Need Help? We are right here!
Search Results:
×
Privileged Password Management (PPM) is a solution that focuses on securing, storing, and managing passwords for privileged accounts. It is a core function of Privileged Access Management (PAM).
Also known as Enterprise Password Management or Password Vaulting, PPM automates credential discovery, access control, secure storage, and password rotation. It provides alerting, reporting, and monitoring capabilities to ensure full oversight of privileged credentials. By enforcing strict password policies and eliminating shared or static credentials, PPM enhances security, compliance, and protection against cyber threats such as credential theft and unauthorized access.







miniOrange password rotation in PAM offers password rotation at system level. For instance, to protect the endpoints, we offer RDP, SSH and VNC. Also, for servers, we offer system level password auto-rotation for AD and DB. Here is a simple workflow of how it is executed:
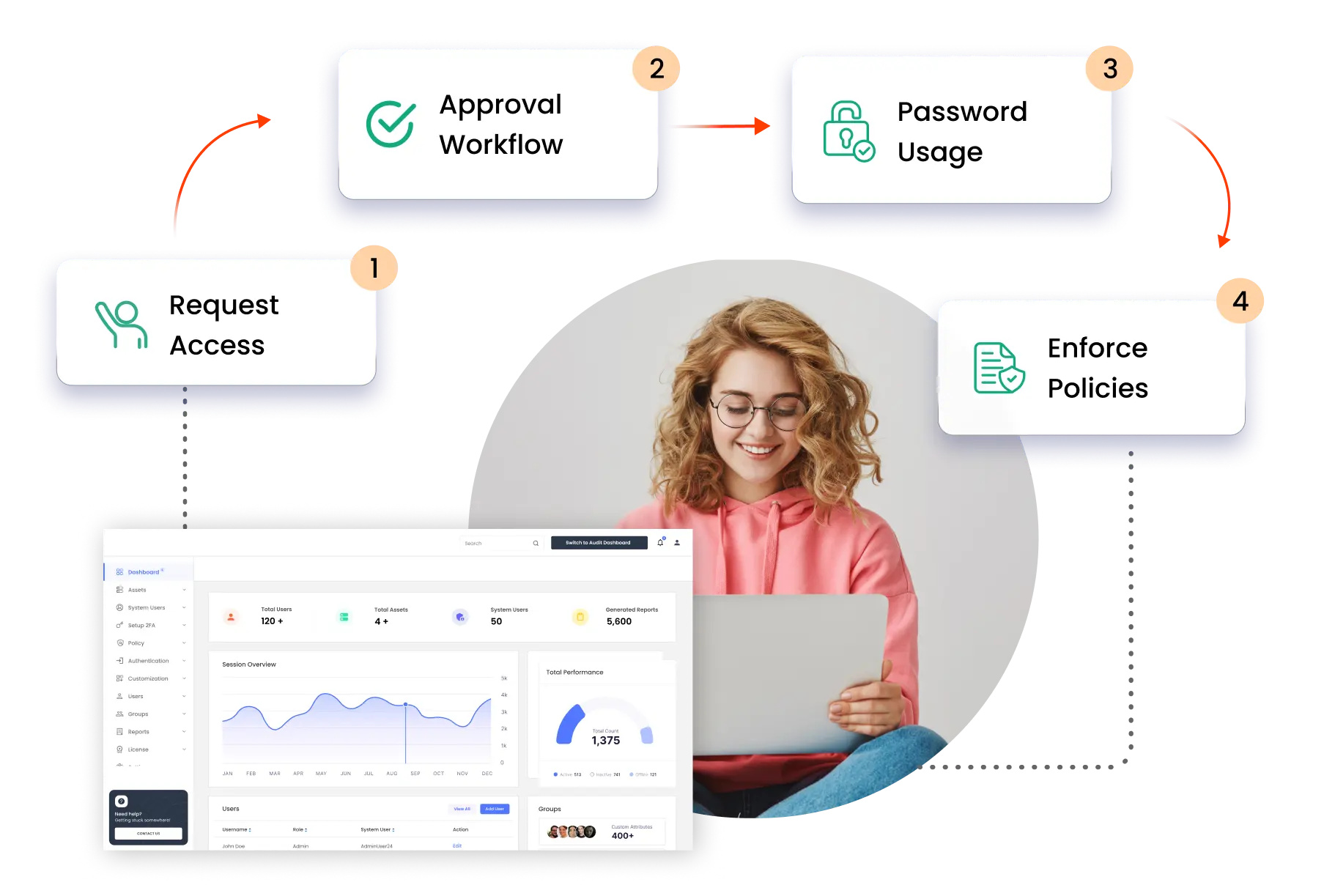
Simplifies the creation of strong, unique passwords by generating secure credentials with customizable length and complexity.
Enhances security by automatically rotating passwords at regular intervals, ensuring continuous protection.
The tool also facilitates Password Secure Sharing, allowing users to securely store, copy, and share generated passwords with authorized personnel, maintaining both convenience and security.
Privileged credential management solutions automate the secure storage and retrieval of passwords, enabling seamless application-to-application communication while reducing manual intervention. With automated password rotation and encryption, enterprise password managers guarantee that only authorized applications can access critical credentials.
This approach enhances security by enforcing the principle of least privilege, providing granular access control over privileged accounts.
Seamlessly integrate with a wide range of password managers and vaults supported by miniOrange
Such as; GCP Secret Manager, AWS Secrets Manager, Azure Key Vault, HashiCorp Vault, KeePass Vault, and any other third-party vault or manager.
It minimizes the risk of unauthorized access, even if the master password is compromised.
Integrating MFA into password managers strengthens account protection and ensures sensitive data remains secure.
A Hardware Security Module (HSM) is a specialized device designed to securely manage and protect cryptographic keys throughout their lifecycle. HSMs act as trust anchors, ensuring that sensitive keys are stored and processed within a tamper-resistant environment.
They are crucial for safeguarding transactions, identities, and applications by providing secure encryption, decryption, and authentication
Digital signing services, verify the integrity and authenticity of digital documents and communications.
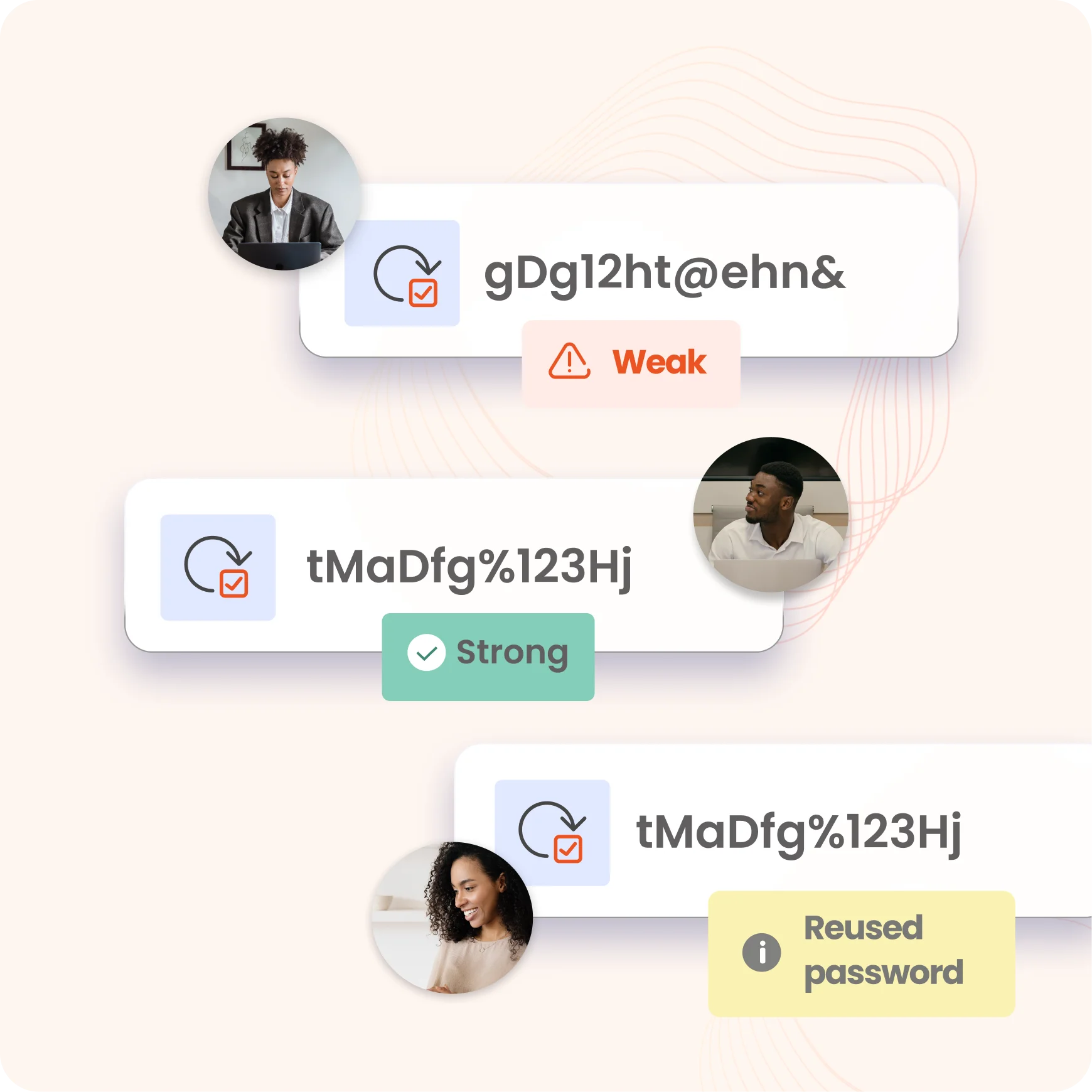
Privileged password vaults leverage AES-256 encryption, a globally recognized standard for securing sensitive data. This ensures end-to-end protection, making stored passwords virtually impossible to decrypt without proper authorization.
With built-in compliance and reporting capabilities, the system automatically monitors, records, and logs privileged credential activities, enforcing granular, policy-based access controls. This helps organizations meet stringent security and regulatory requirements, ensuring privileged credentials remain secure and auditable.
Automatically detect and securely store all privileged credentials in a centralized vault, ensuring complete visibility and control.

Share, rotate, and manage privileged passwords from a unified dashboard, streamlining security and reducing manual effort.
Monitor, record, and control privileged sessions in real time, enabling rapid intervention in case of suspicious activity.
Privileged Password Management (PPM) software is essential because it secures the most powerful and sensitive accounts in an organization, those with elevated access to critical systems, infrastructure, and data. These accounts are prime targets for attackers due to the control they offer.
Here’s why PPM software is needed:
Enterprise password management is critical for securing privileged accounts and preventing unauthorized access.
Privileged password management is essential for securing sensitive accounts, preventing credential misuse, and maintaining compliance.
Password requirements for a privileged account is to use a strong, unique password that is at least 12-16 characters long, with a mix of uppercase and lowercase letters, numbers, and special characters. Avoid common words, and personal information, and reuse passwords across different accounts.
Passwords should be regularly rotated, typically every 30 to 90 days, and always paired with multi-factor authentication (MFA) for added security. These measures help ensure the integrity and security of privileged accounts.
Privileged Password Management (PPM) secures accounts with elevated access rights, while regular password management focuses on securing standard user accounts.
If you'd like to understand both in greater detail, here’s more information:
Privileged Password Management (PPM):
Privileged password management (PPM) primarily focuses on securing privileged accounts with elevated permissions, such as root accounts, administrator accounts, or service accounts. These accounts provide access to an organization’s critical systems, sensitive data, and the ability to perform high-risk operations.
As a result, they require an additional layer of protection to prevent unauthorized access and mitigate potential security breaches. Below are the key features of privileged password management:
Password Management:
Password management, in a more general context, refers to securing standard user accounts that typically have less access or control over critical systems. While still crucial for maintaining security, standard password management tends to be simpler than privileged password management. It includes:
Key Differences:
