We have come a long way in a world from no risks to extreme risks where every 39 seconds, there is a data breach. With these alarming rates of breaches comes the most robust form of cybersecurity. Using the least privilege principle, organizations can control how much access to grant a user. This access control is based on the role the user has, for example, standard user, administrator, viewer, editor, etc.
In this article, find everything you need to know about role based access control, its framework, benefits, models, working, standards and RBAC best practices, deployment options, adaptive RBAC and tools. Let’s jump right in.
What is Access Control in Cybersecurity?
Access control is a key cybersecurity concept that ensures only authorized users or systems can access specific data and resources. It acts as a digital gatekeeper, regulating who can enter, what they can do, and preventing unauthorized access to sensitive information.
This protection is crucial against external cyber threats and internal risks, especially with the rise of cloud computing and remote work. Access control also helps businesses meet regulatory requirements by safeguarding personal data and restricting access appropriately.
Common methods include Discretionary Access Control (DAC), Mandatory Access Control (MAC), and Role-Based Access Control (RBAC). RBAC, often used in larger organizations, simplifies management by assigning permissions based on job roles, improving security and efficiency.
What is Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is a widely used security model that assigns permissions to users based on their roles within an organization. Instead of giving individual access to every user, RBAC groups users by their job functions and grants them access only to the data and systems they need to perform their duties. This streamlines permission management and enhances security. It utilizes the principle of least privilege.
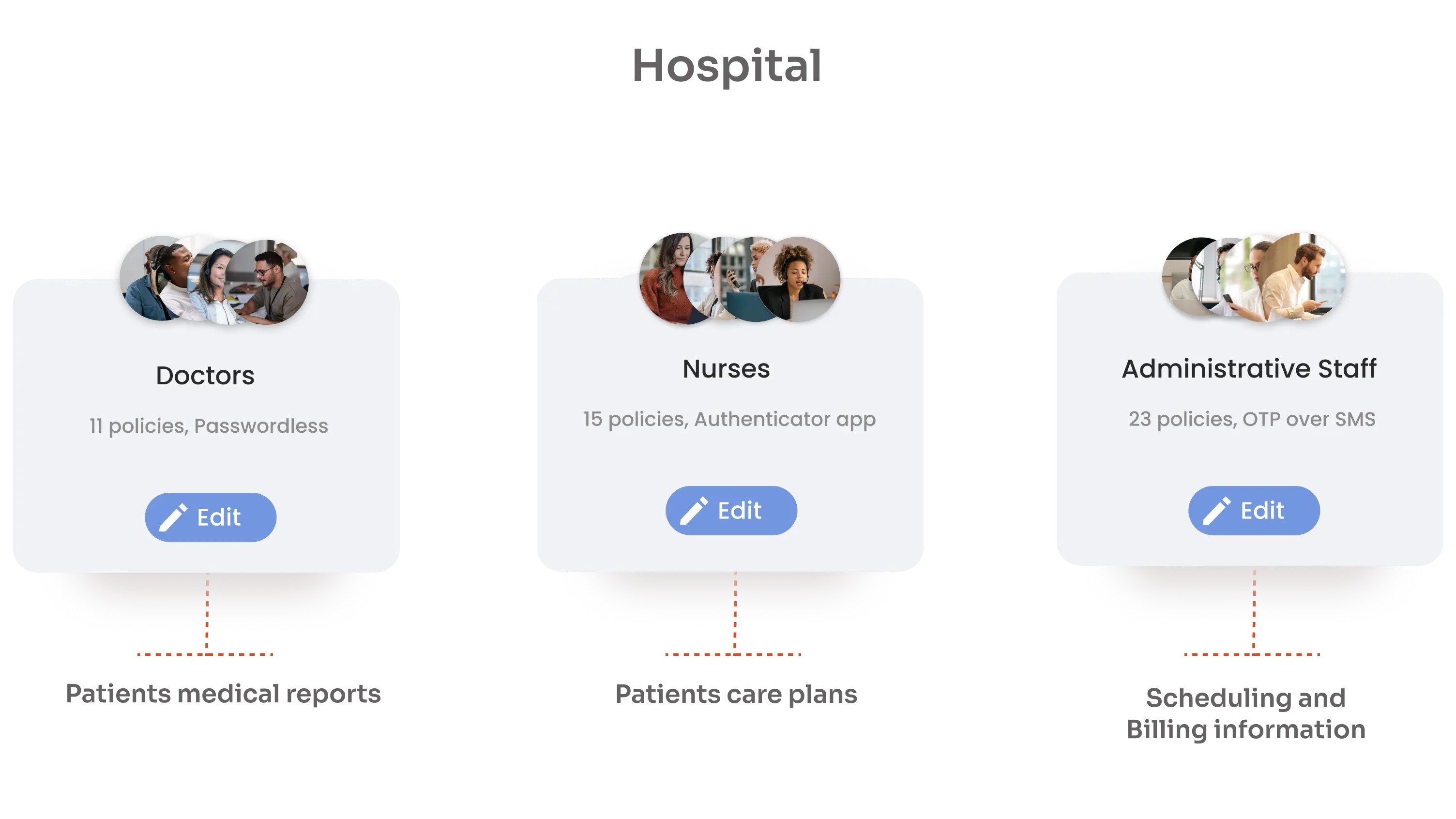
RBAC is especially effective for larger organizations because it reduces the complexity of managing access for numerous employees. By assigning roles with predefined permissions, RBAC limits the risk of unauthorized access and minimizes potential damage from internal threats. For instance, in a hospital, there are doctors, nurses, and administrative staff that have different functions as per their job role. They need access to different systems such as patient medical reports, patient care plans and scheduling and billing information.
Evolution of RBAC in Business Cases
Role-Based Access Control (RBAC), developed in the 1970s to simplify access control based on user roles. In modern dynamic IT environments with cloud computing, microservices, and remote workforces, traditional RBAC models struggle with fluidity. This leads to advanced models like Attribute-Based Access Control (ABAC) and Policy-Based Access Control (PBAC), which use contextual information.
RBAC integrates with these adaptive models, making access management more agile and granular. Combining RBAC with IAM systems streamlines user access, reduces security risks, and ensures compliance with less administrative overhead. This balance is crucial for strong security and seamless user experiences.
RBAC Framework: Core Concepts
In Role-Based Access Control (RBAC), the foundation revolves around three key elements: roles, permissions, and users.
Roles define what users can do within a system, like “Admin,” “Editor,” or “Viewer.” Assigning roles helps organizations control access, making it easy to manage who can view or modify information.
Permissions define what actions or resources a role can access. For instance, an Admin can create, edit, and delete data, while an Editor can only modify content, and a Viewer is limited to reading information. This means only authorized roles perform specific tasks, keeping sensitive data safe and prohibiting unauthorized access.
Finally, users are the individuals in the system. These users are assigned to one or more roles based on their responsibilities.
Benefits of RBAC
- Security and Compliance using Role based Access Control - Role-based Access Control (RBAC) boosts security by assigning role-based access, and thus, preventing unauthorized access while complying to standards like HIPAA, GDPR, and SOX through its clear access control framework. RBAC facilitates the right person with the right access at the right time to safeguard data and build trust.
- Better Operational Efficiency with RBAC - RBAC streamlines access management, lightens IT’s load, and speeds up onboarding and offboarding. It boosts productivity and smoothens workflow by ensuring employees have the right access without unnecessary privileges
- Simplified Administration and Reduced Overhead - RBAC groups users into roles, eliminating individual access management and reducing admin overhead. This boosts efficiency and lets IT focus on strategic tasks while minimizing errors.
RBAC Models: Core RBAC vs. Hierarchical RBAC vs. Constrained RBAC
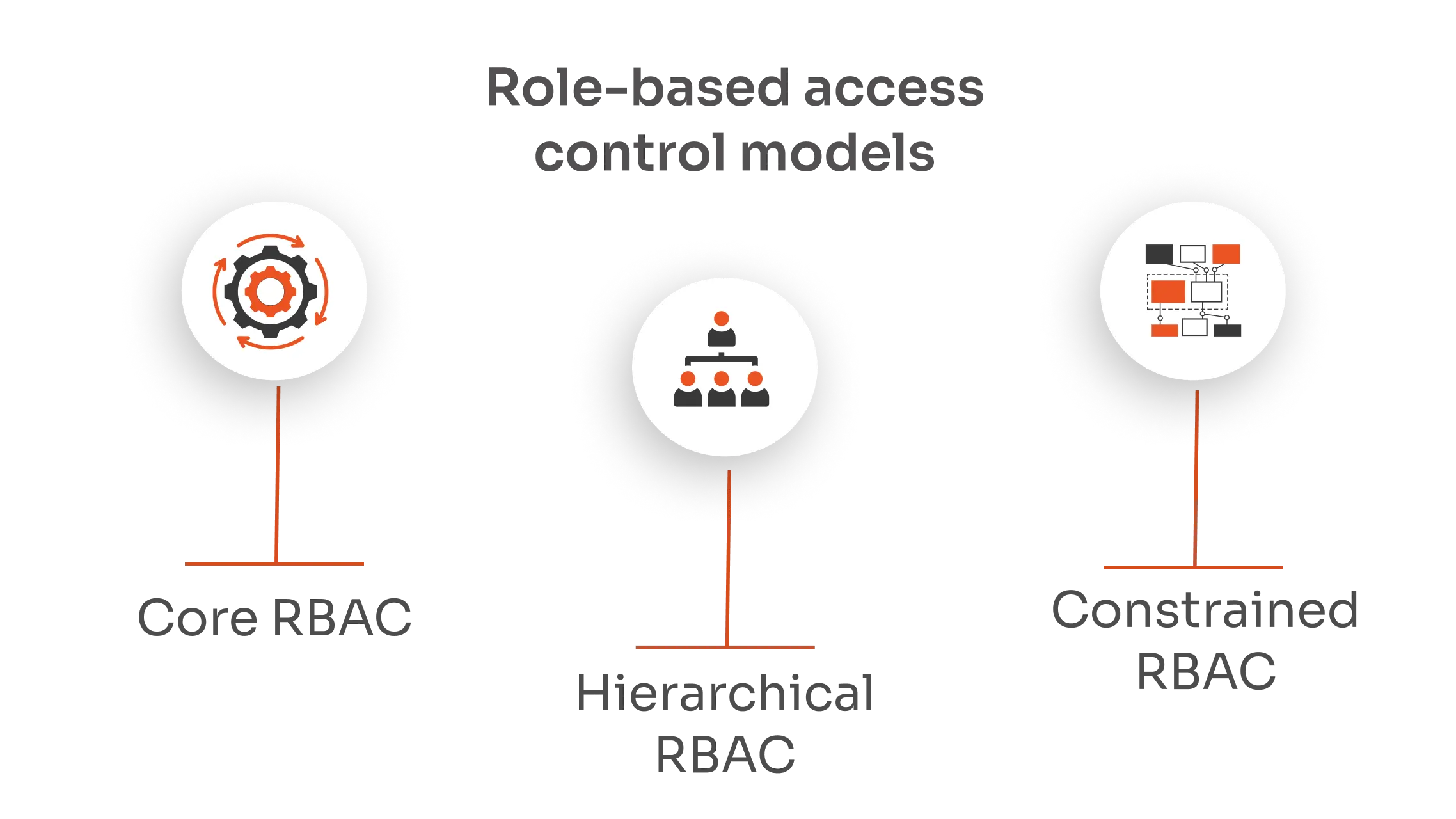
| Feature | Core RBAC | Hierarchical RBAC | Constrained RBAC |
|---|---|---|---|
| Definition | Assigns permissions based on roles. | Inherits permissions across a hierarchy. | Adds constraints to roles and permissions. |
| Example Use | Small to medium organizations. | Large organizations with clear hierarchies. | Environments requiring strict controls. |
| Permission Management | Direct role-permission assignments. | Roles inherit permissions from other roles. | Adds conditions like separation of duties. |
| Complexity | Simple and straightforward. | Moderate, due to role hierarchy management. | High, due to additional constraints. |
| Flexibility | High, easy to implement. | High, scalable with organizational growth. | Moderate, less flexible due to constraints. |
How Does RBAC Work?
Steps to Implement RBAC for Businesses
- Identify Roles: Define roles based on job functions within your organization.
- Assign Permissions: Allocate permissions to each role according to required access.
- Assign Roles to Users: Link employees to roles that fit their responsibilities.
- Review and Monitor: Regularly audit roles and permissions to ensure they remain appropriate.
Common Challenges and Solutions in RBAC
Challenge: Role Explosion
Solution: Regularly audit roles and consolidate similar ones to avoid unnecessary complexity.
Challenge: Inconsistent Role Definitions
Solution: Establish clear and consistent guidelines for defining roles and permissions across the organization.
Challenge: Overlapping Roles
Solution: Conduct periodic reviews to identify and eliminate redundant or overlapping roles.
RBAC Standards and Best Practices
NIST RBAC Model
The NIST RBAC Model is a standardized framework for role-based access control, developed by the National Institute of Standards and Technology (NIST). It was adopted as the American National Standard (INCITS 359-2004) by the International Committee for Information Technology Standards (INCITS) in 2004 and revised in 2012.
This model simplifies security administration by assigning permissions to roles instead of individual users. Users are then assigned to these roles based on their job functions. The NIST RBAC Model is organized into four levels:
- Flat RBAC: Basic role assignment without any role hierarchy.
- Hierarchical RBAC: Supports role hierarchies, allowing roles to inherit permissions from other roles.
- Constrained RBAC: Adds constraints like separation of duties to enhance security.
- Symmetric RBAC: Ensures mutual exclusivity and role symmetry.
By implementing the NIST RBAC Model, organizations can achieve more efficient and secure access control, reducing administrative overhead and minimizing errors.
Defining Clear Roles and Responsibilities
Ensure each role has a well-defined scope of permissions and responsibilities. Clear definitions prevent confusion and overlap, making the system more effective and easier to manage
Regular Audits and Reviews
Conduct frequent audits and reviews to ensure roles and permissions remain relevant and appropriate. This practice helps identify any security gaps and keeps your access control aligned with changing business needs.
RBAC in Cloud Environments
Implementing RBAC in cloud environments like AWS, Azure, and Google Cloud streamlines access control and enhances security. Each platform offers built-in RBAC tools to assign roles and permissions efficiently, ensuring only authorized users can access specific resources. miniOrange is at the forefront of applying the security controls of RBAC to your cloud providers.
Comparisons: RBAC vs. Other Access Control Models (DAC, MAC, ABAC)
| Feature/Aspect | Network Access Control (NAC) | Role-Based Access Control (RBAC) | Attribute-Based Access Control (ABAC) | Policy-Based Access Control (PBAC) |
|---|---|---|---|---|
| Primary Focus | Network access management | Role-based permission assignment | Attribute-based dynamic access decisions | Policy-based rules for access decisions |
| Scope | Network | Systems and applications | Systems, applications, and data | Systems, applications, and data |
| Granularity | Medium | Coarse to medium | Fine-grained | Fine-grained |
| Flexibility | Moderate | Moderate | High | High |
| Management Complexity | Moderate | Low | High | High |
| Key Components | Authentication, compliance checks, monitoring | Roles, permissions, users | Attributes, policies | Policies, centralized management |
| Typical Use Cases | Corporate networks, educational institutions | Organizations with defined job functions | Dynamic and diverse access needs | Large organizations with complex access needs |
| Examples | Cisco ISE, Aruba ClearPass | Microsoft Active Directory, AWS IAM | Okta, AWS IAM with attribute-based policies | Open Policy Agent (OPA), Cisco Policy Suite |
| Implementation Complexity | Moderate | Low | High | High |
| Adaptability | Limited to network context | Limited to predefined roles | Highly adaptable to changing conditions | Highly adaptable to organizational policies |
Future Trends in Adaptive and Dynamic RBAC
Adaptive and Dynamic RBAC is the next evolution in access control, designed to enhance security and flexibility. This approach continuously adjusts permissions based on real-time user behavior and contextual factors like location and device. By doing so, it ensures that access privileges are always appropriate and secure, even as circumstances change. This dynamic adjustment minimizes risks and enhances user experience, making it a must-have in modern IAM strategies.
Tools and Platforms for RBAC Implementation
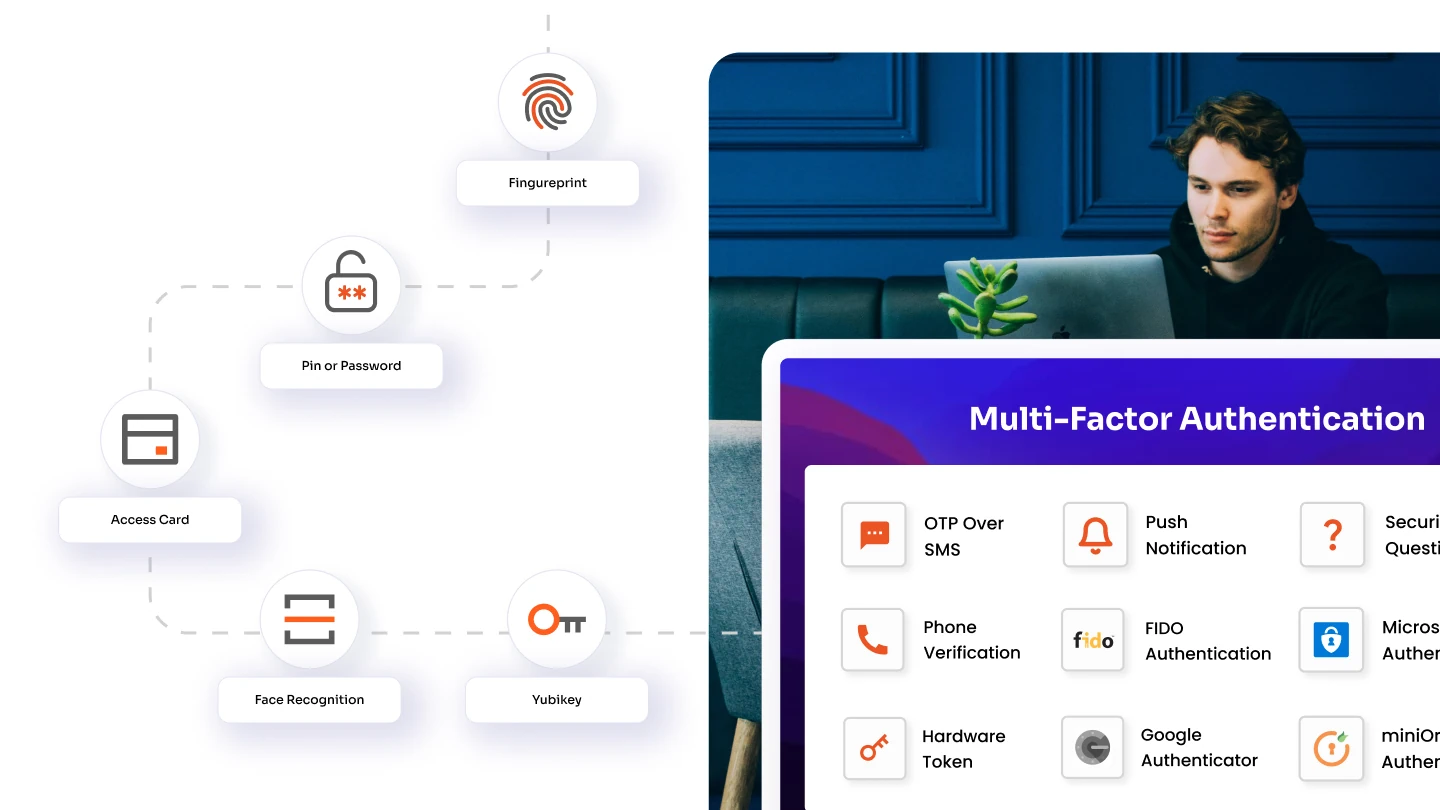
miniOrange provides advanced IAM solutions supporting RBAC, including Single Sign-On (SSO), Multi-Factor Authentication (MFA), and passwordless authentication. Our platform ensures secure and seamless role-based access control for employees, customers, and partners.
Explore miniOrange IAM solutions to secure your organization's access control. Get the miniOrange IAM trial today and take the first step towards a more secure and efficient system!
Author


Leave a Comment