Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
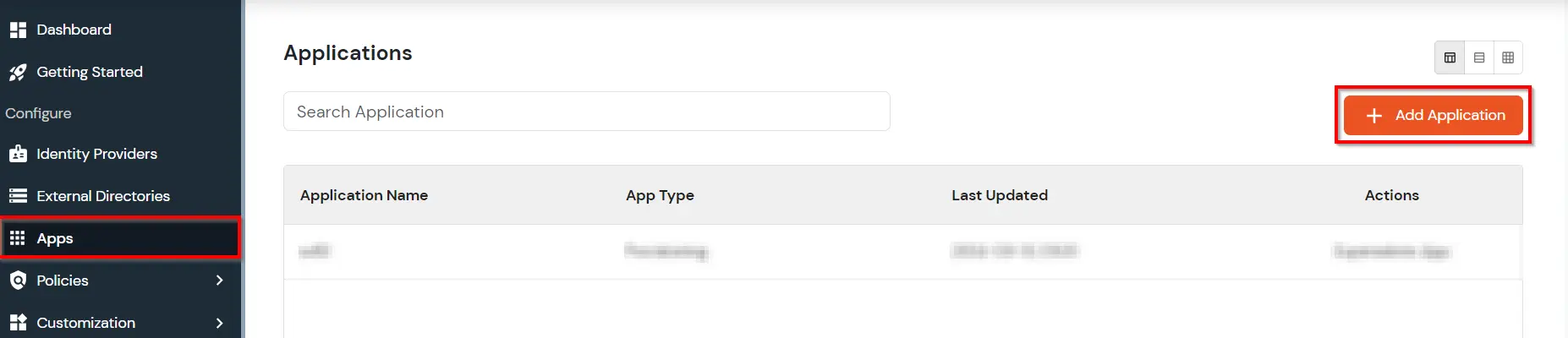
Search Results:
×miniOrange provides the ability for database connection and use it as authentication user store to enable Single Sign-on (SSO), Multi-factor authentication, etc. for your external applications. Here, miniOrange makes custom database work as user store for authentication. Users will login using their custom database credentials only once and have a seamless SSO login into the other applications. We develop connection between miniorange and your database as user store.
miniOrange offers free help through a consultation call with our System Engineers to set up our on-premise server.
For this, you need to just send us an email at idpsupport@xecurify.com to book a slot and we'll help you in no time.



| Database Type | Connection URL | Port Number Default |
| My-SQL/MariaDB | jdbc:mysql://hostname:port/database-name |
3306 |
| MS-SQL | jdbc:sqlserver://hostname:port/database-name |
1433 |
| Postgres sql | jdbc:postgresql://hostname:port/database-name |
5432 |
| OracleDB | jdbc:oracle:thin:@hostname:port/database-name |
1521 |
SELECT '##USERNAME##', username FROM USERS WHERE USERNAME=?




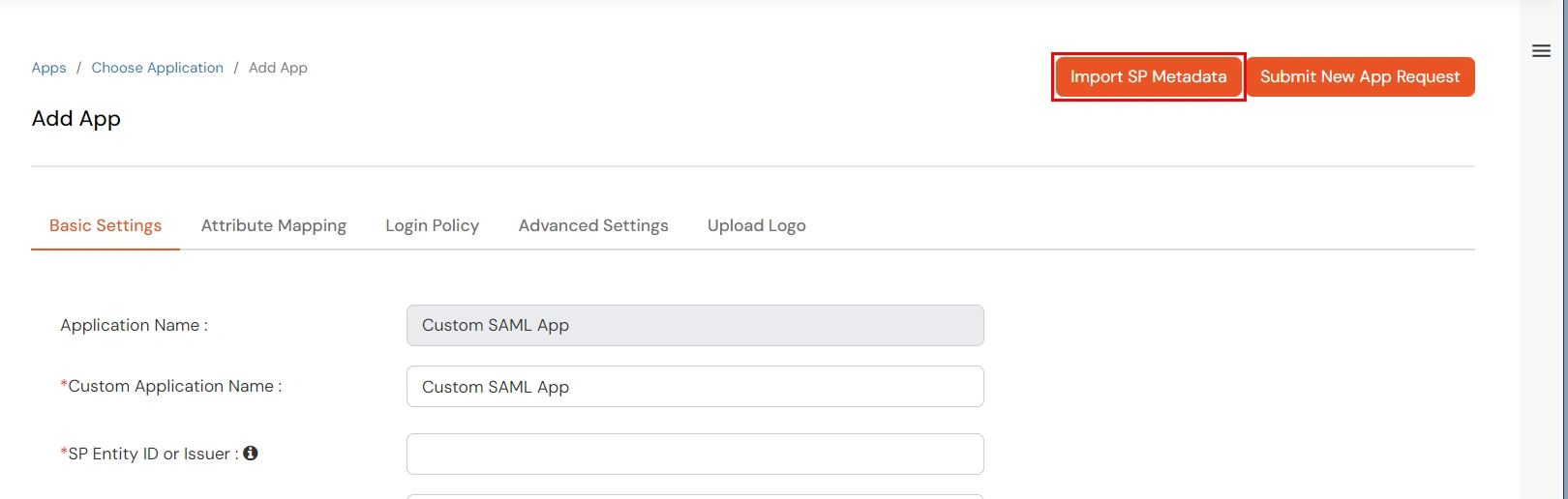
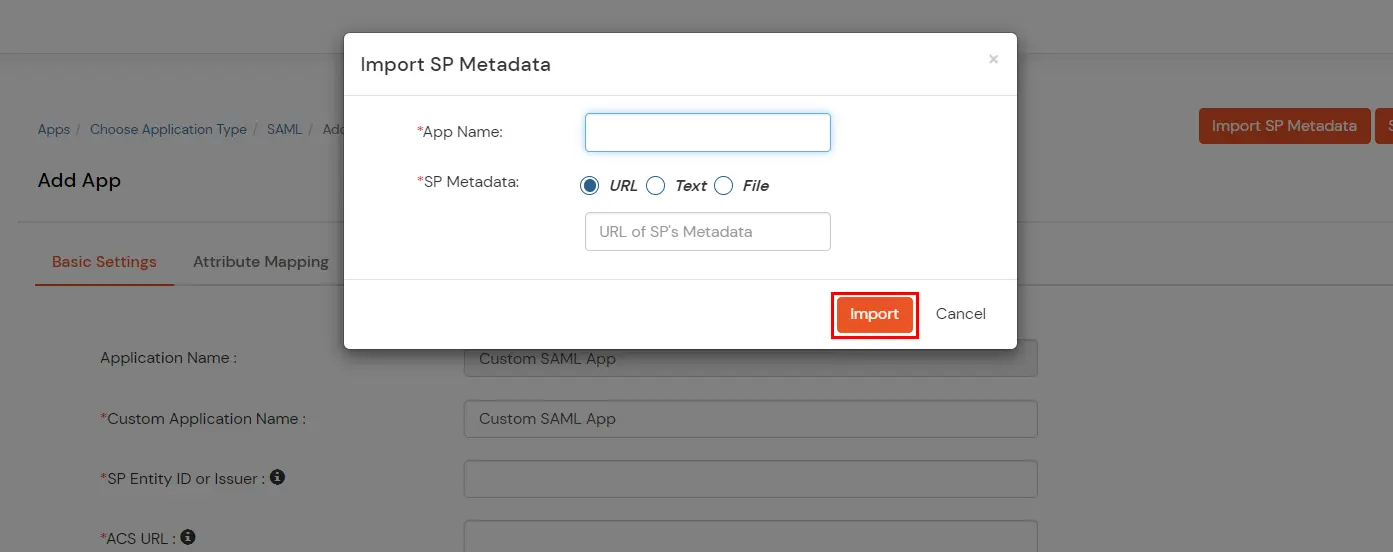
| URL | You get the URL for Metadata information from the Service Provider, you can directly add this URL in the input field provided |
| Text | When you select Text option, you will have to fill all the attributes manually |
| File | When you select File option, you can directly upload the XML file containing all the information. |
https://www.domain-name.com/a/[domain_name]/acs.
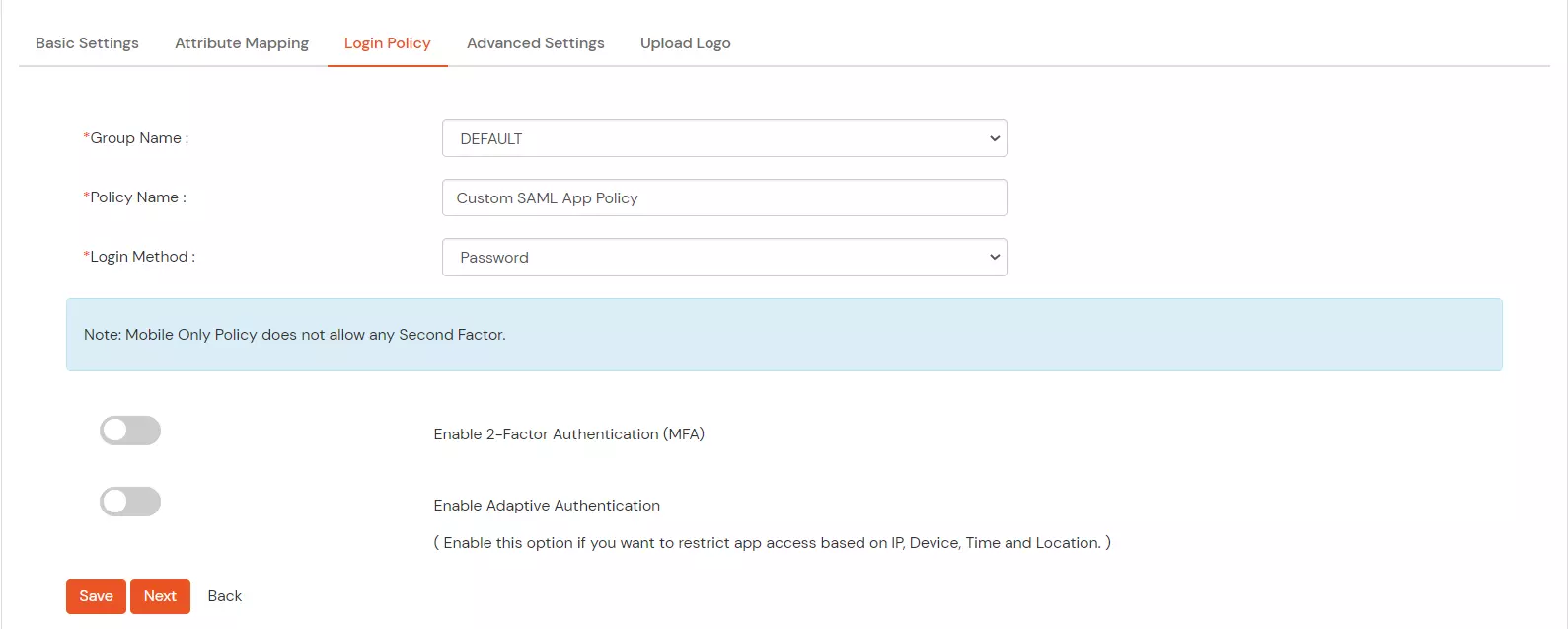
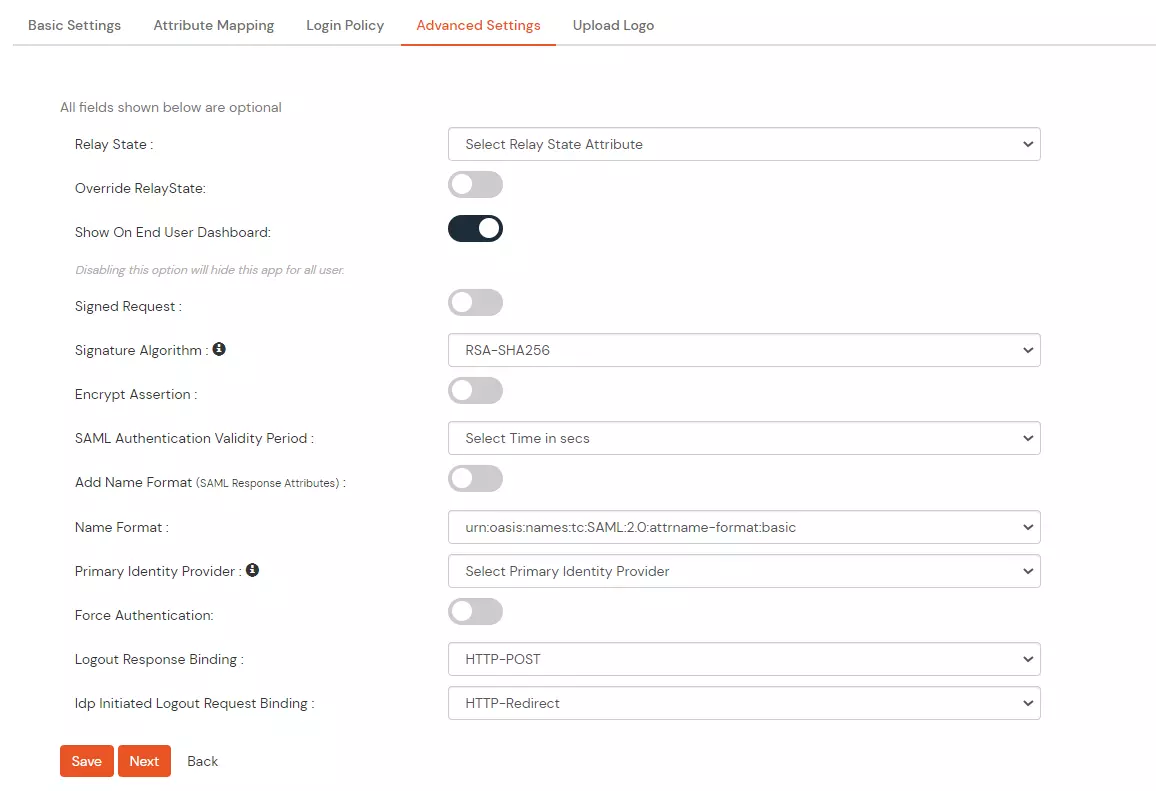
| Relay State | Enter the URL where you want the user to redirect after sign in to the application. |
| Override Relay state | Enable this to override the default relay state of the SP |
| Show On End User Dashboard | Disable this if you do not want the app to be visible for all users on end user dashboard |
| Signed Request | Enable this to sign the request sent by SP to IdP. Provide the X509 certificate or upload the certificate. |
| Signature Algorithm | Select the algorithm that will be used to sign the SAML request/response. |
| Encrypt Assertion | Select this if you want to encrypt the assertion in SAML response and provide the algorithm and certificate for encryption. |
| SAML Authentication Validity Period | The time for which the authentication should be considered valid and the user should be able to perform SSO. After that, the user will have to sign in again. |
| Add Name Format | Enable this to choose a custom name format based on the SP. |
| Name Format | Select the format that is supported by the SP. |
| Identity Source | Select the identity source from where you want the authentication to happen. You will see the list of all configured sources. |
| Force Authentication | Enable this to enforce authentication on each request to access the application. |
| Logout Response Binding | A Logout Response is sent in reply to a Logout Request from SP. It could be sent by an Identity Provider or Service Provider. |
| IdP initiated Logout Request Binding | A Logout Response is sent in reply to a Logout Request from the IdP dashboard. It could be sent by an Identity Provider or Service Provider.
|





Our Other Identity & Access Management Products