Need Help? We are right here!
Search Results:
×Premium Customers
Integrations
Available for you
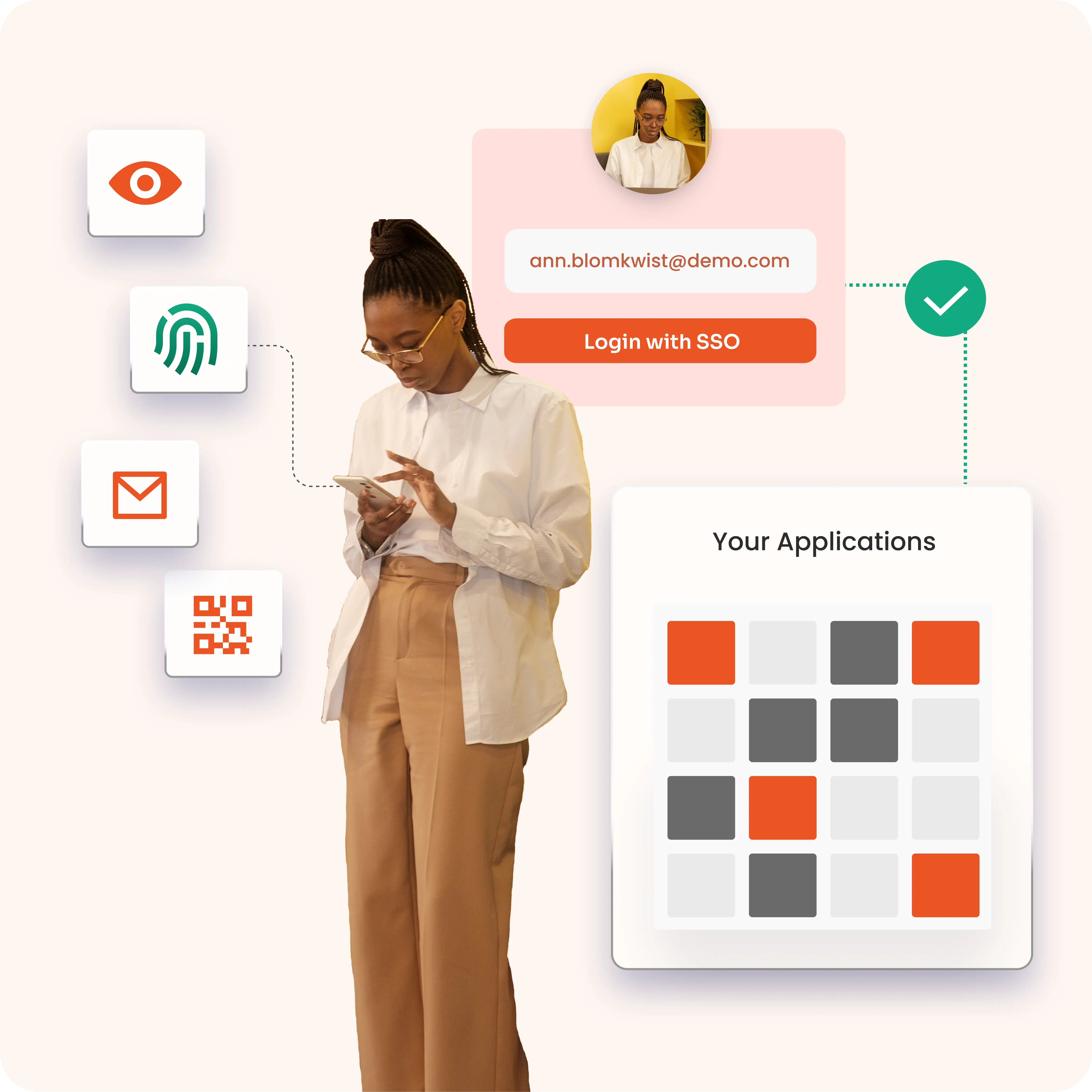
Policy-based access control allows you to manage user access through centralized, tailored policies. You assign permissions based on roles, departments, or specific criteria, simplifying access management and reinforcing security. This approach drops administrative overhead and adapts easily to your changing business needs.
Simplify your access control by managing all policies from a single, unified platform. With miniOrange, you can create, modify, and enforce access rules across your entire organization without the hassle of juggling multiple systems. This centralization reduces administrative overhead and ensures consistent application of security measures, making it easier to maintain compliance and respond quickly to changing business needs.
Tailor permissions with precision by assigning access rights based on specific roles, departments, or even individual users. miniOrange allows you to define detailed policies that align exactly with your organizational structure and workflows. This granularity ensures that employees have access only to the resources they need, minimizing the risk of unauthorized access and enhancing overall security.
Check out more →Improve your security posture with controls that adjust dynamically to real-time contexts. miniOrange's system considers factors like user location, device type, time of access, and network security when granting permissions. If a login attempt appears unusual or risky, the system can require additional authentication steps or restrict access altogether. By adapting to the context, you proactively defend against threats without hindering legitimate user activity.
Check out more →PBAC works seamlessly with any application, regardless of its technical setup, ensuring broad compatibility.
It utilizes any existing data for decision-making, allowing for dynamic and context-aware access control.
Policies are written once and reused, making it ideal for large organizations by simplifying policy management.
Ensures adherence to organizational rules and regulations, providing full visibility for compliance personnel.
Offers better oversight of user activities and access controls, crucial for managing remote employees and collaboration.
Enforces strict access controls, regardless of roles or designations, enhancing security within the organization.
Start your identity management strategy by setting up policies that align with your organization's security requirements.
Here is why you must consider implementing policy-based access control
Assign precise access rights based on policies to minimize unauthorized access and protect sensitive data effectively.
Manage all access policies centrally, reducing complexity and administrative overhead while saving valuable time.
Easily align access controls with regulatory requirements, making compliance audits smoother and less stressful.
Adapt quickly to organizational changes by updating policies in one place, ensuring your access controls scale seamlessly with your business needs.
Gain clear insights into who has access to what resources, making it easier to monitor and audit access controls.
Provide users with the right access at the right time, reducing friction and improving overall productivity.
Let us compare the most popular access control models to restrict user access based on policies, attributes, and roles.
| Feature | Policy-based Access Control PBAC | Attribute-based Access Control ABAC | Role-based Access Control RBAC |
|---|---|---|---|
| Definition | Access is granted based on policies defined by administrators. | Access is granted based on attributes of users, resources, and environment. | Access is granted based on roles assigned to users. |
| Flexibility | High, as policies can be very specific and detailed. | Very high, as it considers multiple attributes. | Moderate, as it depends on predefined roles. |
| Scalability | High, suitable for large and complex environments. | Very high, suitable for dynamic and diverse environments. | Moderate, suitable for stable environments with well-defined roles. |
| Complexity | High, requires detailed policy definitions. | High, requires management of multiple attributes. | Low to moderate, roles are easier to manage. |
| Use Cases | Suitable for environments with complex and dynamic access requirements. | Suitable for environments where access decisions depend on multiple factors. | Suitable for environments with stable and well-defined roles. |
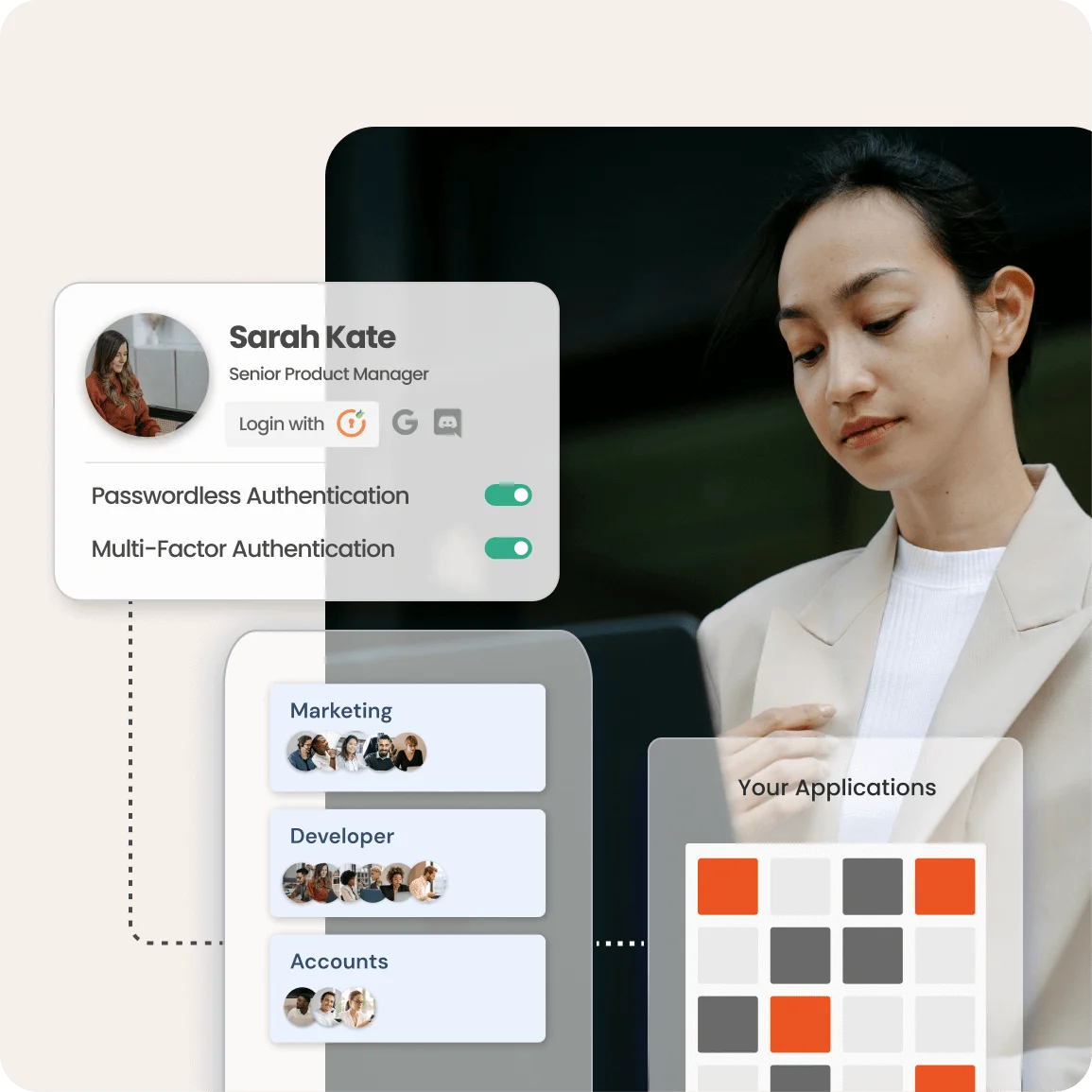
At miniOrange, we offer a powerful PBAC solution designed to secure and streamline your access control needs. Our platform integrates effortlessly with your existing systems, allowing you to manage permissions dynamically based on user attributes and context.
With miniOrange, you can boost security, ensure compliance, and simplify operations, all while reducing administrative tasks. Trust us to protect your resources and empower your team with the right access at the right time.





I can't speak highly enough regarding miniOrange, I am totally satisfied with the process and results in every regard.
5.0

Awesome tech service, Awesome product. Overall Awesome people. This solution is very simple and easy to implement
5.0

Our Other Identity & Access Management Products