Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×Configure ISVA as a Identity Provider (IdP) for Single Sign-On (SSO) into your applications, enabling users to authenticate themselves across multiple applications using their existing ISVA credentials without needing to sign in again.
In this setup, ISVA acts as the Identity Provider (IdP), miniOrange acts as a broker, and other applications act as Service Providers (SPs). This setup eliminates the need to manage different identities as all information is stored in a unified location - ISVA, simplifying the integration process and enhancing overall security.
Additionally, miniOrange's Identity Broker solution facilitates cross-protocol authentication , allowing the user to authenticate using ISVA via the SAML protocol and obtain access to the application, which supports SAML, OAuth and other protocols. This demonstrates how miniOrange Identity brokering enables users to authenticate across different protocols, improving the flexibility and interoperability of SSO solutions.
miniOrange offers free help through a consultation call with our System Engineers to configure SSO for different apps using ISVA as IDP in your environment with 30-day free trial.
For this, you need to just send us an email at idpsupport@xecurify.com to book a slot and we'll help you in no time.








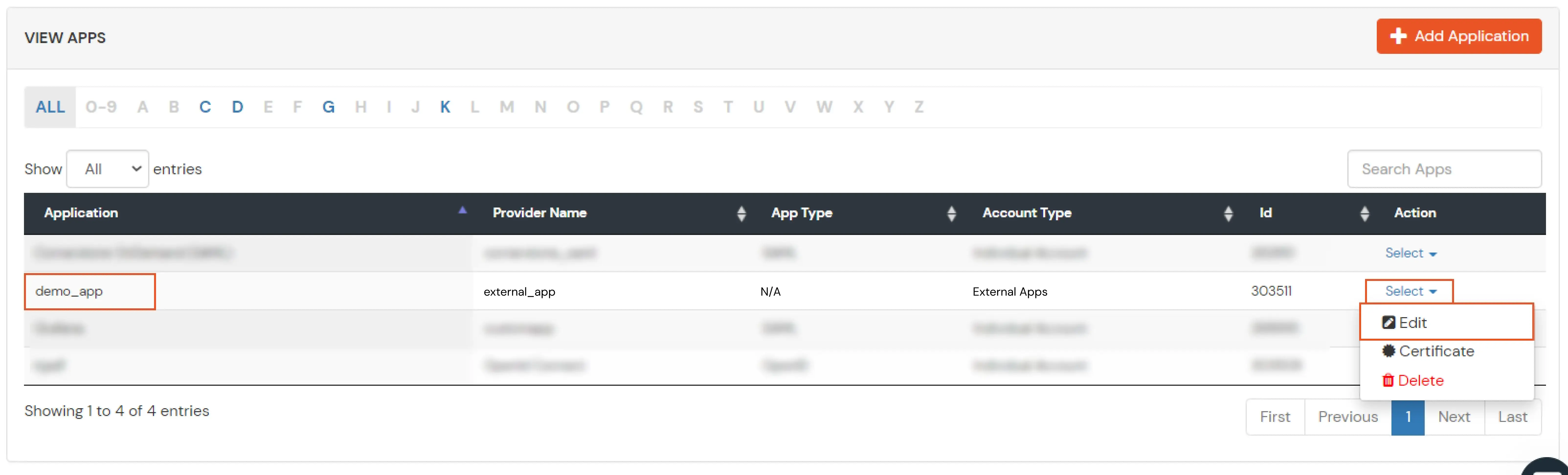
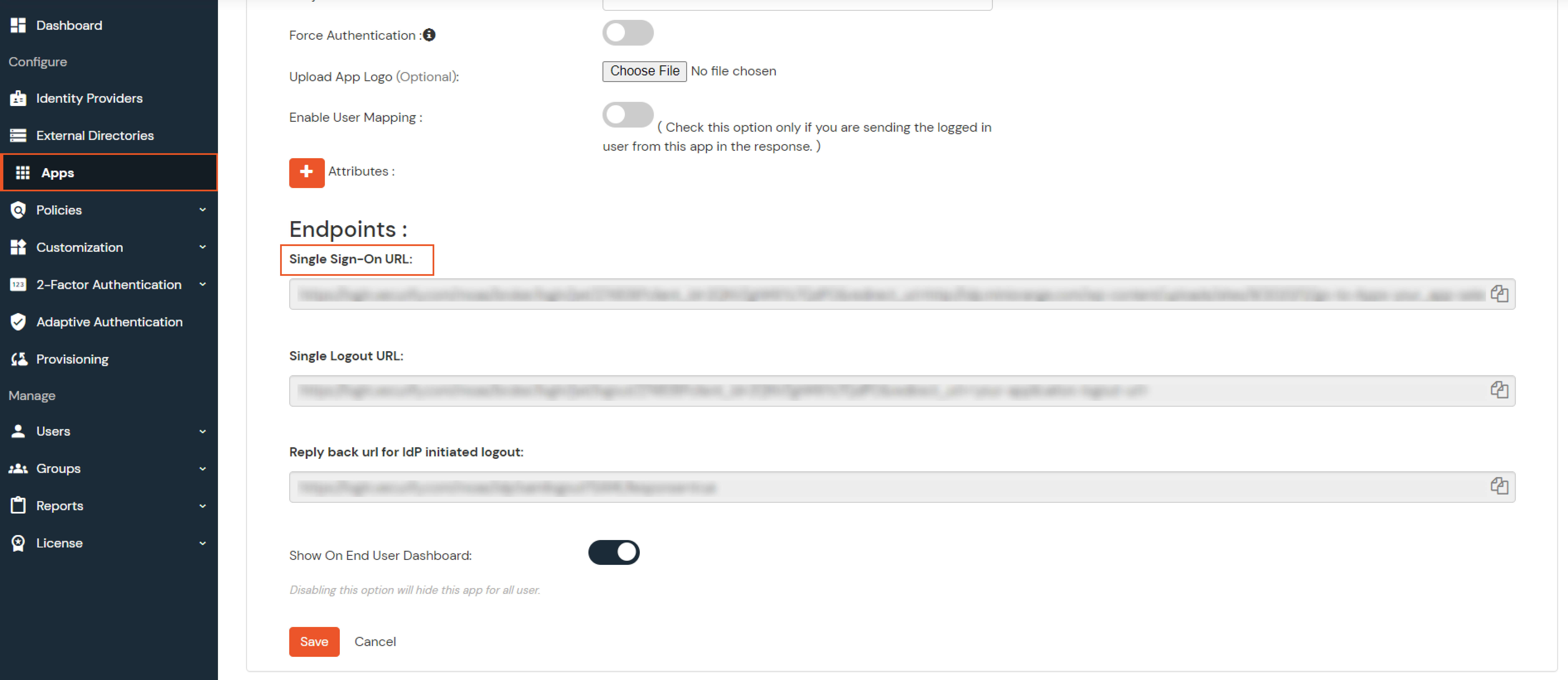
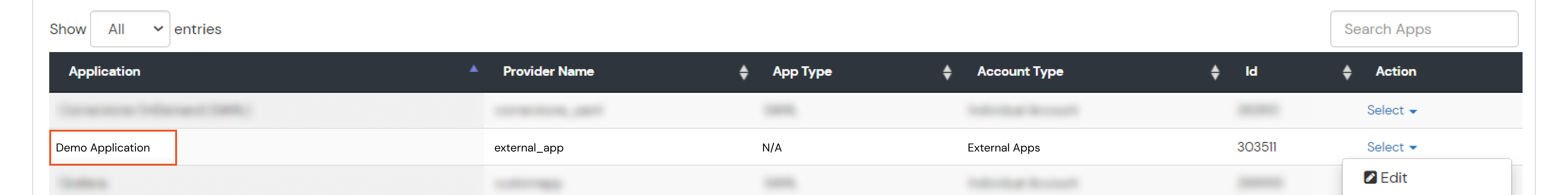
If you have already configured your application in miniOrange you can skip the following steps.
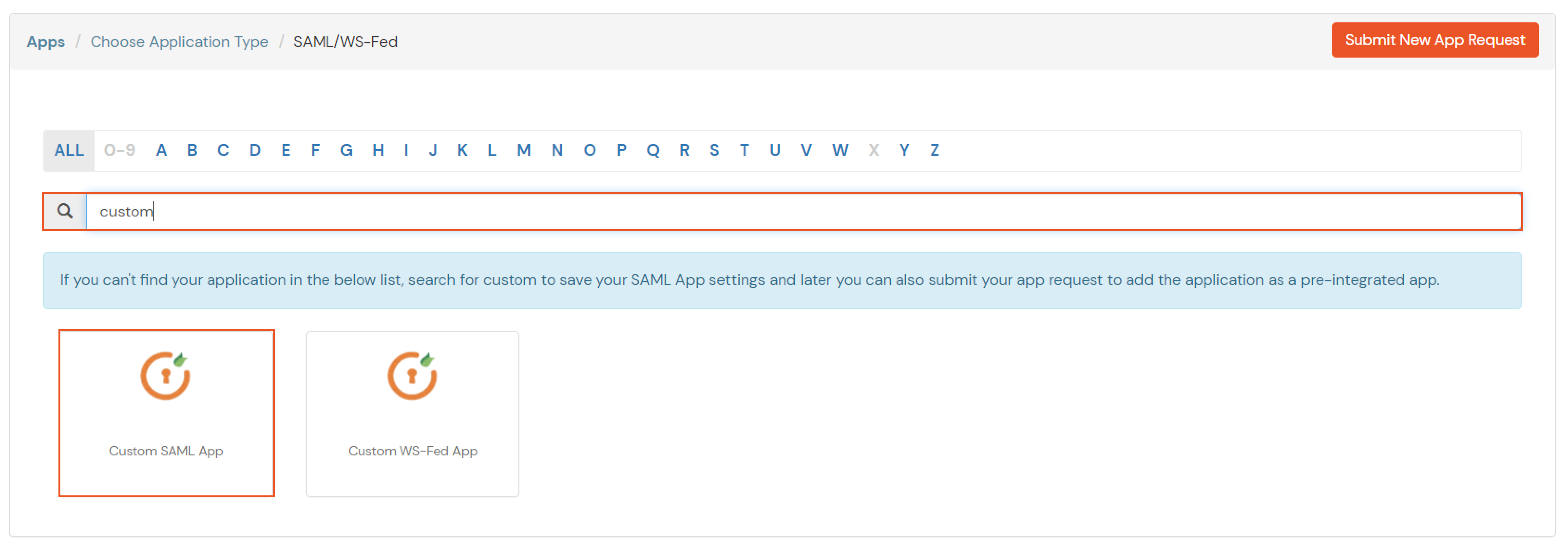
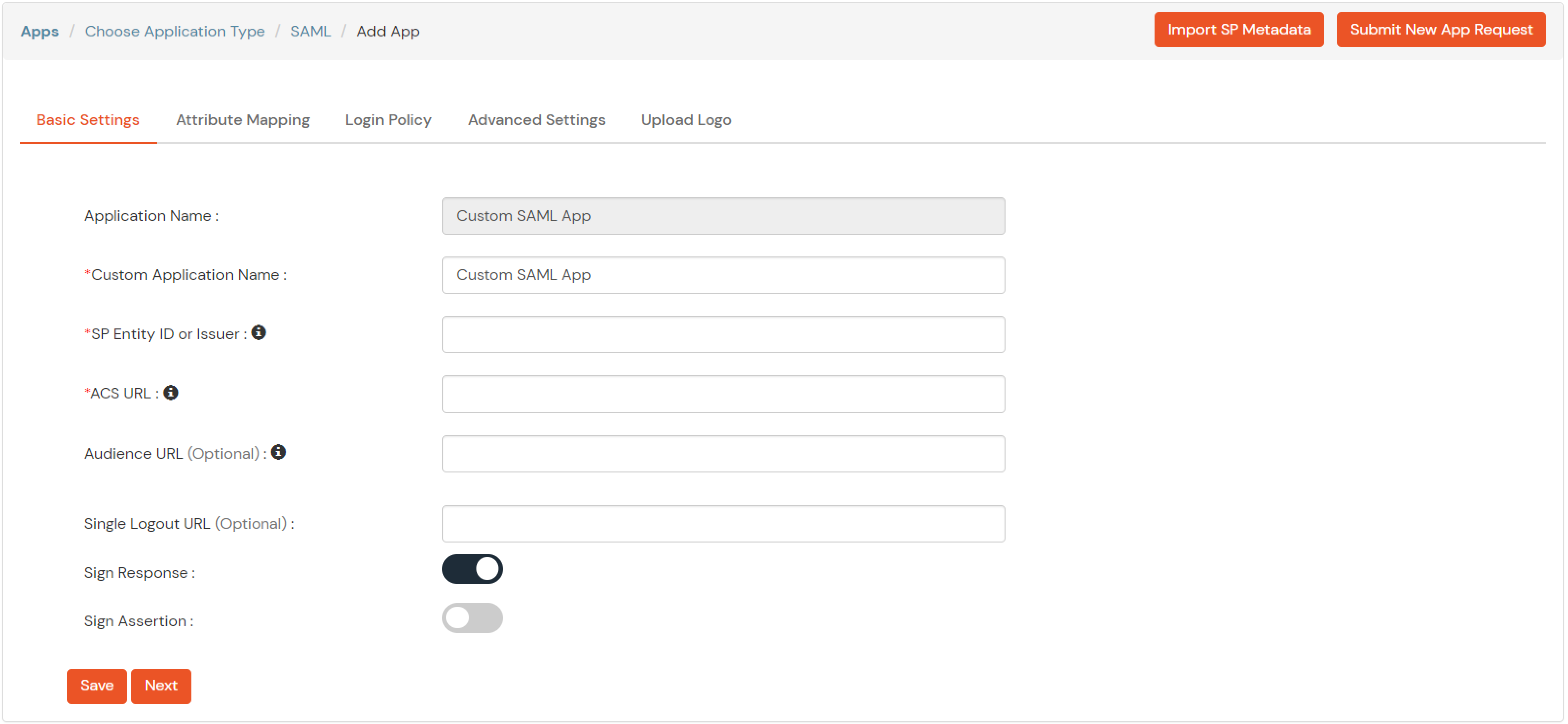
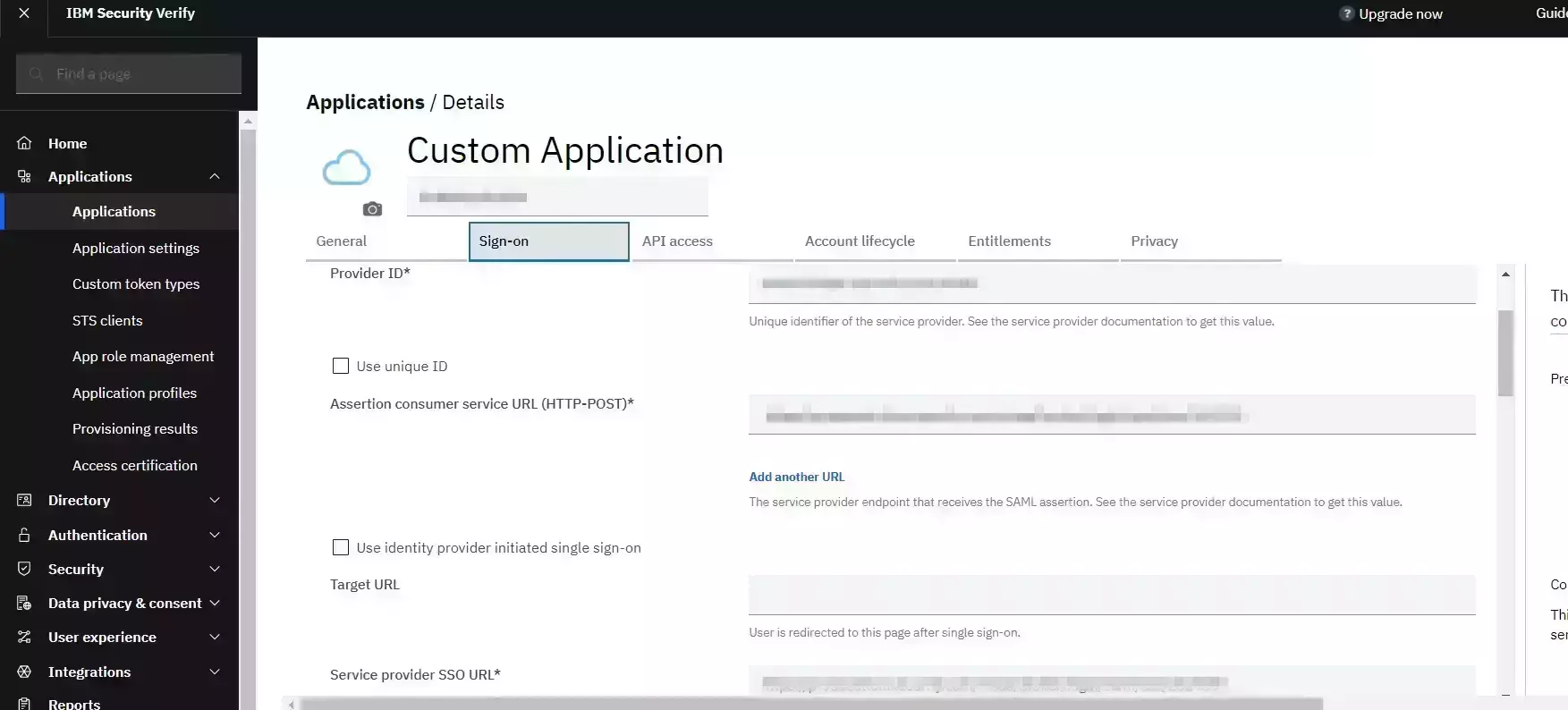
| Service Provider Name | Choose appropriate name according to your choice |
| SP Entity ID or Issuer | Your Application Entity ID |
| ACS URL X.509 Certificate (optional) | Your Application Assertion Consumer Service URL |
| NameID format | Select urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress |
| Response Signed | Unchecked |
| Assertion Signed | Checked |
| Encrypted Assertion | Unchecked |
| Group policy | Default |
| Login Method | Password |
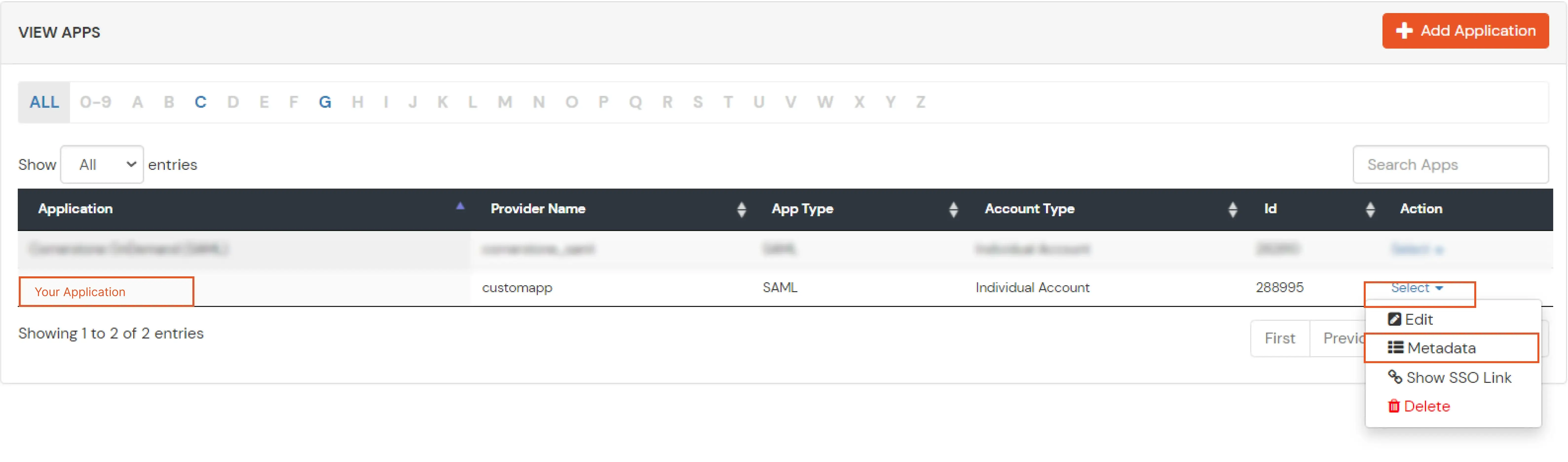
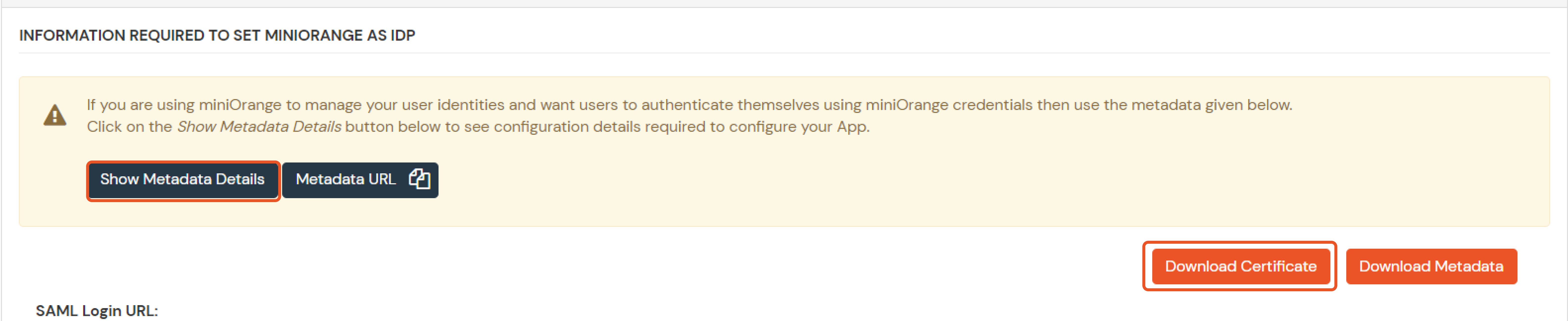
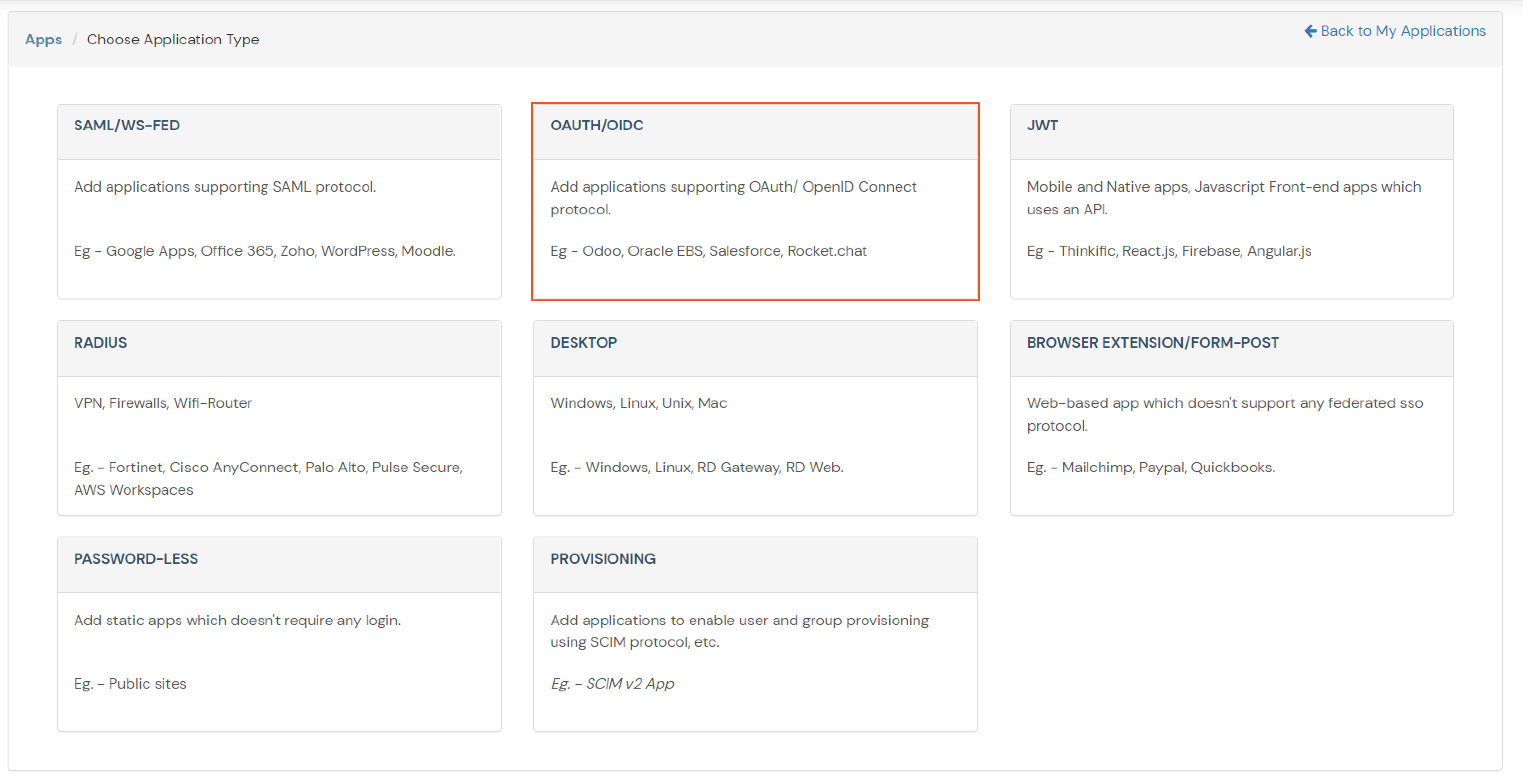

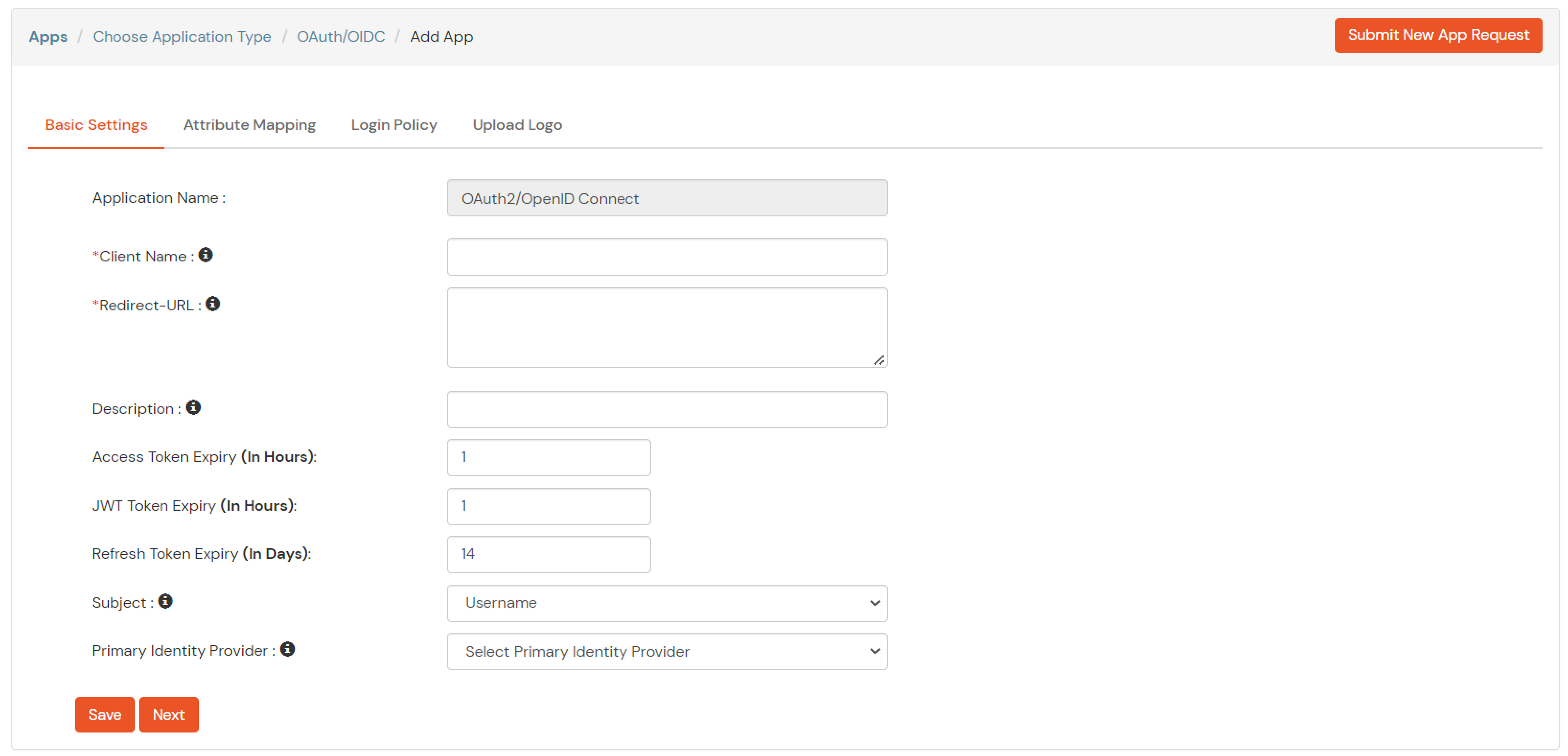
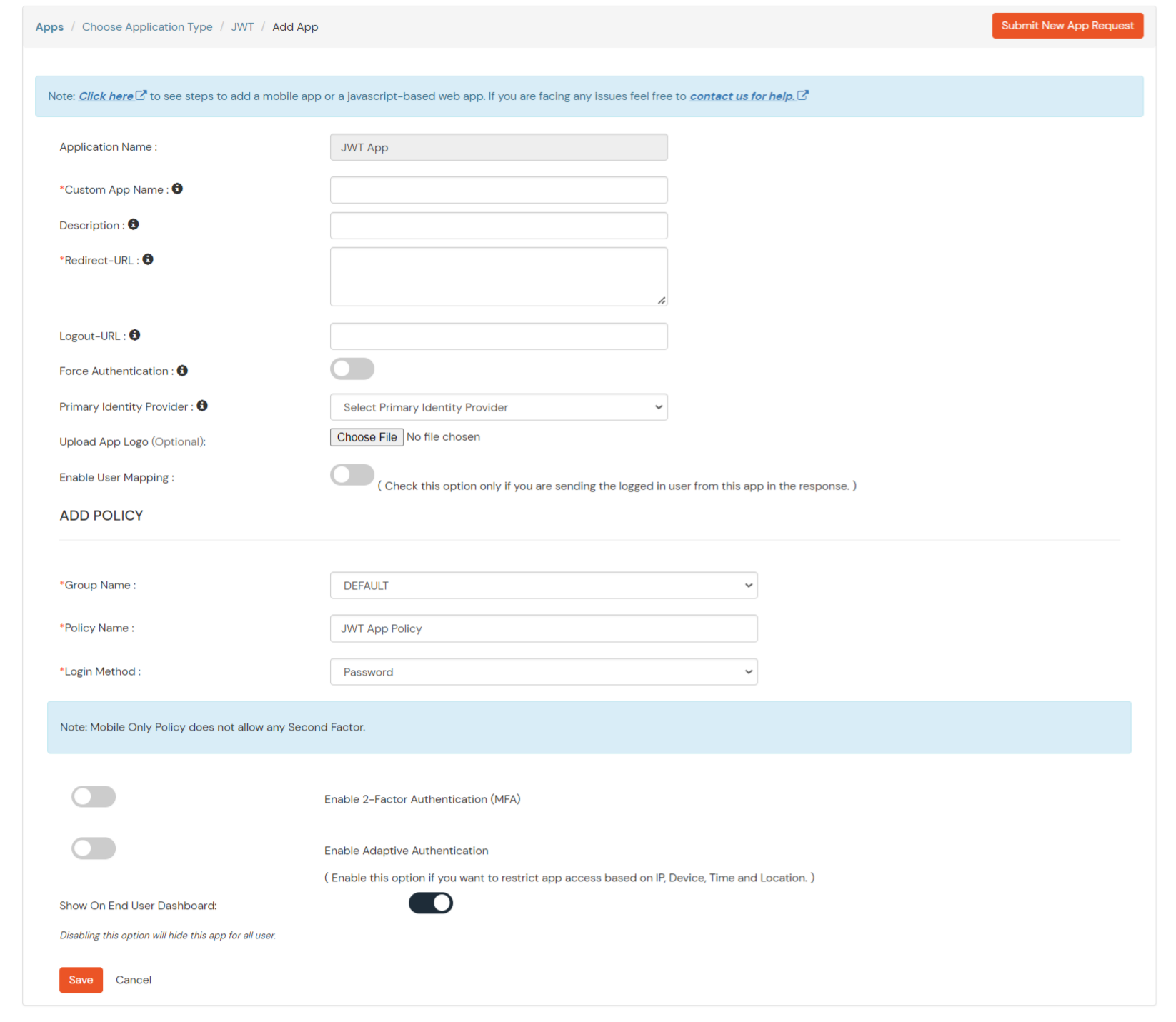
| Client Name | Add appropriate Name |
| Redirect URL | Get the Redirect-URL from your OAuth Client |
| Description | Add if required |
| Group Name | Default |
| Policy Name | As per your Choice |
| Login Method | Password |
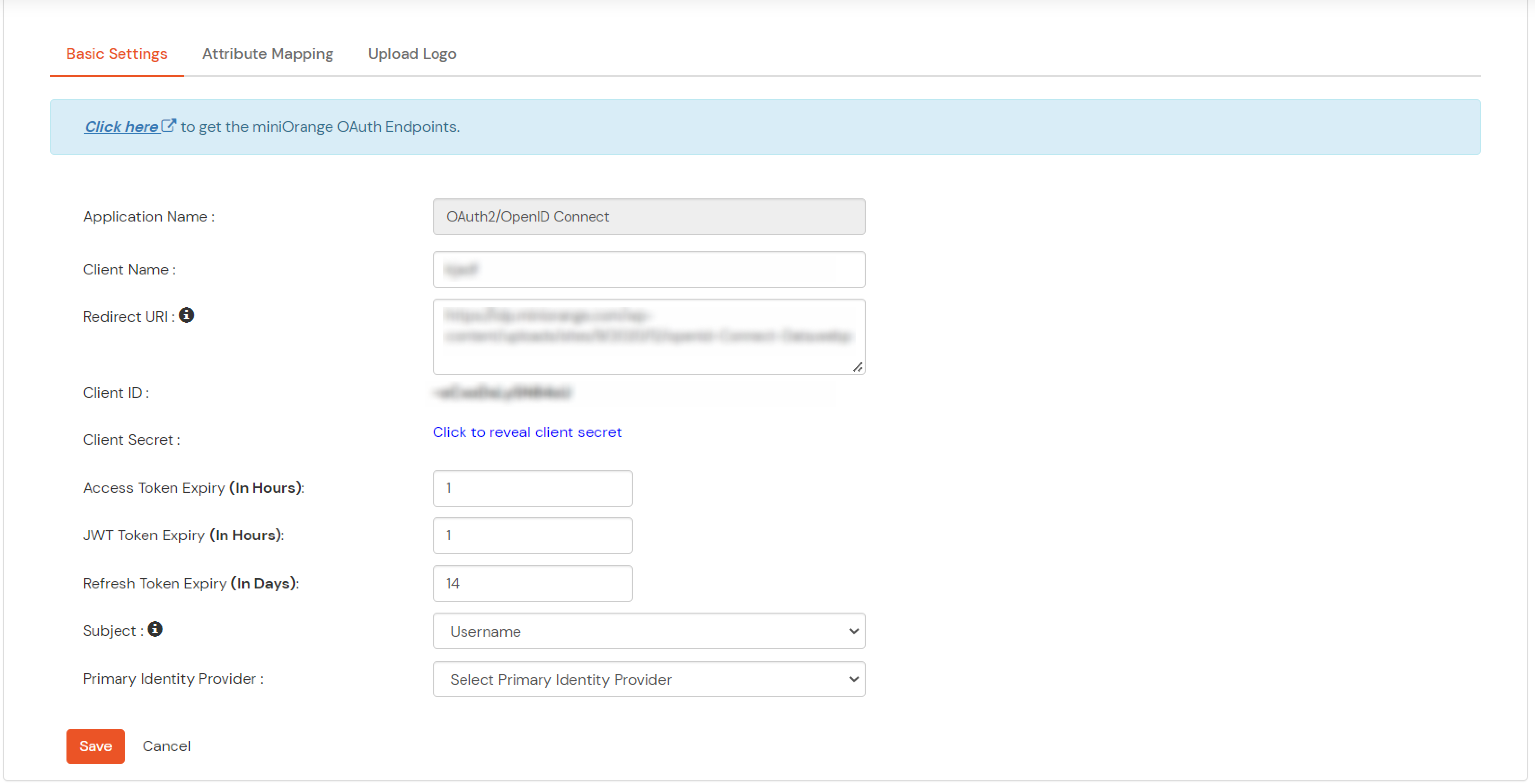
Note: Choose the Authorization Endpoint according to the identity source you configure.
https://{mycompany.domainname.com}/moas/idp/openidssohttps://{mycompany.domainname.com}/broker/login/oauth{customerid}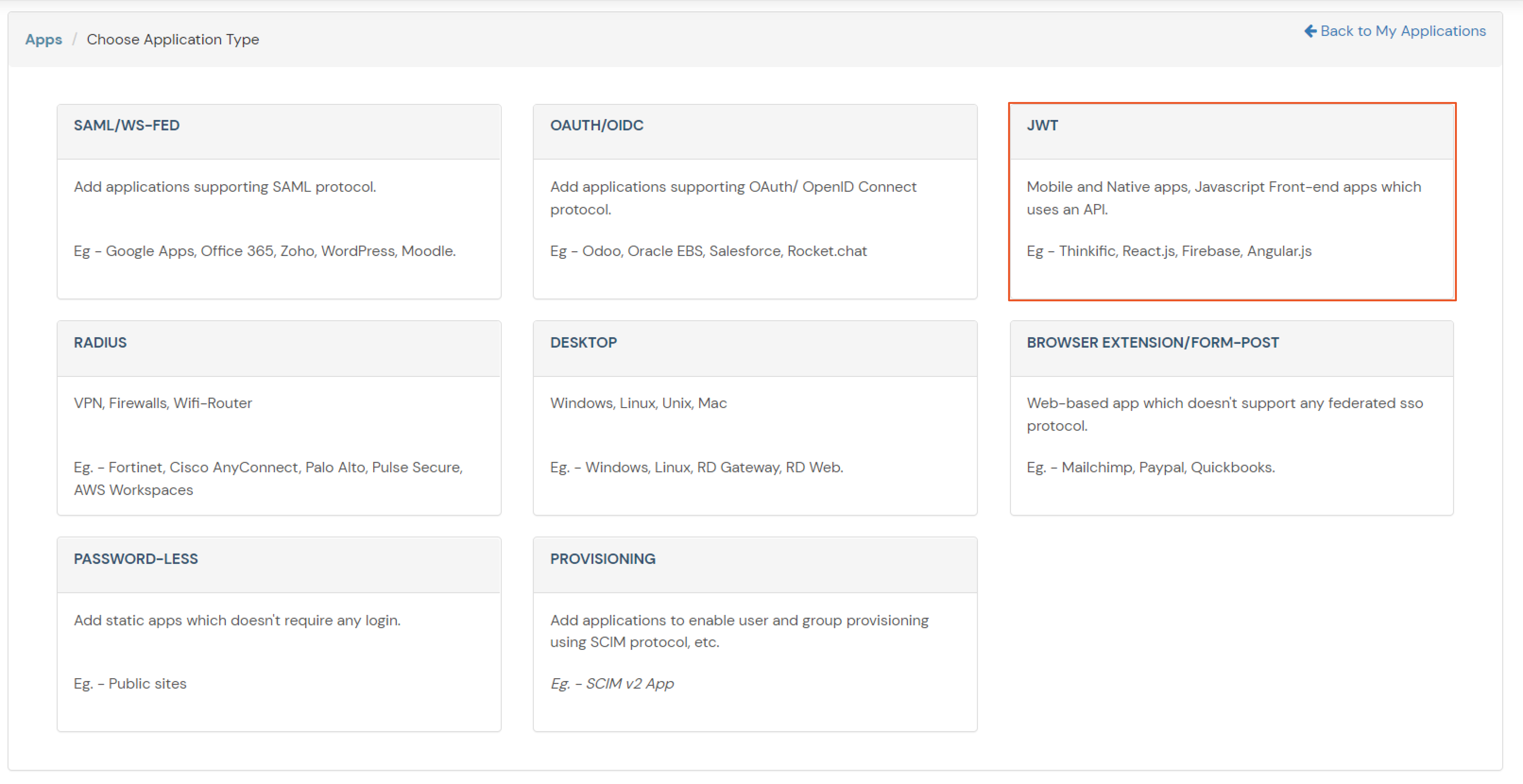
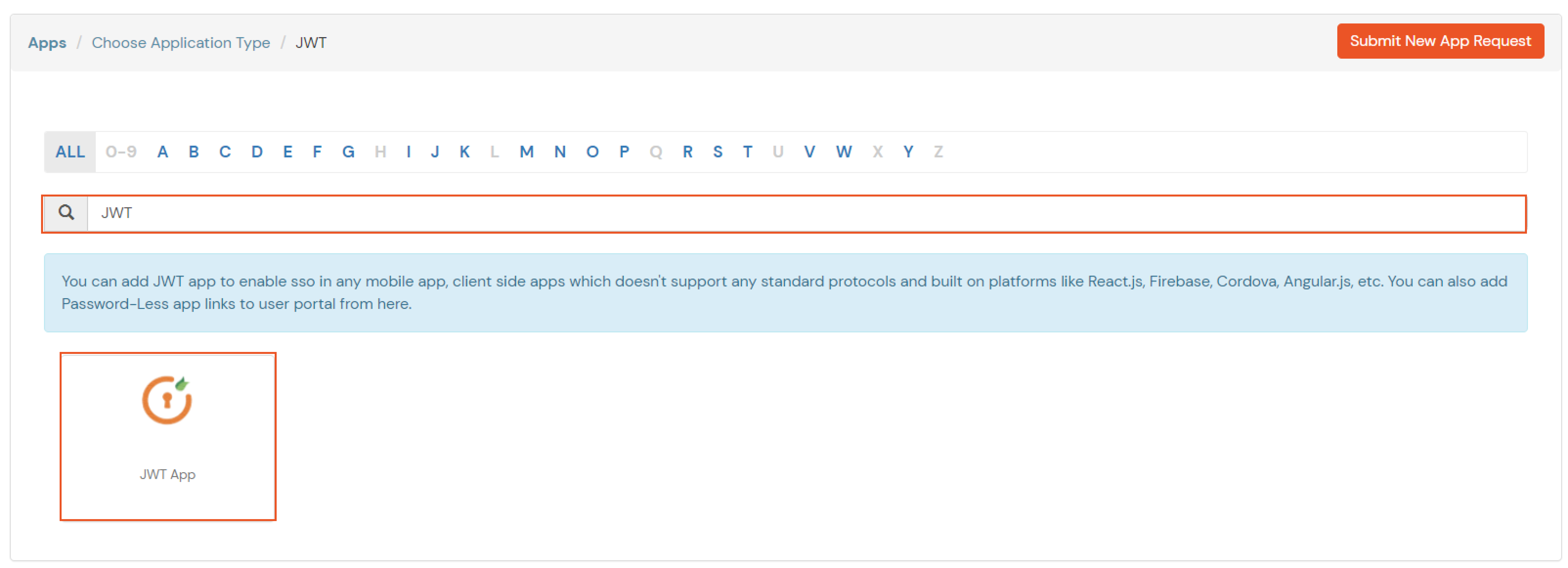
In case you are setting up SSO with Mobile Applications where you can't create an endpoint for Redirect or Callback URL, use below URL.
https://login.xecurify.com/moas/jwt/mobile