Need Help? We are right here!
Search Results:
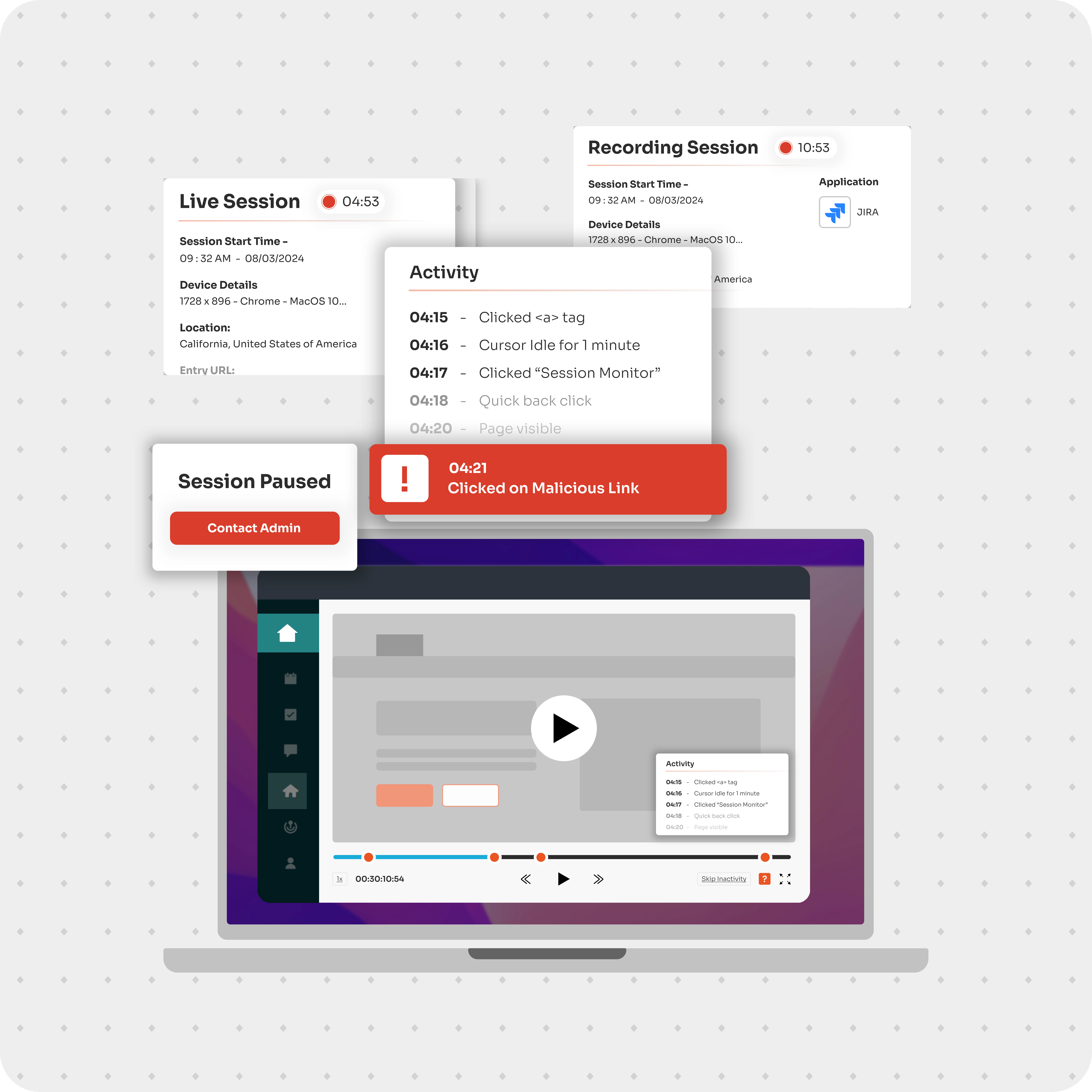
×Privileged Session Monitoring, including session recording and session monitoring capabilities, offers an additional layer of oversight and holds users accountable for their actions when accessing privileged accounts. The session recording and monitoring functionalities enable organizations to monitor privileged sessions and capture privileged user activity in real-time. This helps to prevent intentional or unintentional misuse of privileged accounts and establishes non-repudiation.
Non-repudiation ensures that recorded evidence of user actions cannot be denied, providing strong evidence of user activities and preventing users from falsely repudiating their actions.
Commonly implemented within Privileged Access Management (PAM) systems, session monitoring, and recording are particularly beneficial for organizations seeking to effectively monitor privileged sessions and maintain a comprehensive record of user activities. Secure remote access connections to valuable or privileged systems can also be closely monitored using these capabilities.







Capture and monitor privileged user activities in real-time, preventing unauthorized activities and detecting suspicious behavior for enhanced security. It captures the actions of privileged users accessing specific privileged accounts, and also captures screen activity, recording file transfers, and system configuration changes.
Keep a thorough privileged access audit trail, including session recordings, for regulatory compliance and audits. Monitoring and recording sessions boosts security, reducing data loss and breaches, aiding troubleshooting and compliance reporting.
Recorded sessions are viewable and auditable, allowing review and connection to users, accessed accounts, and activities performed during the session. This provides a detailed record of user actions.
Facilitate prompt incident response and thorough forensic investigations by leveraging detailed records of privileged sessions, enabling identification and analysis of security incidents' source, scope, and impact.
Customize session recording features to align with your organization's specific requirements. Gain flexibility in enabling or disabling data capture elements, such as selectively capturing keystrokes for sensitive applications.
Promote accountability among privileged users, deterring misuse and enhancing security. Effectively track actions, ensure transparency, deter unauthorized activities, and foster a culture of responsibility and security awareness.
Help desk support staff can address difficult-to-reproduce issues. By enabling the recording of user sessions, they can capture time-stamped visual records of errors, thus facilitating faster troubleshooting.
Offers flexible policies to trigger automatic recordings of application and desktop sessions. It also supports dynamic recording, allowing IT personnel to monitor and examine user activity in real-time.
It boosts security for sensitive applications by offering a comprehensive record of user actions during privileged sessions. This includes keystrokes, screen activity, and file transfers, aiding in vigilant monitoring and deterring malicious behavior.
Administrators can monitor employees and third-party contractors, intervening in case of misuse and taking immediate action to terminate or block further misuse, enhancing security and accountability.

There is an in-depth analysis with session timestamping, a trusted timestamp makes recorded sessions invaluable for use as forensic evidence in court. The feature supports trusted time-stamping services offered by third-party providers.
Users can capture and share work activity, aiding onboarding and training. Archived data serves as playback for new employees' learning and training materials for admin development and specific configurations.





I can't speak highly enough regarding miniOrange, I am totally satisfied with the process and results in every regard.
5.0

Awesome tech service, Awesome product. Overall Awesome people. This solution is very simple and easy to implement
5.0
