 en
en Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×Fortinet Single Sign-On (FSSO) solution by miniOrange provides you with secure Single Sign-On access to multiple On-Premise and Cloud Applications using a single set of login credentials. With miniorange’s Identity Provider (IDP) service you can use SSO to login to multiple applications using a single Fortinet username and password. Looking at another way, if your users are in any third-party Identity Providers (Azure Active Directory, Okta, Auth0) and you want your users to log into Fortinet (Fortigate) using existing IDP credentials, you can easily allow them to use SSO to login securely.
miniOrange provides user authentication from various external sources, which can be Directories (like ADFS, Microsoft Active Directory, OpenLDAP, AWS etc), Identity Providers (like Microsoft Entra ID, Okta, AWS), and many more. You can configure your existing directory/user store or add users in miniOrange.
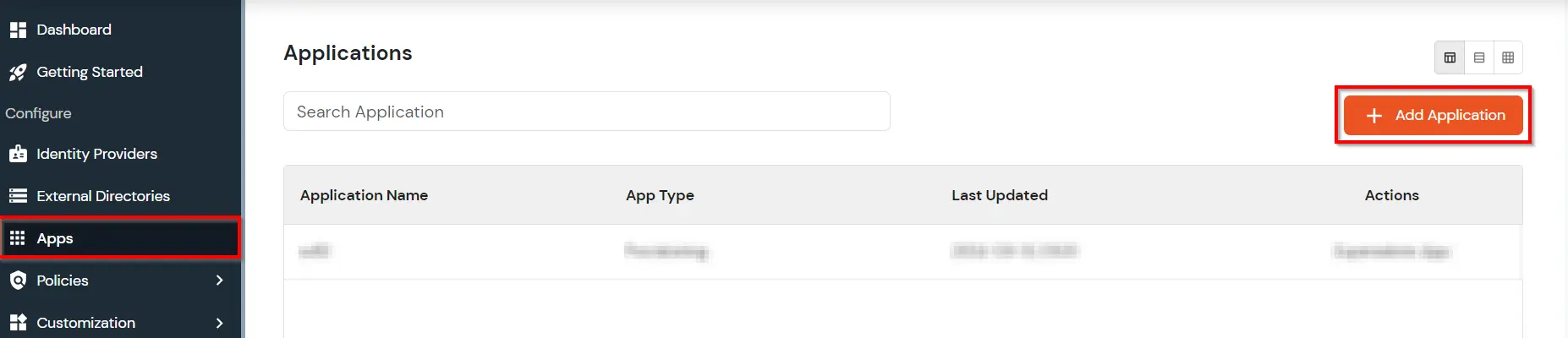
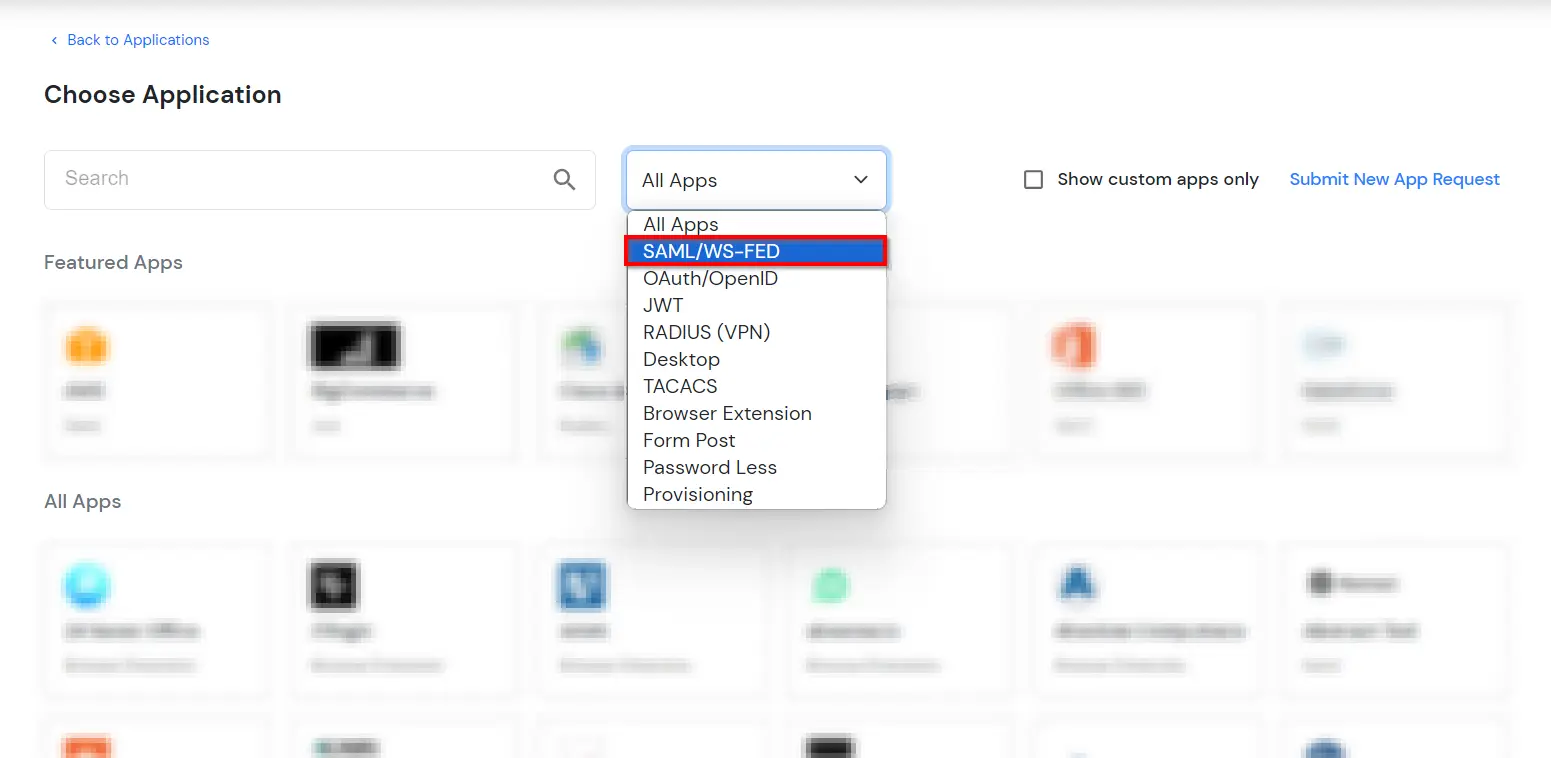
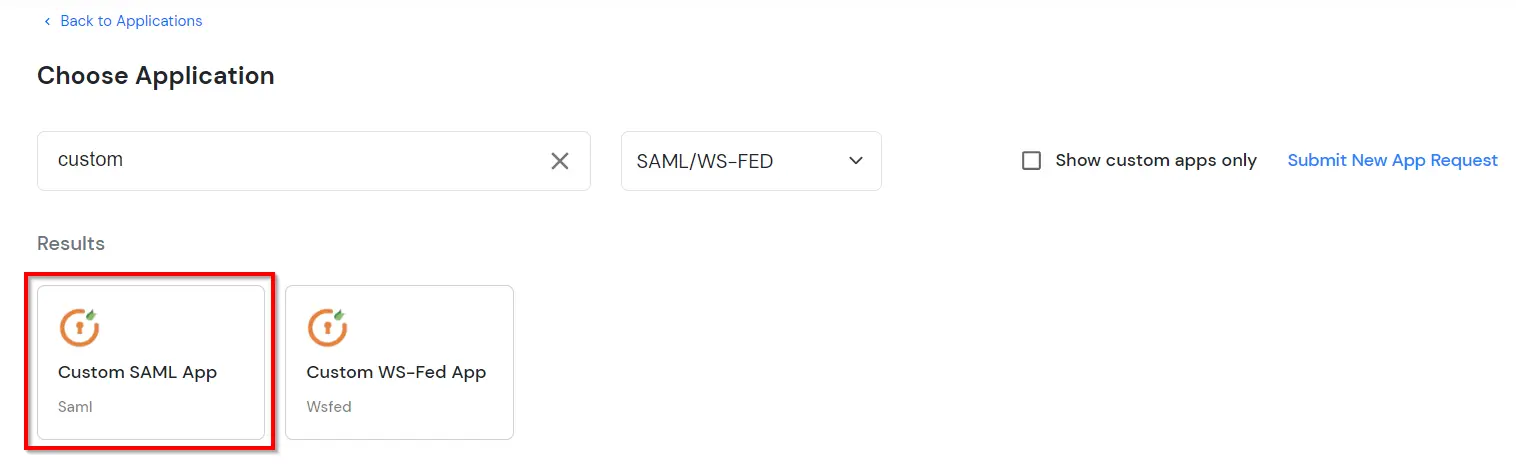
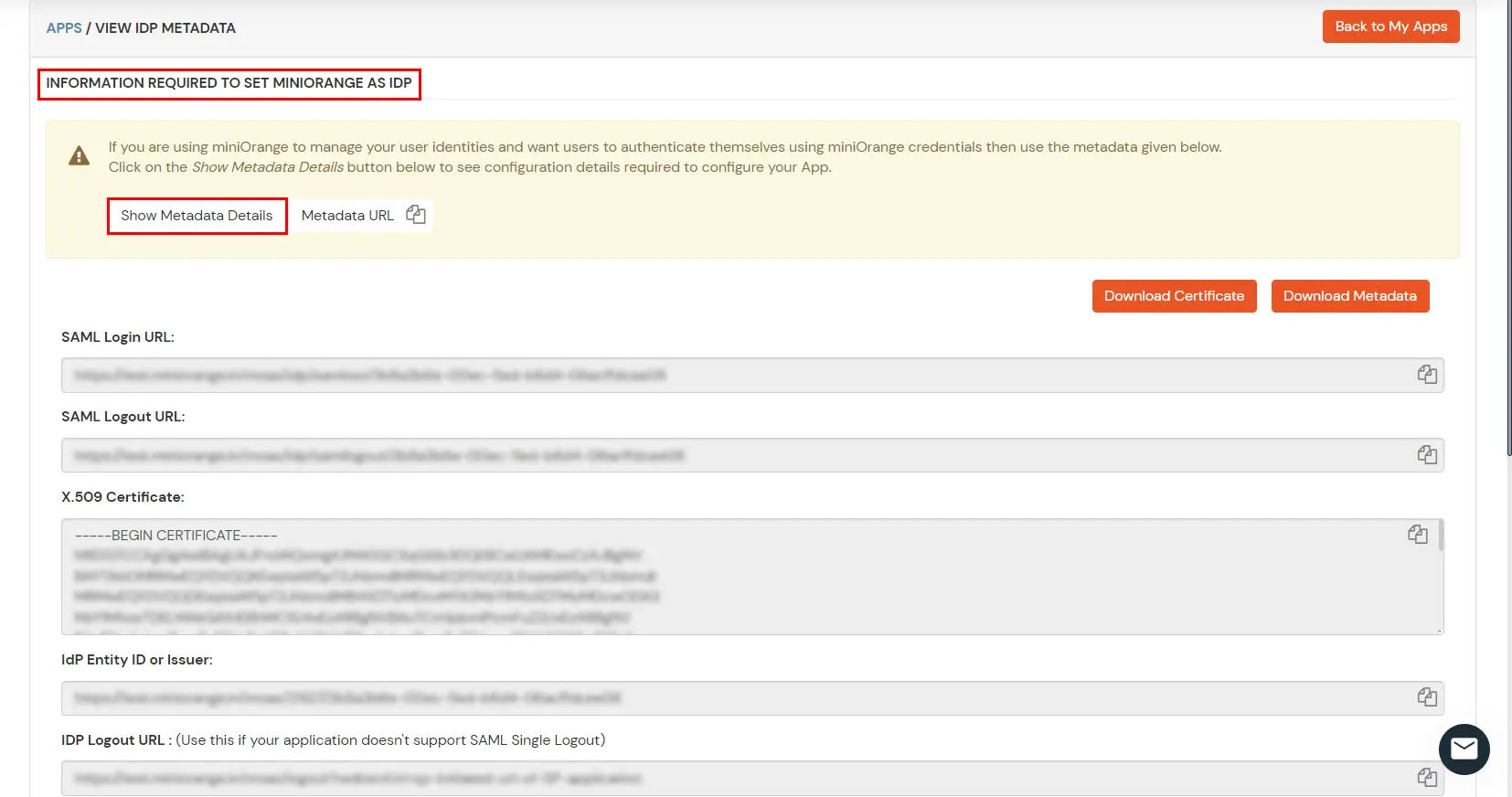
| SP Entity ID or Issuer: | https://fortigate-ip:port/saml/metadata |
| ACS URL: | https://fortigate-ip:port/saml/login |
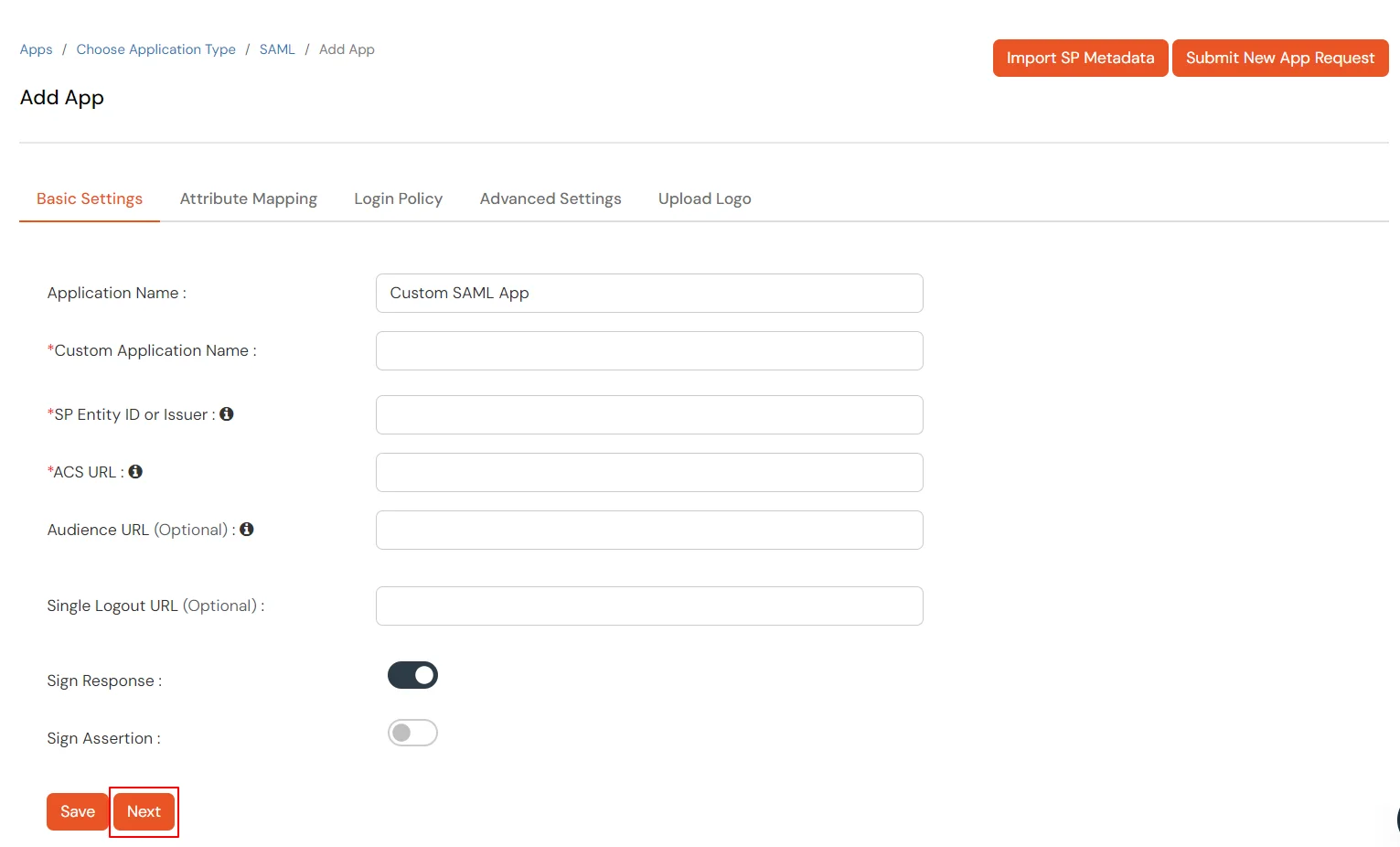
| Name ID: | E-mail Address |
| NameID format: | urn:oasis:names:tc:SAML:2.0:nameid‑format:emailaddress |
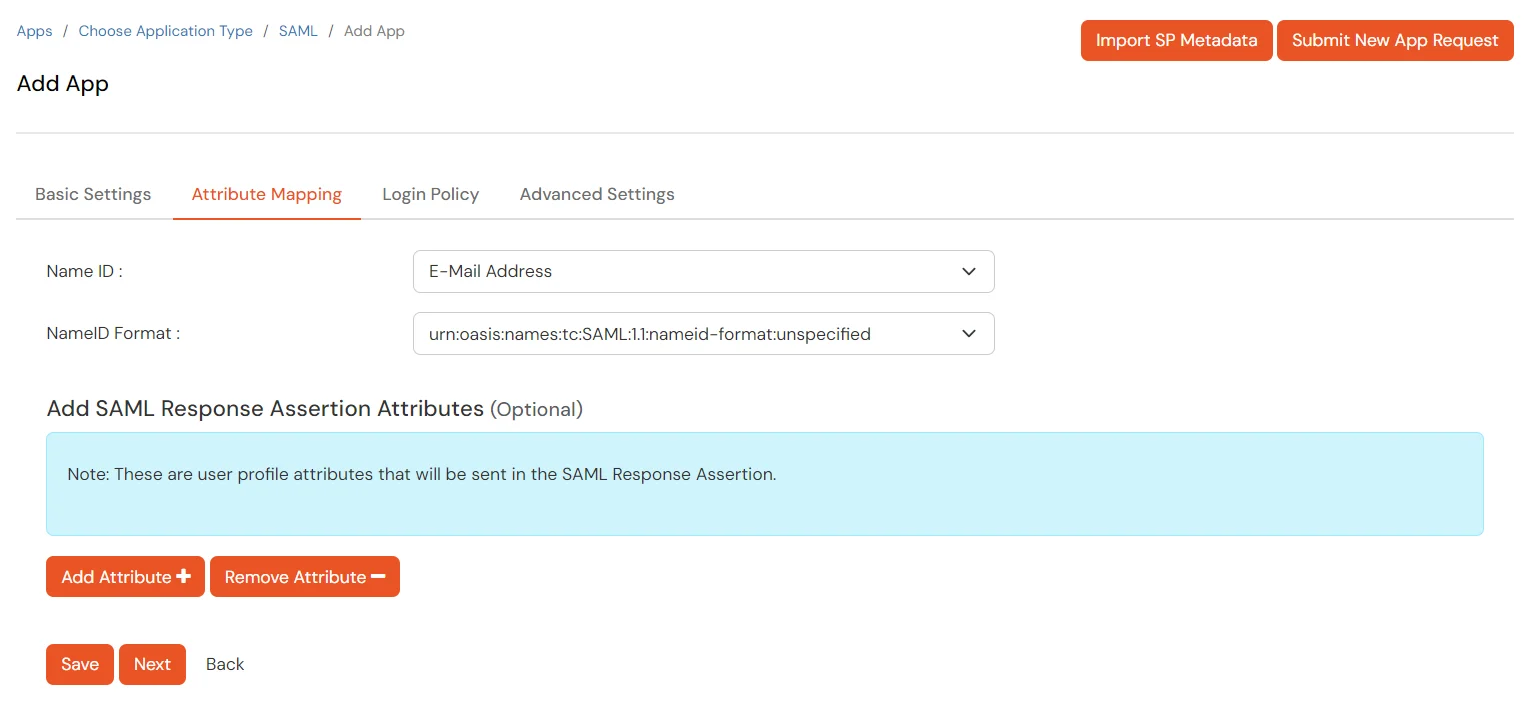
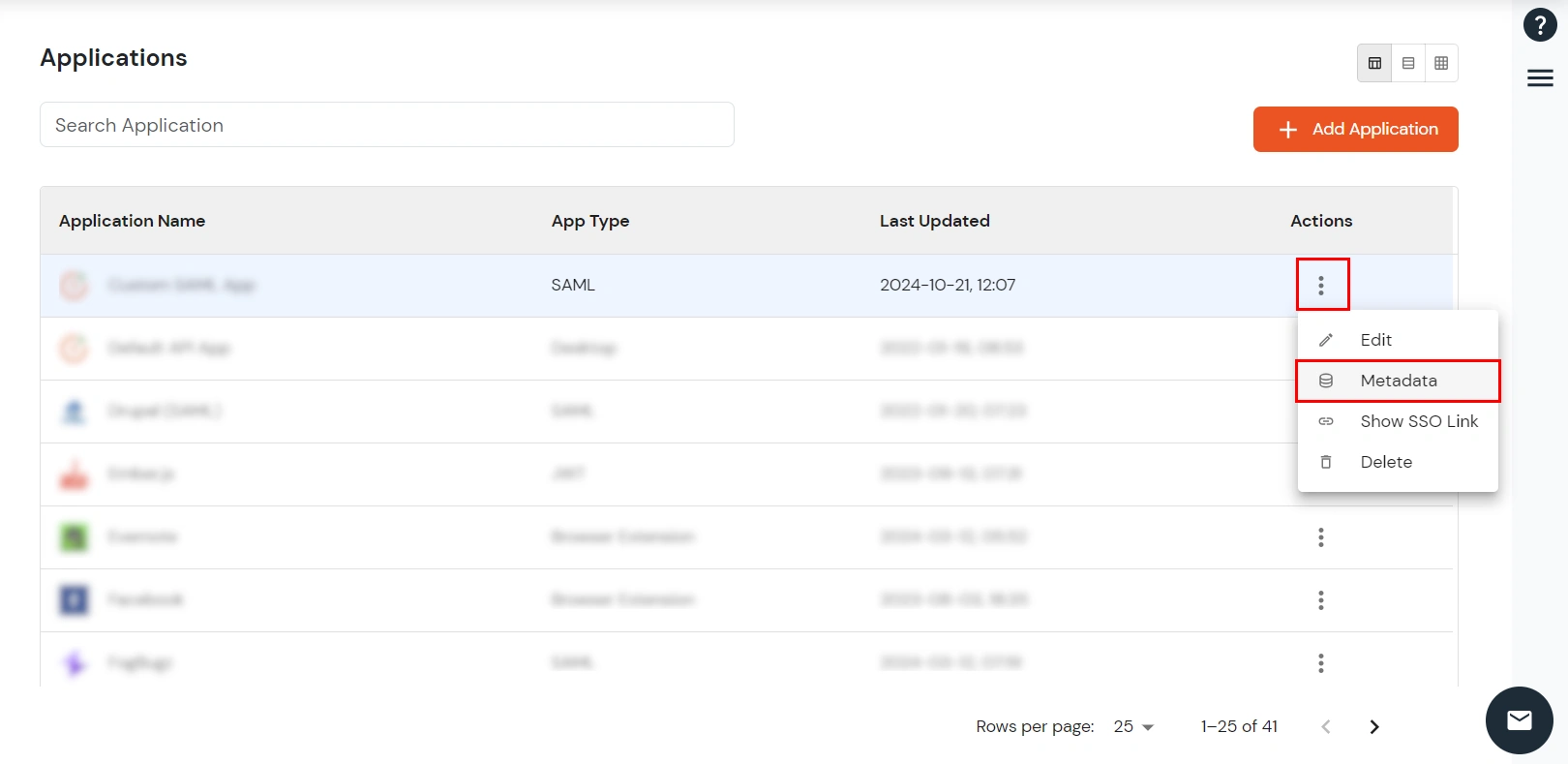
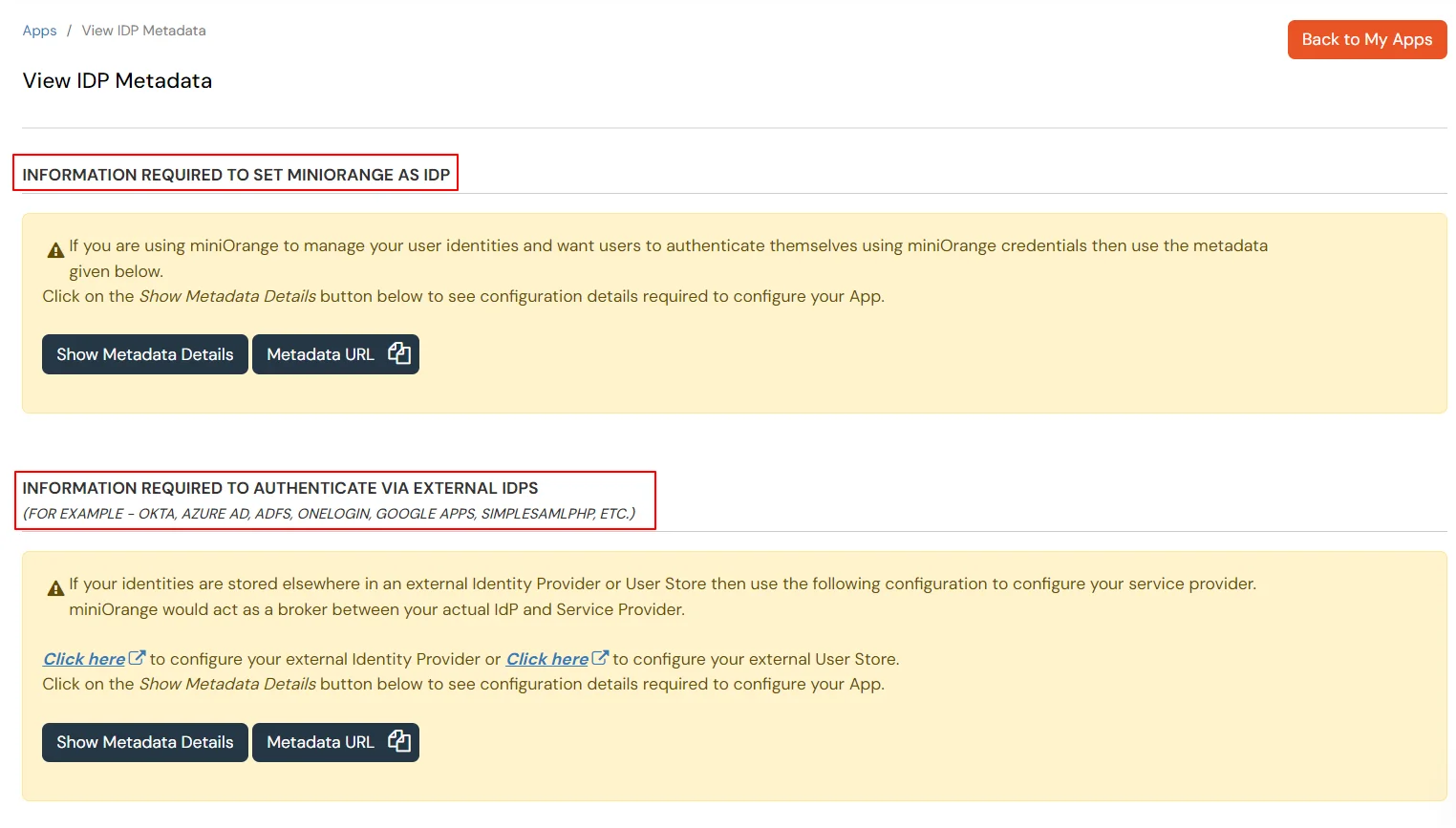
To get miniOrange metadata details in order to configure Fortinet :
| GUI in version 6.2. | Go to User & Device -> SAML SSO |
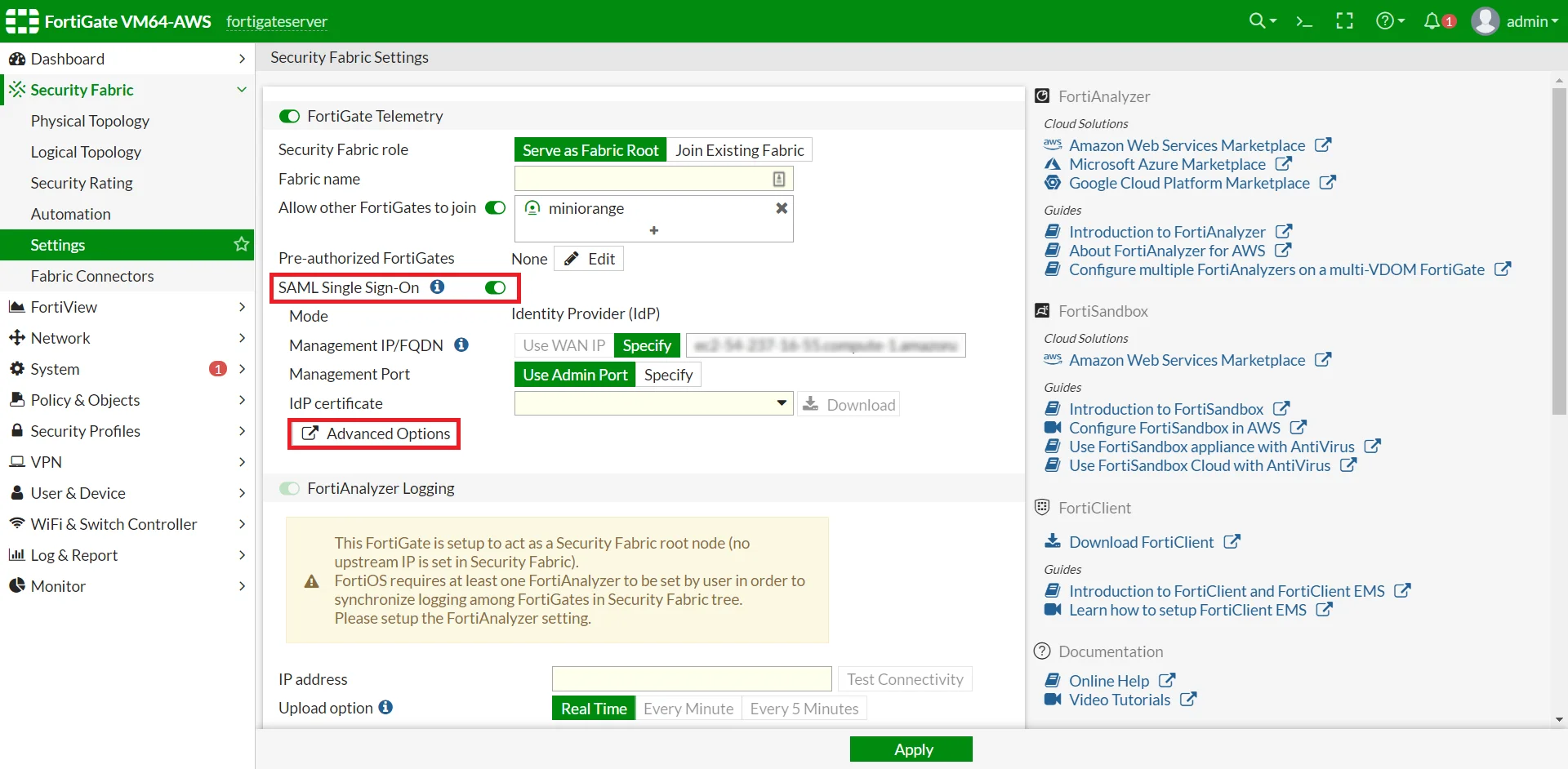
| GUI in version 6.2.3 and above. | Go to Security Fabric -> Settings Enable FortiGate Telemetry, choose a Fabric name and an IP for FortiAnalyzer (can be an unused address) Enable SAML Single Sign-On, Click on Advanced Options |
| GUI in version 6.4 and above | Go to Security Fabric -> Fabric Connectors -> Security Fabric Setup -> Single Sign-On Settings |

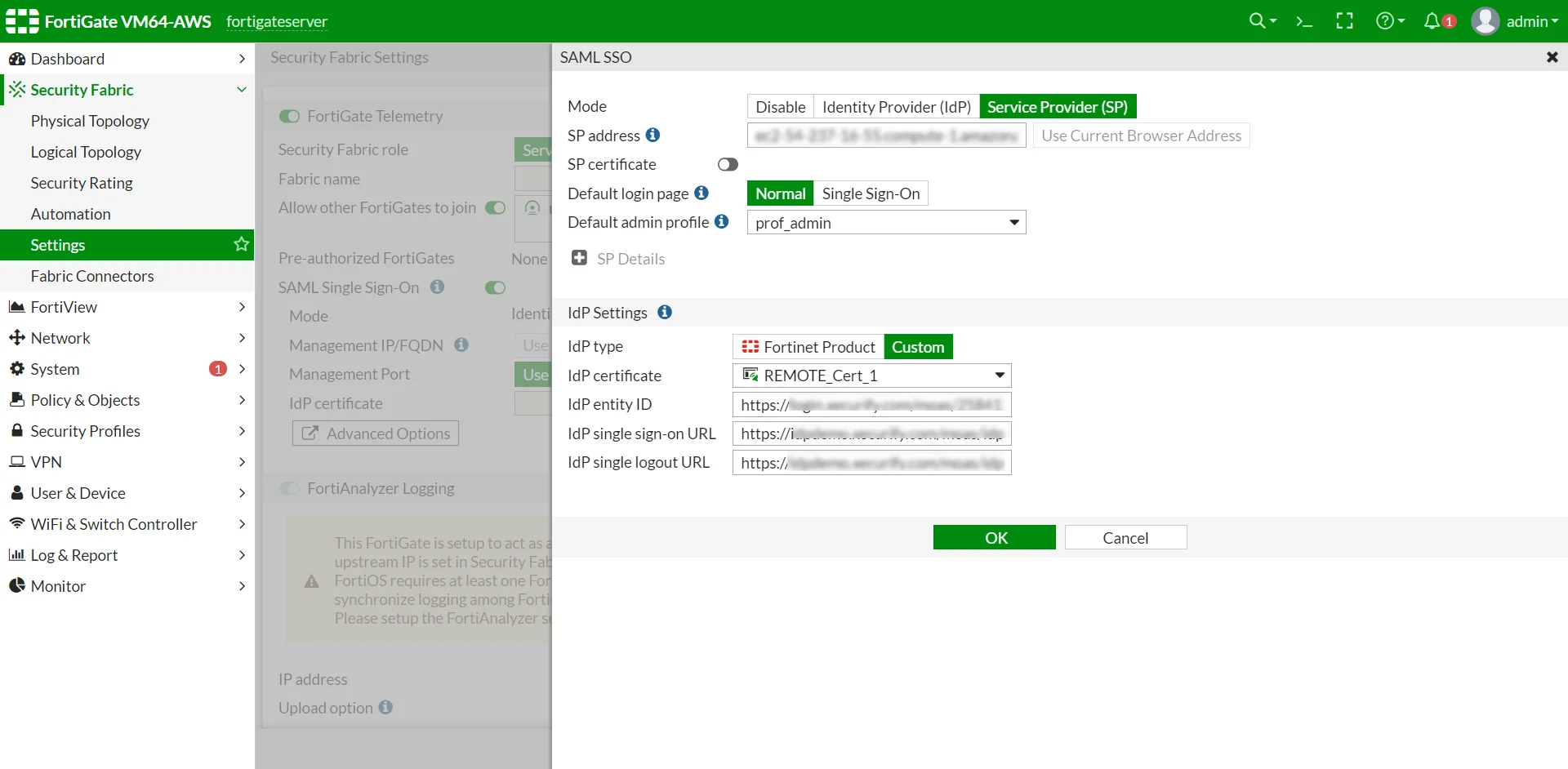
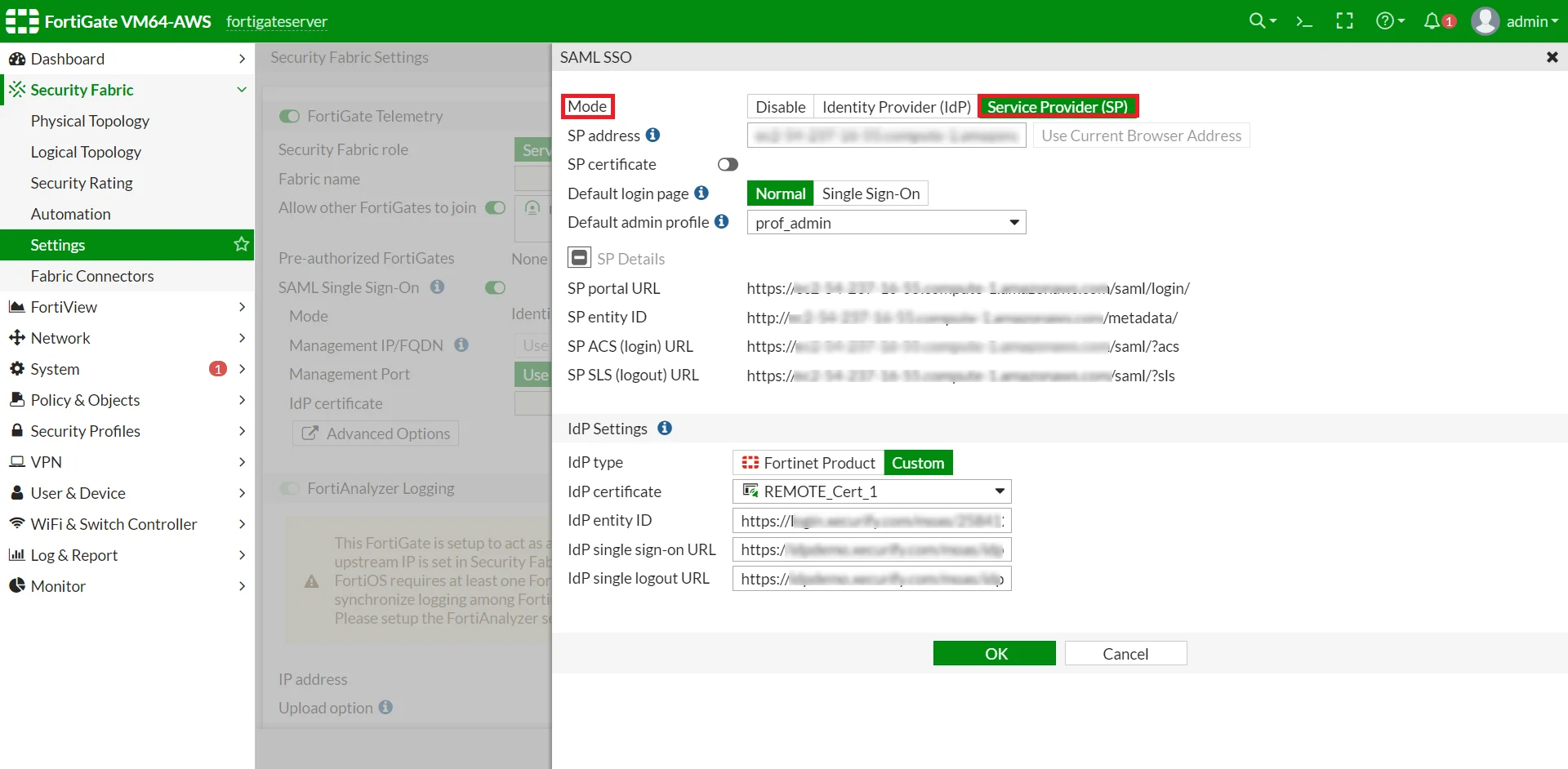
| IDP Entity ID | Entity ID or Issuer in miniOrange |
| IDP Single Sign-On URL | SAML Login URL in miniOrange metadata |
| IDP Single Logout URL | SAML Logout URL in miniOrange metadata |
Test SSO login to your Fortinet account with miniOrange IdP:



Contact us or email us at idpsupport@xecurify.com and we'll help you setting it up in no time.

Our Other Identity & Access Management Products