
Our solution is scalable, cost-effective, and easy to integrate with your existing IT systems and infrastructure. We've designed it to tackle the challenges organizations face when implementing PAM solutions. Backed by our expert team, miniOrange's PAM solution is committed to protecting your digital assets and ensuring regulatory compliance. In the fast-paced world of cybersecurity, we're your trusted partner.
Take the next step in securing your privileged accounts with miniOrange. Remember, your organization's security future starts with the right PAM solution. Advance your cyber defenses with miniOrange’s PAM solution today!
Author



Leave a Comment