Need Help? We are right here!
Search Results:
×






IAM services are important for enforcing robust access control and identity verification processes crucial to safeguarding digital assets and IT infrastructure in any business. These services utilize advanced encryption, multi-factor authentication, and continuous monitoring to prevent unauthorized access and potential breaches. By integrating with a managed IAM service provider, businesses benefit from specialized expertise in deploying scalable solutions that adapt to evolving security threats and compliance requirements. This strategic solution streamlines user management and access governance, enhancing overall IT efficiency and reducing cybersecurity risks.
The range of Identity and Access Management (IAM) services is designed to ensure secure access control and permission management across your organization. By prioritizing security compliance, risk management, and operational efficiency, we deliver end-to-end IAM solutions tailored to meet your specific needs.
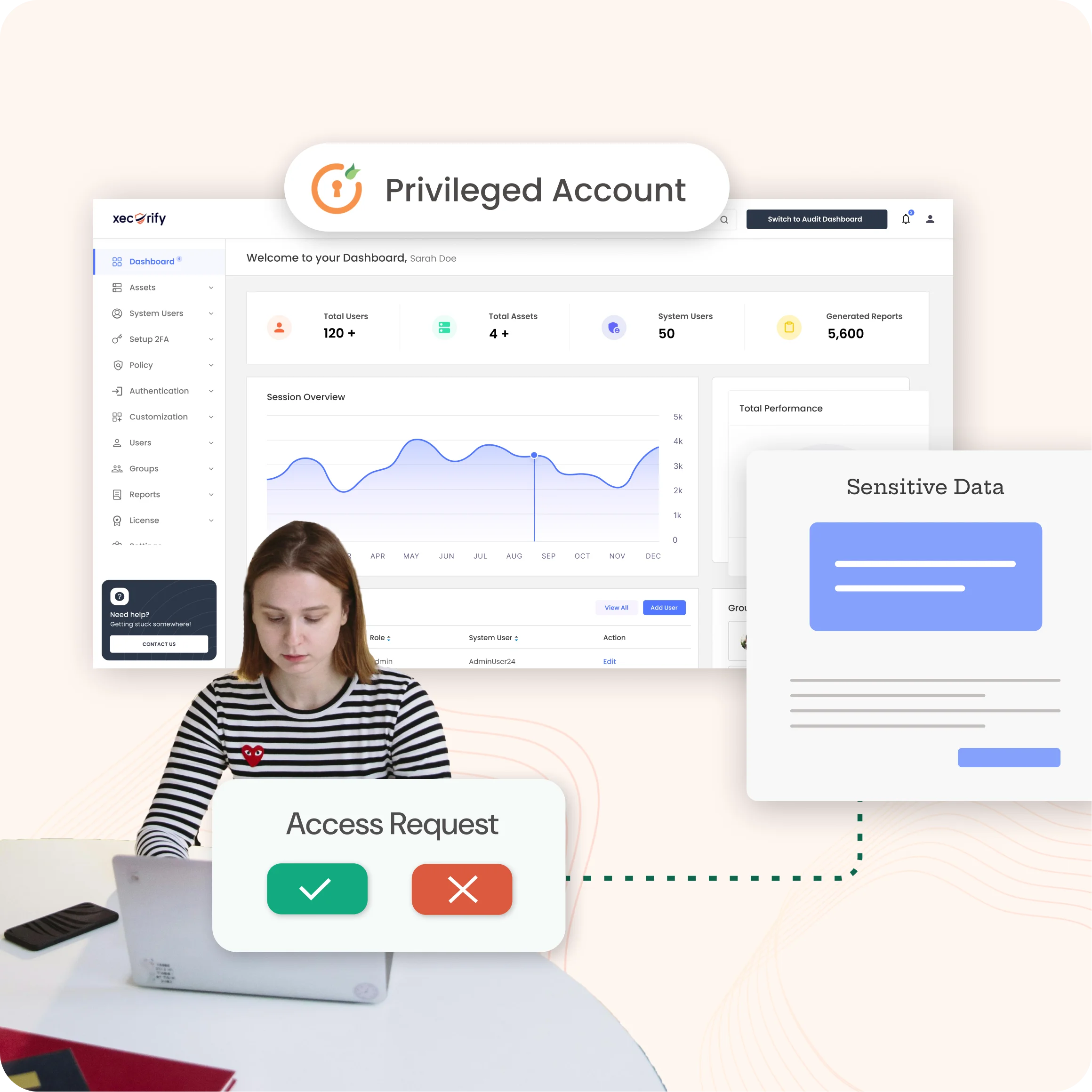
Secures and monitors privileged accounts that have access to critical systems. An effective PAM solution helps to prevent security breaches by controlling, managing, and auditing privileged accounts and sessions, reducing the risk of insider threats.
Enable secure and efficient access to your systems and applications with robust access management strategies. It focuses on authenticating and authorizing appropriate access to resources, ensuring that users have the right access at the right time.
Implement a Zero Trust security model where trust is never assumed and verification is required from everyone trying to access resources on your network. Additionally, Passwordless architectures also eliminates the need for traditional passwords, enhancing security and user convenience.
Manage every stage of the user identity lifecycle—from onboarding to offboarding—ensuring that access rights are correctly assigned and promptly revoked as roles change within your organization.
Single Sign-On solutions streamline the user authentication process by enabling access to multiple applications with a single login credential. This enhances user experience by reducing password fatigue and simplifying the login process. SSO is beneficial when users require access to various systems, minimizing the potential for password-related breaches.
Multi-factor Authentication requires users to provide two or more verification factors to gain access to resources. MFA is an essential component of our IAM services, providing an additional layer of security that protects against unauthorized access. By integrating something the user knows (password), something the user has (security token), and something the user is (biometrics), MFA significantly reduces the risk of security breaches.

Reduces the risk of unauthorized access by enforcing strict authentication, authorization, and user management protocols. MFA & Zero Trust models ensures protection against cyber threats.
Centralized access control via SSO allows secure and easy system and application access, boosting productivity and minimizing login issues.
Supports regulatory adherence with comprehensive audit logs and access tracking, ensuring role-based access control (RBAC) aligns with governance policies.
Through PAM ensures that elevated permissions are monitored and controlled, preventing misuse of critical systems and sensitive data.
Automates user provisioning, deprovisioning, and role adjustments, ensuring accurate access rights throughout an employee's tenure and reducing manual errors.
Leverage analytics to detect anomalous behavior, monitor access patterns, and proactively respond to potential security risks in real time.

We pride ourselves on building lasting relationships with our clients. We integrate deeply with your teams, ensuring a seamless experience and trust in every interaction.
Our depth of knowledge in crafting tailored IAM solutions is unmatched. From advanced Single Sign-On (SSO) systems to robust Multi-factor Authentication (MFA) and beyond, we have the proficiency to enhance your security landscape effectively.
The focus is on delivering IAM solutions that do more than just fulfill immediate needs. Our goal is to provide enduring value, helping your business remain secure and efficient in a rapidly evolving digital world.

Our Other Identity & Access Management Products