Get a Free Trial and explore our pricing on

Check out our Connectors
The miniOrange Crowd SSO connector expands the SAML or OAuth/OpenID SSO functionality from Crowd to its connected Atlassian applications. It also allows users to enable SSO Authentication from any SSO compliant IDP, where SSO requests and responses to and from IDP will pass via the Crowd server.
Clients Success Stories
All Success Stories





Benefits That Make Life Easier for You!
Enhanced Productivity
50% Faster
Boost user productivity with Single Sign-on by faster logins and seamless transition between Atlassian applications with a single click
Auto User Management
120+ Hrs
Effortlessly map user profiles, groups and attributes from your Identity Provider to Atlassian.
Flexible Access Rules
100+ Combinations
Enable local authentication for external users or customers, while enforcing SSO-based login for internal users or admins.
Discover Our App Features

Multi-provider Support
Have multiple sources for your identities? No worries, we have got you covered.
Redirection Rules
Dynamically decide and authenticate your users with their intended authentication source.
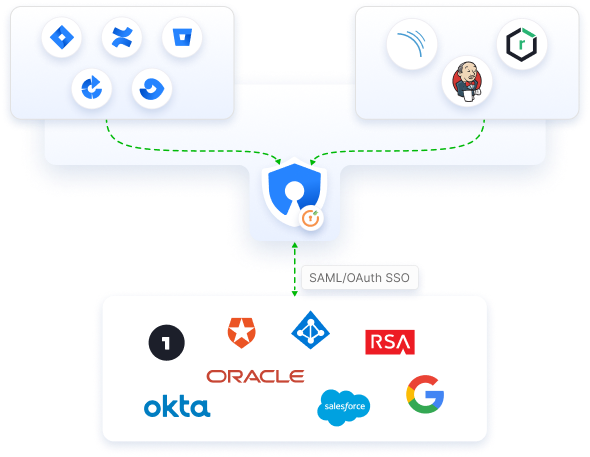
Enable SSO across Crowd Connected apps
Enhance security and extend SSO functionality to Crowd connected Atlassian and non-Atlassian applications. Streamline authentication through any SAML/OAuth compliant Identity Provider, all managed conveniently via the Crowd.
Customize Login Page
Customize the login interface to reflect your brand identity, ensuring a professional experience.

Encryption and signing
Ensure the safety of your SSO with enhanced data encryption.
App specific SSO
Share only the required permissions with the users.
Emergency login
Don’t let the system failure stop you. Access your Crowd with local credentials using emergency login.
Restore & backup settings
Redirect users to IdP instead of showing Crowd login page for logging into Crowd.
Troubleshooting
Faster and better troubleshooting issues, you might need to share plugin configurations and logs via email or customer portal.
Check out pricing
Product Name
Crowd SAML/OAuth SSO
How many users do you have?
2199
/year
Hear It From Our Satisfied Customers
At our core, we prioritize our customers above all else. Every decision we make is in your best interest. Your feedback guides our efforts to continually elevate our products and services


Easy and Feature-packed
Using it since a few years. It is great to give users access via SSo and they can manage their own groups.

Helpful team, great app!
The app works great. The miniOrange team is helpful and prompt in responding to any Technical Questions.

Quick, responsive team!
The plugin works great. I really appreciate the mO team quick responsiveness to all our technical questions. Their expert help in setup and troubleshooting made all the difference.
Integrated Security Suite for Atlassian Cloud
Our product suite offers tailored solutions designed specifically for
Atlassian environments,
ensuring seamless compatibility and integration.














