Need Help? We are right here!
Search Results:
×Integrated Windows Authentication (IWA authentication), introduced by Microsoft for Windows NT-based systems, simplifies user login to web applications by using Windows Active Directory as the user store. It is a popular choice among Windows server users and administrators.
It leverages protocols like Kerberos and NTLM. Kerberos uses tickets to allow nodes to prove their identity securely, while NTLM is a challenge-response authentication protocol. Both protocols are essential for enabling seamless and secure access to resources within a Windows environment.







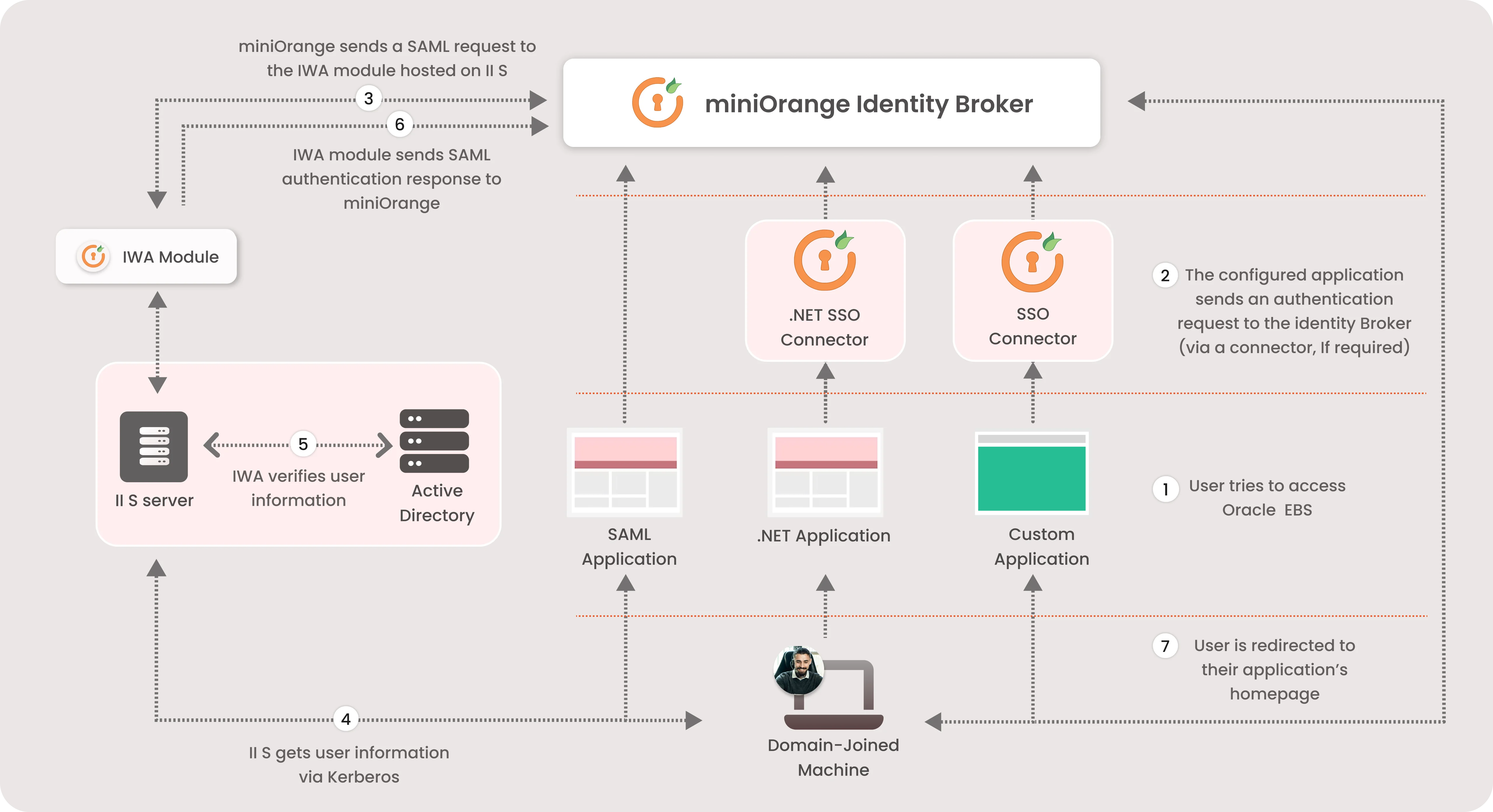
This workflow integrates Windows authentication with SAML to provide seamless Single Sign-On (SSO) for users accessing various applications. The Identity Broker and IWA modules work together to authenticate users against the Active Directory using Kerberos, enabling secure and efficient access management. This IIS server authentication leverages connectors for logging into custom-designed proprietary apps.
The user on a domain-joined machine tries to access their configured application (SAML Application, .NET Application, or Custom Application).
The configured application sends an authentication request to the miniOrange Identity Broker via a connector (if required). miniOrange sends a SAML request to the IWA module hosted on the IIS server.
The IIS server retrieves the user's information via Kerberos authentication from the Active Directory (AD).
The IWA module verifies the user's information with the Active Directory.
The IWA module sends a SAML authentication response back to the Identity Broker. The user is redirected to their application's homepage, successfully authenticated.
Employees accessing internal company websites or applications without repeatedly entering their login credentials.
Integrated into cloud apps and Onpremise applications that require secure and seamless user authentication within a Windows environment.
Seamless integration with Legacy applications e.g. Oracle E-business Suite and SAP ECC.
Single Sign-On (SSO)
IWA enables Single Sign-On, allowing users to log in once and gain access to multiple resources without needing to re-enter credentials.
Security
It uses the underlying Windows security mechanisms, such as Kerberos or NTLM (NT LAN Manager), to authenticate users, providing a secure way to manage authentication.
User Experience
Users experience seamless access to resources, as the authentication process happens in the background using their existing Windows session credentials.
Ease of Administration
Administrators can manage user accounts and access policies centrally through Active Directory, simplifying the management of user authentication and permissions.

*Please contact us to get volume discounts for higher user tiers.
| Feature | Integrated Windows Authentication | Basic Authentication |
|---|---|---|
| Credential Transmission | Not sent in plain text | Sent in plain text (Base64) |
| Security | More secure (Kerberos/NTLM) | Less secure (vulnerable without SSL) |
| User Experience | Seamless, automatic login | Requires manual entry |
| Best Use Case | Intranet environments | Intranet and internet applications |
| Requirement | Domain membership | No domain requirement |
Windows authentication (formerly named NTLM, and also referred to as Windows NT Challenge/Response authentication) is a secure form of authentication because the user name and password are hashed before being sent across the network.
Integrated Windows Authentication is compatible with most modern web browsers but may have limitations with some HTTP proxy servers. It is ideal for intranets where all clients are within a single domain. Supported browsers include:
The key advantage of IWA authentication is that users logged into the Windows domain are automatically authenticated for IWA-enabled web apps without needing to re-enter credentials, provided they are valid users and the main drawback of IWA authentication is its reliance on Windows Active Directory, requiring both the client and server to run Windows NT-based systems and be connected to the server's domain. It is limited to intranet environments.

Our Other Identity & Access Management Products