Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×GitHub SAML Single Sign-On (SSO) for enterprise cloud solution by miniOrange provides secure Single Sign-On access to GitHub & multiple On-Premise and Cloud Applications using a single set of login credentials. With miniOrange IDP service you can SSO login to multiple applications using a single Github username and password. Github Single Sign-On (SSO) can also be enabled if your users are in any of the third-party Identity Providers and you want your users to log into Github uisng existing IdP credentials, you can easily allow them to SSO into Github in a secure manner.
With miniOrange GitHub SSO, you can:
miniOrange offers free help through a consultation call with our System Engineers to Install or Setup Github SSO solution in your environment with 30-day free trial.
For this, you need to just send us an email at idpsupport@xecurify.com to book a slot and we'll help you in no time.
miniOrange Github SAML integration supports the following features:
miniOrange provides user authentication from various external sources, which can be Directories (like ADFS, Microsoft Active Directory, OpenLDAP, AWS etc), Identity Providers (like Microsoft Entra ID, Okta, AWS), and many more. You can configure your existing directory/user store or add users in miniOrange.
https://github.com/enterprises/<custom_domain_name>https://github.com/enterprises/<custom_domain_name>/saml/consume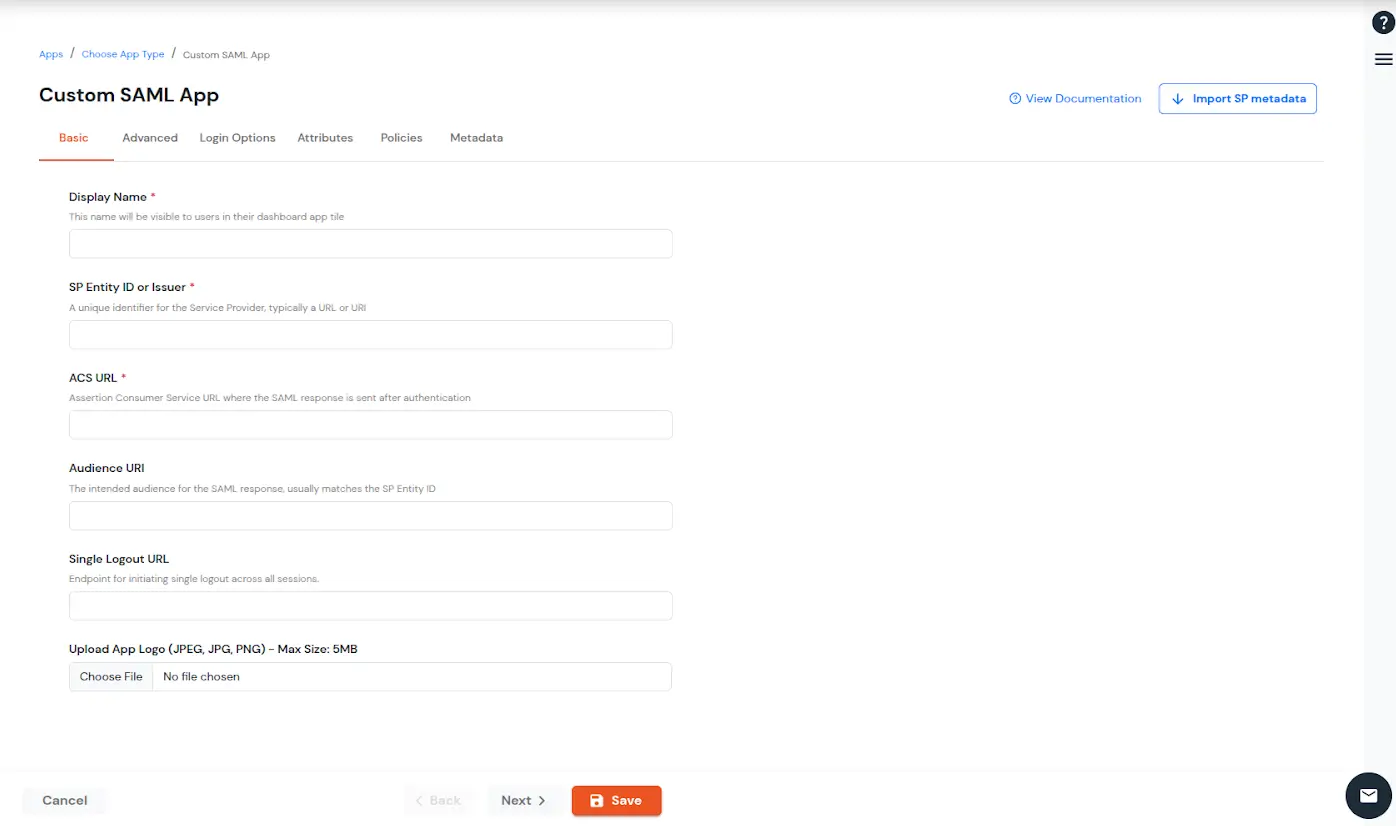
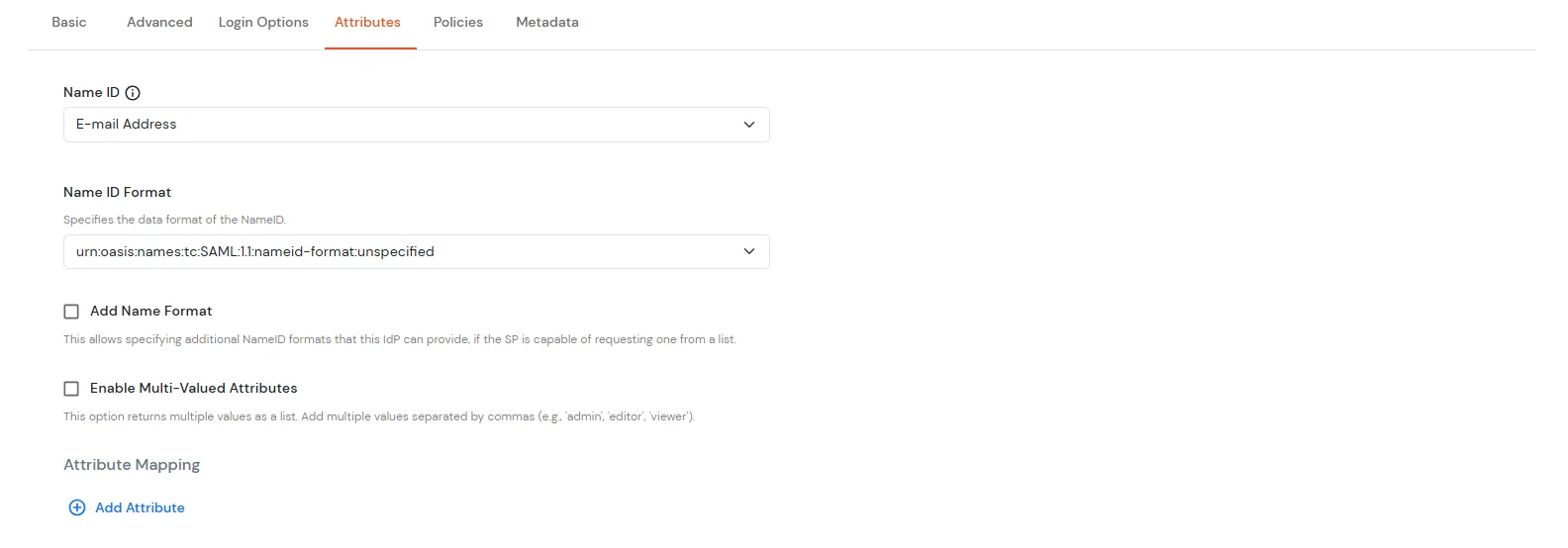
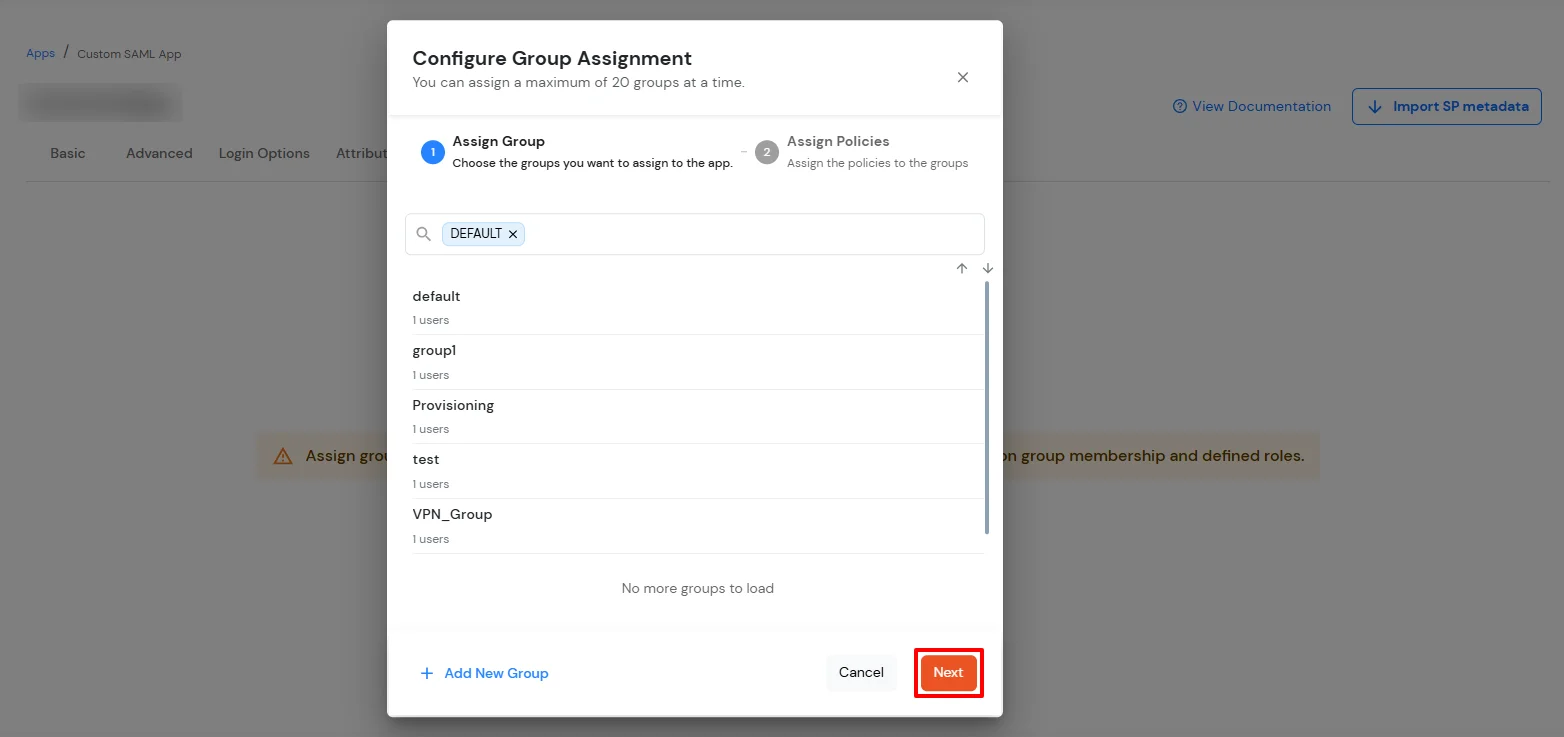
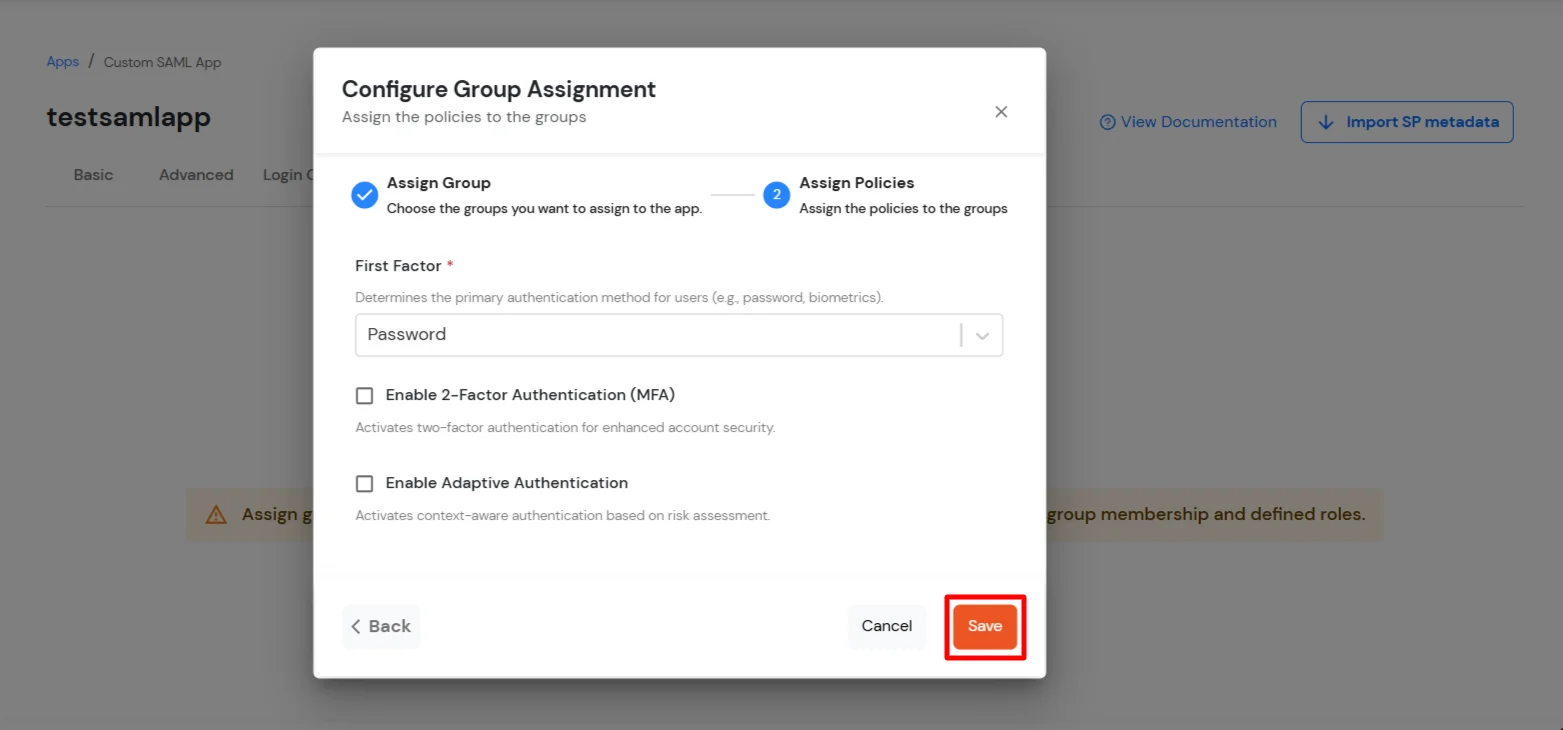
To get miniOrange metadata details in order to configure GitHub:
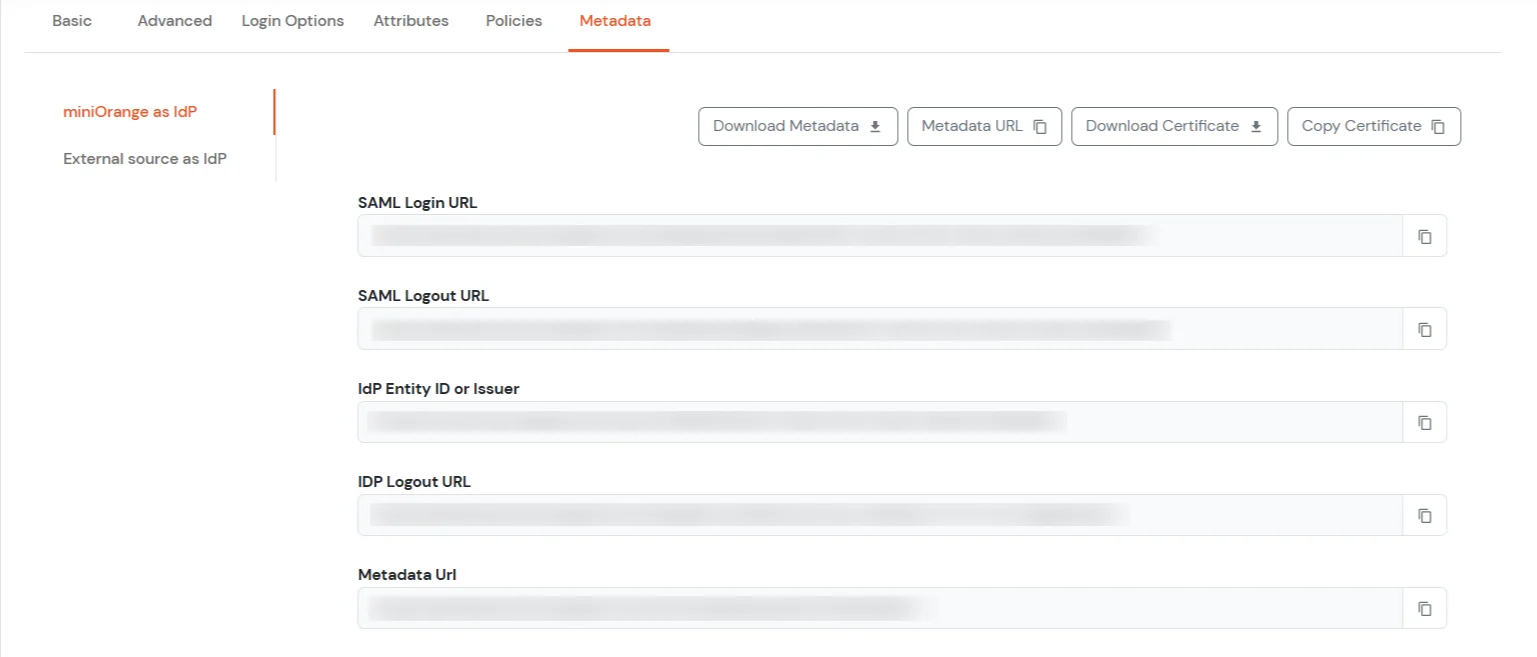
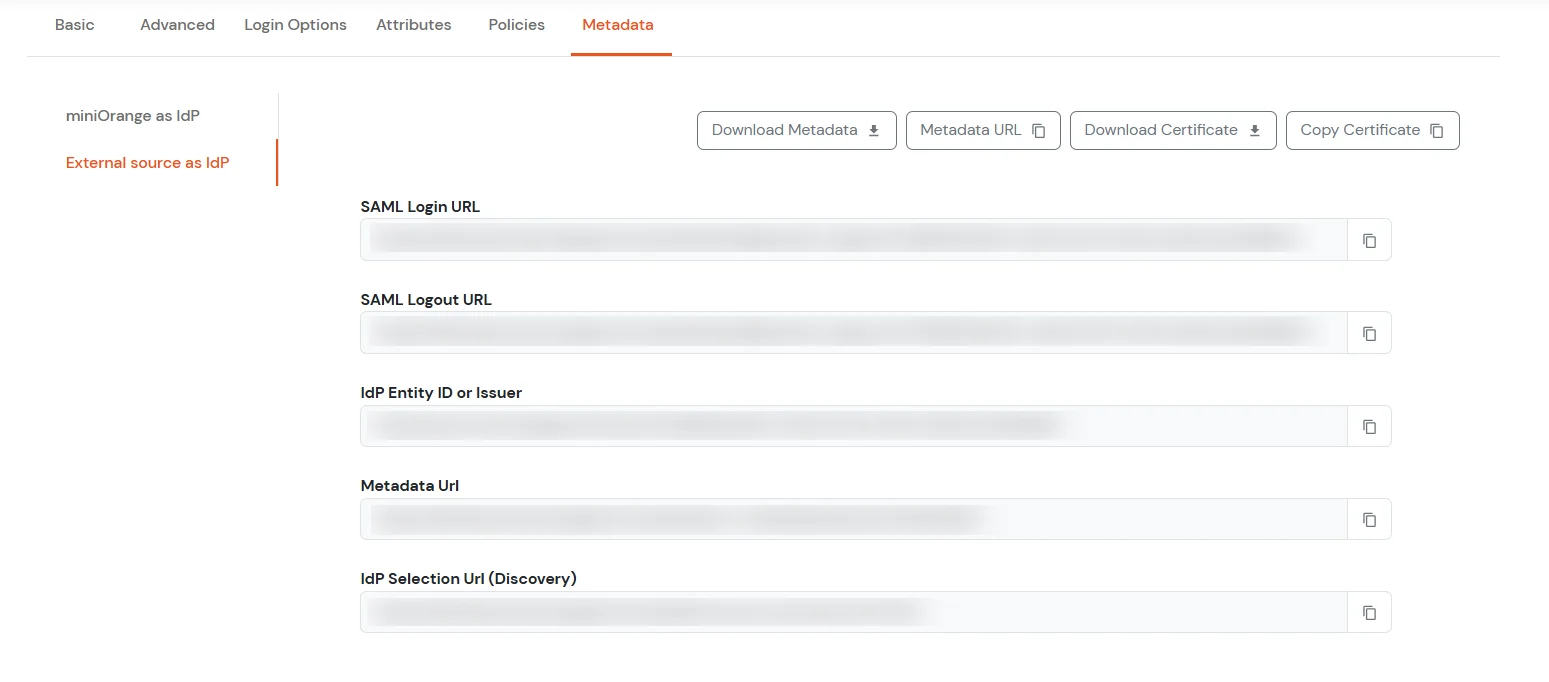
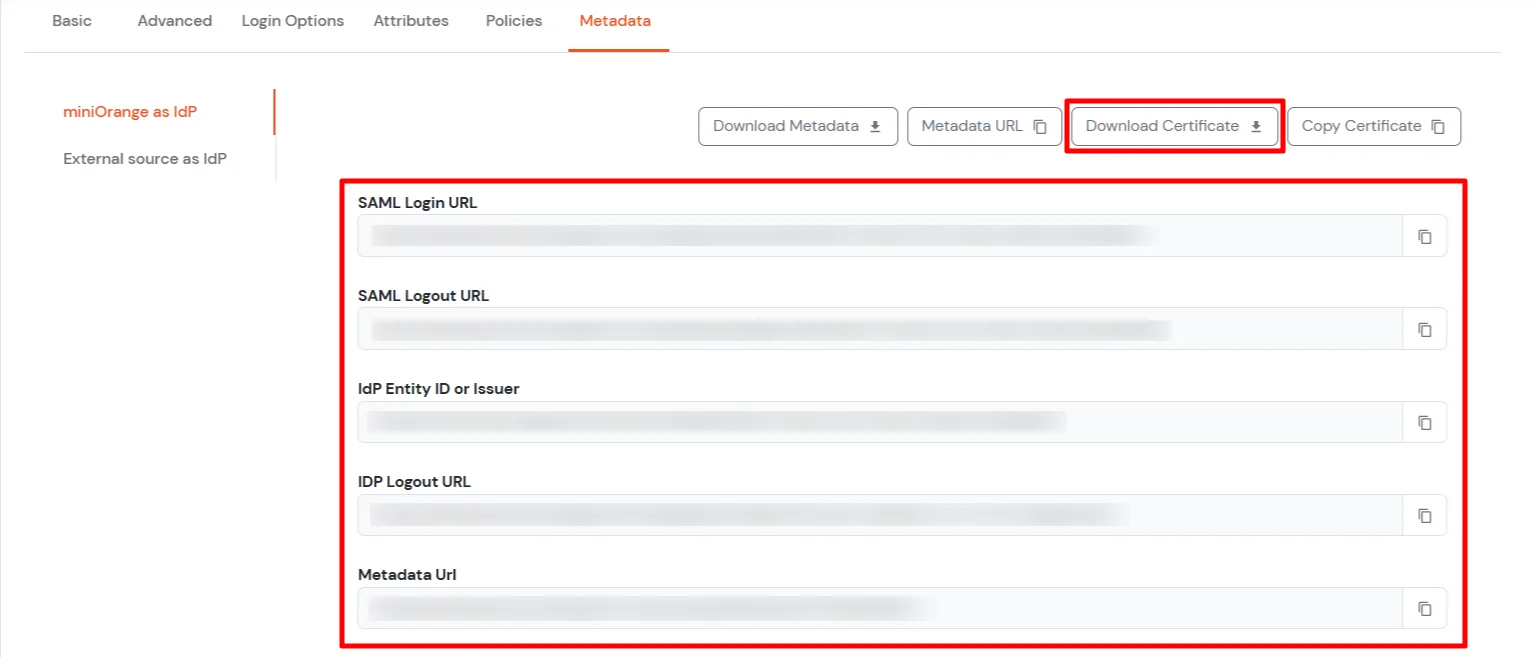


| Sign on URL | Enter the SAML Login URLs for single sign-on requests. |
| Issuer | Enter the IdP Entity ID or Issuer. This verifies the authenticity of sent messages. |
| Public certificate | Paste the X.509 Certificate to verify SAML responses |


Test SSO login to your GitHub account with miniOrange IdP:



Contact us or email us at idpsupport@xecurify.com and we'll help you setting it up in no time.
Yes, GitHub supports the SAML 2.0 protocol for Single Sign-On (SSO). Organizations using GitHub Enterprise Cloud can configure SAML SSO to control and secure access to their organization’s repositories and resources.
When SAML SSO is enabled, members accessing organization resources are redirected to their configured Identity Provider (IdP) for authentication. After successful login via the IdP, they are redirected back to GitHub with an active SAML session, permitting access.
GitHub officially supports and tests IdPs implementing the SAML 2.0 standard, including Microsoft Active Directory Federation Services (AD FS), Microsoft Entra ID (Azure AD), and Okta.
