Need Help? We are right here!
Search Results:
×Privileged Remote Access allows authorized individuals to remotely connect to critical resources, systems, and accounts while implementing stringent security measures. It ensures seamless and secure system management with no VPNs, passwords, or the need for extra software.
An additional layer of security can be achieved through biometric or Multi-Factor Authentication (MFA) for smooth and secure operations.
Privileged Remote Access, a crucial component of Privilege Access Management (PAM) provides organizations with control over third-party vendor access and internal remote access, without compromising security. It aligns with Zero Trust principles, offering secure remote access for privileged users.
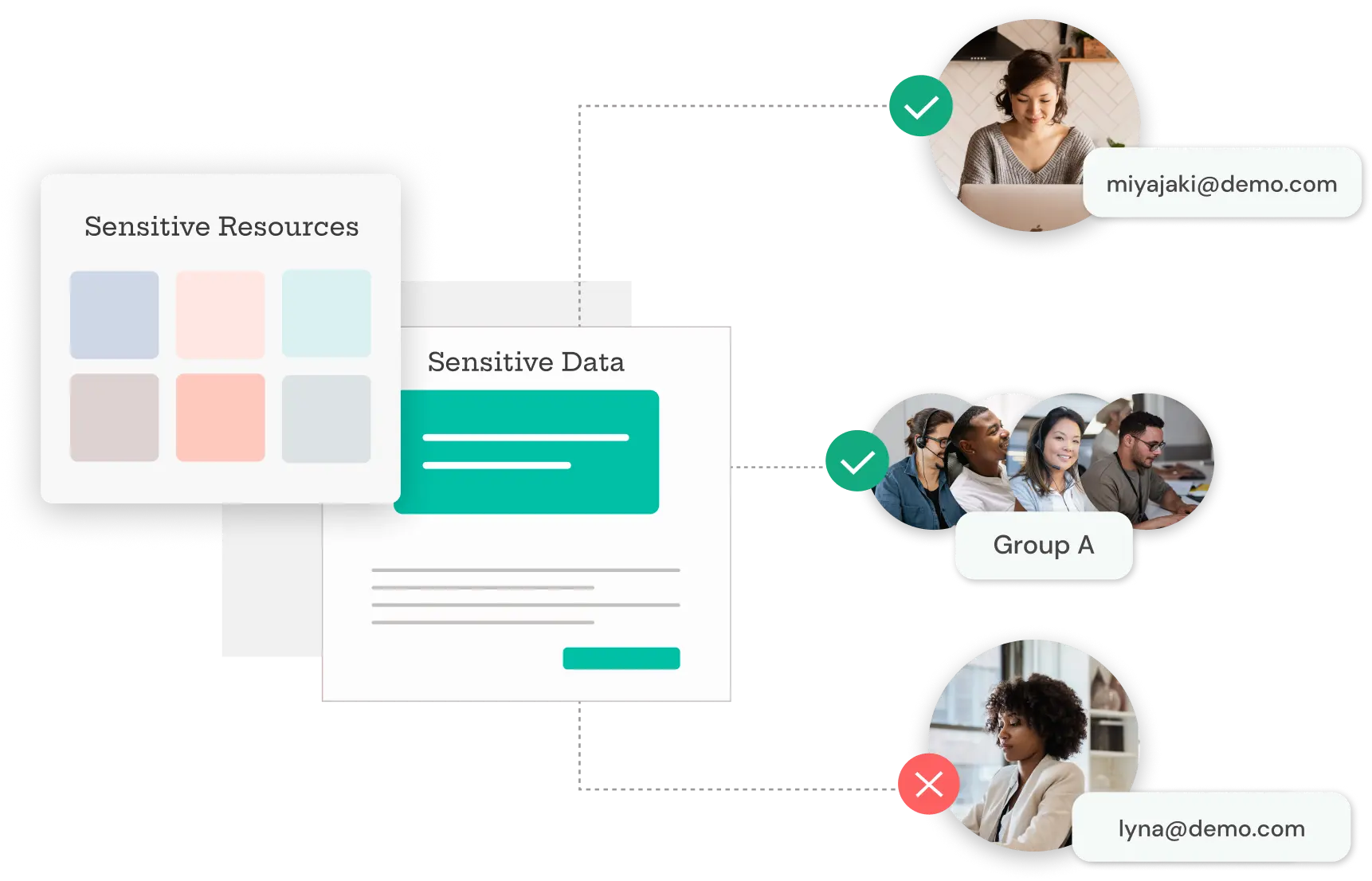
Grants users the precise level of remote access they require for specific moments, or tasks enhancing security, and reducing the overexposure of data and resources.
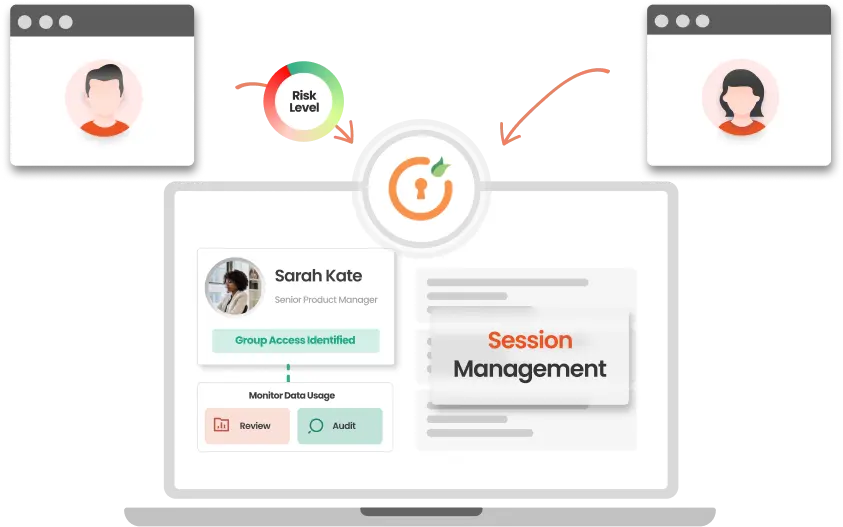
Privileged Remote Access management provides a full solution for the secure management of privileged sessions.
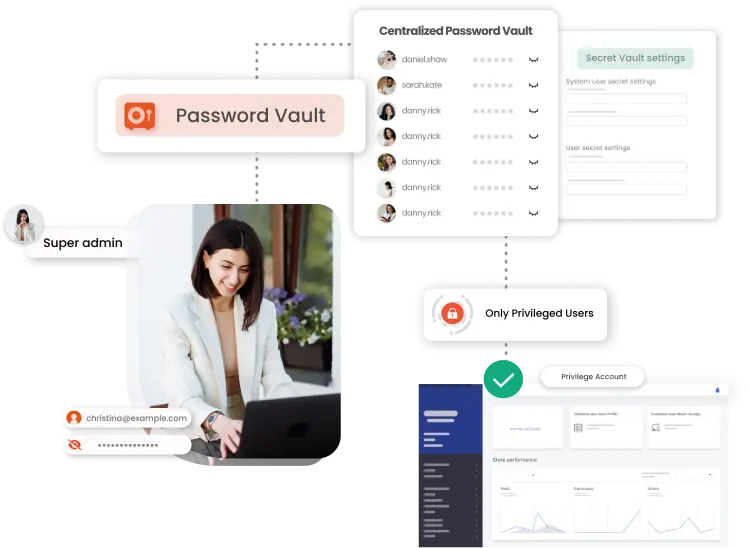
Privileged Password Vaulting guarantees secure management of privileged credentials, automating their rotation and integration for remote sessions.
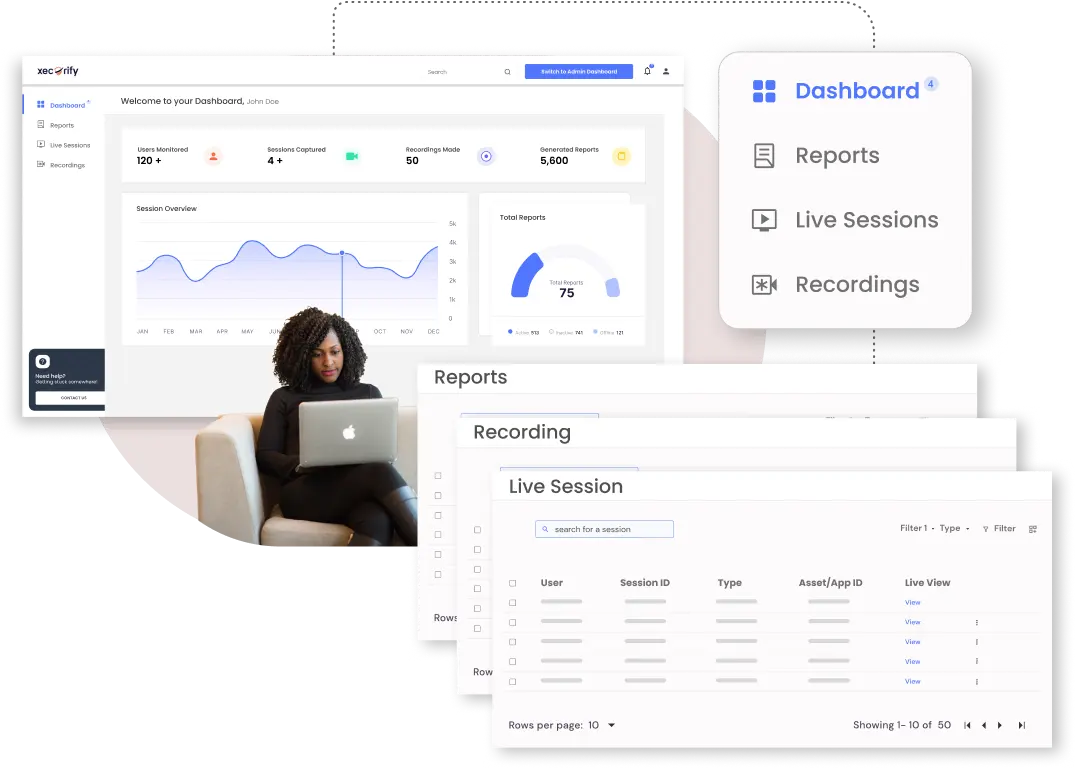
Get detailed audit trails, real-time session data capture, and post-session analysis for compliance and reporting.

This feature centralizes tracking, approval, and auditing of privileged accounts while incorporating a 'just in time' access pathway. By dynamically granting access only when needed, it reduces the attack surface by creating a single access pathway.

Safeguard for Privileged Sessions offers strong control with detailed session recording, supporting various protocols like RDP, VNC, HTTP/S, and SSH for monitoring and accountability.
Privilege Remote Access provides a secure and controlled environment for remote access, ensuring that only authorized users can utilize critical resources thus reducing the risk of data breaches.
Enables authorized users to remotely access, and manage systems and resources, allowing for efficient troubleshooting, maintenance, and administration tasks without physical presence.
Privilege Remote Access eliminates the need for on-site visits or dedicated hardware, reducing travel expenses and infrastructure costs.
It provides a centralized platform to manage and monitor remote access, allowing administrators to enforce access policies, track user activities, and maintain better control over privileged accounts.
Privileged remote access facilitates work-from-home arrangements, disaster recovery situations, and supporting geographically distributed teams.
Through Privilege Remote Access organizations can enforce least privilege principles, limiting user access to only the necessary resources and reducing the potential attack surface, thereby mitigating security risks.
Privileged Access Management seamlessly integrates into your existing infrastructure, ensuring secure and
managed access to critical systems

I can't speak highly enough regarding miniOrange, I am totally satisfied with the process and results in every regard.
5.0

Awesome tech service, Awesome product. Overall Awesome people. This solution is very simple and easy to implement
5.0
Privilege remote access is important for ensuring that IT operations run smoothly and that any issues with critical resources can be quickly resolved. This capability is crucial for the long-term success and security of your organization, as it allows for the secure management and support of systems by authorized personnel, regardless of their geographical location.
The best practices for managing Privileged Remote Access management primarily focus on ensuring secure, controlled, and auditable access to critical resources.
Some of the Key practices include:
The Principle of least Privileges: Grant users the minimum level of access necessary for their role or task to reduce the risk of unauthorized access or breaches.
Multi-Factor Authentication (MFA): Implement MFA to add a layer of security, verifying the identity of users accessing privileged accounts.
Session Monitoring and Recording: Monitor and record sessions in real-time to detect suspicious activities and for audit purposes, ensuring accountability.
Regular Access Reviews: Conduct frequent reviews of privileged access rights to ensure they are still necessary and revoke any that are no longer required.
Privileged Access Management (PAM) Solution: Deploy a comprehensive PAM solution provider such as miniOrange to automate the enforcement of these best practices, streamline privileged access workflows, and provide a centralized platform for managing and monitoring privileged access.
Implementing privileged remote access involves a few steps to ensure secure and efficient control over your organization's critical resources.
1. First, choose a reliable privileged remote access solution, like miniOrange, which offers comprehensive features for secure access management.
2. Define your access policies and requirements, focusing on who needs access, what level of access they require, and under which circumstances.
3. Integrate the solution with your existing IT infrastructure, ensuring compatibility with your systems and applications.
4. Set up multi-factor authentication (MFA) to add an extra layer of security, ensuring that only authorized users gain access.
5. Finally, conduct regular audits and reviews to refine access controls and policies regularly.
By following these steps, you can establish a robust privileged remote access system that enhances your organization's security posture.

Our Other Identity & Access Management Products