How to restrict access to Google Apps & Services using miniOrange CASB
Restricting access to Google apps and services helps protect sensitive business information, maintain data privacy, and prevent unauthorized users from accessing your digital workspace. In this guide, we’ll show you the step-by-step process to implement a miniOrange CASB to restrict access to your favorite Google apps and services.
Step 1: Sign up with miniOrange CASB
Step 2: Configure your Identity Provider
- Sign in to miniOrange IAM using the same credentials as the CASB dashboard and navigate to the Apps section.
(In this guide, we are using miniOrange as the IDP, but you can contact us at proxysupport@xecurify.com to set up your preferred IDP.)
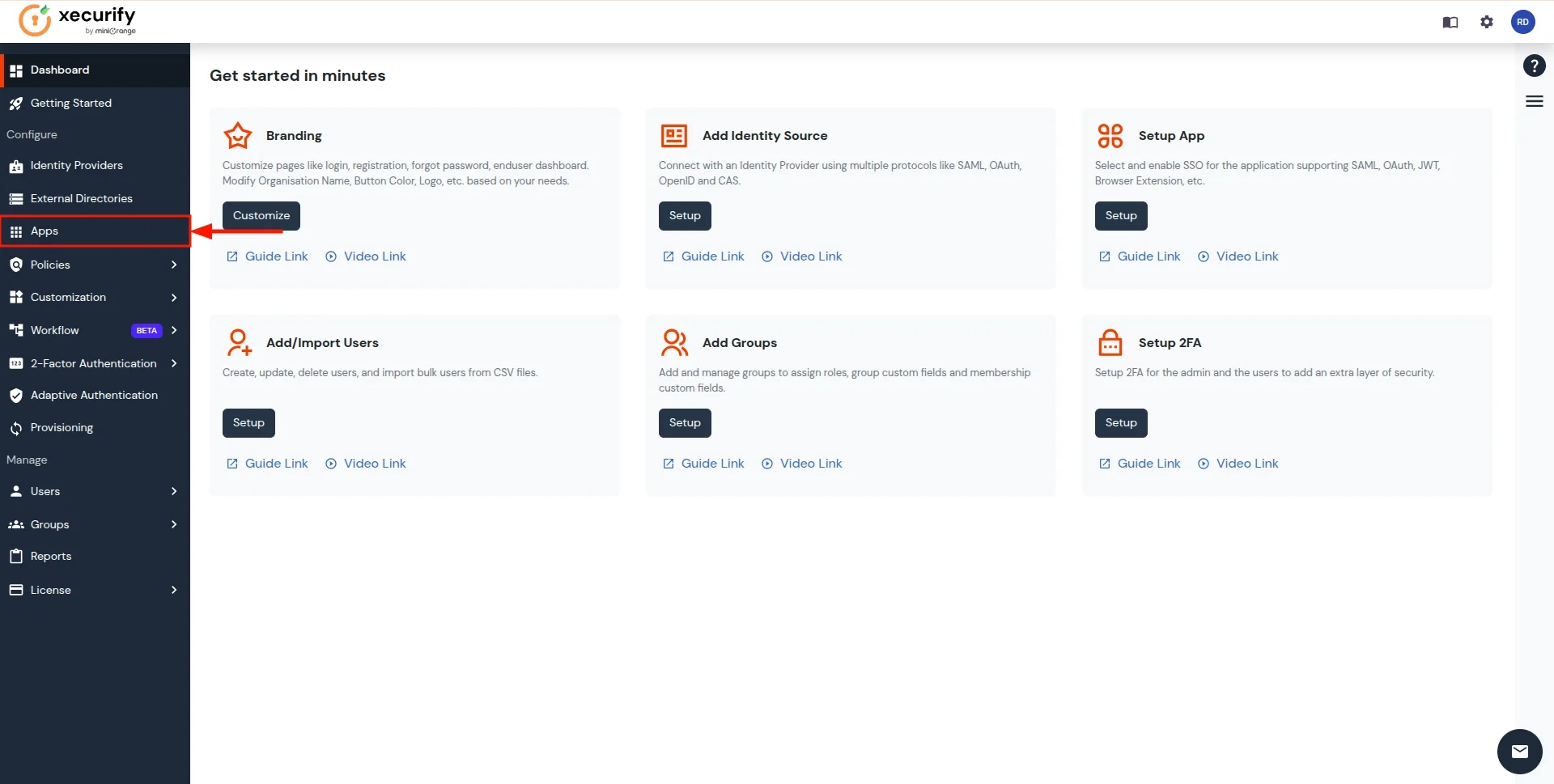
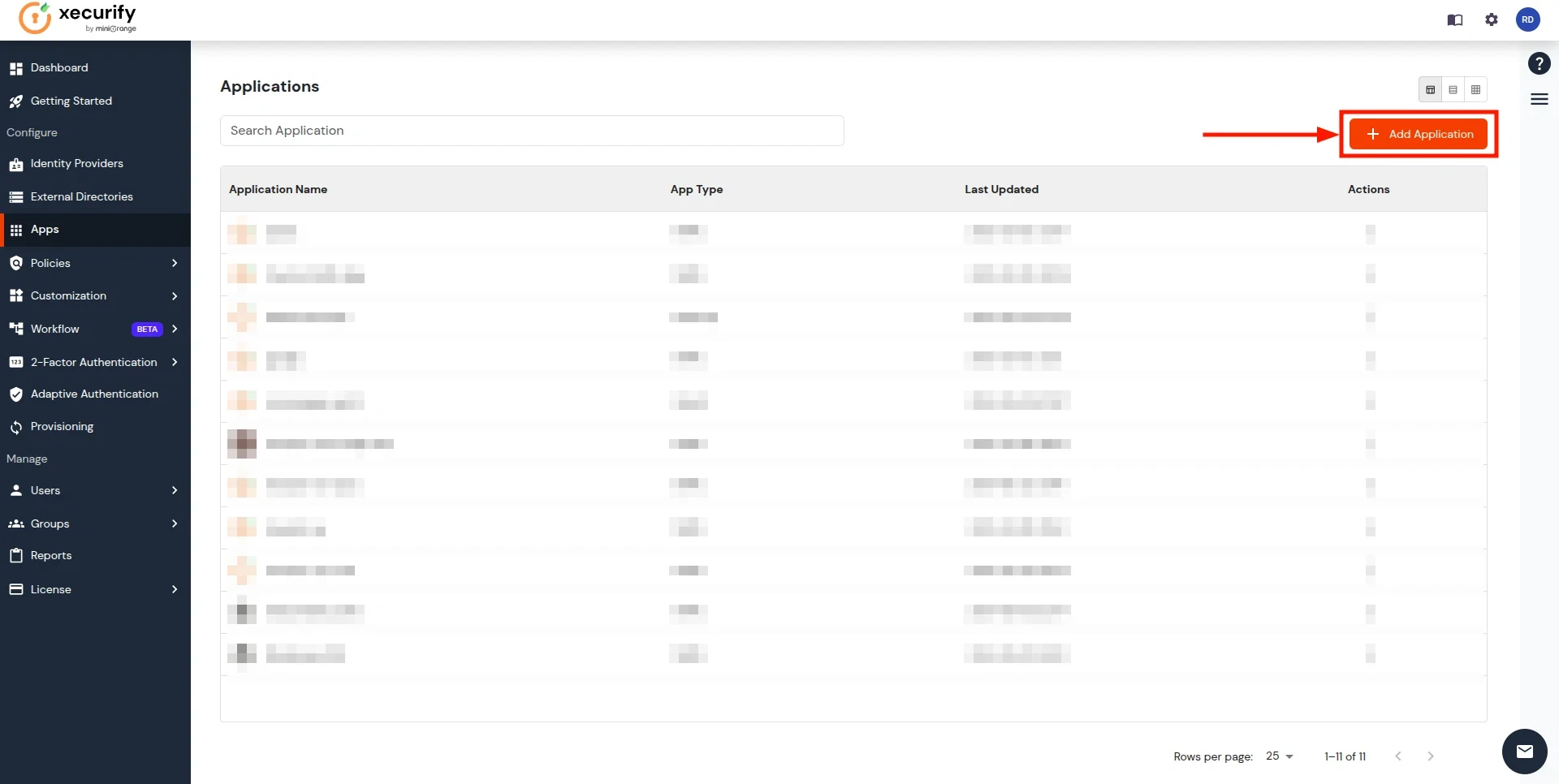
- You will see a list of all configured applications. Click Add Application to create a new one.
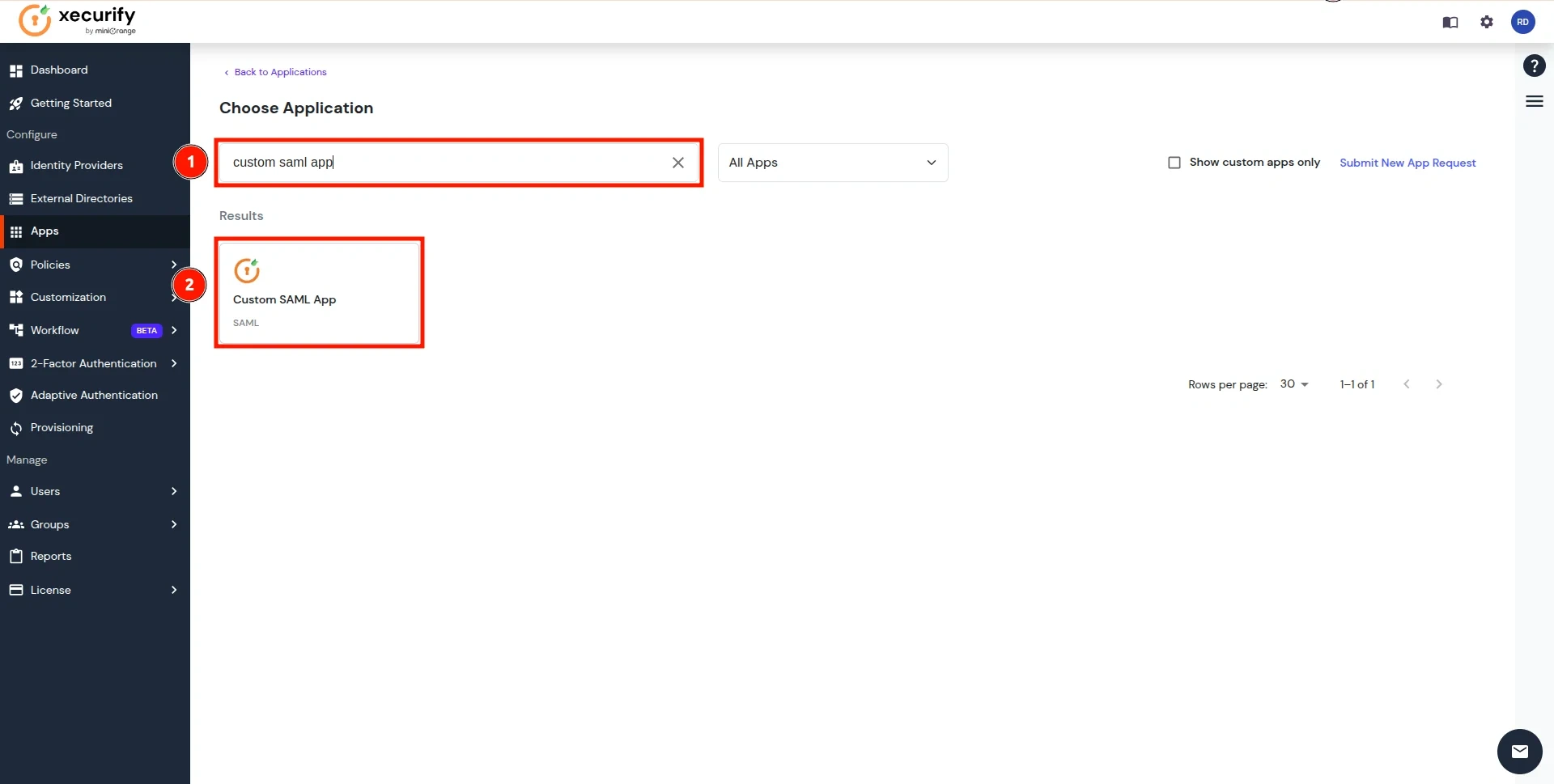
- Search for the Custom SAML App in the search box and click on it.
- Enter a custom application name and click on the Import SP Metadata button in the right corner.
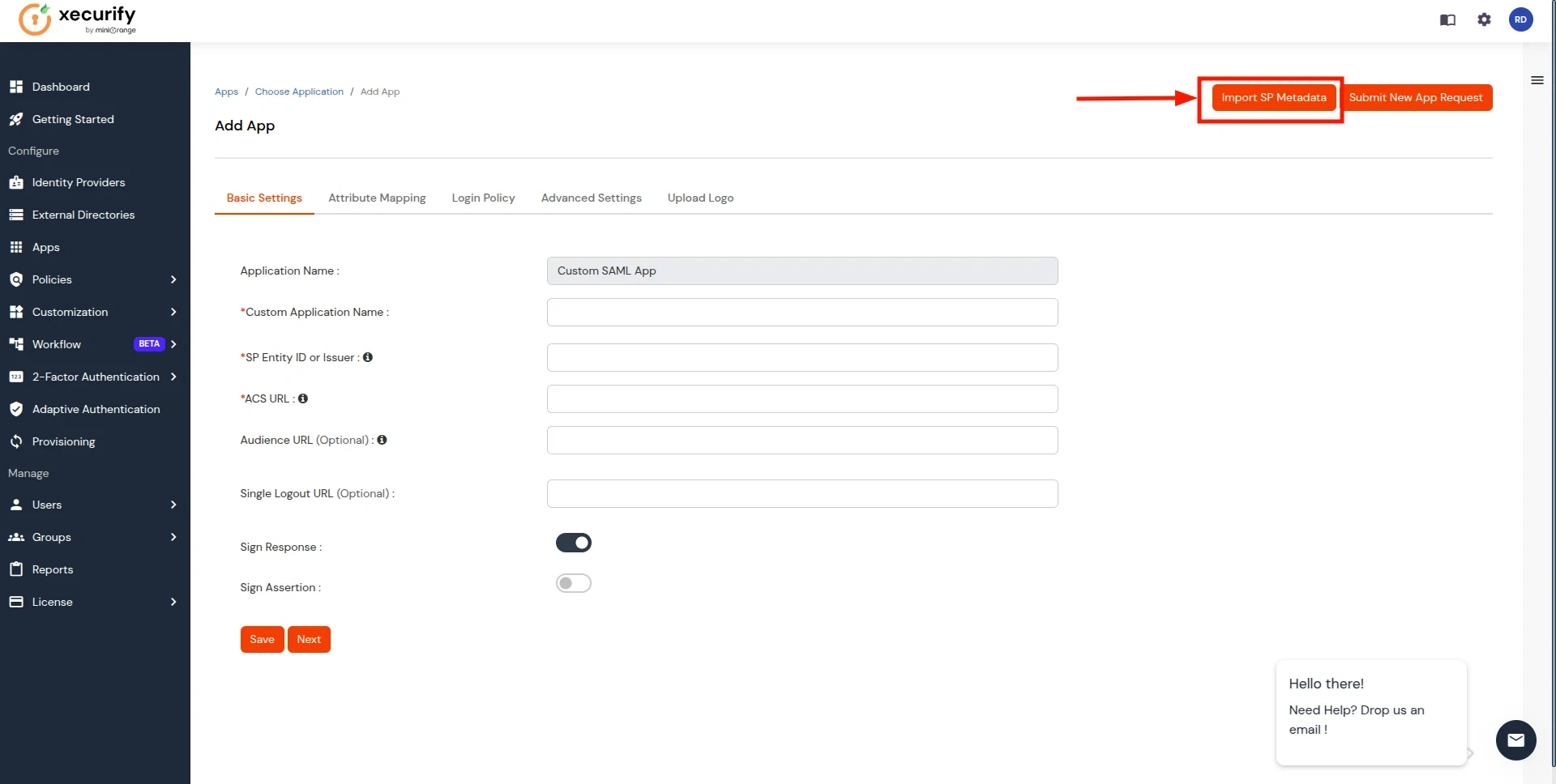
- Add the App Name, and select the file option in SP Metadata. Next, click on the Choose File button. Select the file downloaded in Step 4 and click on Import Button.
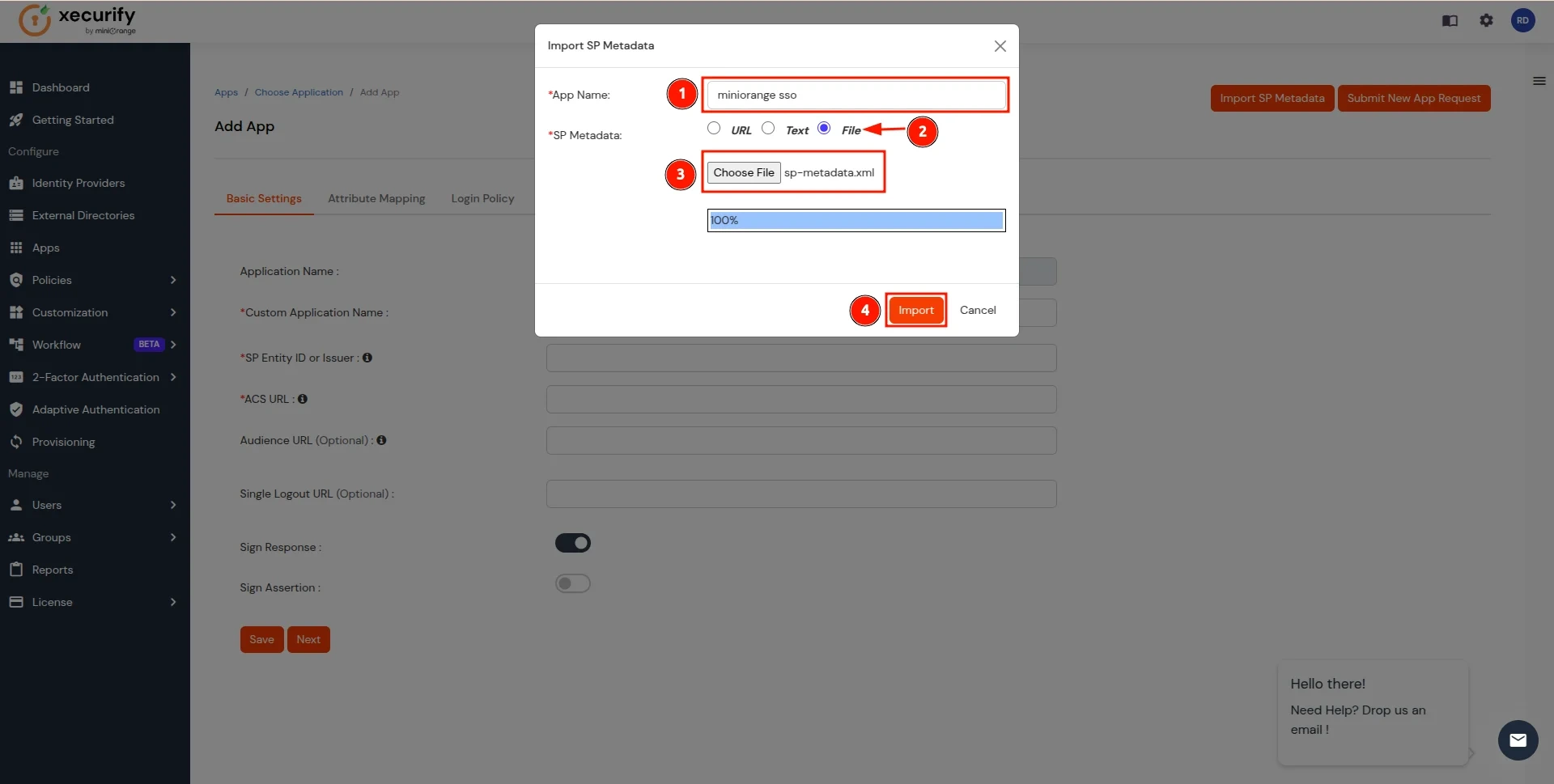
- After the file is successfully uploaded, Click on Next Button.
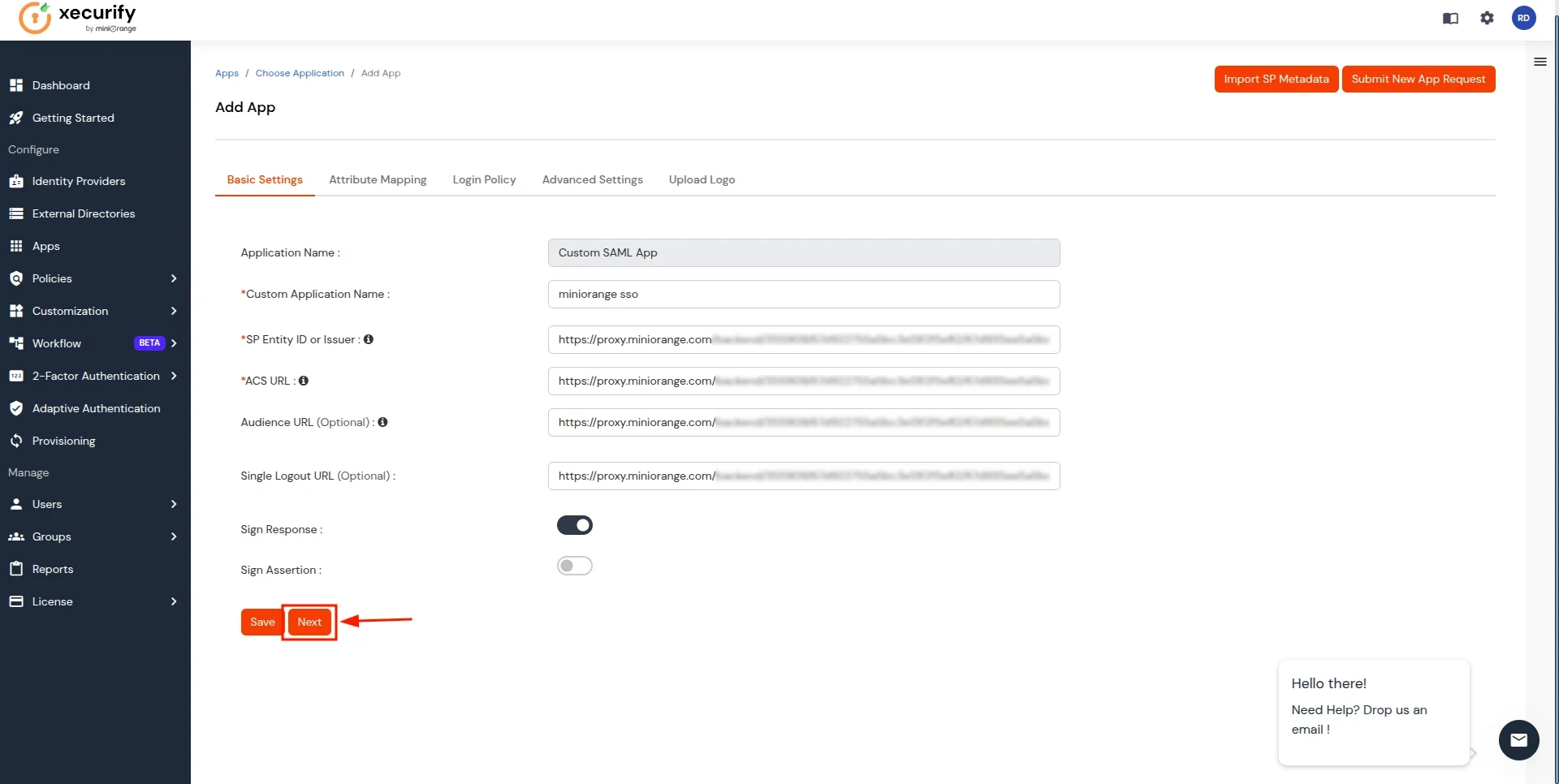
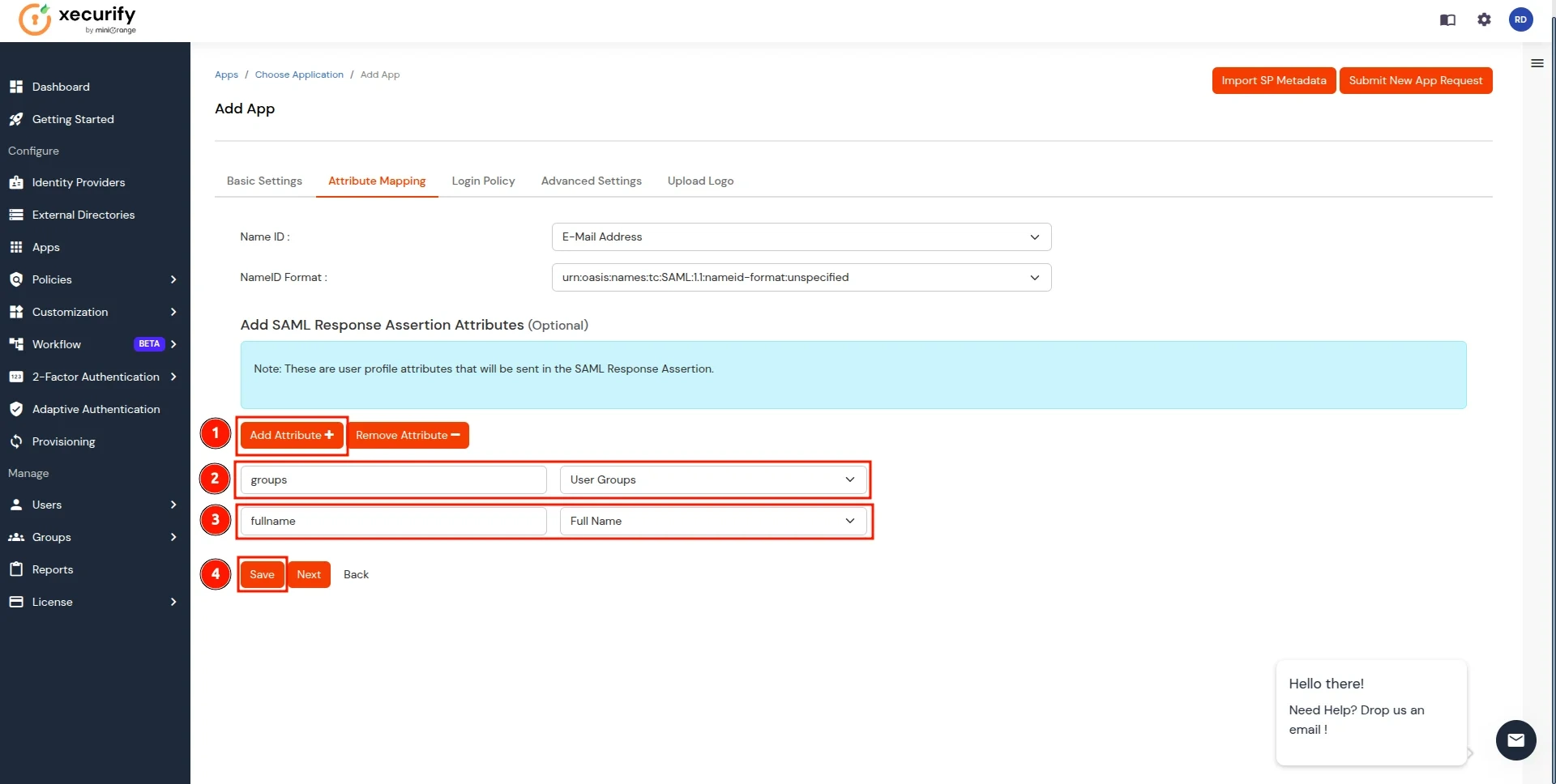
- In the Attribute Mapping section, follow these steps:
- Click on the Add Attribute button.
- Enter groups as the Attribute Name and select User Groups as the Attribute Value.
- Add another attribute by clicking Add Attribute again.
- Enter fullname as the Attribute Name and select Full Name as the Attribute Value.
- Click on the Save button to apply the changes.
- Now you will be redirected to the Applications, screen where your configured application will be listed. Click on the three dots next to the application and select the Metadata option.
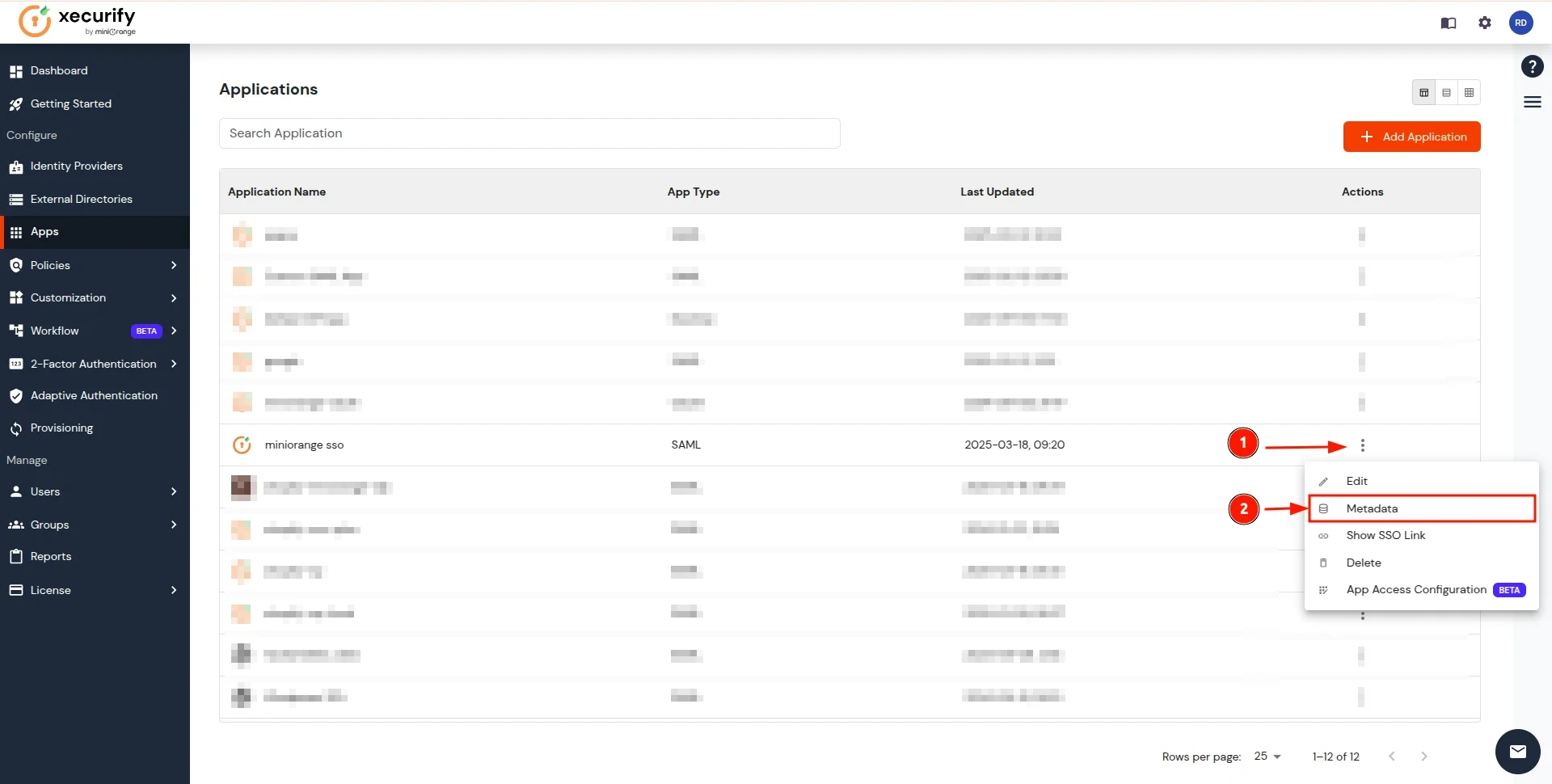
- In the View IDP Metadata section, click on the copy to clipboard next to the Metadata URL to copy it.
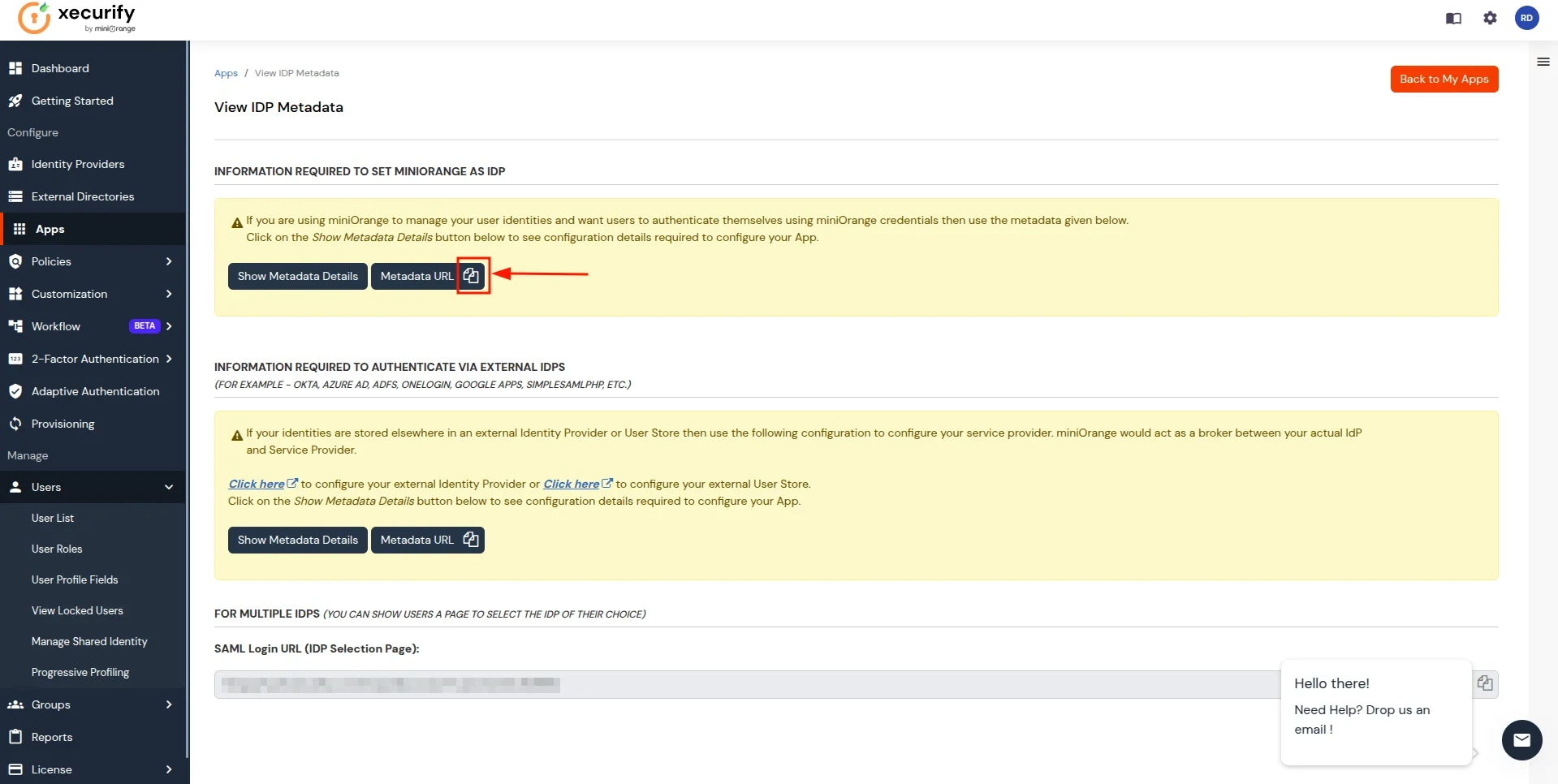
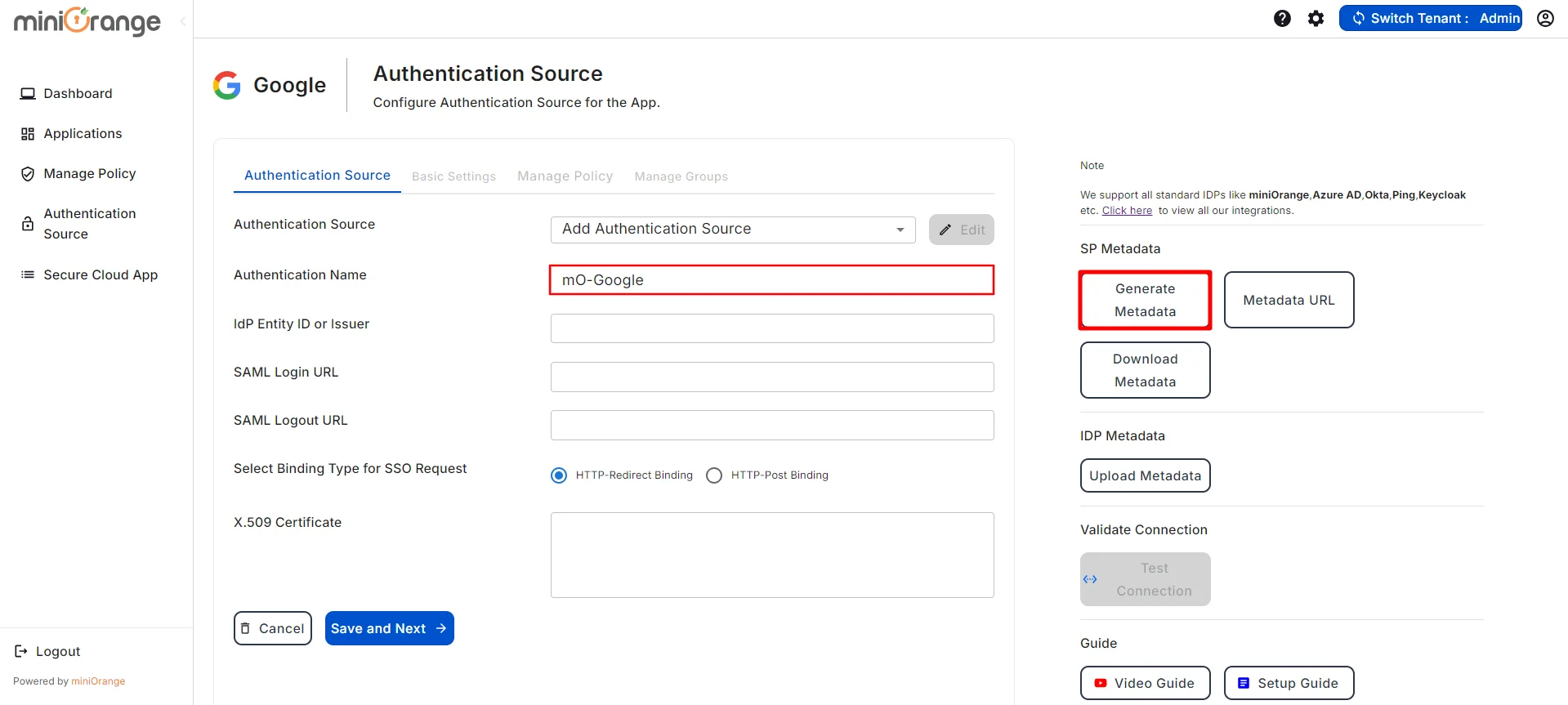
- Return to the CASB Dashboard tab, in the Configure Authentication Source section, locate the IDP Metadata section, and click on Upload Metadata.
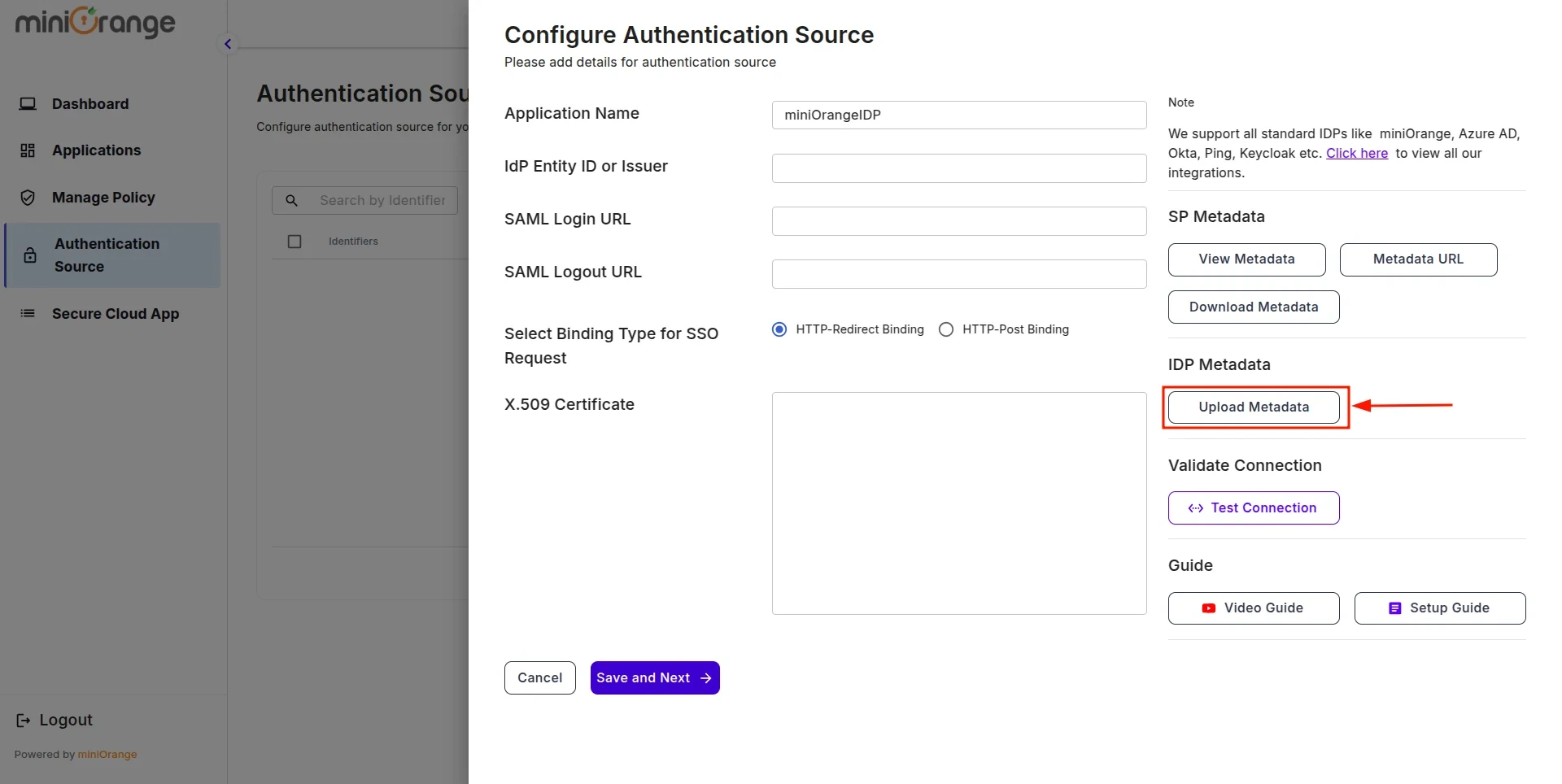
- In Import IDP Metadata, select Import Format as URL, add IDP Metadata url copied from miniOrange IDP, and click the Import button.
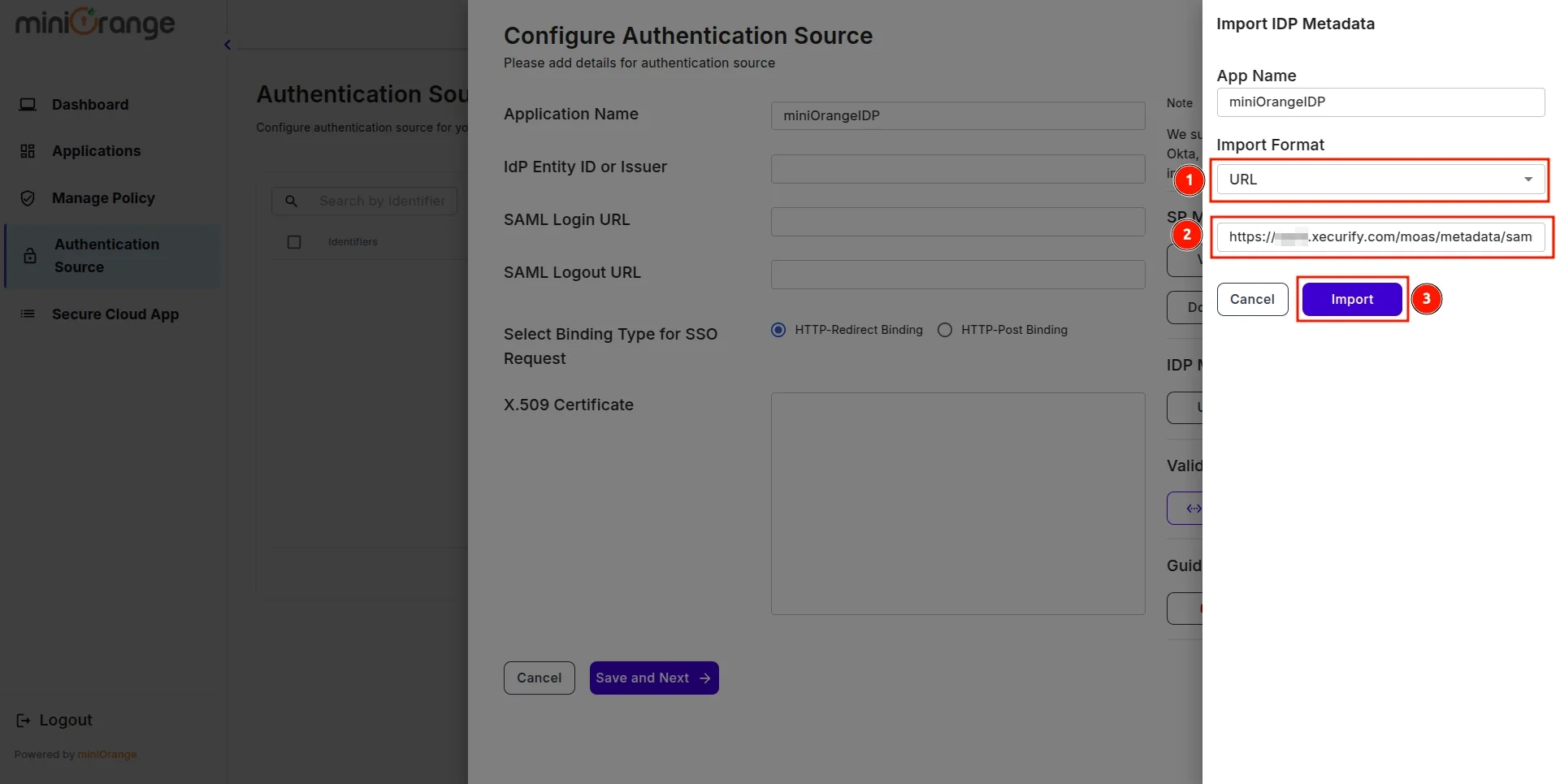
- A prompt will appear confirming that the metadata has been uploaded successfully. Click Save to finalize the configuration.
- Now, return to miniOrange IDP, click on the Users tab in the navigation menu on the left and select User List.
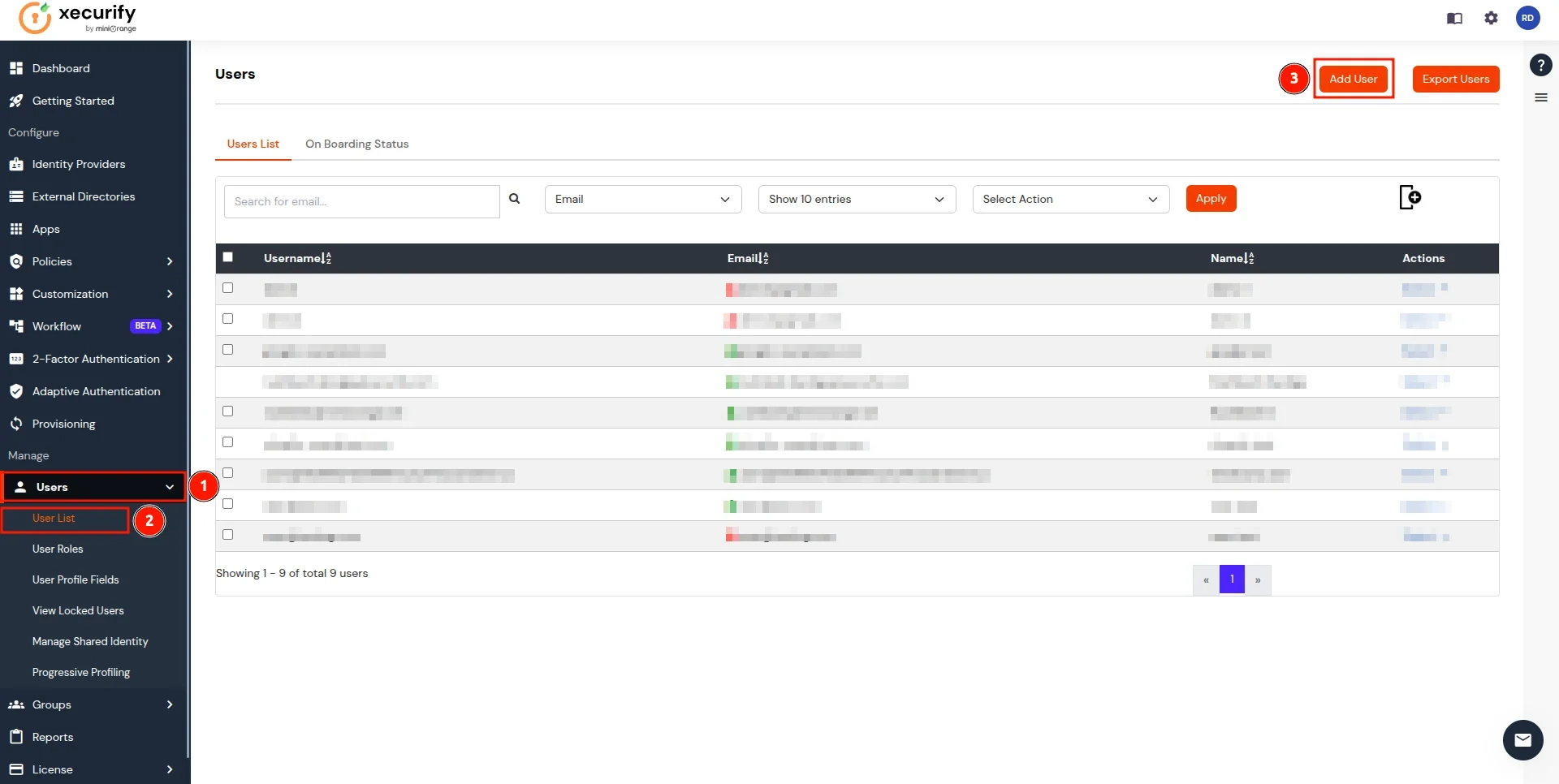
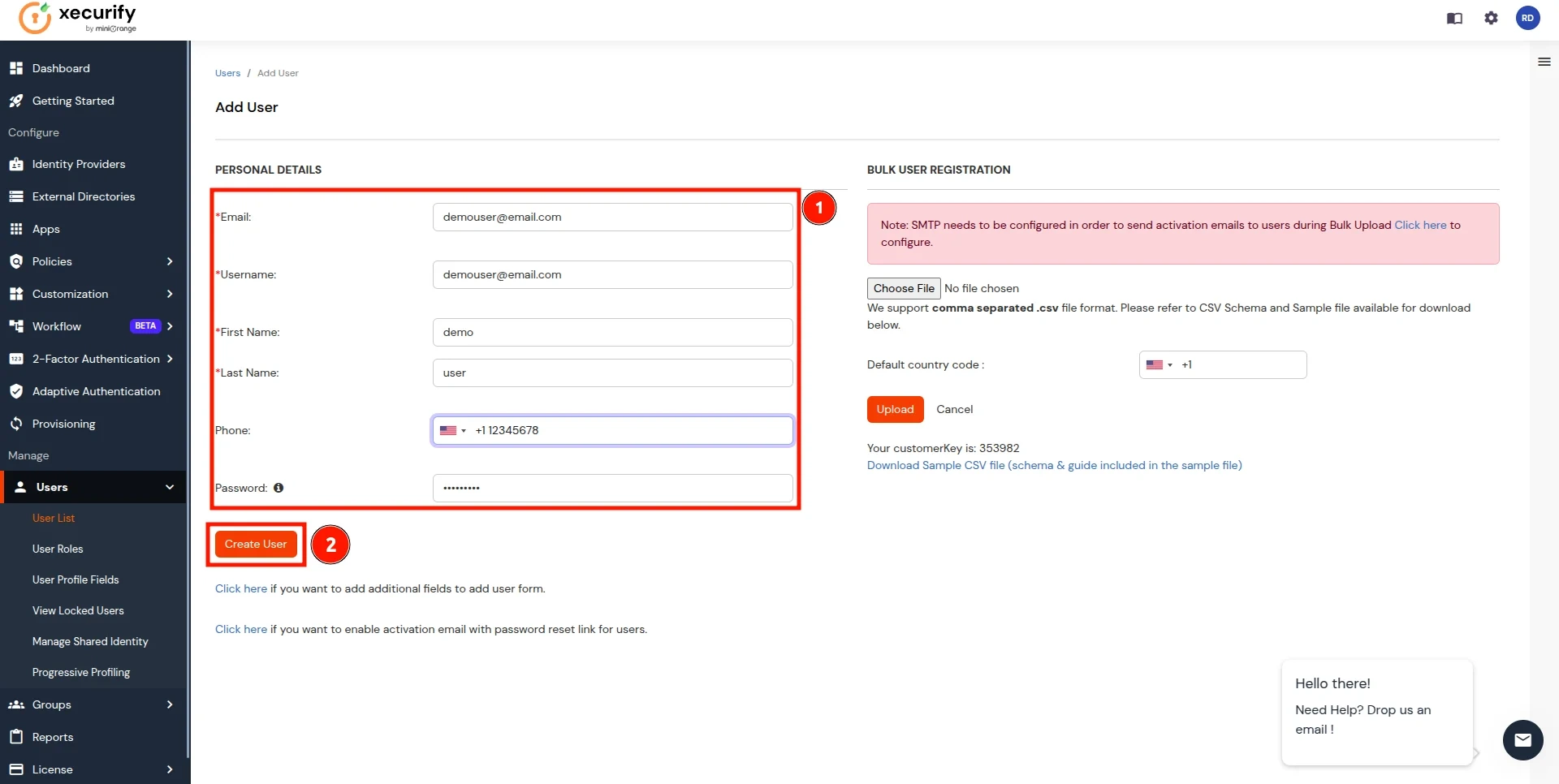
- In the Add User page, add the user's personal details like Email, Username, First Name, Last Name, Phone and Password and click on the Create User Button. (To add multiple users, use Bulk User Registration feature)
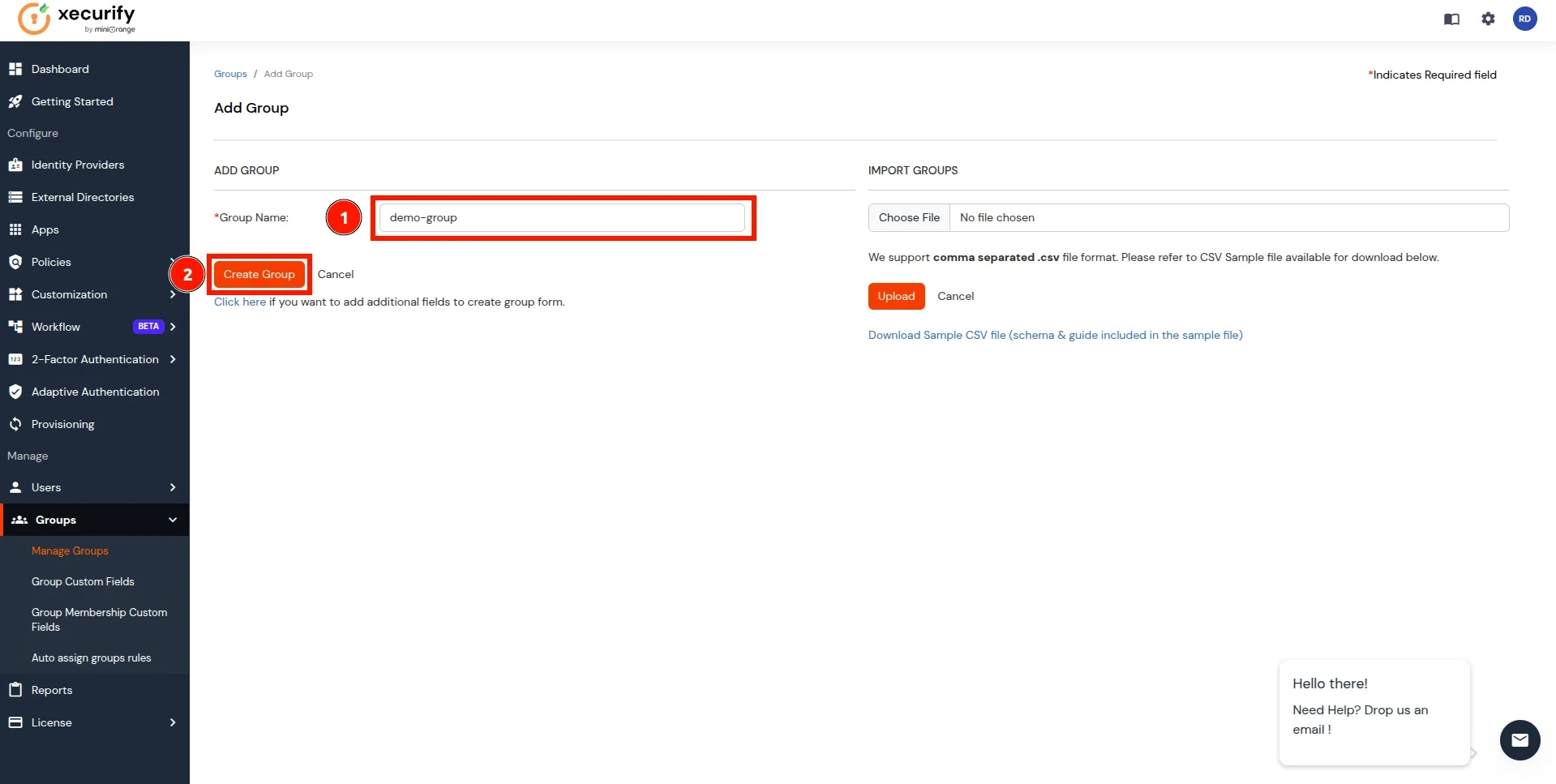
- Now, go to the Groups tab, select Manage Groups, and click on the Create Group button.
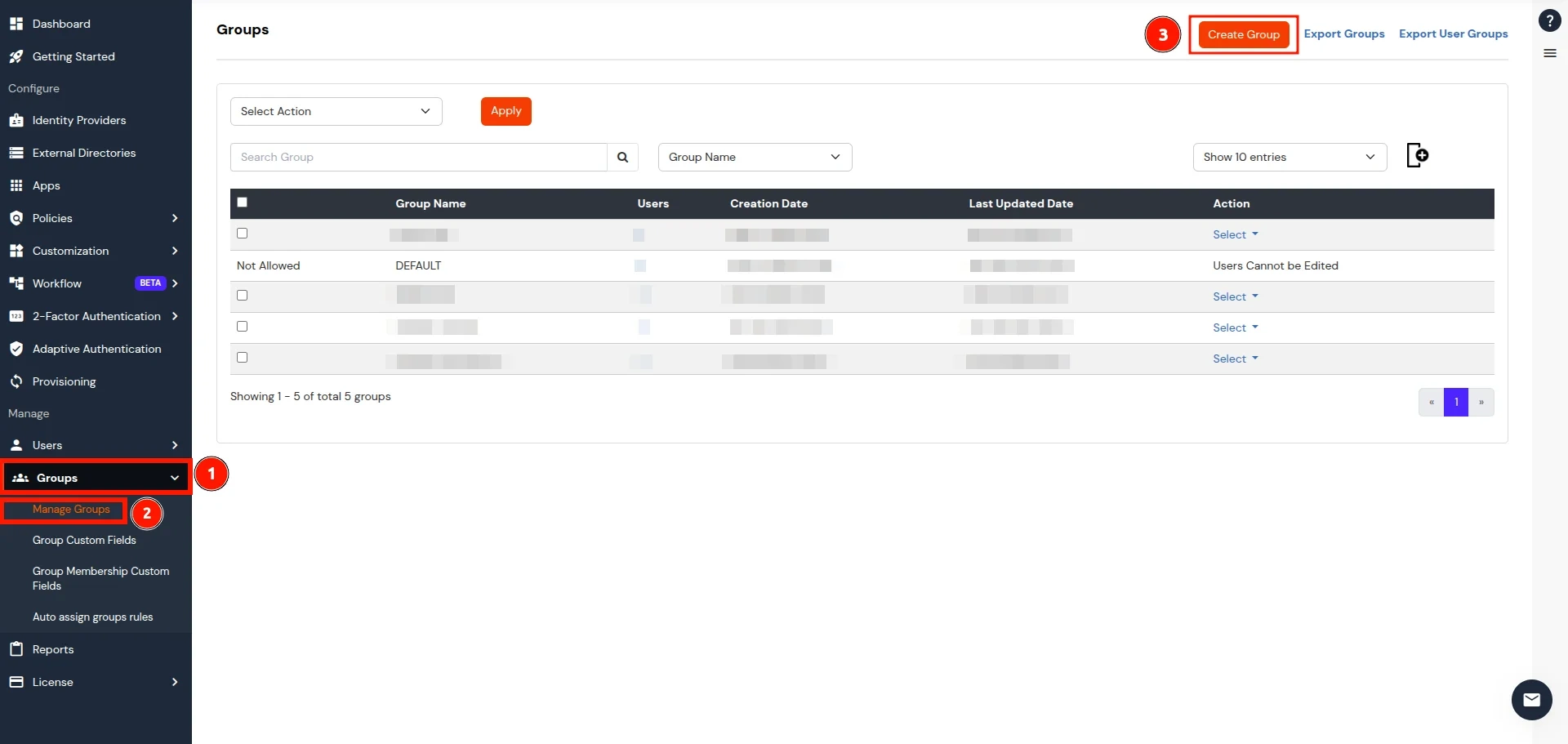
- In the Add Group section, enter a name for the group in the Group Name field and click on the Create Group button.
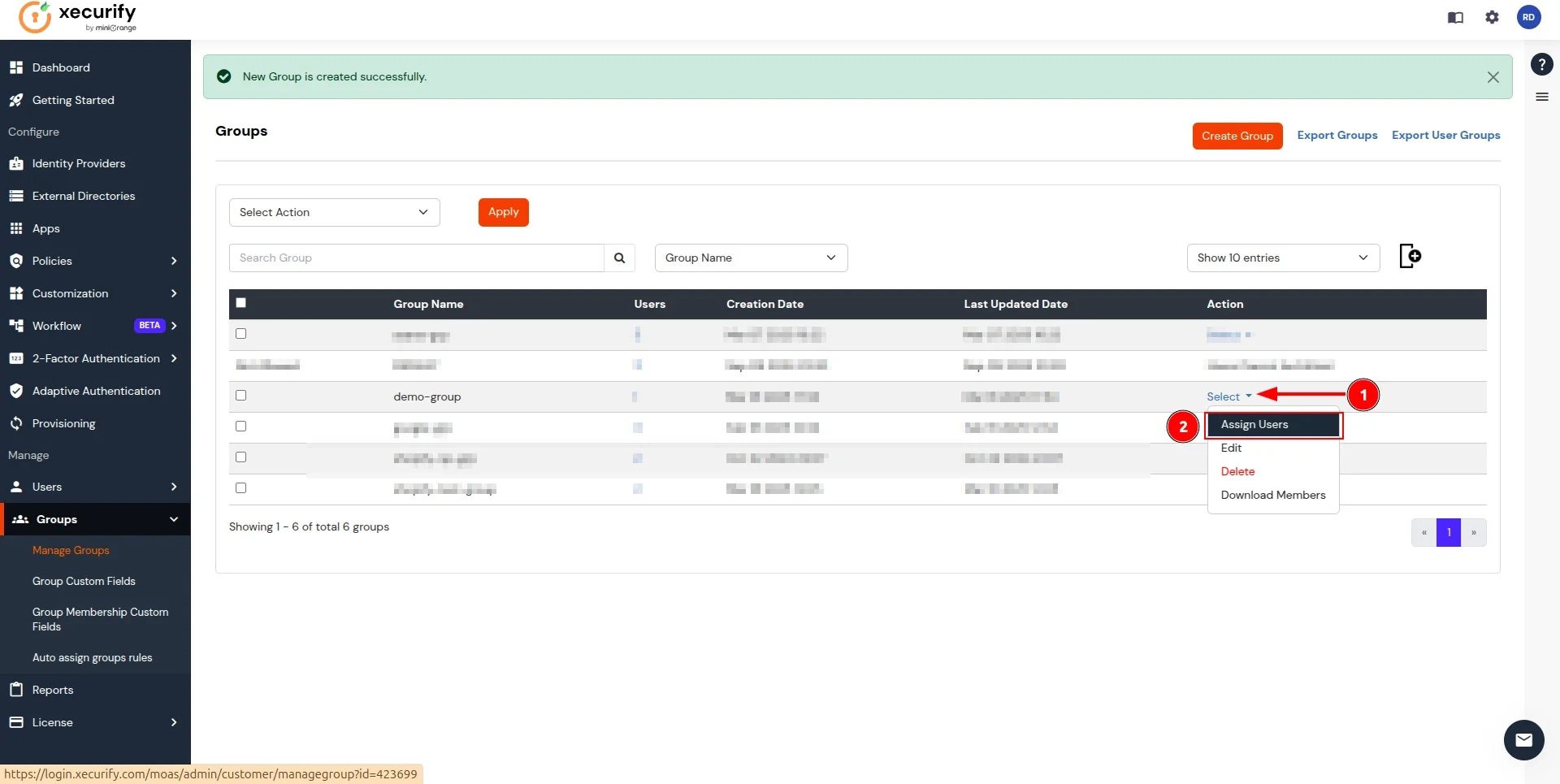
- In the Manage Groups section, search for the newly created group and click on the select button next to it. Click on Assign Users option in the dropdown.
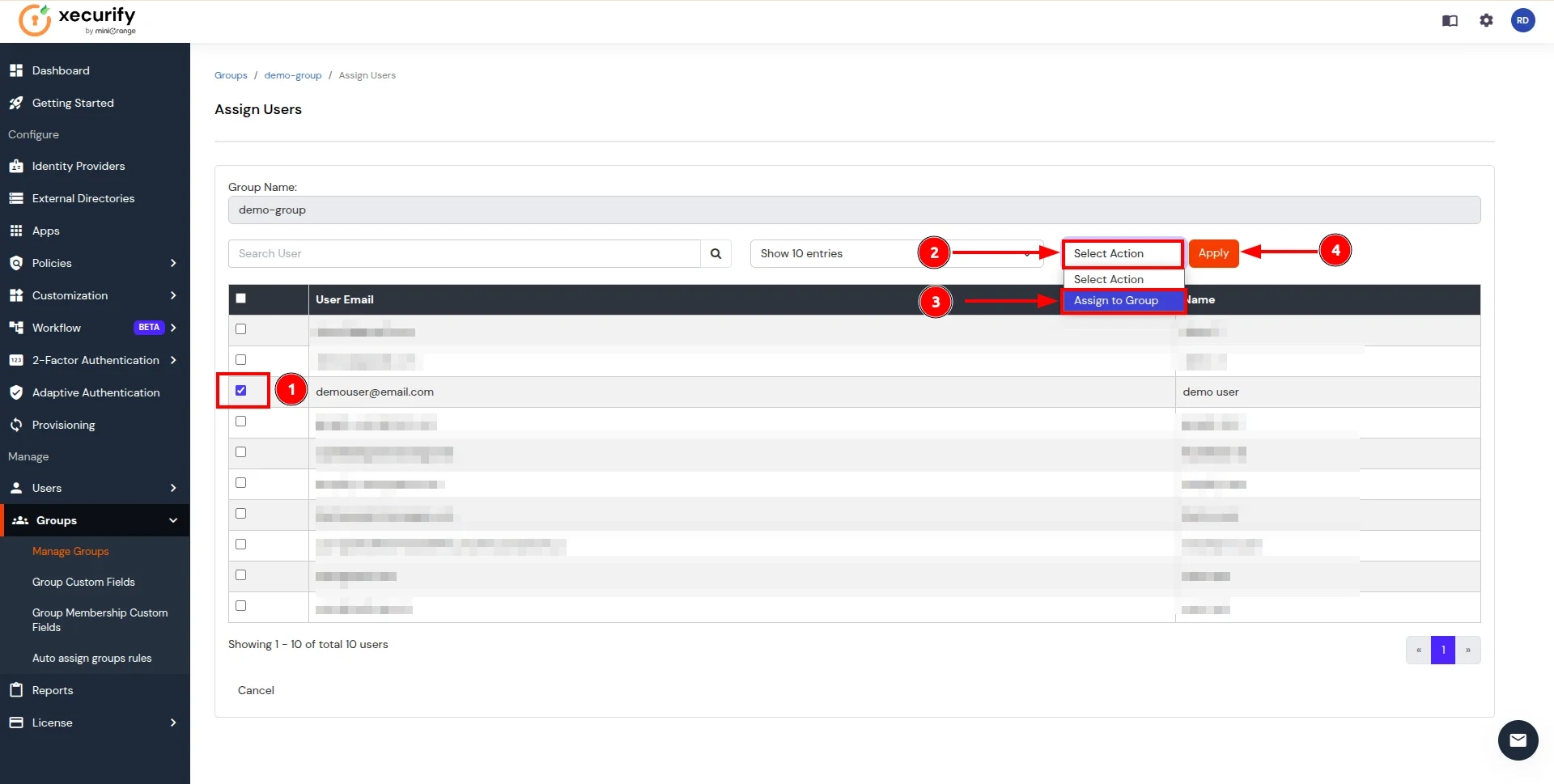
- On the Assign Users page, follow these steps:
- select the checkbox for the user created in here.
- Click on the Select Action button and choose Assign to group.
- Click Apply to add users to the group.
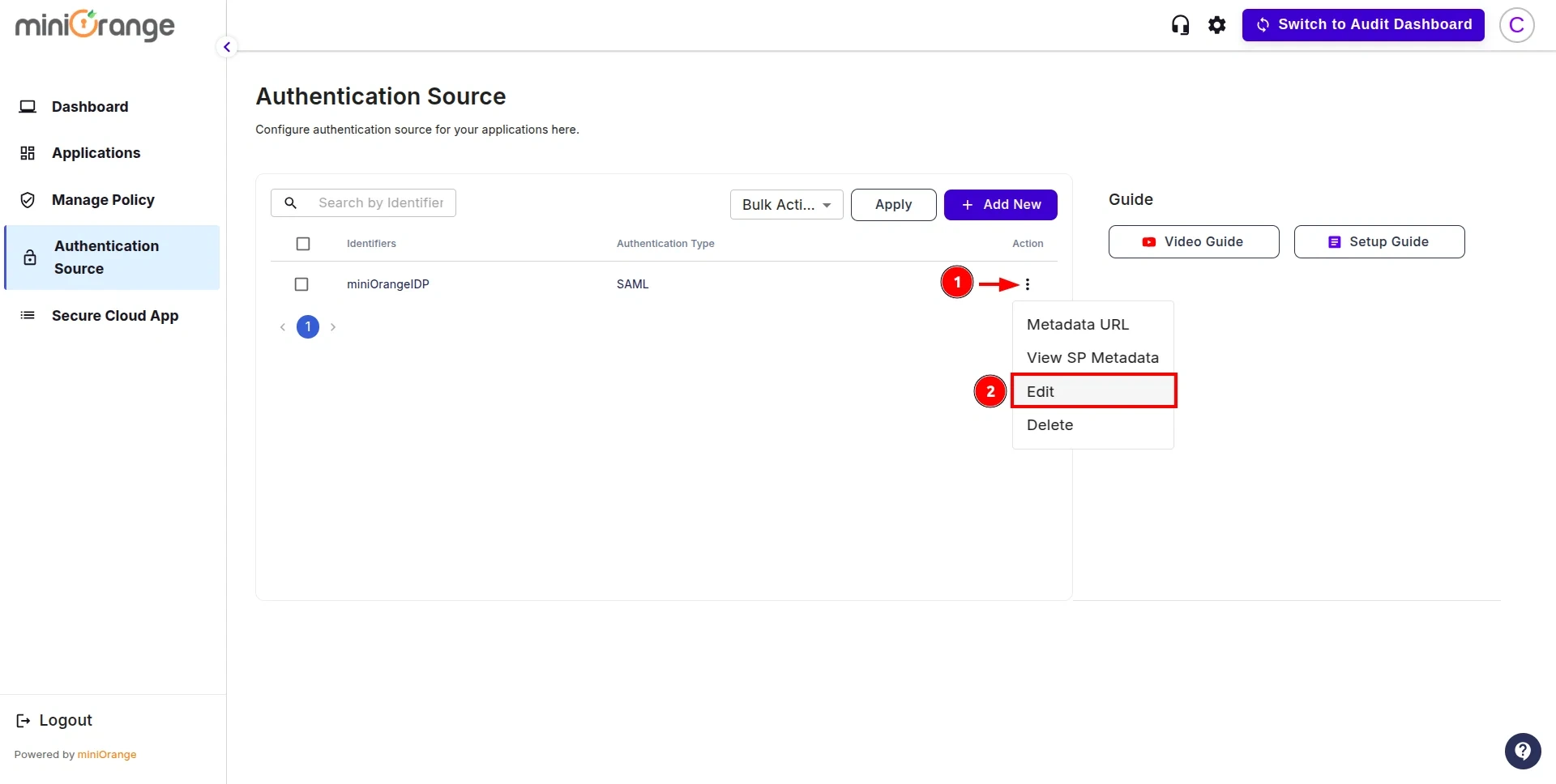
- Now, return to the CASB Dashboard and click on Edit in the action button for the Authentication Source.
- Click on the Test Connection button.
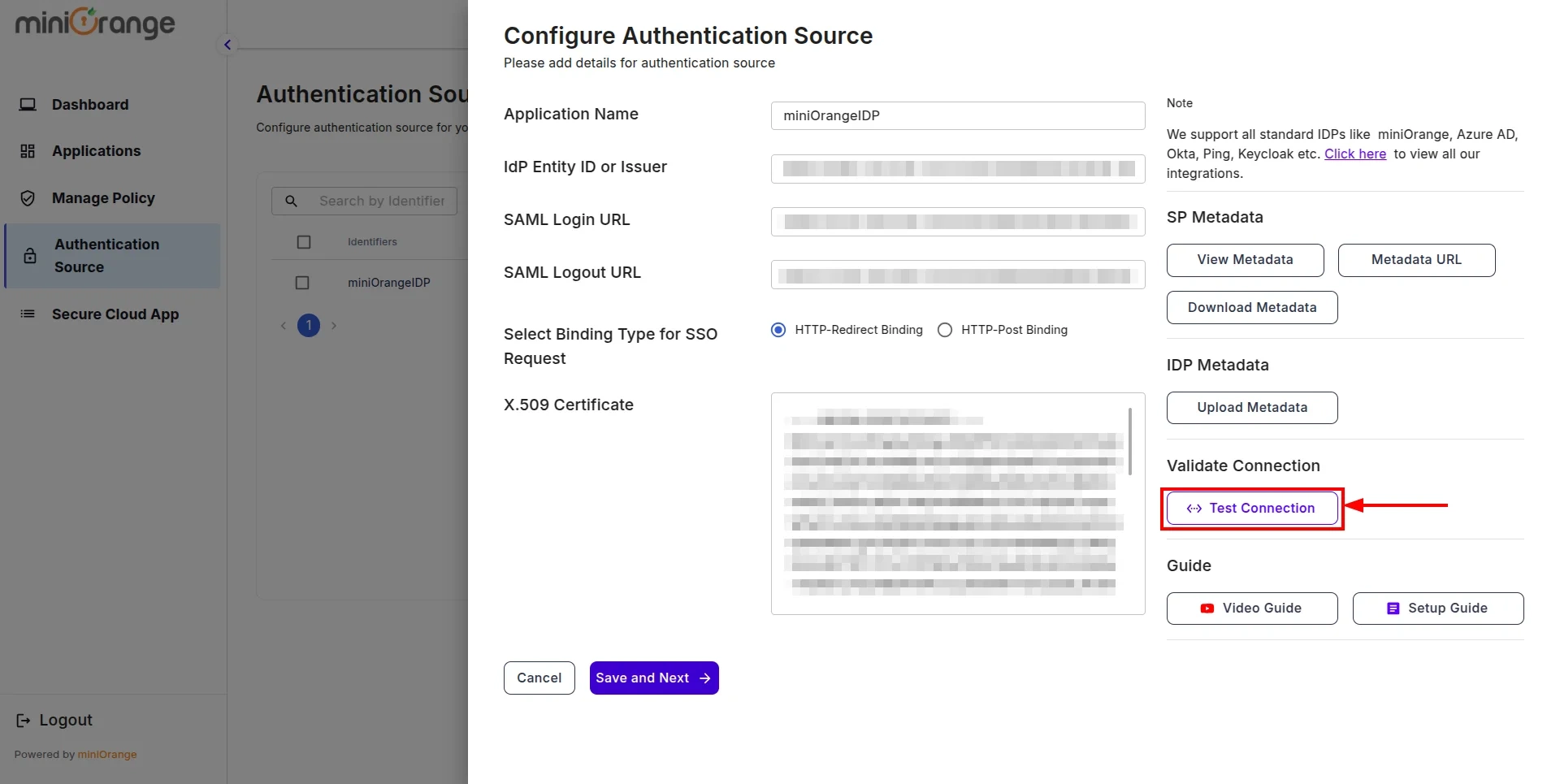
- You will be redirected to the miniOrange IDP Sign-In screen. Enter the credentials for the user added in the previous steps.
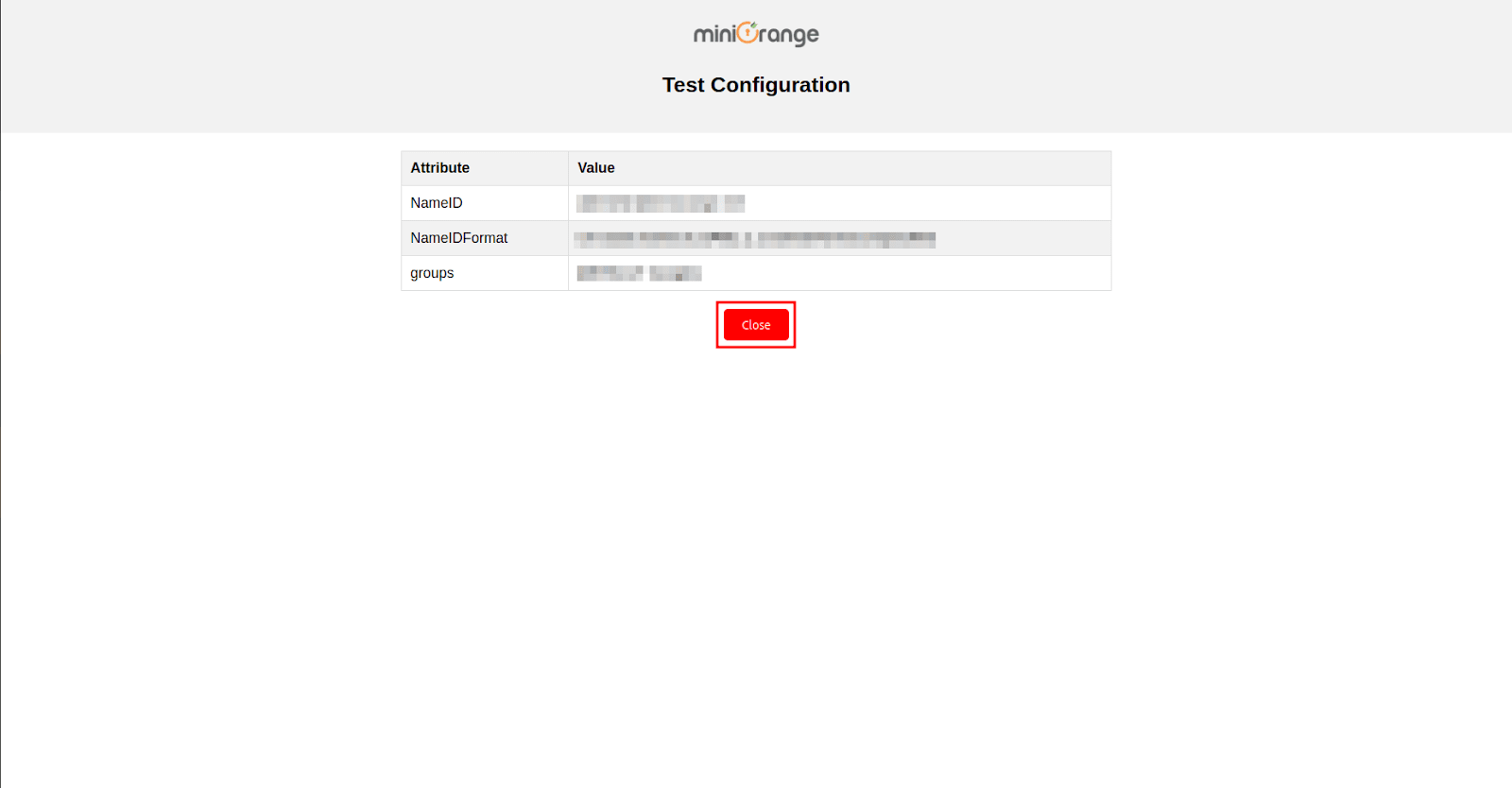
- After successful authentication, you will see a screen displaying Test Connection Details. On the left side, you will find attribute keys, and on the right side, their corresponding values.
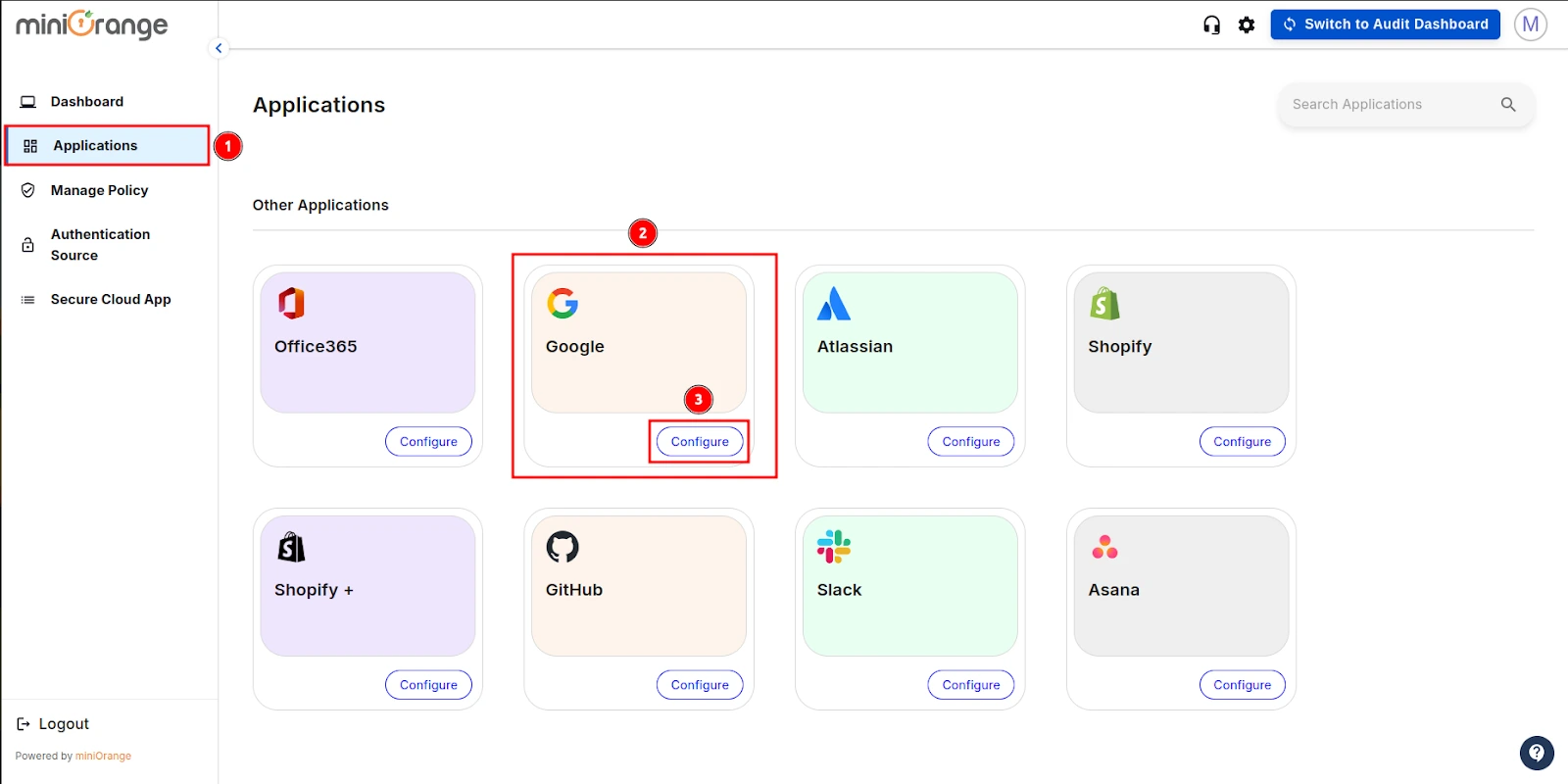
Step 3: Configuring SSO in Google Admin Console
- Once this is done, navigate to the Applications section from the sidebar, go to Google, and click on Configure.
- In this section, open the Authentication Source dropdown, select the authentication source you created earlier, and click Save and Next.
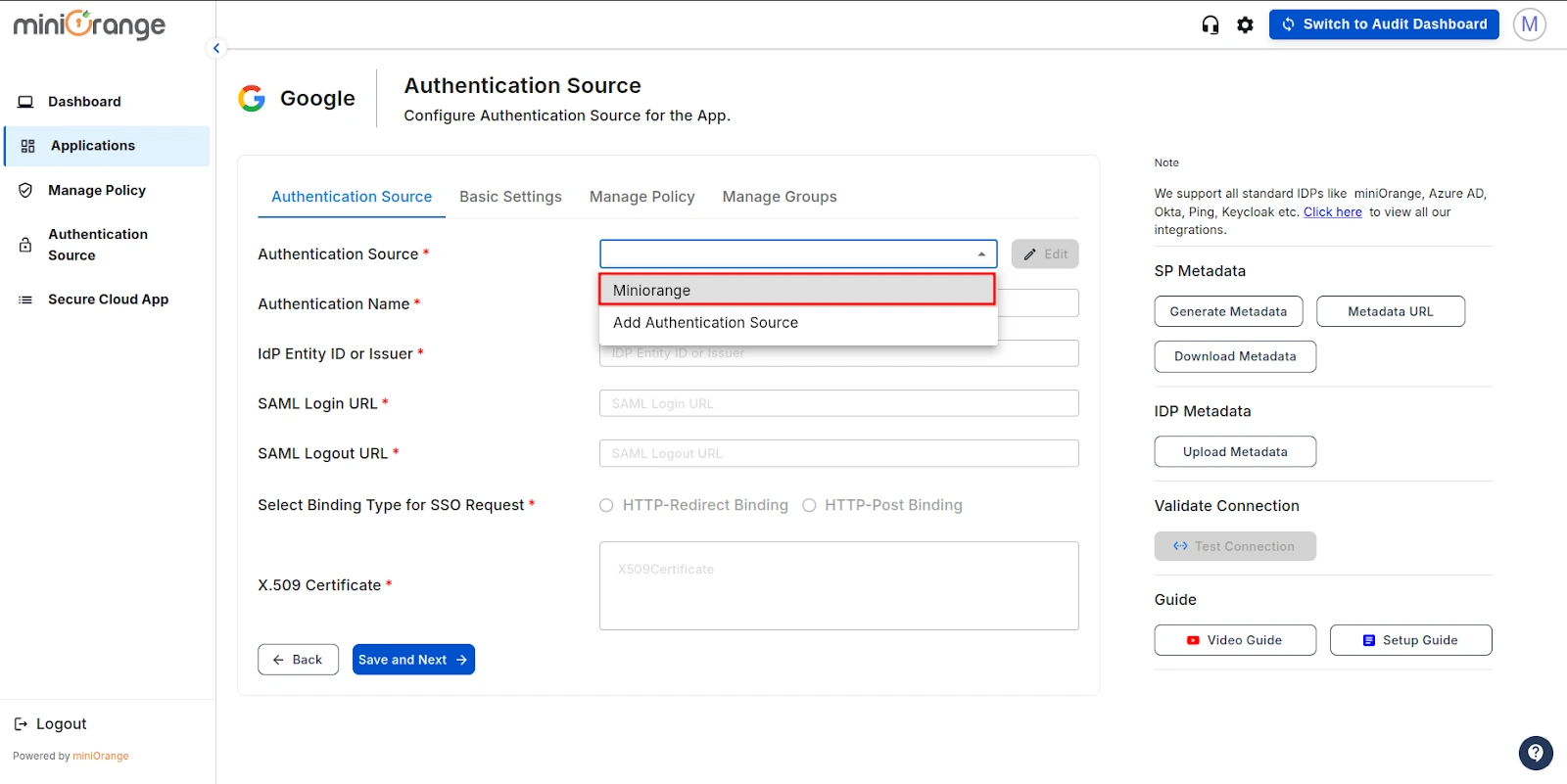
- Now, you will be redirected to the Basic Settings section. Fill in the following details to configure the Google Application:
| Organization Name: |
Enter the name of your organization. |
| Organization Domain: |
Enter your organization's domain on Google. |
| Attribute Key: |
Enter the Group Attribute Key for the SSO app, which you have configured in the IDP under the SAML attribute section. |
| Name Attribute Key: |
Enter the attribute names, such as fname, lname, etc., that you have configured in the earlier steps in the SAML Attributes section. |
| Enter ACS URL: |
You can get the Google ACS URL from the Google admin console. |
| Enter Entity URL: |
You can get the Google Entity URL from the Google admin console. |
| CASB Type |
Select CASB type as Agent. |
| Enable MDM |
If you want to configure miniOrange MDM on your device, enable it. (This check only works with miniOrange MDM) |
- For ACS URL and Entity URL, you need to first configure Google Admin Authentication using the below steps.
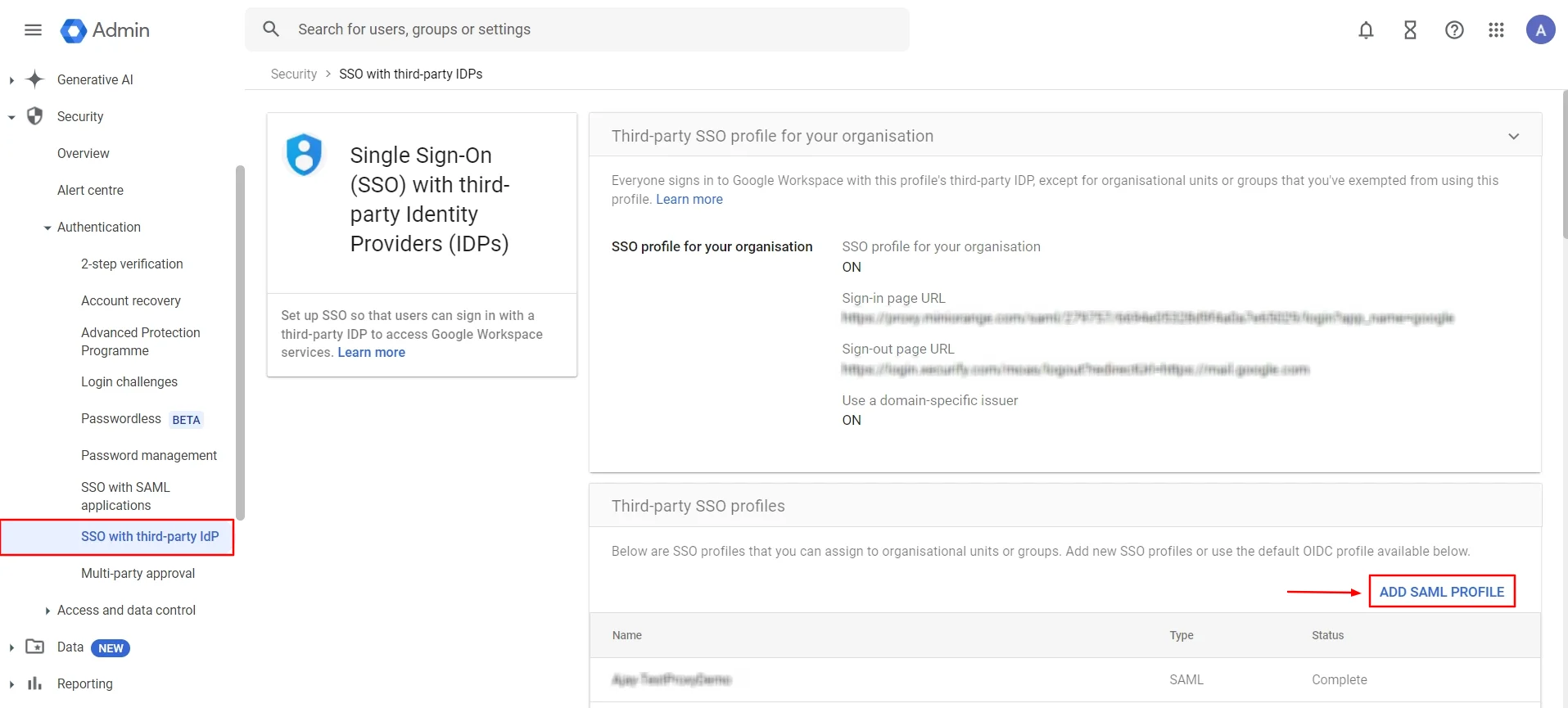
- Firstly, Login to your Google Admin Dashboard.

- On the left side, below the menu icon (☰), click on Home () ⤏ Security () ⤏ Authentication ⤏ SSO with third-party IDP.

- Now, click on ADD SAML PROFILE to create a new SAML profile.
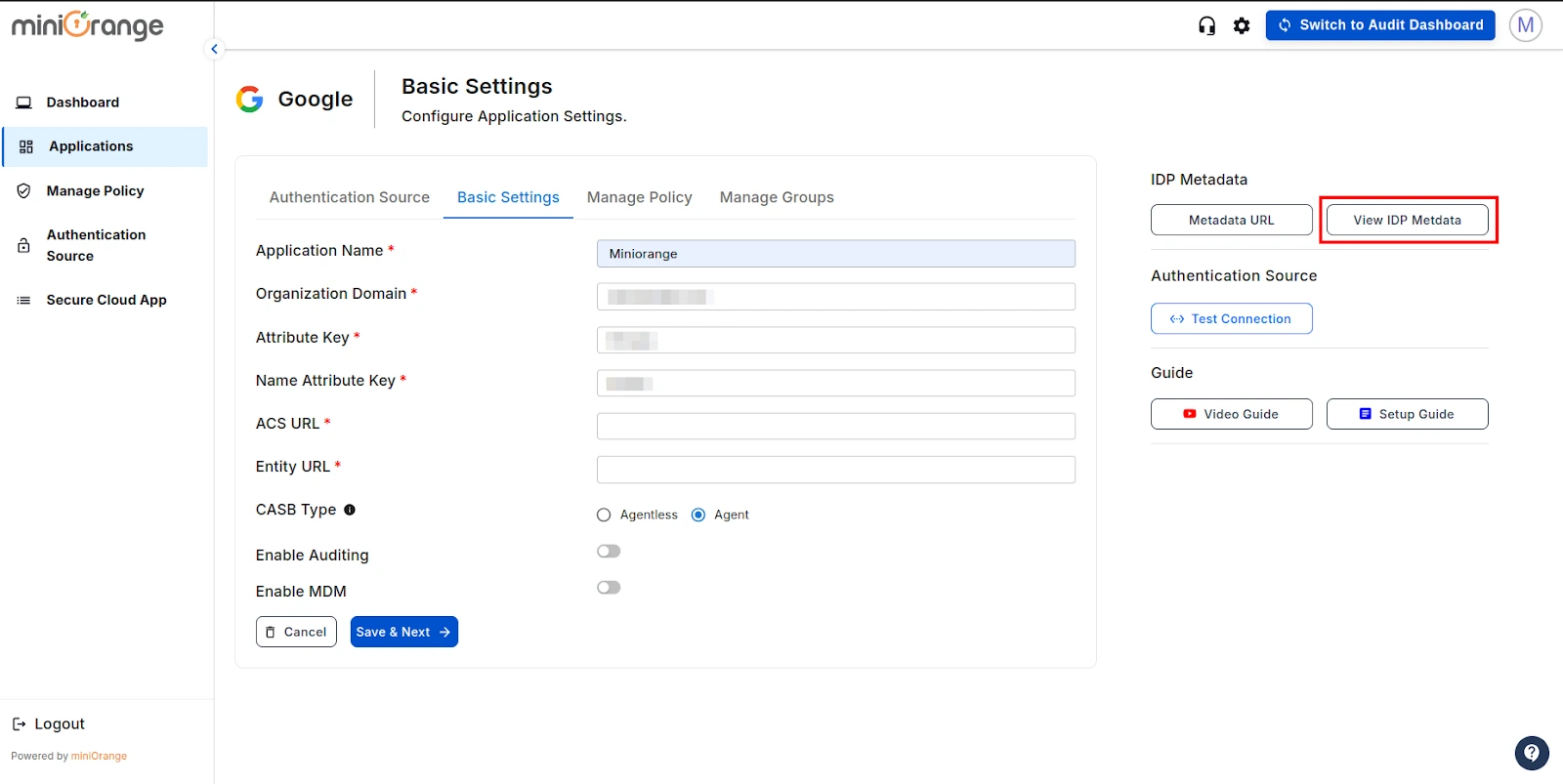
- Go to the CASB Dashboard basic settings screen and click on View IDP Metadata button.
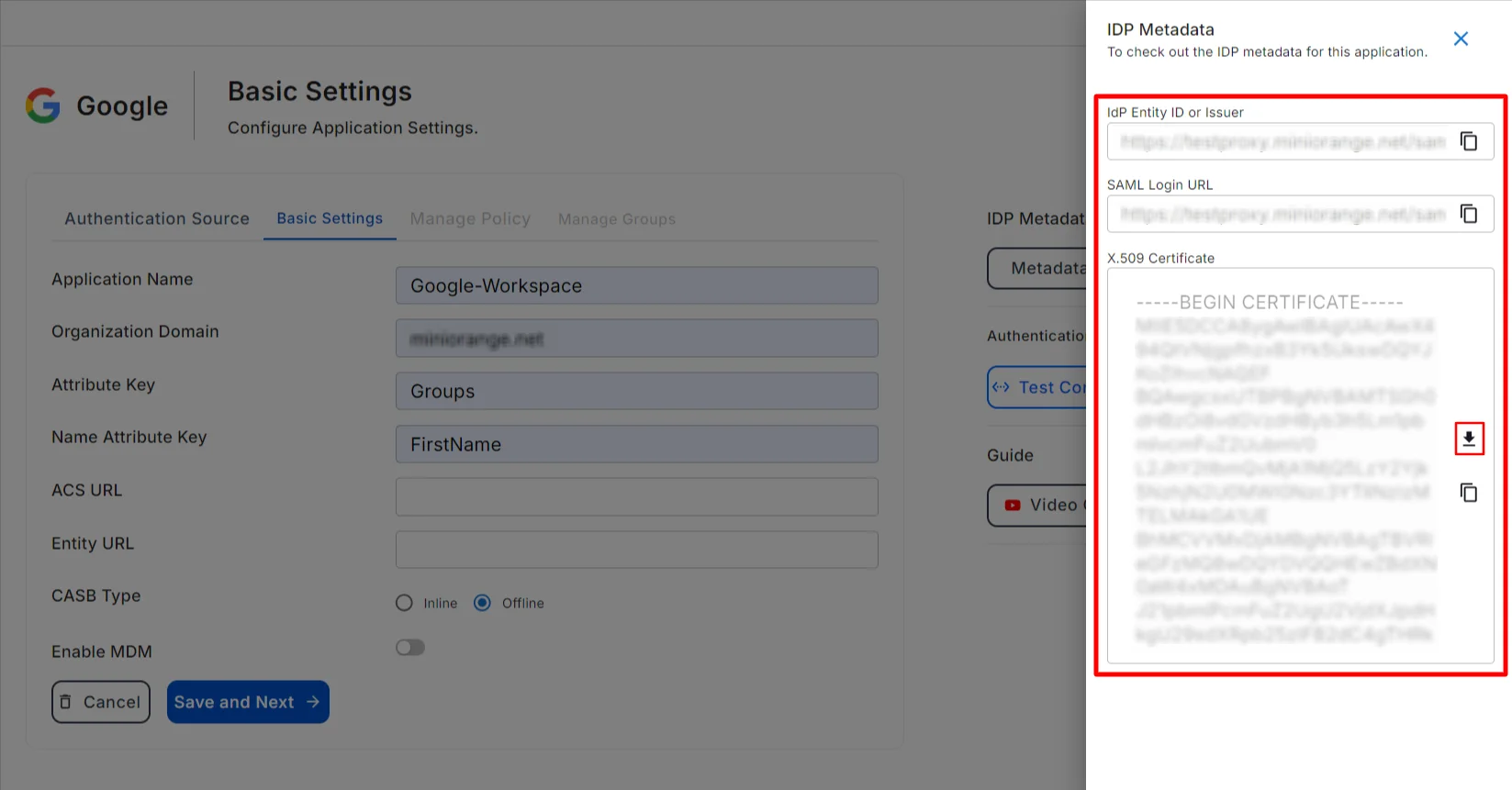
- Find the IDP entity ID and Sign-in page URL. You can also Download the X.509 Certificate from here.
- Enter SAML SSO profile name & Copy and paste the IDP entity ID and Sign-in page URL and attach the X.509 Certificate in Upload Certificate and click on the Save button.
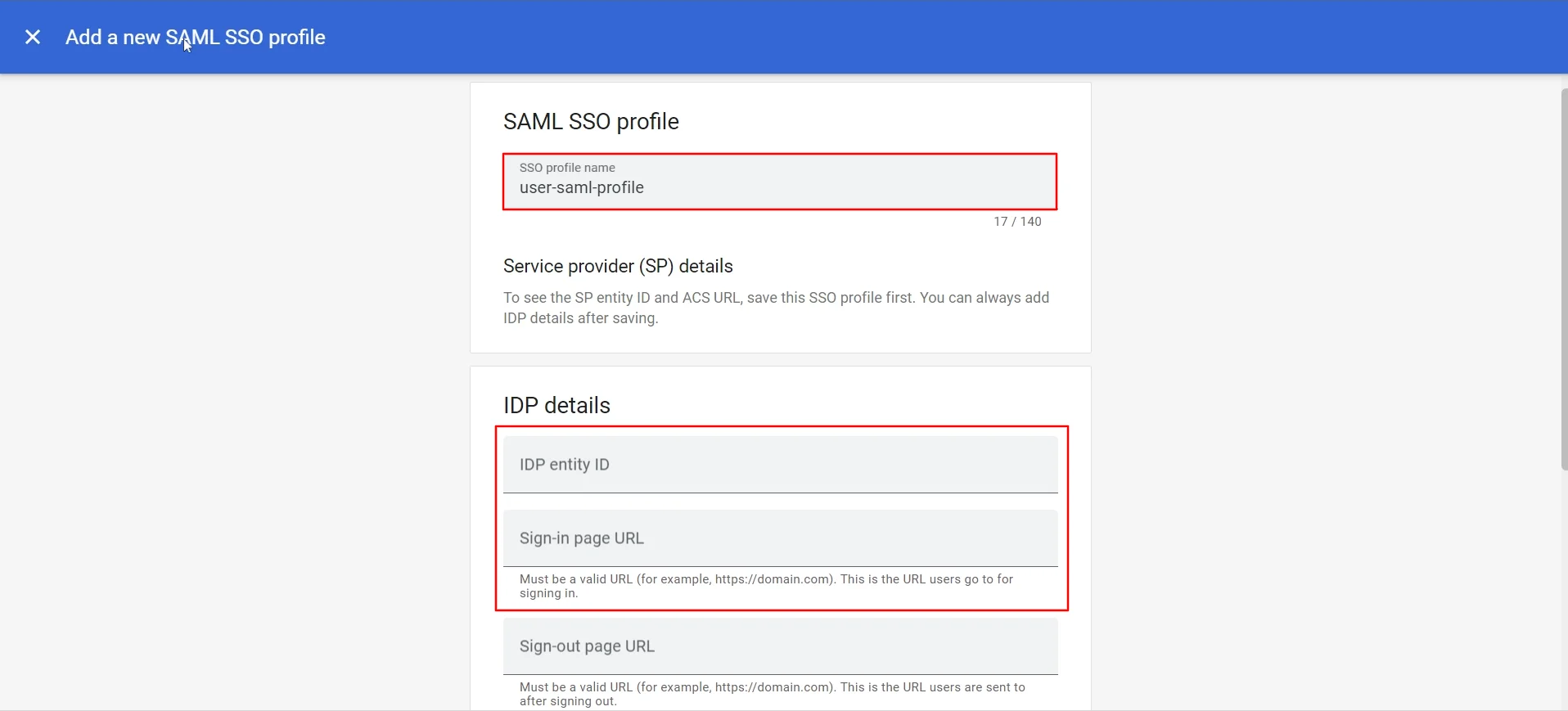
- Set up SSO to allow all existing users to access Google Workspace services through third-party identity providers.
- Click on the Edit Button highlighted in the red box in the image below.

- After clicking on the edit icon, a menu will be displayed, as shown below.

- Select the checkbox “Set up SSO with third-party identity provider”.
- Fill in the details on the Sign-in page URL (i.e., the Sign-in page URL is the SAML login URL that you have in the IDP metadata).
- Now, click on the “REPLACE CERTIFICATE” button, which will open a window to upload the certificate. Upload the X.509 Certificate that you have in the IDP metadata.
- Once done with these steps, click on the SAVE button to update the configuration.
- Set up Single Sign-On (SSO) to allow existing users within an organization to individually access Google Workspace services through third-party identity providers.
- On the left side, Click on Directory ⤏ Organisational units ⤏ Create organisational unit as shown below.
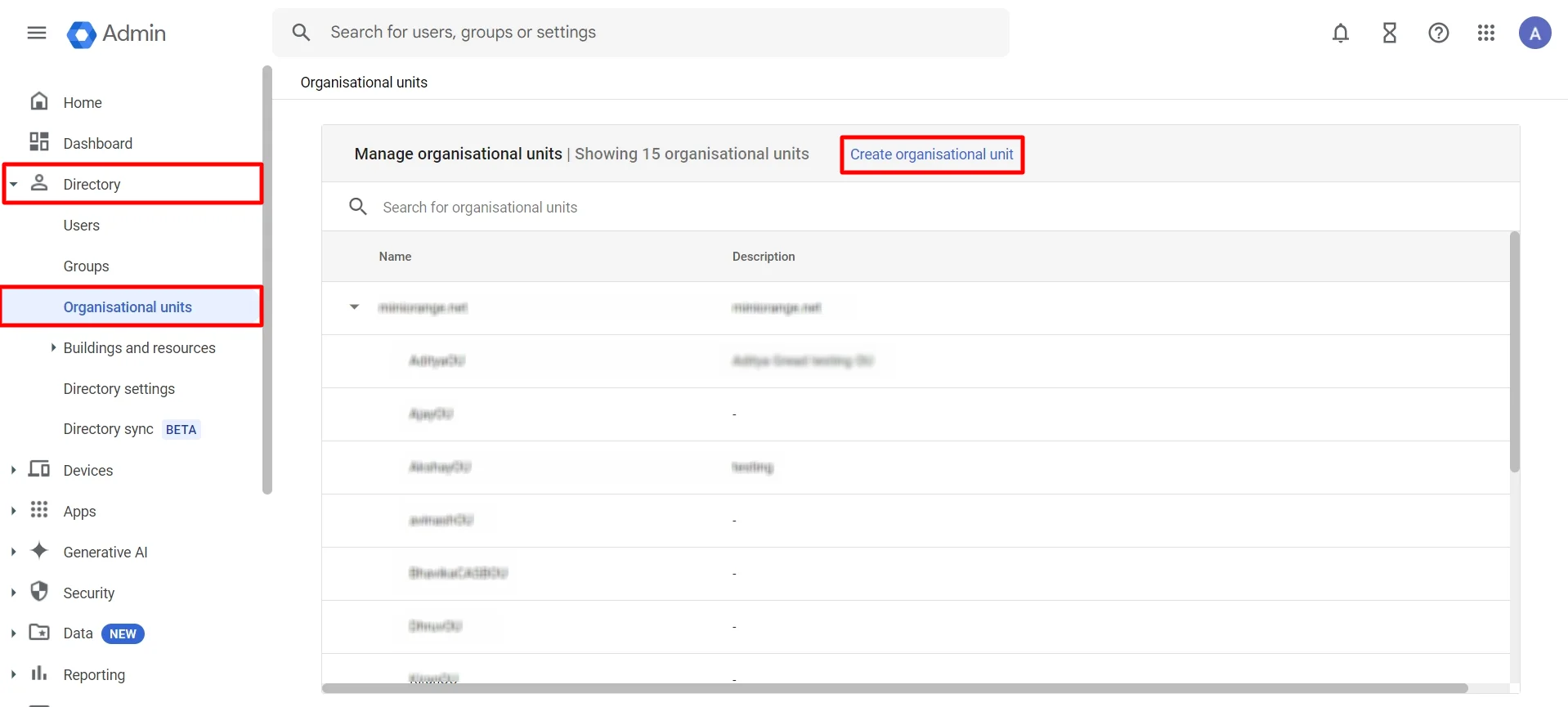
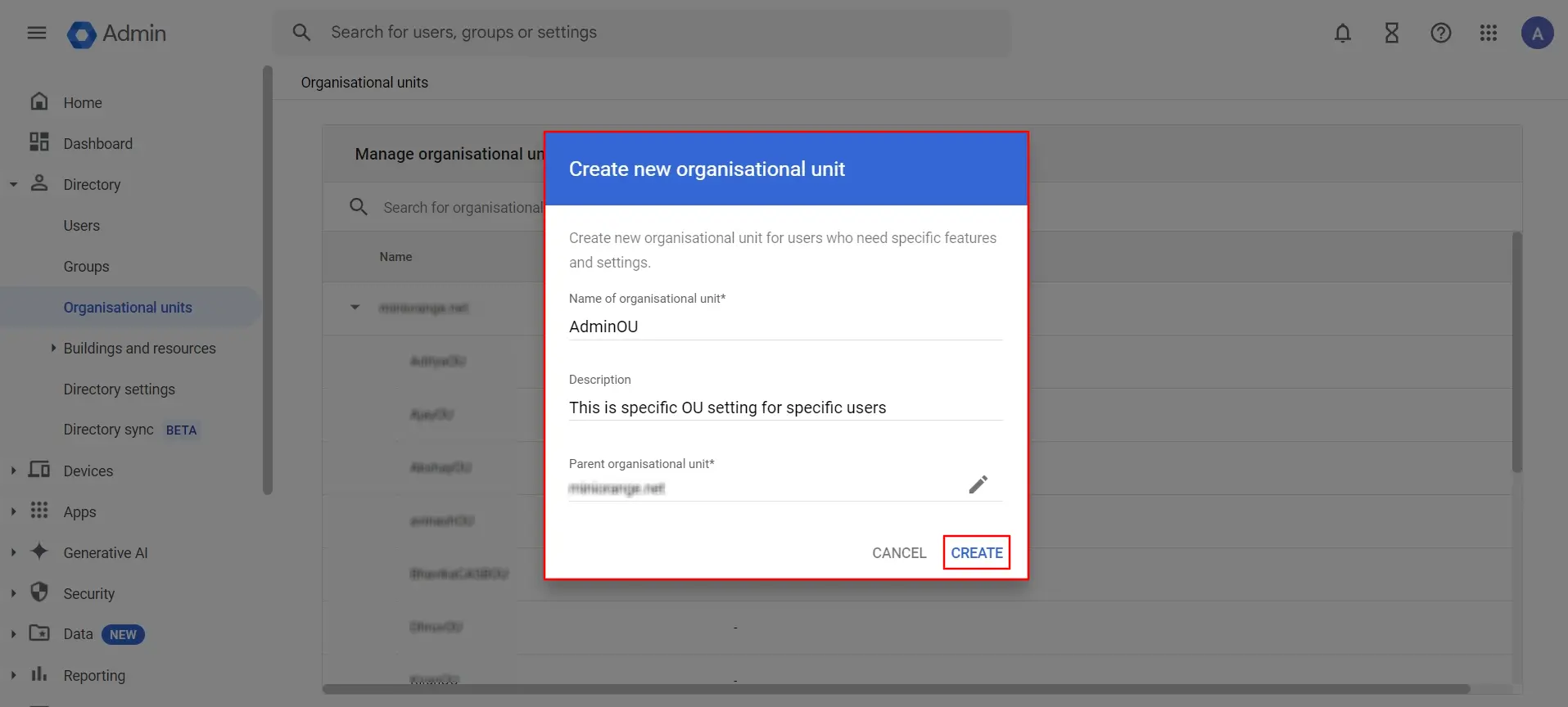
- Next, click on Create Organizational Unit. A pop-up will appear where you can enter the Organizational Unit Name and a Description to identify it. Once done, click the CREATE button.
- Now, on the left side, click on Security () ⤏ Authentication ⤏ SSO with third-party IDP ⤏ MANAGE button.
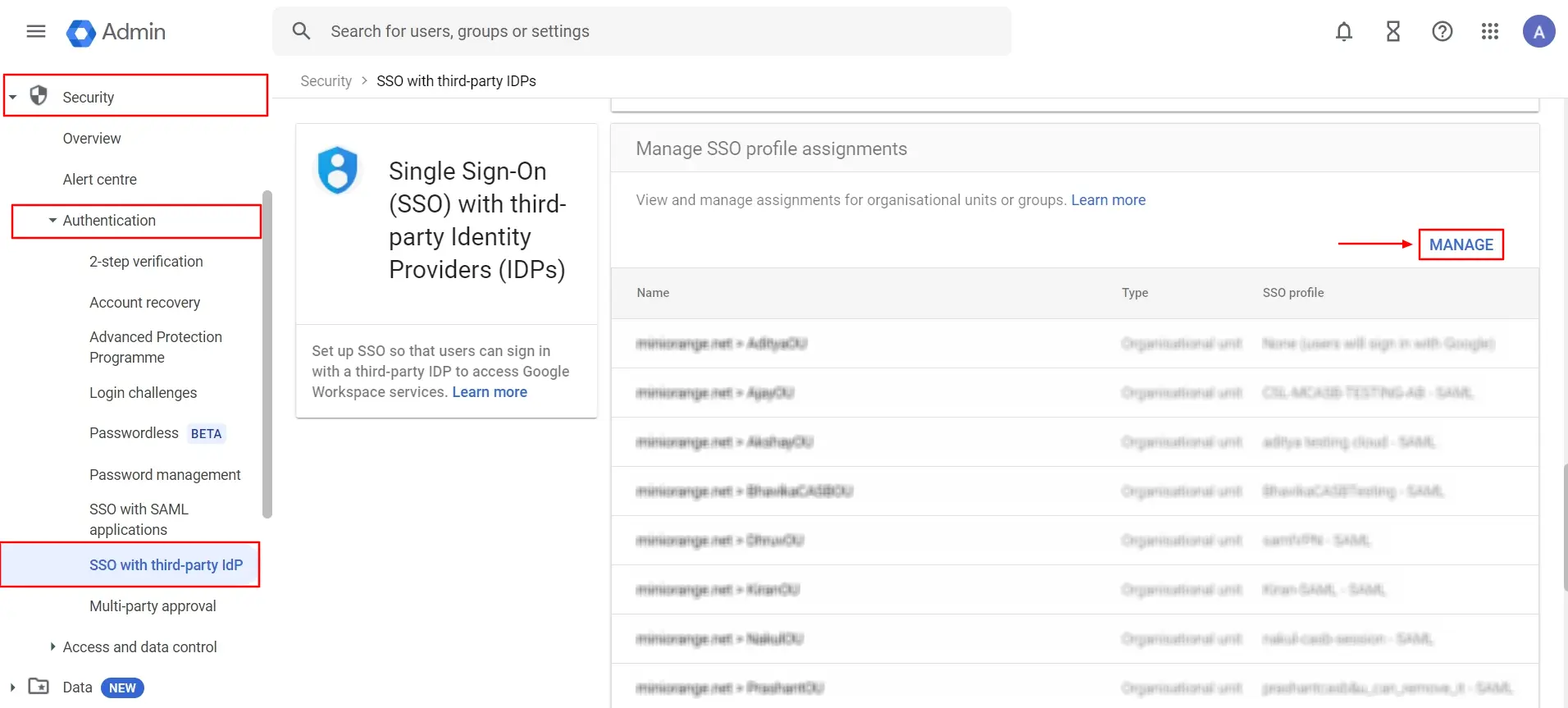
- Select the Organizational Unit that you created, click on the Select SSO Profile option, choose the SAML SSO Profile from the dropdown that you created earlier, and click Save.
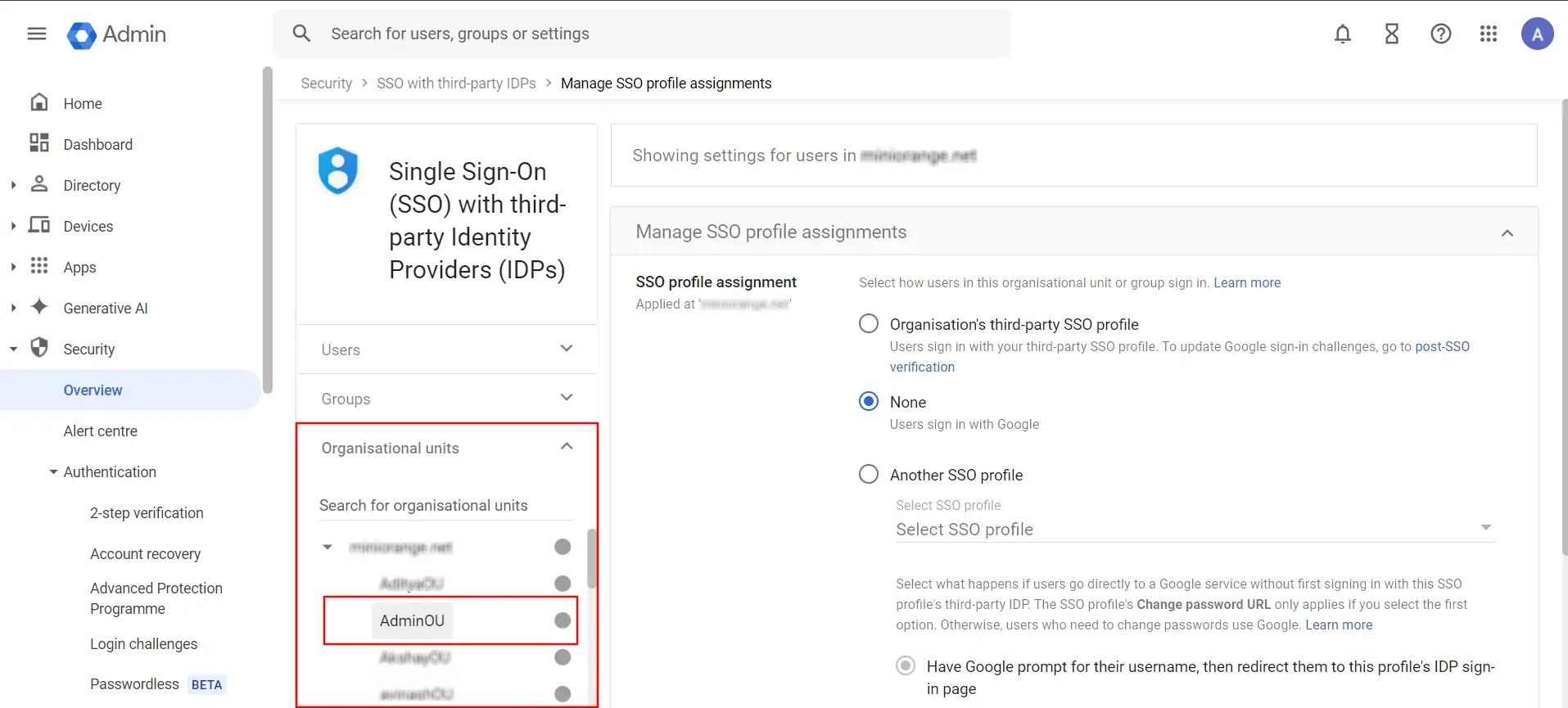
- Select the created user from SSO with third-party IDP section and copy the ACS URL and Entity URL as shown below.
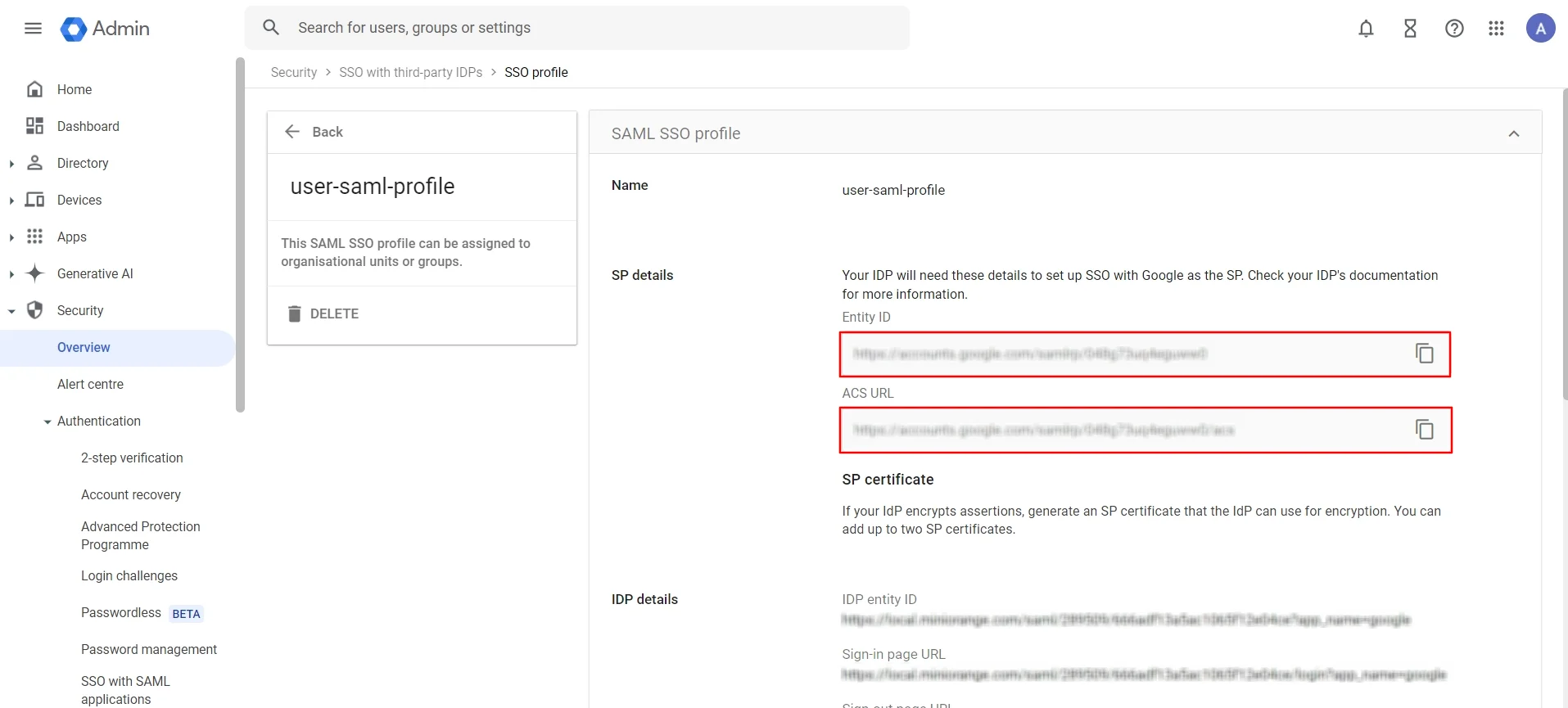
- Paste it into the ACS URL and Entity URL fields in the Basic Settings section.
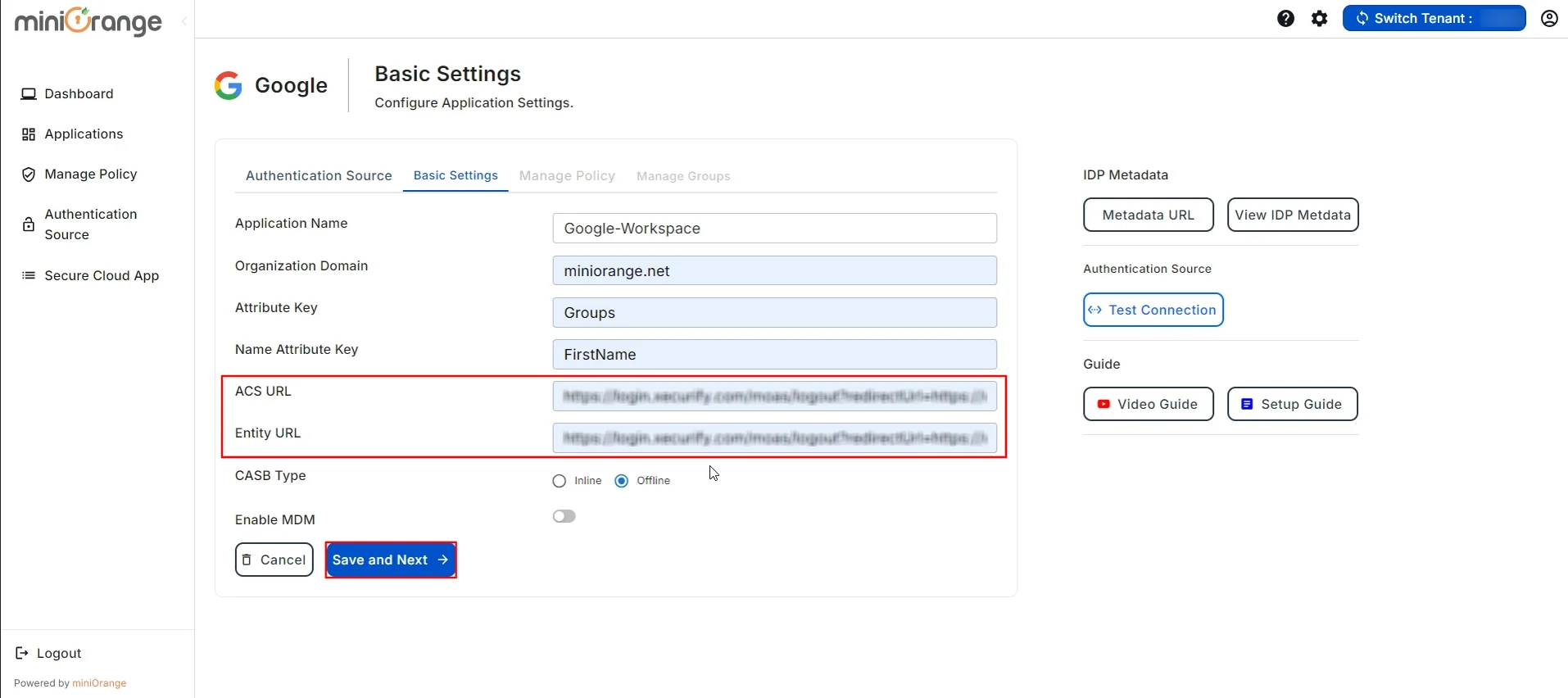
- Once done with these steps, click on the Save and Next button to update the configuration.
- You have successfully created the SAML SSO with Third Party IDPs!
Note:
To access your applications, you need to set up the miniOrange CASB extension. Click here to follow the steps.
External References
miniOrange CASB offers a wide variety of security features with flexible scalability, all available at the most affordable price to all types of businesses. Start by signing up now!