Need Help? We are right here!
Search Results:
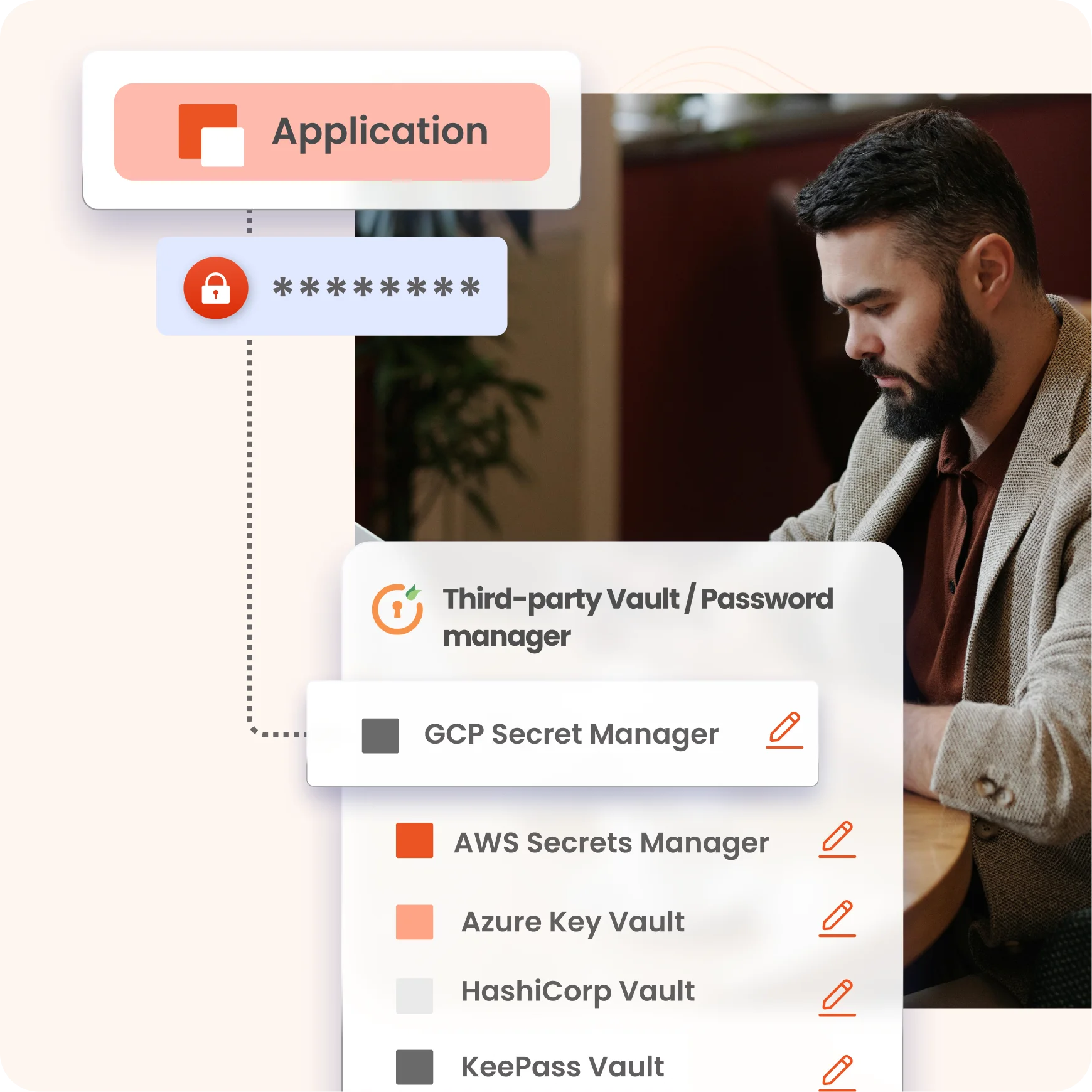
×Privileged Access Management (PAM) for Web Applications is a comprehensive security approach that focuses on managing and safeguarding access to critical areas within a web system. It efficiently works privileged access to legacy, custom applications. It ensures that only authorized users with elevated privileges can interact with and manage sensitive resources, such as databases or administrative interfaces.
PAM employs robust access controls, authentication mechanisms, and continuous monitoring to mitigate the risk of unauthorized access, reducing the potential for security breaches and data compromise within web applications and effectively handling privileged access to browser-based user interfaces, including custom, legacy, and industry-specific ones that may be unfamiliar to users.







PAM systems smoothly integrate with existing web applications. This integration streamlines user access management and reinforces security. Integration with in-house web applications or custom applications extends PAM's security features and safeguards critical resources, bolstering overall operational efficiency and security posture.
Continuous monitoring of privileged sessions in real-time not only enables immediate threat detection and response but also aids in forensic analysis and compliance audits, ensuring accountability and enhancing incident management capabilities.
JIT grants real-time elevated privileged access for specific tasks temporarily, ensuring minimal standing access, to a specific resource and for a specific timeframe. Its Audit trail capabilities help organizations identify who gained access to which systems, when, and for how long.
PAM provides secure remote access to web apps for privileged users, with strong authentication like MFA and robust encryption protocols. By enabling privileged users to access web applications remotely, organizations accommodate the needs of geographically dispersed teams while upholding security standards.
PAM helps organizations meet regulatory requirements and compliance standards by enforcing access policies and maintaining detailed audit trails.
Strengthens security by limiting access to critical web resources, reducing the risk of data breaches. It also helps to identify and mitigate risks posed by privileged users with malicious intent, ensuring the integrity of web applications and their data.
PAM simplifies the process of granting access to authorized users, minimizing disruption and maintaining the efficiency of operations while improving security.





I can't speak highly enough regarding miniOrange, I am totally satisfied with the process and results in every regard.
5.0

Awesome tech service, Awesome product. Overall Awesome people. This solution is very simple and easy to implement
5.0
