Need Help? We are right here!
Search Results:
×Federal Information Processing Standards (FIPS), specifically FIPS 140-2, are critical for ensuring the security of cryptographic modules that protect data during storage (data-at-rest) and transmission (data-in-motion). FIPS 140-2, defined by the National Institute of Standards and Technology (NIST), outlines stringent requirements for encryption algorithms to ensure they meet the high-security standards necessary for federal and defense cybersecurity compliance.
FIPS (Federal Information Processing Standards) are essential guidelines that ensure cryptographic security across various platforms. Among these, FIPS 140-2 is important, addressing the security requirements for cryptographic modules protecting sensitive data both at rest and in motion. This standard categorizes security into four distinct levels, each offering a progressively higher degree of security:
This basic level requires the use of approved cryptographic algorithms and production-grade equipment. It ensures that the cryptographic module employs at least one tested and validated encryption algorithm.
Enhancing security from Level 1, includes role-based authentication and requires the use of tamper-evident physical devices. Systems must operate on an OS approved by Common Criteria at EAL2.
Targeted for more secure environments, Level 3 adds requirements for tamper-resistant devices and segregates logical and physical interfaces that manage critical security parameters. It mandates identity-based authentication and encrypted key management using FIPS-approved algorithms like AES, RSA, or ECDSA.
The highest security level offered by FIPS 140-2, this level demands that devices be tamper-active and capable of erasing stored information in response to environmental threats. It also imposes stricter OS security requirements, especially in multi-user scenarios.

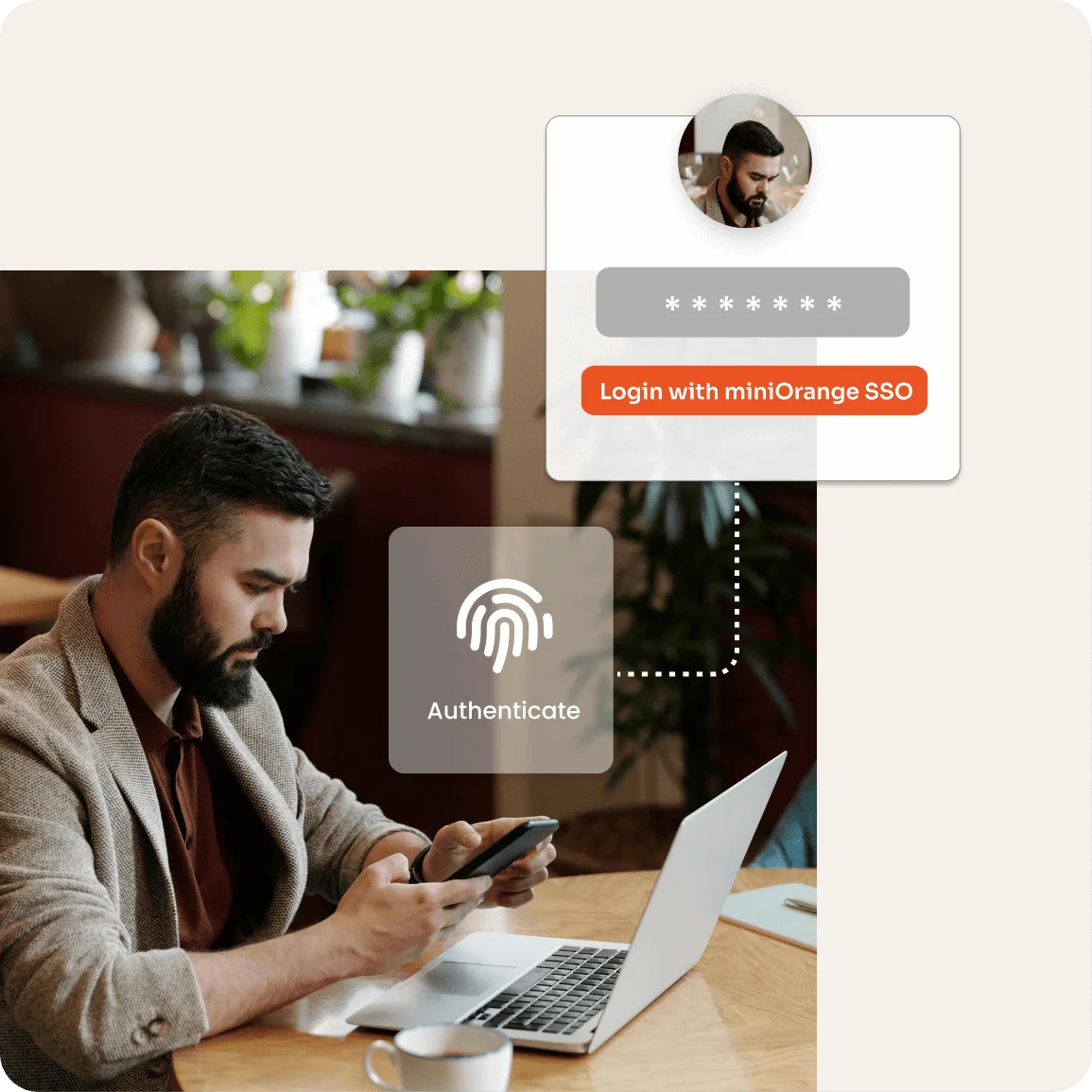
miniOrange offers a comprehensive suite of cybersecurity solutions designed to meet FIPS compliance requirements, ensuring secure encryption and access management. Our Identity and Access Management (IAM) solutions, including Multi-Factor Authentication (MFA), Single Sign-On (SSO), and Privileged Access Management (PAM), provide robust protection for sensitive data at rest and in transit.
With FIPS 140-2 compliant encryption, miniOrange helps organizations enforce stringent security measures, safeguarding cryptographic operations against unauthorized access and threats. Our solutions integrate seamlessly with existing infrastructures, offering real-time monitoring, compliance auditing, and automated reporting to streamline regulatory adherence.
By leveraging miniOrange’s secure and scalable solutions, organizations can confidently achieve and maintain FIPS compliance, ensuring their data security aligns with the highest federal and industry standards.
Years of Experience
Customers Worldwide
Customer Support
Cost Saved