Need Help? We are right here!
Search Results:
×Privileged access management (PAM) for Unix/Linux involves the utilization of root user accounts, which possess the highest administrative privileges within the system. These super accounts allow for various administrative tasks and can be customized with unique names and passwords. The root user, being flexible, can execute diverse administrative functions, control mechanisms, and access privileged resources and system configuration settings. These accounts are crucial in situations of security breaches or cyber attacks, as they grant access to essential data.
miniOrange offers Privileged Access Management (PAM) Solutions designed to enhance Unix/Linux environments.
Through the Privileged Access Management framework, admin tasks related to sensitive Linux resources are automated, facilitating streamlined privilege sharing and access provisioning. This automation ensures both security and efficiency. miniOrange's PAM solution optimizes privilege management within the Unix/Linux environment.







Implementing PAM solutions empowers admins to finely control privileged access on Unix/Linux systems.
Seamlessly add enterprise Linux endpoints regularly. The platform centralizes storage, boosts accessibility, and enhances visibility in complex Unix/Linux networks. Hierarchical organization ensures easy management and control aligned with organizational requirements.
Customized password policies aligned with your internal security requirements. Native password generator effortlessly rotates passwords periodically or on-demand, ensuring robust password security. It tracks all password-related activities, including resets, sharing, and check-outs, for enhanced accountability and control.
Experience heightened security through powerful Just-In-Time (JIT) capabilities. Admins can grant time-limited privileged account access, automatically resetting passwords upon expiry. Enjoy seamless and secure time-bound access control with JIT features.
Linux Privileged Access Management framework enforces strong command control. IT admins can limit user access to privileged commands, granting temporary elevated privileges. This bolsters security, avoids root credential sharing, and efficiently manages admin users while safeguarding Linux resources.
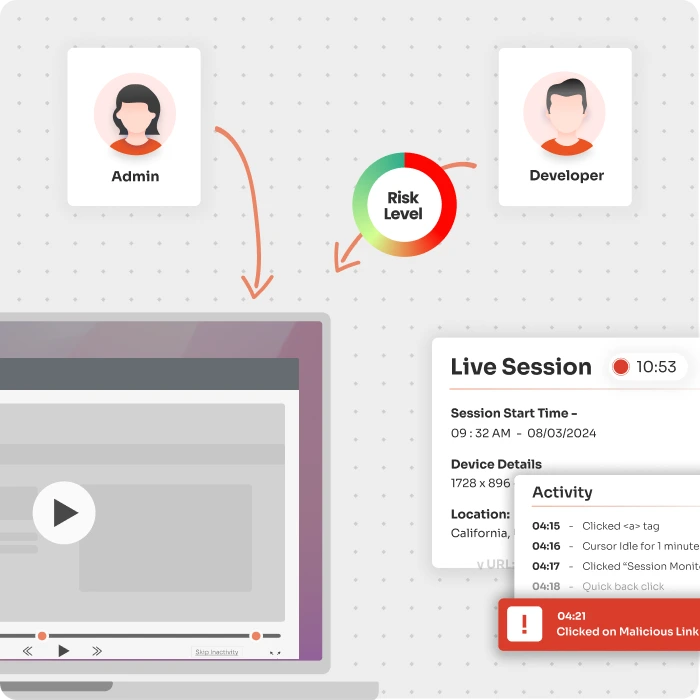
Share Unix/Linux resources with third-party collaborators using the principle of least privilege, ensuring controlled access and immediate privileged revocation.
Safeguard privileged Unix/Linux identities like passwords and SSH keys in a secure vault with standardized encryption thus protecting sensitive credentials.
Audit and record all actions in the Linux/Unix environment, enabling damage control, prevention, and quick break-glass measures.
Maintains an up-to-date record of all active privileged accounts within your Unix/Linux environment, ensuring secure access control.
Implements strict password policies, periodic resets, and one-time-use SSH key pairs, bolstering Linux endpoint security.





I can't speak highly enough regarding miniOrange, I am totally satisfied with the process and results in every regard.
5.0

Awesome tech service, Awesome product. Overall Awesome people. This solution is very simple and easy to implement
5.0
