Need Help? We are right here!
Search Results:
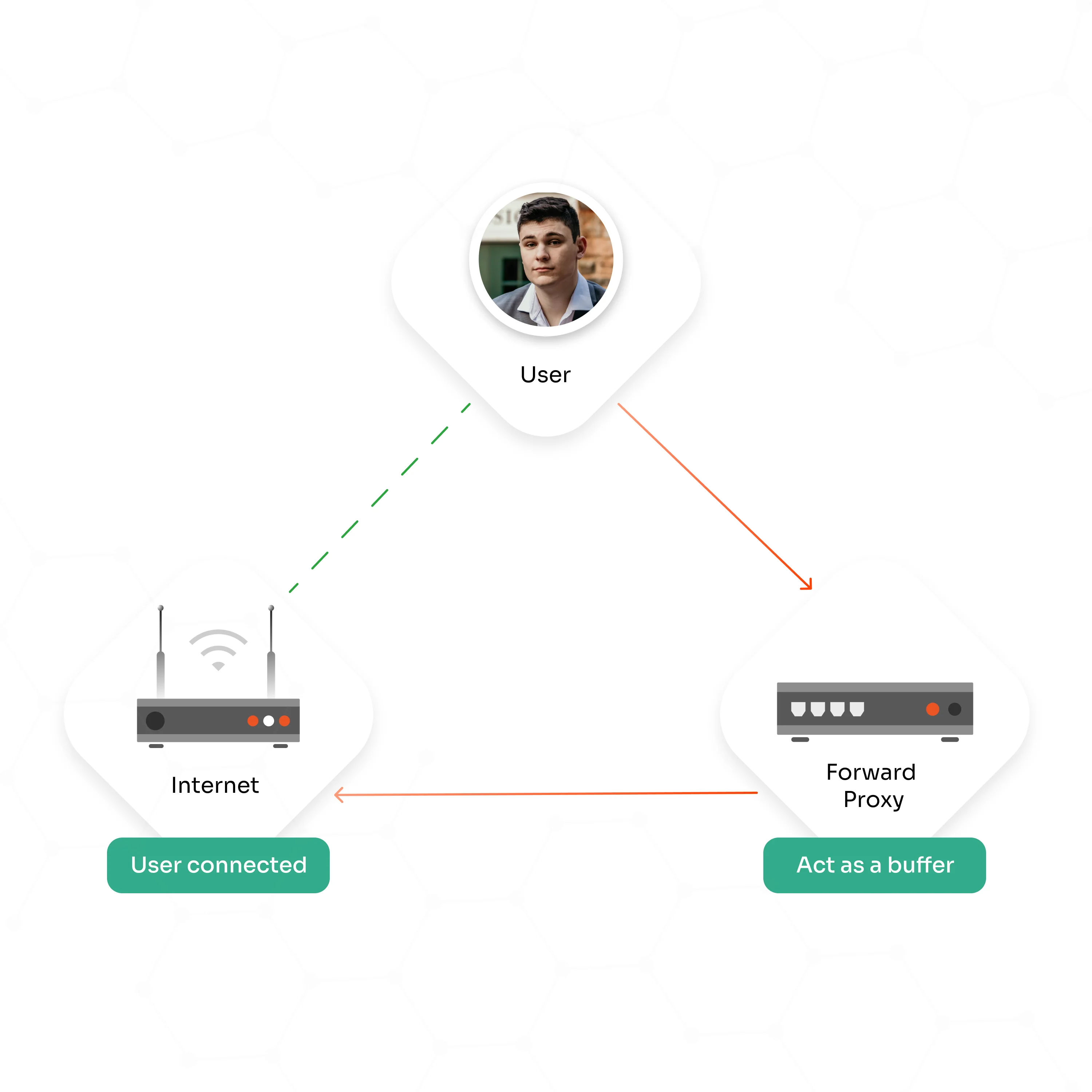
×A Forward Proxy solution acts as a buffer between your corporate computer systems and the internet, allowing secure communication and protecting your sensitive resources and data privacy.

A Forward Proxy acts as a vital facilitator between an organization's internal network and the World Wide Web. By passing queries from company devices to external servers and returning responses, Forward Proxy provides secure communication.
Its pivotal functions also extend to access control, allowing enterprises to filter and monitor internet traffic, prohibit dangerous information, and enforce acceptable use policies or regulations.
A Forward Proxy becomes a versatile tool for preserving sensitive data, ensuring privacy, and eliminating cybersecurity risks within the business environment by anonymizing user identities, optimizing bandwidth, and conducting SSL inspection.
In the dynamic corporate landscape, network security is pivotal and the choice between a forward proxy and a traditional firewall becomes critical. Each caters to specific organizational needs and challenges:
| Aspect | Forward Proxy | Traditional Firewalls |
|---|---|---|
| Corporate Security | Focuses on user privacy and policy enforcement within the internal network. | Used for the purpose of broader access control across network boundaries. |
| Inspection Scope | Inspects and secures web traffic to block online threats and unauthorized access. | Inspects various types of network traffic beyond the confines of web communication. |
| Protocol-Level Expertise | Works minutely at the application layer, specialized for handling web requests. | Operates predominantly at the network and transport layers, but not on the application layer. |
In the corporate network, if the employees can access their personal email accounts using company-issued devices, then there lies a risk that they may knowingly or unknowingly leak sensitive data through their personal email. Hence, blocking personal email access at work is crucial for corporate enterprises.
Using the Forward Proxy solution, companies can configure policies to block access to all email domains other than the company domain. The solution acts as a buffer or gatekeeper that analyzes the client request (user access request) and takes appropriate action as per the policies. Admins can also configure custom policies to block access to certain email accounts as well.
Block user access to personal Gmail accounts while at work to elevate data security, ensuring no data is shared or transferred between personal and business email accounts.
Prevent users from accessing their personal Outlook accounts while at work, and prevent any data from being shared or moved between personal and corporate Outlook accounts.
To ensure that no data is exchanged or transmitted between personal and corporate Hotmail accounts, restrict user access to personal Hotmail accounts while at work.

Navigating the cloud landscape involves a multitude of SaaS applications, and there lies a major challenge in detecting and monitoring user access to Unsanctioned Apps or Shadow IT. This can open up new vulnerabilities to potentially cause critical data breaches. A Forward Proxy solution can be used to discover Shadow IT and monitor user access to these apps by enforcing access governance.
Today, rapid data sharing through different SaaS apps is super easy. The risk of users uploading critical business data to unsafe locations is a major security challenge that most organizations face. To solve this, a Forward Proxy can be used to boast the scalability for meticulously inspecting all web traffic, thwarting the inadvertent exposure of sensitive information between different SaaS apps.


The internal structure of a corporate organization is a potential target for attackers seeking to invade the privacy of the company to gain access to critical data. But by channeling all web traffic through the Forward Proxy, companies can create a formidable barrier, restricting attackers and privacy invaders from gaining the visibility needed to map the corporate network intricacies and weaknesses.

The Cloud Access Security Broker or CASB Forward Proxy serves as an intermediary, allowing secure connections between internal users and the cloud while offering in-depth visibility and governance. The miniOrange CASB Forward Proxy helps organizations protect confidential information, maintain compliance, and reduce security concerns related to cloud computing.
Forward Proxy is widely used for adding Single Sign-On (SSO) for applications that do not support any standard SSO protocol like SAML, OAuth, or OpenID by default. miniOrange supports a huge list of such applications and supports all the standard SSO protocols like SAML, OAuth, JWT, WS-Fed, etc.
The main difference between a forward proxy and a reverse proxy is that a forward proxy allows computers isolated on a private network to access the internet, while a reverse proxy enables computers on the internet to access private networks. Although a reverse proxy and forward proxy both serve a common mission, they perform drastically different functions and serve decidedly different clients.

Our Other Identity & Access Management Products