Need Help? We are right here!
Search Results:
×User Authentication refers to the identity verification process for a transaction or interaction of a particular user with your business. This may involve the use of various methods of authentication, such as password authentication, biometric authentication, or Multi-Factor Authentication, Two-Factor Authentication . The Authentication solution is a fundamental service in any Identity Management solution. miniOrange provides different authentication methods and processes with their Identity solutions like Identity & Access Management (IAM), Customer Identity & Access Management (CIAM), and Privileged Access Management (PAM).
Authentication Solution is paramount for several reasons:
"Ensuring a positive and secure user authentication experience is crucial for building trust with your employees and customers, protecting against fraud, and complying with regulations."
Eliminate elaborate user registration process and multiple password management by allowing users to just log in with one click from a link sent to their emails or OTP sent to their registered mobile devices.
Enable your customer's smooth login into multiple applications with a single set of credentials with Single Sign-On (SSO). Users will be able to save time and quickly access different apps without any hassle.
Identity solutions from miniOrange can be easily deployed in your organization's existing environment.
per month
upto 500 Users
*Please contact us to get volume discounts for higher user tiers.
Now get prebuilt & customized web pages for your business:
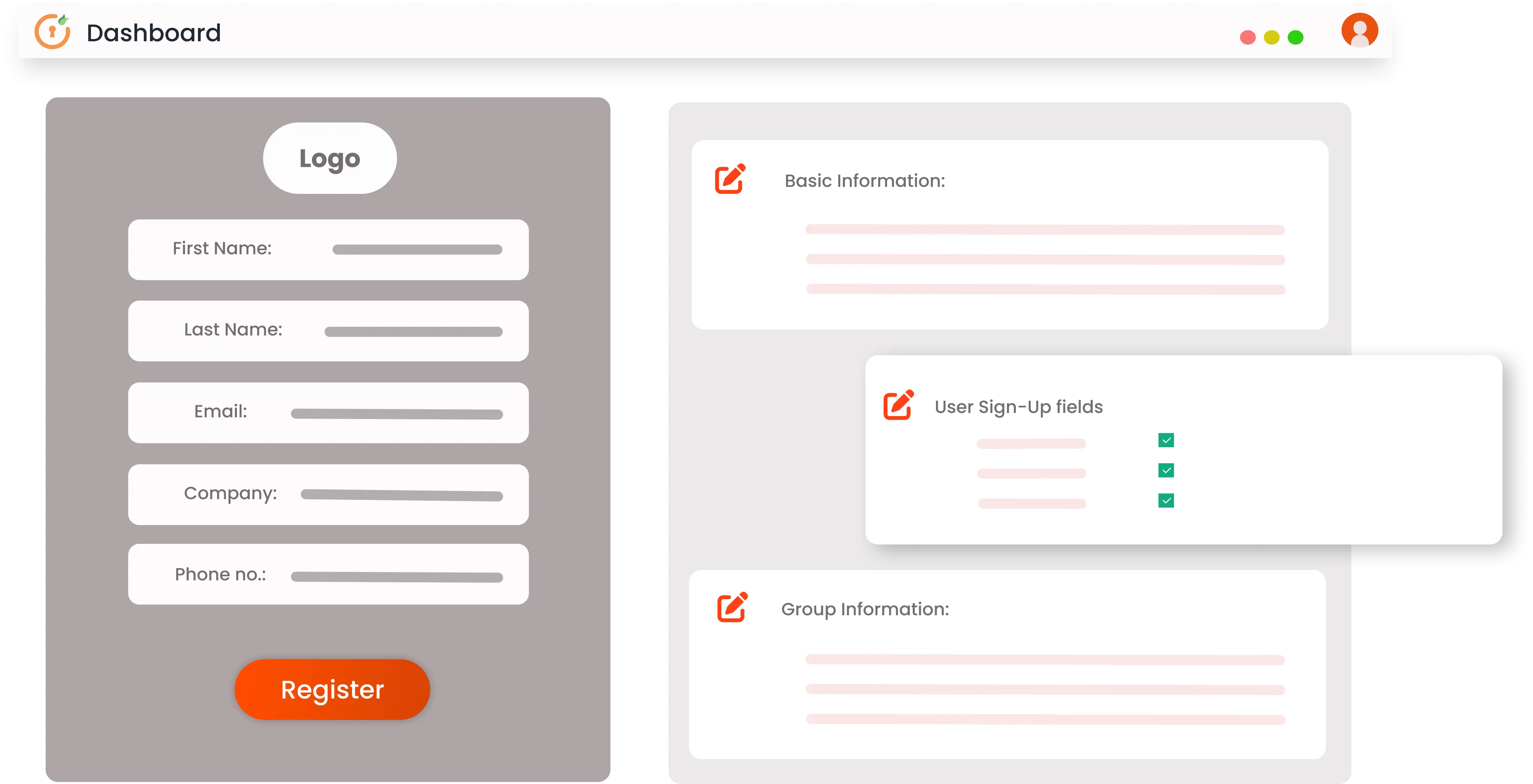
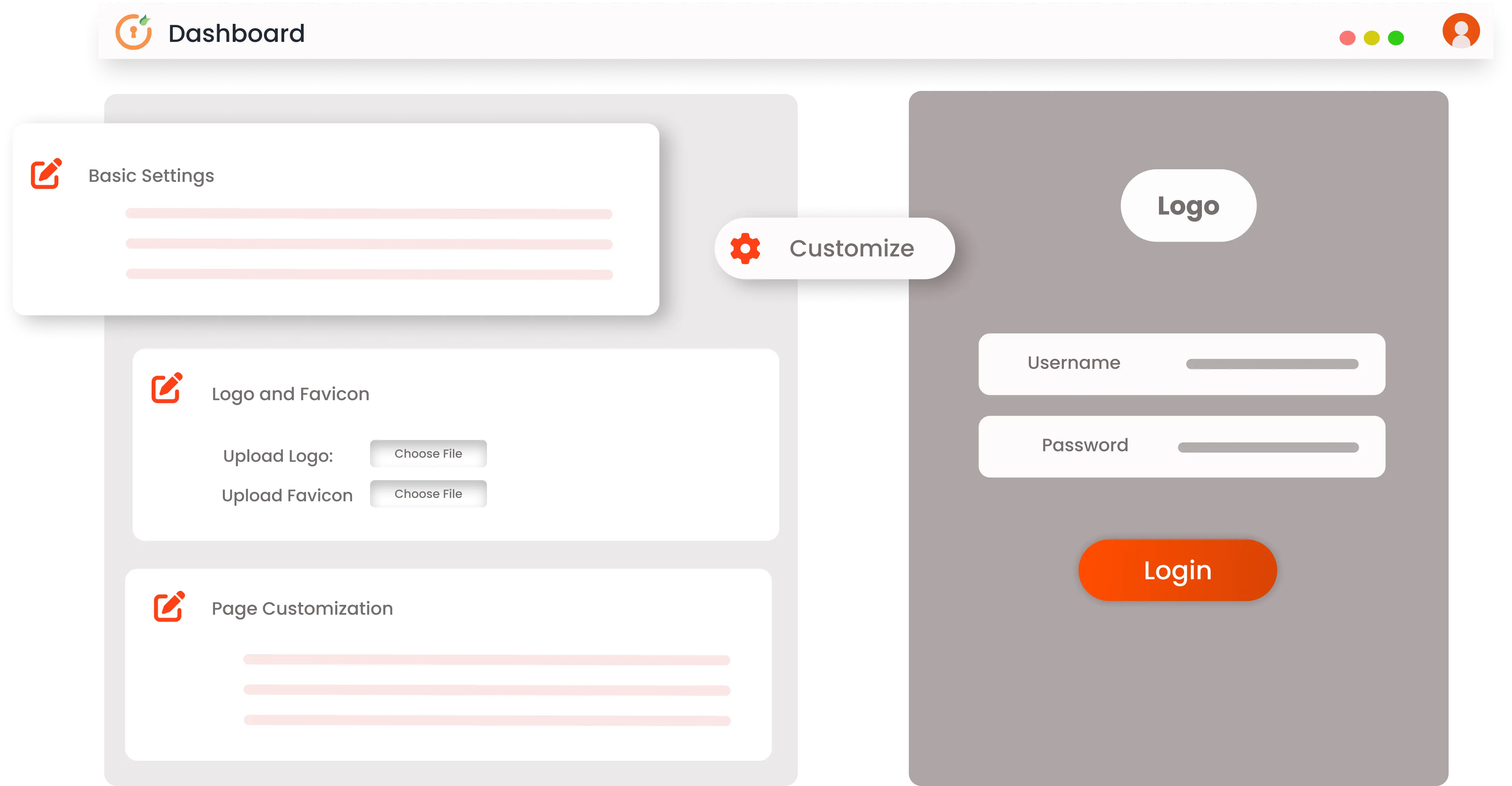
Manage your user experience by personalizing it with your company branding. You can customize web pages and scripts of:
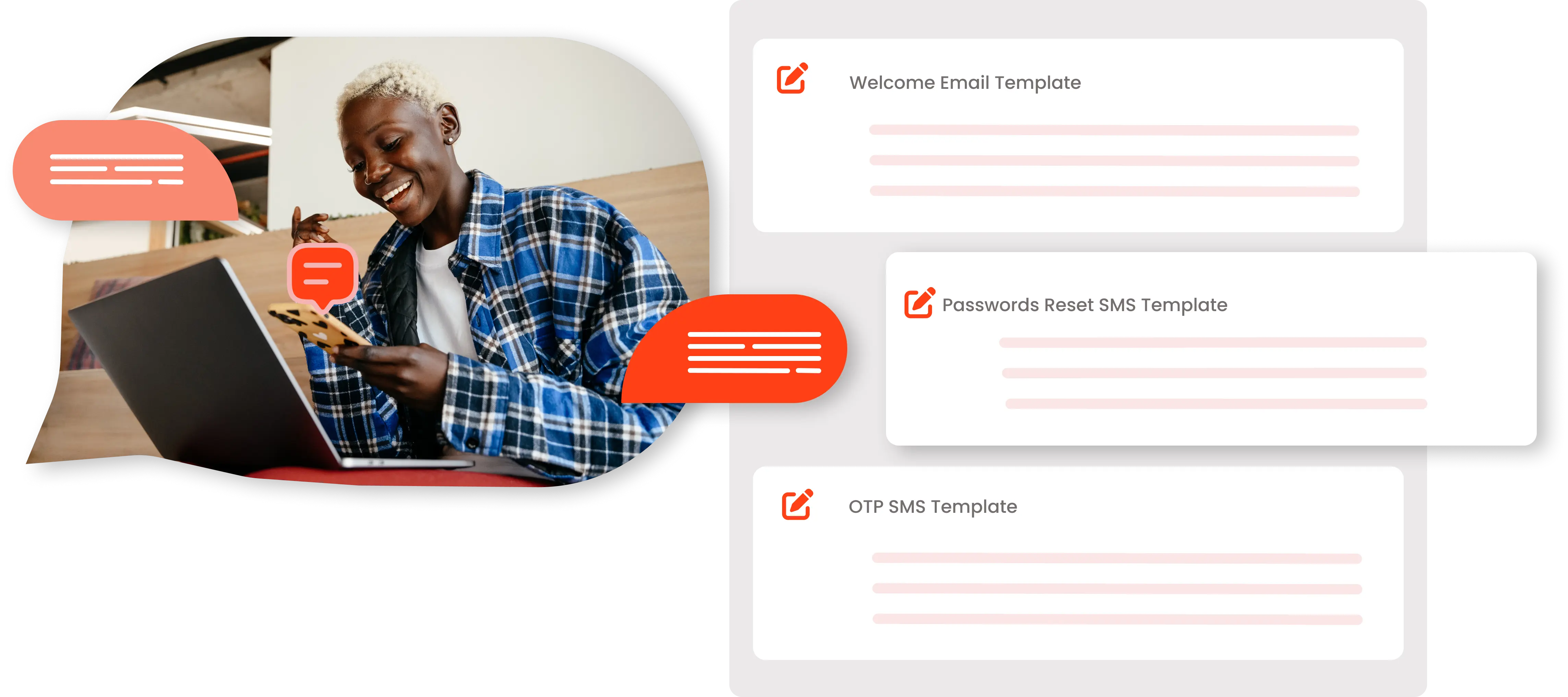
Based on customer engagement level, customize and automate emails & SMSs like:





I can't speak highly enough regarding miniOrange, I am totally satisfied with the process and results in every regard.
5.0

Awesome tech service, Awesome product. Overall Awesome people. This solution is very simple and easy to implement
5.0
Traditional or standard authentication methods using credentials like usernames or passwords are vulnerable. However, an added authentication factor or Multi-Factor authentication(MFA) methods like OTP sent to mobile devices or a link sent to email ids makes the authentication process more effective.


Secure your systems in High-risk Scenarios with an advanced form of MFA, called Adaptive MFA or Risk-Based Authentication. In high risk scenarios, admins can easily add an extra security layer by enabling our Adaptive engine which restricts users from accessing resources based on their IP Address, Location, Device, and Time of Access.
Provide your customers with easy password management so that they don’t have to remember their passwords every time and go through the hassle of changing passwords or setting secure passwords. This will reduce customers’ frustration with password management and increase customer loyalty.

Authentication is a critical aspect of information security that involves verifying the identity of a user or customer. It is a process that typically involves three components: identification, verification, and validation. The user or customer provides a unique identifier, such as a username or email address, and authentication credentials, such as a password or security token. The system then verifies these credentials against a trusted source, such as a database or directory, to determine if the user is authorized to access the requested resource. Once the authentication process is complete and the user's identity has been verified, they are granted access to the requested resource.
Authentication is the process of verifying the identity of a user or customer, involving identification, verification, and validation. Verification, on the other hand, is the process of checking a specific characteristic or attribute of a user or customer and it is a part of the authentication process. While authentication establishes identity and authorizes access to a resource, verification only confirms a particular attribute or characteristic.
Cloud-based applications typically require users to authenticate themselves before they can access the application and its associated resources. There are several ways to implement authentication for cloud-based applications, including using a cloud-based identity provider, such as miniOrange IAM & CIAM. If you want to create a hassle-free authentication experience for your customers who are logging into your cloud apps, it is recommended that you opt for the miniOrange CIAM solution.
An example of authentication in the context of Customer Identity and Access Management (CIAM) is when a customer logs into a retailer's e-commerce website to make a purchase. The customer is asked to provide their email address or username, along with a password or another form of authentication, such as a one-time code sent to their mobile device. The customer's credentials are then verified against a user database or directory managed by the CIAM solution. If the credentials are valid, the customer is authenticated and granted access to their account and the retailer's e-commerce platform. This authentication process ensures that only authorized customers can access their accounts and make purchases, which helps protect against fraudulent activity and enhances the overall security of the e-commerce platform.
