Lots of companies are now allowing their employees to work from home, the office, or anywhere else, all thanks to cloud apps and services. Employees can now use cloud platforms to access their work-related data from anywhere, at any time, subsequently maintaining a healthy work-life balance.
But here’s the catch: all this seamless and quick access to cloud apps and data is possible because of servers located worldwide. Traditional network setups that businesses often use aren’t designed to cope with this, making things slow and sometimes not very secure.
That’s where Secure Access Service Edge, or SASE, comes in. It’s a special kind of tool that is designed for our modern, roam-free work life.
But what exactly is SASE, and why is it so important for businesses today?
Let’s find out!
The Basics: What is SASE?
Imagine you own a company that has offices in New York, Tokyo, and London, with teams working remotely from all across the globe. Everyone within your company is using online tools like Google Drive and Salesforce for document storage and customer management.
Let’s say Sarah, one of your employees from the London-based office, needs to update customer data in Salesforce and access files on Google Drive.
Without SASE in place, Sarah might get slow access to these cloud apps due to backhauling traffic to the data center. Her access to these apps might also be less secure, putting confidential company data at risk.
However, with SASE, when Sarah tries to connect to these cloud services, the system will first verify Sarah's identity and her device's security status. Once approved, SASE will then determine the quickest and safest route for her data to travel across the internet, Google Drive, and Salesforce servers to update and access files.
So, to put it in simple words, Secure Access Service Edge (SASE) makes sure that the right people get quick and safe access to the necessary cloud apps and data, no matter where they are or what type of device they're using, all while keeping bad actors out.
What is SASE Architecture?
Consider having a simple and convenient system that takes care of both your network performance and security all in one place. That's what SASE architecture is. Whether you are working in the office or from home, SASE makes accessing cloud services a breeze.
In the past, traditional cloud security systems focused on creating a security perimeter, something like a protective bubble around your network. But this approach had its limitations, especially for employees who worked remotely.
SASE architecture breaks free from these limitations. It goes above and beyond to give your business a flexible and speedy solution without compromising on security. So no matter where your employees are working, they can enjoy seamless access to cloud services without any worries.
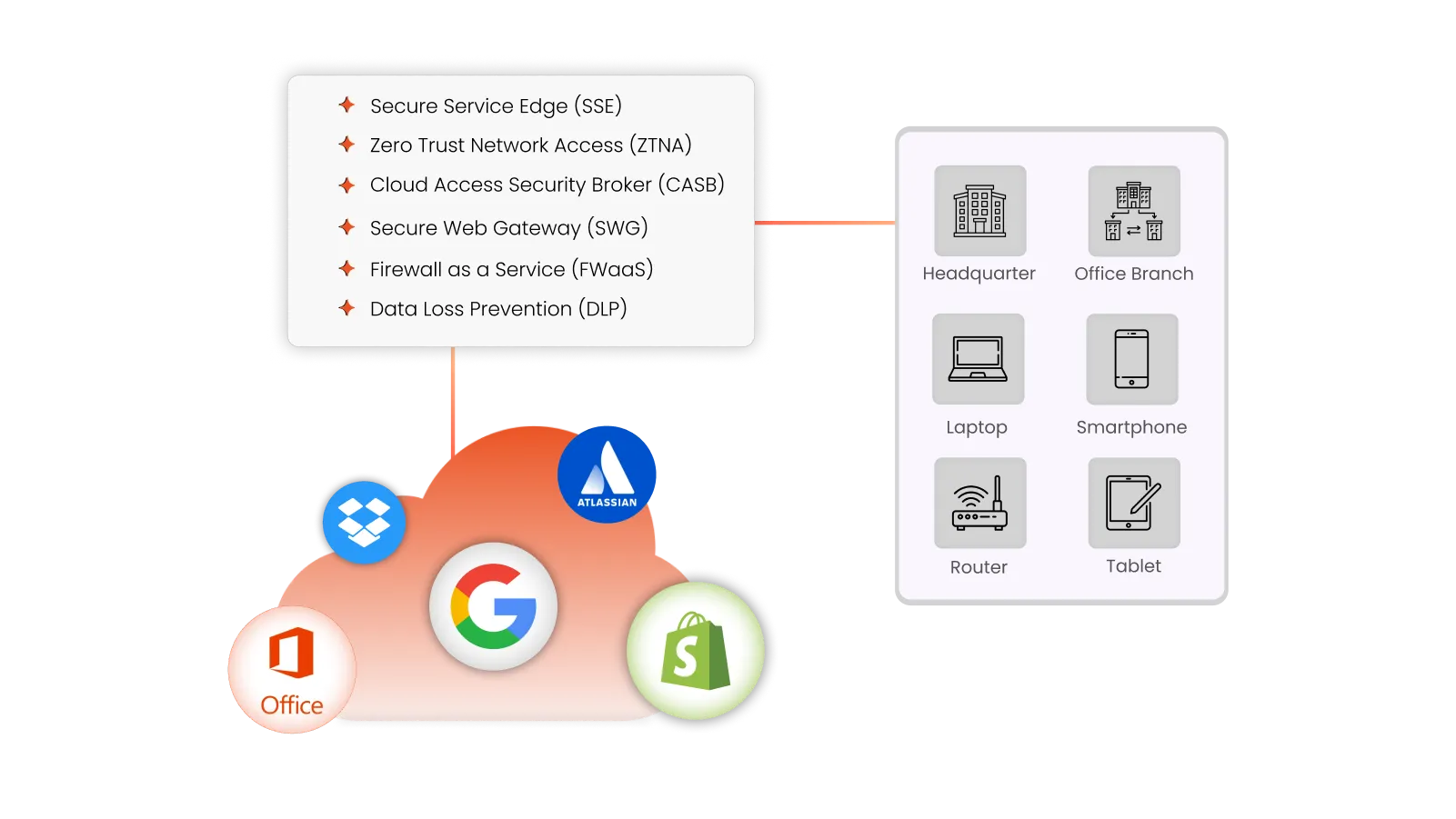
SASE Components Explained
Diving deeper, Secure Access Service Edge (SASE) isn't just a single tool or piece of software but a suite of components working together.
Let's check these SASE security components one by one:
Software-Defined Wide Area Network (SD-WAN)
SD-WAN, a key component of Secure Access Service Edge that manages network performance and bandwidth optimization, acts as a smart guide that securely connects your users to cloud apps and activities, irrespective of their location. The system makes sure that cloud data and apps can be easily accessed over the internet, enhancing performance and reducing costs while meeting the organization's security policies and compliance requirements. It is an essential part of the SASE framework, which enables secure, dynamic, and optimized connectivity that modern businesses demand.
Secure Service Edge (SSE)
SSE is the security component of SASE that acts as a security guard for your cloud apps and activities. When your employees are using cloud services for work, SSE makes sure only authorized personnel can access certain information and keeps unwanted visitors out. This is done by checking who’s trying to enter and what permission they have as per security policy. This means you can safely use cloud services and websites without worrying about cyber threats or data leaks.
SSE further comprises several subcomponents for securing the cloud infrastructure, which include the following:
1. Cloud Access Security Broker (CASB): Think of CASB as the mediator that enforces your organization's security policies when users want to access cloud services, ensuring secure and compliant use of cloud applications. It checks what’s being sent and received, making sure your sensitive business data is secure and protected. Essentially, CASB helps your company use cloud apps and services without compromising on safety, acting as a watchful protector.
2. Secure Web Gateway (SWG): Another key element of SASE, Secure Web Gateway (SWG) checks the online services and websites your employees are trying to visit are protected and follow the rules set by your company and internet usage policies. It also filters unwanted software/malware from user-initiated web/internet traffic and blocks unauthorized access.
3. Firewall as a Service (FWaaS): FWaaS is like having a virtual firewall that keeps an eye on everything coming in and going out of your network, making sure no viruses or hackers can get through. It inspects and filters traffic between your network and the internet based on set security policies. FWaaS works everywhere you need it to — whether employees are working from home, in the office, or on the go. This means your business is always protected.
4. Data Loss Prevention (DLP): Data Loss Prevention (DLP) is a security component of Secure Access Service Edge (SASE) that prevents unauthorized users from accessing your company's confidential data. DLP makes sure that your sensitive business information doesn’t get accidentally shared or stolen. Think of it like a filter that stops your confidential information from getting transferred when it shouldn’t. This way, DLP helps keep your business-critical files safe and ensures you meet privacy standards and regulations.
5. Endpoint Detection and Response (EDR): EDR is a security service of SASE that monitors the devices in use to detect cyber threats like malware that are present on the device. With EDR, the SOC team can monitor and gain detailed insights into security incidents and make decisions to mitigate them in the future.
Zero Trust Network Access (ZTNA)
ZTNA is the latest addition under the umbrella of Secure Access Service Edge to verify users and authenticate their permissions before accessing any cloud services. This SASE security component also prevents unauthorized access, isolates threats in the infrastructure, and prevents users from accessing sensitive data from any unknown network.
Centralized Management
All your security and performance services can be managed from a centralized dashboard to monitor all user activity, schedule updates, isolate threats, manage bandwidth, ensure efficient network utilization, and a whole lot more. It simplifies managing security and network settings, making sure everything runs smoothly.
SASE Benefits
1. Centralized Control: SASE security is a highly effective and efficient centralized solution that lets your admin keep an eye on the security and performance of their entire cloud infrastructure. It gives them a clear picture of how secure their system is, helps spot and deal with shady activities, and makes sure everything runs quickly and smoothly.
2. Secures Access For All Users: Whether the users are working remotely or from the office, SASE solutions prioritize data protection at all times to mitigate threats and detect Shadow IT practices. This is especially vital in today’s world, where remote work has become the norm and the line between professional and personal internet use is thin. SASE security consistently monitors and manages access for all users, regardless of their location.
3. Improved Monitoring: The SASE framework offers the admins deep visibility with its CASB solution to monitor user actions and how they interact with the cloud services to detect risky user behavior before it leads to a severe incident, enabling quicker response times and mitigating potential damage. SASE security enables real-time monitoring & analytics of employee actions across cloud environments.
4. Optimized Network Utilization: The SD-WAN features in SASE solutions improve network performance and reduce latency in delivery, even during high traffic periods. It allows for intelligent path selection for traffic routing, which means the system can choose the most efficient route for data packets to travel across the network. SASE is particularly beneficial during high-traffic periods, as it ensures that critical apps receive the bandwidth they require by rerouting traffic away from congested paths.
5. Reduced Operational Cost: With the SASE framework, from deployment to handling peak network traffic conditions, the entire network cost and maintaining infrastructure security are reduced, which offers the chance to scale your network further ahead. SASE solutions reduce the complexity and overhead associated with managing disparate security tools. This consolidation leads to streamlined operations, better resource utilization, and cost savings. Organizations benefit from a unified security posture that is easier to manage and more effective in detecting and responding to threats.
Top Uses of SASE Solutions
Secure Access Service Edge (SASE) security framework can cover a wide variety of use cases to help enterprises drive growth without compromising on cloud security.
Let's explore how SASE solutions can be applied in real-world scenarios.
SASE in a Hybrid Work Model
Hybrid work solutions have become the norm as employees are now looking to balance their personal and professional lives. With SASE security solutions, employees can connect with any of the enterprise cloud apps, offering a scalable system, low latency, optimized application delivery, efficient bandwidth utilization, and in-depth visibility. The solution helps secure access and verify users before they can access any of the cloud SaaS apps.
Scenario: Consider a multinational company that plans to shift to a hybrid work model. It wants to allow its global workforce to work from home, the office, or various other remote work locations as required. The company has multiple branches and cloud resources and therefore requires secure, fast, and reliable connections.
The Challenge:
1. Performance Issues: Employees experienced delays accessing cloud apps and shared resources
2. Security Concerns: Shift to remote work has increased the possibility of cyber threats, with existing security measures not equipped to provide granular access control for remote users.
3. Complex Infrastructure: Managing separate solutions for networking (SD-WAN) and security (SSE) was cumbersome and inefficient.
SASE Solution:
The company adopted SASE security solutions to address these challenges. By combining using SD-WAN and Secure Service Edge (SSE) in a single framework, SASE solutions provided the following benefits:
1. Optimized Bandwidth Utilization and Reduced Latency: SASE solutions, with its SD-WAN capabilities, optimize network routes, reduce latency, and improve access speeds to cloud services and internal resources. This led to an increase in network performance, enabling employees to access cloud apps and data swiftly, regardless of their location.
2. Robust Security with Granular Access Control: By incorporating SSE components, SASE offered comprehensive security measures, including real-time data access permissions and network restrictions under data and cloud security protocols.
3. Efficient Resource Utilization and Simplified Management: SASE solutions allowed the company to streamline its network and security management, reducing the complexity and costs associated with managing multiple disparate solutions.
Result:
The SASE framework helped the company smoothly transition to a hybrid work model. It not only addressed its immediate network performance and security issues but also provided a scalable, flexible solution that could adapt to the evolving needs of its global workforce.
Cyberthreat Alerts
SASE solutions are always up and ready to mitigate threats targeting cloud apps and business-critical data. As the cases of data breaches and the sale of customer information on deep websites have risen, the need for cloud security has become vital. The SASE architecture checks every piece of data that is accessed and transferred through the network to detect threats in real-time.
Scenario: Imagine a company that uses a cloud-based Customer Relationship Management (CRM) system to manage sales, customer interactions, and data analysis. This CRM system is important for their business as it contains sensitive information about sales strategies, clients, and internal communications.
The Challenge:
Risk of data breach and cyber threats: With the CRM system accessible over the internet, it's vulnerable to a range of cyber threats, from phishing attempts to sophisticated data breaches aimed at leaking sensitive customer information. This could lead to significant financial losses as well as damage the company's reputation and trust with its customers.
SASE Solution:
Real-Time Monitoring and Threat Detection: With a SASE solution in place, the company’s CRM data traffic is continuously monitored. Every request to access or transfer data within the CRM is checked in real-time, ensuring that only legitimate activities are allowed.
Automated Threat Response: Whenever a suspicious activity is detected—like an unusual login attempt from an unknown location—the SASE framework acts immediately, blocking user access to isolate the threat.
Ongoing Vigilance: SASE solutions continuously scans the cloud infrastructure and is always on the lookout for new threats, employing advanced algorithms and threat intelligence.
Result:
The application of SASE to protect cloud apps like a CRM system offers businesses a dynamic and proactive defense mechanism against the ever-growing threat of cyberattacks. With continuous monitoring, real-time threat detection, and automated response capabilities, SASE provides the comprehensive security posture required to protect critical business operations.
Connecting and Scaling Businesses
SASE security offers an exponential increase in performance with SD-WAN and SSE, helping businesses grow by optimizing bandwidth utilization, boosting network speeds, reducing latency, securing data access permissions in real-time with granular access control, and enabling network restrictions, under data and cloud security.
Scenario: A global retail chain based in the United States plans to expand its operations into Europe and Asia. The expansion plans include adding new retail outlets and distribution centers and supporting the local online payment systems.
Challenge:
1. Connectivity: Ensuring fast and reliable connections between all retail outlets, headquarters, distribution centers, and cloud services across continents.
2. Security: Guard sensitive customer data and financial transactions from cyber threats while meeting diverse regional data protection regulations.
3. Scalability: Quickly scale network resources based on demand, especially during peak shopping seasons.
4. Management: Simplify the management of a wide-area network (WAN) that spans multiple countries and regions.
SASE Solution:
The retail chain decided to implement a Secure Access Service Edge (SASE) solution to address these challenges effectively. Here's how the SASE framework supports their business needs:
1. Enhanced Performance: SASE integrated SD-WAN capabilities to improve bandwidth utilization and reduce latency. This ensures high-speed connectivity between all locations, critical for real-time inventory management, smooth online payment processing, and enhancing the overall customer experience both online and in-store.
2. Strong Security: The Secure Service Edge (SSE) component of SASE offers advanced security features. It protects data access and transactions in real-time by implementing granular access control and enabling network restrictions.
3. Zero Trust Network Access (ZTNA): SASE's Zero Trust component ensures that only authenticated and authorized users can access the network and specific applications, minimizing the risk of data breaches and insider threats.
Result:
The use of SASE, along with its dynamic security policies and Zero Trust offerings, provides a comprehensive solution for businesses looking to scale securely and efficiently across the globe.
IoT Adoption
IoT is gaining widespread acceptance as businesses are looking to make their processes seamless. Several businesses have already made plans to transition to an IoT office environment, but lack the infrastructure for it. SASE framework is the basis for IoT adoption as it provides efficient network performance and an excellent bandwidth utilization method, along with several security policies to help you build an IoT ecosystem.
Scenario: A multinational manufacturing company has multiple factories spread across different continents. The company aims to optimize its production lines and reduce operational costs by transitioning to a smart IoT model. This initiative involves deploying thousands of IoT devices across its factories to monitor machinery health, optimize energy consumption, and automate quality control processes.
Challenge:
Lack of secure connectivity: IoT devices need to be securely connected to the company's network, requiring efficient network performance, excellent bandwidth utilization, and robust security policies to prevent data breaches and ensure the integrity of the manufacturing process.
SASE Solution:
1. Security Policies for IoT Ecosystem: With the adoption of SASE security, the company can enforce security policies across all IoT devices and locations. This allows for the seamless integration of security services such as firewalls, secure web gateways, and zero-trust network access (ZTNA).
2. Efficient Bandwidth Utilization and Network Performance: SASE architecture is implemented to provide a scalable and efficient networking solution. By combining SD-WAN capabilities with cloud-native networking, it enables the company to prioritize critical IoT traffic and optimize bandwidth usage.
3. Seamless IoT Integration: SASE facilitates the easy deployment and management of IoT devices by providing a single management framework for both networking and security. This simplifies the operational overhead and allows the company to quickly scale its IoT environment as needed, without compromising on performance or security.
Result:
The integration of SASE in an IoT environment showcases how enterprises can securely and efficiently embrace IoT technology to transform their operations. The ability of SASE to provide scalable networking performance and robust security policies is crucial for building a resilient and efficient IoT ecosystem, paving the way for the future of smart enterprises.
The Future is SASE
For businesses looking to thrive in the era of cloud computing and remote work, adopting SASE security could very well be the key to unlocking new levels of agility and protection. It represents a transformative approach to networking and security, offering a flexible, scalable, and efficient way to manage the ever-evolving digital landscape. Whether you're employees are working from a cafe or logging in from a beach halfway around the world, SASE ensures your digital experience is secure, seamless, and productive.
miniOrange is one of the leading providers of SASE cloud security solutions. Thanks to our amazing products, active support staff, and the most affordable prices available, we have gained recognition as the pioneers of cyber security solutions.
So, what are you waiting for? Drop us an email at info@xecurify.com and we will get right back to you!
Reference links
Check out more resources by miniOrange for SASE security.
Author



Leave a Comment