Zero Standing Privileges (ZSP) is a proactive security strategy that focuses on restricting access to sensitive data by removing permanent access rights. This approach ensures that access privileges are granted on a Just-in-Time basis, significantly reducing the risk of data breaches and compliance issues.
In this blog, we will dive into the concept of zero-standing privileges,
- Examine how standing privileges arise
- Discuss the implementation of Just-in-Time (JIT) access, and
- Know more about the ZSP model.
We will also highlight the potential risks associated with standing privileges, outline the advantages of adopting a zero standing privilege philosophy, and overview of the best practices for integrating ZSP into your security framework.
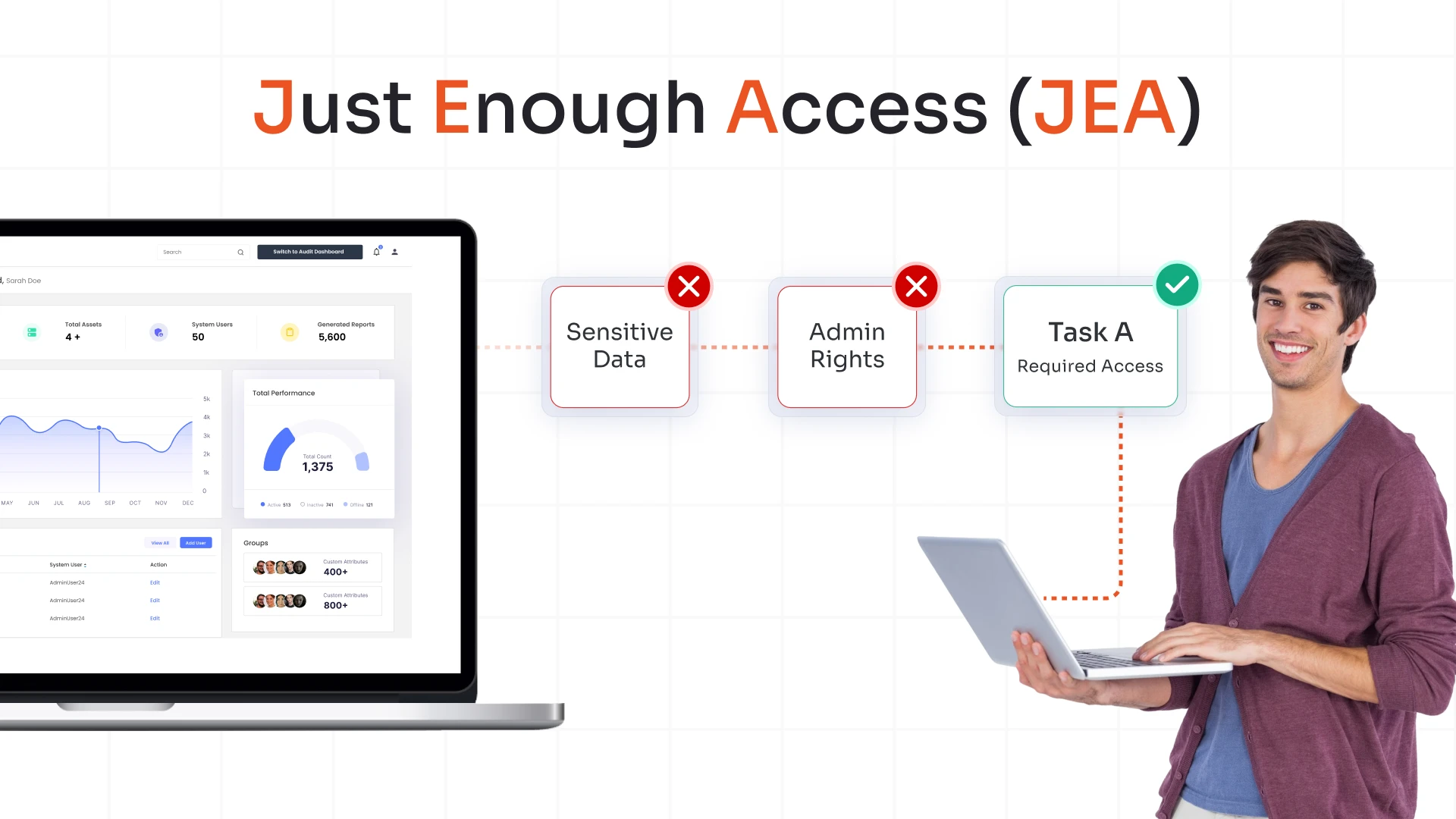
What is Zero Standing Privileges (ZSP)?
The term Zero Standing Privileges (ZSP) was coined by Gartner that define the ideal state for managing privileged access in an organization to reduce the risks of credential theft, misuse of privileges, security breaches, and data loss.
Zero Standing Privileges (ZSP) is a security concept where no persistent or always-on privileged access rights are granted to any identities or accounts, be it a human or a machine. This approach aims to eliminate standing privileges, operating under the principle that privileges should only be granted on a Just-in-Time (JIT) basis.
ZSP represents the ideal outcome in a Privileged Access Management (PAM) model, where continuous authentication and the application of the least privilege are essential. The framework aligns closely with Zero Trust strategies, which advocate for the removal of default, and uninterrupted access privileges and emphasize that no access should be given based on assumed trust.
Implementing ZSP means that administrative or authorized access is never pre-assigned but is automatically allocated for specific tasks and only for the necessary duration. This method significantly reduces the cyberattack surface by limiting the opportunities for privilege abuse. By ensuring that privileges are securely tailored and short-lived, ZSP helps prevent the collection of access rights that could lead to data breaches, unauthorized data access, and other security violations. This approach enhances security protocols and supports compliance by implementing strict access control standards.
What is a Just-in-Time Access Model?
The Just-in-Time (JIT) Access Model is a strategic approach to privilege management that drastically reduces the active window during which privileges are available. Unlike traditional models that grant standing privileges indefinitely, JIT access limits privilege activation to the precise moments they are needed. This targeted allocation minimizes the attack window, significantly enhancing the organization's security structure. By controlling the duration of access, JIT effectively closes the gaps that could potentially be exploited by malicious user activities.
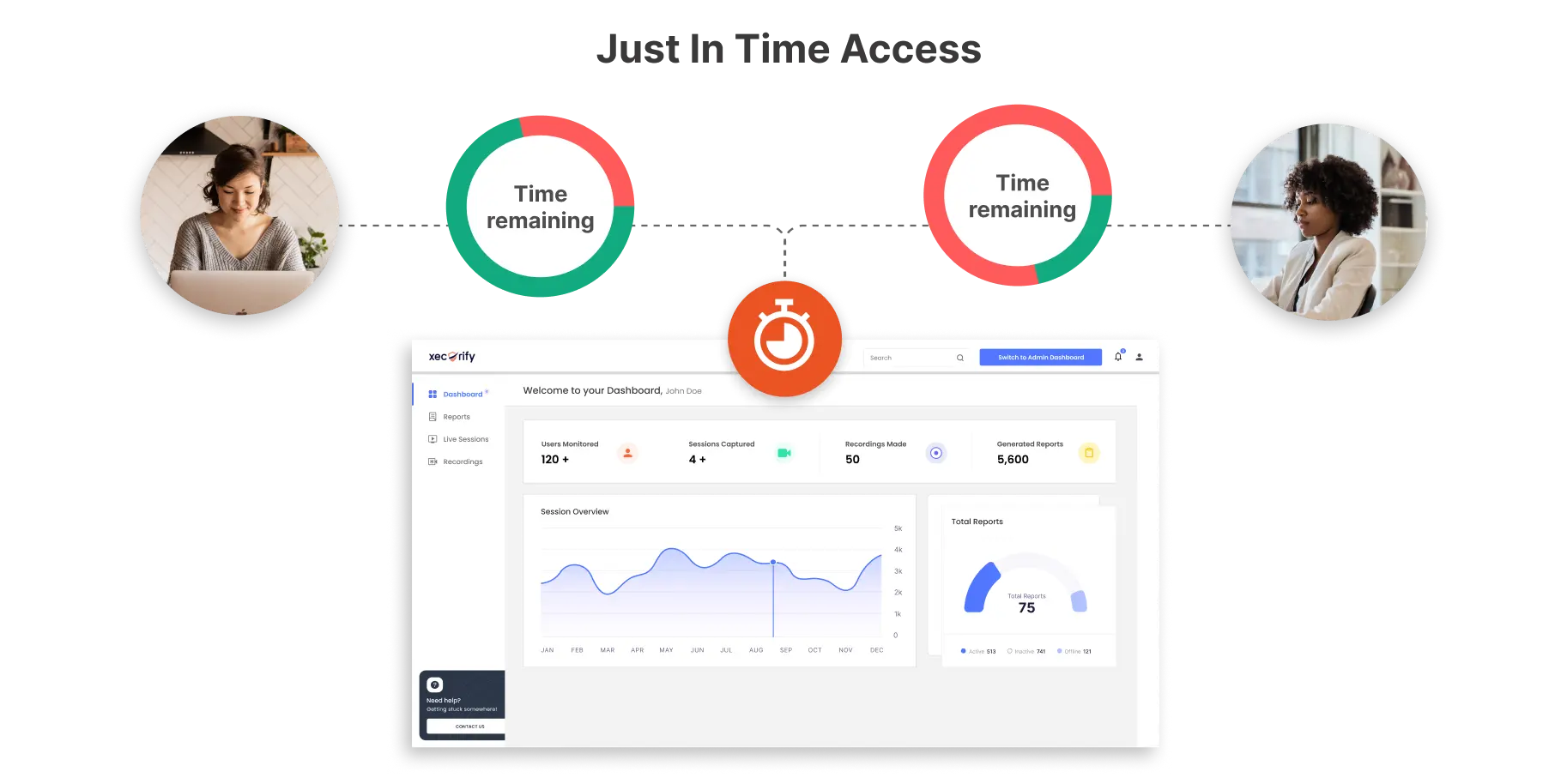
Implementing a JIT model transforms how administrative privileges are handled. For example, in a standard environment, an administrator might have continuous access throughout the week, 24*7, 7 days a week, totaling 168 hours.
However, with JIT, this access could be restricted to as little as a few hours, or even minutes per week, based on specific tasks and operational requirements. This reduction ensures that access rights are provided dynamically and only as needed.
Why are Zero Standing Privileges Important?
Zero Standing Privileges (ZSP) are increasingly recognized as an essential aspect of modern cybersecurity frameworks, particularly in environments where access rights need to be revised frequently. By adopting ZSP, organizations implement granular access control, policy-based security controls that provide users with short-term access on a needed basis.
This approach not only ensures that access rights are promptly revoked after the completion of a task but also significantly reduces the administrative burden on IT teams who would otherwise spend considerable time on provisioning and de-provisioning access. Moreover, the limited access granted under ZSP can enhance an organization's eligibility for cyber insurance, potentially lowering the costs associated with recovering from a security breach.
Another critical advantage of ZSP is its capacity to limit excessive administrative privileges, which are commonly overextended in many IT environments. Administrative users often retain high levels of access, which can pose significant security risks if exploited. By limiting administrative access to only what is necessary for specific tasks and durations, ZSP minimizes the risk of unauthorized activities and potential internal and external threats. Additionally, this model reduces the need for an organization to manage a large volume of passwords, secrets, and keys, thereby simplifying the security infrastructure and further securing the IT environment against breaches and unauthorized access.
The risks of standing privileges
Let us now have a look at a few of the risks associated with standing privileges
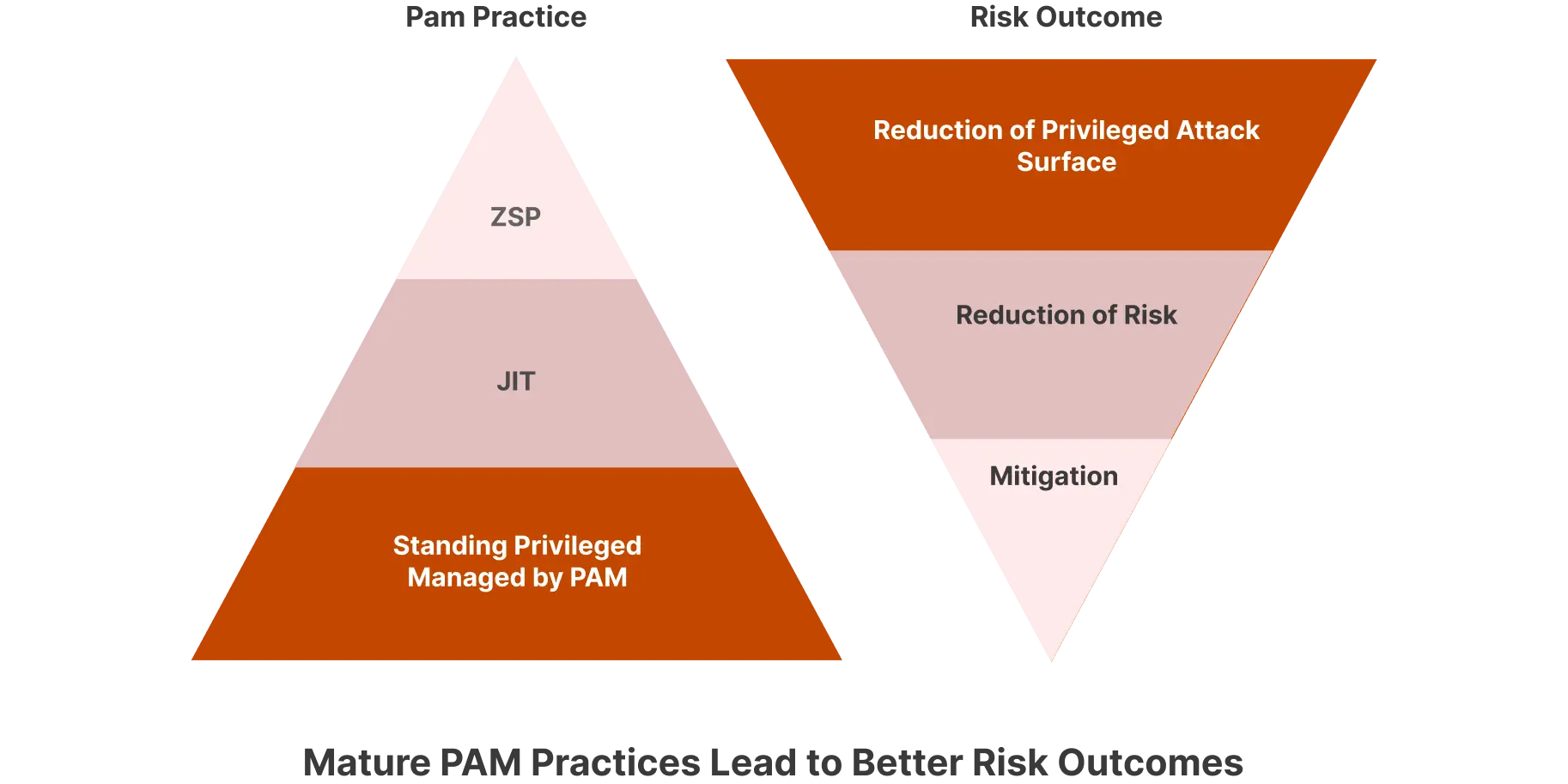
- Excessive Access Risk: Standing privileges allow for continuous, unmonitored access to IT resources, making them vulnerable if credentials are compromised, granting attackers unrestricted entry into the system.
- Security Issues with Permanent Access: The necessity to constantly monitor who has access to what, especially in growing IT environments with remote work, demands significant ongoing management and can lead to security oversights.
- Increased Risk of Lateral Movement: Withstanding privileges, attackers can use compromised credentials to move laterally within the network, accessing sensitive areas and escalating privileges, thus amplifying the potential damage from a breach.
- Resource Drain in Access Management: Continuous provisioning and de-provisioning of access for new or departing employees can overextend an organization's resources, increasing the chance of errors that lead to breaches.
- Inadequacy of Traditional PAM Solutions: Traditional Privileged Access Management solutions often fail to adequately prevent breaches from compromised credentials, underscoring the need for a Zero Standing Privileges approach to limit access to resources strictly as needed.
What is Zero Trust vs least privilege?
Zero Trust and the principle of least privilege are two fundamental concepts in cybersecurity that focus on minimizing access risks, but they differ in their approach and emphasis.
Zero Trust operates on the principle of "never trust, always verify." This means it doesn't automatically trust anything inside or outside its network. Instead, Zero Trust requires verification for every access request regardless of where the request originates or what resource it accesses. It involves continuous authentication and authorization checks to ensure security is maintained throughout a session, not just at the entry point.
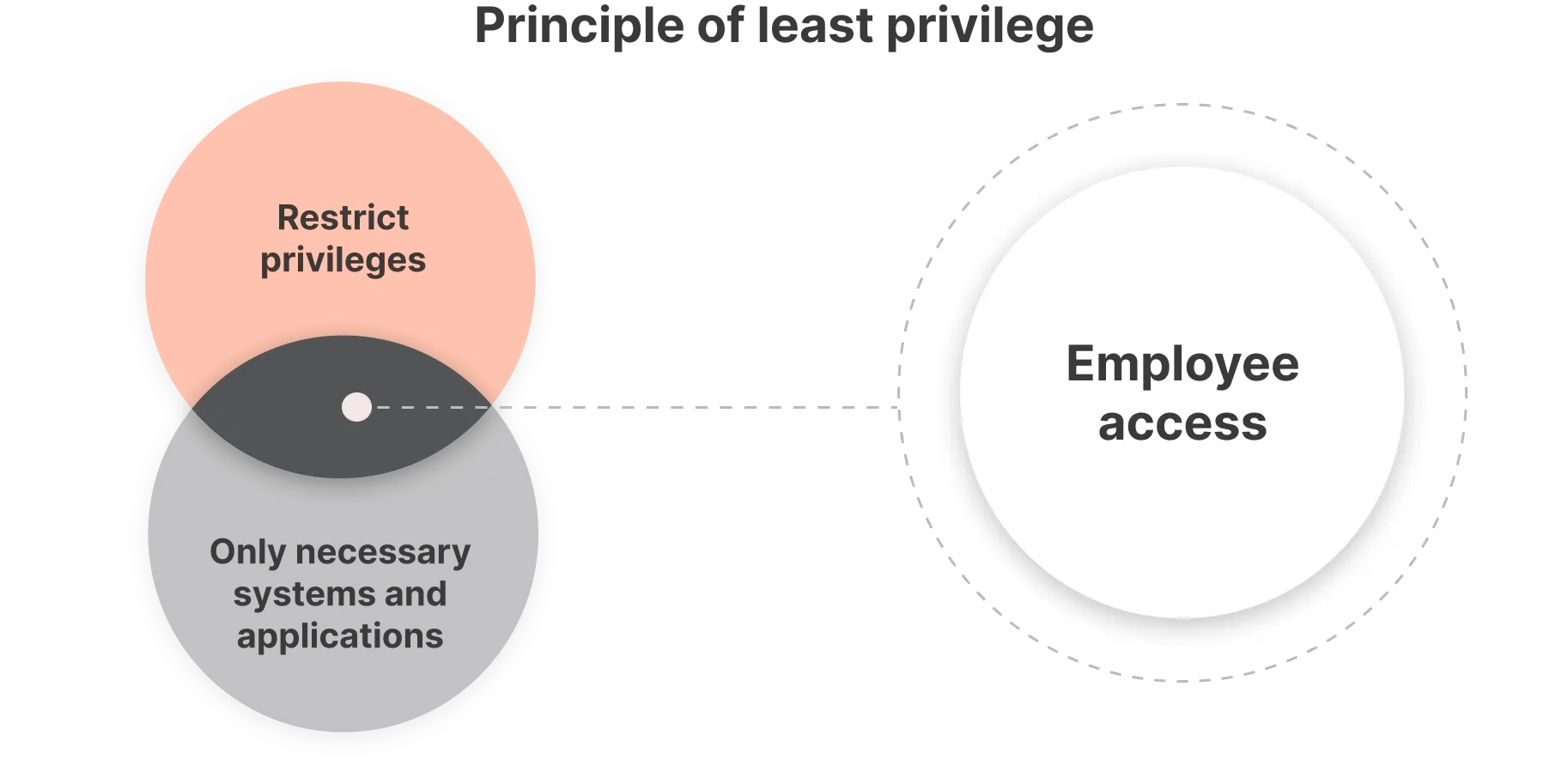
Least Privilege, on the other hand, is about limiting user access rights to only what is strictly necessary to perform their job functions. It focuses on minimizing the potential damage that could occur if an account is compromised. By providing the minimum level of access required, it reduces the risk and impact of a security breach.
While Zero Trust encompasses a broader, more holistic approach to network security—constantly questioning the security status of assets and user access—least privilege is more specifically concerned with ensuring users don’t have more access than they need. Both approaches aim to enhance security by controlling access based on user identity and context, but they apply their principles in slightly different ways to protect digital environments.
Difference between ZSP and PoLP
| Aspect | Zero Trust Security (ZTS) | Principle of Least Privilege (PoLP) |
|---|---|---|
| Core Principle | Never trust, always verify. | Grant the minimum necessary access. |
| Verification | Continuous authentication and checks. | Initial setup of minimal access, adjusted as needed. |
| Scope | Broad: network, devices, users, data. | Specific: user and application access. |
| Focus | Trust validation at every access. | Limiting access to minimize risk. |
| User Access | Dynamic based on risk assessment. | Static setup, modified as needed. |
| Implementation | MFA, micro-segmentation, monitoring. | Role management, access reviews, audits. |
| Examples | Multi-checkpoint user verification, secure remote access. | Assigning read-only access to sensitive data. |
How does Zero Standing Privileges work?
Zero Standing Privileges (ZSP) is a security approach designed to minimize the risk of excessive or unnecessary access rights within an organization's IT environment to their Privileged Accounts.
Here’s how it works step-by-step:
- Authentication and Request : The process begins with a user authenticating themselves in the system. After authentication, the user requests specific access rights or entitlements. These requests are aligned with the principle of least privilege, meaning the user asks only for the access necessary to perform a particular task.
- Time-bound Access : The request includes not only the specific entitlements needed but also the duration for which they are required. This duration should be as short as feasible to minimize risk, as longer access periods can potentially expose the system to greater security threats.
- Processing the Request : After the request is made, it needs to be processed. In simpler or smaller-scale implementations, this might involve a manual approval flow where an assigned approver manually reviews and approves the request. However, for efficiency and to reduce the chance of human error, automating this approval process is recommended where feasible.
- Provisioning Access : Once the request is approved, the system automatically provisions the requested entitlements to the user's federated identity. This means the access rights are temporarily granted to the user for the duration specified.
- Performing the Task : With the entitlements provisioned, the user can then proceed to carry out the necessary tasks or work. The system ensures that access is configured correctly for the duration of the session.
- Termination of Access : After the work is completed, the user either actively ends the session or lets the access rights expire as per the set time limit. The ZSP system then automatically enforces the removal of all the entitlements or roles that were granted temporarily.
This approach effectively reduces the risk of permanent, excessive, or unused privileges within the system, aligning with broader security strategies like Zero Trust by continuously adapting access controls based on ongoing assessments of need and risk.
The user is returned to the default state of zero permissions.
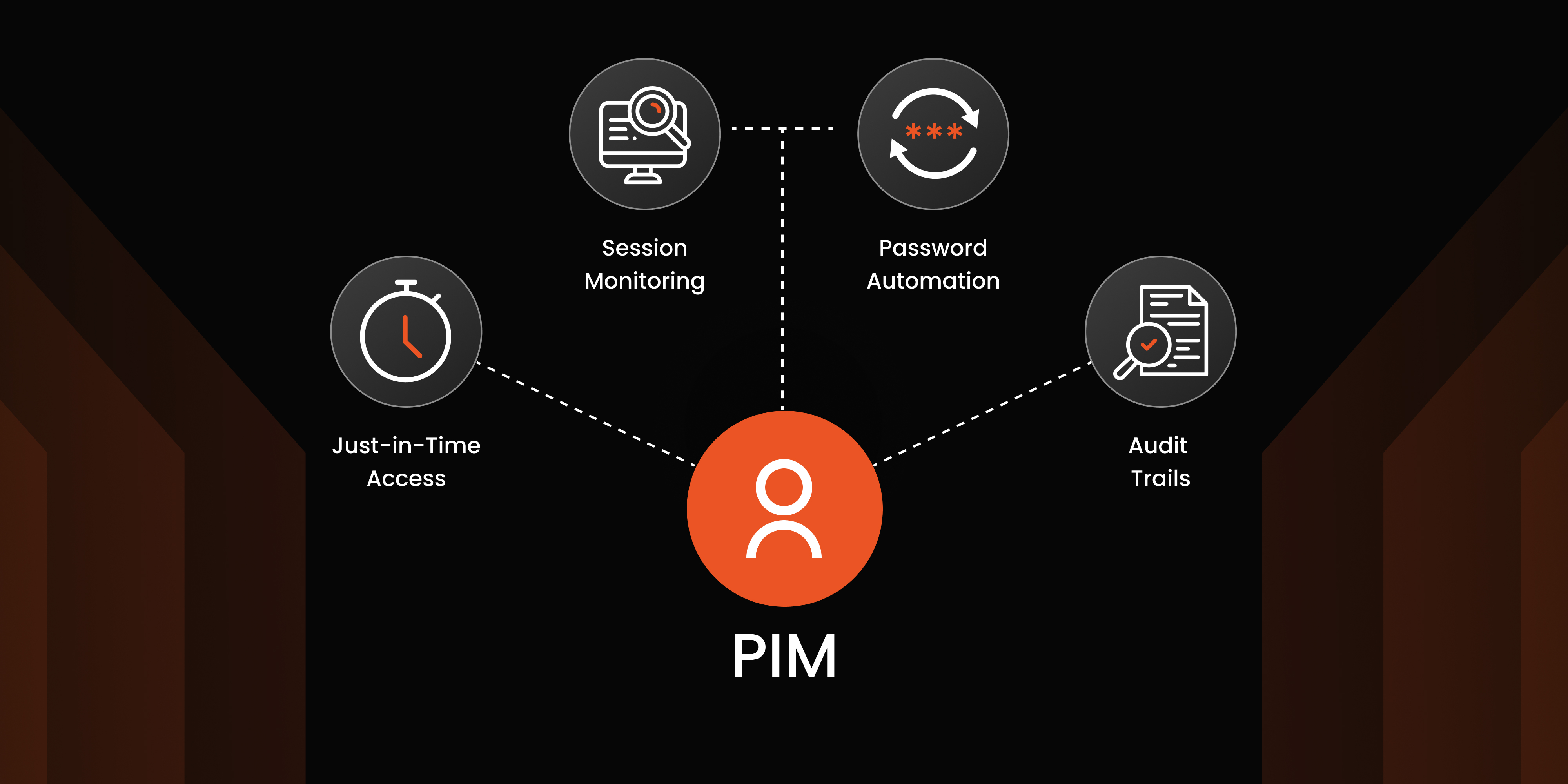
Explore miniOrange PAM Solution
miniOrange PAM solution revolutionizes traditional Privileged Access Management by offering seamless and secure control over your organization's critical resources. With miniOrange PAM, you empower your team to grant access precisely when it's needed, enhancing security without compromising on productivity. Our solution utilizes the principles of zero standing privileges and just-in-time access, which minimizes the risk of unauthorized access and significantly reduces the threat of data breaches.
Start a free 30-day free trial of miniOrange PAM today and experience firsthand how straightforward and effective implementing zero standing privileges and just-in-time access can be.



Leave a Comment